Pegasus Spyware, NSO Group, and State Surveillance: The Landmark £3M Saudi Court Victory [2025]
In January 2026, a London High Court made legal history by piercing the veil of state immunity to award a Saudi activist more than £3 million in damages after finding "compelling evidence" that his iPhone had been compromised with Pegasus spyware. This wasn't just another surveillance case. It represented the first time a government had been successfully held accountable in a Western court for weaponizing NSO Group's mobile surveillance tool against a private citizen living abroad. According to The Guardian, this ruling marks a significant precedent in international law.
Ghanem Al-Masarir, a London-based satirist and human rights activist, had sued Saudi Arabia after his devices were targeted with this government-exclusive spyware around the same time he was physically assaulted in London in 2018. The court's ruling validated what researchers, journalists, and activists have suspected for years: Pegasus isn't just a surveillance tool—it's a weapon wielded by authoritarian regimes to silence dissidents, suppress free speech, and coordinate hybrid attacks combining digital and physical violence. As reported by Modern Ghana, the implications of this case are far-reaching, affecting how digital privacy is perceived globally.
This case matters far beyond the courtroom. It exposes the architecture of digital oppression, reveals how NSO Group's surveillance technology enables human rights abuses, and demonstrates the growing vulnerability of activists and journalists operating in exile. It also raises fundamental questions about corporate responsibility, government accountability, and the future of digital privacy in an age when spyware has become normalized as a tool of statecraft.
Let's unpack what happened, why it matters, and what it reveals about the intersection of cybersecurity, human rights, and international law.
The Pegasus Spyware Arsenal: What Makes It Devastating
Pegasus isn't just sophisticated. It's categorically different from consumer malware because it operates at a level of access that most security researchers didn't think possible until the tool became public knowledge through the Pegasus Project investigation in 2021. According to Dark Reading, Pegasus exploits zero-day vulnerabilities to penetrate iPhones and Android devices without requiring any user interaction.
Developed and sold exclusively by NSO Group, an Israeli cyber-intelligence firm, Pegasus exploits zero-day vulnerabilities (previously unknown security flaws) to penetrate iPhones and Android devices without requiring any user interaction. You don't need to click a malicious link. You don't need to download an attachment. The spyware can be installed remotely, invisibly, and with zero trace on the device itself.
Once installed, Pegasus grants operators complete access to the target device. This includes real-time access to messages, emails, call logs, location data, photos, videos, and any other information stored on the phone. The spyware can activate the microphone and camera at will, essentially turning the device into a remote surveillance pod that the target carries everywhere.
What makes Pegasus particularly insidious is its stealth profile. Unlike conventional malware that might cause battery drain, network congestion, or suspicious activity, Pegasus operates invisibly. Targets have no indication they're being monitored. The spyware doesn't leave obvious traces in system logs. Apple can't detect it with standard security tools because it exploits vulnerabilities Apple itself didn't know existed, as noted by Wired.
NSO Group has always maintained that Pegasus is designed exclusively for "authorized law enforcement and intelligence use" targeting criminals and terrorists. The company claims it implements strict controls, vetting processes, and oversight mechanisms to ensure governments don't abuse the tool. This narrative collapsed spectacularly in 2021 when the Pegasus Project, a collaborative investigation by major news organizations, revealed that the tool had been used against journalists, opposition politicians, lawyers, doctors, human rights activists, and business executives across dozens of countries, as highlighted by Aliran.
The financial incentive is massive. NSO Group reportedly charges between
For targets like Al-Masarir, the implications were existential. A government with access to every message, every location, every call, and every document has the power to crush dissent, silence critics, and coordinate physical attacks against targets whose whereabouts are now known with precision.
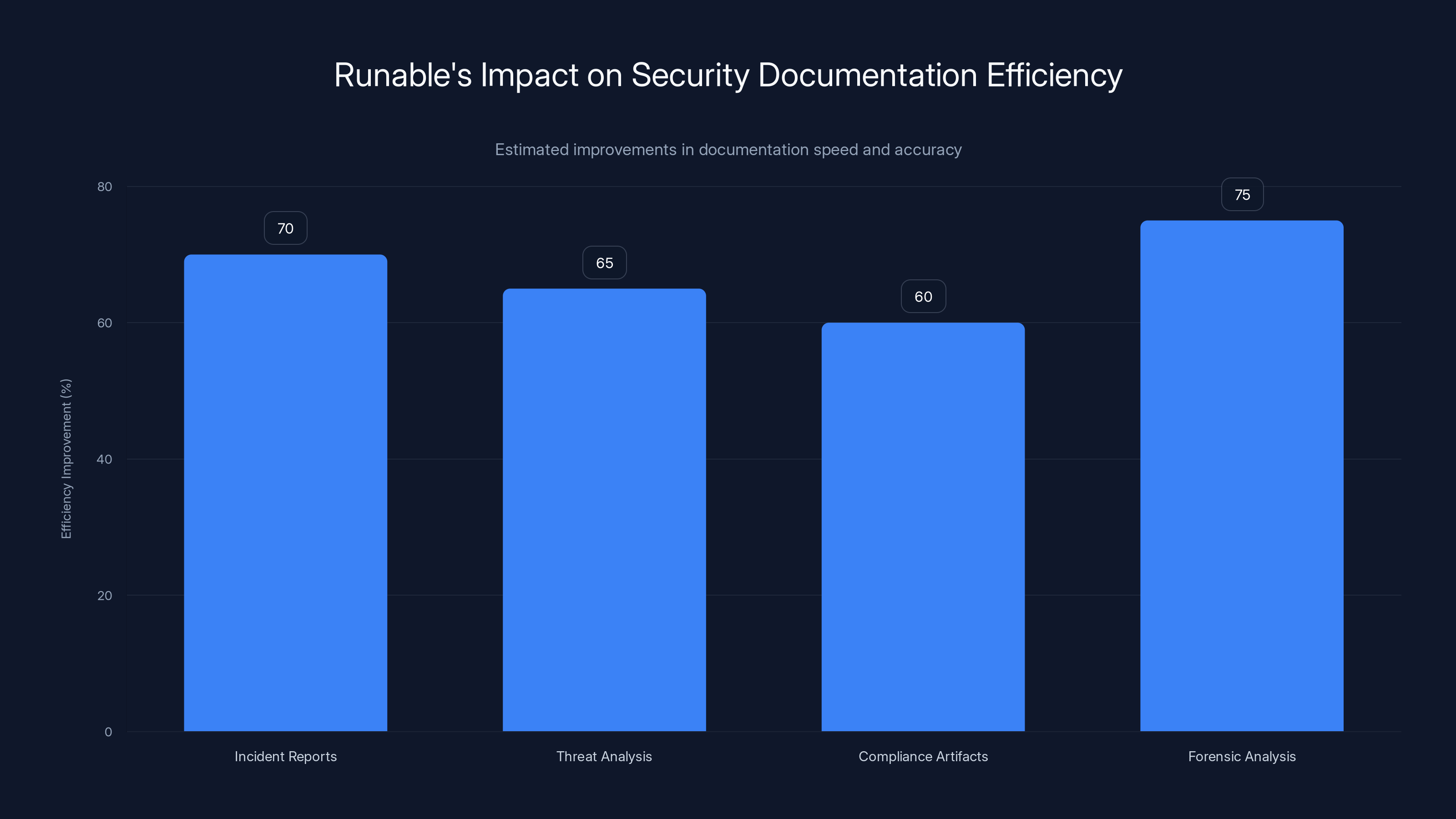
Runable significantly enhances the efficiency of creating security documentation, with improvements ranging from 60% to 75%. Estimated data.
