Tax Season Security Threats: How to Protect Your Data [2025]
Tax season isn't just stressful for accountants and taxpayers—it's a golden season for cybercriminals. Every year between January and April, hackers sharpen their tools and target the firms that handle your most sensitive financial information. Social Security numbers, tax returns, banking details, health insurance agreements—all of it becomes a target.
Here's the brutal reality: when a tax firm gets hit by ransomware, it's not just their problem. Your data walks out the door. Cybercriminals harvest it, leak it on dark web marketplaces, or use it to commit fraud in your name. You don't find out until months later when strange accounts appear on your credit report or the IRS contacts you about a fraudulent return filed under your SSN.
This isn't theoretical. Tax firms across the US have been hit hard recently. One Massachusetts accounting firm, CSA Tax & Advisory, fell victim to a ransomware gang calling itself Lynx. The breach exposed Social Security numbers, tax returns, health coverage agreements, and internal correspondence. The attackers leaked samples online, confirming the theft. And CSA wasn't alone—these attacks happen constantly during tax season.
The scary part? Most taxpayers have no idea this is happening until it's too late. You file your return through a tax firm you trusted, they get breached, and suddenly criminals have everything they need to steal your identity. By then, the damage is already done.
This guide walks you through exactly what's happening, why tax firms are targets, what data you're at risk of losing, and what you can actually do to protect yourself. We'll cover the technical side—how these attacks work—and the practical side: what to do if your information gets compromised, warning signs to watch for, and steps to take right now.
Let's start with the painful truth: tax season is hunting season for hackers.
TL; DR
- Russia-linked ransomware gangs like Lynx actively target tax firms during filing season to steal SSNs, tax returns, and banking data
- Exposed data enables full identity theft: criminals can open credit cards, file fraudulent tax returns, claim insurance fraud, and drain bank accounts in your name
- Tax firms are vulnerable because they centralize sensitive data, use outdated security, and face operational pressure during peak season
- Warning signs include phishing emails impersonating the IRS or your tax firm, requests for unusual information, and suspicious account activity
- Immediate actions: enable two-factor authentication, freeze your credit, monitor your credit report, file a police report, and contact the IRS if you suspect fraud
- Long-term protection: use strong unique passwords, verify firm security practices before submitting documents, and consider working with firms that prioritize cybersecurity

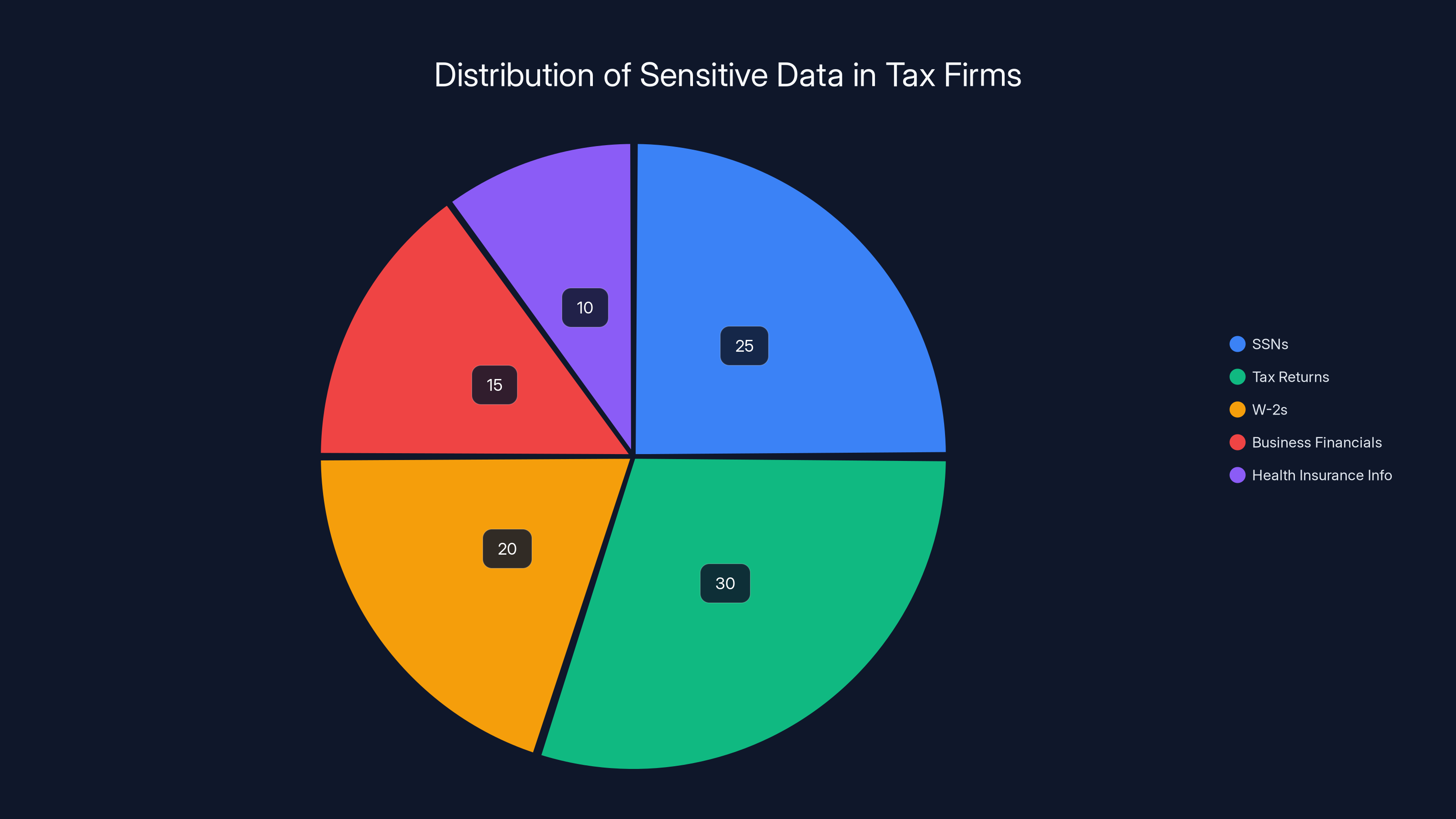
Estimated data shows tax firms handle a variety of sensitive data, with tax returns and SSNs being the most prevalent. Estimated data.
Understanding the Tax Season Attack Window
Tax season creates a unique vulnerability window. Between January and April, tax firms are flooded with client files—thousands of returns stacked up, each containing decades of financial history. The pressure is immense. Partners push to process more clients faster. Quality control sometimes slips. Security takes a backseat to speed.
This is exactly what attackers exploit. They know firms are overwhelmed. They know staff are working overtime, tired, and more likely to click a malicious link. They know the firms are desperate to keep operations running, which makes them more likely to pay ransoms if systems go down.
Moreover, tax firms handle a concentration of sensitive data that's unusual even for financial services. A single firm might have SSNs, tax returns, W-2s, business financial statements, and health insurance information for thousands of people. Compromise one firm, and you've compromised thousands of individuals at once.
The attackers also understand tax firm security is historically weak. Many of these firms are small to mid-sized operations. They're not tech companies. They often run legacy systems because they work and the firm lacks budget to upgrade. They have maybe one IT person managing everything. Security patches get delayed. Multi-factor authentication isn't standard. Remote access during peak season isn't properly secured.
