Introduction: When the Darknet's Last Safe Haven Disappears
Imagine the internet has a hidden layer where illegal goods, stolen data, and digital weapons trade hands openly. For years, there was one place where ransomware dealers, hackers, and cybercriminals gathered without fear. That place was called RAMP.
On a Wednesday in January 2026, that changed.
The FBI took over RAMP's servers. Both its dark web and surface web addresses redirected to a banner reading "The Federal Bureau of Investigation has seized RAMP." The seizure notification carried the seals of the Justice Department and the FBI's Computer Crime and Intellectual Property Section. No arrests were announced. No dramatic press conference happened. But the message was clear: law enforcement had finally dismantled one of the most persistent, organized, and brazen criminal forums on the internet, as reported by The Register.
This wasn't just another darknet takedown. RAMP had survived longer than almost every other major cybercrime marketplace. It had weathered increased government scrutiny, survived competitor shutdowns, and maintained operations while law enforcement agencies worldwide escalated their targeting of ransomware groups. The forum's administrator even publicly stated the site earned roughly $250,000 annually, a staggering admission that underscored RAMP's legitimacy within criminal circles.
But what made RAMP's seizure so significant? Why did this single forum matter more than dozens of other illegal marketplaces operating on the darknet? The answer reveals something fundamental about how ransomware works, how law enforcement adapts, and what cybersecurity looks like in an era when digital extortion has become a trillion-dollar criminal enterprise.
This article examines RAMP's rise, its role in the ransomware ecosystem, the law enforcement operation that brought it down, and what its collapse means for cybercrime, corporate security, and government cybersecurity strategy in 2025 and beyond.
TL; DR
- RAMP was the internet's largest organized gathering place for ransomware operators, with over 14,000 registered users and a marketplace specifically designed to help criminals execute attacks
- The FBI's seizure represents a major escalation in law enforcement's ability to target criminal infrastructure, using coordinated efforts with international partners, according to BleepingComputer.
- Ransomware groups are adapting by migrating to smaller, more private forums, making detection and enforcement increasingly difficult
- The takeover may provide law enforcement with unprecedented access to criminal networks, though the full impact remains uncertain
- Bottom line: RAMP's collapse signals that no criminal platform is truly untouchable, but it also proves that ransomware's underlying economics remain too profitable to stop entirely
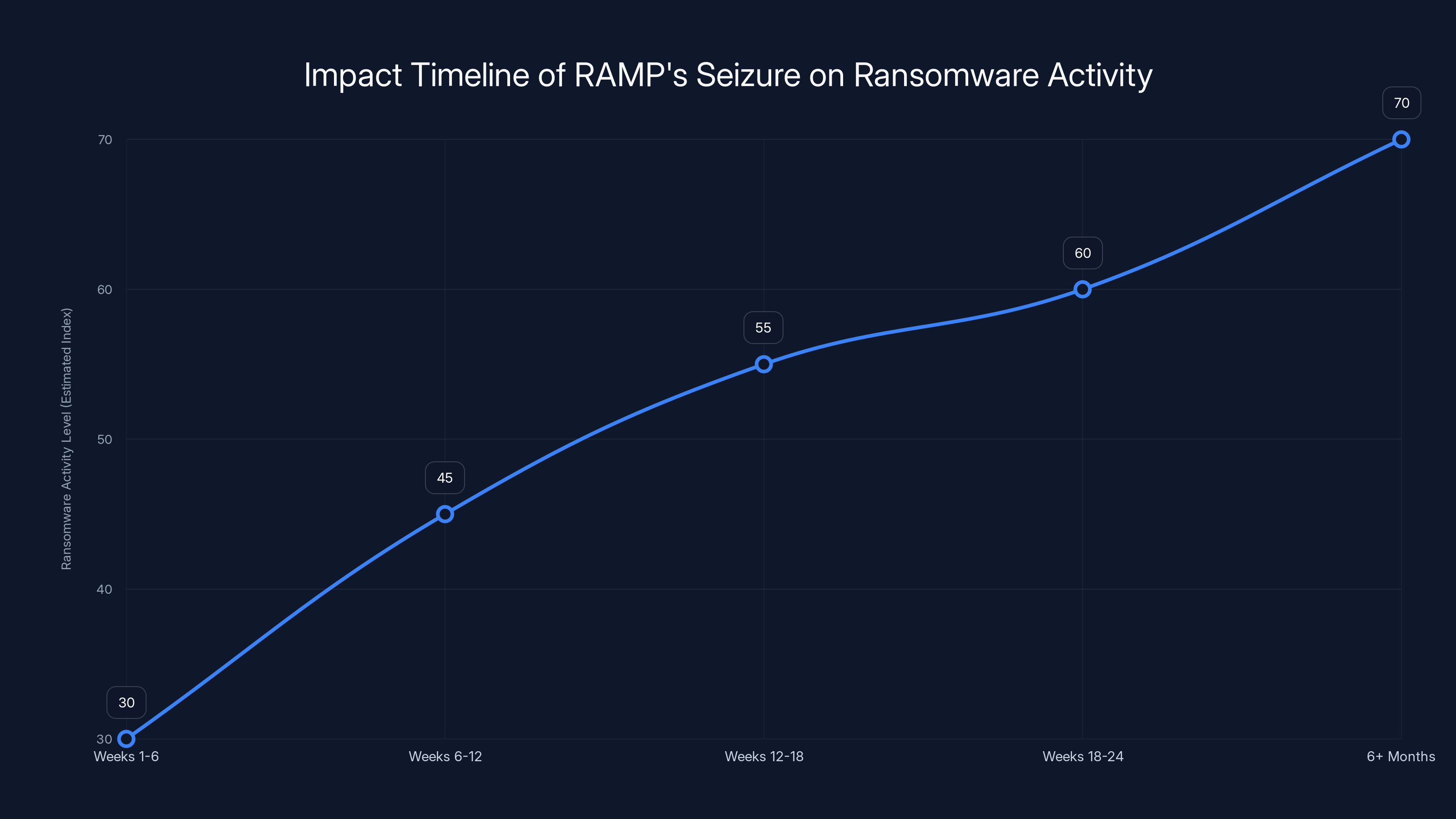
Ransomware activity is expected to initially decrease post-RAMP's seizure, but will gradually increase as criminal groups reorganize and adapt. Estimated data.
What Was RAMP and Why Did It Matter?
RAMP wasn't created yesterday. The platform launched in 2012, originally operating under different names and with different moderators. By 2021, it had rebranded into what most cybersecurity professionals recognized as RAMP—the acronym standing for a Russian-language marketplace that billed itself as "the only place ransomware allowed."
That wasn't marketing exaggeration. It was literally true.
While other darknet forums banned ransomware discussions to avoid attracting law enforcement attention, RAMP made a calculated business decision: we'll take those users, and we'll build our entire platform around serving them. The strategy worked. Cybercriminals flocked to RAMP because they could openly advertise ransomware-as-a-service offerings, share attack techniques, negotiate with victims' families, and trade stolen data without moderators deleting posts or shutting down discussions.
The forum served multiple language communities. Russian speakers dominated, but Chinese and English-language communities also maintained active presences. Registration required strict vetting—applicants had to demonstrate credibility within hacker circles, or they could simply pay $500 for anonymity. This two-tier system kept out law enforcement infiltrators and script kiddies while maintaining a critical mass of serious criminals who would actually use the platform.
By the time the FBI moved against it, RAMP had become something almost institutional. The platform featured dedicated discussion groups organized by topic, comprehensive tutorials on executing cyberattacks, and a working marketplace where threat actors could buy malware, data exfiltration tools, vulnerability information, and operational security advice. Some estimates suggested the forum had accumulated over 14,000 registered users over its operational lifetime.
But RAMP's significance went beyond mere size. The platform represented something psychological and structural. For years, cybersecurity professionals and law enforcement agencies had been slowly dismantling the infrastructure that supported ransomware. Earlier darknet forums like Alpha Bay, Silk Road, and even XSS (the marketplace that immediately preceded RAMP's dominance) had been seized or their operators arrested. Each takedown created a temporary disruption in criminal networks, but the business model was too profitable to stay dead for long.
RAMP filled that vacuum completely. As other forums fell, RAMP didn't just survive—it thrived. It became the default meeting place, the established institution, the place where ransomware kingpins actually did business instead of just talking about it. That durability made it dangerous from a law enforcement perspective. RAMP wasn't an experimental darknet project that might disappear in six months. It was infrastructure. Permanent infrastructure.
That's what made taking it down so strategically important.
The Infrastructure of Ransomware: How RAMP Enabled Global Crime
Ransomware works because of specialization. A successful extortion attack requires multiple distinct skills: initial access (breaking into networks), lateral movement (spreading through systems), data exfiltration (stealing files before encryption), negotiation (talking to victims), and money laundering (converting stolen cryptocurrency into usable funds).
No single criminal possesses all these skills. So they outsource.
RAMP solved that outsourcing problem at scale. The platform functioned as a marketplace where specialists could connect. Need a network access broker to provide credentials for a specific corporate network? RAMP had listings. Want to buy pre-made ransomware that you could customize? Available. Need consultation on negotiation strategy with a Fortune 500 company's IT department? Experienced negotiators advertised their services.
This ecosystem amplified ransomware's destructive power dramatically. Before platforms like RAMP existed, ransomware was largely opportunistic. Criminals would use mass scanning and brute-force attacks to compromise targets semi-randomly, encrypt files, and hope victims would pay. Most wouldn't.