Al-Masarir's Story: From YouTube Satirist to Surveillance Target
Ghanem Al-Masarir isn't a politician or a formal activist organization. He's a satirist. His YouTube channel featured him criticizing Saudi Arabia's government, its policies, and its leadership through comedy, commentary, and social critique. The channel accumulated millions of viewers and made him a genuinely influential voice in Arab diaspora communities.
But in 2018, his work became dangerous.
First, his iPhone was targeted with Pegasus spyware. Then, weeks later, he was physically assaulted in London by individuals he believed were working on behalf of Saudi Arabia's government. The assault was brutal enough to require hospitalization. The timing and coordination suggested that the physical attack followed from the digital surveillance—attackers needed to know his location, habits, and patterns to conduct the assault.
This is the hybrid attack model that researchers have documented repeatedly. Digital surveillance identifies targets and maps their vulnerabilities. Physical attacks follow once the intelligence gathering is complete. The two tactics reinforce each other, creating a coordinated campaign that combines cyber and kinetic violence.
The assault and the spyware targeting caused significant psychological trauma. Al-Masarir described the experience as causing deep depression, effectively ending his YouTube career. His ability to work, to create, and to maintain his public platform had been destroyed by a coordinated campaign combining digital and physical violence.
What makes Al-Masarir's case unique isn't the abuse itself. Hundreds of activists have been targeted with Pegasus. What's unique is that he had the resources, the legal support, and the jurisdiction to actually pursue the case in court, as detailed by Law360.
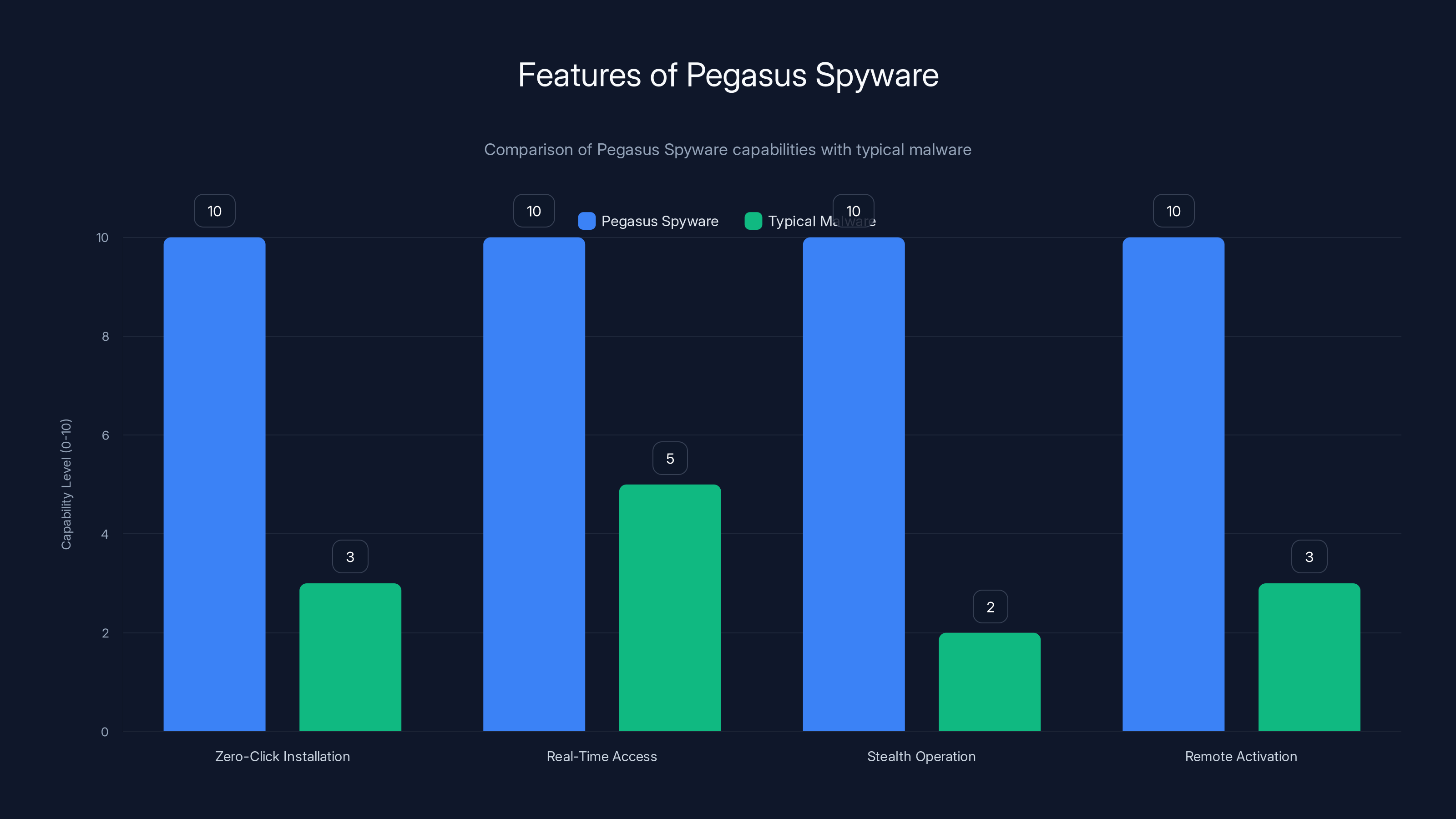
Pegasus Spyware significantly outperforms typical malware in key areas such as zero-click installation and stealth operation, making it a powerful tool for surveillance. Estimated data based on feature descriptions.
The Legal Battle: Piercing State Immunity
When Al-Masarir filed his lawsuit in 2019, Saudi Arabia's response was blunt: the kingdom claimed state immunity. In international law, this is a powerful doctrine. Sovereign nations traditionally cannot be sued in foreign courts for official acts committed within their own territory or in service of state functions. This immunity exists to prevent courts from interfering with foreign affairs.
