Understanding the Mustang Panda Threat Landscape
If you're managing security for a government agency, financial institution, or critical infrastructure organization, you're probably already thinking about advanced persistent threats. But here's the thing—the threat landscape keeps evolving faster than most security teams can adapt. One group in particular has been quietly expanding their toolkit, and their latest moves suggest they're preparing for more sophisticated operations than we've seen before.
Mustang Panda, a Chinese state-sponsored advanced persistent threat (APT) group, has become synonymous with precise, patient, and deeply strategic cyber operations. They're not running spray-and-pray campaigns. Every action they take aligns with specific intelligence objectives, usually targeting government entities, diplomatic institutions, and organizations with strategic value to Beijing's interests.
What makes Mustang Panda particularly dangerous isn't just their technical sophistication—it's their patience. They establish long-term persistence in networks, remain undetected for months or years, and systematically extract intelligence without triggering alerts. When security researchers finally identify their presence, they've already accomplished their mission and moved on to the next target.
Their operational focus splits across multiple geographic regions and target categories. Asia-Pacific governments are frequent targets, particularly those with competing interests against Chinese policy. European diplomatic institutions have also seen increased attention. Russia represents another interesting target profile—despite theoretical alignment on some geopolitical issues, China actively conducts espionage against Russian government networks to monitor intentions, military capabilities, and strategic planning.
The group's sophistication is evident in their tool development approach. Rather than relying on publicly available malware or off-the-shelf RATs, they maintain an extensive arsenal of custom-developed tools. This custom approach provides several advantages: built-in operational security, unique signatures that evade standard detection, and modular functionality that adapts to specific target environments. Cool Client exemplifies this philosophy—it's a purpose-built backdoor designed for specific operational roles within their broader attack infrastructure.
The Origins and Evolution of Cool Client
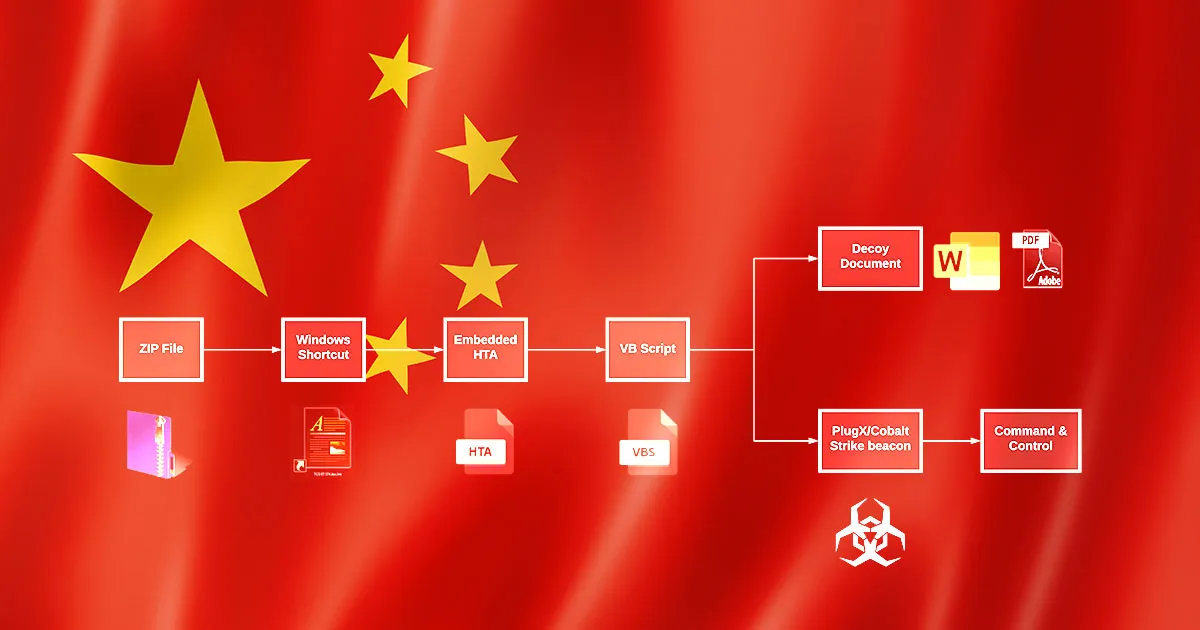
Cool Client first appeared in security research around 2022, but its development likely began months or years earlier. Initial observations suggested it was designed as a secondary backdoor, deployed after initial network compromise established by other tools like Plug X or Luminous Moth. This staged approach to backdoor deployment is intentional—each tool serves specific purposes in a diversified persistence strategy.
The reasoning behind this tiered approach makes operational sense. Primary backdoors like Plug X handle initial persistence and broad command execution. But if a primary backdoor gets detected and removed, having secondary backdoors ensures continued access even after defenders eliminate the obvious infection. Cool Client's role in this architecture centered on targeted data collection and credential theft rather than general-purpose command execution.
Early variants of Cool Client demonstrated capabilities typical of sophisticated Windows backdoors: system profiling, user enumeration, keystroke logging, file operations, and network tunneling. But the developers clearly viewed the initial version as a foundation rather than a finished product. The architecture allowed for modular expansion—they designed it from the start to accept plugins that extended functionality without recompiling the core backdoor.
The group's approach to malware development reflects lessons learned from previous operations. When defenders identify and analyze malware, they often discover architectural limitations that constrain operational capabilities. By building plugin-based architecture from the beginning, Mustang Panda avoided this limitation. They could add new capabilities in response to operational needs or detected detection mechanisms.
Analyzing the timeline of Cool Client's deployment reveals interesting operational patterns. The backdoor appears in cluster campaigns targeting specific regions or sectors, suggesting tailored deployment rather than mass distribution. Each variant shows incremental capability additions, implying active development and operational feedback. Some campaigns show variant-to-variant changes within weeks, indicating the group rapidly tests and deploys improvements.
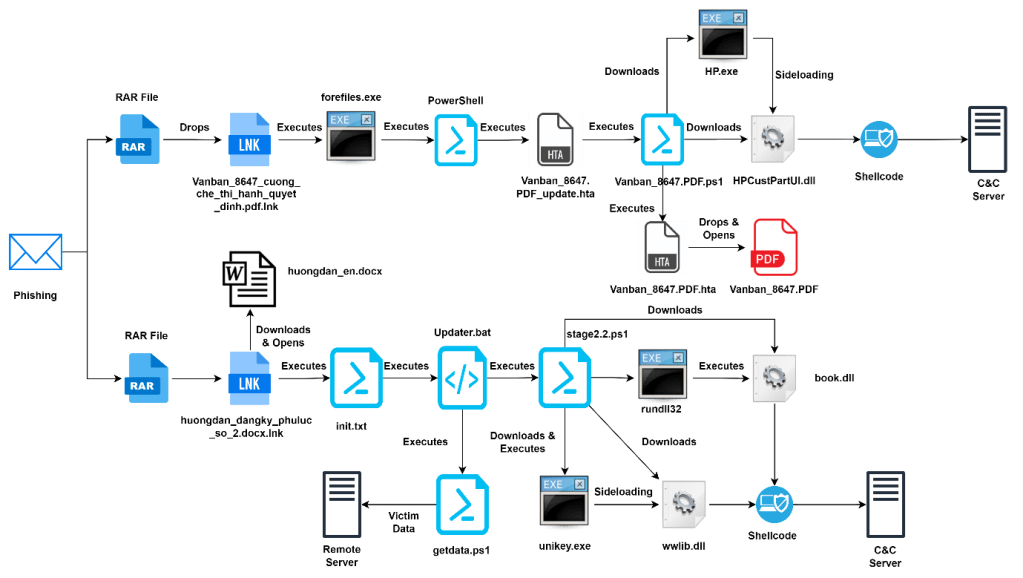
Estimated data shows CoolClient's development likely began before 2022, with significant deployment observed in 2022 and 2023. The modular architecture allowed for rapid evolution.
