Panera Bread Data Breach: 14 Million Records Exposed [2025]
Last week, your favorite fast-casual restaurant chain became the latest victim of a sophisticated cyberattack. Panera Bread, with thousands of locations across North America, fell victim to Shiny Hunters, a notoriously aggressive hacking group that stole 14 million customer records. We're talking names, addresses, email addresses, phone numbers, and account details all compromised in a single breach.
Here's what makes this particularly worrying: the attackers didn't even need to crack through Panera's perimeter defenses the traditional way. They used a technique that's becoming increasingly common in 2025, exploiting something most companies rely on daily to keep their systems secure. Microsoft Entra single sign-on (SSO) became the weak link, and it cost millions of customers their personal information.
But this isn't just about Panera. The breach reveals something much bigger about how modern authentication systems are being weaponized. Panera wasn't alone. Car Max, Edmunds, Crunchbase, and Betterment all fell victim to the same attack vector. And the method? Voice phishing targeting Okta authentication codes, a technique that's sophisticated enough to bypass most security protocols.
If you're a Panera customer, you need to understand what information was stolen and what steps you should take right now. Even if you've never ordered a Cobb salad or Broccoli Cheddar soup from Panera, this breach matters because it exposes a vulnerability that could affect any company using SSO authentication. This is a wake-up call about the state of corporate cybersecurity in 2025.
Let's break down exactly what happened, why it happened, and most importantly, what you need to do about it.
TL; DR
- 14 million Panera customer records stolen including names, addresses, emails, phone numbers, and account details
- Attack vector: Microsoft Entra SSO breach exploited via sophisticated voice phishing campaign targeting Okta authentication codes
- Shiny Hunters responsible for the attack, also targeting Car Max, Edmunds, Crunchbase, and Betterment with the same technique
- No data encryption used during exfiltration, meaning all stolen information is accessible to attackers
- Immediate action required: Change your Panera password, monitor financial accounts, enable multi-factor authentication across all platforms
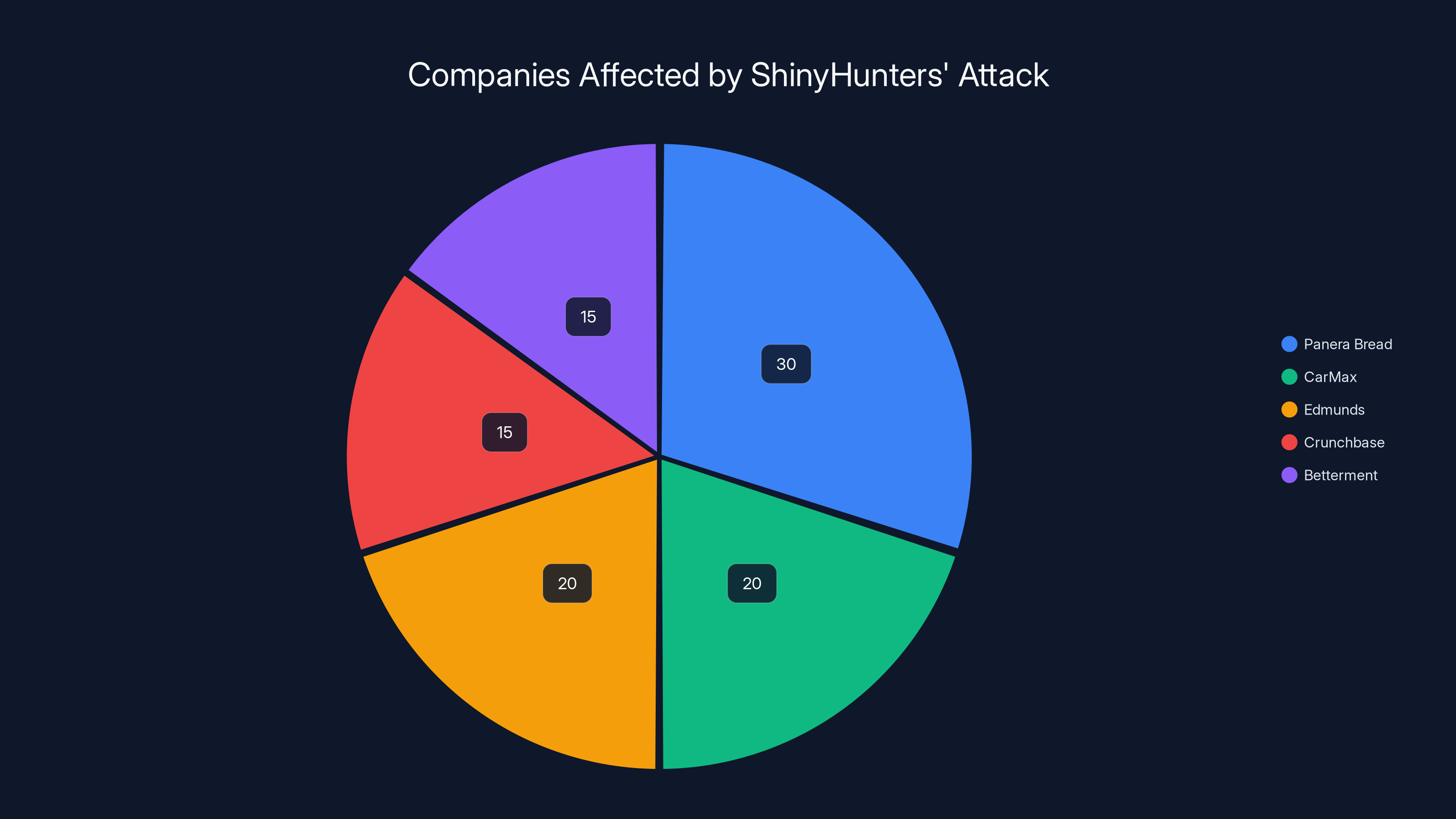
Estimated data shows Panera Bread was the most significantly affected company by ShinyHunters' voice phishing attack, followed by CarMax and Edmunds.
What Exactly Was Stolen in the Panera Breach?
When Panera confirmed the breach, the scope became immediately clear: this wasn't a minor incident affecting a few thousand users. We're talking about 14 million customer records, representing roughly 25-30% of Panera's estimated customer base in the United States and Canada. That's a staggering number when you think about it.