But RAMP enabled precision targeting. A criminal with $50,000 to invest could now purchase network access to a specific healthcare system or manufacturing company, hire specialists to extract valuable data, and execute a coordinated attack designed to maximize pressure on that specific victim. The economics improved for attackers. Success rates rose. Ransom amounts skyrocketed.
Consider the operational timeline of a sophisticated ransomware attack that became common after platforms like RAMP achieved dominance:
-
Initial Access (Day 1-7): Attack group purchases pre-compromised network credentials from an access broker. Cost:
50,000 depending on the target's size and value. The broker found these credentials through RAMP listings. -
Reconnaissance (Day 8-14): Attackers map the network, identify valuable data, and locate backup systems. They might purchase vulnerability information for specific software from RAMP vendors. Cost:
10,000. -
Lateral Movement (Day 15-21): Using purchased exploit code and operational guidance found in RAMP tutorials, attackers move throughout the network. They might pay RAMP consultants for real-time advice. Cost:
20,000. -
Data Exfiltration (Day 22-28): Attackers copy gigabytes of sensitive files. They consult RAMP's data valuation experts about what they've stolen. Cost: varies.
-
Encryption and Negotiation (Day 29): Ransomware deploys. Attackers contact victims using templates and negotiation advice sourced from RAMP. Cost: already sunk.
-
Money Laundering (Day 30+): Victims pay (often $1-10 million). Attackers convert cryptocurrency using money laundering services advertised on RAMP. Final cost to victim: devastating.
Rolled together, RAMP transformed ransomware from a crude extortion technique into a sophisticated, specialized, and devastatingly profitable criminal industry. The platform's existence directly enabled the billion-dollar ransomware epidemic of 2018-2025.
That infrastructure complexity is why RAMP's seizure matters so much more than takedowns of smaller, less organized forums. Shutting down a darknet marketplace with 2,000 users causes minor disruption. Shutting down a specialized, well-established platform with 14,000+ users that provides integrated services disrupts the entire criminal supply chain.
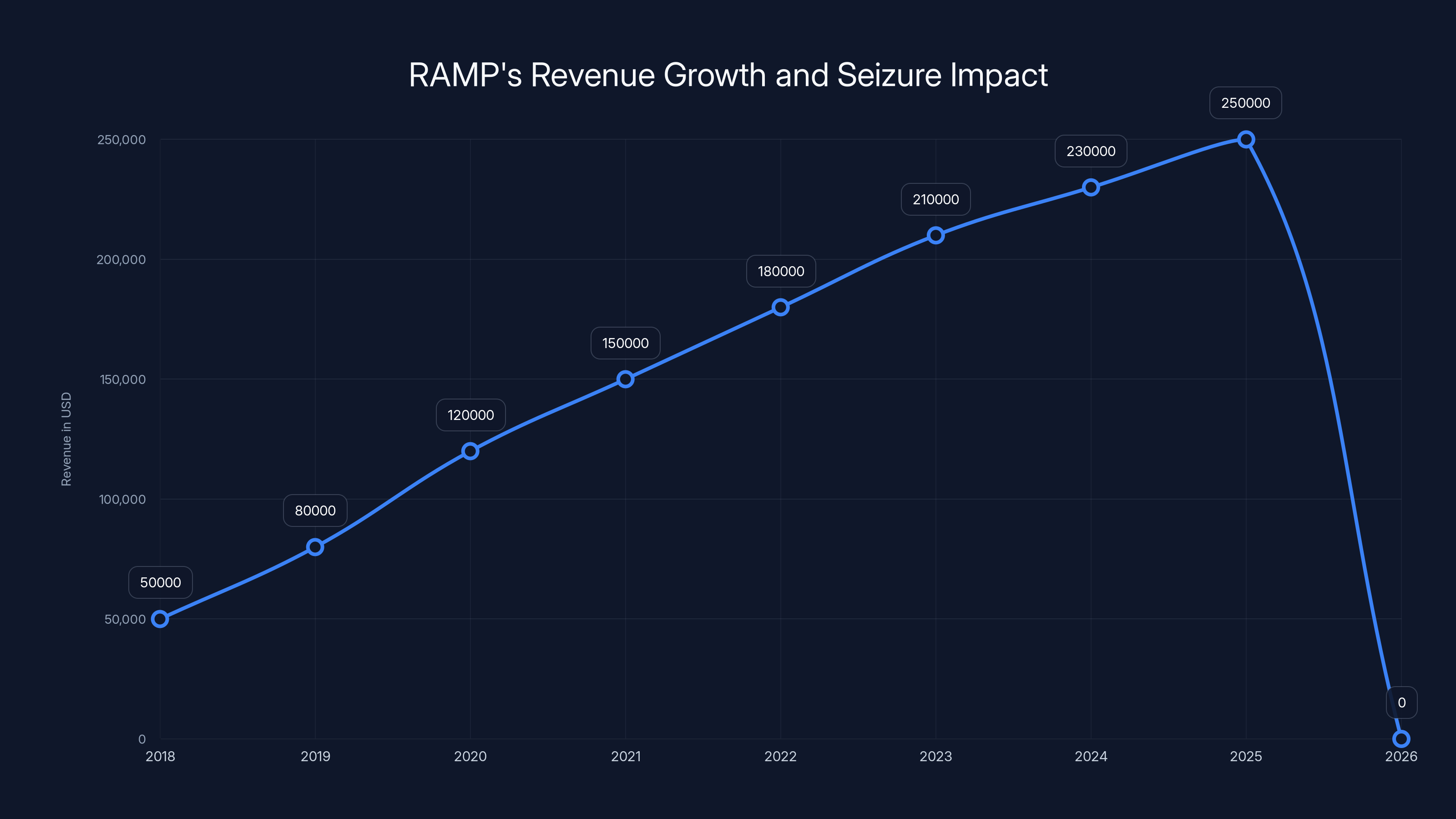
RAMP's revenue grew steadily from 2018 to 2025, peaking at $250,000 annually before its seizure in 2026, highlighting its dominance in the darknet market. Estimated data.
RAMP's Rise: From Obscurity to Dominance
RAMP didn't start as a ransomware forum. In 2012, when it launched, ransomware wasn't the dominant threat it would become. The malware ecosystem was more scattered, less organized. But as ransomware became more profitable throughout the 2010s, RAMP's leadership made strategic decisions that positioned it to capture market share.
The first critical decision: accept ransomware discussions when other forums banned them.
Most established darknet forums have moderation policies that explicitly prohibit ransomware content. Forum administrators adopted these policies for practical reasons: ransomware attracts law enforcement attention, generates media coverage, and can result in seizures that affect all users. So reputable marketplace administrators banned ransomware discussions.
Ramp took the opposite approach. The leadership recognized that ransomware was becoming increasingly profitable and that banned criminals needed a place to organize. By positioning RAMP as "the only place ransomware allowed," the administrators created a refuge for the largest and fastest-growing segment of the cybercriminal economy.
The strategy proved correct. As traditional ransomware marketplaces and forums either shut down voluntarily or were seized by law enforcement, RAMP's user base grew. Criminals who would have used other platforms migrated to RAMP because it was specialized, established, and explicitly welcoming.
By 2020-2021, RAMP had achieved something almost unprecedented in darknet marketplace history: legitimacy. Not legal legitimacy, obviously, but legitimacy within criminal circles. Threat actors trusted the platform, moderators, and the infrastructure. New ransomware groups didn't struggle to find information about how to launch attacks. They could consult tutorials on RAMP. They could purchase tools. They could network with other operators.
The 2021 rebranding solidified this position. By changing names and refreshing the platform's appearance, RAMP's administrators signaled commitment to long-term operations. New platforms often get seized within months or years. The fact that RAMP survived its rebranding and continued growing suggested serious operational security and law enforcement evasion capabilities.
Looking at the timeline of major forum takedowns provides context:
- 2015: Silk Road 2.0 shut down, founder arrested
- 2017: Alpha Bay seized by FBI and DEA
- 2019: Wall Street Market shut down
- 2020: Dream Market voluntary closure
- 2020: Hydra expanded (though it was more pure narcotics-focused)
- 2021: RAMP rebrand and expansion
- 2024: XSS leader arrested by Europol; forum users migrate
- 2026: FBI seizes RAMP
Ramp occupied the gap in the market. When competitors fell, criminals needed somewhere to go. RAMP was that somewhere.
The Administrator's Confession: RAMP's Own Admission of Success
One of the most revealing moments in RAMP's history came in 2024 when the forum's chief administrator made a public statement about the platform's annual revenue. The figure: approximately $250,000 per year.
That number deserves scrutiny because it reveals something profound about how criminal platforms actually operate and how different they are from stereotypes.
First, the number itself.
Why would a criminal administrator publicly state these numbers? Conventional thinking suggests criminals operate in absolute secrecy. But that's not how mature criminal organizations actually work. Criminal organizations function similarly to legitimate businesses in many ways. They have reputations to maintain, need to attract quality members, and benefit from transparency about operations and profitability.
By stating these numbers publicly, the RAMP administrator was essentially making a business pitch: "Look, this platform is profitable, stable, and will continue operating. Join, invest, participate." It's the criminal equivalent of publishing financial statements.
The fact that the administrator felt comfortable making this statement also reveals something about RAMP's perceived durability. They weren't worried about law enforcement learning about the forum's finances. They already knew law enforcement knew about RAMP. The FBI, Europol, and every major cybersecurity agency had been monitoring RAMP for years. The money laundering information, the user database, the transaction histories—all of it was known to exist.
