Tri Zetto Provider Solutions Data Breach: Everything You Need to Know About the 700K+ Exposure
In October 2025, a healthcare technology company discovered something that would shake the industry. Tri Zetto Provider Solutions (TPS), a subsidiary handling critical infrastructure for major US health insurers and providers, had been breached. What made this worse wasn't just the discovery date, it was the timeline. Unauthorized actors had been inside their systems for almost a full year, quietly exfiltrating sensitive data since November 2024.
The number keeps growing. Initially reported at several hundred thousand, the breach now affects over 700,000 individuals. That's not a typo. More than seven hundred thousand people's names, Social Security numbers, health insurance information, and personal details are now in the hands of criminals who are actively looking for ways to weaponize that data.
If you work in healthcare, run a provider organization, or you're just one of the millions of Americans whose data might be caught in this mess, you need to understand what actually happened, what's at stake, and what you should do right now.
TL; DR
- Over 700,000 people affected by the Tri Zetto Provider Solutions breach, with exposure including names, SSNs, addresses, birth dates, and health insurance details
- Breach timeline: Attackers accessed systems in November 2024, but weren't discovered until October 2025 (almost 11 months of undetected access)
- No payment data or medical records stolen, but the compromised information is enough for medical identity fraud and targeted phishing attacks
- Multiple class-action lawsuits filed against Cognizant, TPS's parent company, with claims of negligent security practices
- Victims should freeze credit, monitor accounts, and consider identity theft protection services immediately

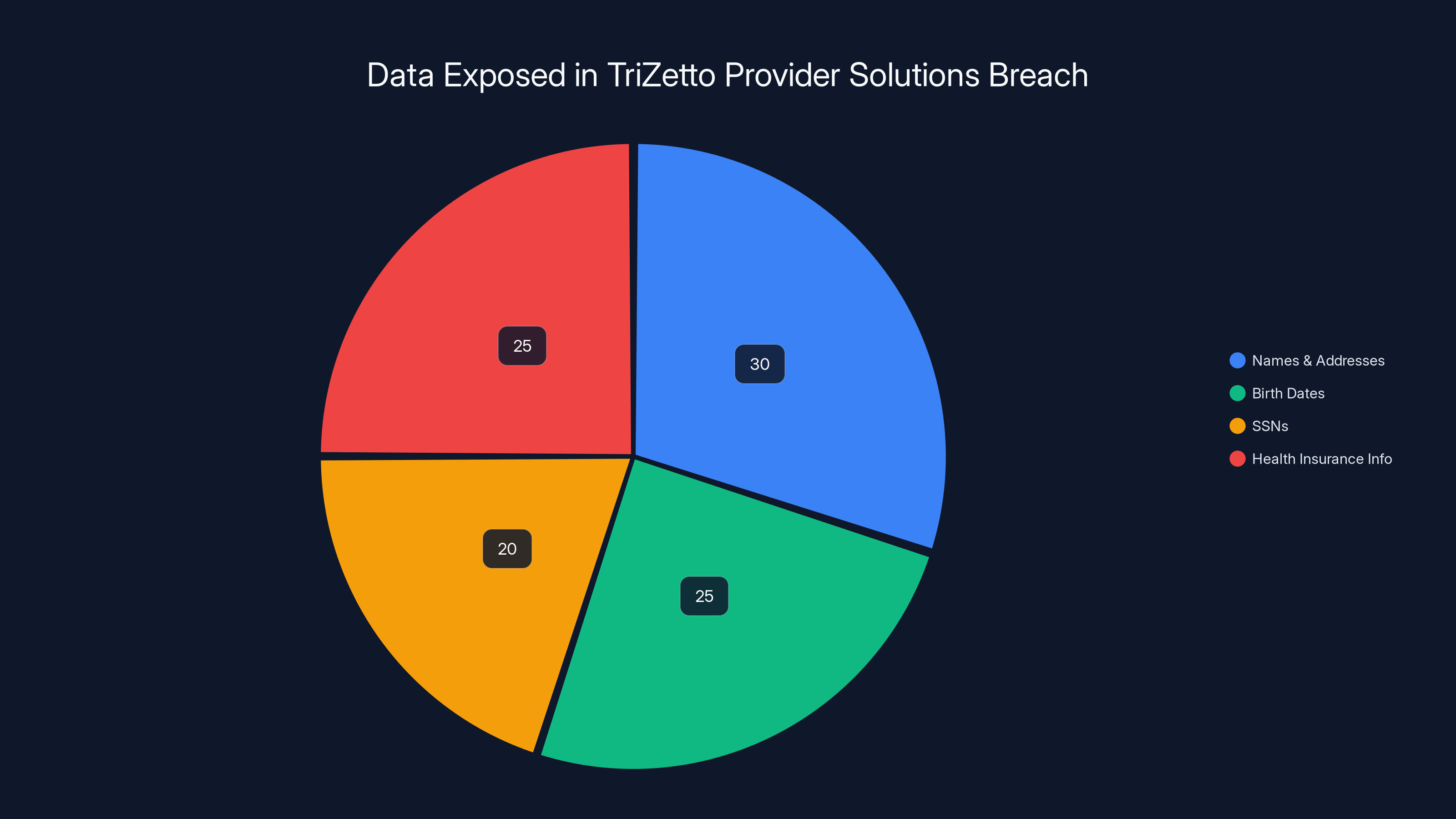
The breach exposed various types of personal information, with names and addresses being the most common, followed by birth dates, SSNs, and health insurance information. Estimated data.
What Exactly Is Tri Zetto Provider Solutions?
Before we dive into the breach itself, you need to understand why this company matters so much. Tri Zetto Provider Solutions isn't some small healthcare startup you've never heard of. It's a critical piece of infrastructure for how healthcare billing and claims processing actually works in America.
TPS is a subsidiary of Cognizant, a multinational IT services company with tens of thousands of employees. Cognizant owns TPS, and TPS serves as the backbone software platform for revenue cycle management and claims processing. That's not jargon that sounds important—it's literally how health insurance companies and healthcare providers move money around, process claims, and manage patient billing.
The customer list reads like a who's who of American healthcare. Denver Health and Hospital Authority uses TPS systems. So does Emblem Health, one of the largest health insurers in New York. Bucksport Regional Health Center relies on it. Deschutes County Health Services, which made the breach public, uses TPS infrastructure. Think about your last doctor's visit. The billing you received, the insurance claim that got processed, the explanation of benefits that landed in your mailbox. TPS systems very likely touched that transaction somewhere in the pipeline.