The attackers exfiltrated approximately 760 MB of compressed data from Panera's systems. Uncompressed, that's roughly 2-3 GB of raw customer information. The data included:
- Full names of customers
- Email addresses (both primary and secondary accounts)
- Postal addresses (home addresses, not just billing addresses)
- Phone numbers (mobile and sometimes home numbers)
- Account details (loyalty program information, account preferences, transaction history)
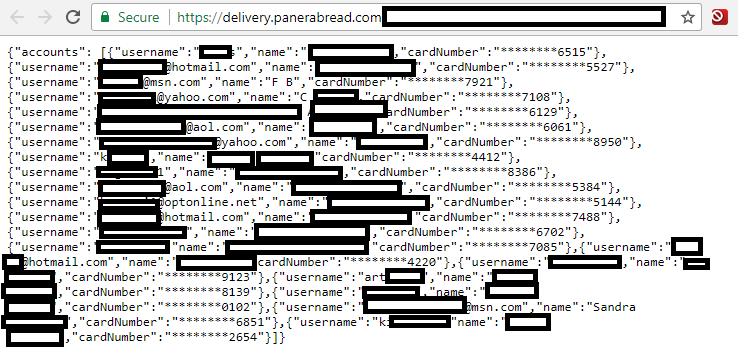
What's particularly concerning is that none of this data was encrypted during the exfiltration process. The attackers could access it immediately without needing to crack encryption. This is in stark contrast to data breaches from previous years, where companies often claimed "the stolen data was encrypted so it's not a real risk." Not here. Shiny Hunters had direct, readable access to everything.
The timing of the discovery is also worth noting. Panera didn't discover the breach themselves. The breach was announced publicly when Shiny Hunters posted the stolen data on their leak site, demanding payment for the information. This suggests the attackers had undetected access to Panera's systems for an unknown period. Without a clear timeline of when the breach occurred, it's impossible to know how long your personal information was exposed.
For Panera loyalty program members, the breach is even more serious. Attackers now have your ordering history, preferred locations, payment methods on file, and dietary preferences. All of this personal behavioral data can be used for targeted phishing campaigns, identity theft, or sold on the dark web to other criminals.
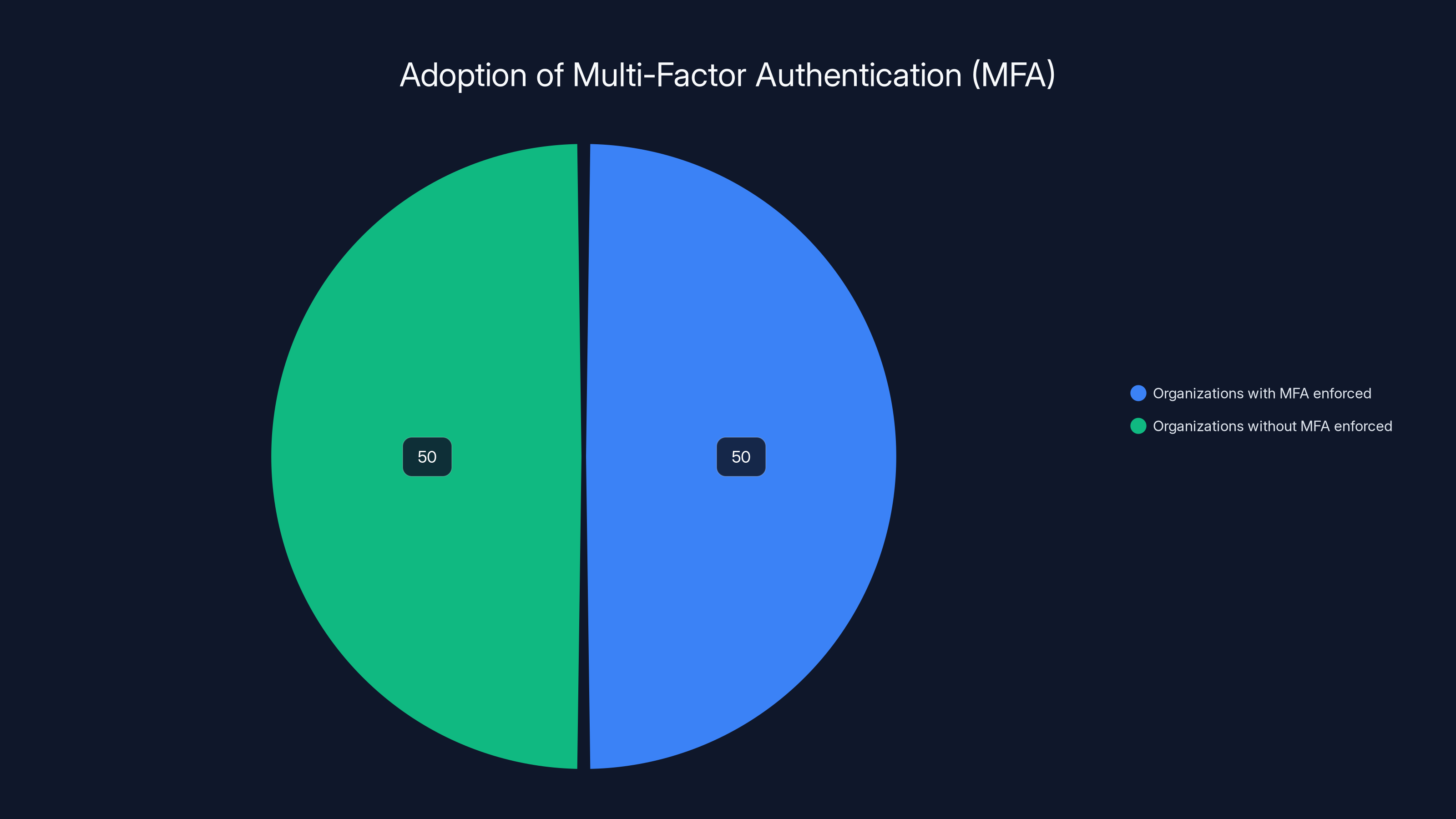
An estimated 50% of organizations worldwide have enforced multi-factor authentication across all accounts, highlighting a significant gap in identity security measures. (Estimated data)
The Attack Method: Microsoft Entra SSO Breach
Here's where the technical details get interesting and frightening in equal measure. Shiny Hunters didn't brute-force their way into Panera's systems. They didn't exploit a zero-day vulnerability in some obscure software. They used something far more elegant and devastating: they compromised the company's Microsoft Entra single sign-on system.
Single sign-on, or SSO, is one of those technologies that seems brilliant until someone exploits it. Instead of employees maintaining dozens of different passwords for different systems, they log in once with their corporate credentials, and that single authentication grants them access to everything they need: email, collaboration tools, internal databases, customer systems, cloud storage, payment processing.
For IT administrators, SSO is a dream. It reduces password fatigue, simplifies user management, and supposedly increases security by centralizing authentication. When it works, it's seamless. You log in once in the morning, and you're authenticated to all your applications.
But here's the critical vulnerability: if someone compromises that single point of entry, they've essentially opened a master key to every door in the building. That's what happened with Panera.
Microsoft Entra (formerly known as Azure AD) is Microsoft's cloud-based identity and access management service. It's trusted by millions of organizations worldwide because it's integrated into Microsoft 365, Azure, and thousands of third-party applications. When Panera's employees logged in through Entra, they granted themselves access to customer databases, payment systems, internal networks, and administrative tools.
The question everyone's asking is: how did Shiny Hunters compromise Entra? The answer involves something called voice phishing, and it's scarily effective.