Think about it from the attacker's perspective: tax firms are soft targets with valuable data. They're busy. They're not as well-defended as banks or insurance companies. But they hold data almost as sensitive. It's a rational choice for cybercriminals looking to maximize return on effort.
The Lynx gang that hit CSA Tax & Advisory follows this pattern exactly. They identify firms during tax season, compromise systems (usually through phishing or exploiting known vulnerabilities), install ransomware, and demand payment. If the firm refuses, they leak the data publicly, which forces payment eventually because the regulatory and legal consequences become worse than paying the criminals.
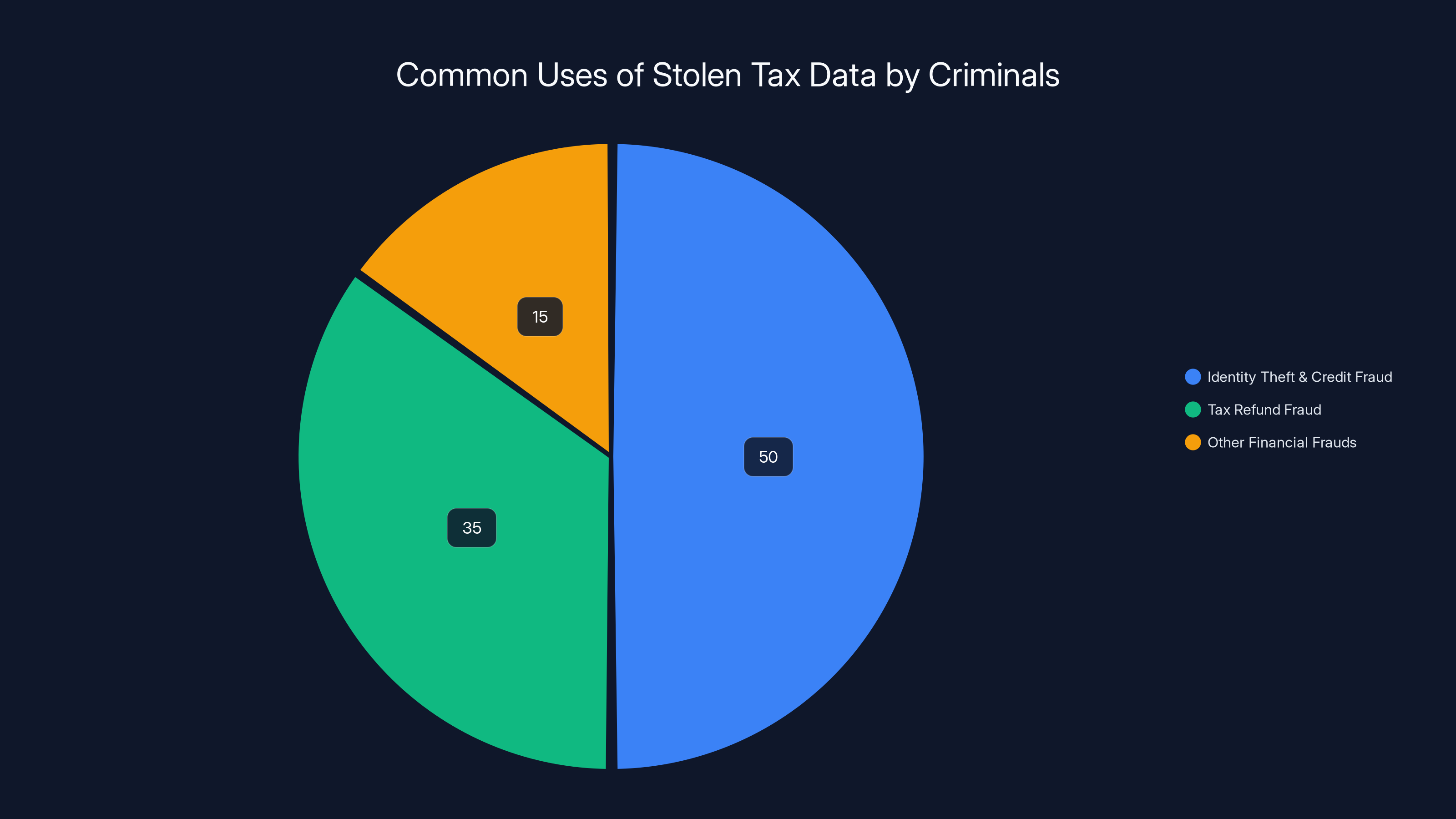
Identity theft and credit fraud account for approximately 50% of criminal activities using stolen tax data, followed by tax refund fraud at 35%. Estimated data.
How Ransomware Breaches Tax Firms
Most ransomware attacks follow a predictable attack chain. Understanding this chain helps you recognize threats and understand why your firm might be vulnerable.
Initial Access
Attackers typically start with phishing. An employee at the tax firm receives an email that looks legitimate—maybe it claims to be from a client, a software vendor, the IRS, or a colleague. The email contains an attachment or link. The attachment is malware disguised as a spreadsheet or PDF. The link directs to a fake login page that harvests credentials.
During tax season, phishing is more effective because volume is high and people are rushed. An accountant juggling 50 client files is more likely to click a suspicious link than someone with normal workload.
Alternatively, attackers exploit known security vulnerabilities in public-facing systems. If the firm has a web portal for clients to upload documents, and that portal hasn't been patched, attackers can exploit it directly without needing to trick anyone.
Once they're in, they move laterally—from the initial compromised system to other systems on the network. They look for domain controllers, backup systems, and servers storing client data. They create back doors so they can get back in later even if the initial access is discovered.
Encryption and Ransom
Once they've mapped the network and identified valuable data, they deploy ransomware. This encrypts every file on the compromised systems—making them unreadable without a decryption key that only the attackers have. The firm suddenly can't access client data, can't process returns, can't operate.
The attackers leave a note with payment instructions and deadlines. Pay in Bitcoin or other cryptocurrency within X days, or we leak your data. Or we delete the decryption key. Or we sell the data to competitors and fraud rings.
For a tax firm, this is catastrophic. They can't work. Clients can't file returns. Regulatory deadlines are missed. The firm's reputation is destroyed. Often, paying the ransom seems like the only option.
Data Exfiltration
Before they even encrypt anything, though, sophisticated attackers like Lynx copy the data. They're not just holding the firm's systems hostage—they're holding the data hostage. Even if the firm refuses to pay and restores from backups, the attackers have the data.
This is why Lynx put CSA's data sample on their leak site. They wanted proof of access to pressure payment. It's a double-leverage tactic: pay or your clients get their data leaked and your firm faces lawsuits and regulatory action.
What Data Gets Compromised in Tax Firm Breaches
When a tax firm gets breached, what exactly walks out the door? Understanding this helps you understand your actual risk.
Personal Identification
SSNs are the crown jewel. Combined with your name, address, and date of birth (all of which are on tax forms), someone has everything needed to open credit cards in your name, take out loans, or file fraudulent tax returns. SSNs don't expire. A stolen SSN is useful to criminals forever. Even if you catch the fraud after five years, that stolen SSN can be monetized for years afterward.
Drivers' licenses and passport numbers are also valuable. These are used for identity verification at banks, insurance companies, and government agencies. With these, criminals can pass background checks and access more of your financial accounts.
Financial Records
Tax returns contain bank account numbers, investment account numbers, business revenue figures, profit margins, and deduction details. For business owners, tax returns reveal how profitable the business is—valuable intelligence for extortion or targeted fraud.