This is why the breach matters at a systemic level. It's not like a small medical clinic got hacked. It's like finding out the nervous system connecting hundreds of healthcare organizations to each other and to insurance companies got compromised and nobody noticed for nearly a year.
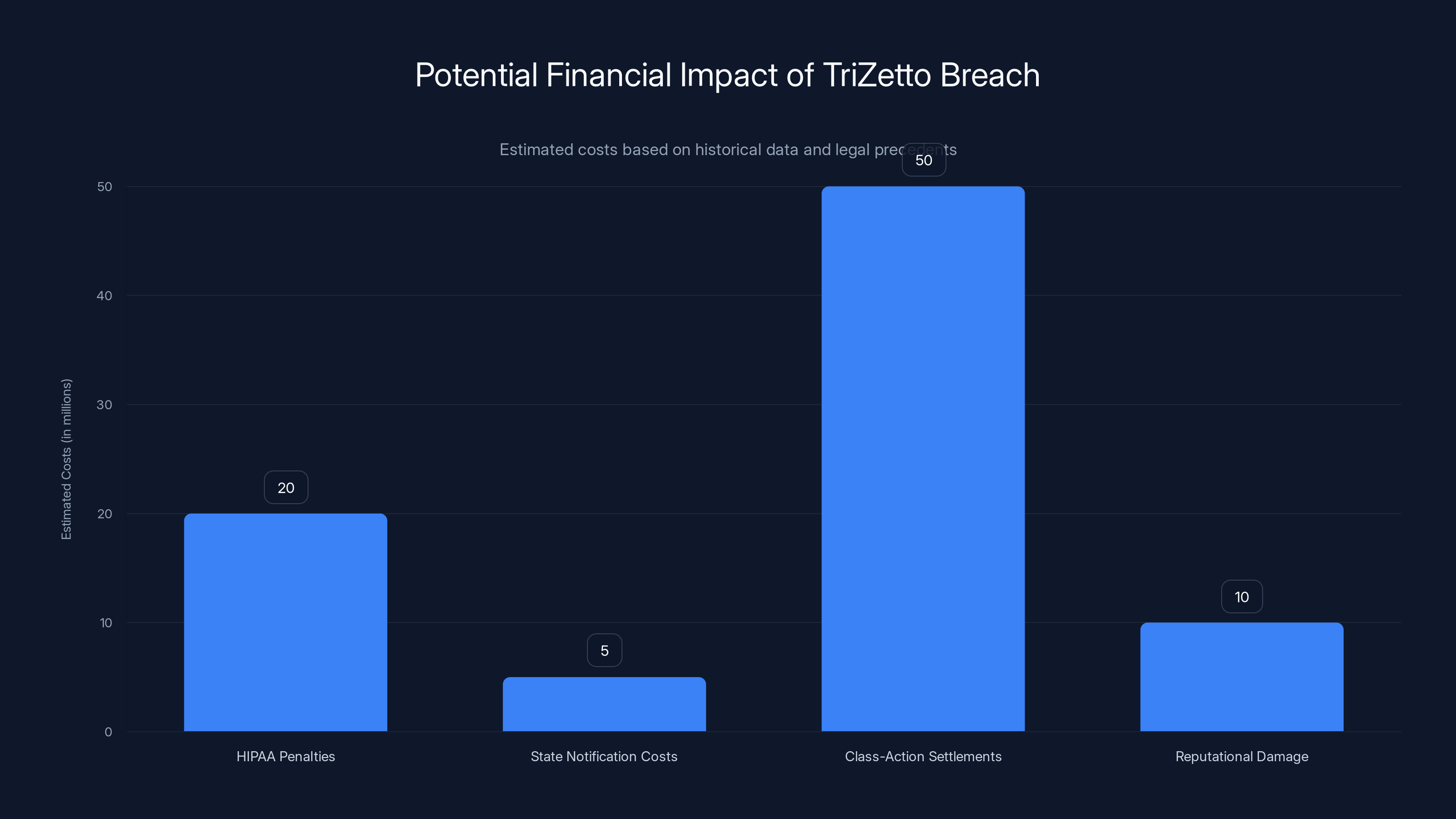
The TriZetto breach could lead to significant financial impacts, with class-action settlements potentially reaching $50 million. Estimated data based on historical precedents.
The Timeline: How Long Were Attackers Inside?
This is where the breach gets genuinely chilling. The timeline alone should make every healthcare CTO lose sleep.
In November 2024, threat actors gained unauthorized access to Tri Zetto Provider Solutions systems. They didn't blow the doors off with a dramatic zero-day exploit that everyone noticed immediately. They got in quietly. They established persistence. They started exploring what data they could reach and began planning how to extract it.
Then they waited. And extracted. And waited. They had direct access to systems containing personal health information, insurance details, and Social Security numbers for hundreds of thousands of people. They were like thieves who'd found a master key to a bank vault and decided to take their time looting it, stealing a little bit each day, betting that no one would notice.
Eleven months passed. That's 330+ days of undetected breach. That's roughly 40 weeks that attackers could move through systems, understand how the infrastructure worked, escalate privileges, establish backup access points, and download everything they wanted. It's not hyperbole to say that this was an exceptionally long dwell time for a breach of this magnitude.
In October 2025, TPS finally spotted something. The timeline isn't entirely clear on what triggered the discovery, but it was reactive, not proactive. Someone noticed unusual activity, launched an investigation, and realized that the barn doors had been wide open for almost a year.
The delay between the initial breach in November 2024 and discovery in October 2025 represents a catastrophic failure in security monitoring and threat detection. Most organizations should have detection capabilities that catch unusual data exfiltration within days or weeks, not months.

What Data Was Actually Stolen?
Let's be specific about what the attackers obtained. The exposed data includes:
Personal Identifiers: Full names of affected individuals. These are tied directly to healthcare relationships, making targeted attacks much easier to execute.
Social Security Numbers (SSNs): This is the golden ticket for identity theft. Your SSN is one of the few pieces of information that can be used to open credit lines, apply for loans, file fraudulent tax returns, and establish new identities in your name.
Addresses and Birth Dates: Combined with your name and SSN, these create a complete identity profile that can be weaponized in dozens of ways.
Health Insurance Information: This includes insurance carrier names and member ID numbers. These details are particularly dangerous in healthcare fraud scenarios.
Provider Names: Information about which healthcare providers you've used can reveal medical conditions and treatment patterns.
What Was NOT Stolen (important to note): The companies confirmed that medical diagnoses, treatment information, and payment card data were not included in the exposure. That's the only small silver lining here.
