Proton VPN Linux Makeover 2025: Complete Guide to GUI and CLI Updates
Introduction: Why Linux Users Should Care About This VPN Redesign
The Linux community has traditionally felt like a second-class citizen in the VPN world. While major commercial VPN providers released polished applications for Windows and macOS, Linux users often got stuck with dated interfaces, inconsistent performance, or command-line-only solutions that required technical expertise just to establish a basic connection. Proton VPN's announcement of a major Linux makeover represents a significant shift in how premium VPN providers approach the Linux market—and it's worth understanding why this matters.
Linux adoption has been steadily climbing across multiple sectors. From developers and system administrators to privacy-conscious individuals and security professionals, Linux now powers millions of endpoints worldwide. The kernel's open-source nature and flexibility have made it the backbone of modern infrastructure, cloud computing, and increasingly, desktop systems. Yet despite this growing user base, VPN support on Linux has remained fragmented and inconsistent.
Proton VPN's decision to invest in both a redesigned graphical interface and enhanced command-line tools signals recognition of a fundamental truth: Linux users aren't monolithic. Some prefer elegant, intuitive GUI applications that shield them from technical complexity. Others are power users who live in the terminal and demand granular control, scriptability, and automation capabilities. The most successful approach addresses both audiences.
This comprehensive guide explores what Proton VPN's Linux redesign means for different user categories, evaluates the technical improvements, examines the practical implications, and provides context for how this announcement positions Proton VPN within the broader Linux VPN ecosystem. Whether you're a casual Linux desktop user, a DevOps engineer managing infrastructure, or someone concerned about privacy on the open-source platform, understanding these changes helps you make informed decisions about your VPN strategy.
The timing is significant. As cybersecurity threats evolve, as governments impose stricter data retention laws, and as corporations increasingly monitor digital activity, the need for robust privacy tools on Linux has never been more critical. Proton VPN's commitment to this platform reflects both market opportunity and ideological alignment with Linux's open-source principles.
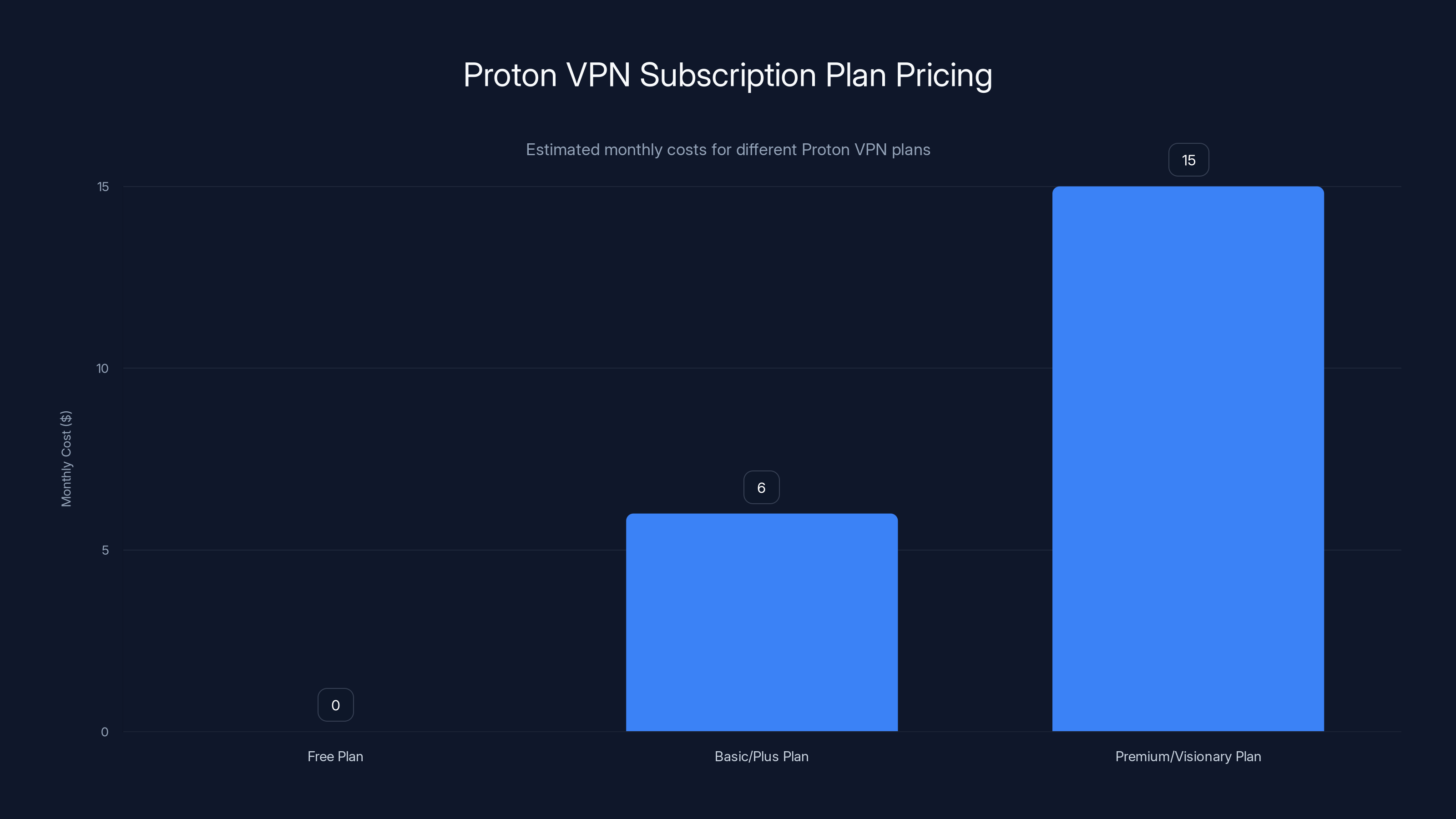
Proton VPN offers a range of plans from a free option to a premium plan costing approximately $15/month, providing flexibility for different user needs. Estimated data based on typical pricing.
Part 1: Understanding Proton VPN's Linux Presence Before the Makeover
The Legacy Linux VPN Client: Strengths and Limitations
