Ingram Micro Ransomware Attack: Complete Guide to the 42,000-Person Breach
Introduction
In July 2025, one of the world's largest IT distribution giants discovered something every company fears: unauthorized access to sensitive employee and job applicant data affecting tens of thousands of people. Ingram Micro, a company that serves over 160,000 customers globally, detected the breach on July 3, 2025, and immediately launched an investigation that would reveal the scope of the attack.
The numbers are staggering. Exactly 42,521 individuals had their personal information stolen during this ransomware attack. We're talking about real data here: Social Security numbers, driver's license numbers, passport information, employment records, dates of birth, and contact details. For context, that's roughly the population of a small city compromised in a matter of hours.
What makes this attack particularly significant isn't just the victim count. It's the sophistication of the group responsible. Safe Pay, the ransomware collective claiming responsibility, alleges they stole 3.5 terabytes of sensitive documents. To put that in perspective, 3.5TB could hold approximately 700,000 feature-length movies or the equivalent of roughly 1.4 million high-resolution photos. The ransom demand, though not publicly disclosed, likely reached the millions given Ingram Micro's market position and the value of the stolen data.
This incident serves as a critical wake-up call for businesses of all sizes. It demonstrates that even established IT infrastructure companies with dedicated security teams can fall victim to sophisticated ransomware operations. The attack exploited vulnerabilities between July 2 and 3, 2025, giving the threat actors a narrow but deadly window to extract massive amounts of data.
If you're affected by this breach, you need to take immediate action. If you're a business concerned about your own cybersecurity posture, this incident offers valuable lessons about detection, response, and prevention. Let's break down everything you need to know.
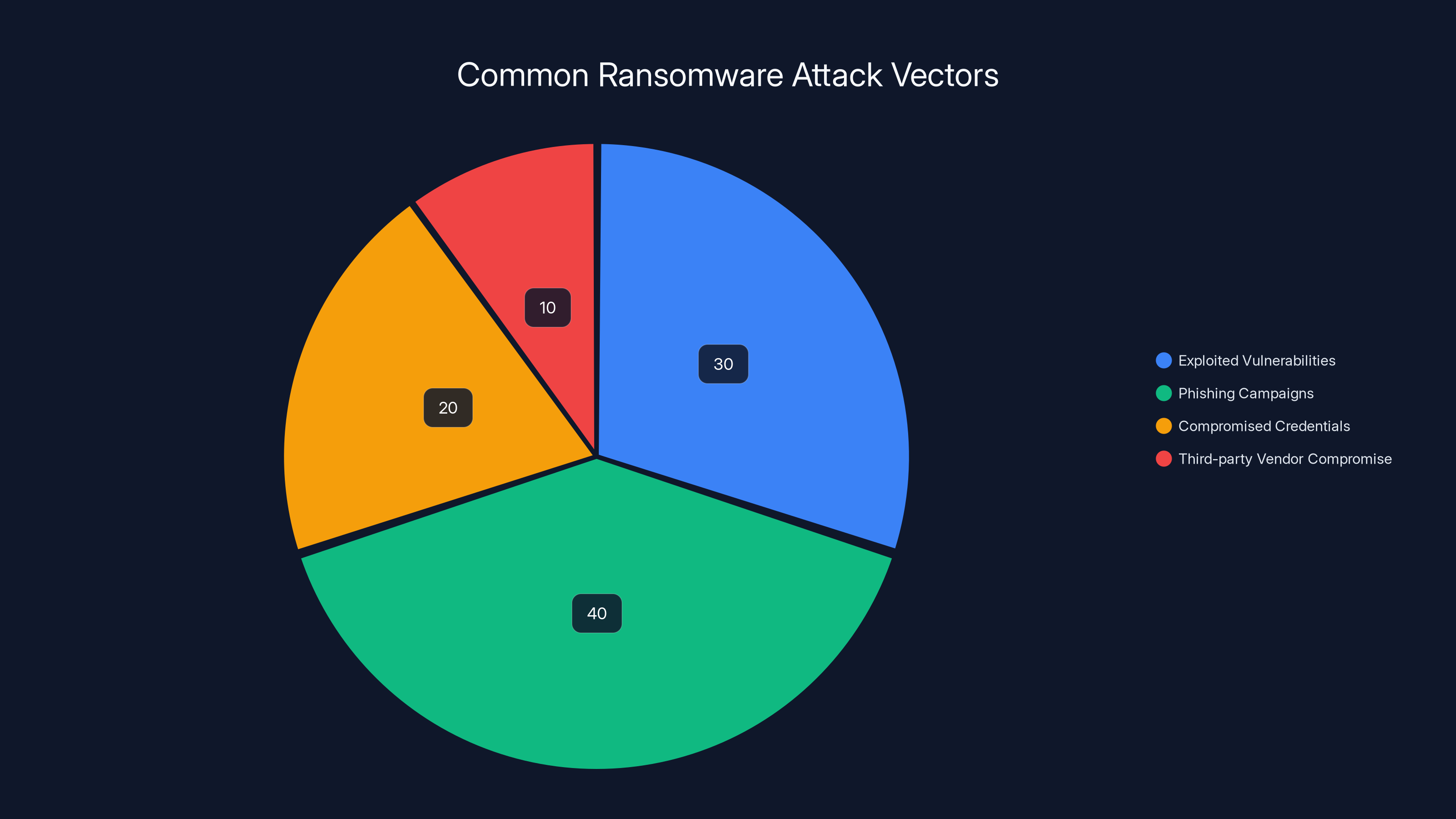
Phishing campaigns are estimated to be the most common initial access method for ransomware attacks, followed by exploited vulnerabilities. (Estimated data)
TL; DR
- Attack Scale: 42,521 individuals affected by Ingram Micro ransomware breach in July 2025
- Data Stolen: Social Security numbers, driver's licenses, passport information, employment records, dates of birth, and contact information
- Group Responsible: Safe Pay ransomware collective claims responsibility for the attack
- Data Volume: 3.5TB of sensitive documents allegedly stolen from company file repositories
- Timeline: Unauthorized access occurred between July 2-3, 2025
- Company Response: Free credit monitoring for 2 years offered to affected individuals
- Bottom Line: This represents one of the largest ransomware attacks on IT infrastructure companies, highlighting critical vulnerabilities in even well-resourced organizations
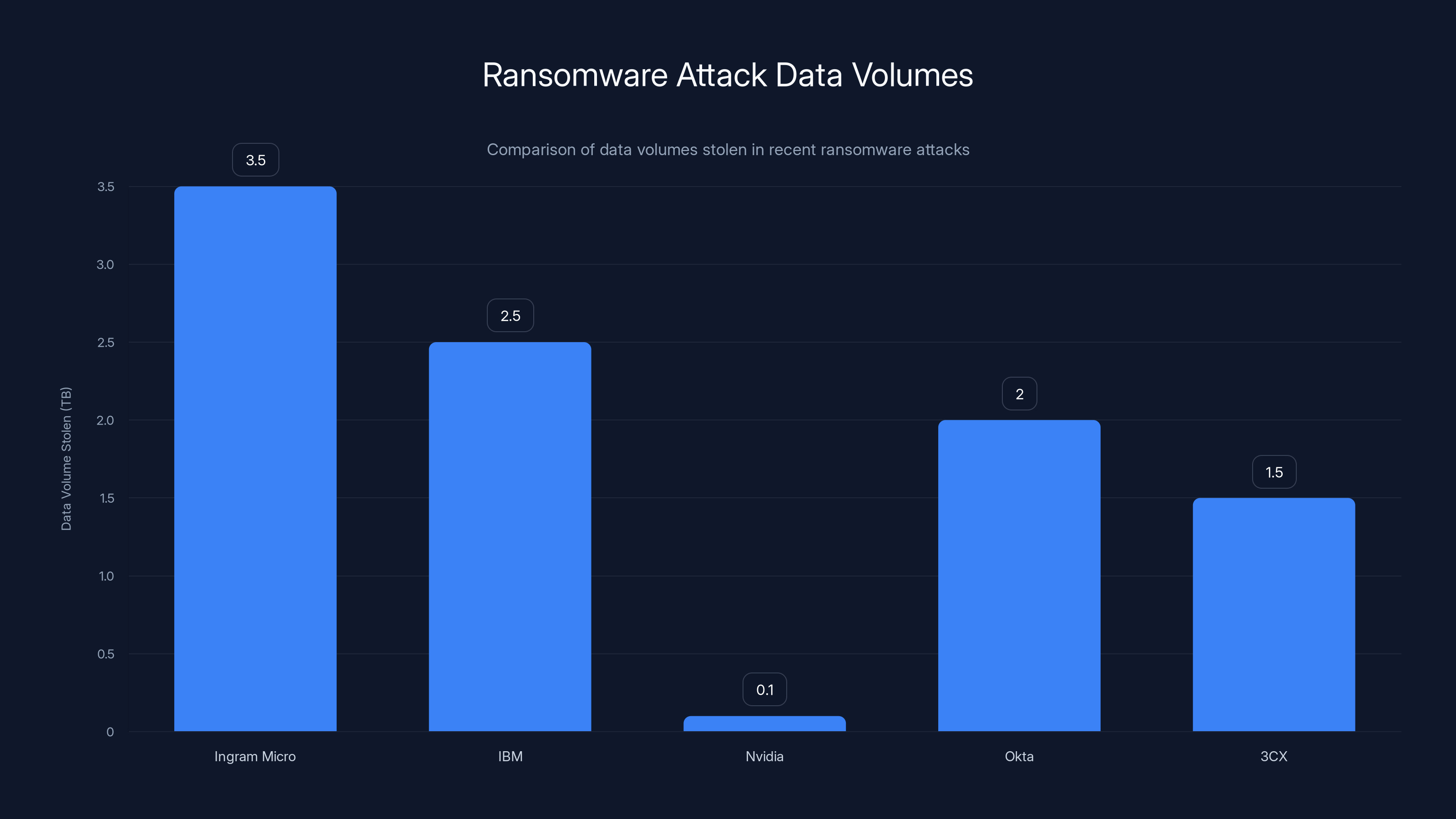
Ingram Micro's data breach involved 3.5TB of data, which is significant but not the largest compared to other recent attacks. Estimated data used for comparison.
The Attack Timeline: How Safe Pay Infiltrated Ingram Micro
The timeline of the Ingram Micro attack reveals a dangerous reality about modern cybersecurity: sophisticated threat actors can move through systems with alarming speed and precision.
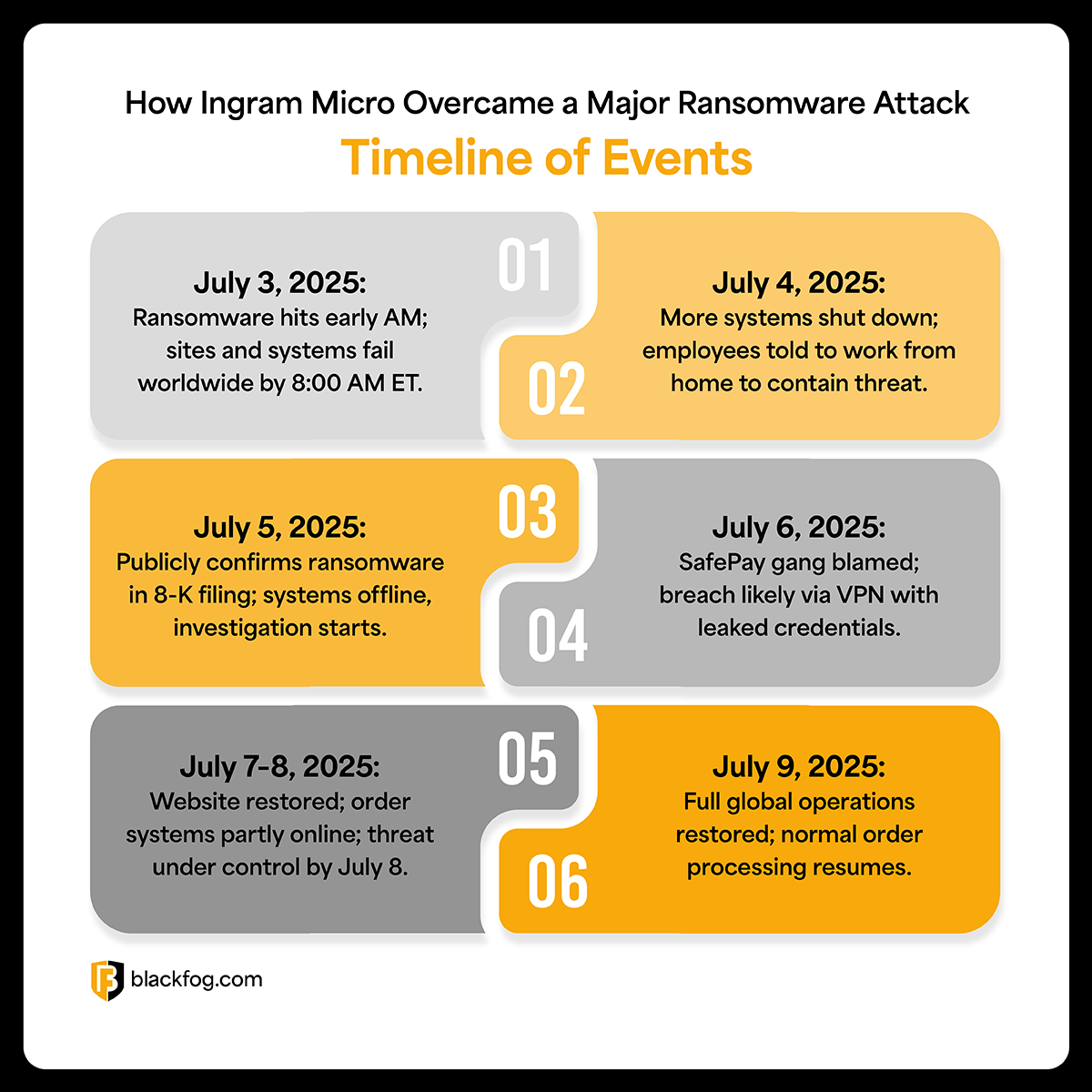
July 2-3, 2025: The attack window. This 48-hour period proved catastrophic for Ingram Micro. During this time, an unauthorized third party gained access to internal file repositories and successfully exfiltrated massive amounts of data. The speed suggests the attackers had prior reconnaissance or access pathways already established.
July 3, 2025: Detection day. This is actually positive news in the timeline. Ingram Micro's security team detected the cybersecurity incident and immediately launched a formal investigation. The relatively quick detection (on the same day as the breach completion) suggests they had monitoring systems in place. However, the damage was already done. The attackers had already downloaded and removed data from the system.
Following Investigation Period: Ingram Micro engaged third-party security firms to assist with forensic analysis. This is standard procedure and helps provide independent verification of what happened. They also notified law enforcement and relevant regulatory authorities.
Weeks After Attack: Safe Pay emerged from the shadows. The ransomware group posted on its dark web leak portal, claiming responsibility and alleging the theft of 3.5TB of sensitive documents. This is the typical pattern for modern ransomware operations: steal data, encrypt systems, wait for payment offers, then start threatening to sell or leak data if demands aren't met.
The timing of Safe Pay's announcement weeks after the attack is telling. It suggests the group needed time to verify the data they stole, catalog it, and assess its value before making their claims public. This patience is often more effective than immediate disclosure, as it puts maximum pressure on victims to negotiate without public scrutiny.
What we don't know is critical too. Ingram Micro has never publicly disclosed the ransom demand amount. Given that the company serves 160,000 customers and operates in over 190 countries, a ransom demand in the $10-50 million range would be consistent with attacks of this scale. Whether Ingram Micro paid or refused remains undisclosed, though most large companies negotiate to some extent.
Understanding Safe Pay: Who Are They?
Safe Pay isn't a household name, but it's become a significant player in the ransomware-as-a-service ecosystem. The group operates what's essentially a criminal startup, complete with standardized operations, multiple victim streams, and professional infrastructure.
Operational Model: Safe Pay functions as a ransomware-as-a-service (RaaS) outfit. This means they've developed malicious code and attack infrastructure that they lease or partner with other cybercriminal groups to use. It's the democratization of cybercrime. You don't need to be a brilliant programmer to launch a ransomware attack anymore—you just need access to Safe Pay's tools and a distribution mechanism.
Attack Pattern: Their modus operandi follows the standard playbook for modern ransomware gangs. First, they establish unauthorized access to a target network. This might involve exploiting an unpatched vulnerability, purchasing stolen credentials on the dark web, or compromising a third-party vendor. Second, they move laterally through the network, avoiding detection while gathering intelligence about valuable data and backup systems. Third, they extract high-value data (for extortion purposes). Finally, they encrypt critical systems and issue ransom demands.
The Dual Extortion Model: What makes Safe Pay particularly effective is the dual-extortion approach. They don't just encrypt your data and demand payment for decryption keys. They also threaten to publicly disclose or sell sensitive information if you don't pay. This creates multiple pressure points: the operational disruption of encryption plus the regulatory and reputational risk of data disclosure.
For the Ingram Micro attack specifically, we know Safe Pay claimed 3.5TB of stolen data. In the underground criminal markets, employee records with personally identifiable information (PII) combined with employment data typically sell for

