149 Million Credentials Exposed: The Massive Data Leak Explained [2025]
Last year, something genuinely frightening happened. A cybersecurity researcher discovered a massive cloud storage container sitting on the internet completely unprotected. We're talking about 98 gigabytes of data containing 149 million combinations of usernames and passwords. No encryption. No password protection. Just sitting there for anyone to download.
The scope here is almost impossible to comprehend. This wasn't some niche database of a single service. The exposed credentials spanned financial accounts, cryptocurrency wallets, banking platforms, social media profiles, dating apps, and even government email addresses using the .gov domain. If you had an account anywhere on the internet, there's a reasonable chance your credentials were in that pile.
What makes this particularly troubling isn't just the sheer volume of exposed data. It's how accessible it was made. The database was indexed using reverse host paths, making credentials searchable by service. This suggests either a sophisticated hacker operation collecting credentials systematically, or a research project that went catastrophically wrong and got publicly exposed. Either way, the implications are staggering.
In this deep dive, we'll walk through exactly what happened, how bad this actually is, what makes your credentials valuable to attackers, and most importantly, what you need to do right now to protect yourself. This isn't theoretical cybersecurity scaremongering. This is a real incident affecting real people, and understanding it could be the difference between becoming a victim of fraud and staying safe.
TL; DR
- 149 million credential pairs were discovered exposed in an unencrypted cloud storage container containing approximately 98 gigabytes of usernames and passwords
- Multiple account types were included: financial services, cryptocurrency wallets, banking, social media, dating apps, and government (.gov) email accounts
- Searchable indexing made credentials easily accessible, suggesting the database was either from organized criminals or a research project that leaked
- Took nearly one month to get the cloud container taken down after discovery
- No passwords or encryption protected the database, meaning anyone with the URL could download the entire thing
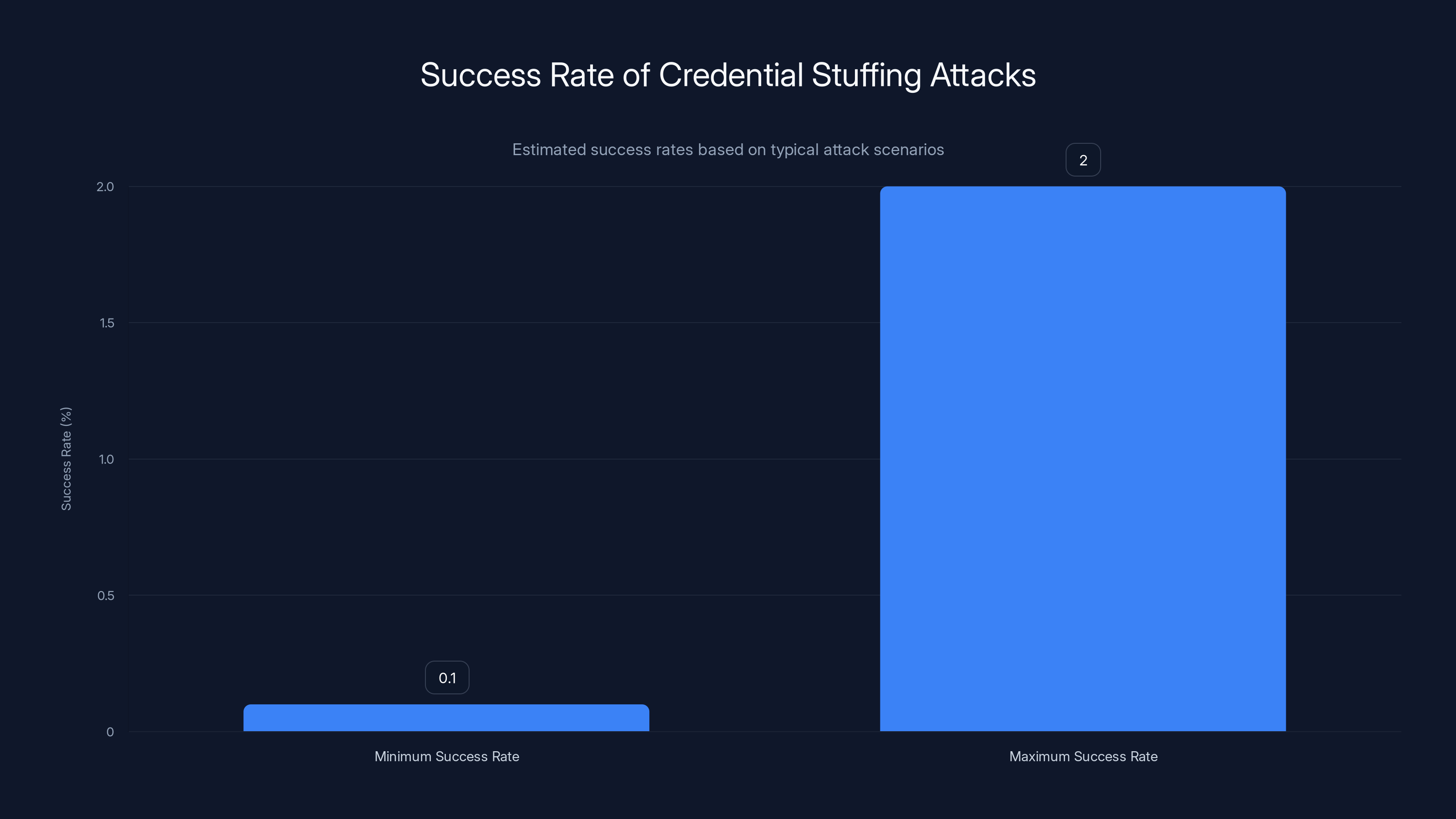
Credential stuffing attacks have a success rate between 0.1% and 2%, which can result in tens of thousands of compromised accounts when targeting millions.
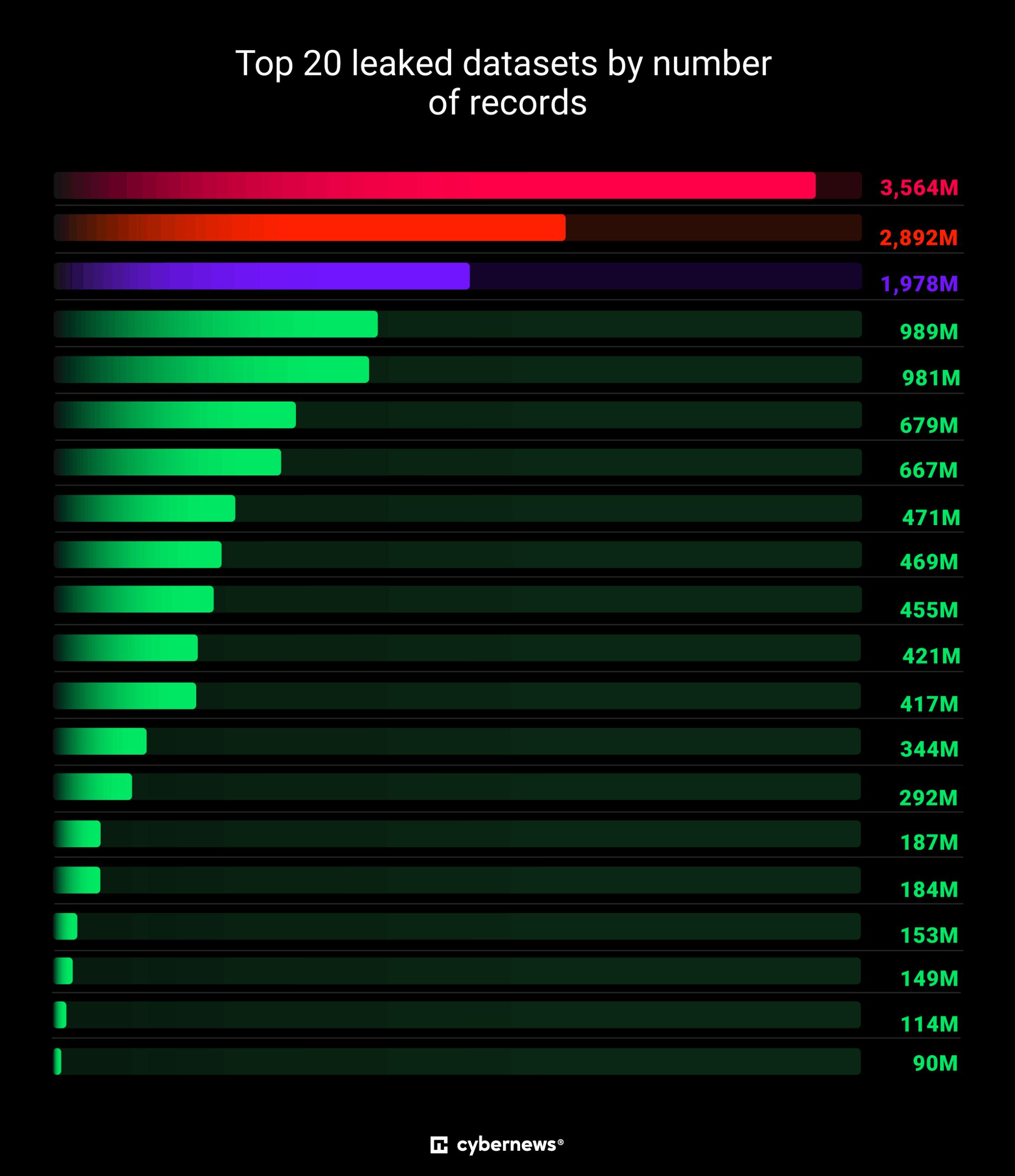
Understanding the Scale of the Breach
Before we talk about what this means, let's get a real sense of the numbers. 149 million credentials. That's roughly equivalent to the population of Russia, or about 45% of the United States population. For context, the largest breaches in history have topped out around 200 million records. This is right there competing with the worst data exposures we've ever seen.