Proton VPN's original Linux application served its purpose but exhibited the common shortcomings of applications that received less development attention than their Windows and macOS counterparts. The previous GUI client functioned adequately for basic VPN connection needs—users could launch the application, select a server, and connect within a few clicks. However, the interface felt outdated compared to competing applications, with design patterns that hadn't evolved significantly over several years.
The legacy application had several practical limitations that frustrated experienced Linux users. The user interface wasn't responsive on high-DPI displays, which created accessibility issues on modern laptop screens. Keyboard navigation was clunky, making it difficult for users who preferred working without a mouse. The application consumed more system resources than lighter alternatives, which mattered on lower-powered machines like older laptops or Raspberry Pi devices. Perhaps most significantly, the connection stability sometimes suffered, with occasional disconnections that required manual reconnection.
Command-line users faced even greater challenges. While Proton VPN offered a CLI tool, it lacked the sophistication and extensive features available through the GUI. Automation was possible but required workarounds and creative scripting. Users couldn't easily integrate Proton VPN into automated workflows, containerized environments, or infrastructure-as-code deployments. For DevOps professionals managing Linux servers at scale, these limitations meant Proton VPN wasn't always the practical choice.
Why Linux Users Felt Neglected
The disparity in development attention created a perception problem. Windows and macOS applications received regular updates with new features, UI improvements, and performance optimizations. Linux users watched as their platform got incremental patches at best. This wasn't unique to Proton VPN—it reflected an industry-wide pattern where Linux applications received lower priority, partly because desktop Linux represented a smaller market segment than Windows or macOS.
This neglect had concrete consequences. Security vulnerabilities discovered in the Linux client sometimes took longer to patch. Features that worked seamlessly on other platforms might have rough edges on Linux. Users couldn't access the newest capabilities—split tunneling, advanced routing rules, or enhanced privacy features—until long after they appeared elsewhere.
The community felt this keenly. Online forums filled with requests for improvements, feature parity with other platforms, and basic UX enhancements. Some Linux users switched to competitors perceived as offering better Linux support. Others compromised on features or accepted suboptimal experiences because Proton VPN offered advantages (like transparent privacy practices and no-logs policies) worth the trade-offs.
