Void Link: The Advanced Linux Malware Reshaping Cloud Security [2025]
Something shifted in the threat landscape last month, and most organizations don't even know it yet.
Security researchers uncovered a Linux malware framework so advanced, so comprehensively designed, that it's forcing the entire industry to reconsider what we thought we knew about Linux vulnerabilities. It's called Void Link, and unlike the opportunistic worms and script kiddie tools we're used to seeing, this thing was built by professionals who understand cloud infrastructure, containerization, and long-term persistence in ways that previous Linux threats simply didn't.
Here's what makes it different: most Linux malware in the wild is designed for quick exploitation. Grab credentials, execute a ransomware payload, move on. Void Link is the opposite. It's architected for stealth, for patience, for becoming a ghost in your infrastructure that nobody detects for months or years. It includes over 37 distinct modules that can be mixed and matched depending on the target environment. It knows how to detect which cloud platform it's running on. It includes rootkit functionality. It can harvest credentials across multiple systems. And worst of all, researchers haven't found it actively attacking anyone yet, which means we're potentially looking at a honeypot period where attackers are testing, refining, and waiting for the perfect moment to deploy.
This isn't a theoretical threat. This is the future of Linux attacks arriving early.
In this guide, we're going to break down what Void Link actually is, how it works, why it's fundamentally different from previous Linux malware, and most importantly, what you need to do about it. Whether you're managing cloud infrastructure, running containerized workloads, or just trying to keep your Linux systems secure in an increasingly hostile environment, understanding Void Link is now non-negotiable.
TL; DR
- Void Link is a modular malware framework containing 37+ modules designed for cloud-first attack operations, not quick exploitation
- Cloud detection is built-in: It identifies AWS, GCP, Azure, Alibaba, and Tencent environments, suggesting future expansion to other providers
- Professional infrastructure: Localized for Chinese-affiliated operators with anti-analysis, rootkit, and credential harvesting modules indicating serious threat actor investment
- Zero wild infections discovered: This is pre-deployment reconnaissance, meaning defenders have a rare window to prepare
- Containerization awareness: Void Link detects Docker and Kubernetes environments, targeting modern application deployment architectures
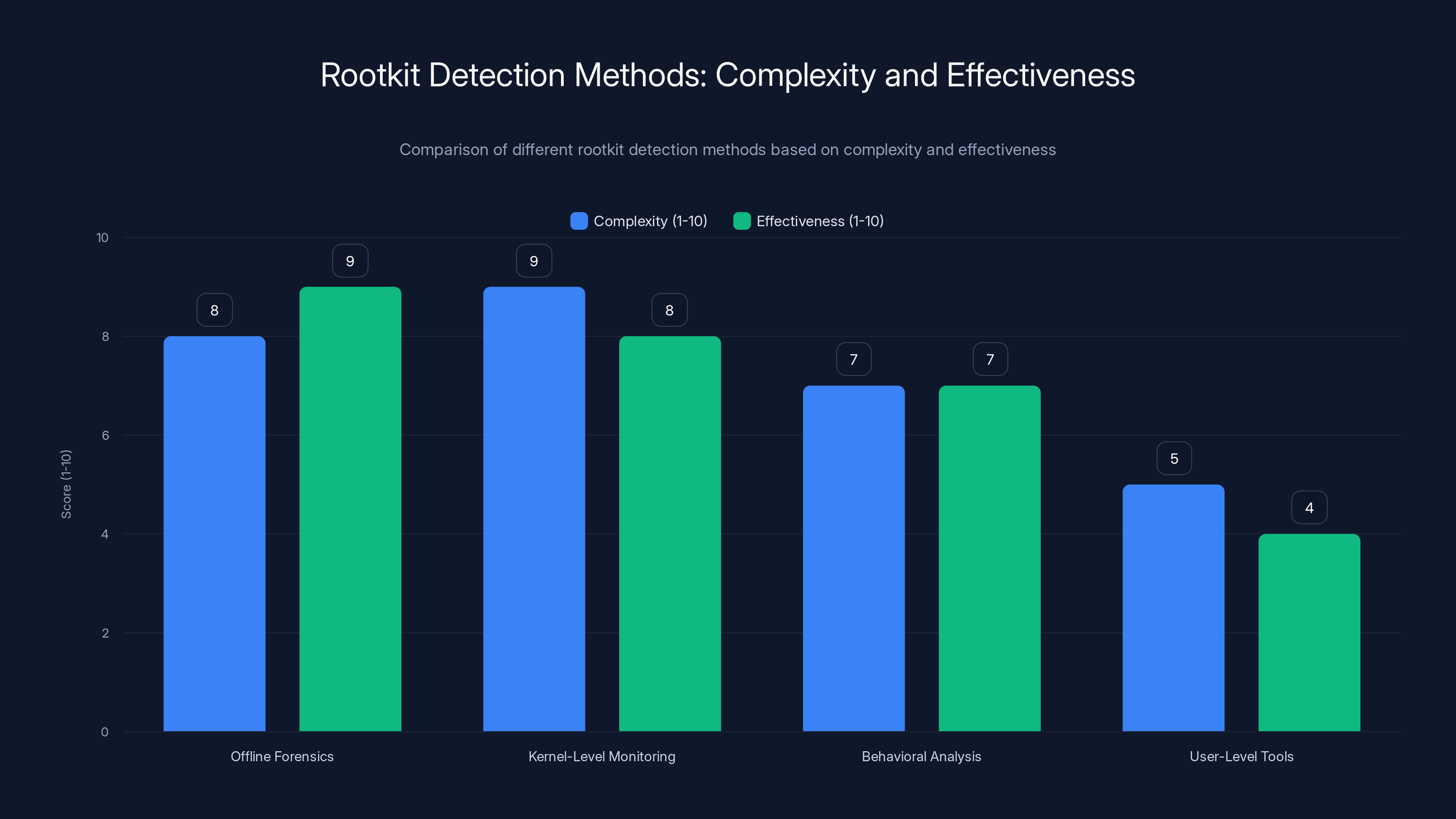
Offline forensics and kernel-level monitoring are the most effective but also the most complex methods for detecting rootkits. User-level tools are less effective due to rootkit interception.
What We're Actually Dealing With: The Void Link Reality
When security researchers first started analyzing the binaries, they didn't immediately understand what they were looking at. The code was clean. The architecture was sophisticated. The comments in the source code were in Chinese, suggesting the development team wasn't trying to hide their origin. But what really stood out was the deliberate decision-making visible in every module.