But here's what makes this particularly notable: these weren't just email addresses or usernames. These were active credential pairs - meaning someone had the actual passwords. Username-password combinations are exponentially more valuable to attackers than either data point alone. With both pieces of information, an attacker can attempt account takeover immediately.
The 98-gigabyte size tells you something important too. That's a massive amount of data to store unencrypted on a server. For comparison, that's roughly equivalent to the storage capacity of the internal drive on an older laptop. Someone didn't accidentally expose this. They actively built and maintained this database.
What's particularly chilling is that security researchers estimate the database went undetected for an unknown period. It could have been weeks. It could have been months. During that time, anyone who stumbled upon the cloud storage container could have downloaded the entire dataset and started systematically attacking accounts across multiple platforms.
The discovery itself came through Jeremiah Fowler, who's built a reputation for finding these kinds of exposed databases. Fowler reached out to the hosting provider, but the provider claimed the container was hosted by a subsidiary operating independently. This shell game between companies delayed response time dramatically. It took nearly a month to get the thing taken offline after discovery. Thirty days. During a month-long window, the most sensitive authentication credentials for millions of people were sitting in plain sight.
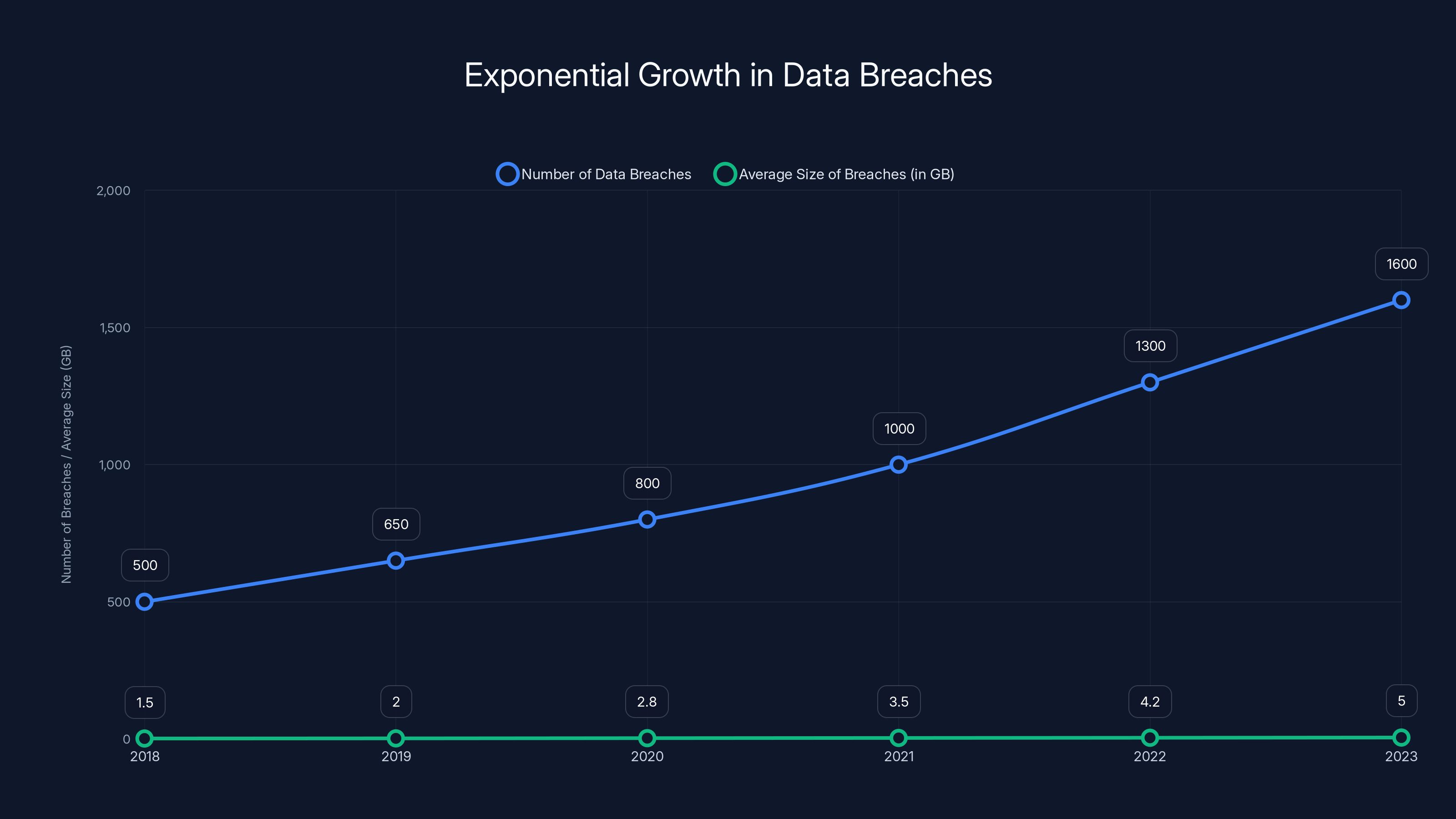
Data breaches have grown exponentially from 2018 to 2023, with both the number of breaches and their average size increasing significantly. (Estimated data)
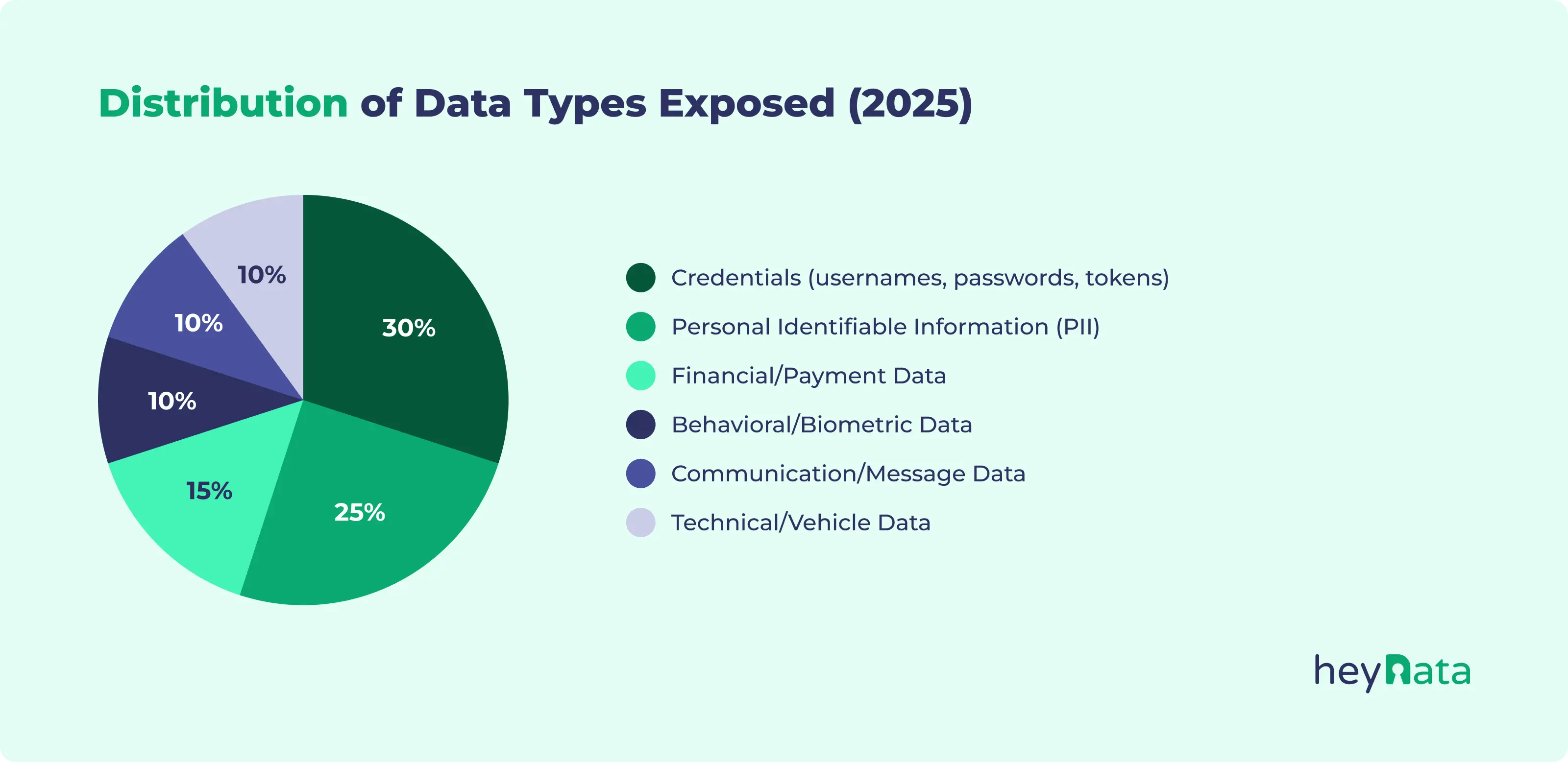
Breaking Down What Was Actually Exposed
The database didn't contain just one type of account. That's actually what makes it so dangerous. Different types of breached accounts create different risks for victims.