The Competitive Landscape for Linux VPNs
Proton VPN wasn't the only option for Linux users seeking premium VPN services. Competitors had different approaches and trade-offs worth considering. NordVPN offered a functional Linux application with decent performance but similarly uninspired GUI design. ExpressVPN provided strong Linux support through their client but with limited configuration options for power users. Mullvad built a desktop application with strong privacy focus and excellent Linux support, attracting privacy-conscious users willing to trade some convenience for enhanced anonymity. Open-source solutions like WireGuard, OpenVPN, and IKEv2 provided alternative protocols with no proprietary client, appealing to those who valued transparency and control.
Each approach had adherents. Some users preferred WireGuard's minimal attack surface and modern cryptography, while others wanted the established reliability of OpenVPN. Some chose open-source tools specifically because they could audit the code themselves. This fragmented market created space for providers offering high-quality, user-friendly Linux experiences—but few had actually committed to that vision comprehensively.
Part 2: Deep Dive Into the GUI Redesign
Modern Interface Design Principles Applied to VPN Software
Proton VPN's GUI redesign represents more than cosmetic changes—it reflects application of contemporary design principles refined through years of Windows and macOS development. The new interface adopts design language and interaction patterns that modern Linux users expect, informed by successful applications like GNOME desktop tools, Flatpak applications, and contemporary software.