What the administrator misjudged was law enforcement's timeline. They may have believed they could operate indefinitely through operational security alone. They may have thought that as long as they didn't get too aggressive with attacks against US critical infrastructure, the government wouldn't prioritize taking them down. Or they may have simply accepted the risk as part of doing business.
The seizure proved that miscalculation.

The Precedent: Learning from XSS, Alpha Bay, and Other Fallen Platforms
Understanding RAMP's seizure requires understanding what happened to its predecessors. The darknet marketplace and forum ecosystem has experienced repeated cycles of creation, dominance, and law enforcement takedown.
XSS (also known as XSSForum) provides the most recent and relevant comparison. XSS was one of the last truly major forums dedicated to cybercrime discussions and marketplace activities. Like RAMP, it featured discussion groups, tutorials, and a marketplace for malware, exploit code, and services.
In late 2024, Europol announced that it had worked with international partners to dismantle XSS. More importantly, they arrested the forum's leader. That action had direct consequences for RAMP: XSS users migrated to RAMP because it was the largest remaining platform that offered similar functionality.
Before XSS, the pattern was similar. Alpha Bay, one of the largest darknet marketplaces ever created, operated for approximately four years (2014-2017) before the FBI, DEA, and international partners executed a coordinated seizure. Alpha Bay's takedown involved actual arrests of operators, not just seizure of infrastructure. The impact was significant—criminals lost access to years of transaction history, reputation ratings, and marketplace infrastructure.
But within months, new platforms emerged to fill the void. Wall Street Market, Hydra, and others launched. Some were independent creations. Others were directly founded by operators who had been using Alpha Bay and wanted to recreate its functionality.
The pattern reveals something important about the criminal marketplace ecosystem: it's highly resilient. Platforms matter less than the underlying demand. As long as criminals need to buy and sell services, and as long as they find value in organized gathering places, new platforms will emerge.
RAMP's seizure will follow the same pattern. Already, smaller forums are positioning themselves as RAMP replacements. Some have posted statements like "RAMP is gone but we're still here." Criminal operators are consolidating into encrypted chat groups on platforms like Telegram, which are harder to take down than centralized forums.
The difference is efficiency. RAMP provided centralized infrastructure that criminals could rely on. Fragmentation into multiple smaller forums and encrypted groups means less organization, higher transaction costs, and greater difficulty for law enforcement to monitor activity. It's possible that RAMP's seizure actually makes the ransomware problem slightly worse in the short term by forcing criminals to use less transparent channels.
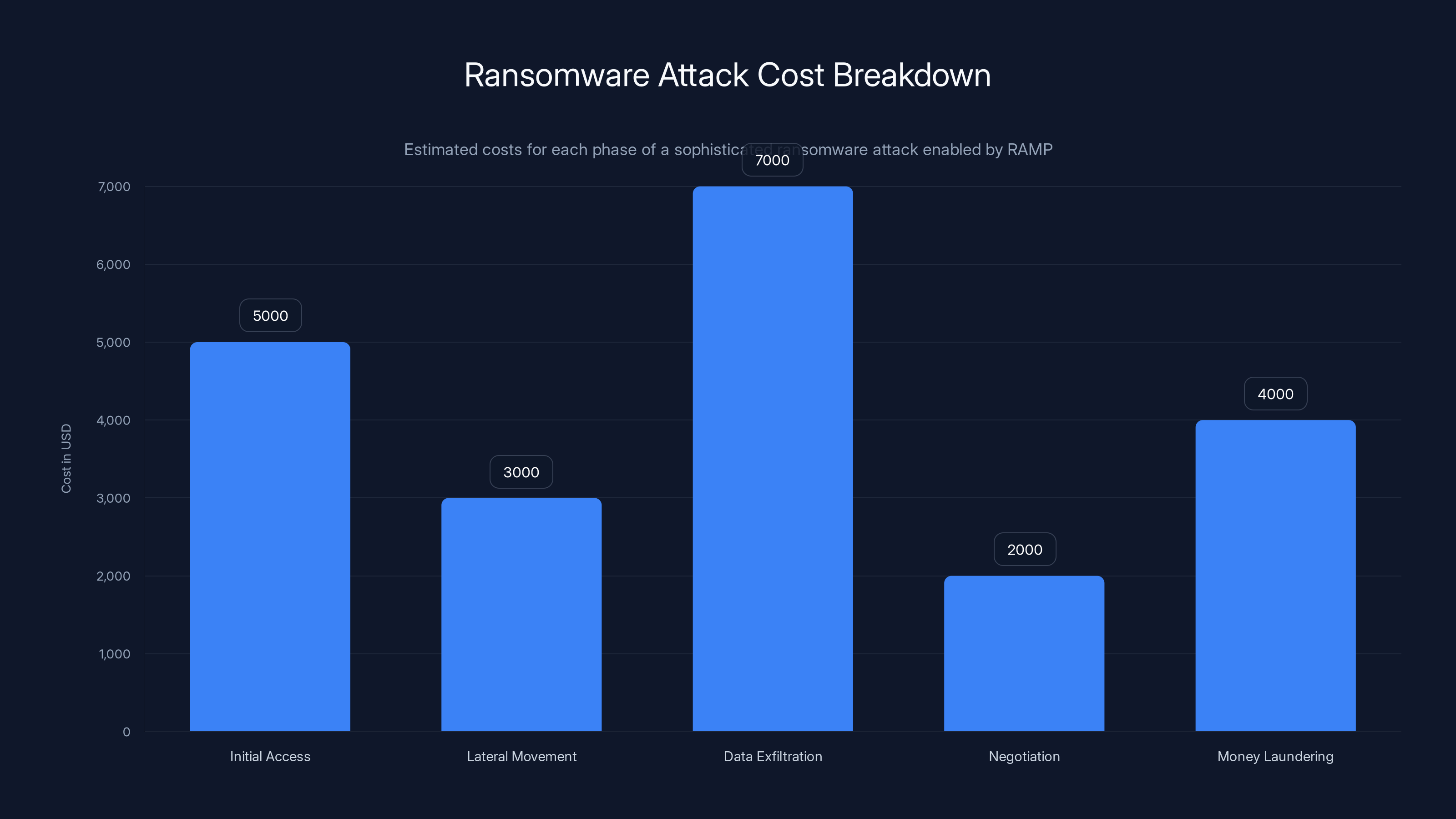
Estimated data shows that initial access and data exfiltration are the most costly phases in a ransomware attack, with costs ranging from
Law Enforcement Operations: Coordination, Timing, and Intelligence
The FBI's seizure of RAMP wasn't a sudden or unexpected action. It was the culmination of years of investigation involving multiple agencies and international coordination.
The seizure notice mentioned coordination with the United States Attorney's Office for the Southern District of Florida and the Department of Justice's Computer Crime and Intellectual Property Section (CCIPS). This organizational structure reveals the official pathway for taking down major criminal infrastructure.
But the invisible work happened long before the seizure notice appeared. Federal agents likely spent years gathering intelligence on RAMP. They probably had informants within the forum, analyzed user databases if possible, and tracked ransomware attacks that originated from RAMP users to understand the platform's role in the broader criminal ecosystem.
The technical challenge of taking down a darknet forum is non-trivial. RAMP operated on the Tor network, which provides anonymity through multiple layers of encryption and routing. Simply visiting the site from the public internet won't reveal the underlying server. The FBI likely had to locate RAMP's physical servers, gain access to them through legal authority (warrants or international cooperation), and then seize the infrastructure.
International coordination almost certainly played a role, even though the seizure is being presented as an FBI action. Darknet platforms often have servers distributed across multiple countries specifically to make seizure difficult. Taking down RAMP probably required cooperation from law enforcement agencies in Eastern Europe, potentially Russia, and other jurisdictions where servers might have been hosted.
The question that remains unanswered: does the FBI now have access to RAMP's user databases and transaction histories?
If so, the implications are massive. Every person who registered on RAMP, every transaction they made, every conversation they had could now be reviewed by law enforcement. Usernames, IP addresses (though obscured by Tor), cryptocurrency wallets, and communication history could all be part of the investigative package.
This represents law enforcement's greatest prize in dismantling criminal platforms: intelligence about the criminal network itself. Taking down the platform is significant, but capturing the infrastructure is potentially more significant because it reveals the network's structure.
However, it's worth noting that sophisticated criminals on RAMP likely took countermeasures. They probably used pseudonyms with no connection to their actual identities, routed their connections through additional anonymization layers, and were careful about what information they exposed. Still, even partial intelligence about the forum's user base would be valuable.