But here's the thing most news coverage doesn't emphasize: they don't need your medical records to cause serious harm. They don't need to know about your chemotherapy or your psychiatric medications. They just need your SSN, insurance number, and some basic personal information. That's enough to:
- Commit medical identity fraud by using your insurance to get treatments, medications, or durable medical equipment
- File false insurance claims in your name
- Open new insurance policies and rack up fraudulent claims
- Run highly targeted phishing campaigns pretending to be your insurer
- Sell your information on darknet markets to other criminals

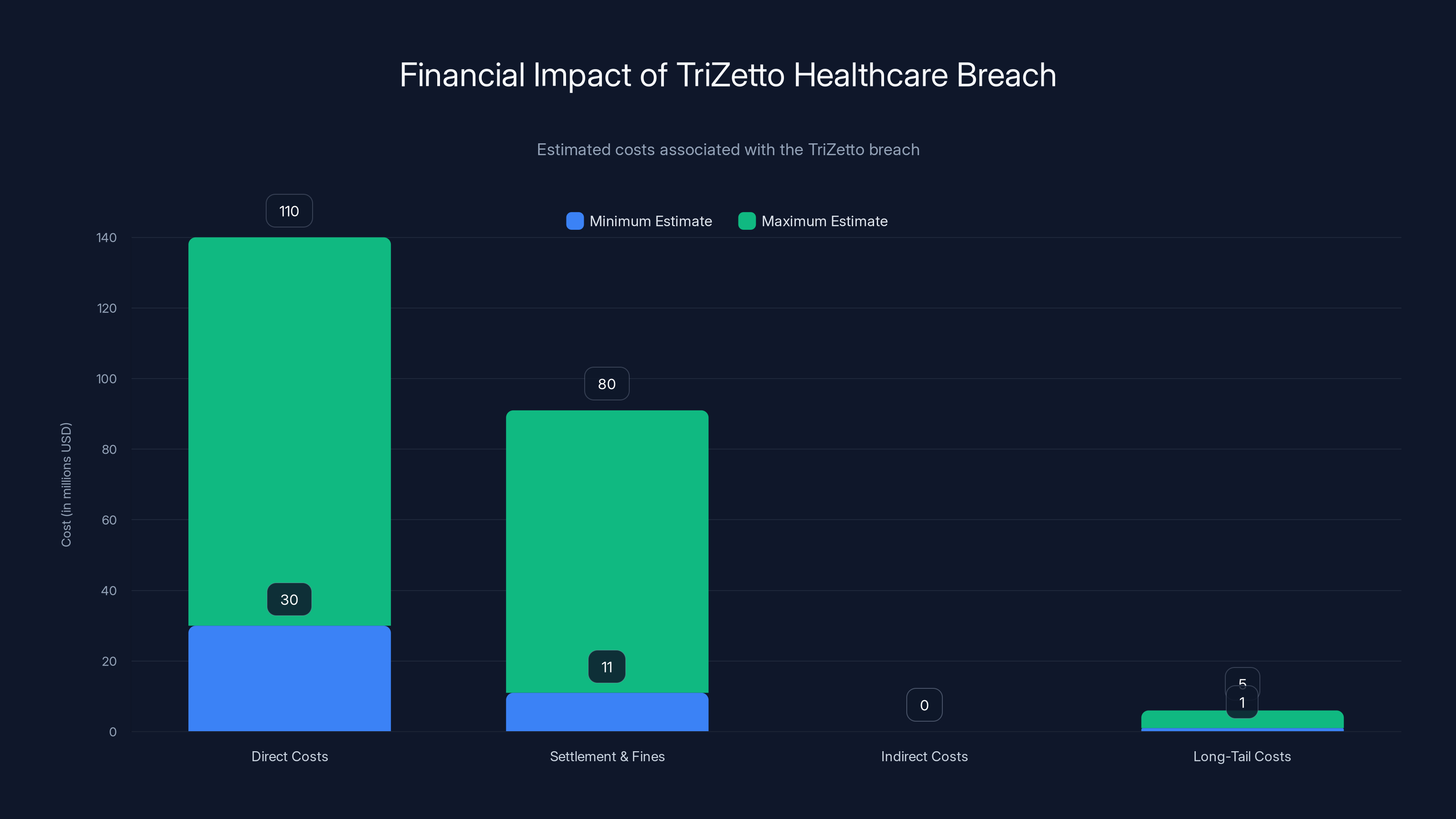
The TriZetto breach could cost between
The Scope of Impact: Which Organizations and Individuals Are Affected?
The breach affects customers of Tri Zetto Provider Solutions. TPS itself wasn't breached directly by its own negligence in a sense that they introduced a vulnerability in the customer's networks. But TPS infrastructure—the systems TPS owns and operates—was breached, and it contained aggregated data about patients of multiple healthcare organizations.
Confirmed affected organizations include:
Deschutes County Health Services (DCHS) in Oregon, which was the first to go public with breach notifications.
Best Care, a healthcare provider organization.
La Pine Community Health Center, another provider in Oregon.
But these three are just the ones that have publicly disclosed so far. The breach likely touches patients and members at dozens of other organizations that use TPS systems for claims processing and billing. Every time a covered individual visits an in-network provider or submits a claim, their demographic information flows through TPS systems.
The geographic distribution is nationwide. People in US states from California to Maine to Florida are likely affected. The organizations using TPS have different service areas, but collectively they reach millions of Americans.
The timeline of notifications has been slow. Many affected individuals may not even realize they're part of this breach yet. Organizations are still working through the complex process of identifying exactly which individuals need to be notified, writing notification letters, setting up credit monitoring services, and preparing for the inevitable lawsuits that follow.

Why Wasn't This Detected Sooner?
Let's talk about the elephant in the room: this breach went undetected for 11 months. That's not a security failure. That's an infrastructure-wide failure in how cybersecurity is being practiced at scale.
A few possibilities explain the lengthy dwell time:
Insufficient Logging and Monitoring: TPS systems may not have been logging data access and exfiltration attempts comprehensively. If you're not recording who accesses what data, you can't detect unusual patterns.
Insufficient Threat Detection Tools: Even with logs, you need tools and people who can analyze those logs in real-time. Small indicators of compromise (IOCs) like unusual data export volumes, access from unusual geographic locations, or escalated privilege usage need to be flagged automatically.
Segmentation Failures: Once attackers got into one system, they apparently had relatively easy lateral movement to access customer data aggregated across multiple client organizations. Better network segmentation might have contained the damage.
Resource Constraints: Healthcare IT teams are notoriously under-resourced. TPS might not have had enough security personnel to monitor threat alerts effectively, meaning alarms went off but nobody was available to investigate them.