Saudi Arabia had successfully used this argument before. When the kingdom faced accusations that Crown Prince Mohammad bin Salman had ordered the murder of Washington Post journalist Jamal Khashoggi at the Saudi consulate in Turkey in 2018, Saudi Arabia invoked state immunity and largely escaped accountability in most jurisdictions.
But the London High Court took a different approach. Justice Pushpinder Saini examined the nature of the alleged conduct and determined that hacking a private citizen's phone, even if authorized by state actors, wasn't a legitimate state function deserving immunity. The court's reasoning was significant: surveillance of a private individual living in exile, conducted through commercial spyware, isn't the kind of official state conduct that immunity doctrines were designed to protect.
The rejection of state immunity opened the door for the substantive case. Saudi Arabia, recognizing it had lost the immunity argument, chose not to participate further in the litigation. This meant the court would hear evidence and arguments primarily from Al-Masarir's legal team without meaningful contradictory evidence from the Saudi government.
With state immunity rejected, Justice Saini reviewed the technical evidence, expert testimony, and circumstantial indicators that Al-Masarir's iPhones had been compromised with Pegasus spyware. The evidence was compelling enough that the judge ruled there was "compelling basis for concluding that [al-Masarir's] iPhones were hacked by Pegasus spyware which resulted in the exfiltration of data from those mobile phones."
The judge further determined that the hacking was "directed or authorised" by the Saudi government or its agents. This is the critical finding. It didn't just confirm that spyware was used. It attributed the attack to Saudi Arabia's government at the highest levels.
The court also found it probable that the Saudi government was responsible for the physical assault. This was significant because it validated the hybrid attack model and showed the coordination between digital surveillance and physical violence.
The damages award of £3 million (approximately $4.1 million USD) was substantial, though it paled in comparison to the actual harm caused to Al-Masarir's life, career, and mental health. Still, it represented the first time a Western court had assigned monetary damages specifically for state-sponsored surveillance using Pegasus spyware.
The Broader Implications: Corporate Liability and State Accountability
The Al-Masarir case raises uncomfortable questions for NSO Group. The company has always positioned itself as a neutral vendor of tools, arguing that responsibility for abuse lies entirely with the governments that purchase the technology. This is technically true—NSO Group itself doesn't operate Pegasus. It sells access to governments that deploy the spyware against targets they designate.
But this liability model is increasingly untenable. NSO Group controls access. The company chooses which governments to sell to. The company can monitor how its tools are being deployed. And the company has knowledge that some governments will inevitably abuse the technology.
The London court's ruling doesn't directly hold NSO Group liable, but it establishes that governments using Pegasus can be held accountable for the consequences. This creates a legal pathway for victims to pursue damages against the state actors who weaponized the spyware.
For NSO Group itself, the risks are mounting. Lawsuits have been filed in multiple jurisdictions. The United States Department of Commerce has effectively blacklisted NSO Group, restricting its ability to operate and banning exports of its technology. Tech giants like Apple have initiated legal action against the company. Several countries have begun formal investigations into NSO Group's practices and client relationships, as reported by EDRi.
The company's business model depends on secrecy and plausible deniability. As courts begin holding governments accountable for Pegasus attacks, the reputational and legal risks for NSO Group intensify. Clients may become more cautious about purchasing the tool. Underwriters and investors may become more skeptical of the company's longevity.
Moreover, the London ruling establishes a precedent. Other victims of documented Pegasus attacks now have a legal framework for pursuing claims in jurisdictions that don't recognize state immunity. This could trigger a wave of similar lawsuits.

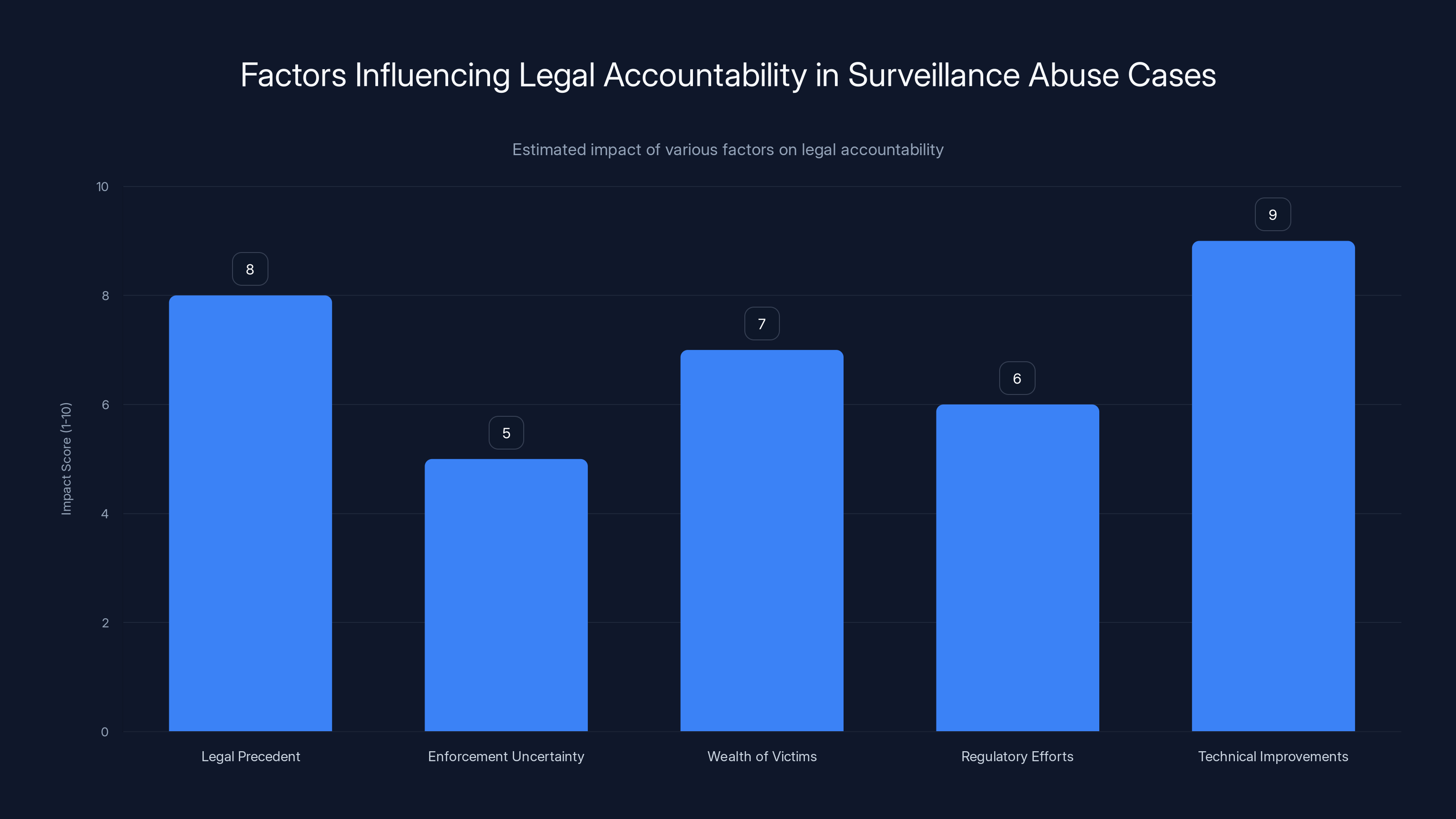
Legal precedent and technical improvements have the highest estimated impact on enhancing legal accountability against surveillance abuse. Estimated data.