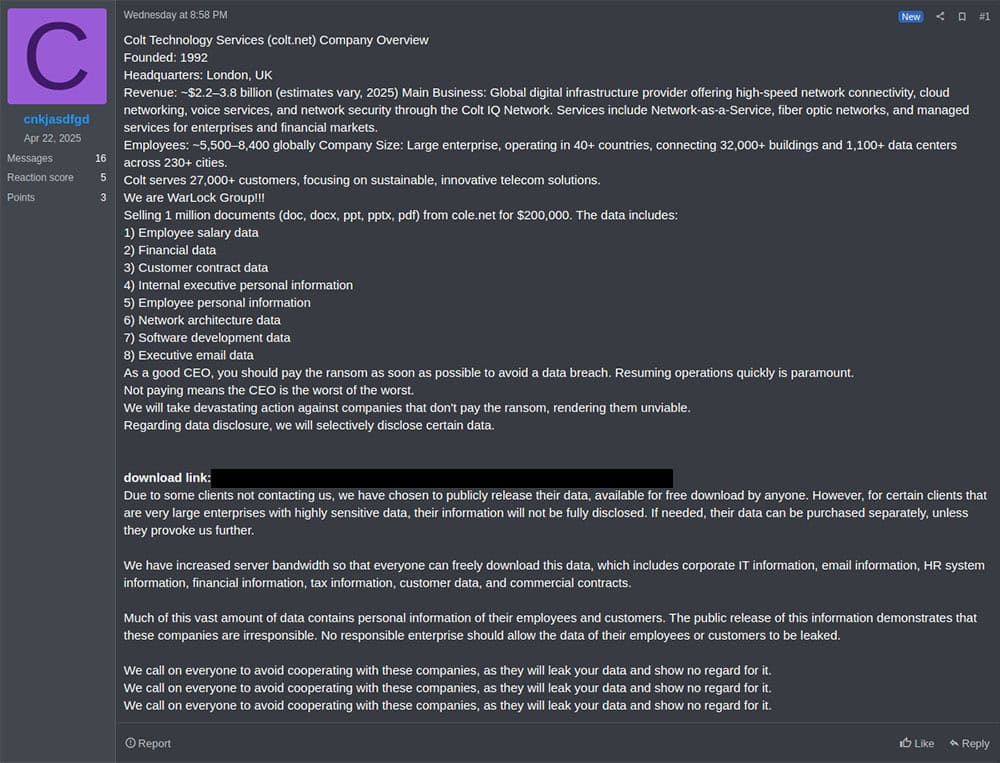
The Administrator's Statement: A Rare Window into Criminal Psychology
The shutdown announcement posted by the RAMP administrator (signing as "Stallman") provides unusual insight into how serious darknet operators think about their operations.
Translated from Russian, the message read:
"To all those concerned: I regret to inform you that the police authorities have taken control of the Ramp forum. This event has destroyed years of my work building the freest forum in the world, and while I hoped this day would never come, I always knew in my heart it was possible. It's a risk we all take. Although I no longer manage Ramp and will not be creating a new forum from scratch, I will continue to purchase access. My main business remains unchanged. Good luck to everyone, take care of yourselves and your loved ones."
Several aspects of this statement are revealing:
First, the resignation. The administrator doesn't express surprise or rage. They acknowledge that seizure was always a possibility. This isn't the statement of someone who believed their operational security was impenetrable. It's the statement of a professional who understood the risk-reward calculation and accepted the downside.
Second, the reference to "the freest forum in the world." This language reveals something about the administrator's self-perception. They weren't running a criminal marketplace from their perspective. They were running "the freest forum," a place where people could operate without censorship or restrictions. This framing is important because it suggests the administrator may have genuinely believed they were providing a service, not just facilitating crime.
Third, the indication that "my main business remains unchanged." The administrator is suggesting that RAMP was just one revenue stream for them. They have other criminal enterprises that will continue. This is consistent with how sophisticated criminal operators work—they diversify rather than putting all resources into a single platform.
Fourth, the message's appearance on XSS (a forum that had just lost its own leadership to law enforcement) is symbolic. Criminal forums are interconnected. Operators, moderators, and users migrate between them. By posting the announcement on XSS, the RAMP administrator was communicating across the criminal network simultaneously.
This message, more than any official law enforcement statement, reveals how professional criminal infrastructure has become. RAMP wasn't run by amateurs. It was operated by someone with years of experience, sophisticated understanding of operational security, and realistic expectations about the government's capabilities.
Where Do Ransomware Operators Go Now? The Fragmentation Effect
With RAMP seized, approximately 14,000+ criminal users need new platforms. Some will try to transition to smaller, existing forums. Others will create new platforms. But the landscape they migrate to will look fundamentally different from what existed under RAMP's dominance.
The most likely outcome is fragmentation. Instead of one centralized marketplace, the ecosystem will become more distributed. Encrypted Telegram groups, private Discord servers, and direct peer-to-peer networks will replace the centralized forum model.
Fragmentation has both benefits and drawbacks from a law enforcement perspective. On the benefit side, distributed networks are harder to take down completely. You can seize a server, but you can't seize Telegram. Law enforcement would have to infiltrate each individual group or criminal network.
On the drawback side, fragmentation makes criminal activity less efficient. Operators spend more time finding each other, vetting new connections, and negotiating services. This increased friction may slightly reduce the volume of ransomware attacks simply because it becomes harder to execute them smoothly.
Some criminal groups are already positioning themselves as RAMP alternatives. For example, the forum Russian Market (which itself was seized in 2024, after criminal operators were arrested) had positioned itself as a successor to Hydra. The pattern repeats: platform emerges, gains users, gets seized or abandoned, users migrate.
Other groups are taking a different approach: private. Rather than creating a new public forum, sophisticated ransomware groups are building private networks of operators they can trust. Membership would be by invitation only. Security would be higher. But the user base would be smaller and coordination would be more difficult.
Telegram has become increasingly popular as a replacement for forums. The platform offers some anonymity benefits (you can create anonymous accounts), is difficult for law enforcement to monitor at scale, and allows encrypted group communications. Ransomware operators have already been using Telegram for operational communication. The RAMP seizure will likely accelerate this migration.
But Telegram-based communities are fundamentally less sophisticated than centralized forums. You can't replicate the marketplace functionality, the reputation systems, or the searchable historical discussions. Operators will have to rebuild all of that from scratch on less suitable infrastructure.
The net effect: ransomware will likely continue as a criminal enterprise, but the ecosystem will be less organized, less efficient, and potentially easier to disrupt on an ad-hoc basis. However, the most sophisticated groups—the ones generating hundreds of millions in ransoms—won't be significantly impacted. They already have private networks and direct relationships. RAMP was useful for them primarily as a marketplace to sell stolen data or recruit lower-level operators.
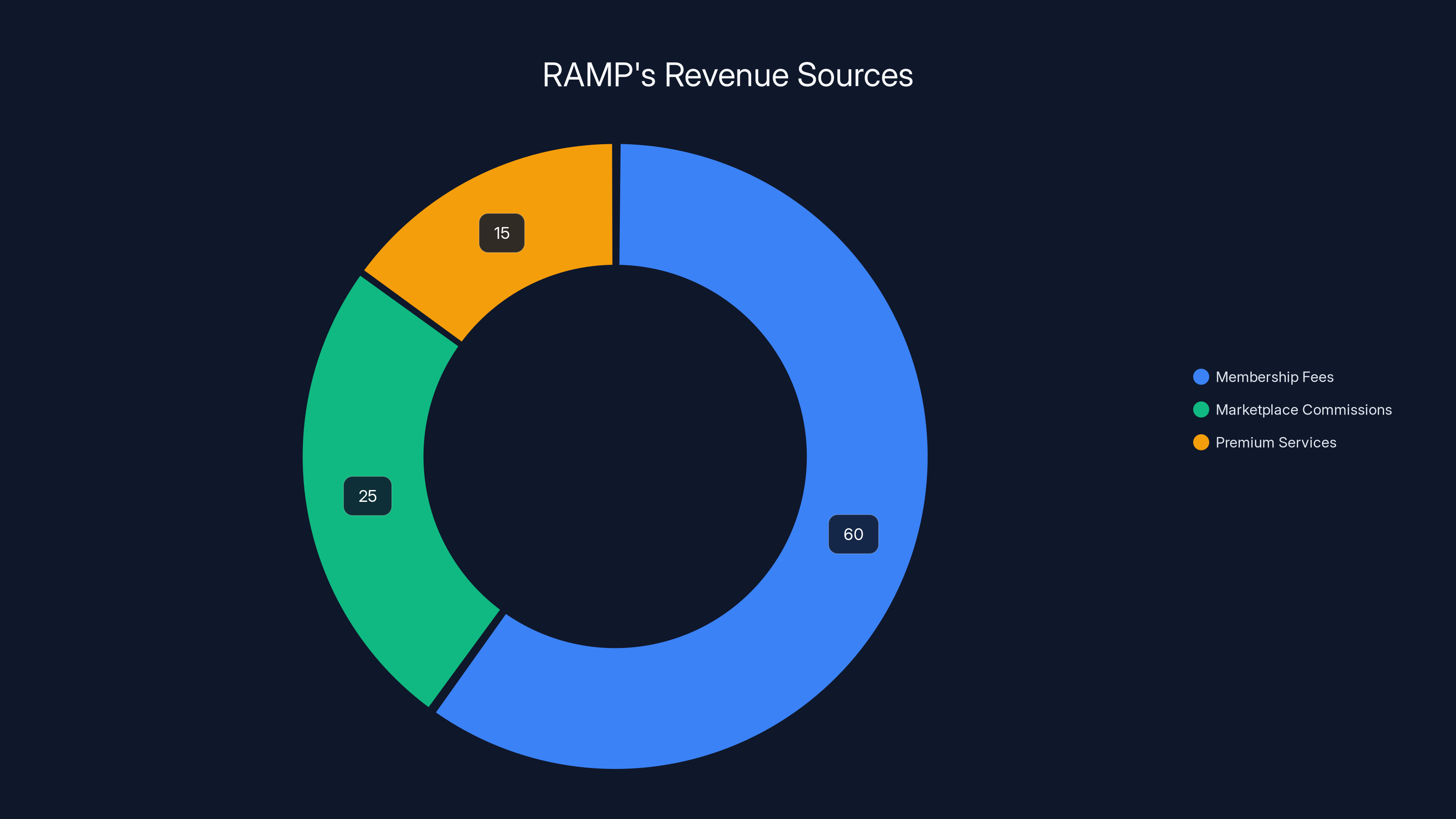
Estimated data shows that the majority of RAMP's revenue in 2024 came from membership fees, highlighting its business model's reliance on user subscriptions.