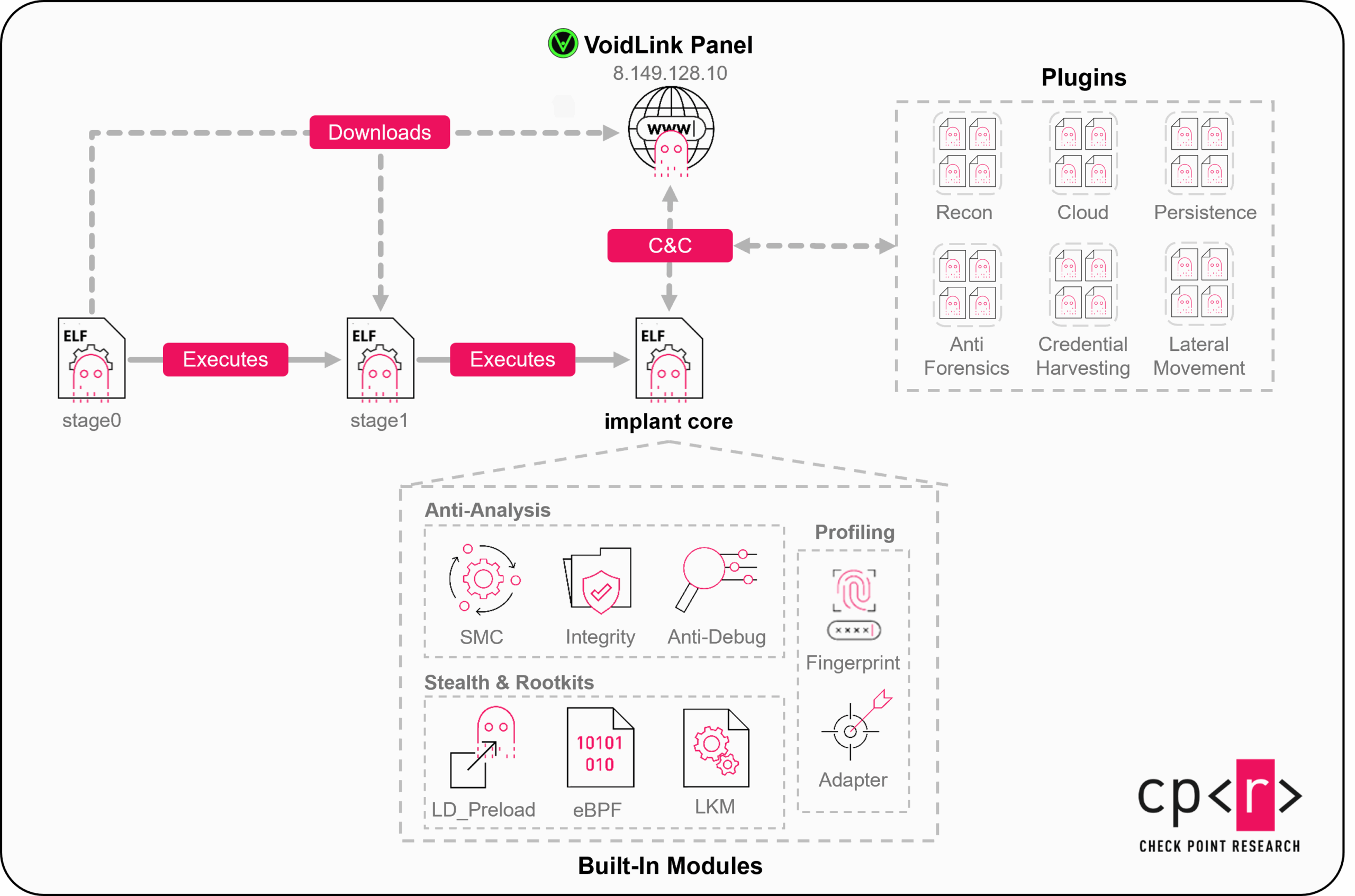
Void Link isn't malware in the traditional sense. It's an implant framework. Think of it as a Trojan horse equipped with a full toolkit for post-compromise operations. You deploy it once, it establishes a foothold, and then it becomes a delivery mechanism for whatever else the attacker wants to do. The malware itself is less interesting than what it enables.
The discovery came through a relatively mundane channel. Researchers were monitoring clusters of Linux binaries on Virus Total, the service where antivirus vendors and security researchers share samples. Inside one batch, they found something unusual: a two-stage loader. The first stage is stripped down, minimal, designed to avoid detection. The second stage is where things get interesting. It contains core modules that are baked into the binary, plus APIs and infrastructure for downloading and installing plugins at runtime. This architecture means you could deploy the same base malware across thousands of systems and customize each one's capabilities based on what that particular environment offers.
The presence of no known infections in the wild creates an unusual situation. Typically, when researchers discover malware, it's already compromised hundreds or thousands of systems. They're analyzing forensic evidence from real attacks. Void Link is different. This appears to be a framework still under development, discovered before widespread deployment. The source code contains TODO comments and incomplete features. The researchers found indications that attackers plan to add detection for additional cloud providers like Huawei, Digital Ocean, and Vultr in future versions. This is a threat actor in the middle of their development cycle, and we're watching them build in real-time.
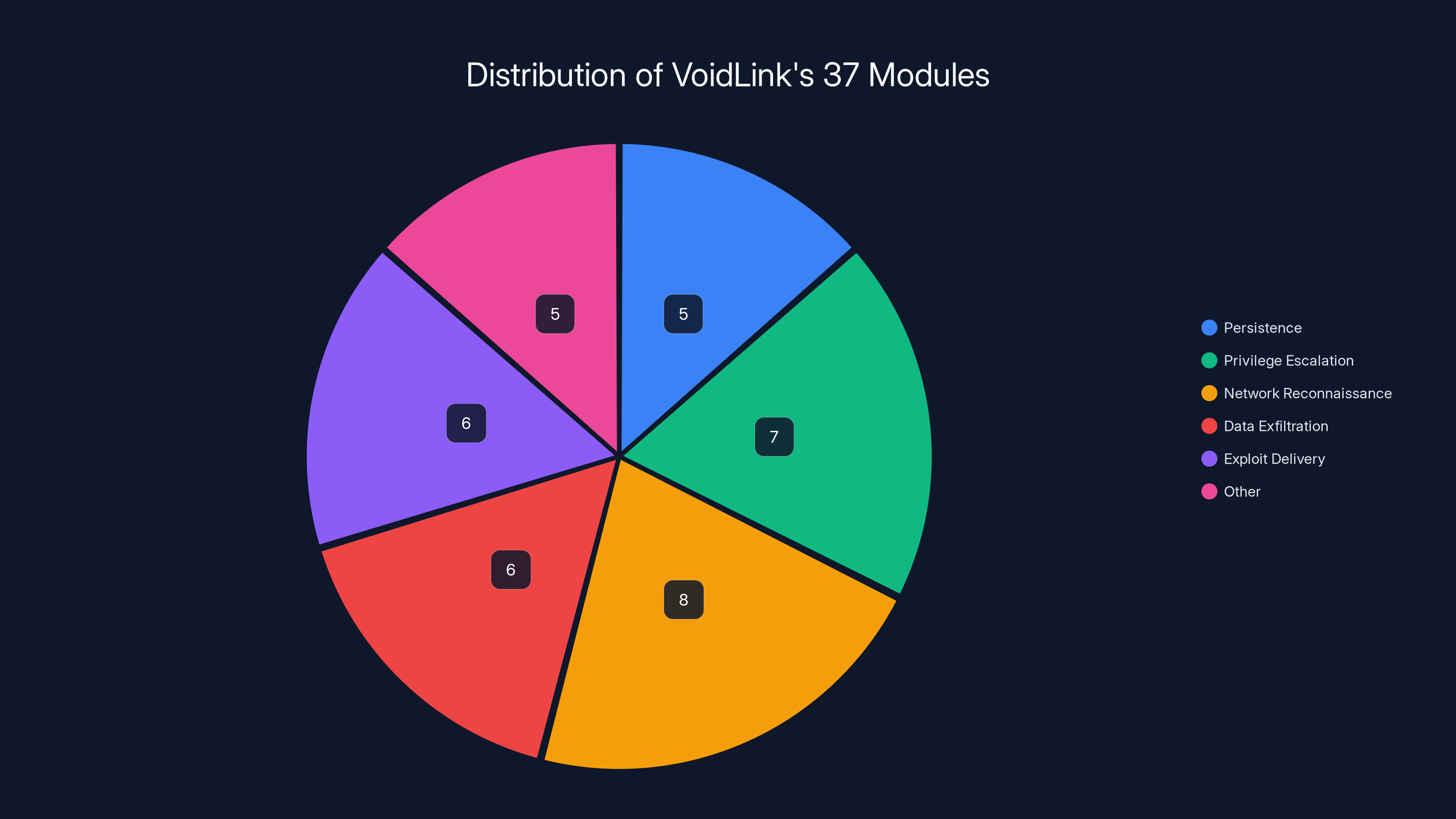
VoidLink's modular architecture includes 37 modules, with a significant portion dedicated to network reconnaissance and privilege escalation. Estimated data based on typical malware capabilities.
The Modular Architecture: Why 37 Modules Changes Everything
Understanding why Void Link's architecture matters requires understanding how most malware is built. Traditionally, attackers bundle specific capabilities into a single malware executable. Need to steal SSH keys? Include key-stealing code. Need to escalate privileges? Include privilege escalation exploits. Need to move laterally? Include network reconnaissance tools. The executable gets bigger, slower, and more detectable.