NSO Group's Defense: The Authorized Operator Argument
When NSO Group responds to Pegasus allegations, the company consistently makes the same argument: we sell the tool to authorized governments for authorized purposes. Any misuse is a violation of the client agreement and the client's responsibility, not ours.
This argument has several problems. First, NSO Group's vetting process for determining which governments are "authorized" and which aren't is opaque. The company has sold Pegasus to Mexico, UAE, Saudi Arabia, Morocco, India, and numerous other countries with documented records of government abuse. If NSO Group is genuinely vetting clients, the standards are being applied inconsistently or are deeply flawed.
Second, NSO Group has demonstrated minimal capability or willingness to enforce client agreements when abuses are documented. When the Pegasus Project revealed hundreds of instances of abuse, NSO Group issued a statement saying these cases were under investigation and that it terminated relationships with misbehaving clients. But the company didn't provide concrete evidence of terminations or corrective action. And subsequent investigations found that despite these promises, surveillance using Pegasus continued unabated in many countries.
Third, NSO Group controls the infrastructure that enables Pegasus deployments. The company can monitor how the tool is being used. It can see which targets are being surveilled. It can identify patterns of abuse. Yet the company has consistently maintained that this monitoring data is proprietary and unavailable to courts, governments, or oversight bodies.
This creates a perverse incentive structure. NSO Group profits from selling Pegasus. The company isn't incentivized to aggressively police misuse because doing so would antagonize clients and threaten contract renewals. The only meaningful external accountability comes from court cases, regulatory action, and reputational pressure.
The Surveillance State Context: Where Pegasus Fits
Pegasus is one tool in an increasingly comprehensive surveillance ecosystem. Authoritarian and semi-authoritarian governments have invested heavily in digital surveillance infrastructure. This includes monitoring of telecommunications networks, financial transactions, social media, email, messaging apps, and increasingly, hardware-level device compromise.
What makes Pegasus distinctive is its capability level and its exclusivity. Other surveillance tools are available on the open market or can be developed domestically. Pegasus, by contrast, represents the cutting edge of mobile device compromise. Only governments with the resources to purchase from NSO Group or develop equivalent capabilities in-house can deploy it.
This creates a surveillance pyramid. At the bottom, mass surveillance of telecommunications infrastructure captures everyone's data indiscriminately. In the middle, behavioral analysis and targeted searches identify individuals of interest. At the top, Pegasus provides granular surveillance of high-value targets.
Activists, journalists, and opposition figures exist at the top of this pyramid. Once a government decides a person is a threat, resources are deployed that make privacy virtually impossible. The target cannot know if they're being monitored. They cannot defend themselves against attacks enabled by comprehensive surveillance. They cannot even safely communicate with lawyers, family, or colleagues.
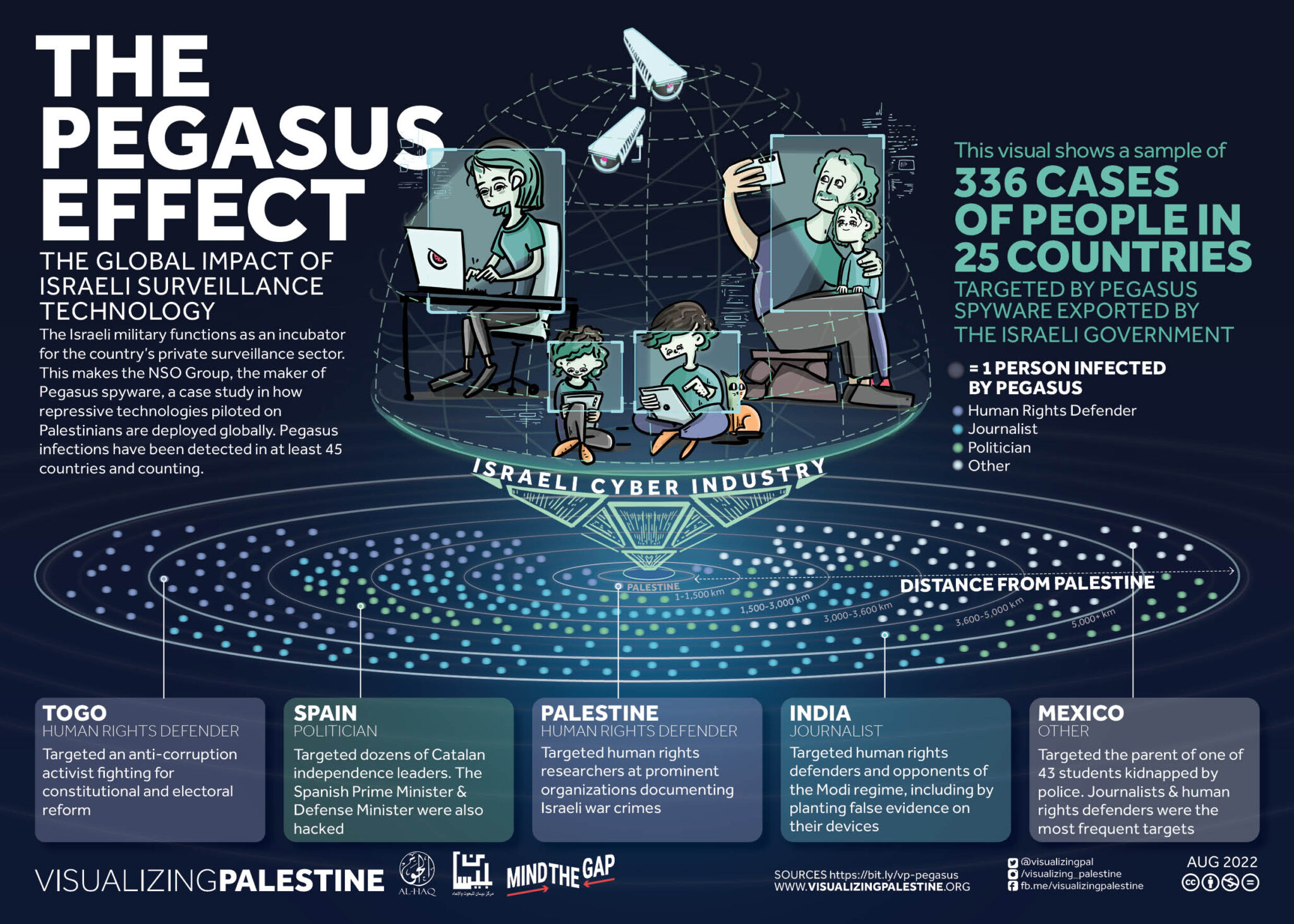
This isn't theoretical. Researchers at the Citizen Lab have documented instances where activists' locations from Pegasus surveillance were used to inform physical attacks. In some cases, targets were arrested immediately after their location was revealed by surveillance. In other cases, family members were detained or harassed, as noted by WebProNews.