The Intelligence Windfall: What Law Enforcement Might Have Gained
One of the most significant but least discussed aspects of RAMP's seizure is the potential intelligence capture. If the FBI successfully accessed RAMP's databases, they now have access to years of criminal communication and transaction history.
Consider what a RAMP database might contain:
User Information: Approximately 14,000 registered user accounts. Even with anonymization, patterns of behavior, communication style, and activity timing can help law enforcement link accounts to specific criminal operators.
Transaction History: Records of who bought what services, when, and for how much. If the FBI can correlate specific transactions with known ransomware attacks, they can potentially identify who purchased access to victim networks.
Discussions and Tutorials: Years of posts about how to execute attacks, avoid detection, and operate ransomware-as-a-service operations. This information provides law enforcement with understanding of current attack techniques and criminal innovation.
Marketplace Listings: Profiles of threat actors offering services, including some individuals' actual credentials, operational capabilities, and claimed victim counts. This turns the forum's public-facing content into an intelligence database.
Cryptocurrency Wallets: If RAMP stored or mediated cryptocurrency transactions, law enforcement can now track some portion of the money flow. Cryptocurrency transactions are permanent, traceable, and can potentially be tied back to banks and exchanges using transaction analysis.
The intelligence value is highest if law enforcement can match RAMP users to specific real-world criminal operators. This would happen through a combination of:
-
Signal Analysis: Comparing writing style, timezone activity, technical vocabulary, and other behavioral signals from RAMP accounts to known criminal communications
-
Infrastructure Correlation: Matching IP addresses (if Tor exit nodes were recorded) to previously identified criminal infrastructure
-
Cryptocurrency Analysis: Tracing wallets used for RAMP transactions to exchange accounts that required identity verification
-
Victim Correlation: Working backward from ransomware attacks to identify which RAMP users likely purchased the access or tools used
-
Informant Information: Using existing human sources within criminal networks to identify which RAMP users they know personally
Even without definitively identifying specific users, law enforcement now understands the structure of the criminal network much better. They know which services are most frequently offered, which victim types are most targeted, what price ranges criminals expect for various services, and where the bottlenecks are in the criminal supply chain.
This intelligence could lead to:
- Targeted arrests of high-value criminal operators
- Sanctions against cryptocurrency exchanges connected to RAMP transactions
- Disruption of criminal supply chains by targeting access brokers or malware developers
- Negotiation pressure on victim organizations that paid ransoms (potentially recovering funds)
However, sophisticated criminals likely took countermeasures. They may have used one-time cryptocurrency wallets, hidden their true identity through multiple layers of pseudonyms, and been careful about what technical information they revealed. The intelligence gained might be valuable but incomplete.
Impact on Critical Infrastructure and Victim Organizations
RAMP's seizure creates both immediate and long-term effects for the organizations that ransomware groups target: hospitals, utilities, government agencies, and corporations.
Immediate Effects (Weeks 1-6):
The period immediately after RAMP's seizure will likely see reduced ransomware activity. Not because the threat has been eliminated, but because criminal operators are reorganizing, assessing which backup platforms to use, and rebuilding their supply chains. This creates a temporary window of relative safety for organizations that have been struggling with ransomware threats.
Organizations should use this window strategically. Patch vulnerabilities. Upgrade backup systems. Improve detection capabilities. The respite is temporary, but valuable.
Medium-Term Effects (Weeks 6-24):
As criminal operators migrate to new platforms and reorganize their networks, the ecosystem will become more chaotic. Coordination will decrease. Some criminal groups will fragment. Others will consolidate. During this period, you might see:
- Increased volume of lower-sophistication attacks as access to tools and services becomes harder to obtain
- Fewer mega-attacks against Fortune 500 companies as the most sophisticated groups struggle with supply chain disruption
- More targeting of mid-market organizations where coordinated attacks against specific targets are harder to execute
Long-Term Effects (6+ Months):
The criminal ecosystem will stabilize at a new equilibrium. Ransomware attacks will continue, but the infrastructure supporting them will be different. This change is actually somewhat concerning because:
- Smaller platforms are harder to identify and take down, so law enforcement has less visibility
- Encrypted peer-to-peer networks are more secure for criminals, reducing interception risks
- The barrier to entry for new criminal groups decreases when specialized forums no longer exist and criminals must build private networks
From a victim organization perspective, the RAMP seizure is modestly positive short-term and neutral long-term. It demonstrates that law enforcement can still disrupt criminal infrastructure, which might make some would-be criminals reconsider their operations. But it doesn't fundamentally change the economic incentives that make ransomware profitable.
Ransom amounts have been exceeding

Global Law Enforcement Coordination: A Rarer Achievement Than You Think
Taking down a major darknet platform requires coordination that most people assume routinely happens but actually doesn't. The seizure notice mentioned the FBI and the Department of Justice. But the actual work likely involved agencies worldwide.
Darknet platforms often distribute their servers across multiple countries specifically to make seizure difficult. RAMP's actual infrastructure was probably hosted in:
- Eastern European countries (favorable to hosting services with minimal oversight)
- Potentially Russia (though US agencies rarely have direct access to Russian law enforcement cooperation on criminal matters)
- Asia-Pacific regions (hosting infrastructure that routes traffic through multiple jurisdictions)
For the FBI to seize RAMP completely, they likely needed cooperation from law enforcement agencies in those countries. This is diplomatically complex. It requires:
- Legal mutual legal assistance treaties (MLATs) that allow countries to cooperate on criminal investigations
- Diplomatic negotiation to convince foreign governments to prioritize this particular crime
- Coordination on timing to prevent warning signals from leaking to RAMP administrators
- Technical cooperation to simultaneously access servers and prevent data destruction
When you see law enforcement successfully taking down a major platform, the visible action (seizure) represents months or years of invisible coordination.
The specific mention of the Southern District of Florida as the coordinating office suggests that major ransomware cases in that district probably provided the jurisdictional hook. The Southern District of Florida has been particularly active in prosecuting major cybercrime cases and has relationships with international law enforcement agencies.
This coordination capability is both impressive and limited. It's impressive because it demonstrates that despite all the anonymization tools available on the darknet, law enforcement can still disrupt sophisticated criminal infrastructure. It's limited because it only works when multiple countries decide to cooperate, which doesn't always happen.
For context, consider some platforms that have NOT been successfully seized despite years of operation:
- Hydra Marketplace: Operated from Russia for years. The US imposed sanctions but couldn't seize it directly. Eventually, individual operators were arrested in other countries, but the platform itself continued until 2022 when it was finally taken down after internal disputes
- Ru Tor: A Russian forum that has operated since 2011 and continues operating because it's hosted and protected within Russia
- Monero-focused marketplaces: Increasingly used because Monero's privacy features make money laundering harder to trace than Bitcoin
The RAMP seizure represents a successful law enforcement operation, but it's important to recognize that the most strategically protected criminal platforms (those hosted in Russia or China) remain essentially untouchable by Western law enforcement without explicit cooperation from those governments, which is politically unlikely.
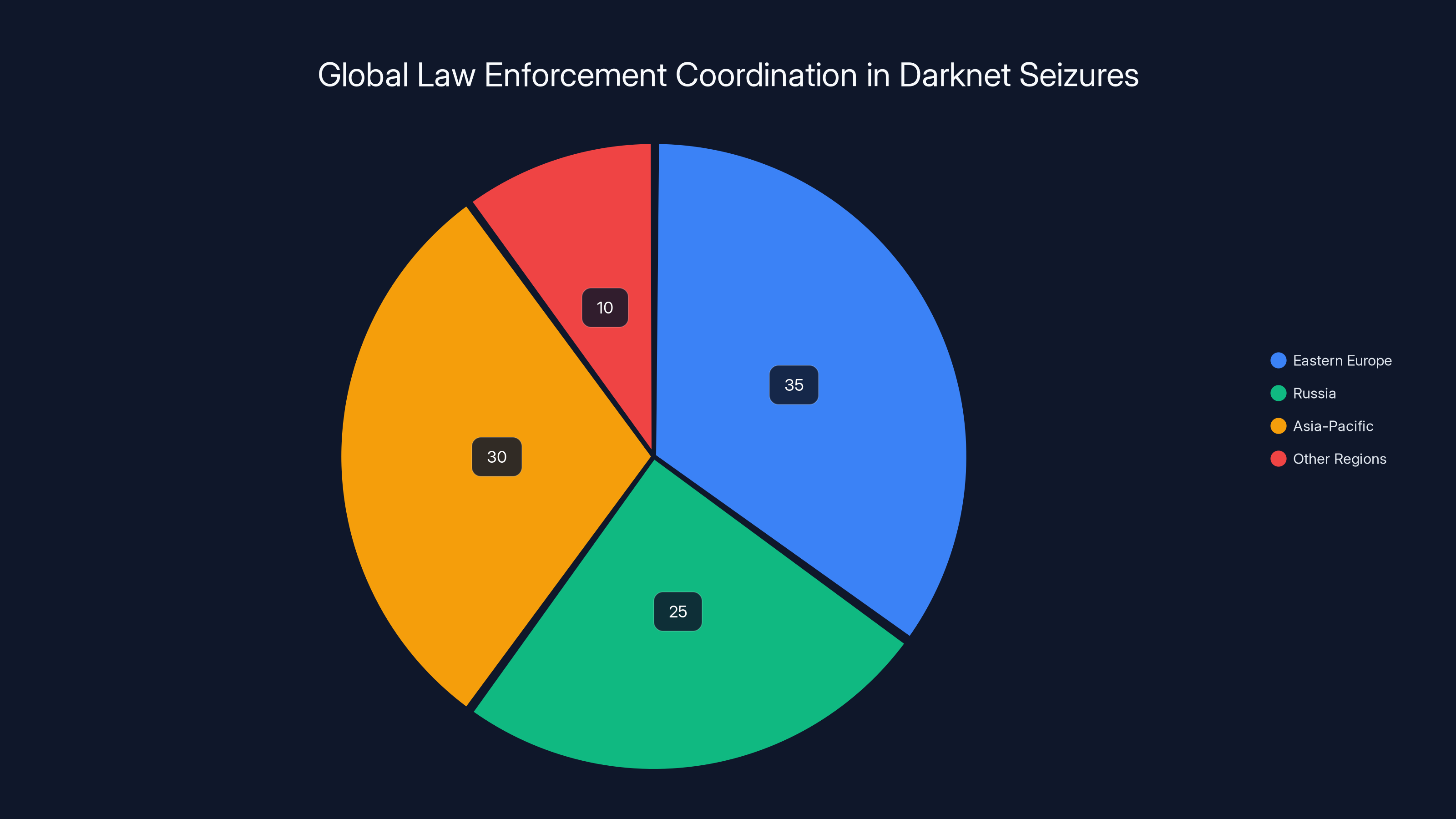
Estimated data shows Eastern Europe and Asia-Pacific regions are major players in darknet infrastructure hosting, requiring significant international law enforcement coordination.