Financial Services and Banking Accounts
This is the nightmare scenario for most people. Your banking credentials in the hands of attackers means someone can potentially access your money. But here's the good news: most modern banks have additional security layers beyond just username and password. Two-factor authentication, out-of-band verification, and transaction limits all add friction for fraudsters.
That said, having banking credentials exposed puts you in immediate danger. Attackers will attempt login. Many will succeed on the first try because passwords are often simple or reused. Even if they don't immediately gain access to your account, they might use the credentials for social engineering attacks against your bank's customer service representatives. "I forgot my password, can you help me reset it?" combined with your actual credentials sometimes works.
Cryptocurrency wallets and trading accounts present an even more terrifying scenario. Unlike banks, most crypto exchanges don't have as robust security infrastructure, and transactions are immediate and irreversible. Someone with your exchange credentials can liquidate your entire crypto portfolio and transfer it to their wallet in minutes. There's no bank to call for a chargeback. There's no customer service that can reverse the transaction.
Social Media and Digital Identity
Exposed social media credentials might seem less critical than banking information, but don't underestimate the damage here. Your social media account is often linked to password reset functions for other accounts. Someone gains access to your Twitter, Facebook, or Instagram? Suddenly they can use password reset flows to take over email accounts, which then cascades to taking over everything else.
Social media also provides attackers with detailed information about your life. They see your friends, your habits, your travel patterns, and your interests. This data feeds into more sophisticated social engineering attacks. An attacker might message your friends pretending to be you. They might contact family members claiming to be stranded and needing money urgently. Real conversations become weapons.
Dating and Personal Apps
This category gets less attention than financial breaches, but it's genuinely devastating for victims. Dating app credentials are linked to deeply personal information. Your preferences, conversations with matches, location data, and intimate details all become accessible.
The blackmail potential here is significant. We've seen coordinated campaigns where exposed dating app users are contacted by criminals threatening to share their profile or messages with family members unless they pay extortion fees. For people in vulnerable situations, this represents a serious threat.
The overlap between dating app users and other services creates compounding risks too. Attackers might notice someone on multiple dating platforms using the same credentials. They might impersonate them on one platform to build credibility before switching to another. They might contact victims directly claiming to have found compromising messages and requesting payment.
Government and Official Email Accounts
The inclusion of .gov domain email accounts in this breach raises immediate national security concerns. Government workers often use the same passwords across multiple systems. Officials might reuse credentials from personal accounts for government access. The targeting of government accounts suggests either a very sophisticated state-sponsored operation or at minimum a criminal group specifically hunting for government employee credentials.
How This Database Was Likely Built
Understanding how this massive credential database was compiled tells us a lot about the threat landscape we're navigating. The database wasn't created by someone sitting at a keyboard manually entering credentials. It was built systematically, probably over months or years.
The Infostealer Connection
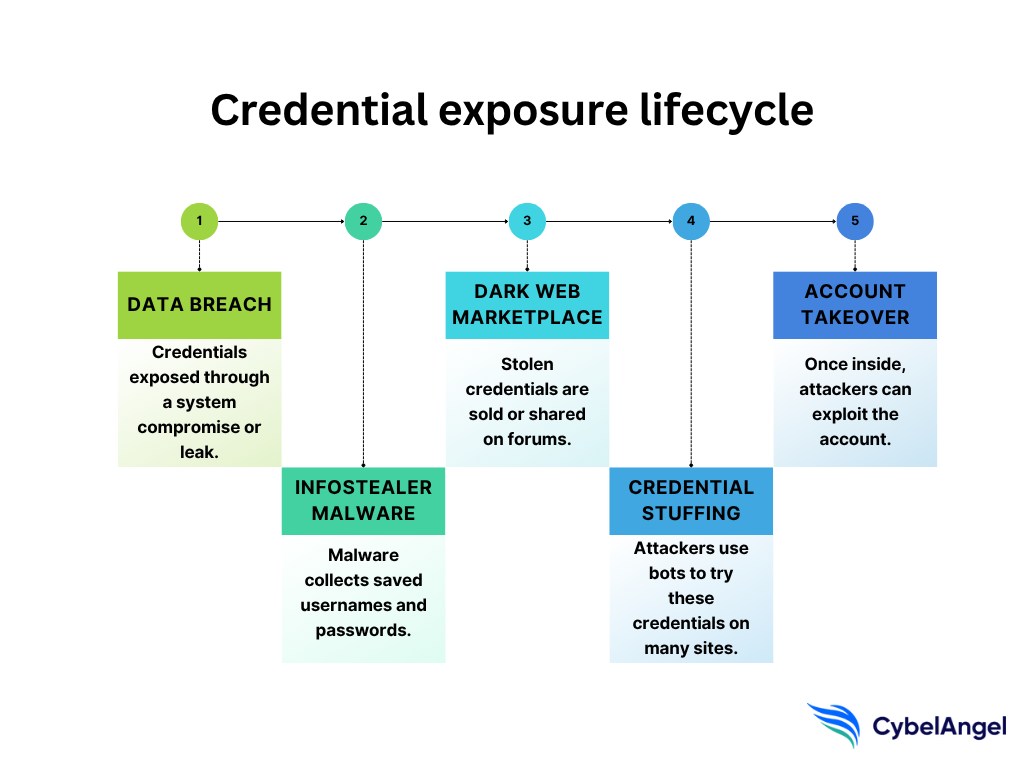
The research notes traces of infostealer malware within the database. Infostealers are a category of malware specifically designed to harvest credentials from infected systems. When you install malware or click a malicious link, infostealers work in the background, scraping saved passwords from your browser, capturing credentials entered into login forms, and monitoring clipboard activity.
The presence of infostealer signatures in this database suggests at least some of the credentials came from infected computers. An attacker distributes malware, infects thousands of machines, and automatically siphons off every credential stored on those systems. Over time, you accumulate hundreds of thousands or millions of username-password pairs.
Keylogging and Form Hijacking
Keyloggers capture everything you type. Someone logs into their email account? The keylogger grabs it. Someone enters a banking password? Captured. Over the course of even one year on an infected machine, a keylogger accumulates thousands of credentials.
More sophisticated malware doesn't just log keystrokes. It intercepts data sent to and from web forms before encryption. It hooks into browser APIs to capture passwords at the moment they're entered. Some malware even takes periodic screenshots to capture two-factor authentication codes displayed on screen before the user can use them.
Dark Web Trading and Aggregation
Not all credentials in this database came from fresh infections. Many were likely purchased from other criminals or scraped from previous breaches. The dark web operates as a trading ground for stolen data. Someone breaches a service with 500,000 user accounts? They list it for sale. Other criminals buy it, combine it with credentials from other breaches, and build larger databases.