The timeline illustrates the progression of the SafePay attack on Ingram Micro, from initial infiltration to public announcement. Estimated data based on typical attack patterns.
The Actual Data Stolen: What Victims Lost
The specifics of what Safe Pay stole matter tremendously for affected individuals. This wasn't just random files—it was personal information designed for maximum exploitation.
Government-Issued Identification Numbers: The theft of Social Security numbers (SSNs), driver's license numbers, and passport information is particularly damaging. These are the crown jewels of identity theft. With a person's SSN, date of birth, and name, criminals can:
- Open fraudulent credit accounts
- File fake tax returns
- Apply for loans or mortgages in the victim's name
- Access medical services
- Commit employment fraud
- Sell the data to other criminals
SSN theft is so consequential that it often leads to identity theft cases emerging years after the initial breach. Victims discover unauthorized credit accounts or tax complications that stem directly from this breach.
Employment and Job Applicant Records: The inclusion of employment-related evaluations and job applicant information reveals something interesting about what the attackers were accessing. These records suggest they had penetrated not just one file repository but multiple systems spanning HR departments, recruiting systems, and performance management databases.
Employment records are valuable because they often contain:
- Full names and addresses
- Email addresses (sometimes personal, sometimes corporate)
- Phone numbers (landline and mobile)
- Start dates and employment history
- Salary information
- Manager names and relationships
- Performance reviews and evaluations
- Reasons for termination (for former employees)
Contact Information: Names, addresses, phone numbers, and email addresses form the foundation for social engineering attacks. Criminals can use this information to impersonate victims, contact their banks pretending to be account holders, or send targeted phishing emails.
Date of Birth: Combined with names and addresses, dates of birth enable account takeovers on many online services. Many websites use date of birth as a security verification question.
The Variation Factor: Ingram Micro explicitly stated that "data stolen varies from person to person." This is important. Not everyone had all their personal information compromised. Some victims may have only had names and email addresses stolen, while others lost complete identity profiles including SSNs, driver's licenses, and passport information. The variation likely depends on which specific systems were accessed and the age of employment records.