Void Link throws this approach out the window.
Instead, it implements a robust plugin system. The base malware is lean and focused on establishing persistence and providing the infrastructure for plugins. The actual attack capabilities come from modules that are downloaded, installed, and executed at runtime. This approach has several profound implications:
First, it dramatically reduces detection surface. Antivirus signatures can't scan for capabilities that don't exist in the base malware. If the system isn't currently running the privilege escalation module, antivirus software won't find privilege escalation code. An attacker could deploy the malware across an entire organization, and each system would look different to defensive tools.
Second, it enables precise targeting. An attacker investigating a target environment could determine that a particular system is running Docker containers, and only deploy the container-exploitation modules to that system. Another system running traditional services gets a completely different module set. This granular customization makes it much harder for defenders to create blanket detection strategies.
Third, it allows the framework to evolve without redeploying the base malware. New capabilities can be distributed as plugins. Exploits can be updated without touching the core implant. This means Void Link deployments become increasingly dangerous over time, not stale.
Researchers identified these 37 modules, though this list is incomplete because some functionality was still being developed:
Cloud Detection and Profiling: Modules that identify which cloud provider is hosting the system by examining metadata, checking for cloud-specific processes, and querying cloud provider APIs. This isn't just about identifying AWS versus Azure. It's about understanding the infrastructure topology, which services are available, and what kind of access the compromised system might have.
Credential Harvesting: Perhaps the most dangerous modules. Void Link can extract SSH private keys from user home directories, passwords from various sources, browser cookies that might contain authentication tokens, Git credentials stored in configuration files, API keys embedded in environment variables, and items stored in the system keyring. For a cloud infrastructure penetration, this is the jackpot. One compromised system can provide credentials for dozens of other systems and services.
Privilege Escalation: Modules designed to move from the initial compromised user account to root access. This might include known CVE exploits, token manipulation, or capabilities that take advantage of misconfigured sudo rules. The researchers didn't detail specific exploits, but the presence of multiple privilege escalation modules suggests attackers planned for various scenarios.
Process and Service Discovery: Deep reconnaissance modules that enumerate all running processes, services, and their configurations. This helps attackers understand what applications are running, what capabilities they might have, and how they're configured.
Rootkit Functions: These modules modify system behavior at low levels, potentially hiding processes, files, network connections, and other evidence of compromise from standard monitoring tools. A rootkit makes detection exponentially harder because defensive tools see a falsified view of system state.
Lateral Movement: Modules designed to move through a network, identify other systems, and attempt to compromise them. These might scan for services, attempt credential reuse, or deploy variations of Void Link to other hosts.
The practical implication is this: Void Link isn't built for ransomware or data exfiltration or any single objective. It's built for acquiring and maintaining access. Once deployed, it becomes a beachhead for whatever the attacker wants to do next. That might be cryptomining, data theft, lateral movement into other systems, or serving as a launching point for attacks against other organizations.

Cloud-First Tradecraft: Why This Matters Now
For years, Linux malware was a secondary concern compared to Windows threats. This was partially accurate. Most enterprise workloads ran on Windows. Most malware authors focused where the targets were. But the industry was underestimating a fundamental shift happening in real-time: the migration of workloads to cloud platforms and containerized environments.
Void Link explicitly acknowledges this shift. The framework includes dedicated detection and exploitation capabilities for AWS, GCP, Azure, Alibaba, and Tencent Cloud. These aren't afterthoughts. They're core design considerations. The malware checks for cloud-specific metadata services, examines environment variables that cloud platforms set, and queries cloud provider APIs to understand the infrastructure topology.
Why does this matter? Because cloud platforms have fundamentally different attack surfaces than traditional on-premises infrastructure. A Linux server sitting in your data center is isolated. It has defined network connections. You can monitor who logs in, what gets installed, what services run. A Linux instance in AWS might have ephemeral IP addresses. It might be part of an auto-scaling group that adds and removes instances constantly. It might have temporary credentials that rotate every few hours. It might be accessible only through a bastion host or jump server. Traditional Linux defensive strategies don't translate cleanly to cloud environments.
Void Link's designers clearly understood this. They built capabilities specifically for cloud environments:
Metadata Service Exploitation: Cloud platforms expose metadata services that running instances can query. AWS has the EC2 metadata service, GCP has the metadata server, Azure has the metadata endpoint. These services leak enormous amounts of useful information: instance identity, IAM role names, temporary credentials, user data scripts, VPC configuration, and more. Void Link likely queries these services to extract information attackers need for further attacks.
Container Detection: The framework explicitly detects whether it's running inside a container. This matters because container compromises have different implications than bare-metal compromises. A compromised container might have limited persistence opportunities. Container technologies like Kubernetes automatically restart crashed processes. Shared kernel vulnerabilities might be exposed that don't affect non-containerized systems. Void Link adjusts its behavior based on what it detects.
Service Account Credential Harvesting: In cloud-native deployments, applications authenticate using service accounts with specific permissions. These credentials might be stored in files that Void Link's credential harvesting modules could extract. Compromising service account credentials is often more valuable than compromising user credentials because service accounts often have broader permissions.
Environment-Specific Persistence: Different cloud platforms and container technologies provide different persistence opportunities. A Linux instance in AWS might persist through VPC flow logs or through modifications to auto-scaling group launch templates. A Kubernetes pod might persist through modifications to the deployment configuration. Void Link likely includes modules that exploit platform-specific persistence mechanisms.
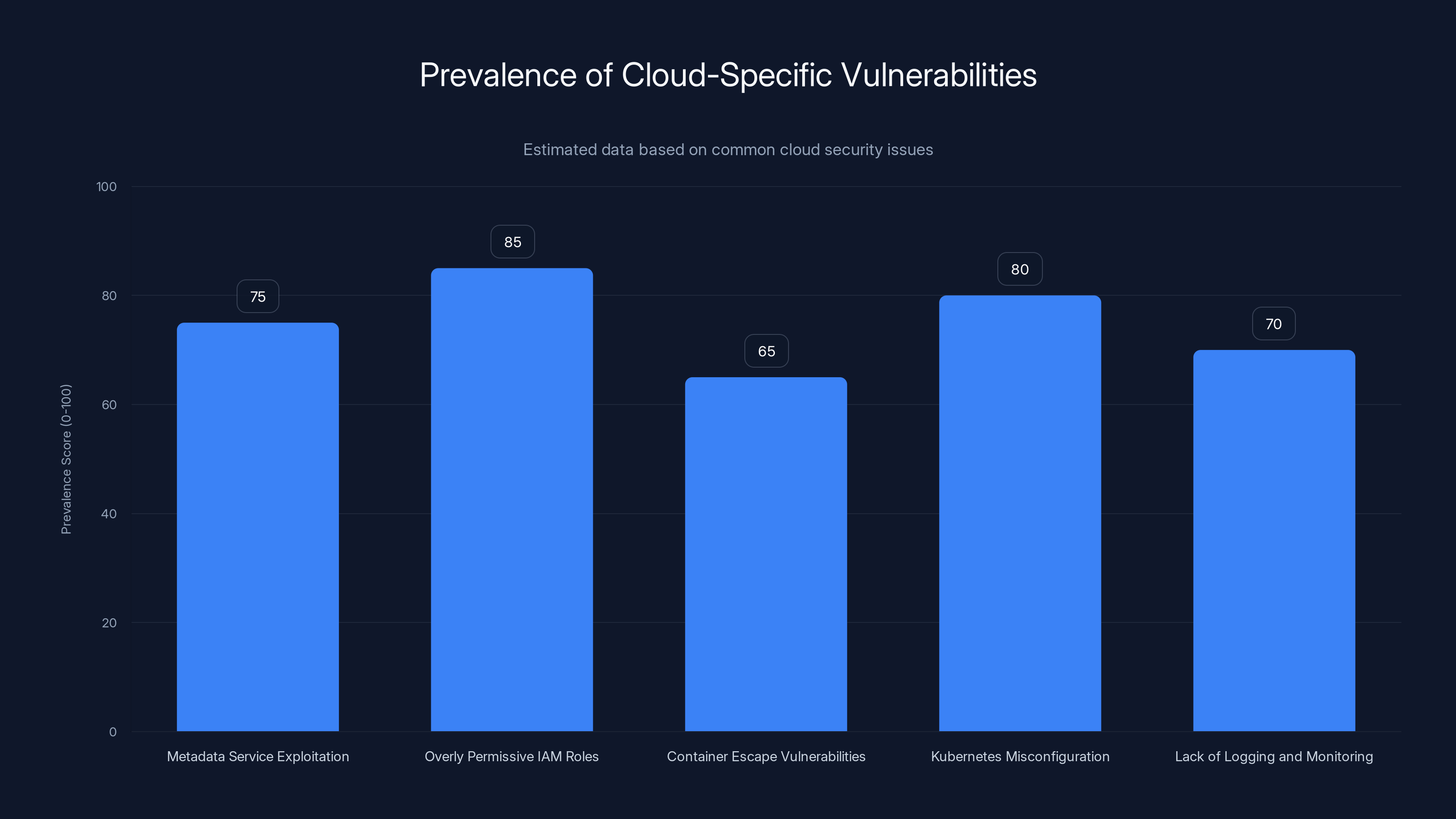
Overly permissive IAM roles and Kubernetes misconfigurations are estimated to be the most prevalent cloud vulnerabilities, highlighting areas needing improved security practices. Estimated data.