IRS e-file signature authorization forms contain digital signatures that can be forged to file fraudulent returns in future years, even if the victim changes passwords and secures accounts. These documents are particularly dangerous because they're designed to bypass normal verification.
W-2s show employer information and earned income. Combined with SSN and identification data, W-2s enable criminals to file fraudulent returns claiming refunds they're not entitled to.
Health and Insurance Information
Spousal health care coverage agreements reveal family structure and health insurance details. This enables insurance fraud (submitting fake claims), impersonation, and extortion based on sensitive medical information revealed in coverage agreements.
While less immediately valuable than financial data, health information is protected by HIPAA and state privacy laws. Exposure triggers mandatory breach notifications and regulatory investigations.
Business and Internal Data
Internal correspondence between firm employees and clients reveals approval processes, decision-makers, spending patterns, and authorization thresholds. Criminals use this for business email compromise (BEC) attacks—impersonating executives to trick staff into transferring money or revealing information.
Invoices and contracts reveal vendor relationships, payment terms, and financial obligations. This enables supplier impersonation and invoice fraud.

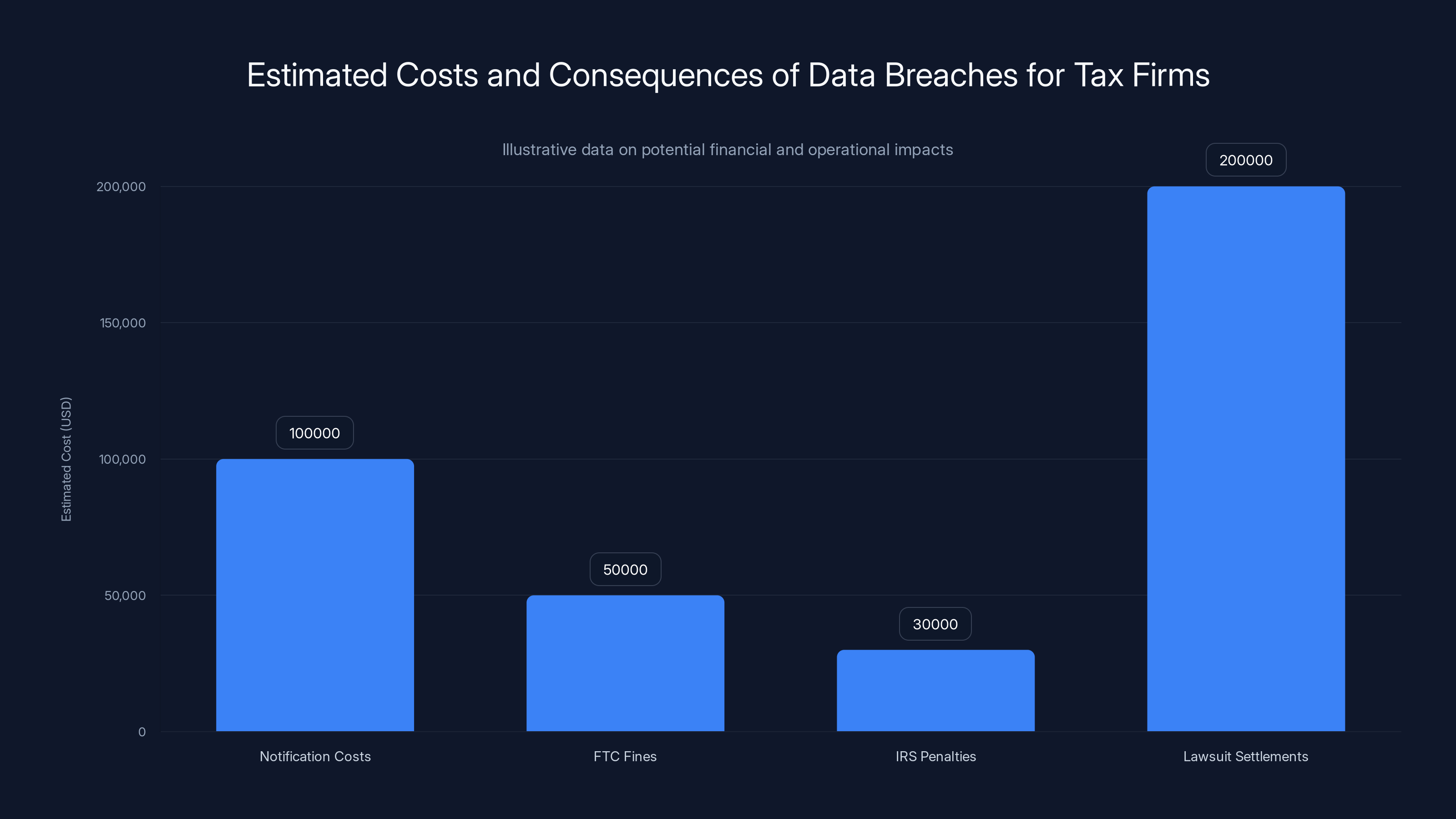
Estimated data shows notification costs can exceed $100,000, with potential FTC fines and IRS penalties adding significant financial burdens. Lawsuit settlements can be the most costly consequence.
How Criminals Use Stolen Tax Data
Once data is stolen, the monetization begins. Criminals have multiple options, all profitable.
Identity Theft and Credit Fraud
The most direct path: criminals use stolen SSN, name, and address to open credit card accounts. They run up charges and disappear. The victim doesn't realize until they check their credit report weeks later.
The victim then has to contact the credit card company, prove they didn't open the account, dispute the charges, and work with the card issuer to close the account. This process takes weeks. Meanwhile, the damage appears on the victim's credit report, potentially affecting mortgage, auto loan, or employment eligibility.
With financial records from the breach, criminals can also apply for personal loans or lines of credit. They might take out a $25,000 personal loan against your name and immediately default. You discover this when credit collection agencies start calling.
Tax Refund Fraud
Criminals file fraudulent tax returns using your SSN, claiming refunds they're not entitled to. The IRS processes the return and issues a refund to an account controlled by the criminal.
You don't know this happened until you file your legitimate return and it's rejected because a return for that SSN was already filed. Now you have to contact the IRS, prove you're the victim, and request a fraud investigation. The IRS will investigate, verify that one of the returns is fraudulent, and eventually process your legitimate return. But this takes months. If you were counting on the refund to pay bills, you're out of luck while the investigation proceeds.
The criminal gets the refund money instantly. If they're smart, they cash out through banks in different jurisdictions where tracking is harder.
Insurance Fraud
With health coverage agreements, criminals submit fraudulent insurance claims for medical services never rendered. They might claim you received prescription medications, surgeries, or hospitalizations that never happened.
Insurance companies might initially honor these claims. When they investigate and realize the claims are fraudulent, they deny coverage and might investigate the policyholder (you) for fraud. Meanwhile, your insurance rates increase and your coverage might be dropped.
Alternatively, criminals might contact your insurance company claiming you want to change coverage, authorize treatments, or withdraw claims. Impersonation is easier when the criminal has your policy numbers, family member names, and medical history.
Business Email Compromise (BEC)
For business owners, internal emails reveal payment processes and approval hierarchies. A criminal impersonates the business owner or CFO and requests an urgent wire transfer for a vendor invoice, merger, or acquisition.
Staff is trained to follow the approval chain—and the criminal knows the chain from leaked emails. The request looks legitimate, comes from a familiar-looking email address, and matches the urgency level they expect. Money gets wired. By the time anyone realizes, the criminal has moved the money to another account and withdrawn it.