Impact on the 42,521 Affected Individuals
Being one of 42,521 victims of a ransomware attack means living with uncertainty and elevated risk, potentially for years.
Immediate Risks: The most immediate danger is identity theft. Criminals who now possess SSNs and dates of birth can begin attempting fraudulent credit applications, loan applications, and account openings. The first 30-60 days after a breach notification are typically the most dangerous, as criminals move quickly to exploit fresh data before victims have placed fraud alerts.
Credit Monitoring Provisions: Ingram Micro offered free credit monitoring and identity theft protection services for two years. This is actually on the generous side compared to some companies, though security experts argue it's inadequate. Why? Because the threat window for SSN misuse extends far beyond two years. Criminals can use stolen SSNs years after a breach, particularly for tax refund fraud or medical identity theft.
The credit monitoring typically includes:
- Daily credit report monitoring from all three bureaus (Equifax, Experian, Trans Union)
- Fraud alerts and notifications
- Credit freeze services
- Social Security number monitoring on the dark web
- Identity theft restoration services if fraud occurs
- Legal consultation for identity theft cases
Long-Term Consequences: Even after the two-year monitoring period ends, victims should remain vigilant. Some specific risks:
- Tax Fraud: Criminals file fake tax returns using stolen SSNs and dates of birth, claiming refunds. The IRS eventually contacts the victim, leading to complicated resolution processes.
- Medical Identity Theft: Someone uses the victim's identity to access medical services or prescription medications, creating false medical records that can affect future healthcare.
- Loan Fraud: Years later, victims discover loans or mortgages opened in their names during the initial breach period.
- Employment Fraud: Criminals may use the stolen information to obtain employment, affecting the victim's background check records.
Regulatory Notification Requirements: Ingram Micro's notification to the Maine Attorney General's Office represents compliance with state breach notification laws. Most U.S. states now require companies to notify residents of any security breach involving personal information. The Maine Attorney General likely received a detailed report about the breach, affected individuals, and remediation steps.