Indicators of Professional Threat Actor Development
One detail keeps getting lost in discussions of Void Link: this is clearly professional work.
Not professional in the sense of competent. Professional in the sense of institutional. Some threat actor with resources, expertise, and organizational structure spent significant time building this. The code quality is high. The architecture is sophisticated. The approach to detecting different cloud platforms is methodical. The inclusion of rootkit functionality, multiple lateral movement techniques, and credential harvesting across different systems suggests a team with diverse expertise: kernel-level programmers, cloud infrastructure specialists, systems administrators, and security researchers.
Several pieces of evidence support this:
The Localization: The code is localized for Chinese-affiliated operators. Strings, comments, and variable names are in Chinese, suggesting the development happened in a Chinese development environment. This isn't necessarily nefarious—many legitimate teams work this way. But it suggests a specific origin point and organizational context.
The Ongoing Development: The source code contained TODO comments and incomplete features. This isn't finished malware. It's malware under active development. The researchers found indications that future versions would add detection for Huawei, Digital Ocean, and Vultr. An amateur threat actor wouldn't be planning for platform expansion. A professional organization would.
The Architectural Sophistication: The plugin system, the modular design, the API infrastructure—these reflect careful planning. Someone designed this architecture based on understanding how malware needs to evolve in the field, how defenders respond to threats, and how to build systems that survive initial compromise and continue to be useful as defenders adapt.
The Absence of Obvious Monetization: Most malware in the wild is designed for quick financial gain. Ransomware pays out quickly. Credential theft sells credentials quickly. Cryptomining monetizes immediately. Void Link doesn't appear designed for any of these. It's designed for access and control, suggesting an attacker more interested in maintaining long-term capability than quick paydays. This is typical of government-sponsored threat actors or advanced cybercriminal organizations targeting specific high-value victims.
The Anti-Analysis and Evasion Capabilities
One aspect that deserves deeper examination is how Void Link avoids detection and analysis. Malware typically fails because defensive teams identify it, analyze it, and develop countermeasures. Void Link incorporates multiple layers of protection against this.
Anti-Debugging: The malware detects debuggers that security researchers and automated analysis tools might attach to processes. When a debugger is detected, the malware behaves differently, often crashing or entering infinite loops. This prevents dynamic analysis—the process of running malware in a controlled environment and watching what it does.
Integrity Checks: The malware verifies that its code hasn't been modified or patched by defensive tools. If integrity checks fail, it exits or alerts operators. This protects against defensive techniques like code patching or hooking that modify malware behavior to prevent malicious operations.
Security Product Detection: Void Link enumerates installed security software and hardening measures. If it detects antivirus software, EDR (Endpoint Detection and Response) agents, or other defensive tools, it likely alters its behavior. It might disable certain capabilities, slow down its operations, or avoid certain attack techniques that would trigger the detected security software.
Legitimate-Looking Network Connections: The command and control communication uses what appear to be legitimate outbound connections. Instead of connecting to obviously malicious servers, Void Link might tunnel commands through seemingly normal traffic, making network-based detection much harder.
Stealth Modules: The rootkit functionality allows Void Link to hide itself from standard system monitoring. A rootkit intercepts system calls and returns modified results. When you run ps to list processes, the rootkit removes Void Link from the output. When you check network connections with netstat or ss, the rootkit hides Void Link's connections. When you examine file system activity, the rootkit hides Void Link's files.
The combination of these techniques creates a defensive nightmare. Traditional signature-based detection might not see anything amiss because Void Link can hide itself. Behavioral-based detection gets fooled because the malware detects the detection tool and changes behavior. Rate-based detection (flagging systems that suddenly generate lots of network traffic) gets bypassed because Void Link is designed for stealth, not speed.
VoidLink's architecture excels in stealth and detection evasion, making it a sophisticated implant framework. (Estimated data)
The Credential Harvesting Nightmare
Let's dig deeper into the credential harvesting modules because this is where individual system compromise turns into network-wide catastrophe.
When Void Link compromises a system, one of its first priorities is extracting every credential available on that system. These aren't just user passwords. They're a comprehensive inventory of authentication material:
SSH Private Keys: These are stored in ~/.ssh/id_rsa, ~/.ssh/id_ed 25519, and similar locations. SSH keys are how administrators and automated systems authenticate to other Linux systems. Stealing SSH keys means an attacker can log into other systems without passwords, without triggering brute-force detection, without leaving evidence in login logs (if PAM isn't configured to log key-based authentication). An attacker could have dozens of administrators' SSH keys extracted from a single compromised system.
Passwords and Authentication Tokens: Void Link looks for passwords stored in shell configuration files like .bash_history, .zsh_history, and .fish_history. These files often contain commands with passwords in plaintext. Environment variables might contain API keys. Configuration files for applications often contain hardcoded credentials.
Browser Cookies and Session Tokens: If any administrator or developer is using a browser on a compromised Linux system (via X11 or a remote desktop protocol), Void Link can extract cookies and session tokens from browser storage. These tokens might be active sessions to cloud provider consoles, Git Hub, Git Lab, or internal administrative interfaces.
Git Credentials: Many developers store Git credentials in ~/.gitconfig or in credential helpers. These credentials provide access to Git repositories, which often contain source code, deployment scripts, and other sensitive information.
API Keys and Authentication Tokens: Applications running on the system might store API keys in environment variables, configuration files, or environment-specific secret storage. A compromised application server could expose API keys for payment processors, third-party services, or internal APIs.
System Keyring Contents: Modern Linux systems store credentials in keyrings that applications can access. SSH agents store passphrases for encrypted SSH keys. Other keyrings might store database passwords, VPN credentials, or other sensitive authentication material.
The implications are severe. A single compromised system becomes a starting point for attacking dozens of other systems. An attacker could extract SSH keys from a bastion host and use them to compromise every internal Linux server that host can reach. Extracted API keys could provide access to cloud resources, payment processing systems, or internal APIs. Git credentials could provide access to repositories containing deployment scripts, which in turn could provide access to all production systems.
This is why credential harvesting is often called the "keys to the kingdom." For a sophisticated attacker, compromising a single well-connected system is often more valuable than compromising many isolated systems because that one system has credentials for accessing many others.
Lateral Movement and Network Propagation
Once Void Link establishes a foothold, the lateral movement modules kick in. These are the tools that transform a single compromised system into a beachhead for attacking the broader network.