Sophisticated Attackers: In fairness, we don't know who performed this attack. If it was a nation-state or sophisticated criminal organization, they might have specifically gone after detection systems, disabled logging, or covered their tracks in ways that made discovery more difficult.
The most likely explanation is a combination of all these factors. Cognizant is a massive company, TPS is a subsidiary product line, and it's entirely possible that security investment didn't match the critical nature of the infrastructure being protected.

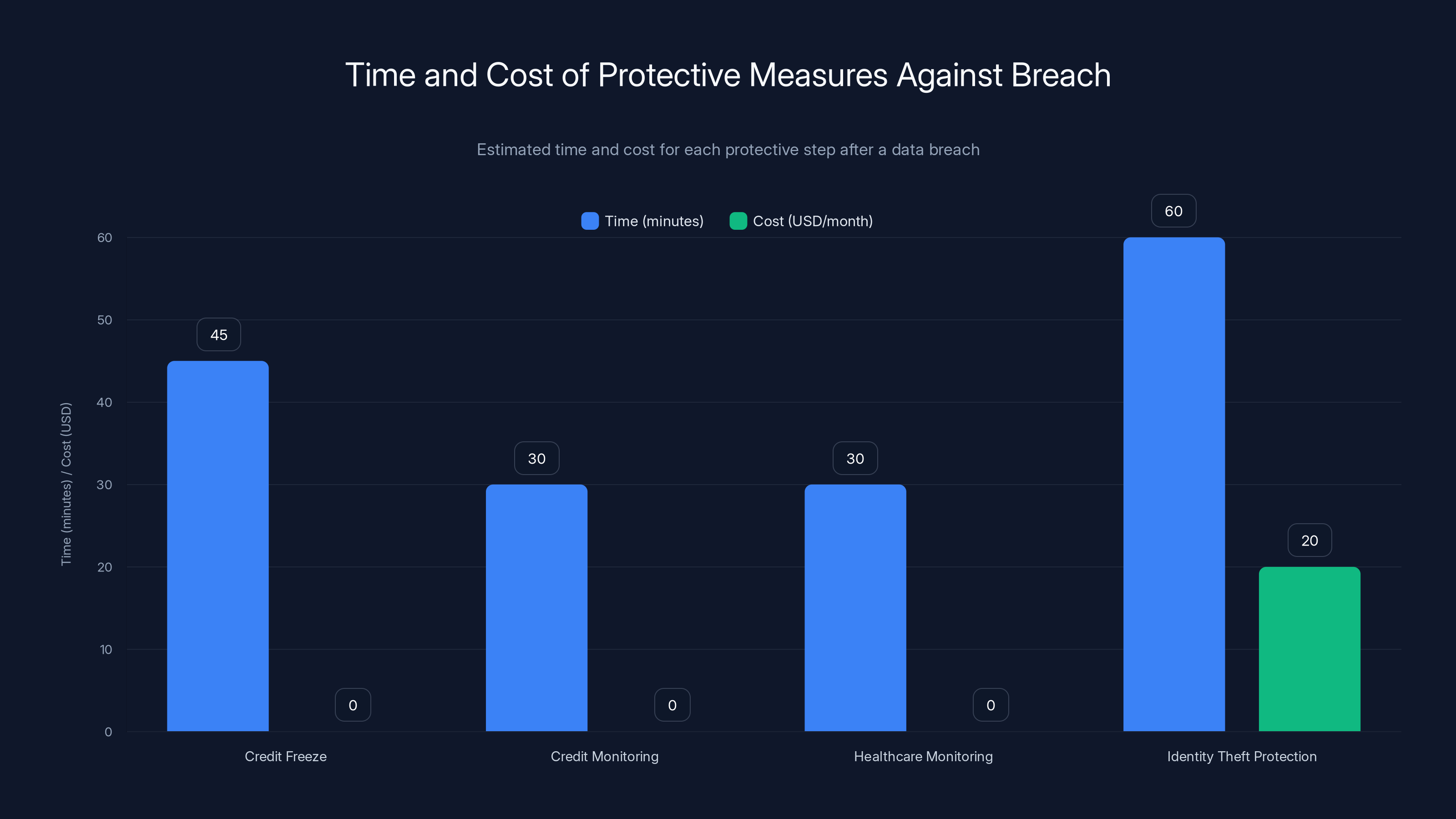
Estimated data shows that while credit freeze and monitoring are free, identity theft protection can cost $20/month but offers comprehensive protection.
The Immediate Consequences: Credit Monitoring, Lawsuits, and Regulatory Scrutiny
When a breach of this magnitude occurs, the consequences ripple outward immediately.
Affected Individuals Receiving Notification: Deschutes County Health Services has already begun sending breach notification letters. These letters include notifications about free credit monitoring services, typically provided for 2-3 years. Similar notifications are rolling out from other affected organizations.
Class-Action Lawsuits: Multiple class-action lawsuits have already been filed against Cognizant. These suits claim negligent security practices, failure to implement adequate safeguards, and failure to detect the breach in a timely manner. If history is any guide, these will settle for millions, though individual plaintiffs typically see payouts in the
Regulatory Investigations: State attorneys general, particularly in states with large affected populations, are likely to launch investigations. The Department of Health and Human Services Office for Civil Rights (OCR) will also be involved, as this involves covered entities under HIPAA. OCR can impose penalties ranging from
Reputational Damage: Healthcare organizations that relied on TPS are now facing questions from their patients about why they trusted a third party with sensitive data without more stringent security requirements. The damage to customer trust is immediate and long-term.
Insurance Claims: Cognizant and potentially the affected healthcare organizations will file cyber liability insurance claims. This will drive up insurance premiums for the entire healthcare tech industry.
How Attackers Might Use This Data: Real Threats
We keep hearing that the data "hasn't been abused in attacks yet" (as of the time the breach was disclosed), but that's not a guarantee going forward. Here's how criminals could weaponize 700,000 stolen healthcare records:
Medical Identity Fraud: This is the most direct threat. Using your insurance member ID and insurer name, criminals can:
- Call your healthcare provider pretending to be you and schedule expensive procedures
- Visit clinics or urgent care facilities, provide your insurance information, and receive treatments you never got
- Use your insurance to buy durable medical equipment (wheelchairs, CPAP machines, walkers) that they resell for cash
- Submit prescriptions in your name
- The damage per incident often exceeds $10,000, and victims may not discover it for months
Targeted Phishing and Social Engineering: Criminals now know:
- Your name
- Your health insurer
- Your member ID
- That you've used specific healthcare providers
They can send emails claiming to be your insurer ("Verify your account immediately") with perfect context because they know real details about your healthcare. Phishing emails that reference your actual insurer are vastly more effective at getting people to click malicious links or enter credentials.