This timeline illustrates the recommended frequency of credit report checks, tax fraud prevention, and ongoing protective measures over a seven-year period following a data breach. Estimated data.
Ingram Micro's Response: Investigation and Remediation
How a company responds to a ransomware attack matters enormously for both immediate damage control and long-term reputation recovery.
Third-Party Security Firm Engagement: Ingram Micro brought in external security experts to conduct forensic analysis. This serves multiple purposes:
- Provides independent verification of what happened
- Demonstrates to regulators and affected individuals that they're taking the breach seriously
- Generates forensic evidence for law enforcement
- Creates documentation for potential lawsuits
- Helps identify the root cause and prevent similar attacks
Forensic analysis typically involves examining:
- Attack vectors and initial compromise methods
- Lateral movement patterns through the network
- Data exfiltration methods and volume
- Dwell time (how long attackers were in the system)
- All systems potentially compromised
- Timeline reconstruction
Law Enforcement Notification: Ingram Micro notified law enforcement, which likely included the FBI's Cyber Division and potentially the Cybersecurity and Infrastructure Security Agency (CISA). This is required for incidents of this scale and helps with:
- Investigation of the ransomware group
- Attribution and intelligence gathering
- Warnings to other potential victims
- International cooperation if the group operates across borders
Affected Individual Notification: The company notified all 42,521 affected individuals through data breach notification letters. These letters must include:
- Description of what happened
- Date range of potential compromise
- Types of information compromised
- What Ingram Micro is doing about it
- Contact information for more details
- Credit monitoring services offered
- Recommendations for protective steps
Credit Monitoring and Identity Theft Protection: The two-year complimentary service package is the financial remedy offered. While appreciated by victims, this measure is often criticized as insufficient by privacy advocates who argue the threat window extends far longer.

Ingram Micro's Business Context: Why This Matters
To understand the significance of this breach, you need to understand what Ingram Micro actually does and who relies on them.
Global Distribution Giant: Ingram Micro serves as a critical middle layer in the IT supply chain. The company has over 160,000 customers worldwide across roughly 190 countries. They distribute hardware, software, cloud services, and IT solutions from major manufacturers to resellers, system integrators, and other channel partners.
Think of them as the Costco of IT products. Major tech companies like Cisco, Dell, HP, Microsoft, and others rely on Ingram Micro to distribute their products at scale. When Ingram Micro experiences disruption, it cascades through the IT industry.
Customer Base: The company's clients include:
- Computer retailers and resellers
- System integrators and consultants
- Managed service providers (MSPs)
- Value-added resellers (VARs)
- Cloud service providers
- Telecommunications companies
- Government agencies
Employment Scale: With over 160,000 customers and a sprawling global operation, Ingram Micro employs thousands of people across sales, engineering, supply chain, and support roles. The 42,521 affected individuals represent current employees, former employees, and job applicants.
Why This Breach Matters to Customers: While Ingram Micro's breach doesn't directly compromise data about its reseller customers or end-user organizations, it does raise serious questions about the security practices of a company that handles critical IT infrastructure and distribution. If Ingram Micro's systems can be breached this severely, what does that say about their commitment to security?
Industry Implications: This breach occurred in the IT distribution channel, a sector that's increasingly targeted by ransomware groups. Why? Because distributors have:
- Access to huge volumes of product and customer data
- Extensive network connectivity to downstream customers
- Multiple third-party integrations creating attack surface
- High-value data for extortion
The breach should serve as a warning to other distributors and resellers about the critical need for network segmentation, access controls, and threat detection.