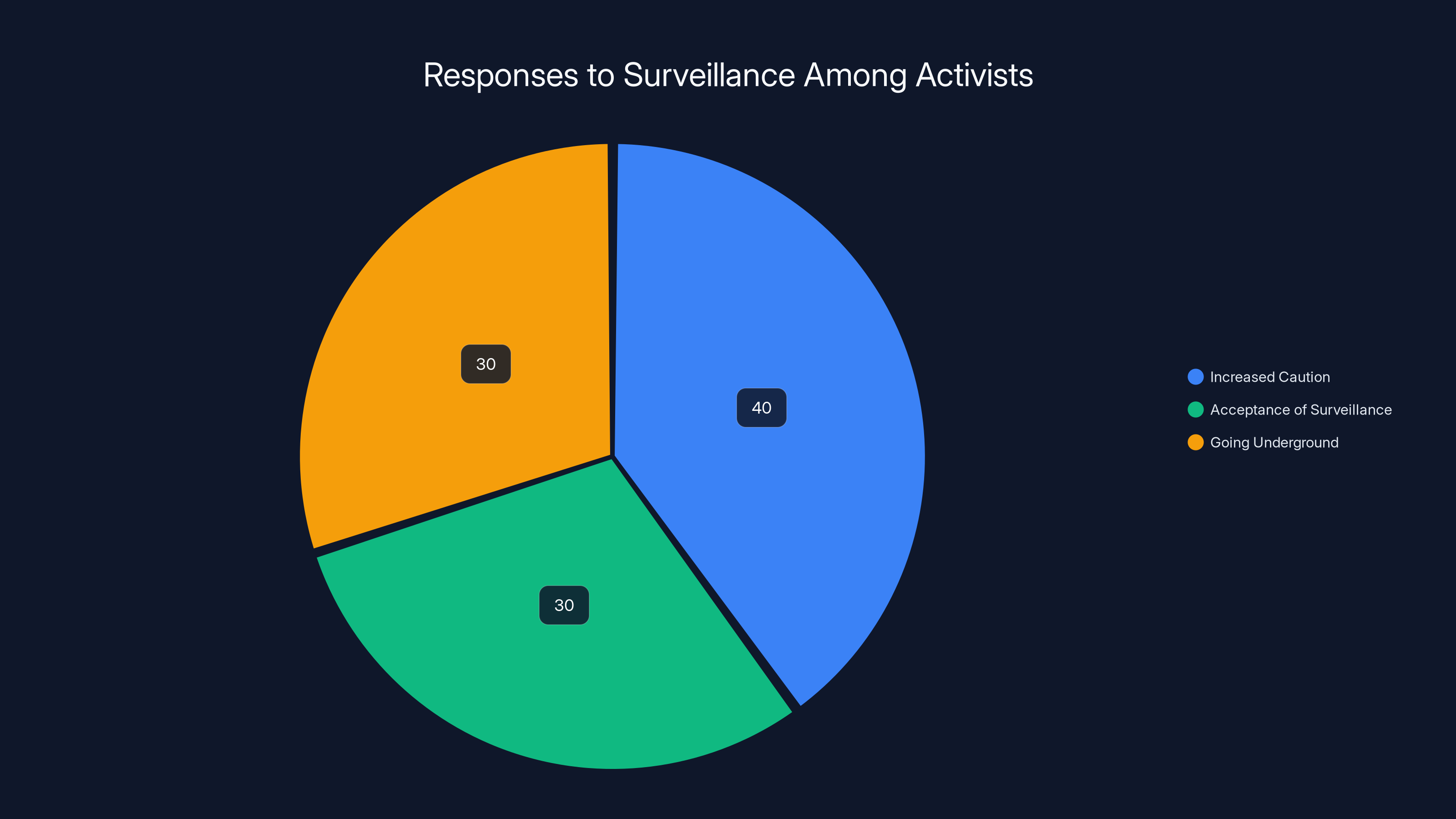
Estimated data shows that activists respond to surveillance by increasing caution (40%), accepting surveillance (30%), or going underground (30%).
The Physical Attack Component: Hybrid Threats
One of the most significant aspects of the Al-Masarir case is the court's finding that the Saudi government was probably responsible for the physical assault. This isn't a coincidence. Multiple independent analyses have documented that digital surveillance using Pegasus is often coordinated with physical threats.
Here's how it works. Digital surveillance identifies the target's location, daily routines, security patterns, and vulnerabilities. Once this intelligence is gathered, physical attacks can be planned with precision. The attacker knows when the target will be at a specific location. They know the target's schedule. They know whether the target has security or how to evade it.
These hybrid attacks are particularly effective against activists in exile. Targets assume they're relatively safe abroad, away from the government that's persecuting them. But with Pegasus, geography becomes irrelevant. A government in Saudi Arabia can know, in real-time, where Al-Masarir is in London. Agents can be sent to that location. The physical attack follows the digital reconnaissance.
What makes these hybrid attacks particularly insidious is that the victim often doesn't connect the dots. They know their phone might be compromised. They're cautious about digital security. But they also have to leave their house, go to work, meet with colleagues. The digital surveillance doesn't prevent them from living. It just enables precise targeting when a physical attack is planned.
The court's finding that Saudi Arabia was probably responsible for both the digital surveillance and the physical attack validates this threat model. It shows that governments aren't just using Pegasus to gather intelligence. They're using it as an operational tool, coordinating surveillance with physical violence against targets abroad.

Broader Patterns: Pegasus Abuse Across Governments
The Al-Masarir case isn't unique in terms of the abuse. What's unique is that it resulted in a court judgment. Hundreds of other individuals have been targets of documented Pegasus surveillance. Many of them have evidence of targeting. Few have pursued legal action, and fewer still have succeeded.
In Mexico, journalists covering corruption and cartel violence have been targeted with Pegasus. Researchers found that surveillance was heaviest when these journalists were covering politically sensitive stories about government officials. The surveillance served as a tool to track the journalists' reporting and identify their sources.