The lateral movement process typically follows this pattern:
Environmental Reconnaissance: Void Link first enumerates detailed information about the compromised system and its network environment. It discovers all network interfaces and their IP addresses. It determines which networks the system is connected to. It identifies the default gateway and attempts to determine the network topology. It enumerates all users on the system and attempts to determine which other systems they might have access to.
User and Group Enumeration: Understanding what users and groups exist on a system provides crucial context for lateral movement. Void Link can identify administrative users, service accounts, and application-specific users. It can determine group memberships, which indicate what resources different users might access. It can identify which users have recently logged in, indicating they might have active sessions on other systems.
Service and Application Discovery: Different systems run different services. A database server has different attack surfaces than a web application server, which has different attack surfaces than a mail server. Void Link identifies what services are running, what version they're running, and whether known vulnerabilities exist. It identifies applications that might have valuable data or capabilities.
Network Service Enumeration: Void Link scans the local network for other systems running services it can attack. This might include services that have known vulnerabilities, services that use default credentials, or services that might accept stolen credentials extracted from other systems.
Privilege Escalation for Broader Access: Once the environment is mapped out, Void Link attempts to escalate privileges on the compromised system. With root access, the malware can modify network configurations, inspect network traffic, or access protected authentication material that might not be available to non-root users.
Credential Reuse: The harvested credentials from the compromised system become tools for attacking other systems. An attacker tries extracted SSH keys against other systems in the network. They attempt extracted passwords against systems that might use the same password. They use API keys to access cloud resources. Each successful authentication provides another entry point for Void Link deployment.
Deployment and Persistence: Once another system is compromised, Void Link deploys itself and establishes persistence mechanisms specific to that system. The attacker now has not one, but two footholds in the network, providing redundancy and expanding access.
This process repeats, expanding the attacker's reach system by system. In a poorly segmented network, a single compromised system could provide access to hundreds of others. In a well-segmented network with proper credential management, lateral movement becomes much harder, potentially stopping the attack.
VoidLink framework shows a high focus on AWS, GCP, and Azure due to their widespread use, with slightly less emphasis on Alibaba and Tencent. Estimated data.
Detection Challenges: Why This Is So Hard to Spot
Understanding why Void Link is dangerous requires understanding why it's difficult to detect. Traditional security approaches don't work well against sophisticated implants like this.
Signature-Based Detection Doesn't Work: Signatures are like wanted posters. You describe what the bad guy looks like, and defenders look for that match. But Void Link uses rootkit functionality to hide itself. Running ps doesn't show it. Listing network connections doesn't show it. Checking running modules doesn't show it. Traditional signature-based tools that look for malware by scanning running processes won't find it because it's hiding itself at the kernel level.
Behavioral Detection Gets Fooled: Some security tools look for suspicious behavior rather than signatures. Unusual network traffic gets flagged. Unexpected file modifications get flagged. Rapid process spawning gets flagged. But Void Link is specifically designed to avoid these behaviors. It's designed for slow, patient reconnaissance and stealing credentials quietly. It might not generate unusual network traffic if it communicates infrequently. It doesn't rapidly spawn processes. It's patient, which makes behavioral detection much harder.
Log Analysis Becomes Unreliable: Linux administrators typically rely on analyzing logs to detect compromise. But a sophisticated attacker might modify logs to remove evidence. Void Link, with root access, could truncate or modify syslog, auth.log, audit logs, or other system logs. If logs have been tampered with, traditional log analysis becomes unreliable. You're analyzing incomplete data, not realizing that evidence of the compromise has been deleted.
Encrypted Communications Hide Command and Control: If Void Link's command and control communications are encrypted and tunneled through legitimate-looking traffic, network-based detection becomes very difficult. A network defense tool might see HTTPS traffic to a legitimate server and not recognize that the traffic is also carrying covert commands to malware. The defender can't inspect the traffic because it's encrypted.
Anti-Analysis Defeats Testing: Security researchers and incident responders often test systems to see how they respond to certain stimuli. Attempt to attach a debugger? Void Link detects it and crashes. Try to modify the malware? Integrity checks fail, and the malware stops running. Spin up analysis tools? Void Link detects them and enters a standby mode. These anti-analysis features prevent normal testing approaches.
The convergence of these factors creates a situation where traditional defensive approaches are largely ineffective. You can't detect what you can't see. You can't analyze what fights back against analysis. You can't trust logs that have been tampered with.
Cloud-Specific Vulnerabilities and Attack Surfaces
Void Link's explicit focus on cloud environments highlights vulnerabilities in how organizations typically manage cloud security. These aren't new vulnerabilities, but they're often neglected.
Metadata Service Exploitation: Cloud metadata services are designed to provide instances with information they need to operate, but they're often over-privileged. An application inside an EC2 instance can query the metadata service and obtain temporary AWS credentials with the same permissions as the instance's IAM role. If the IAM role has too many permissions, the metadata service leak is catastrophic. An attacker could extract credentials that provide access to all S3 buckets, databases, and other resources the role can access.
Overly Permissive IAM Roles: Many organizations assign broad permissions to compute instance roles for convenience. "Let the application access any S3 bucket" is easier to configure than "let the application access only this specific S3 bucket." But this creates the situation where compromising any compute instance potentially compromises all resources that instance's role can access.
Container Escape Vulnerabilities: Containers provide isolation, but they share the host kernel. A vulnerability in the kernel could allow an application inside a container to break out and compromise the host. A compromised container host might be able to access other containers on the same host, potentially exposing data or capabilities from other applications.
Kubernetes Misconfiguration: Kubernetes provides security features like network policies and RBAC (role-based access control), but these are often configured poorly or not at all. A compromised pod in one namespace might be able to access pods in other namespaces. An attacker might be able to escalate to cluster-admin privileges. An attacker might be able to read secrets stored in the cluster.
Lack of Logging and Monitoring: Many organizations move to cloud platforms without implementing adequate logging and monitoring. Application logs might not be collected. API calls might not be audited. Network flows might not be captured. This means a compromise might go undetected for months because there's no mechanism to detect it.
Temporary Credential Leakage: Cloud platforms rotate temporary credentials frequently, but these credentials are exposed in many places: environment variables, logs, temporary files, credential caches, and more. An attacker could extract these temporary credentials and use them before they expire. Even if rotation is happening, the window of opportunity might be sufficient.
Void Link's architecture explicitly targets these vulnerabilities. The malware is designed to exploit the specific ways organizations often misconfigure cloud security.