What we're probably looking at here is an aggregated database combining credentials from multiple sources across several years. That's why it's so massive and why it includes such diverse account types.
The Searchable Indexing Question
Here's what really fascinates security researchers about this particular database: it was indexed using reverse host paths. This means credentials were organized by domain and easily searchable. You could query for all credentials from a particular bank, dating app, or email provider.
This level of organization suggests either:
- An organized criminal operation actively collecting and cataloging credentials for systematic exploitation
- A research project that documented credentials for analysis and somehow leaked
- A data broker compiling information for sale or rent
The organization is too sophisticated for accidental exposure. Someone invested time in building this structure. They wanted to be able to search and filter this data quickly. That speaks to intentional purpose.
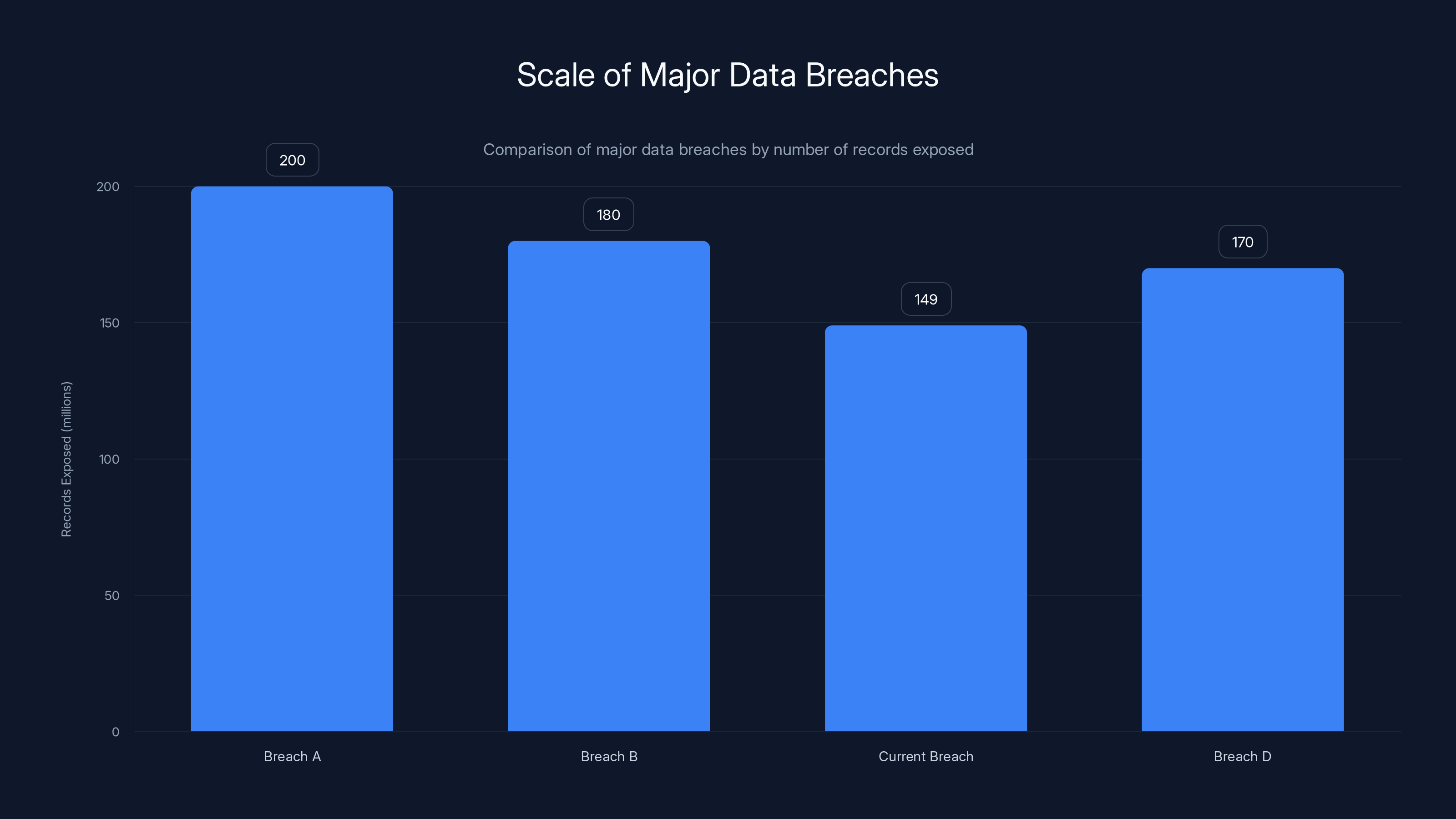
The current breach exposed 149 million records, making it one of the largest breaches in history, close to the largest known breach of 200 million records.
The Timeline and Response Failure
One of the most frustrating aspects of this incident is how long it took to actually take the database offline. Let's walk through what happened.
A security researcher discovered the exposed container. They documented the exposure. They attempted to identify the owner but couldn't find any associated information. They reached out to the hosting provider.
Here's where things get murky. The hosting provider claimed the container was hosted by a subsidiary operating independently. This kind of shell company structure creates accountability gaps. The parent company points fingers at the subsidiary. The subsidiary claims they're not responsible for what clients store. Meanwhile, 98 gigabytes of exposed credentials sits on their servers.
It took almost a full month to get the container taken down. Thirty days. In cybersecurity incident response, that's an eternity. Every day the database remained accessible, thousands more people potentially downloaded the full dataset. Every day represented another opportunity for attackers to weaponize this data.
This timeline reveals something important about the internet's response infrastructure. We don't have a standardized, rapid mechanism for taking down exposed data. There's no emergency protocol where a researcher can flip a switch and immediately disable an obviously dangerous cloud storage container. Instead, there's a bureaucratic process of emails and phone calls and companies passing the buck.
The researcher did the right thing by discovering this and attempting to notify the responsible parties. But the system failed catastrophically by not having mechanisms in place to quickly act on that notification.
Why Your Credentials Are So Valuable
To understand the actual danger here, you need to understand why attackers want these credentials in the first place. A stolen username and password isn't just a security problem. It's the skeleton key that opens doors to your entire digital life.
Immediate Account Takeover
Most obviously, attackers can use your credentials to log into your actual accounts. But they're smart about this. They don't immediately log in from some obvious foreign IP address. They use proxies and VPNs to make the login appear to come from a location where you might plausibly be.
Once inside your account, they change the password immediately, locking you out. They enable two-factor authentication using their own phone number. They might add a recovery email address they control. Within minutes, your account is completely theirs, and you've lost access.
Password Reset Attacks and Account Cascading
Here's where the real danger emerges. Your email account is the master key to everything else. Someone gains access to your email? They can reset passwords for every other service. They don't even need your original password for those accounts. They just need access to your email.
But it goes further than that. Many services use identity verification questions to reset passwords without email. "What's your mother's maiden name?" "What city were you born in?" "What's your oldest sibling's name?" Most of this information is publicly available on social media or can be learned through social engineering.
Someone with your email and your password to one critical account can methodically take over your entire digital identity. They reset your banking app password. They reset your crypto exchange password. They reset your social media passwords. It all cascades.
Fraud and Impersonation
Attackers aren't necessarily trying to use your accounts themselves. Sometimes they're selling access to other criminals. Someone pays a few dollars for your email credentials. A different criminal pays for your banking credentials. A third group pays for your social media access.
Each criminal uses that access differently. One might attempt to drain your account. One might impersonate you to contact your friends and family. One might maintain access for months, slowly stealing information and waiting for the perfect moment to strike.
Extortion and Blackmail
The dating app exposure is particularly vulnerable to this. An attacker gains access to your dating profile and private messages. They compile screenshots showing your matches, conversations, and preferences. They contact you directly: "Pay me $500 or I'm sending these screenshots to your family."
It's crude, but it works. Victims pay because they're terrified of exposure. The attacker typically doesn't follow through on the threat (because they want to remain anonymous), but the victim has already lost money.
Establishing Persistent Access
Once inside your account, sophisticated attackers don't immediately exploit it. They establish persistence. They create backup accounts. They set up auto-forwarding rules on email. They add secondary authentication methods they control. They plant malware on your connected devices.
The goal is to maintain access indefinitely, even if you change your password. They want to stay in your account for months, passively observing and harvesting information, waiting for the moment when maximum exploitation is possible.