A successful BEC fraud can cost businesses

The Scale of Tax Firm Breaches
How widespread is this problem? The answer is sobering.
Tax and accounting firms report breach incidents constantly during tax season. The Lynx gang that hit CSA Tax & Advisory isn't unique—there are dozens of groups actively targeting this sector. Some groups like Cl 0p focus on exploiting vulnerabilities in file transfer platforms commonly used by accountants. Others like Black Cat/ALPHV use general ransomware tactics.
Most breaches aren't publicly reported. A firm gets hit, quietly pays the ransom to criminals (who often accept payment just for the encryption key, with a side agreement not to leak data), and life goes on. The victims might never find out they were compromised.
But some breaches leak anyway. The attackers disappear. The negotiation breaks down. Or someone at the firm reports the incident to authorities, which forces public disclosure.
When breaches do become public, the numbers are staggering. A single tax firm might have files for 10,000 to 50,000 clients. A breach of one mid-sized firm compromises the data of tens of thousands of people.
And tax firms aren't isolated targets. Banks, insurance companies, payroll processors, and HR firms all handle tax data. A breach at your employer's payroll processor exposes your W-2. A breach at your bank exposes your account details. A breach at your insurance company exposes your policy. From a criminal's perspective, there are dozens of points of attack in the tax ecosystem.

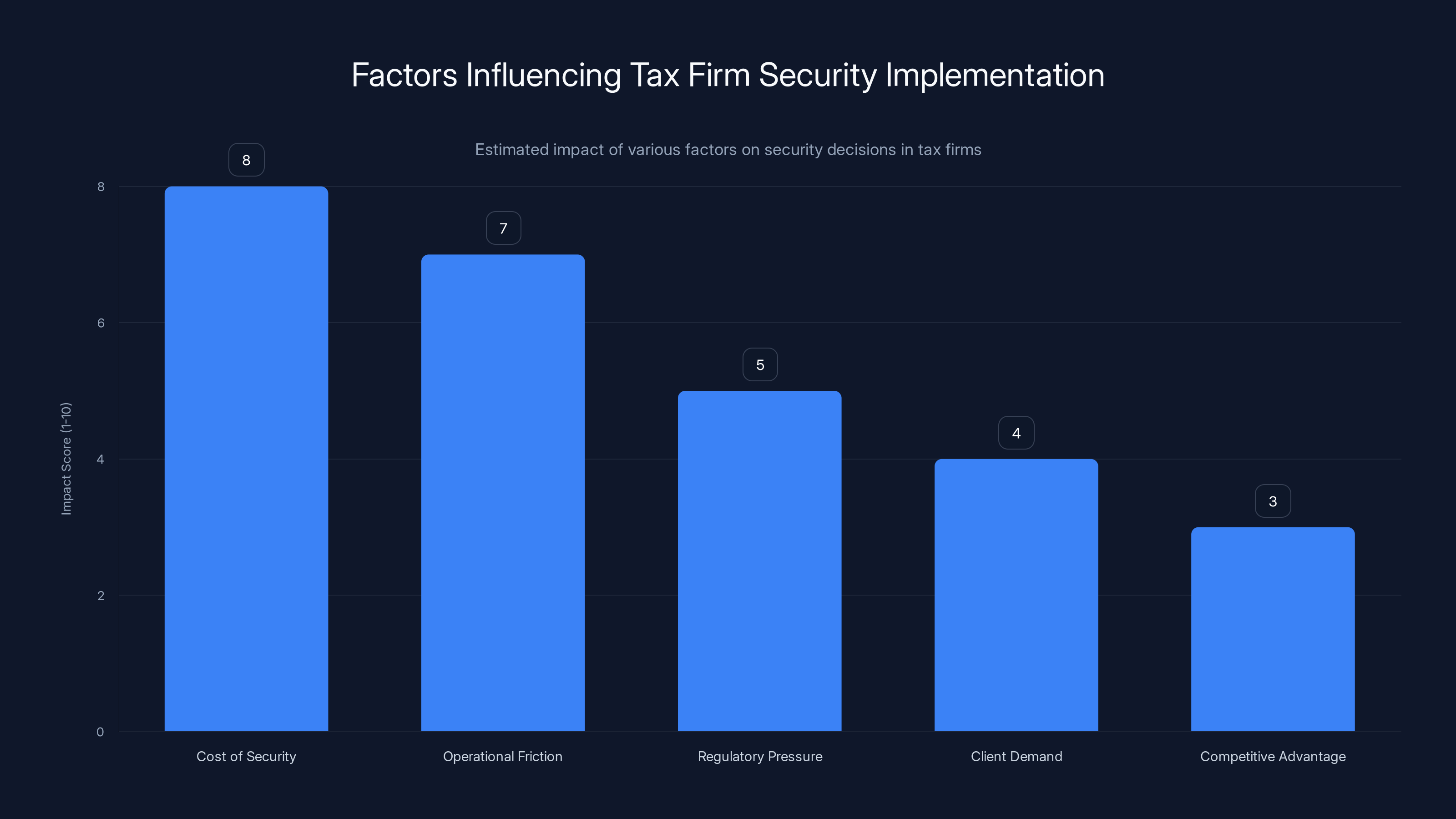
Cost and operational friction are the most significant barriers to implementing strong security in tax firms. Estimated data.
Regulatory and Legal Consequences for Breached Firms
When a tax firm gets breached and data leaks, they don't just face criminal prosecution. They face regulatory action, lawsuits, and mandatory notification requirements.
State Breach Notification Laws
Every US state has breach notification laws. When personal information is breached, firms must notify affected individuals, typically within 30-90 days depending on state. Firms must send letters explaining what data was compromised, what the risks are, and what protections are available (usually credit monitoring for one year).
Sending notifications to thousands of victims is expensive. Firms must validate addresses, handle bounced mail, maintain records of notifications, and respond to victim inquiries. A single breach might trigger $100,000+ in notification costs.
FTC Action
The Federal Trade Commission (FTC) investigates significant breaches, particularly when they involve security failures that violated federal standards. The FTC can impose consent decrees requiring firms to implement security programs, conduct annual audits, and maintain compliance for 20 years. Non-compliance results in significant fines.
IRS Scrutiny
When tax data is breached, the IRS opens investigations. They scrutinize how the firm stored data, what security measures were in place, whether the firm followed IRS Publication 1075 (security guidelines for tax professionals), and whether patterns of fraud emerge from the breach.
If the firm failed to follow required security guidelines, they might face penalties or loss of e-file authorization (the ability to electronically file returns on behalf of clients). For a tax firm, losing e-file authorization is business death.
Lawsuits and Professional Liability
Victims can sue the firm for negligence, breach of contract, and violation of state privacy laws. These lawsuits typically allege the firm failed to implement adequate security, failed to detect the breach in a timely manner, or failed to notify victims promptly.
Even if the firm ultimately wins the lawsuit (because security was "reasonable"), defending the lawsuit costs tens of thousands in attorney fees. Most firms settle rather than fight.
Professional liability insurance might cover some costs, but policies often have exclusions for certain types of breaches or have caps that are exceeded in large incidents.

Red Flags: How to Spot Tax Scams and Phishing
Now that you understand what's at stake, let's talk about protection. You can't control whether your tax firm gets breached, but you can control whether you fall for phishing and scams.