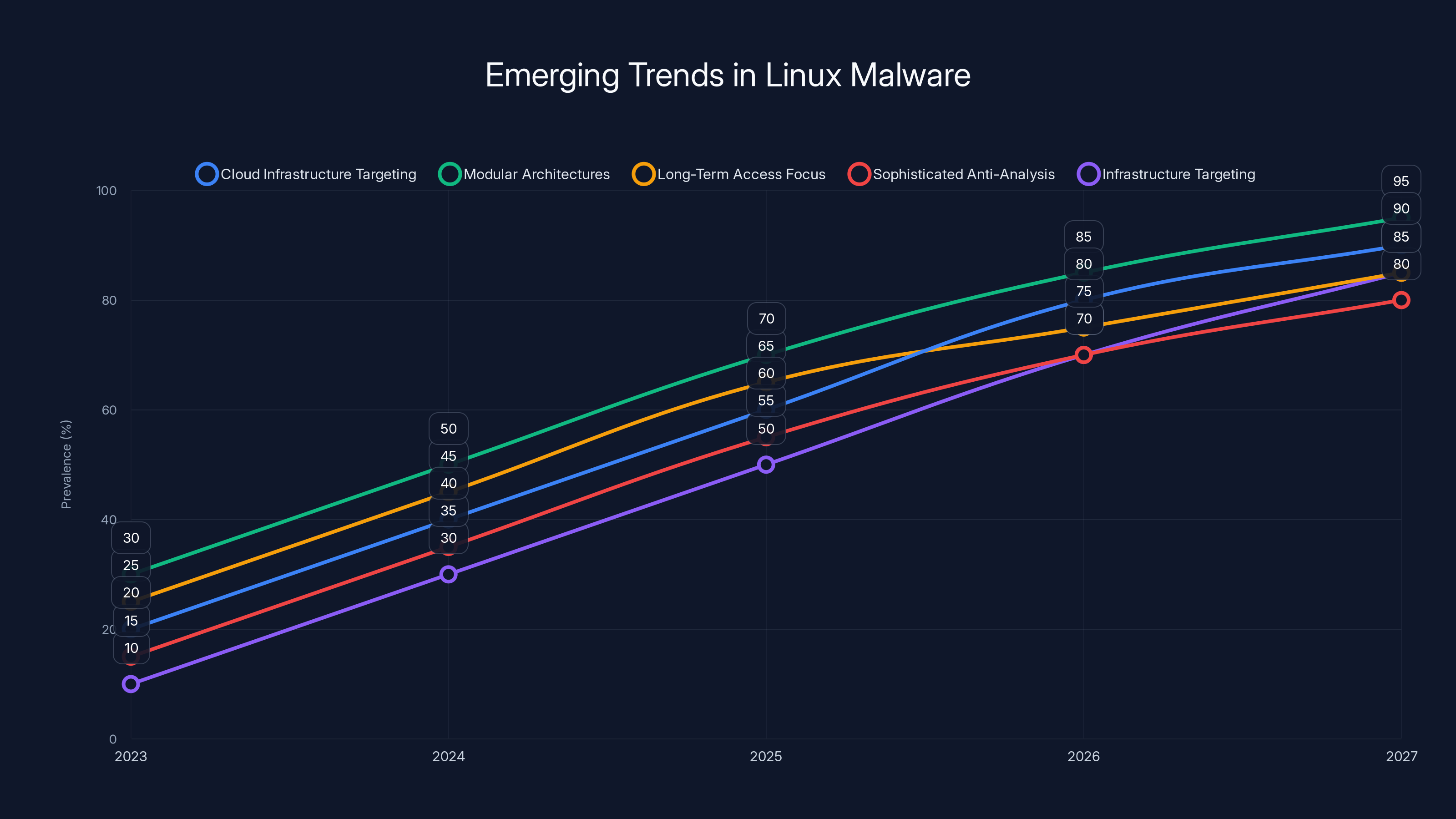
Estimated data shows a significant rise in cloud infrastructure targeting and modular architectures in Linux malware by 2027, highlighting the need for advanced security measures.
The Rootkit Component: Hiding in Plain Sight
The rootkit functionality deserves special attention because it's what transforms Void Link from "dangerous malware" to "nearly undetectable persistent threat."
A rootkit is malware that operates at a privileged level and modifies how the operating system reports its state. Instead of actually hiding processes or files, a rootkit intercepts system calls that would normally return the truth and substitutes lies.
When you run the command ps aux to list all running processes, you're making a system call to the kernel asking "what processes are running?" A rootkit intercepts this call and filters the results, removing the malware process from the list. The user sees what looks like a complete list of processes, but the malware process has been hidden.
The same applies to other system calls. When you run ss -tlnp to list network connections, a rootkit might hide connections to the malware's command and control server. When you examine file system activity with auditd, a rootkit might hide file modifications made by the malware. When you examine loaded kernel modules with lsmod, a rootkit might hide the rootkit itself if it's loaded as a kernel module.
The key insight is that from the perspective of tools running at user level, nothing suspicious appears. The system looks normal. All processes visible appear legitimate. All network connections appear expected. The system is hiding in plain sight.
Detecting rootkits requires different approaches:
Offline Forensics: Powering down the system and analyzing the disk from another system can sometimes reveal evidence of a rootkit because the rootkit can't intercept requests from outside the system. But this is disruptive and requires expertise.
Kernel-Level Monitoring: Monitoring from kernel space or from hardware can sometimes bypass rootkit interception. But this requires specialized tools and is more complex than typical system administration.
Behavioral Analysis: Sometimes rootkits leave behavioral clues even if they hide their artifacts. Unusual resource consumption, unexpected CPU activity, or unusual kernel logs might indicate a rootkit is present.
Hardware-Level Security: Some modern systems include security features that operate at the hardware level, below the operating system and thus below where rootkits can interfere. But these features aren't universally available or enabled.
The presence of rootkit functionality in Void Link means that typical system administration approaches won't detect it. You can't run commands to find it. You can't examine logs to verify it's not present. You need specialized tools and approaches.
The Plugin System: Evolution Over Time
One aspect that makes Void Link particularly dangerous is its plugin architecture. Most malware is relatively static. Once deployed, it has the capabilities it was built with. New campaigns might deploy updated versions, but each version has a fixed set of capabilities.
Void Link's plugin system means the capabilities can evolve dynamically. This has profound implications for how the malware can be used over months and years.
Consider a scenario: Void Link is deployed across an organization's cloud infrastructure in January. The attacker knows the environment and has confidence the malware will be undetected. Over the following months, the attacker learns more about the organization's defenses, capabilities, and objectives. In March, they push a new plugin that exploits a vulnerability discovered in January. In June, they push another plugin that implements a completely new attack technique. The organization might be monitoring for the original malware, but new capabilities are added without requiring redeployment of the base malware.
This also means that security researchers analyzing Void Link might be analyzing incomplete samples. The 37 modules currently known might represent only the modules that were present in the sample discovered. Additional modules might exist in deployments that haven't been analyzed. The framework might be more dangerous than current understanding suggests.
Why This Matters Now: The Timing of Void Link
The discovery of Void Link during a period of no known wild infections raises critical questions about timing and deployment intentions.
Threats typically follow a pattern: they're developed, tested, deployed against targets, detected by defenders, analyzed by security researchers, and countermeasures are developed. The time between deployment and detection has shrunk dramatically. A malware variant today might be detected within days or weeks rather than months or years.
Void Link's discovery before wide deployment suggests a few possibilities:
First, this might be a pre-deployment phase. Threat actors develop and test malware before wide deployment. They might test it in their own environment, against test systems, or in limited deployments against friendly targets. This might be what we're seeing—threat actors have finished development and are in testing before they begin campaigns against real targets.
Second, this might be preparation for a specific campaign. Threat actors sometimes maintain malware in reserve, perfecting it for weeks or months before using it against specific high-value targets. This malware might be prepared for targeting specific organizations or industries.
Third, this might be a leaked sample. Perhaps someone with access to the threat actor's infrastructure leaked the sample, or perhaps it was exfiltrated by another threat actor and shared. Either way, we have visibility into something we shouldn't have.
Regardless of which scenario is accurate, the implication is clear: defenders have a window of time to prepare. Most malware that causes significant damage does so because defenders had no advance warning. In this case, we have advance warning. The question is whether organizations will use that time effectively.
Detection and Response: A Defensive Playbook
Understanding Void Link's capabilities is important, but it's only useful if it translates into defensive actions.
Immediate Actions:
-
Obtain Indicators of Compromise: Security researchers published detailed indicators of compromise for Void Link. These include file hashes of known samples, file paths where components might reside, registry keys (if running in WSL or other Linux on Windows), and command-and-control server addresses. Import these indicators into security information and event management (SIEM) systems, EDR tools, and other detection platforms. This won't catch all variants, but it will catch known samples.
-
Audit Cloud IAM Configurations: Since Void Link explicitly targets cloud environments, examine IAM roles, policies, and service accounts for excessive permissions. Identify instances or services with overly broad access. Implement principle of least privilege across cloud resources. Remove permissions that aren't actively needed.
-
Enable Cloud Audit Logging: Ensure that API calls to cloud platforms are being logged and monitored. This includes Cloud Trail for AWS, Cloud Audit Logs for GCP, and Activity Log for Azure. Configure alerts for suspicious activities: unexpected credential use, unusual API calls, or permissions changes.