New Capabilities: Clipboard Monitoring and Credential Harvesting
The upgraded Cool Client variant represents a significant tactical shift toward direct credential harvesting and data exfiltration. The addition of clipboard monitoring functionality seems subtle, but it's actually brilliant from an attacker's perspective. Modern users constantly copy-paste sensitive information: passwords from password managers, cryptocurrency wallet keys, authentication tokens, API keys, and confidential URLs. All of this data flows through the clipboard.
Password manager integration has actually enabled this attack vector. Users rely on managers to generate complex passwords and auto-fill them into login forms. But here's where the problem emerges: when users need to manually authenticate to a system that doesn't support auto-fill, they copy the password from the manager and paste it into the application. During that brief moment when the password exists in the clipboard, clipboard monitoring malware can capture it.
The attack becomes even more effective when you consider what lives in clipboard history. Power users frequently copy-paste API keys into terminal sessions, database credentials into connection strings, SSH keys into deployment scripts, and sensitive URLs containing authentication parameters. Monitoring the clipboard doesn't just capture passwords—it captures the full spectrum of authentication credentials users handle throughout their workday.
HTTP proxy credential sniffing represents an even more insidious capability. Modern organizations increasingly use web proxies for content filtering, data loss prevention, and security monitoring. Users authenticate to these proxies with domain credentials or dedicated proxy credentials. When malware running in the user's context monitors HTTP proxy authentication, it harvests these credentials with perfect accuracy.
Why does this matter beyond the obvious credential theft? Because proxy credentials often apply across entire organizational networks. Compromise a proxy credential, and you gain the ability to direct network traffic through your own infrastructure, monitor unencrypted traffic, inject malicious content, or bypass security controls that rely on proxy authentication. For attackers, harvesting proxy credentials is more valuable than individual user passwords because the impact scales across the entire organization.
The technical implementation of these features probably leverages Windows API functions available to user-mode processes. Monitoring clipboard contents requires accessing the clipboard chain or using functions like Get Clipboard Data(). Proxy credential sniffing likely hooks into Windows credential storage or monitors network traffic at the WINSOCK layer. All of these techniques operate from within the user's security context, avoiding the kernel-level monitoring that might trigger endpoint protection alerts.
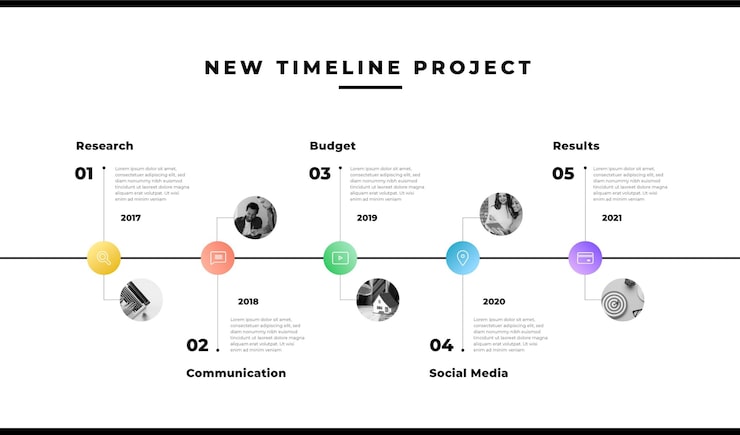
The modular plugin architecture of CoolClient offers significant operational advantages, such as reduced footprint and enhanced persistence management. (Estimated data)
Expanded Plugin Ecosystem and Operational Flexibility
The evolution toward an expanded plugin ecosystem fundamentally changes how Cool Client functions operationally. Rather than a monolithic backdoor doing everything, the new architecture treats Cool Client as a platform for modular capabilities. Each plugin provides specific functionality that can be deployed, updated, or removed independently based on operational needs.
This architectural approach provides several operational advantages that explain why sophisticated groups invest in this level of engineering. First, it reduces the footprint of the main backdoor—the core Cool Client process remains relatively small and less detectable, while plugins add functionality without bloating the main executable. Second, it allows for specialized plugin development optimized for specific tasks rather than generic code trying to do everything. A file manager plugin optimized for exfiltration works better than general file operations in the main backdoor. Third, it enables rapid capability deployment—developers can write and test new plugins without touching the core backdoor, reducing risk of introducing bugs that might break persistence.
The remote shell plugin appears designed for interactive command execution, giving operators the ability to type commands and receive output in real-time. This interactive interface contrasts with batch command execution, which many simpler backdoors use. Interactive command shells allow experienced operators to explore the compromised system in real-time, adapting to what they discover rather than following pre-scripted command sequences.
The service management plugin deserves particular attention. Windows services run with SYSTEM privileges and start automatically when the system boots, making them attractive persistence mechanisms. A plugin dedicated to managing services suggests the group plans to use Cool Client for persistence management—creating services that maintain access even if the main backdoor binary gets detected and removed. The plugin probably provides functions to enumerate running services, create new services pointing to malicious executables, modify service configuration, and manage service startup triggers.
Enhanced file management plugins provide more than basic file operations. They probably include capabilities like recursive directory enumeration with filtering, archive creation for efficient exfiltration, file attribute modification to hide malicious files, and perhaps clever use of alternate data streams or other Windows filesystem features to hide data. Sophisticated file management in targeted intrusions matters because exfiltrating the right data matters more than exfiltrating everything.
The credential theft via infostealer plugins indicates integration with broader malware families. Infostealers typically focus on harvesting stored credentials from browsers, email clients, VPN applications, and other software where users save passwords. Integrating infostealer functionality as a plugin suggests the group doesn't need to deploy separate infostealer malware—they can use Cool Client's plugin system to add this capability when targeting specific systems.
Cloud Services for Covert Data Exfiltration
One of the most strategically interesting capabilities in the updated Cool Client is the use of legitimate cloud services for exfiltrating stolen data. This represents a sophisticated understanding of how modern network security architecture works and how defenders balance visibility against operational practicality.
Most organizations restrict outbound connections to known malicious domains and block common malware command-and-control infrastructure. But blocking all cloud services would cripple legitimate business operations. When operators use cloud storage services like One Drive, Dropbox, Google Drive, or similar platforms for exfiltration, they're hiding malicious traffic within the massive volume of legitimate cloud service traffic. A file uploaded to attacker-controlled cloud storage accounts looks identical to legitimate cloud backups from a network monitoring perspective.
This technique also avoids the operational security risks of traditional command-and-control infrastructure. Running C2 servers requires operational security discipline, infrastructure investment, and increased risk of detection. Using cloud services transfers hosting to legitimate, well-resourced companies with sophisticated uptime and security. The attacker doesn't need to maintain servers or worry about infrastructure being taken offline—cloud providers handle all of that.
The integration suggests the group maintains multiple cloud storage accounts for each operation, potentially registered with fake identities or compromised credentials. When operating against target networks, they configure Cool Client with cloud service credentials specific to that operation. Stolen data gets packaged, compressed, and uploaded to these cloud accounts through authenticated connections that cloud providers see as normal user activity.