IRS Impersonation
Criminals frequently impersonate the IRS. They call, email, or text claiming you owe back taxes or your return was rejected. They create urgency—"Pay within 24 hours or we'll pursue legal action."
Here's the truth: the IRS rarely initiates contact by phone or email about bills owed. If they do, they mail a formal notice first. The IRS doesn't demand immediate payment via gift cards or wire transfers. These are scam tactics.
If you receive an IRS communication you're unsure about, don't click links or call numbers in the message. Instead, go to irs.gov directly and look up the relevant information, or call the IRS at their official number: 1-800-829-1040.
Tax Firm Impersonation
Criminals also impersonate your tax firm. They send emails claiming to be from your CPA firm or tax preparer, asking you to verify information, update payment details, or re-submit documents.
Red flags: the email comes from a suspicious domain (taxprep@gmail.com instead of @taxfirm.com), contains spelling errors, uses generic greetings ("Dear Client" instead of your name), or requests information your firm already has.
Before responding to any request from your firm, contact them directly using a phone number you find independently (not from the email). Call the main office number and ask if they sent you that message.
Phishing Emails and Links
Phishing emails are designed to look legitimate but contain malicious links or attachments. Common themes during tax season:
- "Your tax return is ready for review—click here to approve"
- "Updated W-2 attached—please confirm receipt"
- "IRS e-file signature needed—click to complete"
- "Urgent: Security alert detected on your account—verify here"
Red flags: unfamiliar sender addresses, generic greetings, urgency language, requests to click links or download attachments, or misspellings of official agency/firm names.
Suspicious Requests
Your tax firm already has your SSN, address, and banking information. They don't need to re-request it. If your firm asks you to re-submit this information or "verify" it by entering it on a website, that's suspicious.
Similarly, legitimate firms don't ask for passwords, PIN codes, or multi-factor authentication codes via email or phone. If someone claiming to be from your firm asks for this, it's a scam.
Social Engineering Attacks
Criminals sometimes call directly, claiming to be from your bank, the IRS, or your tax firm. They use social engineering—building rapport, creating urgency, or claiming to help you solve a problem—to manipulate you into revealing information or taking action.
Social engineering works because it exploits psychology, not technology. You're polite, you want to help, and you trust authority figures. Scammers exploit this.
Defense: hang up, independently verify the caller's identity, and call back using a number you find yourself. If it's really your bank or firm, they won't mind you hanging up to verify their legitimacy.
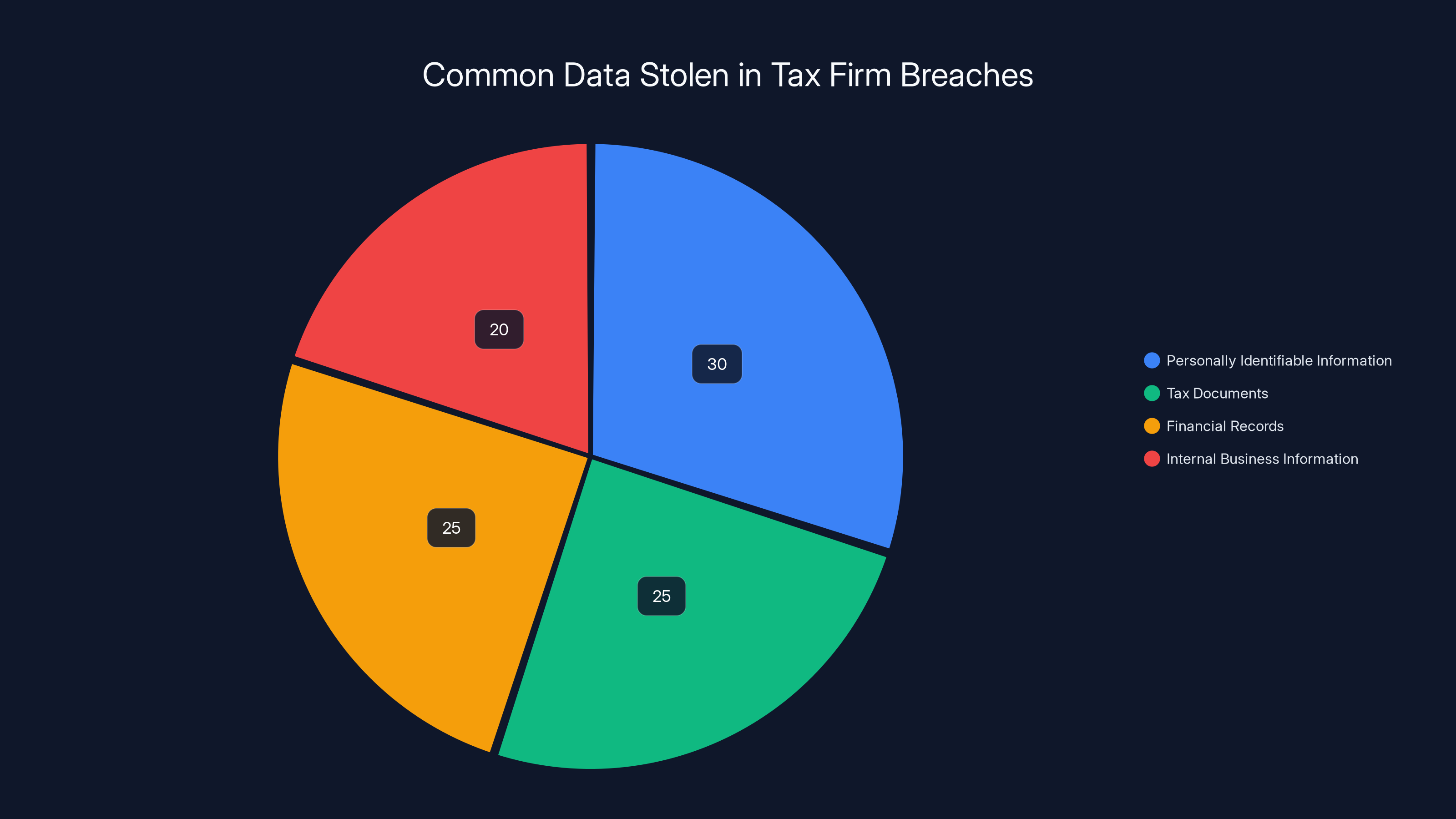
Estimated data shows that personally identifiable information and tax documents are the most commonly stolen data types in tax firm breaches.
What to Do If Your Tax Data Is Compromised
If you suspect your tax data has been compromised—whether through a known breach, phishing attack, or suspicious activity—act immediately. Delays make recovery harder.
Step 1: Notify the Relevant Firm
If you know your tax firm was breached, contact them directly by phone (not email) and ask what happened, what data was compromised, and what notifications they're sending. Ask about credit monitoring services they might be offering (many firms include free credit monitoring as part of breach response).
Document this conversation—date, time, name of person you spoke with, what they said. You might need this record later for dispute resolution.
Step 2: Place a Fraud Alert
Contact one of the three major credit bureaus (Equifax, Experian, or Trans Union) and request a fraud alert. When you place a fraud alert, lenders must verify your identity before opening new accounts in your name.
You only need to contact one bureau—the bureaus share information, so placing an alert with one bureau automatically alerts the others.
Fraud alerts last one year but can be renewed if fraud is still occurring. Here are the contact methods:
- Equifax: 1-888-378-4329 or www.equifax.com
- Experian: 1-888-397-3742 or www.experian.com
- Trans Union: 1-800-680-7289 or www.transunion.com
Step 3: Freeze Your Credit
A credit freeze prevents anyone (including you) from opening new accounts in your name without a PIN. This is stronger than a fraud alert and is the gold standard for identity theft prevention.