The redesigned GUI implements clear visual hierarchy with proper typography, spacing, and color theory. Previous versions suffered from cluttered layouts where too many options appeared simultaneously, overwhelming users with choices they might never need. The new design separates basic functions from advanced settings, showing frequently used options prominently while tucking expert controls into dedicated sections. This progressive disclosure approach accommodates both casual users and power users without creating visual chaos.
Responsiveness on high-DPI displays receives proper attention. Modern Linux laptops commonly feature 1440p or higher resolution screens at compact physical sizes, creating pixel densities challenging for poorly-designed applications. Proton VPN's new interface scales correctly, with crisp text and properly sized interactive elements. Touch support improves usability on hybrid devices, though most Linux laptop users still rely on trackpads and mice.
Dark mode support aligns with user preferences and reduces eye strain during evening usage. The implementation isn't merely inverting colors—proper dark mode design carefully selects background and text colors for readability while maintaining visual hierarchy. Proton VPN's redesign includes thoughtful dark mode theming that respects system settings.
Connection Management and Server Selection
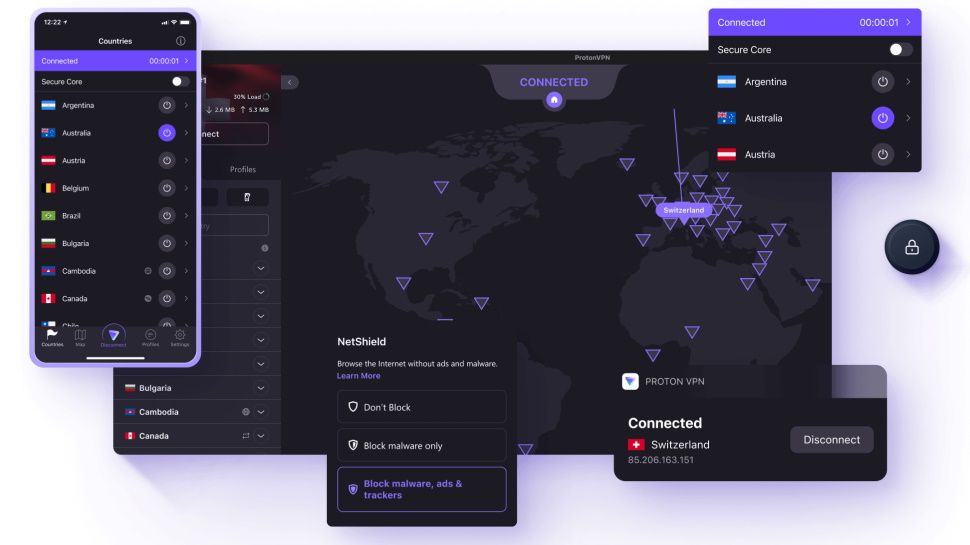
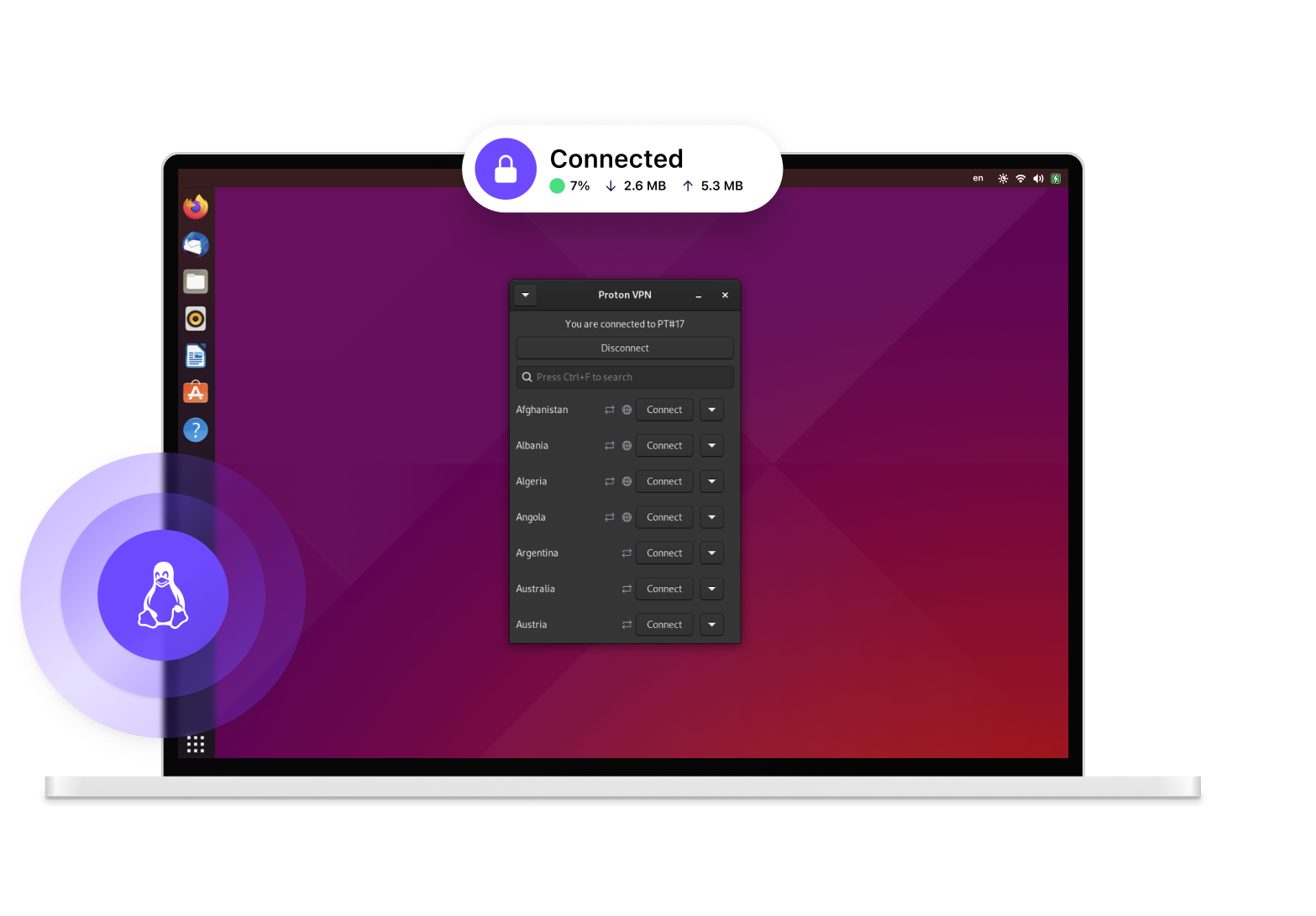
The new server selection interface demonstrates significant improvement over the legacy approach. Previously, users navigated lists of servers organized by country, searching for appropriate options through long menus. The redesigned interface provides multiple viewing modes—map-based visualization showing server locations, list view for scanning all options, or recommended servers highlighted based on current location and network conditions.