Financial Identity Fraud: Your SSN combined with your name, address, and birth date is enough to:
- Apply for credit cards in your name
- Take out loans
- File fraudulent tax returns
- Open utility accounts
Darknet Sale of Data: Your complete identity profile (name, SSN, address, birth date, insurance details) has value on darknet markets. It might sell for

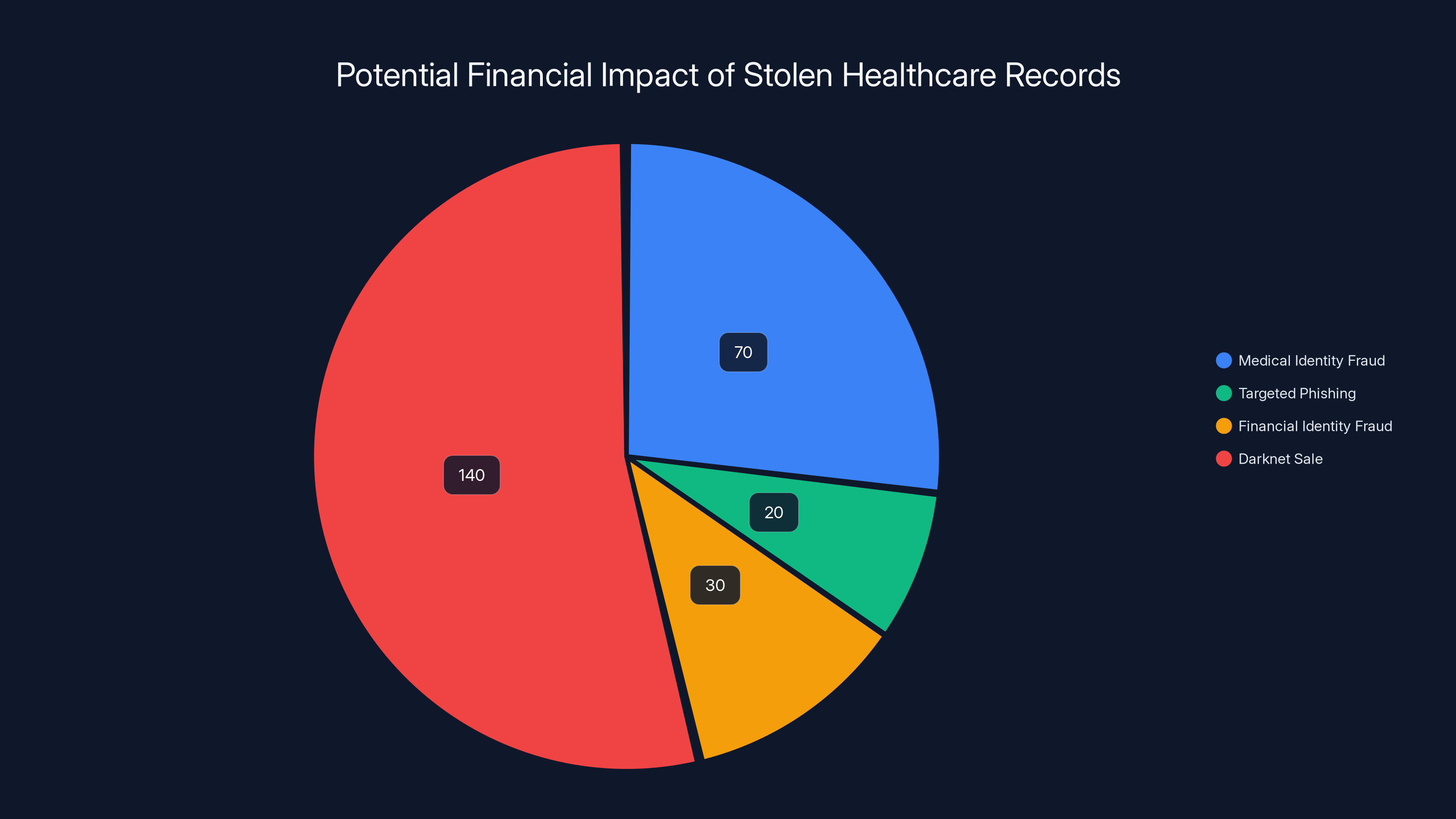
The sale of 700,000 stolen healthcare records could generate an estimated
Immediate Steps You Should Take If You're Affected
If you received a breach notification letter or if you suspect you're part of the TPS breach, here's what you should do right now:
1. Place a Credit Freeze: Contact the three major credit bureaus (Equifax, Experian, Trans Union) and request a credit freeze. This is free and blocks anyone from opening new credit accounts in your name without contacting you first. It takes about 15 minutes per bureau.
2. Monitor Your Credit Reports: Request your free annual credit reports from annualcreditreport.com and review them for unfamiliar accounts or inquiries. Check for:
- Accounts you didn't open
- Hard inquiries you don't recognize
- Incorrect personal information
3. Enroll in Credit Monitoring: The notification letters typically include free credit monitoring. Sign up. You'll get alerts when new accounts are opened or significant changes occur.
4. Monitor Your Healthcare Bills and Explanation of Benefits: Check every EOB you receive. Look for:
- Services you didn't receive
- Visits to providers you don't use
- Procedures you didn't have
- Unusual prescription activity
5. Consider an Identity Theft Protection Service: Services like Life Lock or myfico go beyond credit monitoring and include:
- Dark web monitoring (alerts if your SSN appears in compromised databases)
- Identity theft insurance
- Recovery assistance if fraud does occur
- Some plans include legal consultation
These services cost
6. Document Everything: Keep copies of all notification letters, credit monitoring enrollment confirmations, and communications with creditors or healthcare providers. You'll need this documentation if you later need to dispute fraudulent charges.
7. File a Police Report (if fraud occurs): If you discover fraudulent activity, file a report with your local police and request a report number. This helps when disputing charges with creditors.
The Regulatory and Legal Aftermath: What Comes Next
The Tri Zetto breach will have a long legal and regulatory tail that extends years into the future.
HIPAA Violation Implications: While HIPAA only applies to covered entities and business associates, the breach still triggers HIPAA regulations because the affected organizations that use TPS are HIPAA-covered entities. The Department of Health and Human Services Office for Civil Rights can impose penalties. Historical precedent suggests settlements in the range of
State Breach Notification Laws: All 50 states have breach notification laws with varying requirements. Cognizant and the affected healthcare organizations must comply with all of these. Some states (like California) require notification without unreasonable delay, and California's law includes statutory damages.