The Ransomware Ecosystem After RAMP: A Fragmented but Persistent Threat
Rumors are already emerging about where RAMP users might migrate. Several smaller forums have announced themselves as RAMP alternatives. Some Telegram communities are consolidating users. A few sophisticated criminal operators are likely building private infrastructure.
The new ecosystem will have characteristics that are worth understanding:
Lower Centralization: With RAMP gone, there's no single platform where criminals can reliably find all services. This increases friction and search costs for operators.
Higher Barriers to Entry: New criminals trying to enter the ransomware business will find it harder to find tutorials, tools, and potential partners. The next-best platforms are smaller, less organized, and require stronger credentials to join.
Increased Use of Encryption: Migration to platforms like Telegram and Signal means encrypted communications become the default. This makes law enforcement surveillance more difficult but also makes coordination harder for criminals.
Possible Consolidation Among Top Groups: The most sophisticated ransomware operations might form their own private networks, excluding less experienced criminals. This could reduce the total number of ransomware attacks but increase the average damage per attack.
Continued Profitability for Top Operators: The economic fundamentals that drive ransomware haven't changed. Organizations still pay ransoms. Cryptocurrency still allows value transfer. The profit motive remains intact.
For cybersecurity professionals, the post-RAMP landscape requires different defensive approaches. When all criminals use a single forum, researchers can monitor that forum and identify attack patterns, tools, and techniques. When criminals fragment across multiple platforms, visibility decreases.
Organizations should shift focus to:
- Hardening critical systems against attack regardless of the criminal's toolkit
- Detecting lateral movement within networks rather than trying to identify attack sources
- Securing backups against encryption and deletion, the true defensive measure against ransomware
- Preparing incident response assuming breach will eventually occur rather than trying to prevent all breaches
The RAMP seizure is tactically significant for law enforcement. Strategically, it's one battle in a longer war where the economics still favor criminals.
Lessons for Law Enforcement: Scaling Operations Against Darknet Threats
The RAMP seizure reveals important lessons about law enforcement's evolving capabilities against darknet crime.
First, law enforcement has developed operational competence in targeting major criminal platforms. The FBI, working with partners, successfully:
- Located RAMP's actual servers despite Tor anonymization
- Obtained legal authority to seize them
- Coordinated internationally to prevent circumvention
- Deployed the seizure effectively
This represents a significant capability that didn't exist 10-15 years ago. Early darknet platforms like Silk Road were taken down through a combination of undercover operations and luck. Modern operations are more systematic.
Second, law enforcement understands that taking down one platform isn't a victory against the underlying crime. Ransomware will continue. Criminals will reorganize. The goal isn't elimination but disruption and intelligence gathering.
Third, law enforcement continues to struggle with prosecution. The seizure notice makes no mention of arrests, indictments, or criminal charges against RAMP operators. This suggests that despite seizing the infrastructure, law enforcement hasn't successfully identified or prosecuted the administrators.
For context, compare this to the arrest of Silk Road founder Ross Ulbricht, who faced extensive charges and is now serving a life sentence. Or the arrest of Alpha Bay administrator Alexandre Cazes, who committed suicide in Thai custody. Successful prosecutions require identifying specific individuals and building legal cases against them.
The lack of announced arrests suggests that RAMP's leadership either:
- Operated from jurisdictions where law enforcement can't easily reach them
- Had sufficient operational security that attribution remains uncertain
- Are subjects of ongoing investigation that hasn't yet reached the prosecution stage
For future law enforcement operations, the challenge will be scaling success. The RAMP seizure required resources that most agencies don't have. It required international coordination that takes months or years to arrange. It required sustained attention to a single target.
There are thousands of smaller forums, scam sites, and criminal platforms that could theoretically be seized. But law enforcement doesn't have resources to target all of them. So the strategy must be selective: focus on the largest platforms, the ones causing the most damage, the ones where prosecution is most likely.
RAMP qualified on all three counts. Its seizure was a logical choice from a resource allocation perspective. Future operations will likely follow the same pattern: periodically target whichever darknet platform has achieved sufficient size and notoriety to justify the effort.
The Cryptocurrency Angle: Tracing Ransomware Money
One critical aspect of the RAMP seizure that deserves deeper analysis is the cryptocurrency dimension. Ransomware is fundamentally a cryptocurrency crime. Attackers demand Bitcoin, Ethereum, or increasingly Monero. Victims pay in cryptocurrency. The entire money laundering process depends on cryptocurrency exchanges and mixing services.
If law enforcement successfully seized RAMP's database and it included wallet information, they can now track a significant portion of the money that flowed through the platform. Blockchain analysis companies already perform this work, tracing cryptocurrency transactions to identify where stolen funds move.
For example, if law enforcement can see that User A on RAMP received $500,000 in cryptocurrency for selling network access, and User B later received a ransom payment from a victim, and User C's wallet received funds from User B, law enforcement can potentially build a chain connecting the attack to the payout.
This intelligence becomes even more powerful when combined with exchange data. Most cryptocurrency exchanges require identity verification (KYC—know your customer requirements) to convert cryptocurrency back to fiat currency. If law enforcement can identify which exchange accounts received proceeds from RAMP transactions, they can request account information from those exchanges.
Several exchanges have already cooperated with law enforcement in criminal investigations. A subpoena requesting account information for wallets that received RAMP-related funds could result in identification of individuals who cashed out the proceeds.
This creates a secondary wave of investigation risk for RAMP users. The initial risk is being identified through forum communications. The secondary risk is being identified through cryptocurrency tracing.
Sophisticated criminals account for this. They use multiple pseudonyms, create new wallets frequently, and employ mixing services or privacy coins to obfuscate transaction trails. But not all criminals are equally sophisticated, and mixing services themselves have become targets of law enforcement.
The Monero cryptocurrency, which provides built-in privacy features, has become increasingly popular in criminal circles specifically to address this tracing problem. However, some RAMP users likely used Bitcoin or Ethereum, both of which are traceable.
Law enforcement's ability to trace cryptocurrency is improving. Blockchain analysis tools are becoming more sophisticated. Exchange cooperation is increasing. The result is that cryptocurrency-based money laundering is becoming riskier for criminals.
For the ransomware ecosystem, this creates a long-term pressure point. As tracing becomes easier and riskier, criminals will migrate toward privacy coins and non-cryptocurrency payment methods. Some criminal groups are already experimenting with accepting traditional banking transfers, though this brings its own set of legal risks.
The RAMP seizure, combined with ongoing cryptocurrency tracing, creates a multi-layered risk for ransomware operators:
- Forum-based risk: Being identified through communications and trading history
- Cryptocurrency risk: Being identified through wallet analysis and exchange data
- Operational risk: Having attack infrastructure disrupted by law enforcement targeting victim networks
No single risk is sufficient to deter the most profitable criminal enterprises. But combined, they create enough friction that some criminal operators are reconsidering their involvement or shifting to less traceable activities.