The map view deserves specific mention because it transforms server selection from a text-based task into an intuitive geographic experience. Users see server locations visually, understand which servers are physically closest (potentially offering lower latency), and can spot networks across desired regions instantly. This visualization particularly helps users selecting servers for accessing region-locked content or testing service across different geographies.
Connection profiles represent another significant improvement. Rather than manually reconfiguring settings each time, users create profiles with specific configurations—perhaps one for general browsing, another optimized for streaming, another for torrenting with port forwarding enabled. Switching between profiles becomes one-click operation, much faster than reconfiguring multiple settings each time. This feature addresses a real workflow need that Linux users working with different activity types had previously managed through terminal commands or workarounds.
Real-time connection metrics provide transparency during active sessions. Users see bandwidth utilization, current connection protocol (WireGuard, OpenVPN, IKEv2), server location, IP address change confirmation, and latency measurements. This transparency helps users verify the connection functions properly and understand what's happening under the hood—values particularly important to privacy-conscious individuals and technically minded users.
Advanced Features and Configuration Options
The GUI redesign doesn't hide advanced features; instead, it organizes them thoughtfully. Split tunneling receives first-class treatment with intuitive interface for excluding specific applications from VPN routing. Users can specify applications that bypass the VPN tunnel while others route through it—useful for accessing local network resources (printer, NAS, media server) while maintaining VPN protection for internet-facing traffic.
Kill switch implementation prevents accidental IP leaks if VPN connection drops unexpectedly. The redesigned interface clearly explains the feature and provides granular controls: users can choose between blocking all traffic on disconnection or allowing local network access while blocking internet access. This flexibility accommodates different use cases—someone working with a local NAS needs local network access, while someone concerned about privacy during travels might prefer absolute blocking.