Class-Action Litigation: The lawsuits that have already been filed will likely settle for millions of dollars. The settlement funds typically pay:
- Attorneys' fees (30-40% of the settlement)
- Settlement administration costs (5-10%)
- Cy pres awards (where remaining funds go to related nonprofits)
- Individual claims paid to people who can prove they suffered damages
Historical patterns suggest settlements between
Reputational Impact on Cognizant: Cognizant faces long-term reputational damage. Healthcare organizations will now scrutinize their contracts with Cognizant and may begin migrating to competitors. Earnings calls will feature analyst questions about security practices. Customer retention becomes more difficult.
Industry-Wide Security Audits: After major breaches, the entire industry typically undergoes increased scrutiny. Insurance companies will demand better security measures from healthcare IT vendors. Customers will renegotiate contracts to include stricter security requirements and audit rights.

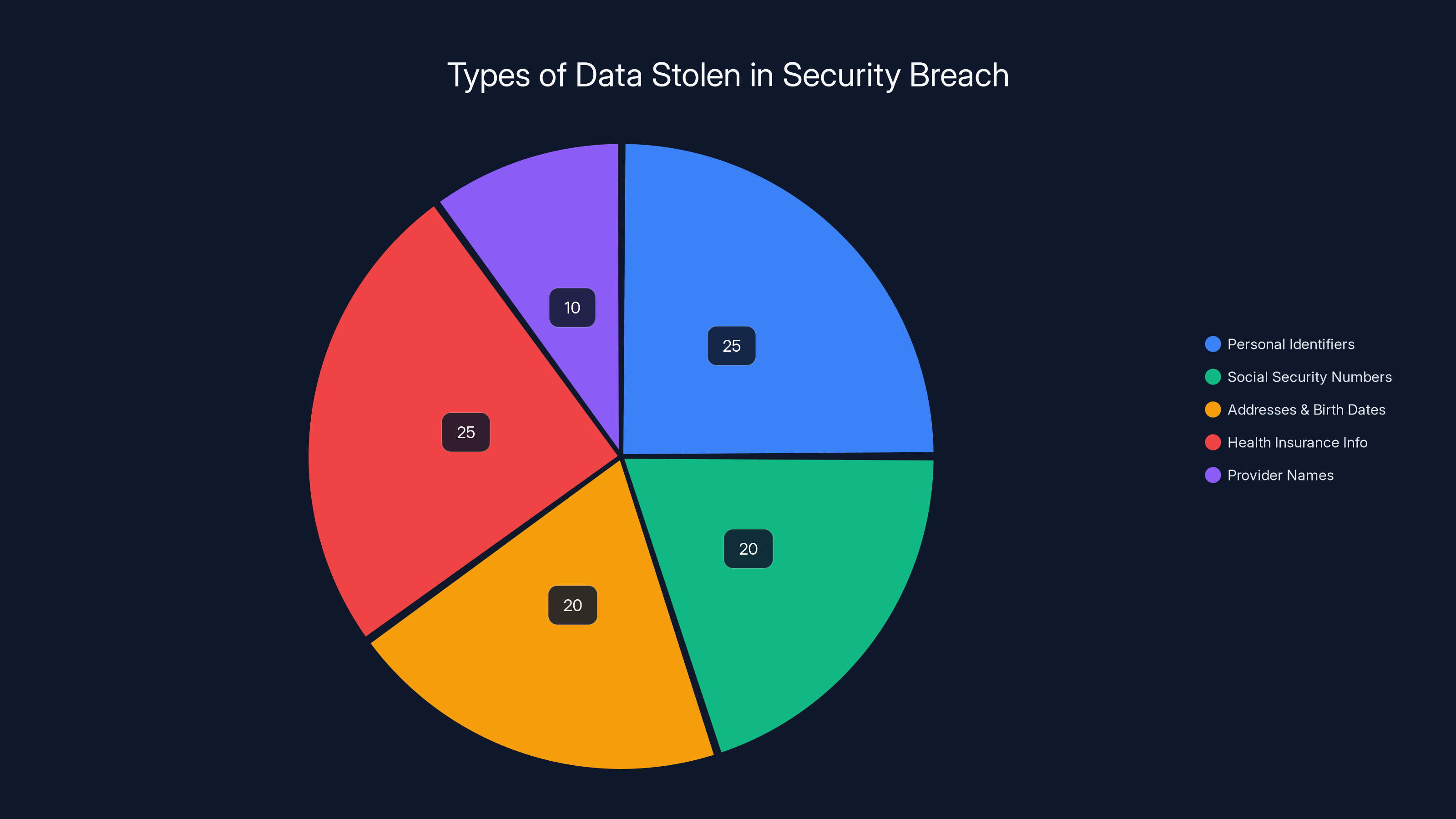
Estimated data distribution shows Personal Identifiers and Health Insurance Info as most commonly stolen, each comprising 25% of the breach. (Estimated data)
Lessons for Healthcare Organizations: How to Prevent This
If you run a healthcare organization or work in their IT department, the Tri Zetto breach is a masterclass in what not to do. Here's what the incident teaches us:
Implement Comprehensive Logging and Monitoring: Every database query that touches patient data should be logged. Every user action should be recorded. This needs to be centralized in a SIEM (Security Information and Event Management) system that analyzes logs in real-time for anomalies. The 11-month dwell time was only possible because monitoring was inadequate.
Segment Your Network: Attackers should not be able to move freely from a compromised system in one area of the network to patient data in another area. Network segmentation and zero-trust architecture would have limited the damage.
Require Multi-Factor Authentication Everywhere: The attackers likely obtained credentials through phishing, password reuse, or credential stuffing. MFA would have stopped them cold even with valid usernames and passwords.
Audit Third-Party Access: Healthcare organizations should audit all the third parties who have access to their patient data. What access do vendors like Tri Zetto actually need? Can that access be limited to specific data sets, specific times, or specific geographic locations?
Implement Data Minimization: Organizations should minimize how much patient data they send to third parties. Do they really need the full SSN? Can they use a hash of the SSN instead? The less sensitive data you send to third parties, the less damage a breach of that third party can cause.
Regular Penetration Testing and Red Team Exercises: Organizations should hire external security firms to attempt to break in, just like attackers would. This is how you find vulnerabilities before criminals do.
Incident Response Planning: Healthcare organizations should have detailed incident response plans and practice them regularly. Ideally, finding unauthorized access should trigger immediate containment steps within hours, not months.