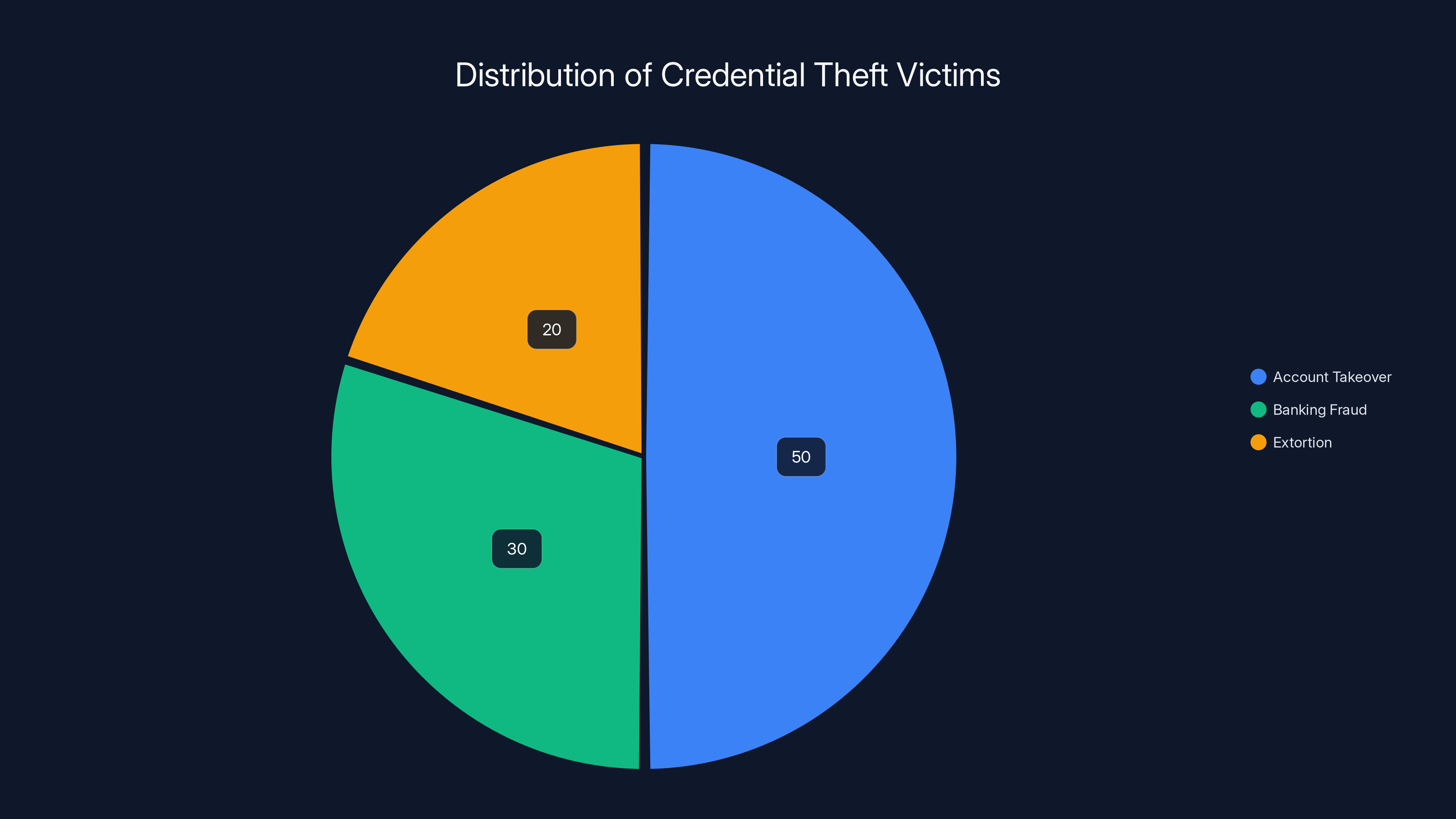
Estimated data shows that account takeovers are the most common type of credential theft impact, affecting approximately 50% of victims, followed by banking fraud at 30%, and extortion at 20%.
The Ongoing Risk After Exposure
Just because the database was taken offline doesn't mean the danger has passed. In fact, the worst is just beginning for people whose credentials were in that database.
Credential Stuffing Attacks
Once attackers have your username and password, they use automated tools to test those same credentials against other services. This is called credential stuffing. They might have your email and password from the breach. They try that combination on Netflix, Hulu, Spotify, Twitter, Facebook, Amazon, and thousands of other services.
Statistics show that somewhere between 0.1% and 2% of credential stuffing attempts succeed. That sounds low, but when you're running the attack against millions of accounts, even 0.1% success rate means tens of thousands of compromised accounts.
Somebody tries your credentials against banking websites, email providers, and cryptocurrency exchanges. They're looking for that small percentage where you reused your password. Once they find it, they're in.
Increased Targeting by Sophisticated Attackers
The organized nature of this database means sophisticated attackers have it. They're not just trying random logins. They're analyzing patterns. They're identifying high-value targets. They're researching targets before attacking.
An attacker might notice you have credentials for multiple financial services. They research you, find your phone number, and attempt to reset your password using SIM swap attacks. They call your bank claiming to be you, mentioning specific transactions they found in the leaked database to appear legitimate, and social engineer access.
Long-Term Identity Theft Risk
The leaked data now exists permanently on the dark web. It's been downloaded. It's been shared. It's been traded. Even if no one attacks your accounts immediately, your credentials are floating in criminal marketplaces indefinitely.
Someone might buy your information months from now. Someone might use it years from now. The exposure creates a perpetual vulnerability. Until the password is changed, the risk persists.

Immediate Steps to Take If You're Affected
If there's any chance your credentials were in this database, you need to act now. This isn't something to put off until tomorrow.
Check If Your Email Is Exposed
First, determine whether you were actually affected. Several services now allow you to check if your email address appears in known breaches. Websites like Have I Been Pwned maintain databases of breached information and can tell you if your email appears in publicly disclosed breaches.
Note that this particular database might not be fully indexed by those services yet, depending on when you're reading this. But checking is a good starting point. Even if this specific breach isn't found immediately, knowing what other breaches you're part of helps you prioritize what to secure first.
Change Your Passwords Immediately
Start with the most critical accounts:
- Email accounts (change primary email password first, since it's the master key)
- Banking and financial (checking, savings, credit cards)
- Cryptocurrency exchanges (if you have accounts)
- Social media (secondary but important)
- Anything else with sensitive information
Don't do this all at once and don't reuse passwords. Create genuinely unique passwords for each account. A password manager makes this manageable. Use random combinations of uppercase, lowercase, numbers, and special characters.
Bad password: My Password 123
Good password: K7$m P9w Qx#Ln 2v Rt
Enable Two-Factor Authentication Everywhere
Two-factor authentication (2FA) is your safety net. Even if attackers have your password, they can't access your account without the second factor. Most services offer multiple 2FA options:
- Authenticator apps (Google Authenticator, Authy) - most secure
- SMS text messages - less secure but better than nothing
- Security keys (physical USB keys) - extremely secure but more expensive
Prioritize 2FA on email accounts, banks, and any account with sensitive data. If you have to choose between 2FA methods, authenticator apps are more secure than SMS because they can't be intercepted in transit.
Monitor Your Accounts for Suspicious Activity
Check your bank and credit card statements carefully. Look for unauthorized transactions. Check your email account activity logs to see if anyone accessed it recently. Review the devices that have access to your important accounts.
Many banks and email providers let you view login history including device type and location. If you see access from somewhere you've never been, that's a red flag.
Monitor Your Credit
With your full credentials exposed, attackers have everything they need to open new accounts in your name. Pull your credit reports from all three bureaus (Equifax, Experian, Trans Union) for free at Annual Credit Report.
Look for accounts you don't recognize. Look for hard inquiries you didn't authorize. Consider placing a fraud alert or credit freeze on your accounts. These prevent new accounts from being opened in your name without additional verification.
Consider Identity Theft Protection
Services exist specifically to monitor for identity theft. They watch for new accounts opened in your name, monitor the dark web for your personal information being sold, alert you to suspicious activity, and sometimes provide insurance against theft.
These services cost money, but for someone who knows their credentials were compromised, the peace of mind and the protection might be worth it.