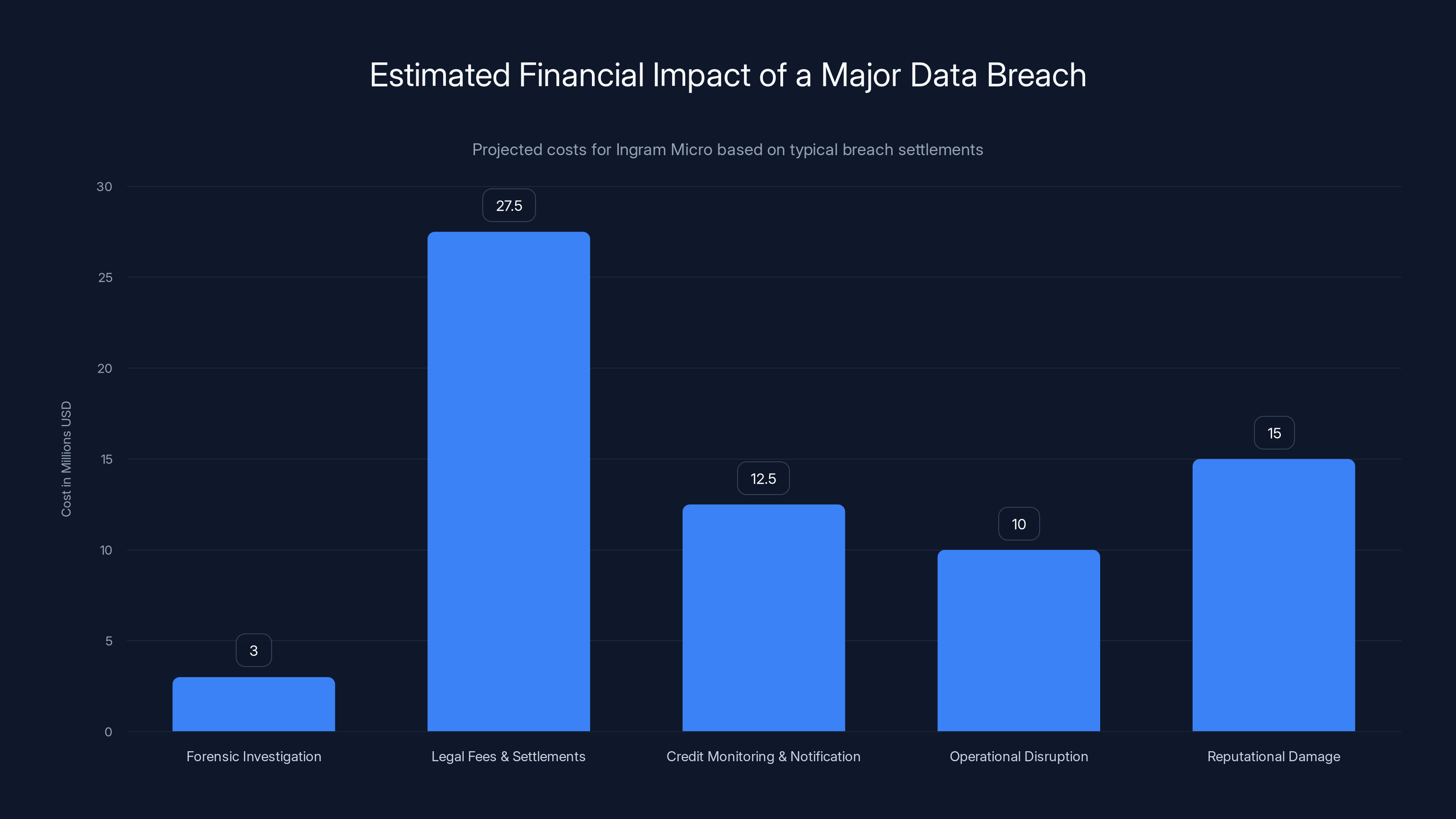
Estimated data suggests that legal fees and settlements could be the largest cost, followed by reputational damage and operational disruption. Total impact could exceed $100M.
How to Check If You're Affected
If you worked for Ingram Micro or applied for a job there between roughly 2020-2025, you might be affected. Here's how to determine your status.
Official Notification Method: Ingram Micro notified affected individuals through official notification letters sent to their last known mailing addresses. These letters included:
- A clear statement that an individual is affected
- Specific information about what data was compromised
- Instructions on accessing free credit monitoring services
- Contact information for the credit monitoring provider
- Recommendations for protective action
Checking Status: If you believe you're affected but haven't received a letter:
- Check your postal mail, including junk mail folders
- Contact Ingram Micro directly through official channels
- Look for official company notifications on their investor relations or corporate website
- Contact your HR department if you were employed by Ingram Micro
Important: Be cautious about phishing scams. Criminals often send fraudulent "breach notification" letters to trick people into clicking malicious links or providing additional personal information. Verify any letters by:
- Contacting Ingram Micro directly using numbers from their official website
- Never clicking links in unsolicited emails claiming to be from Ingram Micro
- Confirming any credit monitoring service activation through official channels
Documentation to Preserve: If you have legitimate breach notification from Ingram Micro, keep it in a safe place. You may need it for:
- Future identity theft claims
- Credit disputes
- Tax fraud recovery
- Legal actions against Ingram Micro

Immediate Actions for Affected Individuals
If you're one of the 42,521 affected by this breach, here's what you should do immediately.
Step 1: Activate Credit Monitoring: Sign up for the free credit monitoring service Ingram Micro provided. The notification letter should include instructions and a registration code. This service monitors all three credit bureaus and provides early alerts if someone tries to open accounts in your name.
The monitoring services typically track:
- New credit accounts opened in your name
- Hard inquiries on your credit reports
- Suspicious activity on existing accounts
- Changes to credit profile information
Step 2: Place Fraud Alerts: Contact the three major credit reporting bureaus (Equifax, Experian, Trans Union) and place fraud alerts on your credit files. This is free and tells lenders to take extra steps to verify your identity before opening new accounts.
You can place an initial fraud alert valid for one year by contacting any one of the three bureaus:
- Equifax: equifax.com
- Experian: experian.com
- Trans Union: transunion.com
Step 3: Consider a Credit Freeze: A credit freeze is more powerful than a fraud alert. It completely prevents new credit from being opened in your name without your explicit permission. The freeze requires creditors to contact you directly for verification.
Credit freezes are free and effective but require you to temporarily unfreeze your credit whenever you want to apply for new credit, loans, or even certain services.
Step 4: Monitor Financial Accounts: Review your bank accounts, credit cards, and loan accounts for unauthorized transactions. Set up alerts for:
- Large transactions
- New account openings
- Any activity at all (high sensitivity)
- Login attempts from new locations
Step 5: Check Tax Records: Every April-May, file your tax return early before criminals can file fraudulent returns using your SSN. Keep records of all tax returns filed in your name. The IRS has a tool to check if someone filed a return using your SSN: IRS.gov.
Step 6: Review Medical Records: Contact your healthcare providers and request copies of your medical records. Look for services or treatments you didn't receive. Medical identity theft can create false diagnoses and medication records that affect your future healthcare.
Step 7: Document Everything: Keep detailed records of:
- All fraud attempts discovered
- Dates and times of fraudulent activities
- Amounts involved
- Names of companies defrauded
- Police report numbers (file a report if fraud occurs)
- Correspondence with financial institutions
This documentation will be essential if you need to dispute fraudulent accounts or pursue legal action.