To freeze credit, contact all three bureaus and request a freeze. You'll receive a PIN—keep this safe because you need it to unfreeze your credit or authorize new accounts. Freezing is free.
The downside: if you want to apply for credit, you'll need to temporarily unfreeze. This takes a phone call and a few minutes, but it's worth it for the protection.
Step 4: Monitor Your Credit Reports
After placing a fraud alert or freeze, monitor your credit reports for unauthorized accounts. You're entitled to one free credit report per year from each bureau at annualcreditreport.com (the official government site).
Request reports from all three bureaus, staggered throughout the year (one from each bureau every four months). This gives you continuous monitoring without paying for services.
Alternatively, if the breach was recent, consider paid credit monitoring for 1-2 years. Services like Lifelock, Identity Guard, or ID Watchdog include daily monitoring, alert notifications, and recovery support if fraud occurs.
Step 5: File an IRS Form 14039
If you suspect your SSN has been used to file fraudulent tax returns, file Form 14039 (Identity Theft Affidavit) with the IRS immediately. This alerts them to the fraud and triggers an investigation.
You can file online at IRS.gov or mail the form to the IRS. Filing early is critical because if the fraudulent return is processed before you report it, the IRS will reject your legitimate return.
Step 6: File a Police Report
Contact local law enforcement and file a police report for identity theft. You'll need this report for:
- Disputing fraudulent accounts with creditors
- Filing a claim with the FTC
- Recovering costs associated with fraud resolution
Keep a copy of the police report—you might need it to prove fraud to creditors or the IRS.
Step 7: Create an FTC Identity Theft Report
File a report with the Federal Trade Commission (FTC) at Identity Theft.gov. The FTC maintains a database of identity theft complaints and shares information with law enforcement.
Creating an FTC report generates an Identity Theft Report, which is different from a police report but serves similar purposes for creditors and agencies.
Step 8: Dispute Fraudulent Accounts
If you discover fraudulent accounts opened in your name, contact the creditor in writing (certified mail) and dispute the account. Under federal law, creditors have 30 days to investigate your dispute.
Provide copies of:
- Police report
- FTC Identity Theft Report
- Proof that you didn't authorize the account
- IRS fraud report (if tax fraud involved)
Creditors typically remove fraudulent accounts from your credit report once they've concluded the account wasn't authorized.
Step 9: Monitor Tax Filings
For the next 3-5 years, file your tax return early and watch for suspicious returns filed in your name. Use IRS.gov's "Where's My Refund?" tool before tax season to confirm no return has been filed for you.
After filing your legitimate return, monitor the status to ensure it processes normally. If the IRS requests additional documentation or delays processing, respond immediately because this often indicates fraud detection.

Protecting Yourself Before a Breach Happens
The best defense is prevention. You can't control whether your tax firm gets breached, but you can reduce your exposure and make your accounts harder to compromise.
Use Strong, Unique Passwords
Password reuse is a major vulnerability. If a criminal gets your password from one breach, they try it everywhere. Use unique, complex passwords for every account.
A strong password:
- Contains 16+ characters
- Mixes uppercase, lowercase, numbers, and symbols
- Doesn't contain dictionary words or personal information
- Isn't reused across accounts
Passwords like "Tr 0pic@l Sunset#2024!" are strong. Passwords like "password 123" or "ilovecats" are weak.
Using a password manager (like 1 Password, Bitwarden, or Last Pass) makes this practical. You remember one strong master password, and the manager stores and auto-fills unique passwords for every account.
Enable Multi-Factor Authentication (MFA)
Multi-factor authentication requires a second factor beyond your password—usually a code from an app, a text message, or a hardware key.
Even if a criminal steals your password, they can't access your account without the second factor. Enable MFA on:
- Your bank and brokerage accounts
- Your email accounts
- Your tax preparation software
- Any IRS accounts
- Credit monitoring services
Prefer app-based authentication (like Google Authenticator or Microsoft Authenticator) over text messages because text messages can be intercepted. Hardware keys (like Yubi Key) are even more secure.
Verify Your Tax Firm's Security Practices
Before submitting sensitive documents to a tax firm, ask about their security measures. Reputable firms can answer these questions:
- Do you encrypt data in transit and at rest?
- Do you use multi-factor authentication for staff access?
- What's your security patch process? How quickly do you patch vulnerabilities?
- Are systems backed up and tested regularly?
- Do you comply with IRS Publication 1075 security guidelines?
- Have you had a third-party security audit in the last year?
If a firm can't answer these questions or won't discuss security, find another firm. Security-conscious firms are proud of their practices and happy to discuss them.
Minimize Sensitive Information Submission
Some tax firms request excessive documentation. Be selective about what you submit:
- Tax firms need tax returns, W-2s, 1099s, and business financial records
- They don't need your passwords, PIN codes, or online banking credentials
- They don't need copies of insurance policies unless relevant to deductions
- They don't need personal information beyond name, SSN, and address
If a firm asks for information unrelated to tax filing, question why they need it.
Use Separate Email Addresses
Consider using a separate email address for tax-related correspondence. This isolates phishing attacks and makes it harder for criminals to link your tax account to other accounts.
For example:
- Personal email for social media and casual correspondence
- Tax email specifically for tax firm, IRS, and tax software communication
- Financial email for banking, investments, and credit monitoring
This segmentation means if one email is compromised in a breach, your other accounts aren't automatically at risk.