-
Harden SSH Access: Since Void Link targets SSH keys and SSH provides a way for attackers to move laterally, implement strong SSH access controls. Use SSH keys rather than passwords. Implement certificate-based authentication. Restrict which users can have SSH access. Monitor SSH access logs for suspicious patterns.
-
Implement Kernel Module Monitoring: Since Void Link might load rootkits as kernel modules, monitor kernel module loads. Unusual kernel modules should be investigated. Implement kernel module whitelisting if possible, allowing only known legitimate modules to load.
Ongoing Monitoring:
-
Network-Based Detection: While encryption can hide command-and-control traffic, analyzing network flows for unusual patterns might reveal compromise. A system that suddenly begins communicating with suspicious infrastructure or that begins lateral movement scanning is a red flag. Implement network segmentation so that lateral movement is more difficult and more visible.
-
Process and Parent Process Analysis: Monitor for unusual process creation chains. A compromised system might spawn unexpected processes. A web server process spawning a shell is suspicious. Processes making unexpected system calls are suspicious. Modern endpoint detection tools can monitor these patterns.
-
File Integrity Monitoring: Monitor critical system files and directories for unexpected modifications. Changes to system binaries, library files, or configuration files might indicate compromise. Tools like aide (Advanced Intrusion Detection Environment) or Samhain can provide file integrity monitoring.
-
Credential Theft Detection: Monitor for unusual access to credential storage locations. If processes are accessing SSH private keys, .bash_history, or other credential repositories, that's suspicious. Monitor for unusual authentication attempts using extracted credentials.
-
Behavioral Baselines: Establish baselines for normal system behavior—CPU usage, memory usage, network bandwidth, process creation rate, file modifications, and so on. Deviations from these baselines might indicate compromise.
Comparing Void Link to Other Advanced Malware
Void Link didn't emerge in a vacuum. It's part of a continuum of increasingly sophisticated malware and attack frameworks. Understanding where it fits helps clarify its significance.
Compared to Emotet: Emotet was notorious Windows malware that served as a delivery platform for other malware. Like Void Link, it used a modular architecture and served as an implant for other attacks. But Emotet primarily targeted Windows systems and was eventually disrupted by law enforcement in 2021. Void Link's focus on Linux and cloud is notably different and reflects the evolution of attack targets.
Compared to Mirai: Mirai was Linux malware that compromised Io T devices and other Linux systems. It was designed for distributed denial-of-service (DDo S) attacks rather than long-term access. Void Link is far more sophisticated, designed for persistent access rather than short-term attack campaigns.
Compared to APT Frameworks: Government-sponsored threat actors often use sophisticated malware frameworks. Tools like Poison Ivy, Cobalt Strike, and other red-team frameworks are used by both legitimate penetration testers and malicious threat actors. Void Link is comparable in sophistication to these frameworks, suggesting threat actors with significant resources and expertise.
Compared to Cloud-Specific Malware: Few pieces of malware have been explicitly designed to target cloud infrastructure and containers. Void Link's cloud-first design and containerization awareness make it relatively unique. This positions it as a watershed moment in malware evolution—the point where threat actors explicitly designed tools for cloud-native architectures.
The Future of Linux Malware: What Void Link Signals
Void Link isn't an isolated development. It signals important trends in malware evolution and attack sophistication.
Trend 1: Cloud Infrastructure Becomes Primary Target: As organizations move workloads to cloud platforms and containerized environments, threat actors are following. The next generation of malware will be explicitly designed for cloud targets, not adapted from Windows or traditional Linux malware.
Trend 2: Modular Architectures Become Standard: Monolithic malware is becoming rare. Sophisticated threat actors use modular implants that can be customized and evolved over time. This will likely become the standard across all categories of malware.
Trend 3: Long-Term Access Over Short-Term Objectives: The trend is away from malware designed for quick financial gain (ransomware, banking trojans) toward malware designed for maintaining access. This reflects a strategic shift from quick attacks to campaigns that might last months or years.
Trend 4: Greater Sophistication in Anti-Analysis: As defensive tools become more capable, malware becomes more sophisticated in detecting and defeating those tools. Void Link's anti-debugging, anti-analysis, and anti-tools capabilities will become standard.
Trend 5: Explicit Targeting of Infrastructure, Not Just Endpoints: Malware designers are increasingly targeting infrastructure—cloud platforms, container orchestration systems, networks—not just individual systems. Void Link's focus on metadata services, IAM credentials, and lateral movement reflects this shift.
Understanding these trends helps organizations prepare not just for Void Link, but for the future of threats.
Lessons for Infrastructure Defense
Tackling a threat like Void Link requires not just incident response but fundamental changes to how infrastructure is designed and managed.
Principle 1: Assume Compromise
Defensive strategy should begin with the assumption that compromise will happen. The question isn't whether an attacker will breach your infrastructure, but when. Given this assumption, defenses should focus on detecting and limiting the damage of compromise, not just preventing compromise.
For Void Link specifically, this means implementing detection mechanisms that assume systems might be compromised. Monitor systems as if they're already compromised. Look for lateral movement as if it's already happening. Audit credentials as if they've already been stolen.
Principle 2: Implement Defense in Depth
Single-layer defenses fail. Firewalls can be bypassed. Antivirus can be evaded. Intrusion detection can be fooled. But an attacker would need to bypass multiple defensive layers simultaneously. This is exponentially harder.
For cloud infrastructure, this means combining network segmentation, IAM policies, monitoring, incident response capabilities, and regular security testing. A compromise at one layer shouldn't immediately compromise the entire infrastructure.
Principle 3: Reduce Blast Radius Through Segmentation
A single compromised system shouldn't provide access to all resources. Network segmentation limits lateral movement. Container isolation limits escape. IAM policies limit what resources a compromised identity can access. The more segmentation exists, the more work an attacker must do to expand access.
For organizations using cloud platforms, this means implementing network policies to restrict communication between resources, implementing RBAC to limit what identities can do, and ensuring that not all resources have access to all other resources.
Principle 4: Invest in Visibility
You can't defend against what you can't see. Comprehensive logging, monitoring, and alerting are essential. This includes:
- Application logs from all applications
- System logs from all systems
- Network logs capturing all network flows
- API logs capturing all interactions with cloud platforms
- Audit logs capturing who did what and when
Void Link is designed to avoid being visible, which makes it essential that defenders implement the monitoring necessary to see it despite its efforts to hide.
Principle 5: Maintain Incident Response Capabilities
Even with excellent prevention and detection, compromises will happen. Organizations need the capability to respond effectively. This means:
- Incident response plans that are regularly tested
- Forensic capabilities to investigate compromises
- Recovery capabilities to restore systems after compromise
- Threat intelligence to understand what happened and how to prevent similar attacks
Organizational Response: Building Your Defensive Strategy
For organizations concerned about threats like Void Link, a comprehensive response strategy should include multiple elements:
Immediate (Next 30 Days):
- Conduct a security assessment focused on cloud infrastructure and Linux systems
- Obtain and deploy indicators of compromise for Void Link
- Review and strengthen SSH access controls
- Audit IAM roles and policies for excessive permissions
- Ensure comprehensive logging is enabled for cloud platforms
Short-Term (Next 90 Days):
- Implement network segmentation to limit lateral movement
- Deploy EDR or equivalent endpoint monitoring to Linux systems
- Conduct tabletop exercises simulating Void Link compromise
- Develop incident response playbooks for Linux compromise scenarios
- Implement baseline security configurations for cloud infrastructure
Long-Term (Ongoing):
- Establish continuous monitoring and threat detection capabilities
- Implement zero-trust security architecture
- Conduct regular penetration testing and red-team exercises
- Maintain threat intelligence on emerging threats
- Establish security training and awareness programs
FAQ
What is Void Link and why is it significant?
Void Link is an advanced Linux malware framework featuring 37+ customizable modules designed for cloud environments, containerized infrastructure, and long-term persistence. Its significance lies in its sophisticated architecture, cloud-first design, and professional development indicating institutional threat actor involvement. Unlike opportunistic Linux malware, Void Link is purpose-built for maintaining stealthy access to cloud infrastructure over extended periods, representing a shift in threat actor focus toward cloud and containerized environments.