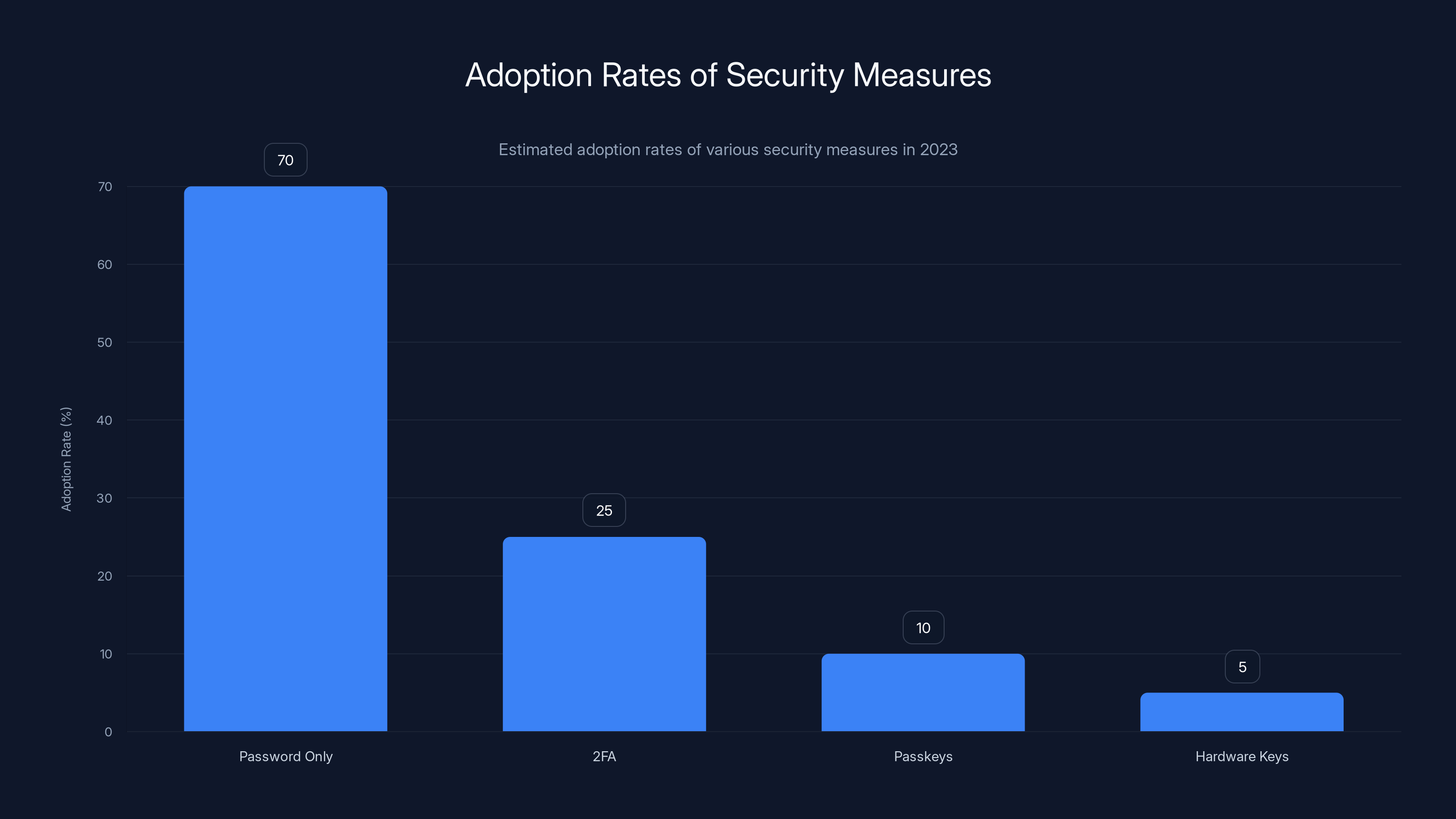
Estimated data shows that while passwords remain widely used, 2FA adoption is still low at 25%, with passkeys and hardware keys even lower. Estimated data.
How This Happened: Root Causes and System Failures
This massive breach didn't happen by accident. It's the result of cascading security failures at multiple levels.
Inadequate Endpoint Security
Malware got onto people's computers in the first place. This means endpoint security (antivirus, anti-malware, endpoint detection and response) failed. Either people weren't running protection, or the protection didn't catch the malware.
This is partly a user problem. Not everyone updates their antivirus. Not everyone patches their operating system. But it's also a systemic problem. Antivirus software doesn't catch all malware. Zero-day exploits exist that no security software knows about.
Cloud Storage Configuration Errors
Someone created a cloud storage container and configured it with completely open permissions. This is a fundamental misconfiguration. Cloud storage services have default settings that should be private. This container was explicitly made public.
Somebody made a choice to expose this data, whether intentionally or through catastrophic negligence. The cloud provider should have warnings and restrictions preventing this, but they don't always.
Lack of Response Infrastructure
There's no emergency protocol for critical data exposures. When a researcher discovered this database, there should have been a rapid-response team that could immediately take it offline. Instead, there was bureaucratic delay.
The hosting provider claimed it was a subsidiary issue. The subsidiary presumably claimed they couldn't act without parent company approval. Meanwhile, the data sat exposed. This infrastructure gap created a month-long window where the database remained accessible.
Continued Password Insecurity
This incident highlights exactly why relying on passwords alone is dangerous. Passwords can be stolen. They can be phished. They can be inferred through social engineering. They can be compromised through breaches like this one.
Yet passwords remain the primary authentication mechanism across the internet. We've built an entire digital infrastructure dependent on a fundamentally insecure model. This is the root cause of everything cascading from it.
The Broader Cybersecurity Landscape Context
This breach doesn't exist in a vacuum. It's part of a larger trend in cybersecurity that's becoming increasingly alarming.
Exponential Growth in Data Breaches
Data breaches are accelerating. More breaches are being discovered. Larger volumes of data are being exposed. The average size of breaches continues to grow year over year.
This isn't necessarily because hackers are getting better (though they are). It's because we're collecting more data, storing it less securely, and relying on systems that were never designed with security as a priority.
The Economics of Credential Theft
Credential theft is economically efficient for attackers. They invest relatively small amounts in malware distribution and database aggregation. They generate revenue through multiple channels: selling credentials, running credential stuffing attacks, extortion, and identity theft.
The barrier to entry is low. You don't need a sophisticated operation. You just need some malware code (available for purchase on dark web forums for $100-500) and a way to distribute it. Once you have a library of credentials, there's immediate market demand.
The Shift from Technical Security to Availability of Exploit Services
There was a time when cybercrime required genuine technical skill. Now there's an entire economy built around providing services that make attacks accessible to non-technical criminals.
You don't have to hack accounts yourself. You can rent access. You can buy credentials. You can contract someone to send phishing emails. You can pay for botnet access. The technical barriers to committing cybercrime have essentially disappeared.
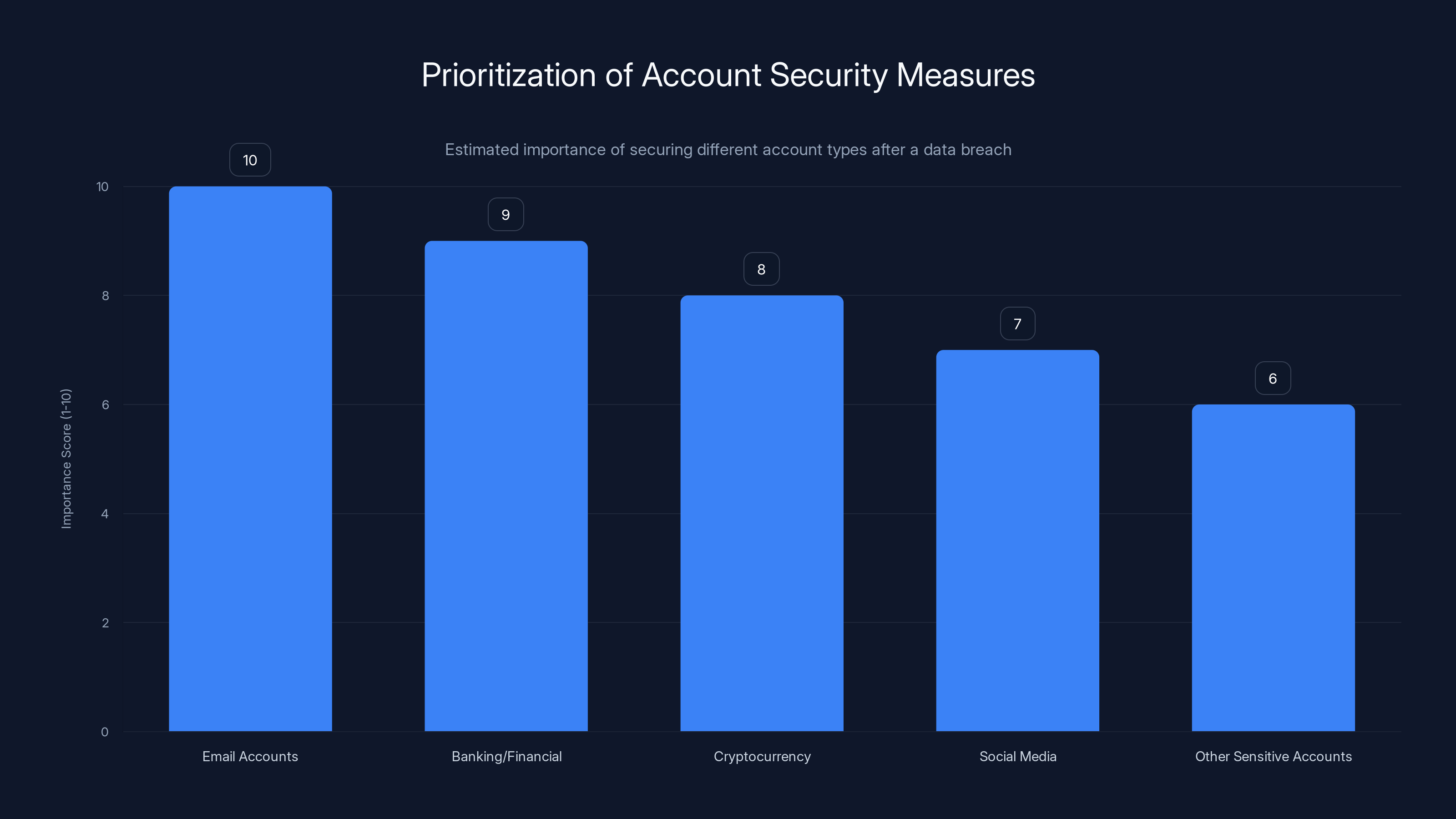
Email accounts are the highest priority for security updates, followed by banking and financial accounts. Estimated data based on typical security recommendations.