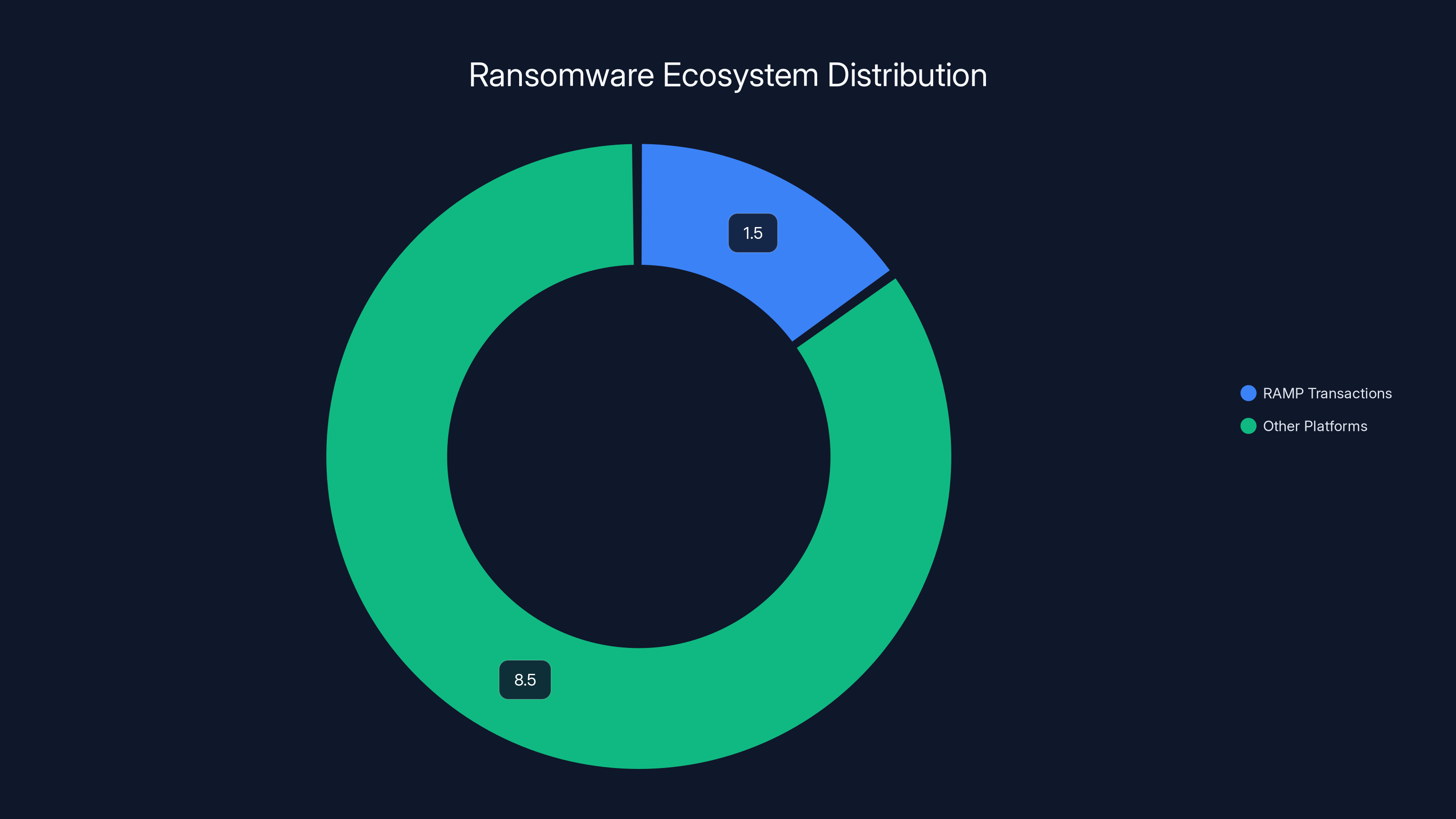
RAMP facilitated an estimated
What Happens to RAMP's Data? Responsible Disclosure of Sensitive Information
One question that hasn't been officially answered: what does the FBI do with RAMP's user database and private communications?
Legally, the data becomes government property as part of the seizure. Law enforcement can use it for:
- Investigation and prosecution: Identifying criminal operators and building cases against them
- Intelligence: Understanding the criminal network and threat landscape
- Notification: Potentially warning victims that their data was exposed
But there are significant privacy and legal concerns. RAMP users—even criminal RAMP users—may have some legal protections regarding how their communications are used. Fourth Amendment considerations, overseas user protections, and other legal frameworks create constraints on how aggressively law enforcement can use the data.
Additionally, the database contains information about victims. RAMP hosted stolen data—files exfiltrated from ransomware victims. Law enforcement now has that data. They face questions about:
- Victim notification: Should law enforcement notify organizations whose data was stolen?
- Data handling: Should law enforcement securely destroy the stolen data to prevent further exposure?
- Publicity: Should law enforcement release details about the seized data to deter future breaches?
Previous platform seizures have handled this inconsistently. When the FBI seized Silk Road, they initially kept the Bitcoin wallets associated with seized accounts, essentially holding significant cryptocurrency value. They eventually auctioned the Bitcoins.
When Hydra was shut down (with Russian government cooperation), the data was largely secured and not made publicly available. Different governments handle seized criminal data differently based on their legal frameworks and policies.
For RAMP specifically, the announcement hasn't provided details about data handling. This is probably intentional—law enforcement typically doesn't publicly discuss how they'll use seized information, both for operational security and to avoid tipping off targets of ongoing investigations.
For organizations concerned about whether they were affected by RAMP, the realistic expectation is that victim notification, if it occurs, will happen months or years after the seizure. Law enforcement moves slowly through the process of analyzing seized data, identifying affected parties, and coordinating notification.
The Broader Context: Ransomware as a Trillion-Dollar Industry
Ransom payments are estimated to exceed $1 trillion cumulatively since ransomware became a major threat around 2015. RAMP's seizure represents law enforcement action against infrastructure supporting a portion of that criminal economy.
The scale provides important context. If RAMP processed even 1-5% of all ransomware transactions (a conservative estimate given its dominance), law enforcement just disrupted infrastructure handling $10-50 billion in criminal activity. That's significant by any measure.
But it's also dwarfed by the underlying economic problem. If RAMP was facilitating
The economics are brutal from a law enforcement perspective. A single law enforcement operation consuming millions of dollars in resources disrupts billions in criminal activity, but doesn't eliminate it. The criminals simply reorganize and continue.
This creates a strategic question: why does law enforcement continue to target darknet platforms if the underlying crime persists?
The answer is that disruption matters, even if it doesn't eliminate the problem. Each platform seizure:
- Slows down criminal operations
- Increases operational costs through need to rebuild infrastructure
- Provides intelligence for ongoing investigations
- Signals to criminals that law enforcement has capability
- May prevent marginal criminal operators from entering the space
These benefits are real but incremental. They nudge the needle on a massive problem but don't solve it.
The fundamental solution to ransomware would require:
- Sanctions against countries harboring cybercriminals (primarily Russia, China, North Korea, Iran)
- Cryptocurrency regulation that makes money laundering significantly more difficult
- Defensive improvements in critical infrastructure
- International law enforcement cooperation on a scale far exceeding current efforts
None of these are politically feasible in the current environment. So law enforcement does what it can: disrupts infrastructure, arrests identifiable criminals, gathers intelligence. The RAMP seizure is a textbook example of this incremental approach.

Defensive Implications: What Organizations Should Do Now
If you're responsible for defending your organization against ransomware, the RAMP seizure provides a strategic inflection point to reassess your defenses.
Here's a practical framework for responding:
Immediate Actions (Next 30 days):
-
Assess backup resilience: Can your backups survive encryption or deletion attacks? If not, fix it now. This is the single most important defensive measure against ransomware.
-
Segment networks: Ensure that compromised systems can't immediately spread to all critical infrastructure. Network segmentation slows down attackers and prevents total compromise.
-
Improve monitoring: Ransomware requires time to spread within networks. Detection systems that identify unusual lateral movement can catch attacks before encryption occurs.
-
Patch critical systems: While the criminal ecosystem reorganizes, prioritize patching vulnerabilities in external-facing systems. This prevents easy initial access.
Medium-term Actions (30-90 days):
-
Develop incident response procedures: Assume breach. Assume encryption. Prepare the specific steps you'll take to contain, recover, and communicate. Practice these procedures.
-
Establish cryptocurrency monitoring: If your organization pays ransoms, understand the cryptocurrency ecosystem. If you pay, law enforcement may be able to help recover funds. Maintain records.
-
Conduct security awareness training: Most ransomware starts with phishing. Train employees to recognize social engineering attempts.
-
Implement email security: Deploy tools that detect and prevent malicious attachments and links. This blocks the attack vector for a significant portion of ransomware incidents.
Long-term Actions (90+ days):
-
Implement zero-trust security: Assume no user or system is trustworthy. Verify every access request. This approach dramatically reduces ransomware's ability to spread.
-
Develop threat intelligence: Monitor where your industry's specific threat actors operate. If they migrate to new platforms post-RAMP, understanding where can inform your defenses.
-
Establish cyber insurance: Cybersecurity is now a shared risk between organizations and insurance providers. Proper cyber insurance can mitigate financial impact if you're hit.
-
Participate in information sharing: Contribute to threat intelligence sharing communities. When multiple organizations monitor the same threat actors, collective understanding improves.
The RAMP seizure doesn't fundamentally change the threat model. Ransomware remains a viable criminal enterprise. But it does create a temporary window for defensive improvements. Organizations should use it.
The Future of Criminal Forums: Are Centralized Platforms Obsolete?
Ramp's seizure raises a deeper question: do centralized criminal forums have a future?
The traditional darknet marketplace model—centralized servers, public listings, reputation systems—has clear advantages for criminals. It provides one-stop shopping for illegal goods and services. It builds trust through reputation mechanisms. It's familiar to users.
But it has an obvious vulnerability: a single point of failure. Seize the central server, and the entire platform disappears.