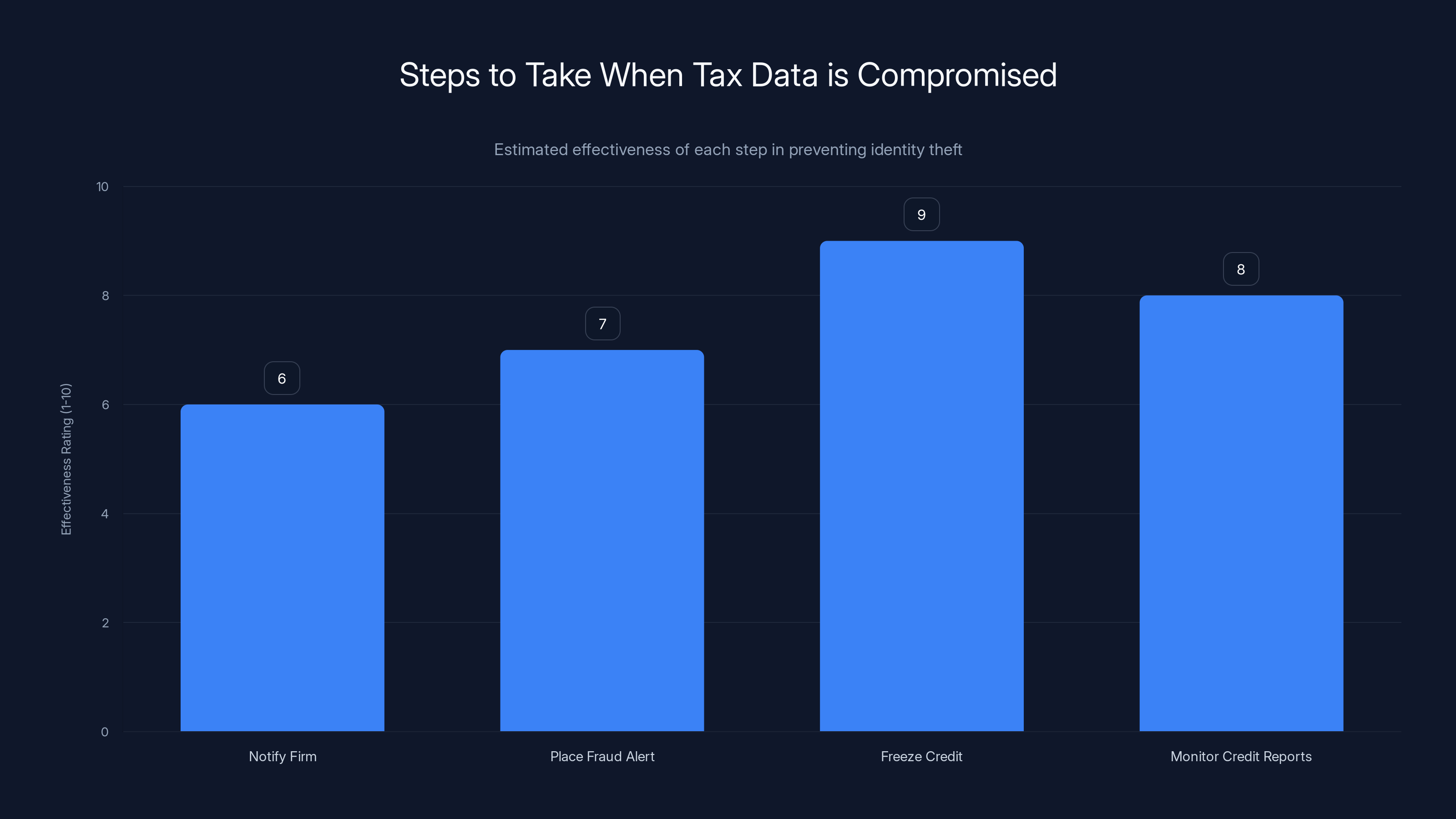
Freezing credit is the most effective step in preventing identity theft, with a rating of 9 out of 10. Estimated data based on typical security practices.
Long-Term Strategies for Tax Data Protection
Beyond immediate protection measures, consider longer-term strategies that reduce your overall risk.
Consider Identity Theft Insurance
Identity theft insurance covers recovery costs if fraud occurs—attorney fees, documentation costs, time spent resolving fraud, lost wages, etc. It's typically inexpensive ($15-30/month) and provides peace of mind.
Note: identity theft insurance doesn't prevent fraud. It reimburses costs after fraud is discovered. But knowing you have support and financial backing for recovery reduces stress.
Review Tax Filing Options
File your own taxes using tax software (like Turbo Tax, H&R Block, or Tax Act) rather than through a tax firm if your return is relatively simple. This eliminates the risk of third-party breach for your most sensitive financial data.
If your return is complex, work with a CPA, but vet their security practices first. You might also consider using a larger firm with more resources for security rather than a small local practice (though size doesn't guarantee security—quality of security practices matters more).
Advocate for Security Standards
If you use a tax firm, advocate for security improvements. Ask about Multi-Factor Authentication implementation, ask how often they audit security, ask what certifications they have.
Vocal clients create pressure for improvements. If multiple clients ask about security, firms are more likely to prioritize it.
Stay Informed About Breaches
Subscribe to breach notification alerts. Websites like Have I Been Pwned (haveibeenpwned.com) let you monitor whether your email address appears in known data breaches.
When new breaches are discovered, you'll receive notifications and can take action immediately rather than discovering compromise months later.

The Business Case for Tax Firm Security Improvements
Why don't all tax firms implement strong security? It's a business problem, not a technical problem.
Security costs money—for tools, staff training, regular audits, compliance consulting, and the overhead of security-first processes. For a small firm already operating on tight margins, these costs are significant.
Security also creates friction. Multi-factor authentication means users need to provide a second factor every time they authenticate. Strict access controls mean staff must request permissions for files. Encryption requires key management. These processes slow work down.
During tax season, when speed is everything, security often loses. Firms are incentivized to move fast and process returns quickly. Security feels like an obstacle.
Moreover, the financial incentive is misaligned. The firm's clients (taxpayers) pay nothing extra for security. The firm bears all the costs. They derive no direct benefit from security until a breach occurs—and if they never breach, they never see the return on their security investment.
This will likely change as regulatory pressure increases. The IRS, state governments, and the FTC are all pushing for better security standards. Eventually, security failures will result in enough regulatory action and client litigation that firms will have to prioritize it.
But until then, client pressure and competition on security might be the only incentives. Choose firms with strong security, encourage others to do the same, and report security incidents to regulators.
Preparing for Tax Season: A Checklist
Tax season is approaching. Before you submit sensitive documents, work through this checklist.
Security Fundamentals:
- Password manager set up with strong, unique passwords
- Multi-factor authentication enabled on all financial accounts
- Credit freeze placed with all three bureaus (or fraud alert if you prefer)
- Credit reports reviewed recently for unauthorized accounts
- Operating system and security software updated
- Backup of important files created and tested
Tax Firm Selection:
- Tax firm security practices researched and discussed
- Tax firm reviews and complaint history checked
- Tax firm's past breach history (if any) researched
- Email address used for tax communication is separate from personal email
- Only necessary documents will be submitted (no extra personal information)
Ongoing Monitoring:
- Identity theft monitoring service or credit monitoring selected
- Have I Been Pwned account set up for breach notifications
- Calendar reminder set to file taxes early
- Plan in place for what to do if fraud is discovered
Documentation:
- Important passwords and recovery information stored securely
- Tax firm contact information saved
- IRS contact information saved
- Police department non-emergency number saved
- FTC Identity Theft.gov bookmark saved

Common Myths About Tax Data Protection
Let's clear up some misconceptions.
Myth: "Small firms never get breached. They're under the radar."
Reality: Small firms are actually attractive targets. They typically have fewer security defenses than large firms, but hold data just as valuable. Attackers know small firms often can't afford to refuse ransom demands. Small firms represent easier targets with equal payout potential.
Myth: "If my tax firm gets breached, they'll pay the ransom and recover my data."
Reality: Even if the firm pays, your data might still be leaked. Ransomware gangs often leak data anyway after receiving payment, or copy data before deleting it and leak it later when negotiations break down. Paying doesn't guarantee confidentiality.
Myth: "I can fix identity theft by myself without professional help."
Reality: While simple cases might be DIY-solvable, complex identity theft cases (multiple fraudulent accounts, tax fraud, business email compromise) require professional help. Identity theft services and attorneys specializing in identity theft recovery are worth the investment for complex cases.
Myth: "Freezing my credit will prevent me from getting new credit."
Reality: A credit freeze prevents others from opening accounts in your name, but you can unfreeze temporarily when you legitimately need credit. It's inconvenient but not blocking.
Myth: "The IRS will help me if my tax data is breached."
Reality: The IRS has limited resources for individual fraud victims. They'll investigate if you file a Form 14039, but response times are slow (often 6+ months). You need to take proactive steps yourself; don't wait for IRS help.

FAQ
What is the Lynx ransomware gang?