How does Void Link establish persistence and avoid detection?
Void Link uses multiple evasion techniques including rootkit functionality to hide itself at kernel level, anti-debugging protections to prevent analysis, integrity checking to detect security tool modifications, and security product detection to alter behavior when defenses are present. The framework's modular architecture means it can customize which capabilities are deployed on each system. Additionally, the plugin system allows capabilities to be added or removed at runtime without requiring redeployment of the base malware, making detection patterns obsolete as new capabilities are distributed.
What are the specific threats Void Link poses to cloud infrastructure?
Void Link explicitly targets AWS, GCP, Azure, Alibaba, and Tencent Cloud environments by detecting metadata services, extracting temporary credentials, exploiting IAM role over-permissions, and harvesting service account credentials. The framework can identify containerized environments and exploit container escape vulnerabilities. Most critically, it performs credential harvesting across multiple systems and protocols including SSH keys, API tokens, and authentication credentials stored in configuration files. A single compromised system could provide access to dozens of other systems and cloud resources through stolen credentials.
How can organizations detect Void Link infections?
Traditional signature-based detection is difficult because Void Link uses rootkit functionality to hide itself from user-level inspection tools. Effective detection requires kernel-level monitoring, network-based behavioral analysis looking for lateral movement patterns, file integrity monitoring of critical system files, and analysis of unusual authentication attempts using harvested credentials. Organizations should implement comprehensive logging of cloud API calls, monitor for unusual process creation chains, and establish behavioral baselines for normal system activity. Deployment of indicators of compromise from security researchers in SIEM and EDR tools can catch known samples, though this won't catch all variants or future versions.
What is the current threat level of Void Link?
No confirmed wild infections of Void Link have been discovered despite its sophisticated capabilities, suggesting it remains in pre-deployment or testing phases. This provides a unique window of opportunity for defenders to prepare. However, the professional quality of the code, explicit cloud-targeting capabilities, and ongoing development visible in the source code indicate this threat will likely become actively deployed against high-value targets in the near future. Organizations should treat this as an emerging threat requiring immediate defensive preparation rather than a current crisis.
How does Void Link's modular architecture differ from traditional malware?
Traditional malware bundles all capabilities into a single executable, making it larger, slower, and more detectable. Void Link deploys a lean base framework that loads capabilities dynamically through plugins at runtime. This approach reduces detection surface by avoiding inclusion of unused capabilities, enables precise targeting by loading only relevant modules per-system, and allows evolution without redeploying base malware. The capability set can be customized per victim, per system, and updated over time as the attacker discovers new opportunities or as defenders develop countermeasures.
What immediate actions should organizations take?
Organizations should immediately obtain Void Link indicators of compromise from security research and deploy them to security tools. Conduct urgent audits of cloud IAM configurations to eliminate excessive permissions. Enable comprehensive audit logging for cloud platforms. Strengthen SSH access controls by implementing key-based authentication with certificate validation. Audit systems for unexpected kernel modules that might indicate rootkit installation. Monitor credentials storage locations for unauthorized access. Begin tabletop exercises simulating Void Link compromise scenarios to test incident response capabilities.
Why is Void Link designed for Chinese-affiliated operators?
The source code is localized for Chinese-affiliated operators with comments, strings, and variable names in Chinese. This suggests development occurred within a Chinese development environment, likely indicating state-sponsored threat actors or sophisticated cybercriminal organizations operating from China. The professional quality, institutional approach, long-term access focus, and cloud-first design all suggest governmental or well-resourced organizational backing rather than individual threat actors or opportunistic cybercriminals.
How does credential harvesting from Void Link lead to network-wide compromise?
Void Link extracts SSH private keys, passwords, API keys, Git credentials, and authentication tokens from compromised systems. These credentials provide direct authentication access to other systems without triggering brute-force detection or password-based alerts. An attacker with extracted SSH keys from an administrative system could authenticate to dozens of other systems the administrator manages. Extracted API keys provide access to cloud resources, payment systems, and other services. Extracted Git credentials provide access to source code repositories containing deployment scripts and other sensitive information. Each compromised system becomes a stepping stone to compromising many others.
What are the biggest gaps in typical Linux security defenses against advanced threats like Void Link?
Most organizations underinvest in Linux security compared to Windows security, leaving detection and monitoring capabilities significantly weaker on Linux systems. Cloud security practices often lack sufficient IAM controls and monitoring. Container security often relies on basic isolation without comprehensive runtime monitoring. Few organizations implement kernel-level monitoring or rootkit detection. Credential management is often poor, with passwords and keys stored in accessible locations. Network segmentation is minimal, allowing lateral movement to succeed. Incident response capabilities for Linux are typically underdeveloped. These gaps collectively make Linux systems attractive targets for sophisticated threat actors like those deploying Void Link.
Conclusion: Preparing for the Next Wave
Void Link represents something we haven't seen often in the Linux threat landscape: a sophisticated, professionally-developed malware framework explicitly designed for cloud environments and containerized infrastructure. This isn't malware adapted from Windows. It's not malware designed for general-purpose Linux systems. It's malware built from the ground up for the infrastructure where organizations are moving their workloads.
The absence of known wild infections doesn't mean the threat is theoretical. It means we have a rare opportunity to prepare before widespread deployment. Threat actors have invested significant resources into building Void Link. They're not going to let that investment sit idle. The question is whether defenders are using this window to implement the security practices, monitoring, and incident response capabilities necessary to detect and contain Void Link when deployment happens.
The security industry is often reactive, responding to threats only after they've caused damage. Void Link offers a chance to be proactive. The indicators are available. The attack surface is understood. The defensive approaches that work against Void Link are known.
The real question is whether your organization is going to act on this advance warning, or whether you'll discover Void Link only after it's already compromised your infrastructure.
Start with the immediate actions: obtain indicators of compromise, audit your cloud configurations, strengthen your access controls, and implement comprehensive monitoring. These steps won't completely prevent Void Link compromise, but they'll significantly improve your chances of detecting it quickly and containing the damage if compromise occurs.
Then work on the longer-term changes: implement defense in depth, reduce blast radius through segmentation, invest in visibility, and build incident response capabilities. These changes transform your infrastructure from a collection of vulnerable systems to a resilient platform that can withstand even sophisticated attacks.
Void Link is coming. The question is whether your organization will be ready.
Key Takeaways
- VoidLink is a professionally-developed 37+ module Linux malware framework designed for cloud infrastructure with modular architecture enabling dynamic capability deployment
- The malware includes explicit detection for AWS, GCP, Azure, Alibaba, and Tencent Cloud environments, with planned expansion to additional cloud providers
- Rootkit functionality, anti-analysis techniques, and credential harvesting across SSH keys, API tokens, and authentication materials create sophisticated evasion and lateral movement capabilities
- Zero known wild infections indicate pre-deployment or testing phases, providing a rare defensive window to prepare before widespread exploitation campaigns
- Effective defense requires defense-in-depth strategies including network segmentation, IAM hardening, comprehensive monitoring, and cloud-specific incident response capabilities
Related Articles
- N8n Ni8mare Vulnerability: What 60,000 Exposed Instances Need to Know [2025]
- Target Data Breach 2025: 860GB Source Code Leak Explained [2025]
- DDoS Attacks in 2025: How Threats Scale Faster Than Defenses [2025]
- Hackers Targeting LLM Services Through Misconfigured Proxies [2025]
- Geopatriation & Cloud Sovereignty: What 2026 Means for Enterprise Data [2026]
- Kimsuky QR Code Phishing: How North Korean Hackers Bypass MFA [2025]
![VoidLink: The Advanced Linux Malware Reshaping Cloud Security [2025]](https://tryrunable.com/blog/voidlink-the-advanced-linux-malware-reshaping-cloud-security/image-1-1768343961125.jpg)