Defense against this approach requires understanding that data exfiltration isn't limited to suspicious domains. Defenders need to monitor what data travels to cloud services, potentially implement policies preventing uploads of certain file types to cloud storage, and require authentication for cloud service access through corporate identity systems rather than arbitrary cloud accounts.
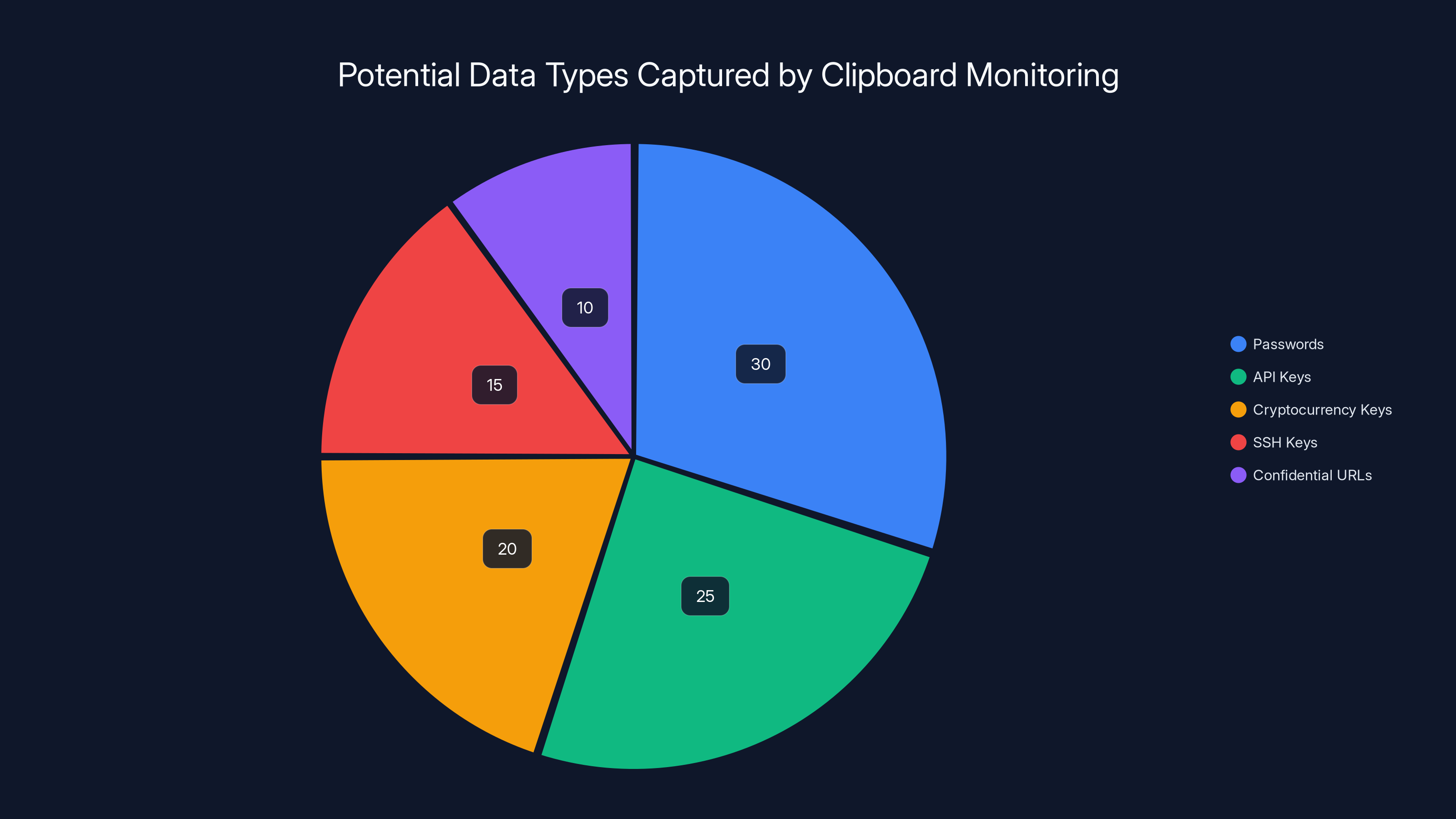
Clipboard monitoring malware can capture a wide range of sensitive data types. Passwords and API keys are the most frequently captured, followed by cryptocurrency keys and SSH keys. (Estimated data)
Geographic Focus: Asia-Pacific and Diplomatic Targets
Kaspersky researchers observed the upgraded Cool Client variant in attacks against government entities across Myanmar, Mongolia, Malaysia, and Pakistan. This geographic clustering isn't random—it reflects strategic intelligence priorities aligned with Chinese government interests. Each of these countries occupies important positions relative to China's regional aspirations and strategic competition.
Myanmar represents a key geographic and geopolitical interest for China. The country sits along crucial trade routes connecting China to the Indian Ocean and serves as a source of natural resources. Chinese economic interests include significant infrastructure investments and resource extraction projects. Monitoring Myanmar's government communications provides intelligence about internal political stability, foreign policy intentions, and potential challenges to Chinese interests.
Mongolia occupies another strategically important position as a buffer state between China and Russia. Understanding Mongolian government intentions regarding resource development, energy policy, and foreign relations directly impacts Chinese strategic planning. The country's mineral resources and geographic position make it a consistent intelligence target.
Malaysia's position in Southeast Asia makes it valuable for monitoring regional geopolitics, particularly around South China Sea disputes and regional power dynamics. Malaysian government communications would reveal positions on critical issues like maritime claims, freedom of navigation, and regional alliance-building that affects China's strategic calculations.
Pakistan represents a long-standing ally with significant Chinese investment through Belt and Road Initiative projects. Despite the alliance relationship, China maintains active intelligence gathering on Pakistani government operations, military capabilities, and internal political dynamics. Understanding Pakistani perspectives on regional issues, particularly regarding India and Afghanistan, informs Chinese strategic planning.
The presence of Cool Client on Russian government networks, while seemingly surprising given China-Russia relations, actually reflects strategic realities. China maintains active intelligence operations against all significant powers, including supposed allies. Monitoring Russian government systems provides insight into Russian intentions, military capabilities, Far East development strategies, and how Russia views China. This intelligence gathering continues despite public statements about partnership.
Targeting government entities rather than private sector organizations reflects Mustang Panda's intelligence mission. Corporate espionage contributes to technology development, but government espionage answers strategic questions about foreign policy intentions, military capabilities, internal political dynamics, and decision-making processes. The choice of targets directly supports high-level policy analysis and strategic planning.

Technical Architecture and Persistence Mechanisms
Understanding how Cool Client establishes and maintains persistence reveals the operational sophistication behind the backdoor. The updated variant likely employs multiple persistence mechanisms, ensuring that even if defenders detect and remove one, others remain functional.
UAC (User Account Control) bypass techniques have been a focus of Windows malware development for years, and Cool Client apparently includes multiple such techniques. These bypasses allow malware running with standard user privileges to execute actions requiring elevated privileges without triggering UAC prompts that would alert users. Techniques like COM object hijacking, token impersonation, and scheduled task abuse can all elevate privileges silently.
DLL sideloading represents another persistence approach in the malware's toolkit. The technique involves placing a malicious DLL in a directory where legitimate Windows applications or third-party software load libraries. When the application runs, it loads the malicious DLL instead of the intended library. The malware then patches the application's normal execution flow, maintaining persistence while the legitimate application continues running and appearing normal to users.