In the UAE, human rights defenders, lawyers, and political activists have been targeted. In one case, a human rights lawyer was surveilled intensively before being arrested on charges widely regarded as politically motivated.
In India, journalists critical of Prime Minister Narendra Modi have been targeted. Opposition politicians have been surveilled. In one case, a journalist was arrested shortly after being targeted with Pegasus, raising questions about whether surveillance enabled or informed the arrest.
In Morocco, journalists, politicians, and activists have been targeted. Amnesty International documented attacks using Pegasus and attributed them to the Moroccan government.
In Pakistan, journalists and human rights activists have been surveilled. In Bahrain, opposition figures and lawyers have been targeted. In Poland, opposition politicians and judges have been surveilled.
The pattern is consistent. Governments that purchase Pegasus tend to use it against domestic critics, opposition figures, and activists rather than against international terrorism suspects or organized crime. This suggests the tool is primarily being used for political control rather than for legitimate law enforcement purposes.

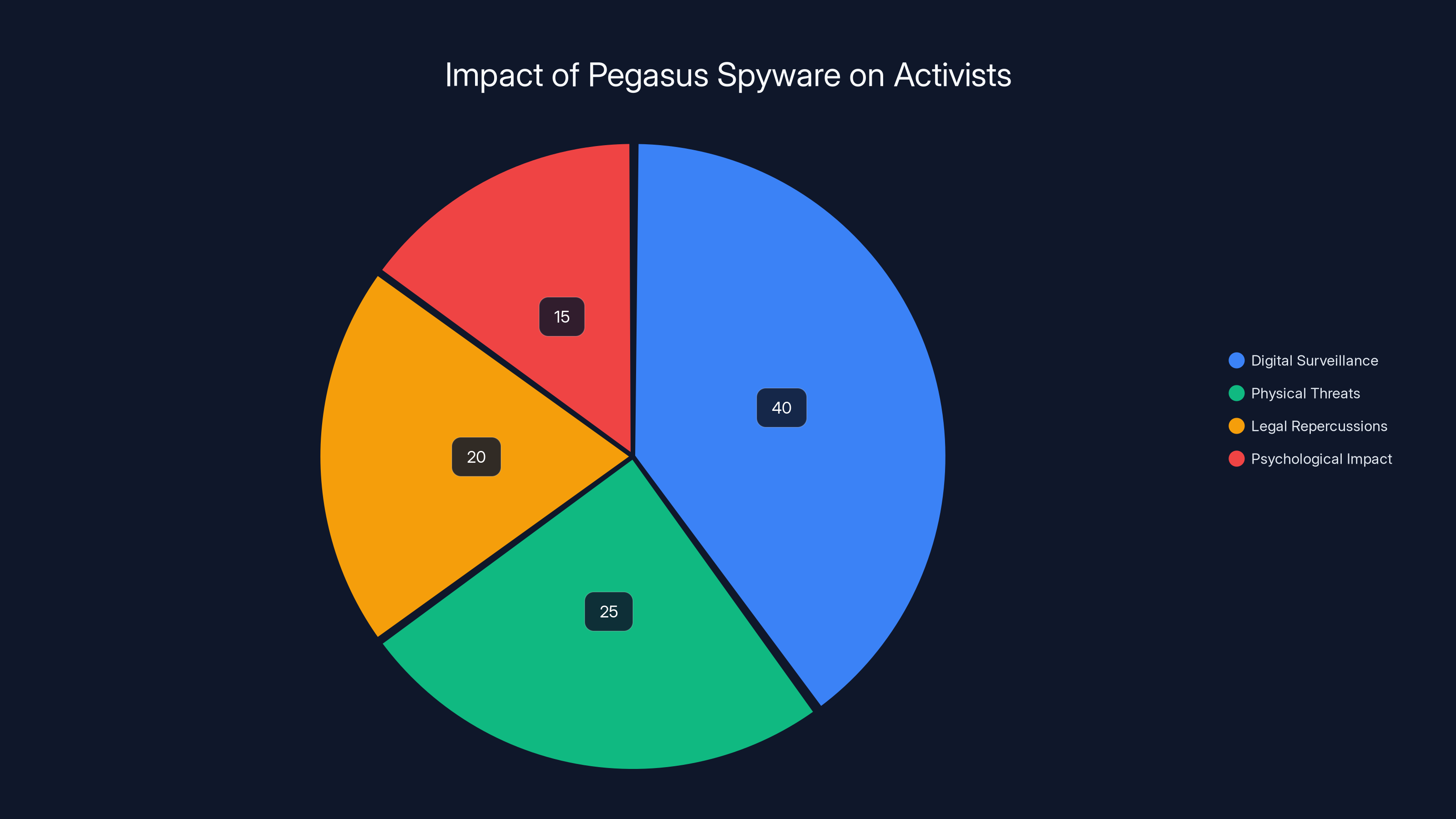
Estimated data suggests that digital surveillance is the most prevalent impact of Pegasus spyware, followed by physical threats and legal repercussions.
The Technical Evidence: How We Know
One of the remarkable aspects of the Al-Masarir case is that it relied on technical forensics to establish that Pegasus was used. This is significant because Pegasus is designed to be stealthy. The spyware doesn't leave obvious traces.
However, researchers at organizations like the Citizen Lab and Amnesty International's Security Lab have developed methods to identify when iPhones have been compromised with Pegasus. These methods rely on several techniques:
First, researchers can examine network traffic patterns. When Pegasus is active, it sends encrypted data to command-and-control servers. By analyzing network logs and packet captures, researchers can identify communications with known Pegasus infrastructure. Apple's iCloud provides metadata about device access and activities that can reveal suspicious patterns.
Second, researchers can look for forensic artifacts. Even though Pegasus is stealthy, it leaves some traces. Changes to system files, modifications to certificates, unusual process creation, and other forensic indicators can suggest compromise. These require deep technical knowledge and access to sophisticated analysis tools, but they're possible to identify.
Third, timeline analysis can establish correlation. If a target received a suspicious message or link, and shortly thereafter their device behavior changed in ways consistent with Pegasus compromise, that correlation can be suggestive of the attack.
Fourth, and most convincingly, researchers can sometimes obtain samples of Pegasus spyware code or configuration files. When the Pegasus Project gained access to a database of surveillance targets, this provided direct evidence of compromise. Some targets had been surveilled years earlier, but the evidence of the surveillance was preserved in records.
For Al-Masarir's case, the technical evidence was strong enough that Justice Saini found it "compelling" that Pegasus had been used. This required testimony from technical experts, possibly including researchers from the Citizen Lab or similar organizations, who could explain how they identified the compromise.

Runable's Role in Digital Security Automation
As organizations grapple with increasingly sophisticated cyber threats like Pegasus, the need for robust security infrastructure has never been clearer. Runable provides an AI-powered automation platform that helps teams create security documentation, incident reports, and compliance artifacts with remarkable speed.