Voice Phishing and the Okta Campaign
About a week before the Panera breach became public, Okta issued a warning. The company had detected a sophisticated voice phishing campaign targeting its employees and customers. Voice phishing, sometimes called "vishing," combines old-school social engineering with modern technology.
Here's how it typically works: An attacker calls a company employee, often impersonating someone from IT support, their bank, or another trusted source. They use psychological tactics to convince the employee to reveal sensitive information or perform an action that compromises security. In this case, the attackers were specifically targeting Okta authentication codes.
Okta provides an authenticator app that generates one-time codes required for multi-factor authentication. Even if someone steals your password, they can't log into your account without this code. It's one of the strongest security measures available.
But here's the vulnerability: if an attacker calls you and says "We've detected suspicious activity on your account. We need you to confirm your authentication code for verification purposes," many people will comply. They're not handing over their password. They're just reading off a number that looks temporary and harmless.
The catch? That code only works for a few minutes. But if an attacker has it and someone's password, they can log in within that window. The attacker now has legitimate access to the account.
Okta warned that this campaign was targeting multiple companies and their employees. The goal was to obtain credentials and authentication codes that would allow attackers to access corporate systems. Panera's employees apparently fell victim to these attacks. Once the attackers had valid Panera employee credentials with Entra access, they could move through the system like legitimate users.
This is particularly dangerous because it bypasses most traditional security measures. Firewalls can't stop you if you're logging in with real credentials. Intrusion detection systems won't flag you as a threat. Your actions look exactly like a regular employee accessing systems they're supposed to access.
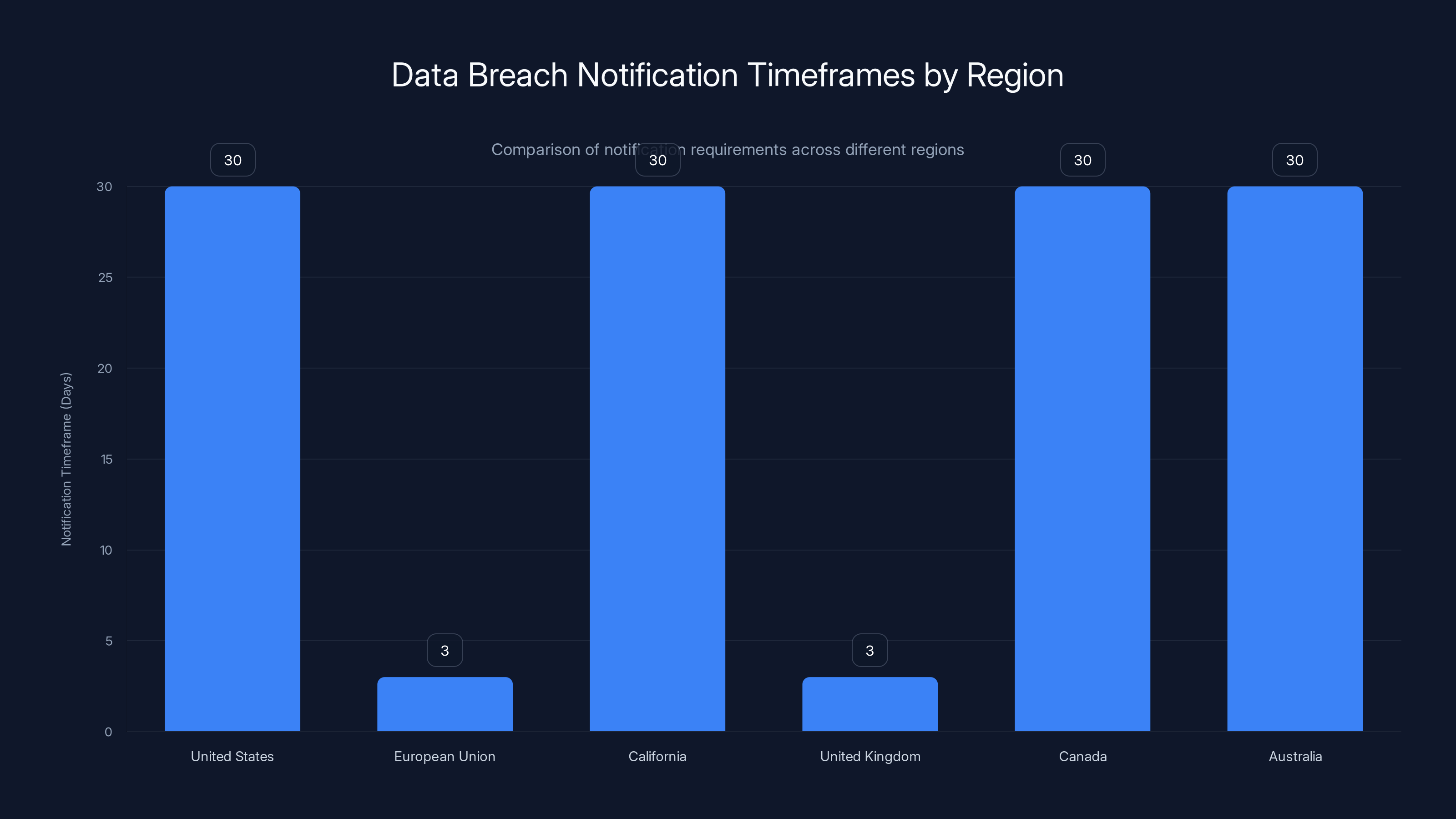
The European Union and the United Kingdom have the strictest data breach notification requirements, mandating companies to report within 3 days. Other regions typically allow up to 30 days.
Shiny Hunters: Who They Are and Why This Matters
Shiny Hunters isn't some random gang of script kiddies operating out of a basement. They're one of the most sophisticated and active hacking groups in the world right now. And what makes them particularly dangerous is their willingness to adapt their tactics and their complete lack of moral boundaries.
The group became infamous around 2019-2020 when they started conducting data breaches and selling stolen information on the dark web. Unlike traditional ransomware groups that encrypted data and demanded payment for decryption keys, Shiny Hunters took a different approach. They simply stole data without encryption and demanded payment for not selling it to competitors or releasing it publicly.
It sounds subtle, but it's brilliant from a criminal perspective. They don't need to maintain decryption infrastructure. They don't need to negotiate with victims. They steal, they announce it, they set a price, and they either get paid or they publish the data. The threat of public release is often enough to motivate payment.
Over the years, Shiny Hunters has claimed responsibility for breaches affecting major companies including Clover Health, Wattpad, Unacademy, a major Indian telecommunications company, and countless others. They're known for targeting companies with valuable customer data: healthcare providers, e-commerce platforms, financial institutions, and apparently, fast-casual restaurant chains.
What's changed recently is their sophistication level. The Panera breach, coordinated with the Okta voice phishing campaign, shows they're not just opportunistic attackers anymore. They're conducting targeted campaigns with specific objectives, using multiple attack vectors, and coordinating across multiple companies simultaneously.