Service installation provides the ultimate persistence mechanism on Windows systems. Services run with SYSTEM privileges, start automatically during boot, and survive user logouts. A service-based persistence mechanism ensures Cool Client remains active even after the user logs off or the system reboots. The service probably masquerades as a legitimate Windows service through careful naming and registry manipulation.
Registry modifications hide the backdoor's presence in plain sight. Windows registry contains countless legitimate entries, and standard users rarely examine registry contents. Malware can hide configuration data, communication targets, and plugin lists in legitimate-looking registry keys, making the backdoor difficult to discover through casual system inspection.
The in-memory execution capability deserves specific attention. Rather than dropping files to disk where endpoint protection might detect them, the updated Cool Client can execute code entirely in memory. This technique loads malicious code into memory, executes it from there, and avoids creating detectable artifacts on the filesystem. In-memory execution significantly complicates forensic analysis and detection because there's no file to scan.

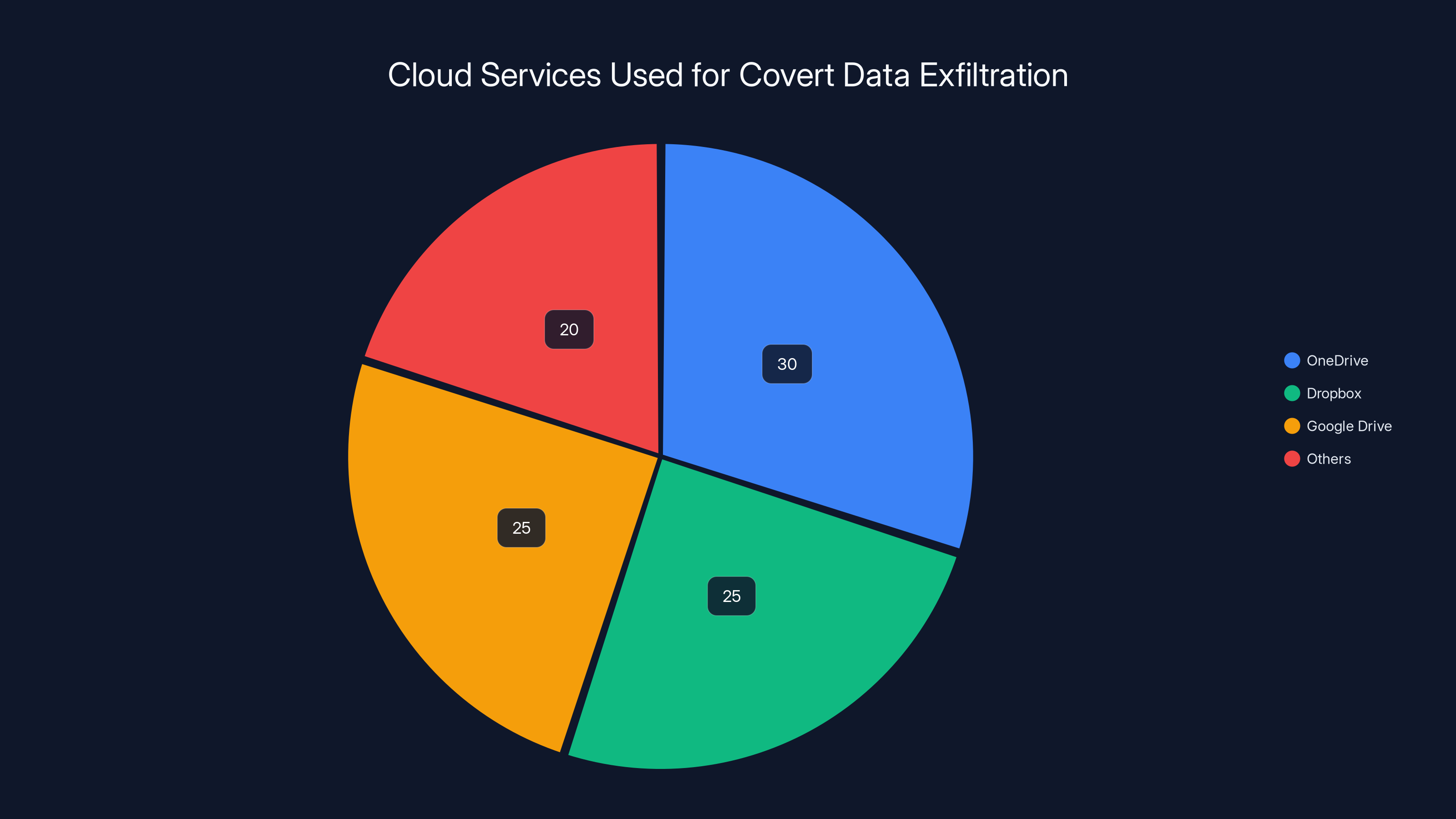
Estimated data suggests OneDrive, Dropbox, and Google Drive are commonly used for covert data exfiltration, with OneDrive slightly leading.
Detection Challenges and Evasion Tactics
Detecting Cool Client presents substantial challenges because the backdoor was specifically designed to avoid triggering standard security controls. The update cycle actually compounds detection challenges by regularly introducing variations that might bypass previously developed detection signatures.
The plugin architecture means that core signatures identifying the main backdoor binary might match one variant but not others. Operators can modify the plugin loading mechanism, change how plugins receive commands, or alter the communication protocol between the main backdoor and plugins. Each variation requires new detection logic, turning detection into an endless game of catch-up.
Cloud service exfiltration particularly complicates detection because the traffic appears legitimate. A file upload to One Drive looks identical to legitimate user backups. Distinguishing between data exfiltration and legitimate cloud service use requires analyzing content patterns, detecting when files uploaded don't match typical user behavior, or recognizing that the cloud account receiving uploads isn't registered to anyone in the organization.
Credential harvesting through clipboard monitoring leaves minimal evidence. There's no network traffic indicating credential extraction—the malware reads local clipboard contents and stores them in memory. Without endpoint monitoring that captures API calls to clipboard functions, detecting this activity becomes nearly impossible. The stolen credentials only become obvious when defenders notice them being used in suspicious ways.
The group's operational security discipline further complicates detection. They likely rotate command-and-control infrastructure frequently, use encrypted communications, deploy backdoors infrequently against specific targets rather than mass-infecting systems, and maintain low behavioral profile to avoid triggering anomaly detection. The combination of careful targeting, limited deployment, and technical sophistication means Cool Client intrusions might remain undetected for extended periods.
Endpoint Protection Platform (EPP) solutions struggle with Cool Client because the backdoor doesn't necessarily perform obviously malicious actions frequently. Modern EPP relies on behavioral analysis to catch unknown malware—actions like suspicious registry modifications, suspicious process creation, or suspicious network connections trigger investigation. But Cool Client's designers understand this detection philosophy and built the backdoor to minimize suspicious-looking behavior. The clipboard monitoring happens via normal API calls, file uploads occur through legitimate cloud services, and command execution happens through standard Windows process mechanisms.
Defensive Strategies for Government and Critical Infrastructure
Organizations targeted by Mustang Panda need defensive approaches that address both technical indicators and operational patterns. Standard antivirus and basic endpoint protection prove insufficient against an adversary of this sophistication.