What Security Experts Are Saying
The cybersecurity community's reaction to the Tri Zetto breach has been one of dismay mixed with a sense of inevitability. Large healthcare data breaches have become so common that security experts often describe the healthcare industry as being in a perpetual state of compromise.
Security researchers who have examined the available details note several concerning patterns:
1. Third-Party Risk is Systemic: The breach demonstrates that when you rely on third parties to handle sensitive data, you're essentially trusting that third party's security posture. If they fail, you fail. Many healthcare organizations don't have adequate contracts requiring third-party security audits or incident response requirements.
2. Detection Technology Failures: The 11-month dwell time suggests that Tri Zetto's security operations weren't effective. This could be due to tool limitations, staffing shortages, or both. Many organizations struggle to hire sufficient security talent, leaving them unable to respond to threats even when detection systems alert them.
3. Budget Constraints in Healthcare IT: Healthcare organizations often lack the budget to implement best-practice security architecture. They're using legacy systems, patching is delayed, and security tools are considered overhead rather than essential infrastructure.
4. Regulatory Compliance Isn't Enough: HIPAA compliance, while necessary, doesn't prevent breaches. An organization can be HIPAA-compliant and still get breached by sophisticated attackers. Compliance is a floor, not a ceiling.
The consensus among security experts is that the Tri Zetto breach, while large, was likely preventable with adequate investment in security infrastructure, threat detection, and incident response.

The Broader Picture: Is Your Data Safe with Healthcare Vendors?
The Tri Zetto breach raises a fundamental question: if your healthcare data goes to third parties for processing, is it really safe?
The honest answer is: not always. Here's why:
Concentration of Data: Companies like Tri Zetto handle data for hundreds of healthcare organizations. That concentration makes them attractive targets for cybercriminals and nation-states alike. One successful breach affects millions of people.
Resource Constraints: Many healthcare tech vendors are growing companies trying to balance innovation with security. Security investment often lags behind product development. They're profitable because they've kept security costs low, not because security is actually robust.
Interconnected Systems: Modern healthcare relies on data flowing between multiple systems: electronic health records, billing systems, pharmacy systems, lab systems, insurance systems. Each connection is a potential attack vector.
Attractive to Attackers: Healthcare data is worth more on the darknet than financial data. Attackers can use it for medical fraud, insurance fraud, and identity theft. The ROI on healthcare breaches is better than on retail breaches.
That doesn't mean you shouldn't use healthcare vendors or trust healthcare organizations. It means you should be alert, monitor your healthcare bills and insurance activity, and understand that no organization is perfectly secure. The best you can hope for is that organizations are doing a reasonable job of security and will detect breaches quickly when they happen.
Insurance and Financial Impact: The Actual Costs
Large healthcare breaches have enormous financial costs that extend far beyond the direct harm to individuals. The total cost of the Tri Zetto breach will likely exceed $500 million when you factor in everything:
Direct Costs:
- Credit monitoring services for 700,000 people for 2-3 years: $15-30 million
- Notification costs (letters, call centers, advertising): $5-10 million
- Forensic investigation and remediation: $10-20 million
- Legal fees: $20-50 million
Settlement and Regulatory Fines:
- Class-action settlement: $5-50 million (historically)
- HIPAA penalties from HHS OCR: $1-10 million
- State attorney general settlements: $1-20 million
Indirect Costs:
- Loss of customer trust and revenue
- Increased cyber insurance premiums
- Cost of implementing better security controls
- Executive time spent managing the breach
- Productivity loss among IT staff dealing with investigations
Long-Tail Costs:
- Identity theft for affected individuals (estimated 2-5% will experience fraud): $1-5 million in damages
- Credit freezes and monitoring lasting years after
- Reputation damage lasting years
For Cognizant, as a large company, these costs are material but manageable. For smaller healthcare organizations, a similar breach could be existential. This is why security investment matters, and why cutting corners on security ultimately costs far more than proper investment would have.

Moving Forward: What Changes Should Happen
The Tri Zetto breach is a wakeup call for the healthcare industry. Several changes should happen as a result:
1. Better Vendor Management: Healthcare organizations should require detailed security assessments before trusting vendors with patient data. They should include security audit rights in contracts and require vendors to maintain cyber insurance.
2. Industry Standards for Third-Party Security: The healthcare industry should develop clearer standards for third-party vendor security. These could be enforced through regulatory requirements or industry certifications.
3. Security Budget Increases: Healthcare IT budgets for security should increase significantly. If organizations are spending less than 15-20% of their IT budget on security, they're under-investing.
4. Better Threat Detection Tools and Talent: Organizations need investment in SIEM systems, threat hunting, and security personnel. Logging and monitoring should be ubiquitous, not optional.
5. Data Minimization Requirements: Vendors should only have access to the specific data they need to perform their function. Sending entire patient databases to third parties should be questioned and limited.
6. Regulatory Enforcement: HHS OCR should impose meaningful penalties for inadequate security. Right now, penalties are often treated as a cost of doing business rather than a genuine deterrent.
7. Public Transparency: Organizations should be required to disclose breach dwell times and detection mechanisms. The 11-month gap in this breach would have been harder to hide under more stringent disclosure requirements.
FAQ
What is the Tri Zetto Provider Solutions breach?
The Tri Zetto Provider Solutions (TPS) data breach is a cybersecurity incident in which attackers gained unauthorized access to systems owned by Tri Zetto, a healthcare technology company that handles claims processing and revenue cycle management for hundreds of healthcare organizations. Attackers accessed the systems in November 2024 but weren't discovered until October 2025, meaning they had nearly 11 months of undetected access. The breach exposed personal and health information for over 700,000 individuals.
How did the Tri Zetto breach happen?
The exact mechanism of the initial compromise hasn't been publicly disclosed, but attackers gained access to TPS systems in November 2024 and maintained that access for approximately 11 months. During this time, they were able to exfiltrate sensitive personal and health data from multiple customer organizations. The lengthy dwell time suggests inadequate network monitoring, logging, or threat detection systems that would have identified unusual activity much sooner. The specific attack vector (phishing, credential stuffing, zero-day vulnerability, etc.) hasn't been confirmed in public disclosures.
What information was exposed in the breach?
The exposed data includes names, addresses, birth dates, Social Security numbers (SSNs), health insurance carrier names, health insurance member numbers, and healthcare provider names for over 700,000 individuals. Importantly, medical diagnoses, treatment records, and payment card information were NOT included in the breach. However, the exposed personal and insurance information is still sufficient for medical identity fraud, insurance fraud, and targeted phishing attacks.