The fact that they also targeted Car Max, Edmunds, Crunchbase, and Betterment with the same technique suggests they either have a larger operation than previously thought or they're selling their tactics to other groups. Either way, it's bad news for corporate security teams everywhere.
The Broader Context: SSO Attacks in 2025
Panera isn't an isolated incident. What we're seeing is a trend of sophisticated attackers focusing on authentication systems as their primary target. This makes sense from an attacker's perspective. Why spend months trying to crack through firewalls and IDS systems when you can just walk through the front door with legitimate credentials?
The irony is that SSO was supposed to make companies more secure. By consolidating authentication, IT teams thought they could better control access, enforce stronger password policies, and monitor suspicious activity in one place. And in theory, they're right. The problem is execution.
Most SSO implementations assume that once someone is inside the corporate network, they're trustworthy. The assumption breaks down when attackers have legitimate credentials obtained through social engineering, phishing, or password breaches from other sources.
Several other major companies have fallen victim to similar attacks in recent months. Each one follows a similar pattern: attackers obtain employee credentials through phishing or social engineering, they use those credentials to access the SSO system, they bypass additional security measures, and they steal data wholesale.
The attack surface is particularly large because SSO systems are often poorly monitored. An IT team might have alerting for direct attacks on servers but not for legitimate-looking authentication events. An employee logging in from an unusual location or at an unusual time? They're probably traveling. An employee accessing systems they don't normally use? Could be a new project. These legitimate-seeming activities are exactly what attackers use to cover their tracks.
The solution isn't to abandon SSO. The technology is too valuable and too widely deployed. But companies need to implement additional security layers: continuous verification, behavioral analysis, and better employee training on social engineering tactics.

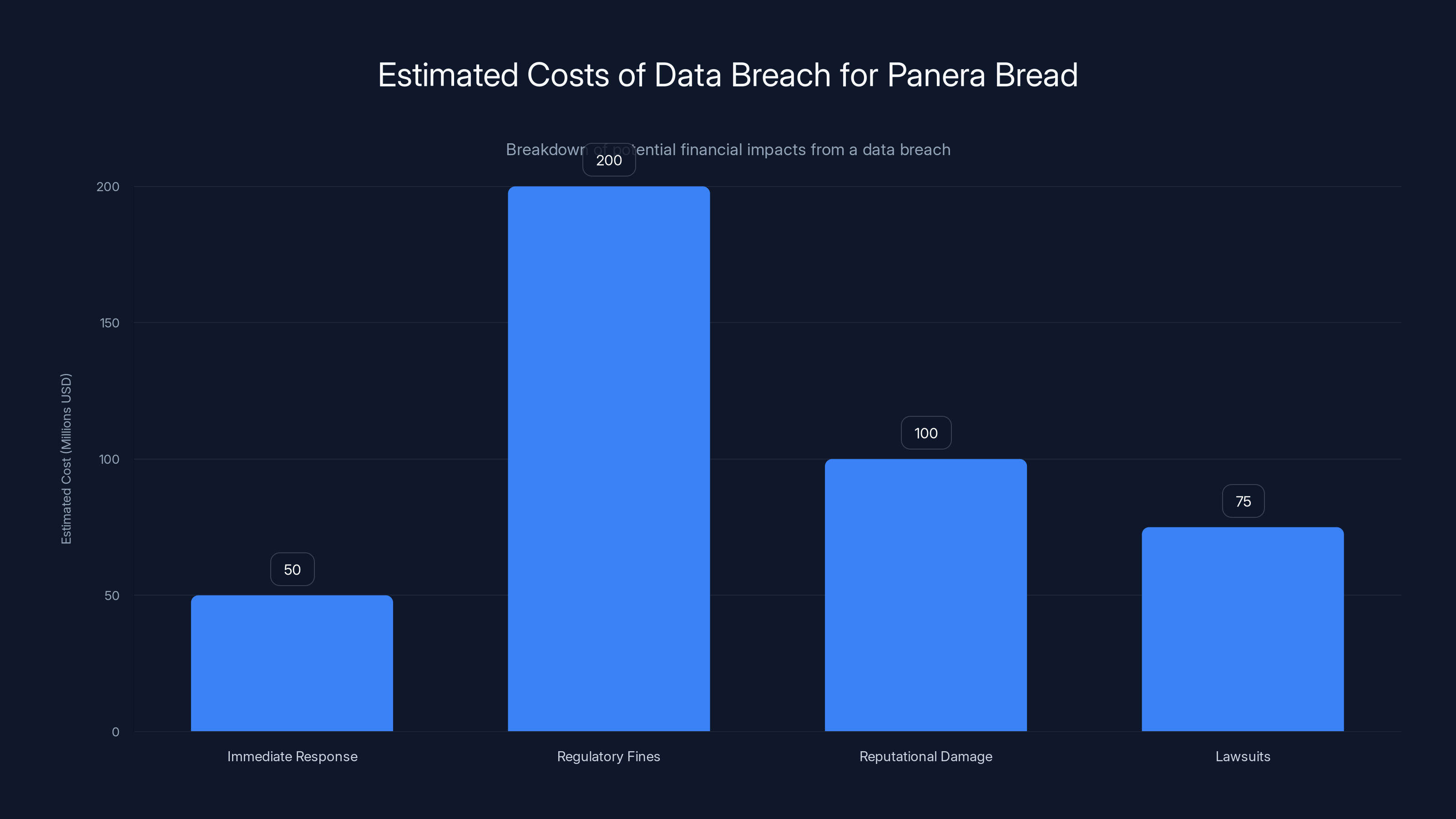
Estimated data shows that regulatory fines could be the largest cost, potentially reaching $200 million, followed by reputational damage and lawsuits. Immediate response costs are also significant.
What Data Breaches Like This Cost Companies
Let's talk about the financial impact, because it's staggering. Panera Bread now faces a cascade of costs that will ripple through their operations for years.
First, there's the immediate response cost. Panera needs to hire forensic investigators to determine exactly what happened, how long the attackers had access, and what systems were compromised. They need to bring in cybersecurity firms to plug the vulnerability and prevent future breaches. They need to notify 14 million customers (a legal requirement under most data breach notification laws). They need to set up credit monitoring services for affected customers. We're talking tens of millions of dollars, minimum.
Then there's the regulatory fallout. Depending on which states and countries affected customers are from, Panera faces fines from multiple regulatory bodies. Some states have explicit penalties for data breaches. The European Union has GDPR, which carries fines up to 4% of global annual revenue. For a company like Panera, that could be hundreds of millions of dollars.
Then there's reputational damage. Every news article about the breach, every notification email customers receive, every discussion on social media erodes customer trust. Panera's brand association shifts from "reliable quick lunch" to "company that lost my personal information." Customers remember breaches. They switch to competitors. This affects revenue for quarters, sometimes years.