Network segmentation provides foundational defense by limiting lateral movement after initial compromise. If an attacker compromises a user's workstation, network segmentation ensures they can't immediately access sensitive servers, databases, or administrative systems. Cool Client's plugins include capabilities for exploring network topology and locating valuable assets—segmentation forces attackers to spend time and operational resources moving through multiple security boundaries.
Credential security takes on heightened importance when facing attackers that specifically target credential harvesting. Multi-factor authentication for sensitive systems prevents compromised passwords from enabling unauthorized access. Passwordless authentication mechanisms like Windows Hello for Business or FIDO2 security keys resist credential-based attacks entirely. Service accounts with regularly rotating credentials limit the damage from compromised credentials.
Endpoint Detection and Response (EDR) solutions provide visibility into behavior that standard antivirus misses. EDR continuously monitors processes, network connections, registry modifications, and file system changes. While Cool Client is designed to minimize suspicious behavior, EDR systems might detect plugin loading, suspicious credential access, or unusual inter-process communication. The key advantage is that EDR provides investigation capabilities—even if individual actions seem legitimate, EDR stores detailed forensic data enabling incident responders to reconstruct attacker activity.
Hunting for Cool Client requires understanding its likely behavior patterns rather than waiting for signature-based detection. Hunters should look for processes accessing clipboard functions, unexpected cloud storage authentication, service creation with unusual timing or naming, or registry modifications in locations typically used for persistence. The hunt becomes more effective when analysts understand that Cool Client likely appears alongside other Mustang Panda tools and behaviors.
Incident response planning should account for the possibility that detected intrusions might represent late-stage discovery of long-existing compromises. Cool Client's focus on persistence suggests the group intends long-term presence, meaning even after detecting and removing one instance, other persistence mechanisms might remain. Comprehensive incident response requires assuming the adversary has been present for an unknown duration and conducting investigation accordingly.

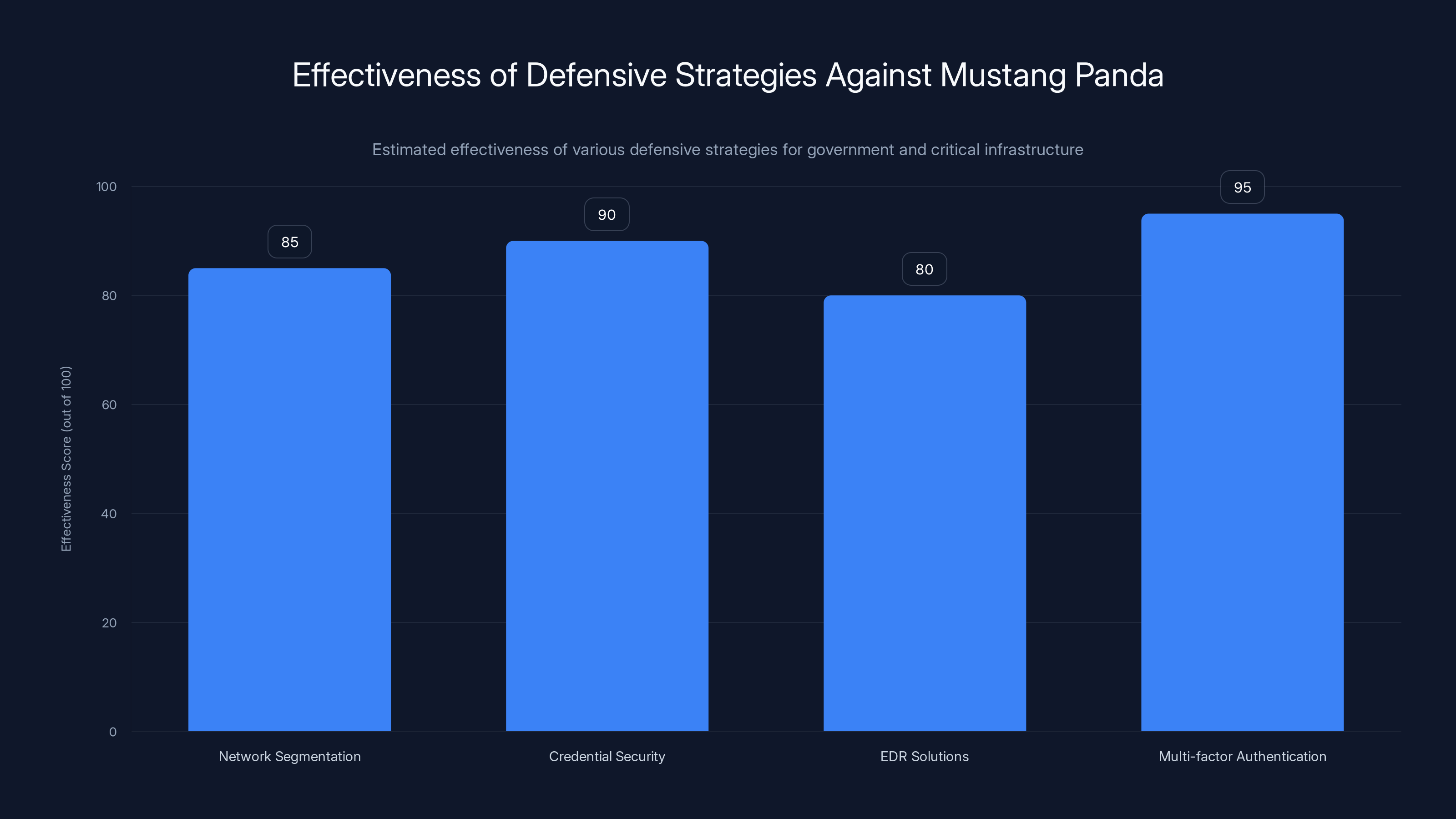
Multi-factor authentication and credential security are estimated to be the most effective strategies against Mustang Panda, scoring 95 and 90 respectively. Estimated data.
Integration with Broader Mustang Panda Operations
Understanding Cool Client requires context within Mustang Panda's broader operational approach. The group doesn't operate a single monolithic malware—they maintain a diverse toolkit where different tools serve different purposes within a coordinated offensive campaign.
Plug X serves as a primary backdoor in many Mustang Panda operations. It's a feature-rich backdoor providing general command execution, file operations, and system reconnaissance. When initial access occurs, Plug X often becomes the first backdoor deployed because it can accomplish most required operational objectives. Its presence on a system indicates an active intrusion with broad backdoor capability.
Luminous Moth focuses on browser-based credential theft and browser traffic interception. The malware specifically targets web browsers, stealing saved credentials and monitoring web traffic. Its presence in an intrusion suggests the group prioritizes attacking web-based systems and needs sophisticated browser automation or traffic monitoring.
Cool Client typically arrives in the deployment sequence after Plug X or Luminous Moth establish initial presence. Its role as a secondary backdoor provides redundancy—if defenders somehow remove Plug X, Cool Client continues providing access. But Cool Client's specific focus on clipboard monitoring, proxy credentials, and cloud service exfiltration suggests it fills niches that general-purpose backdoors don't address as effectively. It's the specialist where Plug X is the generalist.
This tool diversity reflects sophisticated operational planning. Rather than relying on a single backdoor doing everything, Mustang Panda invests in maintaining multiple specialized tools. Each tool gets optimized for specific capabilities, reducing the risk that removing one tool eliminates all access. The group has effectively implemented defense-in-depth from the attacker's perspective—multiple paths to success, multiple persistence mechanisms, and multiple tools for different operational phases.