While Runable isn't a cybersecurity tool per se, security teams use it to automate the creation of incident response reports, threat analysis documents, and security briefings. When a potential compromise like Pegasus targeting is detected, security teams can use Runable to rapidly generate comprehensive incident documentation, forensic analysis reports, and remediation plans.
Use Case: Security teams automating incident response documentation and creating real-time threat analysis reports when suspicious device activity is detected.
Try Runable For FreeFor organizations tracking spyware threats and coordinating security responses, Runable starting at $9/month helps teams generate the documentation and analysis artifacts needed for rapid threat response.

Estimated data shows that technical progress and legal accountability are key strategies, each contributing significantly to combat surveillance technology abuse. Estimated data.
The International Response: Regulations and Restrictions
Following the Pegasus Project revelations, governments and international bodies have begun moving against NSO Group and similar surveillance vendors.
The United States Department of Commerce placed NSO Group on the Entity List, effectively restricting the company's ability to conduct business with American entities and blocking exports of its technology. This is a serious blow because many of NSO Group's clients and business partners have connections to U.S. markets.
The European Union has initiated regulatory discussions about controlling the export of surveillance technology. Several EU member states have banned government procurement of NSO products or are considering restrictions.
Apple filed a lawsuit against NSO Group alleging that Pegasus violates the company's intellectual property and terms of service. While the legal outcome remains uncertain, the lawsuit reflects Apple's growing frustration with surveillance tools that undermine its security infrastructure.
Multiple civil rights organizations have called for a comprehensive ban on government surveillance tools like Pegasus, arguing that the risk of abuse is so high that no vetting process can adequately control it.
These regulatory efforts face headwinds. NSO Group argues that restricting its technology will simply drive countries toward developing domestic surveillance tools or purchasing from less scrupulous vendors. The company contends that NSO at least implements some controls, whereas adversary nations developing indigenous tools have no oversight.
This argument has merit on its surface, but it ignores the fundamental problem: any surveillance tool this powerful will be abused. The issue isn't whether a particular government will misuse Pegasus. The issue is that some governments inevitably will, and when they do, victims have limited recourse.

The Path Forward: Accountability and Privacy
The Al-Masarir case establishes a legal precedent that may enable future victims to pursue damages against governments that have weaponized Pegasus spyware. But the case also highlights the limitations of legal accountability.
First, only victims with substantial resources can afford the legal costs of pursuing a case through the London High Court. Most Pegasus targets are activists, journalists, and dissidents in countries where they cannot pursue legal action domestically. Even accessing foreign courts requires resources and expertise.
Second, even when a judgment is issued, enforcement is uncertain. It's unclear whether Saudi Arabia will comply with the £3 million damages award. Enforcement against sovereign nations is notoriously difficult. They can refuse to pay, appeal indefinitely, or claim that the judgment is unenforceable in their territory.
Third, legal accountability is backward-looking. It addresses past harm but doesn't prevent future surveillance. Al-Masarir won his case, but that doesn't restore his YouTube career or reverse the psychological damage from years of surveillance and physical assault.
Real progress requires multiple approaches working in concert. Technical progress in device security can make tools like Pegasus harder to deploy. Regulatory restrictions can limit the market for surveillance technology. International pressure and reputational damage can discourage governments from using the most egregious tools. Corporate responsibility can push vendors to be more selective about clients. And legal accountability, when it's possible, can impose consequences on governments that abuse surveillance tools.
None of these approaches is sufficient on its own. Together, they might create enough friction to slow the proliferation and abuse of surveillance technology.

The Future of Spyware and Digital Surveillance
Pegasus won't disappear. NSO Group continues to operate despite mounting pressure. Other Israeli surveillance vendors are developing next-generation tools. Countries are investing in domestic surveillance capabilities that rival or exceed Pegasus in sophistication.
What will likely change is the deployment model and the visibility. As Pegasus becomes more restricted and more controversial, governments may shift toward deploying it more selectively and more carefully. They may reduce the transparency around surveillance targets to avoid creating evidence trails like the ones that enabled the Pegasus Project investigation.
Alternatively, governments may migrate toward other surveillance approaches. Hardware-level compromises through supply chain attacks, telecommunications infrastructure surveillance, and AI-driven behavioral analysis might offer similar capabilities with less reputational risk.
From a technological perspective, device manufacturers are steadily improving security. Apple's security architecture has become incrementally harder to compromise. Android security has also improved, though fragmentation remains a vulnerability. New security models like hardware security tokens and verified boot may eventually make attacks like Pegasus significantly more difficult.
But the arms race between security and offense will continue. Every security improvement generates pressure to develop more sophisticated exploits. Intelligence agencies invest heavily in finding and exploiting zero-day vulnerabilities. The financial incentives for surveillance tool developers remain substantial.
The real battle, then, isn't primarily technical. It's geopolitical, legal, and ethical. Can international law establish norms against government surveillance of private citizens abroad? Can countries collectively restrict the export and deployment of tools like Pegasus? Can corporate and civil society pressure push vendors toward greater responsibility?
The Al-Masarir case is a small victory in this larger struggle. It proves that courts can pierce the veil of state immunity when governments weaponize commercial surveillance tools. It establishes that victims can pursue damages. It creates precedent that other courts may follow.
But the case also illustrates how limited legal recourse is without supporting regulatory, technical, and diplomatic efforts. Real progress requires moving beyond litigation to systemic changes in how surveillance is regulated globally.

Real-World Impact on Activists and Journalists
For people like Al-Masarir, the technical and legal details matter less than the practical implications. A documented Pegasus targeting changes how you live. It changes how you work. It changes how you think about your own security.
Some activists respond by becoming more cautious. They limit their movements. They avoid predictable patterns. They assume their devices are compromised and treat them as untrusted. This defensive posture is necessary for survival, but it's also limiting. It reduces the activist's effectiveness and freedom.
Others respond by essentially accepting surveillance as a cost of doing their work. They continue operating relatively openly, knowing they're likely being monitored, but accepting that as part of the landscape of dissent in an age of surveillance.
Still others are driven underground, moving to jurisdictions where surveillance is less comprehensive or taking steps to become harder to locate.
The chilling effect of surveillance is real. When activists know they're being monitored, they may self-censor. They may avoid certain forms of reporting or activism that they fear will attract more intensive surveillance. They may avoid certain associations, assuming that those associations will be monitored and that monitoring may have consequences.
For journalists, the implications are profound. If a journalist knows their phone is compromised with Pegasus, they cannot safely communicate with sources. Sources cannot safely communicate with the journalist. The entire investigative process becomes compromised.
This is why the Al-Masarir case matters beyond the monetary damages. It provides some legal weight behind the principle that governments should not be able to unilaterally declare themselves immune from accountability when they weaponize surveillance tools against private citizens abroad.