Class action lawsuits are almost inevitable. Customers will claim that Panera failed to implement adequate security, that they're entitled to compensation for the breach, for credit monitoring costs, for their time spent protecting themselves. Even if Panera ultimately wins these cases (which is rare), the legal costs are enormous.
Insurance might cover some of these costs, but cyber insurance policies have limits and exclusions. A breach of this magnitude might exceed the coverage limit entirely.
Industry analysts estimate that a data breach affecting millions of records can cost companies

Immediate Steps if You're Affected
If you've ever ordered from Panera Bread, especially if you had an online account, you should assume your information was stolen. This isn't paranoia. This is basic threat modeling.
First priority: change your Panera password immediately. Don't use a password you've used anywhere else. If you're recycling passwords across multiple websites (and statistically, most people are), then attackers now have credentials to try against other platforms. An attacker with your email address and password can attempt to log into Gmail, your bank, Pay Pal, Amazon, and dozens of other services.
Second: enable multi-factor authentication on every account where you've used a similar password. This is tedious, yes. Do it anyway. Multi-factor authentication is the single most effective security measure you can implement as an individual user.
Third: monitor your credit reports and financial accounts. Check your credit score through one of the major bureaus (Equifax, Experian, Trans Union). Set up credit monitoring alerts so you're notified if anyone tries to open a new account in your name. Review your bank and credit card statements for unauthorized transactions.
Fourth: be suspicious of any emails you receive claiming to be from Panera about the breach. Attackers will attempt to capitalize on the publicity by sending phishing emails that appear to be from Panera or services offering "free credit monitoring." These are almost always scams. If you want to check if a communication is legitimate, contact Panera directly through their official website, not by clicking links in emails.
Fifth: consider a credit freeze. This prevents attackers from opening new accounts in your name because creditors won't be able to check your credit report. It's an inconvenience if you're applying for new credit yourself, but it's one of the strongest protections available.

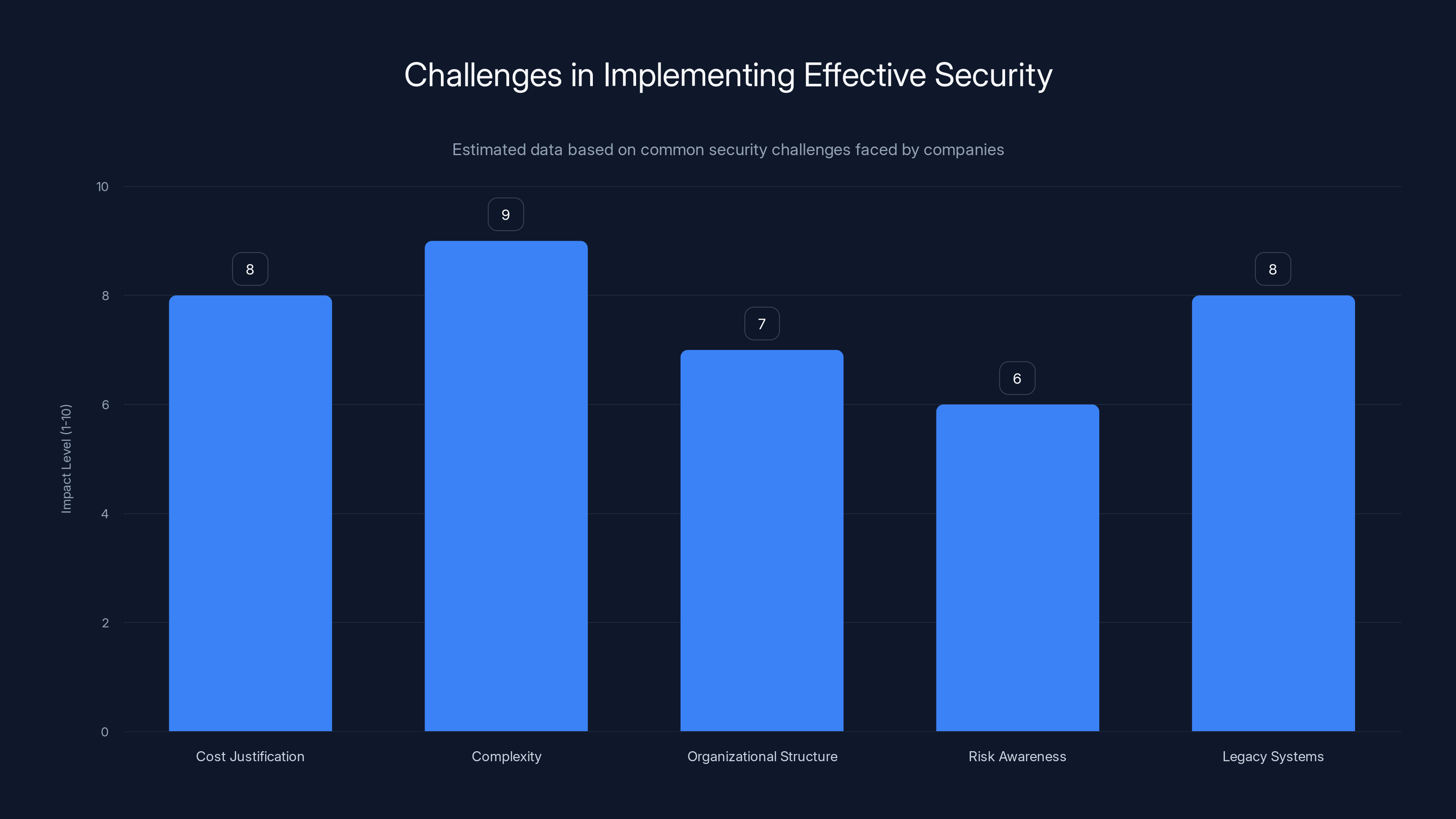
Estimated data shows that complexity and cost justification are major challenges in implementing effective security, with legacy systems also posing significant issues.
How Companies Should Respond to Breaches
While individual users should focus on protecting themselves, companies like Panera should be implementing comprehensive remediation strategies. This is what responsible incident response looks like.
Step one: containment. The moment a breach is discovered, you need to isolate affected systems, revoke compromised credentials, and prevent further data exfiltration. This should happen within hours, not days. Every hour the breach goes uncontained is an hour attackers could be stealing more data or moving deeper into your network.
Step two: investigation. Bring in third-party forensic experts. You need to understand exactly what happened: how attackers got in, what systems they accessed, how much data they stole, how long they had access. This investigation should be comprehensive and documented thoroughly because you'll need this information for regulators and lawyers.
Step three: notification. Once you understand the scope of the breach, notify affected customers immediately. This is required by law in virtually every jurisdiction. Notifications should include what information was stolen, what the company is doing to remediate, and what customers should do to protect themselves.
Step four: remediation. Patch the vulnerability, strengthen authentication, implement additional monitoring, and redesign systems to prevent similar attacks. For Panera, this likely means overhauling their SSO implementation, implementing stronger authentication protocols, and improving employee security training.