What This Means for the Future of Credential Security
This incident forces us to confront some uncomfortable truths about how we've built digital security.
The Inadequacy of Passwords
Passwords were designed for a different era. They were supposed to be unique. They were supposed to be complex. They were supposed to be changed regularly.
None of that happened at scale. People reuse passwords. They choose simple passwords. They don't change them. Attackers adapted to this reality. They built credential databases. They run stuffing attacks knowing the success rate justifies the effort.
Passwords remain because they're ubiquitous and because there's no single replacement that works everywhere. But pretending they're secure is fantasy. They're not. They've never been.
The Critical Importance of 2FA
Two-factor authentication remains the most practical defense against credential compromise. Even if your password is stolen, 2FA creates a barrier.
But adoption remains frustratingly low. Many people still haven't enabled 2FA on critical accounts. Many services don't mandate it. Many users find it inconvenient. Until 2FA adoption reaches 90%+, we'll continue seeing incidents like this one result in actual account compromises.
The Rise of Passkeys and Hardware Authentication
The industry is slowly moving toward authentication methods that don't rely on passwords at all. Passkeys (cryptographic credentials stored on devices), hardware security keys (physical USB devices), and biometric authentication all offer stronger security properties than passwords.
But these technologies still have adoption barriers. They require devices that support them. They have usability challenges. They don't work everywhere yet. The transition will take years.
Regulatory Pressure and Mandates
Governments are starting to mandate security practices. The SEC now requires cybersecurity reporting for breaches exceeding certain thresholds. The EU's GDPR imposes massive fines for inadequate security. Industry regulations like HIPAA, PCI-DSS, and others set baseline standards.
We're likely to see increasingly stringent requirements around authentication, encryption, and breach notification. Companies can't afford to be cavalier about security anymore.

Real-World Impact Stories: Who Actually Gets Hurt
Statistics about 149 million credentials can feel abstract. Let's make it concrete. Here are the kinds of people whose credentials were in this database and what actually happens to them.
The Account Takeover Victim
Someone had their email and social media credentials in the database. An attacker logs in. They change the password. They modify the recovery information. The victim is locked out.
The attacker doesn't immediately sell the access. They wait. They send friend requests to the victim's contacts, attempting to build credibility. They wait for the victim to reach out through an alternative channel. When the victim does, the attacker offers to help reset the account in exchange for payment, or threatens to delete the account permanently unless paid.
This happens thousands of times annually. Victims pay because they've lost access to accounts full of memories, contacts, and digital identity.
The Banking Fraud Victim
Someone's banking credentials were exposed. An attacker logs into their account immediately. The bank's security systems detect the unauthorized access and temporarily lock the account, but the attacker has already transferred $3,000 to another account they control.
The victim goes through the fraud dispute process. The bank eventually reverses the transaction, but it takes 30 days. Meanwhile, the victim is without those funds. The fraud also triggers fraud alerts that prevent the victim from accessing their own account legitimately for weeks.
The emotional toll of that experience is real. Even if the money is returned, the victim feels violated. They've lost trust in their bank.
The Extortion Victim
Someone's dating app credentials were in the database. An attacker accesses their account and screenshots conversations and profile information. The attacker emails the victim: "I have screenshots of your dating profile. If you don't send me $400 in Bitcoin in 24 hours, I'm sending this to everyone in your contact list."
The victim is terrified. They're in a relationship and don't want their partner seeing their dating profile. They're closeted and terrified of being outed. They're in a profession where this information could cause serious professional consequences.
The victim pays. This particular attacker probably doesn't follow through on the threat (because they'd be discoverable), but the victim has already lost $400. Thousands of victims pay thousands of times, making extortion incredibly profitable.
The Undetected Long-Term Compromised Victim
Someone's email credentials were exposed. An attacker logs in and never tells anyone. They just watch. They set up forwarding rules so they receive copies of incoming emails. They periodically reset passwords on connected accounts.
The victim has no idea they're compromised. The attacker spends months observing, learning, and building a profile. They see work emails. They see financial emails. They see sensitive information.
One day, months later, the attacker decides to act. They know the victim's routine. They know when they're traveling. They know their account structures. They conduct a targeted attack that succeeds because of the intelligence they gathered through months of observation.
These aren't edge cases. These are the actual outcomes from credential breaches at scale.
Industry Response and Lessons Learned
How has the cybersecurity industry responded to incidents like this?
Increased Focus on Threat Intelligence
Security companies now actively monitor for exposed databases and credential caches. They've built services that automatically search for breached data and alert organizations when their employees' credentials appear in exposures.
This doesn't prevent the initial breach, but it accelerates response. Organizations can notify affected users more quickly. They can force password resets before attackers weaponize the credentials.
Better Breach Detection and Response Frameworks
Major cloud providers have improved their monitoring for unusual account activity. They detect mass downloads from cloud storage containers. They alert on suspicious access patterns. They can take offline potentially dangerous resources more rapidly than a month-long bureaucratic process.
But there's still work to be done. The month-long timeline in this incident is unacceptable. We need automated systems that can more rapidly quarantine exposed data.
Credential Monitoring as a Service
An entire industry has emerged around monitoring whether credentials have been exposed in breaches. Services like "Have I Been Pwned?" allow individuals to check. Enterprise services allow organizations to monitor all their employees' accounts.
This is reactive (it doesn't prevent the breach), but it's better than being completely blind to your compromise status.
The Zero-Trust Architecture Movement
There's increasing recognition that the traditional security model (secure perimeter, trusted insiders) doesn't work. The zero-trust model assumes every access is potentially malicious. Every request requires authentication and authorization. Every access is logged and analyzed.
This model doesn't prevent credentials from being stolen, but it prevents compromised credentials from being useful. Even with your password, an attacker can't access resources without satisfying additional security requirements.
Prevention: Building Better Systems
How do we prevent incidents like this in the future? The answer involves changes at multiple levels.
Organizations Must Implement Security Fundamentals
Organizations storing credentials (which is basically all of them) must encrypt them using cryptographic standards like bcrypt or Argon 2. They must not store passwords in plain text under any circumstances.
They must implement rate limiting on login attempts to prevent brute-force attacks. They must log all access to sensitive data. They must audit those logs for anomalies.
They must mandate multi-factor authentication for employee accounts, especially administrative accounts. They must conduct regular security audits and penetration testing.
These aren't new recommendations. They're industry standards. Yet so many organizations still fail at these basics.
Users Must Adopt Stronger Authentication
People need to embrace authentication methods beyond passwords. Start with two-factor authentication. Move toward passkeys and hardware keys. Stop reusing passwords.
Use password managers. Let them generate and store unique 20+ character passwords for every service. Yes, that means password managers become a critical infrastructure component. But they're more secure than the alternative of users attempting to remember passwords.