The update cycle for Cool Client suggests the group actively develops and tests new capabilities, incorporating them into operations as they mature. The addition of cloud service exfiltration and credential harvesting in this variant probably resulted from specific operational requirements encountered during previous intrusions. When defenders detect attacks and analyze malware, the group learns lessons about what capabilities work and what might trigger detection, then incorporates those lessons into the next variant.

Supply Chain and Ecosystem Considerations
When Mustang Panda deploys Cool Client variants into specific regions and against specific organizations, they're targeting not just individual systems but integrated ecosystems of infrastructure, supply chains, and critical services. A government agency's compromised systems might provide access to contractors, partner organizations, and related entities.
The focus on credential harvesting and proxy credential sniffing suggests the group plans to leverage compromised networks for broader access. Proxy credentials often work across organizational perimeters—a single compromised proxy credential might enable access to partner networks, supplier networks, or external service integrations. By harvesting proxy credentials, the group gains not just access to the compromised network but potential stepping stones to connected networks.
Clipboard monitoring for cryptocurrency or wallet information reveals interest in both financial espionage and supply chain disruption. If government agencies use cryptocurrencies for international transactions, sanctions evasion, or payment to blacklisted suppliers, monitoring clipboard contents could reveal financial transaction information. If researchers and private sector partners use cryptocurrency wallets, harvesting wallet information enables direct asset theft.
The geographic focus on Asia-Pacific also suggests interest in regional supply chains and economic relationships. Myanmar, Malaysia, Mongolia, and Pakistan all participate in Asian trade networks, Belt and Road Initiative projects, and regional economic structures. Monitoring government knowledge of these relationships, trade terms, and economic dependencies directly supports strategic planning and negotiation in Belt and Road discussions.

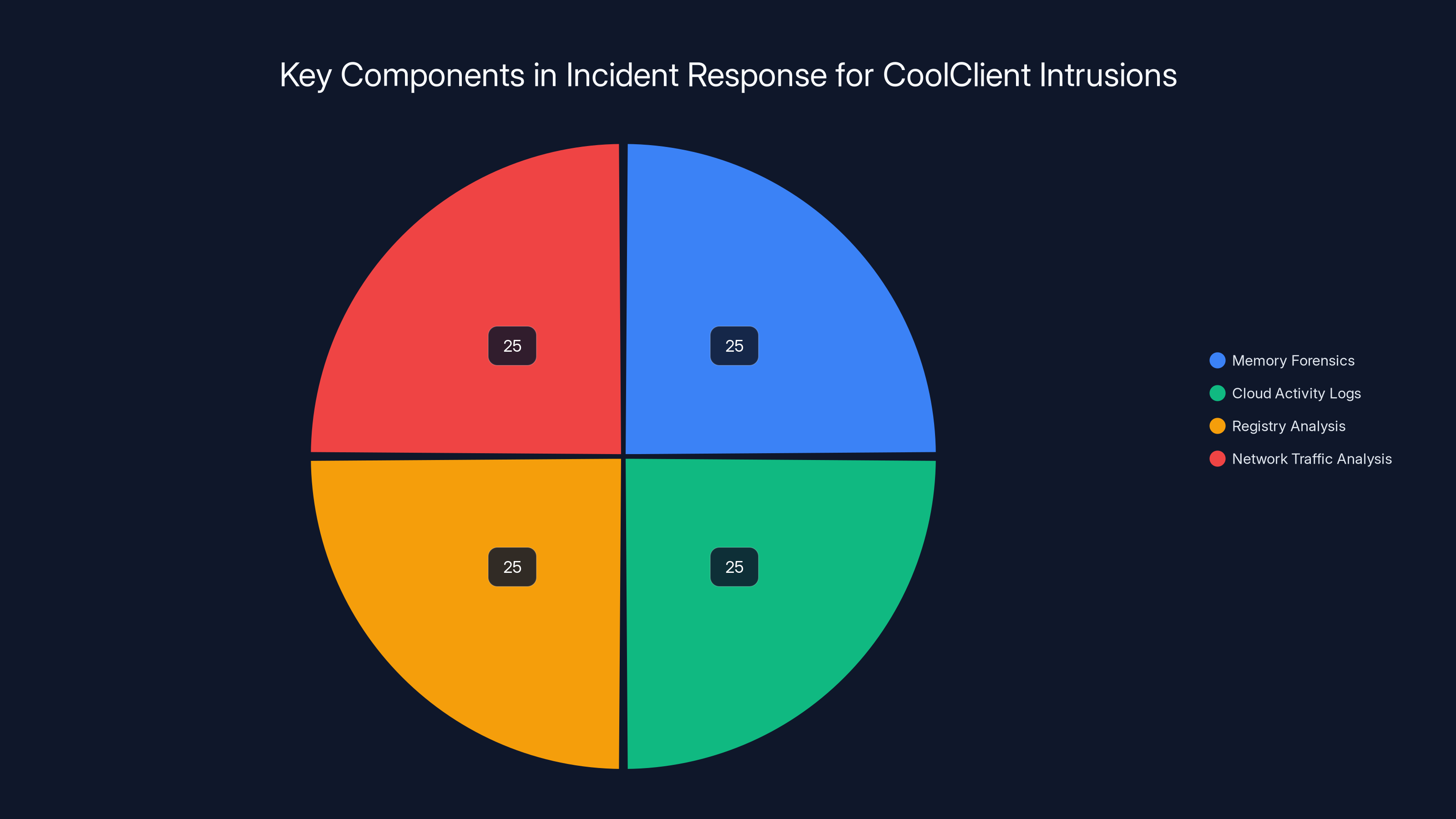
Incident response for CoolClient intrusions involves a balanced focus on memory forensics, cloud activity logs, registry analysis, and network traffic analysis. Estimated data based on typical forensic practices.
Timeline and Future Development Expectations
Analyzing the timeline of Cool Client's development reveals a progression from basic capability to increasingly sophisticated operations. The initial 2022 variant provided foundational backdoor functionality. Each subsequent variant added capabilities addressing specific operational needs encountered during real-world intrusions.
The trend toward credential harvesting and data exfiltration suggests the group's priorities are shifting from access and reconnaissance toward specific intelligence collection. Initial intrusions focus on establishing persistent access and understanding network structure. Once established, subsequent phases focus on finding and exfiltrating specific information. Cool Client's evolution aligns with this progression—new capabilities enable more efficient intelligence collection rather than broader system access.
Future development of Cool Client will likely continue along current trajectories. We should expect continued expansion of the plugin ecosystem, potentially including plugins for document exfiltration, email harvesting, or specialized attacks against government-specific applications. The group will probably continue optimizing for detection avoidance, potentially implementing memory-only execution more thoroughly or developing new persistence mechanisms.
The integration of infostealer capabilities into the plugin system suggests future variants might include plugins for specialized credential theft from government-specific applications, VPN clients, or authentication systems. As defensive measures improve against general credential theft, attackers adapt with more targeted collection focused on high-value authentication methods.
Cloud service integration will probably expand to include lesser-known or niche cloud services, making detection even more difficult. Rather than using obvious services like Dropbox or Google Drive, sophisticated operations might use less-monitored services or even compromise legitimate cloud accounts belonging to government employees, using those accounts as undetectable exfiltration channels.