Step five: transparency and accountability. Cooperate with regulators, provide regular updates to customers, and take responsibility publicly. The companies that recover best from breaches are the ones that are honest about what went wrong and what they're doing to fix it.
Step six: ongoing monitoring. Even after containment and remediation, the attack surface is still larger than before. Attackers have customer data. They might sell it. Criminals might use it for identity theft. The company needs to continue monitoring and responding to these downstream impacts for years.

The Role of Okta and Microsoft in This Breach
Here's a question that's worth asking: how much responsibility do Okta and Microsoft bear for this breach?
Okta, for their part, identified the voice phishing campaign and issued a warning to customers. They provided guidance on how to detect and prevent similar attacks. By security industry standards, this is responsible disclosure. They didn't hide the vulnerability. They told people to be careful.
But one could argue that Okta's authentication system is too vulnerable to social engineering attacks. If an attacker can convince an employee to read off a single-use code, that shouldn't grant access to corporate systems. Better design would involve requiring additional confirmation, showing which application is requesting access, or implementing device binding so codes only work from registered devices.
Microsoft had a similar opportunity. Entra is the authentication gateway for millions of organizations. If even a small percentage of those organizations are compromised through social engineering, that's millions of people with breached data. Microsoft could implement more rigorous verification for suspicious login attempts, better threat detection for unusual access patterns, or stronger pushback against traditional password-based authentication in favor of passwordless systems.
That said, the primary responsibility for this breach falls on Panera. They're the ones who failed to adequately train employees on social engineering tactics. They're the ones who didn't implement sufficient monitoring and alerting for unusual authentication events. They're the ones who trusted their SSO system without implementing compensating controls.
Authentication companies provide the tools. Organizations need to use them properly.

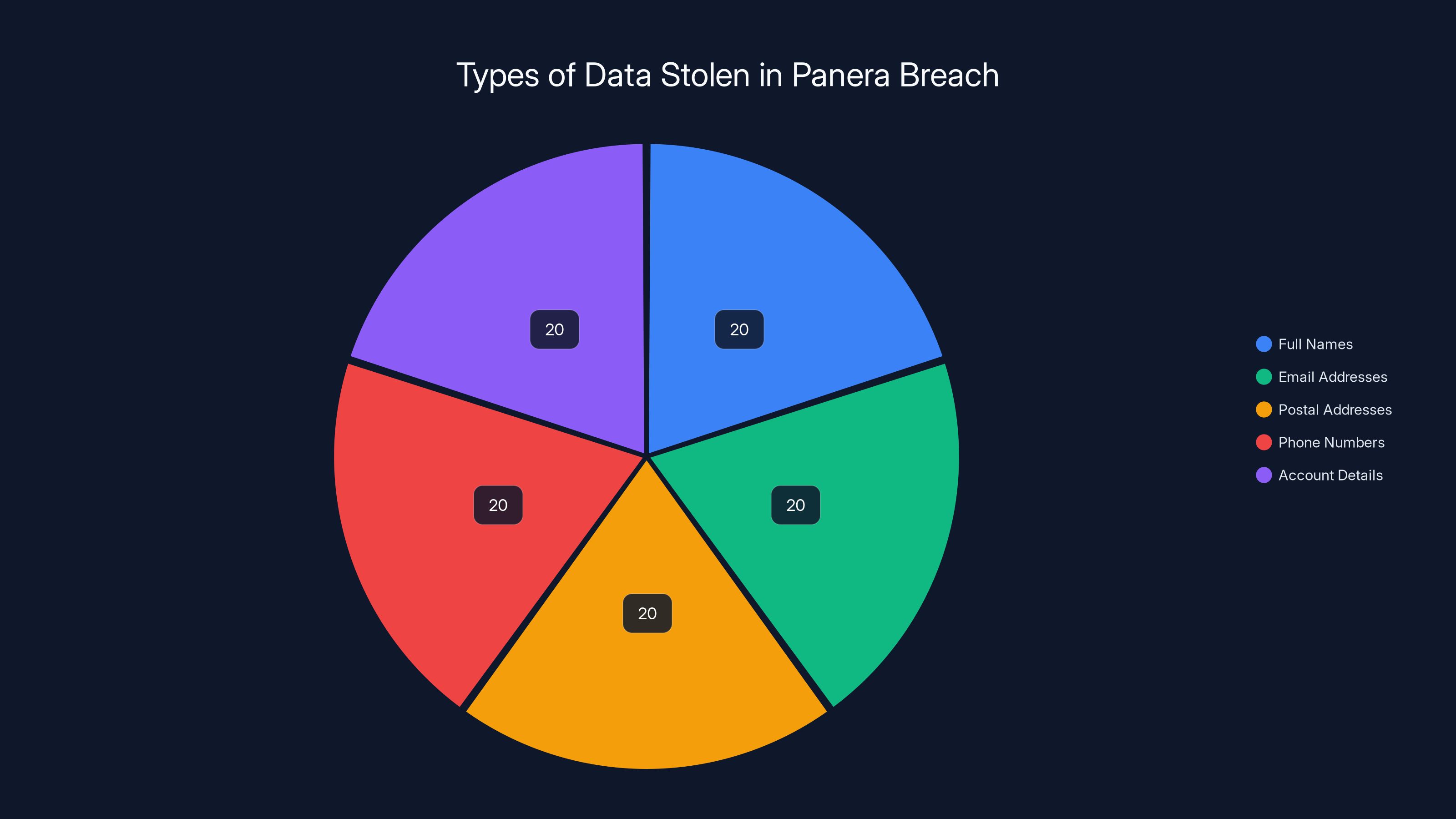
The breach involved a wide range of personal data types, each constituting an estimated 20% of the total stolen data. Estimated data.
How to Protect Your Company from Similar Attacks
If you're responsible for security at any organization, here's what you need to be doing right now to prevent a Panera-style breach.
First, assume your employees will get phished. Social engineering is incredibly effective. Even security-aware people make mistakes under the right circumstances. Train your employees on recognizing phishing and social engineering attacks, but more importantly, implement technical controls that prevent damage even when training fails.
Second, implement multi-factor authentication everywhere. Not just Okta codes. Enforce it for every system that accesses sensitive data. Require something you have (a phone), something you know (a password), and ideally something you are (biometric). Even if attackers have your password and email, they still can't access accounts without your phone.
Third, monitor authentication events aggressively. Set up alerting for impossible travel (someone logging in from two different geographic locations in a short time span), unusual access times, access from new devices, and logins followed by unusual activity patterns. Most breaches have detectable signs if you're looking for them.
Fourth, segment your network. Don't trust that anyone inside the network has blanket access to everything. Employees should only be able to access the systems and data they need for their job. A marketing employee doesn't need access to the production customer database. An accounting employee doesn't need access to source code repositories. This limits the damage when credentials are compromised.
Fifth, enforce password rotation and complexity requirements. Or better yet, move away from passwords entirely. Passwordless authentication using biometrics or hardware keys is more secure and doesn't rely on employees remembering complex passwords.