Lynx is a Russia-linked ransomware gang that targets professional services firms, particularly tax and accounting practices. They compromise networks, encrypt files, exfiltrate data, and demand ransom payments. If firms refuse to pay, they leak stolen data publicly. Lynx recently claimed responsibility for breaching CSA Tax & Advisory, a Massachusetts accounting firm, stealing data from thousands of taxpayers including SSNs, tax returns, and health insurance agreements.
How do tax firms typically get breached?
Most tax firm breaches start with phishing emails sent to employees. These emails trick staff into clicking malicious links or opening infected attachments, which install malware or harvest login credentials. Once inside the network, attackers move laterally to servers storing client data, copy the data, install ransomware to encrypt systems, and demand payment. Some breaches also exploit unpatched vulnerabilities in web-facing systems like client portals. Tax firms are vulnerable because they often run legacy systems, lack sufficient IT staff, and experience operational pressure during peak tax season that drives shortcuts on security.
What data do criminals steal in tax firm breaches?
Criminals steal personally identifiable information (names, Social Security numbers, addresses), tax documents (tax returns, W-2s, 1099s), financial records (bank account numbers, investment details, business revenue figures), and internal business information (emails, approval workflows, vendor relationships). This data enables identity theft, fraudulent tax returns, credit fraud, insurance fraud, and business email compromise attacks. The combination of data makes victims extremely vulnerable—criminals have everything needed to pass identity verification checks and commit sophisticated fraud.
How can I tell if I'm being phished by a tax firm or IRS scammer?
Learn to spot red flags: emails from suspicious or misspelled domains, generic greetings instead of your name, requests for sensitive information your firm already has, urgent language demanding immediate action, links or attachments, poor spelling or grammar, and requests for passwords or MFA codes. The IRS and legitimate tax firms never request passwords, PIN codes, or sensitive information via email or unsolicited phone calls. If you're uncertain, don't click links or open attachments—instead, call the firm or IRS directly using numbers you find independently, and ask whether they sent the message.
What should I do immediately if I think my tax data was breached?
Act fast: contact your tax firm by phone to confirm the breach, place a fraud alert with one of the three credit bureaus (which automatically alerts all three), freeze your credit with all three bureaus if you prefer maximum protection, monitor credit reports for unauthorized accounts, file a police report, create an FTC Identity Theft Report at Identity Theft.gov, and file IRS Form 14039 if you suspect tax fraud. Document everything and keep records of all communications. The faster you act, the easier it is to prevent criminals from using your information.
Can I prevent my tax firm from being breached?
You can't directly prevent a breach, but you can reduce risk by choosing tax firms that prioritize security, asking about their security practices before submitting documents, using a separate email address for tax correspondence, minimizing information you submit (don't provide more than necessary), and enabling multi-factor authentication on your tax software account. You can also advocate for security improvements with your tax firm and use services like tax software or larger firms with greater security resources if your return is simple enough. Most importantly, even if your firm is breached, you can mitigate damage through credit monitoring and fraud alerts.
How long does it take to recover from tax identity theft?
Simple cases (one fraudulent account) might take 2-6 weeks to resolve. Complex cases (multiple fraudulent accounts, tax fraud, business impact) can take 6-12 months or longer. On average, identity theft victims spend 100-200+ hours resolving fraud through credit disputes, IRS correspondence, account closures, and documentation. This is why identity theft insurance and professional recovery services are valuable—they handle much of this work and manage the process from start to finish.
Should I freeze my credit or just place a fraud alert?
Credit freezes provide stronger protection (preventing anyone from opening accounts without your PIN), while fraud alerts are less restrictive (allowing you to open accounts more easily but requiring lenders to verify your identity). If you suspect active fraud, a freeze is better. If you want convenience and fraud seems less likely, a fraud alert is sufficient. You can upgrade from a fraud alert to a freeze later if needed, or use both (fraud alert now, freeze if fraud is discovered). Freezes last indefinitely and can be unfrozen when you need credit; fraud alerts last one year but are renewable.
Is identity theft insurance worth buying?
Identity theft insurance typically costs $15-30 monthly and covers recovery costs (attorney fees, documentation, lost wages, etc.) if fraud occurs. It doesn't prevent fraud, but it reimburses costs and often includes recovery support services that simplify the resolution process. For people who've already been breached or are at higher risk, it's often worth the cost. For the general population, it's optional—the financial risk is manageable through DIY recovery, though professional help can accelerate resolution.
How can I monitor whether my information was in a data breach?
Use Have I Been Pwned (haveibeenpwned.com), a free service where you enter your email address and see if it appears in known breaches. You can also subscribe to notifications, and the service will alert you when your email appears in future breaches. Alternatively, subscribe to credit monitoring services, which include ongoing monitoring and alerts. Most credit monitoring is paid, but the value comes from continuous monitoring rather than one-time checking, and peace of mind knowing you'll be alerted if fraud patterns emerge.

Final Thoughts: Taking Control of Your Tax Security
Tax season opens a dangerous window for your personal and financial security. Criminal gangs actively target tax firms knowing they hold concentrated, valuable data. When breaches happen, the damage is severe: identity theft, fraudulent tax filings, credit fraud, insurance fraud, and in business cases, millions in losses.
But you're not helpless. The steps outlined in this guide—from vetting your tax firm's security to implementing your own protections like credit freezes and multi-factor authentication—significantly reduce your risk and your recovery time if fraud occurs.
Start now, before tax season hits. Enable multi-factor authentication on your financial accounts. Freeze or monitor your credit. Choose a tax firm with strong security practices. These steps take a few hours but provide months of protection.
If you suspect your information has been compromised, act immediately. The first 30 days are critical. Contact your firm, place fraud alerts, freeze your credit, and monitor accounts closely. Early action prevents most fraud from succeeding.
And if you work in a tax firm or know people who do, advocate for security improvements. Ask about their practices. Request upgrades. Suggest they follow IRS Publication 1075 guidelines. Your pressure creates incentives for the security improvements that protect everyone's data.
Tax season doesn't have to be a security nightmare. With the right preparation and quick action if fraud occurs, you can protect yourself and your financial future.

Key Takeaways
- Russia-linked ransomware gangs actively target tax firms during filing season to steal SSNs, tax returns, and banking information from thousands of taxpayers
- Stolen tax data enables criminals to commit identity theft, fraudulent tax refunds, credit fraud, and insurance fraud with minimal detection risk
- Tax firms are vulnerable because they concentrate sensitive data, often run legacy systems, and face time pressure during peak season that creates security shortcuts
- Phishing emails remain the primary attack vector; learning to spot red flags (suspicious domains, generic greetings, urgent requests) protects against compromise
- If your data is compromised, immediate actions matter: fraud alerts, credit freezes, police reports, and IRS notification within 30 days prevent most fraud from succeeding
- Long-term protection requires multi-factor authentication on all accounts, strong unique passwords using a password manager, credit monitoring, and vetting tax firm security practices
Related Articles
- Condé Nast Data Breach: 40 Million Records Exposed [2025]
- The Worst Hacks of 2025: A Cybersecurity Wake-Up Call [2025]
- SMS Scams and How to Protect Yourself: Complete Defense Guide [2025]
- Holiday VPN Security Guide: Expert Tips for Safe Festive Season [2025]
- Holiday Email Scams 2025: How to Spot and Stop Them [Updated]
- How to Explain VPN Importance to Your Parents: 2025 Guide
![Tax Season Security Threats: How to Protect Your Data [2025]](https://tryrunable.com/blog/tax-season-security-threats-how-to-protect-your-data-2025/image-1-1767114733491.jpg)