Criminals are increasingly experimenting with alternatives:
Decentralized Models: Some projects are attempting to build decentralized marketplaces using blockchain technology. These would eliminate the central server problem but create new challenges around dispute resolution, reputation management, and law enforcement targeting of participants rather than infrastructure.
Encrypted Chat Groups: Telegram, Signal, and Wire-based communities are becoming primary infrastructure. These are harder to take down but less organized and require stronger existing relationships to join.
Private Networks: The most sophisticated criminal groups are building proprietary networks for a limited set of trusted partners. This approach maximizes security and minimizes law enforcement visibility.
Surface Web Tactics: Some criminal groups are literally operating openly on clear-web forums or social media platforms, using coded language and obscure references. This approach provides less anonymity but also less law enforcement attention.
The migration toward encrypted, decentralized, or private models has long-term implications. It means law enforcement will lose visibility into criminal communication that was previously available on searchable, observable platforms like RAMP.
From a law enforcement perspective, this is concerning because visibility is essential for investigation. When criminals operate on a centralized platform, law enforcement can infiltrate the platform, monitor all discussions, and build comprehensive intelligence. When criminals migrate to encrypted private networks, law enforcement can only identify criminals through other means: informants, cryptocurrency tracing, infrastructure analysis.
The tradeoff for criminals is that private networks are less efficient. They can't easily find new partners, share updates, or quickly negotiate services. But as law enforcement pressure increases, efficiency becomes less important than operational security.
The long-term forecast: darknet platforms like RAMP become increasingly rare. Criminal infrastructure becomes more distributed, encrypted, and private. Law enforcement's visibility into criminal activity decreases, but prosecution of individual criminals (through cryptocurrency tracing and other means) may actually increase.
Conclusion: RAMP's Seizure as Signal and Limitation
The FBI's seizure of RAMP is significant, but not in the way headline writers suggest. It's not a victory against ransomware. It's a successful law enforcement operation against a particular criminal platform, which is different.
Ramp enabled ransomware at scale. It provided infrastructure, tutorials, marketplaces, and networking that transformed ransomware from a crude attack technique into a sophisticated, specialized, billion-dollar criminal enterprise. The platform didn't invent ransomware, but it absolutely scaled it.
By taking down RAMP, law enforcement achieved several important things:
-
Demonstrated capability: Law enforcement can locate, access, and seize major darknet platforms despite anonymization technology.
-
Disrupted infrastructure: Criminals now must reorganize, move to new platforms, and rebuild relationships. This creates friction and delay.
-
Gathered intelligence: If the database was successfully captured, law enforcement has years of communication history, transaction data, and network mapping that will support investigations for years.
-
Set precedent: Future criminal platforms now know that even mature, established forums can be seized. The risk calculation for operating a visible platform increases.
But critically, the seizure did NOT:
-
Eliminate ransomware: The underlying crime continues. Criminals have reorganized into smaller forums and encrypted groups.
-
Recover stolen data: Much of RAMP's value was as a marketplace for stolen data. That data remains stolen, exposed, and at risk regardless of RAMP's seizure.
-
Arrest major criminals: No major arrests of RAMP operators or notable users have been announced. The platform is gone, but its administrators remain at large.
-
Address the underlying economics: Ransomware remains profitable. Victims continue to pay. The incentive structure remains intact.
For organizations defending against ransomware, the RAMP seizure is tactically relevant but strategically limited. It represents one battle in a much longer conflict where the fundamental problem—criminal profitability and government capacity mismatch—persists.
The appropriate response isn't celebration that law enforcement is winning the war against ransomware. It's recognition that law enforcement achieved one tactical success, and the war will continue for years. Organizations must defend themselves regardless of what happens to criminal platforms.
The RAMP seizure is a reminder that law enforcement has improved capabilities. It's also a reminder that those capabilities operate at the margin of a much larger problem. The smart response to both truths is acknowledgment and preparation: yes, law enforcement can disrupt criminal infrastructure, and yes, your organization still needs comprehensive defenses because disruption doesn't mean elimination.
Ransom payments will continue in 2025 and beyond. Threat actors will reorganize. New platforms will emerge. Law enforcement will periodically target major platforms. This cycle will repeat because the underlying economics favor criminals.
That's not pessimism. That's realism. And realistic security planning requires acknowledging that RAMP's seizure, while meaningful, solves none of ransomware's core problems. What it does is signal that defending against ransomware isn't optional—it's essential.
FAQ
What is RAMP and why was it important to law enforcement?
RAMP was a Russian-language darknet forum that billed itself as "the only place ransomware allowed." It functioned as a marketplace and discussion forum where ransomware operators could buy, sell, and trade services like malware tools, victim data, and operational guidance. The platform had approximately 14,000 registered users and generated an estimated $250,000 annually. Law enforcement prioritized it because it was the largest remaining centralized platform supporting ransomware operations globally, making it a high-value target for disruption.
How did the FBI successfully seize RAMP despite its use of Tor anonymization?
The specific technical details haven't been publicly disclosed, but law enforcement likely used a combination of investigative techniques: identifying physical server locations where RAMP was hosted, obtaining warrants to access those servers, coordinating with international law enforcement agencies in jurisdictions where servers were located, and timing the seizure across multiple locations to prevent data destruction or administrator escape. Tor anonymization protects user identity but not infrastructure, which is ultimately located on physical servers in specific countries.
Will this seizure significantly reduce ransomware attacks going forward?
Likely not substantially. While RAMP's seizure disrupts criminal infrastructure and may temporarily reduce attack volume during reorganization, ransomware remains economically attractive for criminals. Threat actors will migrate to smaller forums, encrypted messaging groups, and private networks. The underlying criminal supply chain will rebuild, though potentially less efficiently. Law enforcement disrupted one platform, not the fundamental economics that make ransomware profitable.
Where are ransomware operators likely to migrate after RAMP's seizure?
Criminals are likely consolidating into three categories: smaller existing forums that can absorb RAMP users, encrypted Telegram groups and private chat servers with restricted membership, and proprietary private networks for established criminal groups. Some threat actors are experimenting with blockchain-based decentralized marketplaces, though these remain experimental. The net effect is fragmentation of the criminal ecosystem—less centralized, less transparent, but also less efficient.
Could organizations that were victims of ransomware attacks recover data from RAMP's seizure?
Possibly, but it's not certain. If law enforcement successfully seized RAMP's complete database, they may have access to files that were stolen by ransomware groups and later sold or posted on the platform. However, law enforcement moves slowly through evidence analysis, and victim notification could take months or years. Organizations with ransomware victims should contact the FBI's Internet Crime Complaint Center and monitor for official notifications about recovered data rather than expecting immediate results.
What are the cryptocurrency implications of RAMP's seizure?
If law enforcement obtained RAMP's transaction records and wallet information, they can now trace cryptocurrency payments made on the platform using blockchain analysis. This creates secondary risk for criminals who attempted to cash out ransomware proceeds through cryptocurrency exchanges. Organizations and law enforcement can now use wallet analysis to identify who received ransom payments and potentially freeze assets if they were converted to traceable cryptocurrencies like Bitcoin or Ethereum.
How does RAMP's seizure compare to previous darknet platform takedowns like Alpha Bay or Silk Road?
RAMP's seizure appears to be a successful infrastructure takedown but lacks the high-profile arrests that characterized previous operations. Alpha Bay's seizure resulted in arrests of operators worldwide. Silk Road's seizure led to founder Ross Ulbricht's prosecution and life sentence. RAMP's seizure has no announced arrests of major figures, suggesting law enforcement seized the infrastructure but may not have definitively identified the administrators, or those individuals remain subjects of ongoing investigation rather than prosecution.
What should security teams do to prepare for increased ransomware activity during platform reorganization?
The recommendation is to assume ransomware threat remains constant regardless of RAMP's status. Security teams should focus on: ensuring backup systems are truly isolated and unencryptable, implementing network segmentation to contain attacks, improving detection of suspicious lateral movement, hardening external-facing systems through patching, and developing incident response procedures. Use any temporary reduction in attack activity as an opportunity for defensive improvements rather than relaxing security posture.

Key Takeaways
- RAMP was the largest organized platform supporting ransomware globally, with 14,000+ users and an estimated $250,000 annual revenue from facilitation of attacks
- The FBI successfully seized the platform in January 2026 through international coordination, disrupting a significant portion of ransomware infrastructure
- Law enforcement likely captured extensive intelligence about criminal networks, techniques, and cryptocurrency flows that will support investigations for years
- Ransomware will not disappear but will reorganize into smaller, more encrypted, and less efficient platforms
- Organizations must maintain defensive vigilance regardless of law enforcement success, as the underlying criminal economics remain intact
Related Articles
- RedDVS Phishing Platform Takedown: How Microsoft Stopped a $40M Cybercrime Operation [2025]
- Covenant Health Breach Exposes 500K Patients: What Happened [2025]
- Nike Data Breach: What We Know About the 1.4TB WorldLeaks Hack [2025]
- From Bitcoin Heist to Cybersecurity: A Hacker's Path to Redemption [2025]
- Under Armour 72M Record Data Breach: What Happened [2025]
- Ingram Micro Ransomware Attack: 42,000 Affected, SafePay Claims Responsibility [2025]
![FBI Seizes RAMP: The Collapse of Ransomware's Last Stronghold [2025]](https://tryrunable.com/blog/fbi-seizes-ramp-the-collapse-of-ransomware-s-last-stronghold/image-1-1769639930398.jpg)