FAQ
What is Pegasus spyware and how does it work?
Pegasus is government-exclusive mobile spyware developed by NSO Group that exploits zero-day vulnerabilities to remotely compromise iPhones and Android devices without any user interaction. Once installed, it grants operators complete access to the target device, including messages, emails, call logs, location data, photos, videos, and can even activate the microphone and camera for surveillance. The spyware operates invisibly, leaving minimal traces that would alert the target device owner.
How did the London High Court prove that Pegasus was used against Al-Masarir?
The court relied on technical forensic evidence presented by security experts who identified indicators of Pegasus compromise including suspicious network traffic patterns, communications with known command-and-control infrastructure, forensic artifacts in system logs, and timeline analysis correlating suspicious messages or events with changes in device behavior. Expert testimony from researchers at organizations like the Citizen Lab provided evidence of how Pegasus operates and how its presence can be identified on a compromised device.
Why did Saudi Arabia lose its state immunity claim in the Al-Masarir case?
The London High Court determined that hacking a private citizen's phone through commercial spyware isn't a legitimate state function deserving immunity protection under international law. State immunity doctrines were designed to protect official government conduct, not surveillance of private individuals living in exile using commercial tools. By ruling that state immunity didn't apply, the court allowed the substantive case to proceed and enabled damages to be awarded against the Saudi government.
What does the Al-Masarir ruling mean for other Pegasus victims?
The ruling establishes legal precedent showing that courts in some jurisdictions can hold governments accountable for Pegasus surveillance despite traditional immunity doctrines. This creates a pathway for other victims to pursue damages in countries with similar legal frameworks, though enforcement of judgments against sovereign nations remains challenging and uncertain.
Is NSO Group directly liable for Pegasus abuse?
The London court ruling doesn't directly hold NSO Group liable, instead focusing on the government actors who deployed Pegasus against Al-Masarir. However, NSO Group faces increasing legal and regulatory pressure globally, including lawsuits from Apple, restrictions from the U.S. Department of Commerce, and civil rights organizations calling for comprehensive bans on surveillance tools like Pegasus.
What measures can activists and journalists take if they suspect Pegasus targeting?
Individuals who suspect sophisticated spyware targeting should contact organizations like Amnesty International's Security Lab, the Citizen Lab at University of Toronto, or similar digital forensics organizations that can analyze devices for compromise. It's also advisable to assume devices may be compromised and treat them as untrusted, limiting sensitive communications on potentially compromised hardware and maintaining multiple communication channels for critical work.
Will the Al-Masarir damages award actually be paid by Saudi Arabia?
Enforcement of the £3 million judgment against Saudi Arabia remains uncertain. Sovereign nations can refuse to pay, claim immunity from enforcement, or appeal indefinitely. Without a mechanism for international enforcement or Saudi Arabia's voluntary compliance, the judgment may remain symbolic rather than resulting in actual financial compensation to Al-Masarir.
What regulatory measures have been implemented to restrict Pegasus and similar surveillance tools?
The U.S. Department of Commerce placed NSO Group on the Entity List restricting business with American entities and blocking exports. The European Union is considering regulatory frameworks for surveillance technology exports. Multiple countries have banned government procurement of NSO products. Tech companies like Apple have pursued lawsuits. However, these measures face limitations due to NSO Group's argument that restrictions simply drive clients toward less ethical alternative vendors.

Takeaways
The Al-Masarir case represents a watershed moment in the battle against government surveillance abuse. For the first time, a Western court awarded substantial damages against a government for weaponizing commercial spyware against a private citizen. This establishes legal precedent and demonstrates that state immunity isn't absolute when governments abuse surveillance tools extraterritorially.
But the case also highlights the limitations of legal accountability. Enforcement is uncertain. Only wealthy victims with access to sophisticated legal systems can pursue justice. The broader problem of Pegasus abuse continues despite regulatory efforts and reputational damage to NSO Group.
What matters most is that this case contributes to building a legal, regulatory, and ethical framework that increasingly constrains governments' ability to weaponize surveillance tools without consequences. Combined with technical improvements to device security, corporate responsibility measures, and diplomatic pressure, legal accountability is part of a broader shift toward a world where surveillance abuse carries real costs.
For activists, journalists, and dissidents operating in authoritarian or semi-authoritarian contexts, this ruling provides some measure of hope. It shows that courts in democratic jurisdictions will increasingly hold governments accountable for surveillance abuse. It establishes that victims have legal pathways to pursue damages. And it demonstrates that even state actors are not immune from the laws of the countries where their victims seek justice.
The £3 million judgment may never be paid. But the message the court sent is invaluable: governments cannot indefinitely weaponize surveillance tools against their critics abroad while hiding behind state immunity doctrines. Accountability is possible. Justice can be pursued. And surveillance abuse has costs.
That's the real significance of the Al-Masarir case. It's not just about one satirist and one court. It's about the principle that democratic societies will increasingly establish: surveillance tools designed for authoritarian control will face legal, regulatory, and reputational consequences when abused. The boundaries of impunity are slowly shrinking.
Use Case: Human rights organizations using AI-powered documentation tools to create comprehensive incident reports, threat analysis documents, and legal briefs for surveillance victims pursuing accountability cases.
Try Runable For Free
Key Takeaways
- London High Court awarded £3 million to Al-Masarir after finding compelling evidence Saudi Arabia hacked his phone with Pegasus spyware
- Court rejected Saudi Arabia's state immunity claim, establishing legal precedent that surveillance of private citizens abroad doesn't qualify for immunity protection
- Pegasus exploits zero-day vulnerabilities to invisibly compromise iPhones and Android devices, providing operators complete access to messages, location data, and device cameras
- NSO Group continues facing increasing regulatory pressure including U.S. Entity List placement, EU sanctions discussions, and Apple litigation despite claims of client vetting
- Hybrid attack model combining Pegasus digital surveillance with physical violence has been documented across multiple countries targeting activists, journalists, and opposition figures
Related Articles
- Tech Workers Demand CEO Action on ICE: Corporate Accountability in Crisis [2025]
- How DHS Keeps Failing to Unmask Anonymous ICE Critics Online [2025]
- Microsoft BitLocker Encryption Keys FBI Access [2025]
- Under Armour Cyberattack 2025: What 7M Users Need to Know [Guide]
- Proton VPN Linux Overhaul 2025: Complete GUI & CLI Guide
- TikTok's New Data Collection: What Changed and Why It Matters [2025]
![Pegasus Spyware, NSO Group, and State Surveillance: The Landmark £3M Saudi Court Victory [2025]](https://tryrunable.com/blog/pegasus-spyware-nso-group-and-state-surveillance-the-landmar/image-1-1769449044195.jpg)