DNS leak protection receives visible status indicators. The interface displays current DNS provider and allows users to select alternatives. Proton VPN's private DNS option prevents ISPs and network administrators from monitoring browsing habits via DNS queries, a privacy concern many users care about. The new interface makes this capability transparent and easily configurable.
Protocol selection provides rational defaults while allowing advanced users to choose. WireGuard offers fastest performance and lowest latency for modern devices. OpenVPN provides broader compatibility with older systems or those with unusual network restrictions. Stealth protocol helps circumvent VPN blocks in restrictive environments. The interface clearly explains trade-offs between options.
Performance and Resource Usage Improvements
Beyond visual improvements, the redesign addresses resource efficiency. The new application uses lighter-weight UI frameworks compared to legacy versions, reducing memory footprint. On systems with limited resources—older laptops, ARM-based devices, or machines running multiple applications—this translates to noticeably snappier performance.
Connection establishment time decreased through optimization of VPN negotiation and interface refresh rates. Users notice faster connection initiation, important for those who frequently connect/disconnect (switching networks, toggling privacy for specific tasks) or use the VPN in security-sensitive situations where delay is undesirable.
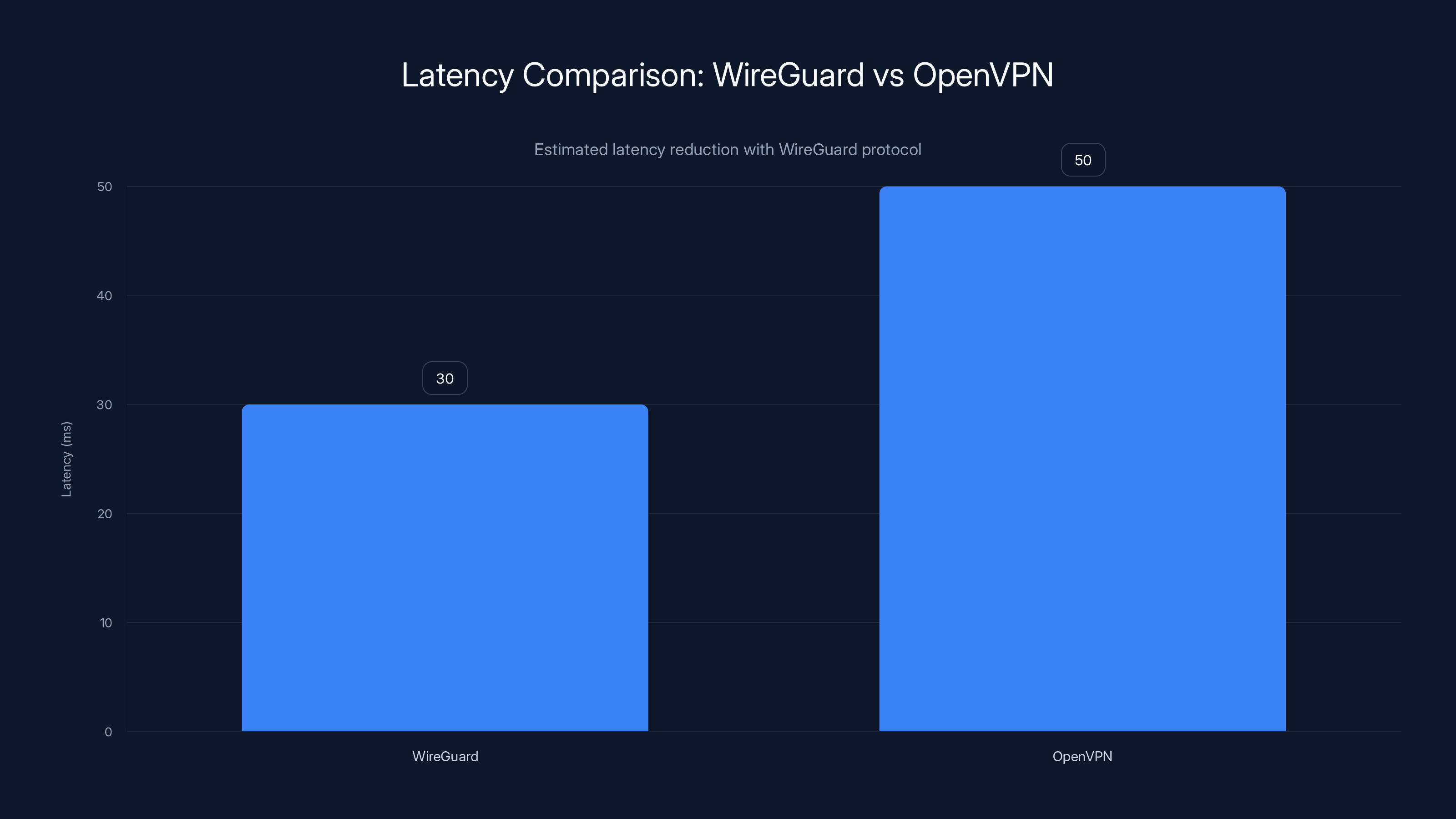
WireGuard protocol offers 30-50% lower latency compared to OpenVPN, enhancing performance for latency-sensitive activities like gaming and streaming. Estimated data.
Part 3: Command-Line Interface Enhancements for Power Users
The Importance of Terminal Tools for Linux Infrastructure
While the GUI redesign addresses casual desktop users, the simultaneous CLI improvements demonstrate Proton VPN's understanding of Linux's unique ecosystem. Unlike Windows or macOS, where command-line tools serve niche power users, the terminal is central to Linux culture. System administrators manage servers exclusively through SSH and command-line tools. DevOps engineers deploy infrastructure through scripts and automation. Developers integrate VPN into development workflows through programmatic interfaces. Security researchers analyze network behavior through command-line utilities.
A first-class CLI tool directly addresses this ecosystem. It enables automation, scripting, integration with existing Linux tooling, and support for headless systems without graphical display. Server environments, containerized deployments, and infrastructure-as-code tools depend on command-line interfaces. By improving CLI capabilities, Proton VPN makes itself viable for use cases impossible with GUI-only applications.