Incident Response and Forensic Implications
Detecting an active Cool Client intrusion requires forensic investigation that goes beyond standard antivirus scanning. Incident responders facing suspected Mustang Panda intrusions should focus on identifying multiple access points, understanding the intrusion timeline, and discovering what intelligence was stolen.
Memory forensics become crucial when investigating Cool Client because the backdoor loads plugins and executes code in memory without necessarily creating detectable files. Analyzing memory dumps might reveal plugin code, configuration information, or even command history. Modern incident response must include memory acquisition and analysis as part of initial investigation.
Cloud activity logs provide crucial forensic evidence when cloud service exfiltration occurred. Investigators should examine One Drive, Dropbox, Google Drive, and other cloud service logs for suspicious authentication, file uploads from unusual locations, or uploads of sensitive file types. Cloud services maintain detailed access logs—even after attackers delete files from cloud accounts, logs reveal that the files existed and when they were uploaded.
Registry analysis focuses on persistence mechanisms and malware configuration. Cool Client likely stores plugin configuration, command-and-control targets, and communication parameters in registry keys. Comparing registry contents against baseline images of clean systems reveals suspicious modifications. Registry timeline analysis shows when modifications occurred, potentially correlating with intrusion timeline.
Network traffic analysis retrospectively reconstructs what communications occurred. If cloud service exfiltration happened, analyzing network traffic shows when connections to cloud services occurred, potentially identifying which files were exfiltrated. If the attacker used legitimate command-and-control channels, network analysis reconstructs the command and response patterns.
The incident response challenge is comprehensive—understanding not just how the backdoor works technically, but what intelligence it collected, how long it remained undetected, what lateral movement occurred, and what data requires notification to affected parties. A single Cool Client infection might cascade into discovery of a months-long intrusion affecting dozens of systems and resulting in exfiltration of classified information.

Broader Industry Response and Intelligence Sharing
The threat posed by Mustang Panda extends beyond individual organizations to the entire security industry. Intelligence sharing about Cool Client variants, deployment patterns, and targeting helps the broader community prepare and defend.
Security vendors use information about Mustang Panda operations to improve detection capabilities. When Kaspersky researchers published details about the updated Cool Client variant, they enabled other security companies to develop detection signatures, behavioral analysis rules, and hunting patterns. The information entered the broader threat intelligence ecosystem, informing defender preparations industry-wide.
Government agencies responsible for cybersecurity share threat intelligence through classified and unclassified channels. Organizations like CISA (Cybersecurity and Infrastructure Security Agency) in the United States issue alerts and advisories about active threats targeting government and critical infrastructure. Similar agencies in allied countries share intelligence through information sharing partnerships. This coordinated response amplifies the impact of early threat discovery.
Industrial sectors targeted by similar threats develop sector-specific defensive approaches. The energy sector, financial sector, government sector, and critical infrastructure operators all develop specialized detection and response capabilities addressing their specific threat landscape. Cool Client threats to government entities inform defensive strategies across that sector.
The challenge remains that intelligence sharing necessarily lags behind threat development. By the time researchers fully document a new variant and recommendations reach defenders, the attacker has often already moved to the next variant. The cycle continues indefinitely—attackers innovate, defenders react, attackers innovate further.
Organizational Risk Assessment
Not every organization faces the same risk from Mustang Panda. Understanding your organization's risk profile determines appropriate defensive investment. Government agencies, diplomatic missions, organizations supporting government operations, and critical infrastructure operators face higher risk. Private sector organizations in targeted geographies or with geopolitical significance also warrant elevated concern.
Risk assessment should consider several factors. First, does your organization possess intelligence of strategic interest to Chinese government policy makers? Government agencies clearly meet this criterion. Diplomatic missions, military organizations, and policy planning organizations also meet it. Second, does your organization operate in targeted geographies or maintain interests in those regions? Third, what's your organization's security maturity and incident response capability? Organizations with strong incident response can survive even sophisticated compromises better than organizations with weak incident response.
For organizations facing substantial Mustang Panda risk, the appropriate response includes comprehensive security architecture, continuous threat hunting for existing compromises, and robust incident response capability. This investment is significant—it requires EDR deployment, threat hunting capability, incident response training, and regular security audits. But for organizations with high strategic value, the investment produces essential risk reduction.
For organizations with lower assessed risk, the appropriate response includes basic security hygiene, awareness training about social engineering tactics common in Cool Client campaigns, and understanding what indicators suggest compromise. These organizations can't afford comprehensive Mustang Panda-specific defenses, but they can implement general security practices that defend against all advanced threats.
Training and Awareness Programs
Cool Client intrusions often begin with social engineering rather than exploit of unknown vulnerabilities. Mustang Panda researchers conduct detailed reconnaissance of target organizations, identifying employees with access to valuable information. They craft targeted phishing campaigns using information about the organization, its culture, and its employees. The initial compromise often comes through email—a carefully crafted message that appears to come from a trusted source, requesting information or asking the recipient to open a document.
Awareness programs addressing this threat should focus on phishing recognition, social engineering tactics, and reporting suspicious communications. Employees should understand that phishing against government organizations is sophisticated—messages might appear to come from colleagues, they might reference real projects or ongoing work, and they might request apparently legitimate information.
The clipboard harvesting capability suggests another training angle—educating users about risks of manual copy-paste operations with sensitive information. Users should understand that when they copy passwords from password managers and manually paste them into applications, they're exposing those passwords to any malware with clipboard access. Using authenticated mechanisms like Windows Hello or federated authentication whenever possible reduces reliance on copy-paste operations.
Proxy credential warnings deserve specific mention. Users often don't realize they're authenticating to organizational proxies. They might see authentication prompts and assume it's normal, entering credentials without realizing those credentials are now compromised if malware has access to that proxy authentication stream. Training should explain proxy authentication and its risks.

Conclusion and Ongoing Evolution
Mustang Panda's continued development and deployment of Cool Client variants reflects a sophisticated threat actor that continuously adapts to defender actions and incorporates new capabilities addressing operational requirements. The backdoor's evolution from basic functionality to credential harvesting and cloud service exfiltration reveals an organization investing in tooling quality and operational effectiveness.
For defenders, Mustang Panda intrusions represent a persistent threat requiring comprehensive, multi-layered responses. No single security control defeats this threat—effective defense requires network segmentation, credential security, endpoint detection capability, threat hunting, and robust incident response. Organizations must assume that detection of Mustang Panda activity represents late-stage discovery of potentially months-long intrusions and must conduct thorough investigation and remediation.
The threat will continue evolving. Cool Client will likely see new variants with additional capabilities. Mustang Panda will continue targeting Asia-Pacific government agencies and expanding operations into new regions. The intelligence collection mission driving these operations will continue regardless of individual incident response efforts. But for individual organizations that invest in comprehensive defense, detection, and response capability, the impact of Mustang Panda intrusions can be substantially mitigated. The key is understanding the threat, preparing for it, and maintaining vigilance for indicators of compromise.
Organizations in targeted sectors and regions should view Mustang Panda not as a hypothetical threat but as a probable adversary. Preparing as if compromise is likely, hunting for existing intrusions, and maintaining rapid incident response capability represents the realistic approach to facing this sophisticated and persistent threat. For government agencies managing national security, diplomatic missions protecting state interests, and critical infrastructure operators protecting essential services, this level of preparation isn't optional—it's necessary security practice.

FAQ
What is Mustang Panda and what are their operational objectives?