Sixth, conduct regular security training specific to your organization's attack surface. Generic security training is helpful but specific scenarios are better. Show employees what a phishing email that targets your company looks like. Show them how social engineers might research them on Linked In to make their calls more convincing. Make it real.
Seventh, conduct penetration testing. Hire external security firms to try to break into your systems using the same tactics attackers use. When they succeed (and they will), you learn where your defenses are weakest.

The Future of Identity Security
Breaches like Panera's are prompting a reevaluation of how organizations handle identity and access management. The industry is slowly moving away from password-based authentication, which is easy to phish and steal, toward passwordless solutions.
One emerging approach is hardware security keys. These are physical devices (about the size of a USB drive) that you plug into your computer and tap when logging in. They're cryptographically secured and extremely difficult to phish. You can't be socially engineered into revealing a hardware key's code because the key doesn't work that way.
Another approach is continuous verification. Instead of authenticating once at login, systems continuously verify that the person using the account is who they claim to be. If behavior changes (different location, unusual access patterns, accessing new systems), the system challenges the user with additional verification.
Biometric authentication is improving rapidly. Facial recognition, fingerprinting, and iris scanning are becoming more secure and more reliable. Combined with something you have (a phone or key) and something you know (a PIN), they create much stronger authentication than passwords alone.
The challenge is implementation. Most organizations have thousands of applications and systems relying on passwords. Migrating away from passwords is expensive, time-consuming, and requires coordination across entire organizations. But the alternative—continuing to rely on passwords that can be phished and stolen—is becoming untenable as attackers get more sophisticated.

The Bigger Picture: Why Companies Struggle with Security
Looking at the Panera breach, one might ask: how does one of the largest restaurant chains in America have such weak security? The answer is more nuanced than "bad security team."
First, security is expensive and doesn't directly generate revenue. A CFO looks at a proposal to implement better authentication systems and asks, "How much will this increase our sales?" The answer is zero. Security is a cost center. It's easier to justify spending on marketing, which clearly impacts sales, than spending on security, which provides an intangible benefit of "avoiding potential breaches."
Second, security is difficult. There's no single solution. You need to implement multiple layers, keep them updated, train employees continuously, and stay ahead of evolving attack tactics. Companies that excel at security have dedicated teams with deep expertise, and they budget accordingly. Smaller companies and even some large ones try to get by with minimal security staff.
Third, organizational structure often prevents good security practices. Developers want to ship features quickly. Infrastructure teams want to avoid downtime. The security team wants to implement controls that slow everything down. Conflict is inevitable. If the security team lacks executive support, their recommendations get overruled.
Fourth, many companies don't understand their actual risk profile. They think breaches happen to other companies, not them. They underestimate how valuable their customer data is to criminals. By the time they experience a breach, it's too late to prevent it.
Fifth, legacy systems create security debt. Many organizations are running systems built 10, 15, even 20 years ago. These systems weren't designed with modern threats in mind. Updating them is expensive. Replacing them is even more expensive. So they continue running insecure systems, adding patches and monitoring on top, but never really fixing the fundamental security problems.
Panera, as a large public company, presumably has more resources than most organizations to invest in security. Yet they still fell victim to a social engineering attack. This suggests that the problem isn't always insufficient resources but insufficient prioritization.

What Regulators Are Doing About Data Breaches
Governments worldwide are getting tougher on companies that fail to protect customer data. The regulatory landscape is evolving rapidly.
In the United States, there's no single federal data breach law. Instead, there are 50+ state laws, each with slightly different requirements. Generally, companies must notify customers of breaches without unreasonable delay. Some states require notification within 30 days. Some allow longer timeframes if notification is combined with identity theft protection services.
The European Union's GDPR is much stricter. Companies must report breaches to regulators within 72 hours. Fines can reach 4% of annual global revenue or €20 million, whichever is higher. For large companies, this is a game-changing regulation.
California's CCPA and newer privacy laws in other states are also increasing requirements. Companies must be transparent about what data they collect, how they use it, and how they protect it. Consumers have the right to know what data exists about them, request corrections, and in some cases, demand deletion.
The UK's Data Protection Act, based on GDPR, provides similar protections. Canada's PIPEDA and Australia's Privacy Act both have explicit data breach notification requirements.
The trend globally is toward stricter regulations, higher fines, and more explicit requirements for security practices. Companies can no longer treat data breaches as inevitable costs of doing business. The regulatory environment is making strong security not just good practice but a legal requirement.

Why the Panera Breach Matters Beyond Panera
On the surface, the Panera breach is about one company's failure to protect customer data. But it's much bigger than that.
First, it's a wake-up call about the vulnerability of SSO systems. Millions of organizations use Microsoft Entra, Okta, Google Workspace, or similar SSO platforms. Many of them have the same vulnerability Panera did: over-reliance on SSO as a security measure without sufficient compensating controls.
Second, it demonstrates the ongoing effectiveness of social engineering. All the sophisticated technical controls in the world don't matter if someone with legitimate access is tricked into giving up their authentication code. This should prompt organizations to reconsider how they approach security training.
Third, it shows that major breaches still happen despite organizations' size and presumed resources. If Panera, a household name with millions in revenue, can fall victim to attackers, any organization can. There's no such thing as "too big to be hacked."
Fourth, it highlights the value of customer data to criminals. In a world where personal information can be sold for money, stolen data is a commodity. Anyone collecting customer data is a potential target.
Fifth, it demonstrates the sophistication of modern attack groups. Shiny Hunters coordinated attacks across multiple companies, leveraged social engineering, exploited authentication systems, and avoided detection for an unknown period. They're not script kiddies. They're professional criminals with significant resources.

Moving Forward: Lessons for Consumers and Companies
The Panera breach should catalyze change on multiple levels.
For consumers, the lesson is clear: your data is constantly at risk. Companies are collecting more of it than ever, and security failures are inevitable. The only way to truly protect yourself is to limit the data you share, monitor for fraud aggressively, and implement strong authentication on your own accounts.
For companies, the lesson should be: security isn't optional. It's not something you can skip to save money. It's not something that can be entirely outsourced to external vendors. Security requires investment, expertise, and continuous attention. It requires making security a priority at the executive level, not just an IT concern.
For security teams, the lesson is: social engineering is your most critical threat vector. Technical controls are important, but they only work if the people using them aren't tricked into bypassing them. Invest heavily in employee training, threat awareness, and building a security-conscious culture.
For regulators, the lesson is: the current approach to data protection is insufficient. Fines need to be larger. Requirements need to be more specific. Companies need incentives to prioritize security before breaches happen, not just penalties after breaches are discovered.
The Panera breach isn't an anomaly. It's a data point in a larger trend of sophisticated attacks targeting authentication systems. The response needs to match the threat level.
FAQ
What exactly was the Panera Bread data breach?