SafePay's attack model is evenly distributed across unauthorized access, lateral movement, data extraction, and encryption, highlighting their comprehensive approach. (Estimated data)
Long-Term Protection Strategies for Breach Victims
The two-year credit monitoring period sounds good until you realize the threat window extends much longer. Here's how to maintain long-term vigilance.
Year 1-2: Active Monitoring Phase: During the credit monitoring period, check your credit reports quarterly even though the monitoring service is doing so. Become familiar with what's normal for your financial profile. Review all credit inquiries and accounts listed.
Year 3-7: Continued Vigilance: After the formal monitoring ends, continue checking your credit reports annually. You're entitled to one free credit report from each bureau annually through annualcreditreport.com (the official site, not the commercial imposter sites).
Stagger your requests:
- January: Pull Equifax report
- May: Pull Experian report
- September: Pull Trans Union report
This gives you complete coverage of all three bureaus annually after the monitoring service ends.
Tax Fraud Prevention: Every year before filing taxes, verify with the IRS that no fraudulent return has been filed using your SSN. The IRS allows you to place a return preparer PIN, which prevents anyone else from filing on your behalf.
Ongoing Protective Measures: Consider:
- Maintaining credit freeze permanently (if not needed for frequent credit applications)
- Using unique passwords for financial accounts
- Enabling multi-factor authentication on all important accounts
- Monitoring the dark web for your information (services like Have I Been Pwned can alert you)
- Using credit monitoring services permanently (inexpensive services cost $10-20/month)

Ransomware Attack Trends: Why Ingram Micro Isn't Alone
The Ingram Micro breach represents a troubling trend in cybercrime: the targeting of major IT infrastructure companies.
The Target Shift: In the past five years, ransomware groups have increasingly targeted:
- Software distributors and resellers
- IT managed service providers (MSPs)
- System integrators
- Cloud service providers
- Supply chain companies
Why? Because these organizations represent leverage points. If you compromise a distributor, you gain:
- Access to sensitive information about their customer base
- Potential lateral movement to downstream customers through supply chain integrations
- Information about products and security systems their customers use
- Employee credentials that work across partner organizations
The Data Volume: The 3.5TB stolen by Safe Pay is substantial but not record-breaking. Recent ransomware attacks have stolen:
- IBM: Compromised credentials and source code (multiple terabytes)
- Nvidia: Source code and credentials (100GB+)
- Okta: Customer support data and credentials (multiple terabytes)
- 3CX: Supply chain compromise affecting thousands of customers
The Ransom Scaling: As stolen data volumes increase, ransomware demands have scaled accordingly. Modern attacks typically demand:
- Small organizations: 500,000
- Mid-size companies: 5,000,000
- Large enterprises: 50,000,000+
- Critical infrastructure: $50,000,000+
Ingram Micro's likely ransom demand (estimated at millions) reflects their size and the value of their data.
Regulatory Response: Governments worldwide are responding to ransomware threats:
- U.S.: Executive orders requiring incident reporting, sanctions against groups, CISA threat advisories
- EU: NIS2 Directive requiring incident reporting and security measures
- UK: Requirements under UK GDPR and NIS regulations
- Canada: Proposed legislation requiring rapid incident notification
These regulatory pressures create disincentives for paying ransoms and incentives for better security.
Preventing Ransomware: Lessons from Ingram Micro
While we may never know the exact vulnerability that allowed Safe Pay to breach Ingram Micro's systems, ransomware attacks follow predictable patterns. Here are the critical defense measures.
Network Segmentation: The most critical lesson from major ransomware attacks is that network segmentation saves companies. If Ingram Micro had properly segmented its network, attackers gaining access to one system wouldn't automatically have access to all file repositories.
Effective segmentation requires:
- Isolating critical file repositories from general network
- Requiring separate authentication for different network segments
- Implementing microsegmentation (ultra-granular network divisions)
- Monitoring traffic between segments
- Blocking unnecessary inter-segment communication
Access Control: The principle of least privilege means every user and system should have access to only what they absolutely need.
This prevents:
- A compromised junior employee account from accessing executive records
- A contractor account from accessing sensitive financial data
- Service accounts from accessing unrelated systems
- Shared credentials that obscure who accessed what
Backup Strategy: The most effective ransomware defense is a robust offline backup strategy. If you have multiple offline backups not connected to your main network, ransomware becomes merely a temporary disruption rather than a disaster.
Effective backup strategies include:
- Daily automated backups
- Multiple backup copies at different time intervals
- Offline backups not accessible from the main network
- Regular restoration testing (not just backing up, but verifying backups work)
- Separate credentials for backup systems
Threat Detection: Early detection can stop ransomware before data exfiltration occurs.
Detection methods include:
- Network monitoring for unusual data transfers (especially large volumes to unknown destinations)
- Endpoint detection and response (EDR) software on all systems
- Unusual account behavior (accounts accessing files they never touch normally)
- Lateral movement detection (unusual network connections between systems)
- Impossible travel alerts (logins from impossible geographic locations)
Incident Response Planning: Having a plan before you're attacked saves critical time.
Effective plans include:
- Predetermined chain of command
- Contact information for forensic firms
- Law enforcement contact procedures
- Communication plan for notifications
- Containment procedures (how to isolate affected systems)
- Backup restoration procedures
- Public relations strategy
Employee Training: Most ransomware infections begin with social engineering or phishing.
Effective training covers:
- Recognizing phishing attempts
- Never using personal devices for work without controls
- Reporting suspicious activity
- Understanding data sensitivity levels
- Proper credential handling
- When to ask questions before acting

The Bigger Picture: Supply Chain Risk and Trust
The Ingram Micro breach raises profound questions about trust in the IT supply chain.
Transitive Risk: When a distributor is compromised, downstream customers face transitive risk. Competitors might learn about their purchasing patterns. Customer information might be exposed. Attackers might use the distributor's credentials to target customer organizations.
Vendor Security Due Diligence: Organizations that use Ingram Micro's services should be asking hard questions:
- What security controls does Ingram Micro actually have?
- How quickly did they detect this attack?
- What caused the breach?
- How many other breaches haven't been disclosed?
- What are they doing to prevent future attacks?
Contractual Implications: Customers harmed by this breach might have contractual claims against Ingram Micro for:
- Negligent security practices
- Failure to maintain adequate safeguards
- Violation of service level agreements
- Damages from downstream attacks
Insurance and Liability: Ingram Micro likely carries cyber liability insurance, but the coverage might be insufficient for a breach of this scale. Lawsuits filed by affected individuals could lead to:
- Insurance settlements
- Direct damages to Ingram Micro
- Regulatory fines
- Reputational harm affecting business relationships
Standards and Compliance: Organizations like Ingram Micro typically must maintain compliance with:
- SOC 2 Type II (service organization controls)
- ISO 27001 (information security management)
- Industry-specific requirements (payment card industry, healthcare, etc.)
Breach of this scale raises questions about whether Ingram Micro was actually compliant with these standards or whether the standards themselves need evolution.