Mustang Panda is a Chinese state-sponsored advanced persistent threat (APT) group focused on cyber-espionage, data theft, and intelligence gathering against government entities primarily in Asia-Pacific regions. Their operational objectives align directly with Chinese national interests, focusing on understanding foreign government policy decisions, military capabilities, and strategic intentions. The group targets government agencies, diplomatic institutions, and critical infrastructure rather than private sector organizations, indicating their mission centers on intelligence collection supporting high-level strategic planning and national security analysis.
How does Cool Client establish persistence on compromised systems?
Cool Client uses multiple persistence mechanisms including UAC bypass techniques, DLL sideloading, service installation, and registry modifications. These techniques work together to ensure that even if defenders detect and remove one persistence mechanism, others remain functional. The backdoor can also execute code entirely in memory, avoiding file-based detection. Service-based persistence proves particularly effective because services run with SYSTEM privileges and survive system reboots, ensuring the backdoor remains active even after the system restarts or users log off.
What new capabilities were added to the Cool Client upgrade?
The upgraded Cool Client variant introduced clipboard monitoring to capture copied credentials and sensitive data, HTTP proxy credential sniffing to harvest authentication credentials, expanded plugin ecosystem for modular capability addition, remote shell plugins for interactive command execution, service management capabilities for managing Windows services, enhanced file management for efficient data exfiltration, and integration with cloud services for covert data theft. These new capabilities shift the backdoor toward more sophisticated credential harvesting and data exfiltration rather than just access and reconnaissance.
How does cloud service integration enable covert exfiltration?
Cloud service integration allows attackers to exfiltrate data through legitimate cloud providers like One Drive, Dropbox, or Google Drive, making the traffic appear indistinguishable from legitimate user cloud activity. This approach avoids the operational security risks of maintaining traditional command-and-control infrastructure, reduces detection risk because cloud service traffic is difficult to distinguish from legitimate usage, and leverages cloud providers' sophisticated infrastructure for reliable data transfer. Operators typically use dedicated cloud accounts for each operation, separating compromised network exfiltration from their other operations.
Which organizations and regions are most at risk from Mustang Panda?
Government agencies in Asia-Pacific regions face highest risk, particularly Myanmar, Mongolia, Malaysia, Pakistan, and adjacent countries with strategic significance to China. Russian government entities also face active targeting despite theoretical alignment. Organizations in targeted geographies with strategic importance, critical infrastructure operators, diplomatic missions, and government contractors supporting government operations all face elevated risk. The group specifically targets entities possessing intelligence of strategic interest to Chinese policy makers rather than mass-targeting or conducting opportunistic intrusions.
What's the most effective approach to detect Cool Client intrusions?
Detecting Cool Client requires multi-layered approaches including endpoint detection and response (EDR) solutions that monitor process behavior, registry modifications, and suspicious activities; memory forensics to identify in-memory execution and plugin loading; cloud activity monitoring to detect unusual authentication or suspicious file uploads; and proactive threat hunting for indicators specific to Mustang Panda operations. Standard antivirus proves insufficient because Cool Client was specifically designed to minimize obvious malicious indicators. Comprehensive incident response capability and assumption that detected intrusions represent late-stage discovery of months-long compromises enables thorough investigation and remediation.
How does the plugin architecture benefit attackers operationally?
The plugin architecture allows attackers to deploy specialized capabilities without recompiling the core backdoor, provides modularity where each plugin optimizes for specific functionality, enables rapid capability deployment to address new operational requirements or discovered defensive gaps, and reduces the core backdoor's footprint making detection more difficult. Plugins can be updated, removed, or replaced independently based on operational needs. This approach contrasts with monolithic backdoors attempting to provide all functionality in a single executable—specialized plugins work better for specific tasks than general-purpose code.
What role does clipboard monitoring play in credential theft?
Clipboard monitoring captures sensitive information that users copy-paste throughout their workday, including passwords from password managers, API keys, authentication tokens, SSH keys, and cryptocurrency wallet information. Users frequently copy credentials from password managers and manually paste them into applications that don't support auto-fill, temporarily exposing passwords in clipboard memory. The technique is effective because users typically don't realize clipboard contents are accessible to malware, and clipboard access leaves minimal forensic evidence compared to network-based credential capture. Harvesting clipboard contents provides direct access to authentication credentials and sensitive information without requiring complex interception techniques.
What initial indicators suggest a Cool Client compromise might exist?
Indicators of compromise include unexpected authentication failures from legitimate credentials suggesting compromise, unusual cloud service authentication from organizational networks, processes accessing clipboard functions unexpectedly, service creation with unusual timing or suspicious naming patterns, credential use patterns suggesting proxy credential compromise, unexplained registry modifications in persistence-related locations, or forensic evidence of plugin loading. However, sophisticated Cool Client deployments might demonstrate minimal suspicious indicators—absence of obvious signs doesn't indicate absence of compromise. Threat hunting specifically for Mustang Panda patterns and comprehensive incident response investigation remains necessary.

TL; DR
- Mustang Panda's Updated Threat: The Chinese APT group deployed an upgraded Cool Client backdoor with new credential-harvesting capabilities, clipboard monitoring, proxy credential sniffing, and expanded plugin ecosystem, making it significantly more dangerous than previous variants
- Target Geography: The upgraded variant targeted government entities in Myanmar, Mongolia, Malaysia, Pakistan, and Russia, aligning with Chinese strategic intelligence priorities across Asia-Pacific and against regional competitors
- Key New Capabilities: Clipboard monitoring harvests copied passwords and sensitive data, proxy credential sniffing captures authentication credentials, and cloud service integration enables covert exfiltration through legitimate services appearing as normal user activity
- Technical Sophistication: Cool Client employs multiple persistence mechanisms, in-memory execution, plugin-based architecture for modular functionality, and sophisticated evasion techniques specifically designed to avoid endpoint protection detection and triggering defender alerts
- Defense Requirements: Organizations facing this threat need multi-layered approaches including network segmentation, EDR deployment, credential hardening, threat hunting capability, and comprehensive incident response planning assuming months-long compromise durations
Key Takeaways
- Mustang Panda upgraded CoolClient backdoor with clipboard monitoring, proxy credential sniffing, and cloud service exfiltration capabilities making it significantly more dangerous
- New capabilities shift from basic access backdoor to sophisticated credential harvesting and data theft targeted at government entities
- The plugin-based architecture enables rapid capability deployment and modular functionality without recompiling core backdoor components
- Asia-Pacific government agencies in Myanmar, Mongolia, Malaysia, Pakistan, and Russia represent primary targeting focus aligned with Chinese strategic interests
- Detecting and defending against CoolClient requires multi-layered approaches including EDR, memory forensics, threat hunting, and comprehensive incident response assuming months-long compromise durations
Related Articles
- VoidLink: The Advanced Linux Malware Reshaping Cloud Security [2025]
- Kimsuky QR Code Phishing: How North Korean Hackers Bypass MFA [2025]
- Browser-Based Attacks Hit 95% of Enterprises [2025]
- OpenAI Scam Emails & Vishing Attacks: How to Protect Your Business [2025]
- North Korean Hackers Target VS Code: Lazarus Group's Contagious Interview [2025]
- Ingram Micro Ransomware Attack: 42,000 Affected, SafePay Claims Responsibility [2025]
![Mustang Panda's CoolClient Backdoor Evolution: What Security Teams Need to Know [2025]](https://tryrunable.com/blog/mustang-panda-s-coolclient-backdoor-evolution-what-security-/image-1-1769614741658.jpg)