Industry Needs Rapid Response Infrastructure
We need standardized emergency protocols for critical exposures. When someone discovers an unencrypted database containing millions of credentials, there needs to be a way to immediately take it offline.
This might involve:
- Dedicated response teams at major cloud providers
- Automated systems that can quarantine resources based on security researcher reports
- Legal frameworks that enable rapid action without needing to identify the account owner first
- Better coordination between companies and law enforcement
The month-long timeline shouldn't exist in 2025.
Regulatory Requirements for Security
Governments are increasingly mandating security practices. These requirements drive behavior change at scale.
Mandatory 2FA for sensitive systems. Mandatory encryption for stored data. Mandatory breach notification within specific timeframes. Mandatory security audits. Fines for non-compliance.
These regulations exist for a reason. They force organizations to take security seriously.
Moving Forward: What You Should Do Right Now
This has been a lot of information. Let's distill it into actionable steps.
Immediate (Today)
- Check if your email is in this breach using breach notification services
- If it is, change your password immediately for that account
- Enable two-factor authentication on your email account
- Review your most critical accounts (banking, crypto) for unauthorized access
This Week
- Change passwords on all accounts you've used the same password for
- Enable two-factor authentication on banking and financial accounts
- Review your credit report for fraudulent accounts
- Consider using a password manager if you're not already
This Month
- Enable two-factor authentication on all accounts with sensitive data
- Consider identity theft protection services
- Set up credit monitoring
- Review and update your digital security practices
Ongoing
- Keep your software and devices updated
- Run antivirus and anti-malware software
- Monitor your accounts for suspicious activity
- Use unique passwords everywhere
- Be cautious about phishing attempts

FAQ
What exactly is a data leak and how is it different from a data breach?
A data leak typically refers to data that's been exposed publicly or to unintended parties without active hacking involved (like this incident where data was just sitting unencrypted). A data breach usually implies that unauthorized individuals actively hacked into systems to steal data. In practice, the distinction matters less than the outcome: your credentials are exposed and at risk.
How do attackers actually use exposed credentials in practice?
Attackers use exposed credentials primarily through credential stuffing (testing them against other services), direct account takeover to steal money or information, or selling them to other criminals. For financial accounts, they might attempt immediate theft. For social media, they might establish persistence or use it as a jumping-off point to compromise email accounts. The approach varies based on what type of account was compromised and how valuable it is.
Is it really necessary to change all my passwords, or just the important ones?
You should prioritize the most critical accounts first (email, banking, crypto), but you should eventually change all passwords if your credentials were in this database. The reason is that attackers will attempt credential stuffing against hundreds of services. Even if your password for a less important service seems secure, if it matches credentials in this database and you've reused it, you're at risk. A password manager makes changing all of them much more manageable.
How effective is two-factor authentication really against this type of attack?
Two-factor authentication is extremely effective against credential-based attacks. Even if attackers have your username and password, they can't access your account without the second factor. This is why organizations should mandate it for sensitive accounts and why individuals should enable it immediately. It's not perfect (some 2FA methods like SMS can be intercepted), but authenticator apps and hardware keys are very secure.
What should I do if I find my credentials in this specific database?
First, change the password for that account immediately, then enable two-factor authentication if available. Monitor that account for unauthorized access for the next 30 days. If it's an email or financial account, consider placing a fraud alert or credit freeze. Watch your credit reports over the next year for signs of identity theft. If you used that same password for other accounts, change those too. Consider identity theft protection services if you're particularly concerned.
Can companies be held legally responsible for not protecting against these types of breaches?
Companies can face legal liability depending on their jurisdiction and the specific regulations that apply. GDPR in Europe, various state laws in the US, and industry-specific regulations like HIPAA all create legal obligations to protect personal data. Penalties can include fines, forced notifications, and civil lawsuits from affected users. However, liability varies significantly based on whether the company was negligent and what security measures they had in place, which is why some companies still get away with inadequate security.
Why does it take so long to take exposed databases offline?
Several factors contribute to delays: identifying who actually owns or operates the server, jurisdictional issues, companies blaming subsidiaries or third parties, lack of emergency protocols, and bureaucratic processes that require multiple approvals. In this case, the subsidiary structure created confusion about responsibility. Ideally, major cloud providers would have automated systems that could immediately quarantine obviously dangerous resources, but this infrastructure is still developing.
How can I tell if my accounts have actually been compromised by someone in my account?
Look at your account's login history or security activity logs. Most services now show recent login locations, times, and device types. If you see access from locations you've never been or devices you don't recognize, that's a red flag. Check if recovery email addresses or phone numbers have been changed. Look for unfamiliar two-factor authentication methods. Some services also let you revoke access from specific devices. If anything looks wrong, immediately change your password and secure your account.
Are password managers safe to use, or are they just another attack vector?
Password managers are significantly more secure than reusing passwords or trying to remember unique passwords. They encrypt all stored passwords, so even if someone hacks the password manager itself, they can't access your individual passwords without knowing your master password. Popular password managers like Bitwarden, 1 Password, and Dashlane undergo regular security audits. The main attack vector would be someone compromising your master password or your email account (which is why those need strong security themselves).
Should I be concerned about older breaches I might be part of, or just focus on recent ones?
Older breaches are still concerning because credentials remain valuable indefinitely. Someone might have purchased your information from a 5-year-old breach but only attempted credential stuffing recently. The risk doesn't expire. If you know you're in an old breach and you haven't already, change your password and enable 2FA. The sooner you act, the better.
Conclusion: The Path Forward
The discovery of 149 million exposed credentials in an unencrypted cloud storage container is a wake-up call for both individuals and organizations. This wasn't some sophisticated attack. This was a basic misconfiguration. Someone put sensitive data on the internet with no protection whatsoever. And it took a month to get it offline.
What we're really looking at here is a failure of systems. Endpoint security failed to prevent the malware that harvested these credentials. Cloud configuration security failed to prevent the data from being placed in a public container. Incident response systems failed to rapidly take the exposed data offline. Authentication systems failed because passwords alone don't provide adequate security.
The good news is that all of these failures are preventable. Organizations can implement endpoint detection and response. They can configure cloud storage securely. They can establish rapid response protocols. They can mandate multi-factor authentication.
Individuals can take steps to protect themselves right now. Change your passwords. Enable two-factor authentication. Use a password manager. Monitor your accounts. Use unique passwords everywhere.
The technology to prevent these incidents exists. The practices to prevent them are documented. What's missing is widespread adoption. Too many organizations don't implement security fundamentals. Too many people don't use strong authentication. Too many systems still rely on passwords as the primary security mechanism.
This incident will happen again. Another database will be discovered exposed. Another batch of credentials will be compromised. Until we collectively shift toward stronger security practices, incidents like this will remain common.
But you don't have to be a victim. Start today. Check if you're in this breach. Secure your accounts. Enable two-factor authentication. Take control of your digital security.
The future of internet security doesn't depend on perfect companies or perfect systems. It depends on individuals and organizations making the conscious choice to implement security practices today. Make that choice. Your accounts will thank you.
Use Case: Teams managing critical accounts can use Runable to automate password rotation policies, generate secure credential documentation, and create audit reports for compliance purposes.
Try Runable For FreeKey Takeaways
- 149 million credential pairs were exposed in an unencrypted cloud storage container, containing usernames and passwords from financial services, crypto exchanges, social media, dating apps, and government email accounts
- The database was indexed using reverse host paths suggesting it was built systematically through malware infostealers, keyloggers, or aggregated from previous breaches
- Credential exposure creates multiple attack vectors: immediate account takeover, credential stuffing against other services, extortion and blackmail, and long-term identity theft risk
- Response to the breach was catastrophically slow, taking nearly 30 days to take the database offline due to corporate shell structures and lack of emergency protocols
- Immediate protection steps include changing passwords on critical accounts, enabling two-factor authentication, checking credit reports, and considering identity theft protection services
Related Articles
- PcComponentes Data Breach Denial: What Really Happened [2025]
- SMS Sign-In Links: A Critical Security Vulnerability Affecting Millions [2025]
- Under Armour 72M Record Data Breach: What Happened [2025]
- Under Armour Cyberattack 2025: What 7M Users Need to Know [Guide]
- LastPass Phishing Scam: How to Spot Fake Support Messages [2025]
- 1Password Phishing Protection: How the New Browser Feature Saves You [2025]
![149 Million Credentials Exposed: The Massive Data Leak Explained [2025]](https://tryrunable.com/blog/149-million-credentials-exposed-the-massive-data-leak-explai/image-1-1769188458295.jpg)