Dark Web Implications: What Happens to Stolen Data
Understanding what happens to the 3.5TB of data Safe Pay stole is critical for understanding long-term risks.
The Criminal Marketplace: On dark web forums and marketplaces, stolen data from breaches follows predictable patterns:
- Initial listing on the ransomware group's leak site for extortion purposes
- Negotiation with the victim company
- If not sold to the company, eventual listing on dark web marketplaces
- Bulk sales to criminal syndicates
- Retail sales to individual criminals
- Resale as "exclusive data" multiple times
Data Degradation Over Time: While identity theft risks are highest immediately after a breach, certain types of stolen data remain profitable for years:
- SSNs and dates of birth: Profitable for tax fraud years later
- Employment records: Useful for targeted social engineering and phishing
- Contact information: Remains useful for scams indefinitely
- Credentials: Useful as long as the systems they access remain unchanged
Monitoring and Detection: Victims can monitor dark web forums for their data through:
- Dark web monitoring services (many credit monitoring packages include this)
- Have I Been Pwned and similar services (limited to known breaches)
- Setting up alerts for your personal information
- Monitoring financial fraud forums for your SSN
Law Enforcement Action: Occasionally law enforcement takes action against ransomware groups or their dark web infrastructure:
- Shutting down leak sites
- Disrupting access to cryptocurrency payment mechanisms
- Arresting individual group members
- Imposing sanctions
However, these actions often come months or years after a breach, providing limited immediate help to victims.

Recovery and Lawsuits: What's Next
The legal aftermath of major breaches can extend years.
Regulatory Investigations: Multiple regulatory bodies likely investigate the breach:
- State attorneys general (Maine, where notification was filed, and potentially others)
- Federal agencies (FBI Cyber Division, CISA)
- International authorities (if the attack involved foreign nationals or governments)
Victim Lawsuits: Class action lawsuits often follow breaches of this magnitude. These lawsuits typically allege:
- Negligent information security practices
- Failure to detect breaches promptly
- Inadequate notice to affected individuals
- Emotional distress
- Costs of credit monitoring and fraud protection
- Loss of data value
Settlement Patterns: Settlements for breaches similar in scale to Ingram Micro typically involve:
- Extended credit monitoring (3-7 years instead of 2)
- Cash settlements to affected individuals (500 per person)
- Implementation of security improvements
- Annual security audits
- Regular reports to attorneys general
Costs to Ingram Micro: The total financial impact typically includes:
- Forensic investigation costs (5M)
- Legal fees and settlements (50M)
- Credit monitoring and notification costs (20M)
- Operational disruption during incident response
- Reputational damage affecting business
- Potential regulatory fines
- Total estimated impact: 100M+

Industry Comparisons: How Ingram Micro Stacks Up
To contextualize this breach, it's worth comparing it to other major ransomware incidents.
Recent Major Breaches:
- Optus (2022): 9.8 million Australians affected, $750K settlement
- Last Pass (2022): 25 million users' master passwords compromised
- MOVEit (2023): Supply chain attack affecting 2,000+ organizations
- Change Healthcare (2024): 100 million Americans affected, $49.5M settlement announced
- Ingram Micro (2025): 42,521 affected from direct employment data
Comparison Analysis:
| Breach | Year | Victims | Data Type | Ransom Estimated |
|---|---|---|---|---|
| Change Healthcare | 2024 | 100M | Medical records, SSNs | $10-50M |
| MOVEit | 2023 | 1000s orgs | Financial, employee data | $5-20M |
| Ingram Micro | 2025 | 42,521 | Employee, applicant data | $10-50M |
| Optus | 2022 | 9.8M | Personal and financial | Unknown |
| Last Pass | 2022 | 25M | Password vaults | $10-50M |
Ingram Micro's breach is significant but not unprecedented in scale.

What Organizations Should Learn
Every organization should extract lessons from the Ingram Micro incident.
Security Priorities: The incident reinforces that fundamental security practices matter more than advanced tools:
- Network segmentation (prevents lateral movement)
- Access controls (limits damage scope)
- Backups (enables recovery)
- Detection (enables fast response)
- Incident response (minimizes impact)
These don't require massive budgets—they require discipline.
Red Flags to Watch: Organizations should monitor for indicators suggesting they might be breached:
- Unusual user account activities
- Unexpected network traffic spikes
- System performance degradation
- Failed login attempts from unusual locations
- Files encrypted with strange extensions
- Ransom notes appearing on systems
- Communication from law enforcement about suspected intrusions
Preparation Activities: Every organization should:
- Conduct tabletop exercises simulating ransomware attacks
- Identify critical systems and data
- Test backup restoration procedures
- Develop communication plans
- Establish relationships with forensic firms
- Document decision-making procedures
- Assign clear incident response roles