Which organizations and people are affected by the TPS breach?
People affected by the breach are those who received healthcare from organizations that use Tri Zetto Provider Solutions for billing and claims processing. Confirmed affected organizations include Deschutes County Health Services in Oregon, Best Care, and La Pine Community Health Center. However, TPS serves hundreds of healthcare organizations nationwide, so many more people are likely affected than have been officially notified so far. If you received healthcare in 2024 or early 2025, there's a possibility your data was compromised.
How can I tell if I'm affected by the Tri Zetto breach?
If you're affected, you'll receive a breach notification letter in the mail from the healthcare organization or insurer whose patient you are. These letters typically include:
- Confirmation that your data was compromised
- Details about what information was exposed
- Information about free credit monitoring services
- Steps you should take to protect yourself
- Contact information for questions
If you haven't received a letter but think you might be affected, contact your healthcare provider or insurance company directly using the phone number on your insurance card (not from any email link).
What should I do if I'm affected by the breach?
You should take several immediate actions: (1) Place a credit freeze with the three major credit bureaus (Equifax, Experian, Trans Union) to prevent new accounts from being opened in your name, (2) Enroll in the free credit monitoring service provided in the notification letter, (3) Monitor your credit reports regularly for unauthorized accounts or inquiries, (4) Watch your healthcare statements and explanation of benefits for services you didn't receive, (5) Consider additional identity theft protection services if you want to go beyond the basics, and (6) Keep copies of all notification letters and communications for your records.
Am I at risk for medical identity fraud?
Yes, medical identity fraud is a significant risk with this breach. Criminals can use your insurance member ID and insurer name to receive healthcare services in your name, purchase durable medical equipment that they resell for cash, file fraudulent insurance claims, or obtain prescription drugs. Medical identity fraud victims typically experience damages exceeding $10,000 per incident and may not discover the fraud for several months or longer. Vigilant monitoring of your healthcare statements and insurance activity is essential.
What lawsuits have been filed related to the breach?
Multiple class-action lawsuits have been filed against Cognizant (TPS's parent company) alleging negligent security practices, failure to implement adequate safeguards, and failure to detect the breach in a timely manner. These lawsuits typically claim that Cognizant failed to implement reasonable security measures that would have prevented the breach or detected it much sooner than 11 months. Class-action settlements in healthcare breaches of similar magnitude have historically ranged from
What are the regulatory consequences of the Tri Zetto breach?
The breach triggers investigations by multiple regulatory bodies, including the Department of Health and Human Services Office for Civil Rights (OCR), which enforces HIPAA, and various state attorneys general. HHS OCR can impose HIPAA penalties ranging from
How long will I need to monitor my credit and identity?
Most organizations provide two to three years of free credit monitoring after a breach. However, identity theft risks can extend longer, particularly if your SSN and other personal identifying information are sold on darknet markets. Most security experts recommend monitoring your credit for at least seven years and taking advantage of the free monitoring period provided, then continuing with at least annual credit report reviews beyond that period. If fraud does occur, the monitoring period may need to extend until you're confident that all fraudulent accounts have been resolved.
What changes should healthcare organizations make to prevent similar breaches?
Healthcare organizations should implement comprehensive logging and monitoring of all database access, segment their networks to limit lateral movement by attackers, require multi-factor authentication for all access to sensitive systems, audit and limit third-party vendor access to only what's necessary, implement data minimization practices to reduce sensitive data exposure, conduct regular penetration testing and red-team exercises, and develop detailed incident response plans with practice drills. Organizations should also require vendors to maintain cyber insurance and provide security audit rights in their contracts.

Conclusion: The Ongoing Reality of Healthcare Data Breaches
The Tri Zetto Provider Solutions breach affecting 700,000+ people is significant, but it's also, tragically, not surprising anymore. Major healthcare breaches have become almost routine in American healthcare. What makes the Tri Zetto breach noteworthy is its massive scale and the astonishing 11-month dwell time that went undetected.
This breach is a stark reminder that healthcare data security remains inadequate across much of the industry. When a company handling critical healthcare infrastructure can be compromised for almost a full year without detection, it's clear that security investment, threat detection capabilities, and incident response procedures are falling short of what they should be.
For individuals affected by this breach, the practical advice is straightforward: enroll in credit monitoring, place a credit freeze, monitor your healthcare bills and insurance activity, and consider additional identity theft protection services. The risk of fraud is real, but it's also manageable with vigilance.
For healthcare organizations and vendors, the lesson should be equally clear: security investment isn't optional, threat detection isn't a luxury, and third-party vendor security isn't something to cut corners on. The Tri Zetto breach will ultimately cost hundreds of millions of dollars in legal settlements, regulatory fines, and remediation efforts. That cost would look trivial compared to the investment that would have prevented it.
The healthcare industry needs to fundamentally change how it approaches security. It needs to treat security as infrastructure rather than overhead, allocate appropriate budgets, hire sufficient talent, and implement controls that would catch breaches in days rather than months. Until that happens, more breaches like Tri Zetto are inevitable, and millions more Americans will find their personal health information in the hands of criminals.
The good news is that prevention is possible. The bad news is that it requires commitment and resources that many organizations are still not willing to invest. For now, affected individuals should assume their data is compromised and take appropriate protective measures. That's not paranoia. That's just being realistic about the current state of healthcare security.
Key Takeaways
- TriZetto Provider Solutions breach affected 700,000+ people with 11-month undetected dwell time from November 2024 to October 2025
- Exposed data includes names, SSNs, addresses, birth dates, and health insurance information sufficient for medical identity fraud
- Multiple class-action lawsuits filed against Cognizant with potential settlements exceeding $50 million plus regulatory penalties
- Affected individuals should immediately place credit freezes, enroll in monitoring, and monitor healthcare statements for fraudulent activity
- Healthcare organizations must implement comprehensive logging, threat detection, network segmentation, and multi-factor authentication to prevent similar breaches
Related Articles
- Major Cybersecurity Threats & Digital Crime This Week [2025]
- AI Toy Security Breaches Expose Children's Private Chats [2025]
- Shadow AI in the Workplace: How Unsanctioned Tools Threaten Your Business [2025]
- Bumble & Match Cyberattack: What Happened & How to Protect Your Data [2025]
- Panera Bread Data Breach: 14 Million Records Exposed [2025]
- Microsoft's Example.com Routing Anomaly: What Went Wrong [2025]
![TriZetto Provider Solutions Breach: 700K+ Affected [2025]](https://tryrunable.com/blog/trizetto-provider-solutions-breach-700k-affected-2025/image-1-1770043021141.jpg)