Panera Bread suffered a data breach where 14 million customer records were stolen by the hacking group Shiny Hunters. The stolen data included names, email addresses, postal addresses, phone numbers, and account details. Approximately 760 MB of compressed data was exfiltrated from Panera's systems without encryption, meaning the attackers had direct access to all stolen information.
How did hackers access Panera's systems?
The attackers compromised Panera's Microsoft Entra single sign-on (SSO) system through a voice phishing attack targeting Okta authentication codes. Voice phishing (vishing) involved attackers calling Panera employees, impersonating IT support, and tricking them into revealing their one-time authentication codes. With valid credentials and authentication codes, attackers could log into corporate systems as legitimate employees.
Who is Shiny Hunters and are they still active?
Shiny Hunters is one of the most active and sophisticated hacking groups operating in 2025. They've been responsible for breaches affecting major companies including Clover Health, Wattpad, Unacademy, and several others. Unlike traditional ransomware groups that encrypt data and demand payment for decryption keys, Shiny Hunters simply steals data and demands payment to prevent public release. They've announced no plans to cease operations.
What other companies were affected by this attack vector?
Beyond Panera Bread, several other major companies fell victim to the same voice phishing attack targeting authentication codes. Companies confirmed affected include Car Max, Edmunds, Crunchbase, and Betterment. Betterment confirmed that employees fell for the social engineering attack on January 9. The pattern suggests Shiny Hunters was conducting a coordinated campaign against multiple companies simultaneously.
What should I do if I'm a Panera customer?
First, immediately change your Panera password and don't use it anywhere else. Enable multi-factor authentication on all accounts where you use similar passwords, since attackers now have your email and potentially your password from Panera. Monitor your credit reports through the free annual credit report service, set up credit monitoring alerts, and watch your financial accounts for unauthorized transactions. Consider placing a credit freeze to prevent attackers from opening accounts in your name.
How can companies prevent similar SSO attacks?
Companies can prevent similar attacks by implementing multi-factor authentication that doesn't rely on codes employees can be tricked into sharing, aggressively monitoring authentication events for suspicious patterns, conducting regular security training on social engineering tactics, implementing network segmentation to limit damage when credentials are compromised, and considering passwordless authentication using hardware security keys or biometrics. Regular penetration testing and threat hunting can also identify vulnerabilities before attackers exploit them.
What is voice phishing and how do I protect myself?
Voice phishing (vishing) is a social engineering attack where criminals call victims, impersonate trusted entities, and trick them into revealing sensitive information. Attackers research victims on social media and Linked In to make calls more convincing. To protect yourself, never give out authentication codes, passwords, or sensitive information to anyone who calls you, even if they claim to be from IT support or your bank. Contact organizations directly through their official websites if you're suspicious about a call.
Will Panera face legal consequences for the breach?
Yes. Panera will likely face multiple lawsuits from affected customers, regulatory fines from state and federal agencies, and potential penalties under GDPR if customers from the EU were affected. Regulatory fines can reach up to 4% of annual global revenue under GDPR and varying amounts under state laws. Combined with the costs of forensic investigation, credit monitoring services for customers, and reputational damage, the total cost of this breach could easily exceed $200 million.
How long will this affect affected customers?
The effects could last years. Criminals could use stolen personal information for identity theft, which can take years to fully resolve. Your information could be sold on the dark web and used by other criminals for fraud. Credit monitoring services are typically offered for 2-3 years after a breach. However, vigilance for signs of fraud should continue indefinitely. The impact on Panera's reputation could last even longer, potentially affecting customer trust for years.
What does this breach tell us about cybersecurity in 2025?
This breach demonstrates that sophisticated attacks increasingly focus on compromising legitimate user credentials rather than breaking through perimeter defenses. It shows that social engineering remains one of the most effective attack vectors despite technical security controls. It also reveals that major organizations with significant resources still struggle with adequate security implementation, suggesting that the problem is often prioritization rather than capability. Finally, it highlights the ongoing value of customer data to criminals and the need for organizations to treat data protection as a critical business function.

The Bottom Line
The Panera Bread data breach represents a watershed moment in cybersecurity discussions. This isn't a story about a company with poor IT infrastructure or outdated systems. This is a story about how even well-resourced organizations with sophisticated authentication systems can fall victim to fundamental human manipulation.
When attackers successfully compromise 14 million customer records by simply calling employees and asking for authentication codes, we need to reconsider what "security" actually means. All the encryption, firewalls, and intrusion detection systems in the world don't matter if someone inside your organization can be socially engineered into giving away the keys.
For the millions of affected customers, the breach should motivate immediate action: change your password, enable multi-factor authentication everywhere, monitor your accounts, and consider a credit freeze. The attackers have your personal information. The threat of identity theft is real and immediate.
For the companies operating in the real world, the breach should be a catalyst for security assessment. If this happened to Panera, what's preventing it from happening to you? What are your employees being trained on? How are you monitoring for suspicious activity? Are you relying too heavily on SSO without compensating controls? These are uncomfortable questions, but asking them now is far better than learning the answers during a forensic investigation after a breach.
For the security industry, the breach validates what experts have been saying for years: social engineering works, authentication is the new perimeter, and companies need to treat employee security training as seriously as technical controls. The future of security lies in reducing reliance on passwords and authentication codes that humans can be tricked into sharing, moving toward passwordless authentication and continuous verification.
This breach won't be the last major attack on a prominent company. But it doesn't have to be a surprise. The attack patterns, the tactics, and the vulnerabilities are well understood. What's lacking is the organizational will to implement proven security practices across the board. Until that changes, we'll continue seeing breaches of this scale. And the 14 million customers affected by Panera's breach are just the latest reminder of the cost of that failure.

Key Takeaways
- ShinyHunters stole 14 million Panera customer records including names, addresses, emails, phone numbers through Microsoft Entra SSO compromise
- Voice phishing campaign targeting Okta authentication codes was the primary attack vector, also affecting CarMax, Edmunds, Crunchbase, and Betterment
- Attackers exfiltrated 760 MB of unencrypted data, giving them direct access to all customer information without needing to crack encryption
- Multi-factor authentication alone is insufficient; organizations need network segmentation, continuous verification, and aggressive monitoring for suspicious activity
- Affected customers must immediately change passwords, enable MFA across accounts, monitor credit reports, and consider credit freezes to prevent identity theft
Related Articles
- Europe's Digital Sovereignty Crisis: Breaking Free From US Tech Dominance [2025]
- Microsoft's Example.com Routing Anomaly: What Went Wrong [2025]
- Encrypt Your Windows PC Without Sharing Keys With Microsoft [2025]
- Microsoft BitLocker FBI Access: Encryption Backdoor Reality [2025]
- 149 Million Credentials Exposed: The Massive Data Leak Explained [2025]
- Microsoft BitLocker Encryption Keys FBI Access [2025]
![Panera Bread Data Breach: 14 Million Records Exposed [2025]](https://tryrunable.com/blog/panera-bread-data-breach-14-million-records-exposed-2025/image-1-1769605919790.jpg)