FAQ
What is ransomware and how does it work?
Ransomware is malicious software designed to encrypt an organization's data and systems, making them inaccessible. Attackers then demand payment (ransom) in exchange for decryption keys or promise to delete stolen data. Modern ransomware operations combine encryption (for operational disruption) with data theft (for extortion leverage), creating what's called "dual extortion" attacks. The Ingram Micro attack exemplifies this model: Safe Pay both encrypted systems and stole data to pressure payment.
How did Safe Pay breach Ingram Micro's systems?
The exact initial compromise vector isn't publicly disclosed, but ransomware groups typically gain access through exploited vulnerabilities, phishing campaigns targeting employees, compromised credentials purchased on dark web marketplaces, or compromised third-party vendors with network access. Once inside, attackers move laterally through the network, escalate privileges, disable security controls, and establish persistent access before exfiltrating data and encrypting systems. The speed of Ingram Micro's attack (July 2-3) suggests attackers had either pre-positioned access or exploited a critical vulnerability.
What should I do if I received a breach notification from Ingram Micro?
First, verify the notification is legitimate by contacting Ingram Micro directly through official channels. Then immediately enroll in the free credit monitoring service provided. Place fraud alerts with the three credit bureaus, consider a credit freeze, monitor financial accounts for unauthorized activity, file your tax return early each year (to prevent tax fraud), and review medical records for identity theft. Keep detailed records of any fraudulent activities discovered. The threat window extends beyond the two-year monitoring period, so maintain vigilance indefinitely.
How can organizations prevent attacks like this?
The most critical prevention measures are network segmentation (limiting attacker spread if they breach one system), robust access controls (least privilege principle), offline backups (enabling recovery without paying ransoms), threat detection (early identification of intrusions), and employee training (most attacks start with social engineering). Incident response planning ensures organizations can respond quickly. These fundamentals matter more than expensive security products. Organizations should also conduct regular security assessments, penetration testing, and vulnerability management.
What is the long-term risk for victims whose data was stolen?
Victims face identity theft risks for years, including fraudulent credit applications, loan fraud, tax refund fraud, medical identity theft, and employment fraud. The most dangerous period is immediately after the breach, but risks persist indefinitely since SSNs don't expire. Even after the two-year monitoring period provided by Ingram Micro, victims should monitor credit reports annually, verify tax filings annually, and maintain awareness of potential fraud. Some victims may need to maintain credit freezes permanently.
Has anyone been held accountable for the Ingram Micro breach?
Safe Pay, the ransomware group claiming responsibility, has not been arrested or prosecuted (as of current information). The FBI and international law enforcement agencies likely investigated the group, but ransomware gangs typically operate from countries not extraditing to the U.S., making prosecution difficult. Ingram Micro may face regulatory fines and civil lawsuits from affected individuals or organizations harmed through supply chain effects. Legal actions often take years to conclude.
Why is 3.5TB of data so significant?
Three and a half terabytes represents approximately 1.4 million high-resolution images or could contain detailed records on hundreds of thousands of people. At typical dark web prices (
What does "dual extortion" mean in ransomware attacks?
Dual extortion refers to the modern ransomware tactic of combining encryption (technical disruption) with data theft (extortion threat). Attackers first steal data, then encrypt systems and demand ransom for decryption keys. If the victim refuses to pay, attackers threaten to publicly disclose or sell the stolen data. This creates multiple pressure points: operational disruption from encryption, regulatory/legal risk from data disclosure, and reputational damage from public breach announcement. It's more effective than encryption alone because even if victims have backups, they still face data disclosure threats.
How does this breach affect Ingram Micro's customers?
Direct impact is limited since customer operational data wasn't compromised. However, indirect risks include exposure of internal employee information that might include customer relationship details, transitive risk if attackers use stolen Ingram Micro credentials to target customers, and general business continuity concerns. Customers may want to review security practices with Ingram Micro, verify their own systems for any indicators of compromise, and assess whether supply chain relationships need adjustment based on security performance.
What are the estimated costs of this breach to Ingram Micro?
Total costs typically include forensic investigation (

Conclusion
The Ingram Micro ransomware attack represents a watershed moment in cybersecurity discourse. When a company serving 160,000 customers across 190 countries can be compromised so thoroughly, it demonstrates that scale and resources alone don't guarantee security. The theft of 42,521 individuals' personal information, from Social Security numbers to employment records, illustrates the cascading effects of modern ransomware attacks.
For the affected individuals, the breach creates a decade-long burden of vigilance. The two-year credit monitoring offered by Ingram Micro provides a foundation but insufficient protection against the full scope of identity theft risks. Years from now, some victims will discover fraudulent accounts, false medical records, or tax complications stemming from this July 2025 compromise. Others may escape unscathed. The uncertainty itself is part of the damage.
For organizations, the incident validates what security professionals have long insisted: the fundamentals matter more than flashy technology. Network segmentation, access controls, backup strategies, threat detection, and incident response planning would have significantly limited Ingram Micro's damage. These aren't new concepts, but they're perpetually underinvested compared to expensive security tools that generate impressive marketing materials.
Safe Pay's successful operation and public claims of responsibility illustrate the professionalization of ransomware operations. These groups function like criminal enterprises with customer service, negotiation tactics, and calculated business strategies. Law enforcement efforts have disrupted some groups and arrested individuals, but the ecosystem remains largely operational and highly profitable.
The broader lesson extends to supply chain risk and the interconnected nature of modern IT infrastructure. When a distributor like Ingram Micro is compromised, the damage radiates outward to thousands of organizations and millions of individuals. Future security strategies must account for this transitive risk through vendor security assessments, contractual requirements, and incident planning that contemplates downstream effects.
Moving forward, we'll likely see regulatory evolution requiring faster breach notification, more robust security requirements for critical infrastructure participants, and potentially sanctions against the countries harboring ransomware operations. Individual organizations should use this incident as a catalyst for security improvements rather than waiting for regulatory mandates.
For victims, the immediate action items are clear: activate credit monitoring, place fraud alerts, monitor accounts closely, and maintain records of protective steps taken. For organizations evaluating their own security posture, the Ingram Micro incident should prompt honest assessment of network segmentation, backup strategies, access controls, and incident response planning. Not because breach is inevitable, but because when breach does occur, these fundamentals determine whether the impact is contained or catastrophic.
The most important question isn't whether your organization will be targeted by ransomware. The question is whether you'll be prepared to detect it quickly, contain the damage, and recover effectively. The Ingram Micro case study suggests that's far from guaranteed, even for established companies with significant resources.

Key Takeaways
- Ingram Micro suffered a July 2025 ransomware attack affecting 42,521 individuals, with SafePay claiming responsibility for stealing 3.5TB of data
- Stolen data included SSNs, driver's licenses, passport information, dates of birth, and employment records—creating serious identity theft risk for victims
- Affected individuals should immediately activate free credit monitoring, place fraud alerts with credit bureaus, and monitor financial accounts for unauthorized activity
- Network segmentation, access controls, robust backups, and threat detection would have significantly limited the damage from this attack
- The breach highlights supply chain risks and the need for organizations to audit vendor security practices, particularly for critical infrastructure providers
Related Articles
- Pax8 Data Breach: 1,800 MSPs Exposed in Email Mistake [2025]
- CIRO Data Breach Exposes 750,000 Investors: What Happened and What to Do [2025]
- Malicious Chrome Extensions Spoofing Workday & NetSuite [2025]
- Proton VPN Kills Legacy OpenVPN: What You Need to Know [2025]
- Cisco CVE-2025-20393 Critical Vulnerability Finally Patched [2025]
- X Platform Outages: What Happened and Why It Matters [2025]