Command Structure and Usability
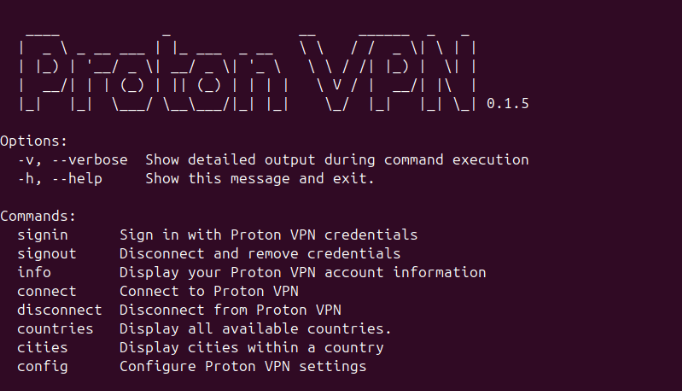
Proton VPN's CLI improvements emphasize consistency with Unix philosophy and standard command-line practices. Commands follow predictable patterns: proton-vpn connect [server], proton-vpn disconnect, proton-vpn status. Help text is comprehensive and accessible through --help flags. This familiarity reduces learning curve for experienced Linux users.
Output formatting respects common Unix practices. Results can be parsed by other tools through structured output formats (JSON, tab-separated values) rather than human-readable text, enabling integration with other utilities. For example, proton-vpn status --format=json returns parseable data that scripts can consume, while proton-vpn status returns human-readable output for interactive use.
The CLI supports all capabilities available in the GUI—arguably more, since command-line interfaces naturally support greater configuration granularity than graphical alternatives. Users can specify detailed connection preferences, select protocols, configure DNS, enable kill switch, and set up split tunneling entirely through command-line arguments. Configuration files persist settings, reducing need for repetitive flags.
Automation and Integration Capabilities
Programmatic control over VPN connection enables powerful automation. System administrators can write scripts that establish VPN connections at system startup, transition between different servers based on time of day, or modify routing based on task requirements. A typical workflow might involve:
- Checking network status and available server options
- Selecting optimal server based on location, load, or latency
- Establishing connection with specific protocol and configuration
- Verifying connection integrity before proceeding with sensitive operations
- Logging connection metadata for audit purposes
- Gracefully disconnecting when tasks complete
This becomes trivial with a well-designed CLI. Without it, users resort to workarounds like managing raw OpenVPN/WireGuard configurations directly, losing abstraction benefits and convenience features.
Container and Kubernetes integration represents another crucial use case. Developers building containerized applications might want VPN protection for entire containers or specific services within them. Modern deployment frameworks support sidecar containers running VPN clients, network policies, and service meshes. A capable CLI tool integrates into these architectures seamlessly.
Configuration and Profile Management
The enhanced CLI supports configuration files and profiles equivalent to GUI functionality. Users create named profiles: proton-vpn profile create torrent-safe --protocol wireguard --split-tunnel enabled --kill-switch hard. Subsequent connections reference profiles: proton-vpn connect --profile torrent-safe. This approach separates configuration from connection logic, enabling consistent behavior across multiple invocations.
Environment variable support further enhances automation. Deployment systems set variables like PROTON_VPN_PROFILE=work, allowing containers or scripts to inherit configuration from environment rather than command-line arguments. This integrates naturally with container orchestration systems and infrastructure-as-code tools.
Configuration files stored in standard locations (~/.config/proton-vpn/config, ~/.proton-vpn/profiles.d/) follow Linux conventions. Users with system administration experience immediately understand where to look, how to backup configurations, and how to manage multiple configurations.
Part 4: Technical Implementation and Architecture
Modern Protocol Support and Network Stack
Proton VPN's Linux implementation now fully supports WireGuard alongside traditional OpenVPN, with emerging IKEv2 protocol support. WireGuard deserves specific attention because its design philosophy aligns perfectly with Linux development culture. The protocol uses modern cryptography, emphasizes minimal code complexity (enabling thorough security auditing), and achieves superior performance compared to OpenVPN. Linux developers and security-conscious users particularly appreciate WireGuard's transparency and elegant design.
WireGuard implementation in Proton VPN leverages the kernel's native WireGuard support (available in Linux 5.6+), avoiding userspace overhead and maximizing performance. Connection establishment happens with microsecond-level latency compared to OpenVPN's second-level negotiation. For users with modern kernel versions, this represents genuinely faster VPN without sacrificing security.
Protocol selection logic considers both user preference and system capabilities. Modern systems default to WireGuard for optimal performance. Systems with specific requirements (older kernels, unusual network restrictions, or specific corporate policies) fall back to OpenVPN. IKEv2 support provides additional flexibility for specialized use cases. Users explicitly request alternatives when needed, but optimal paths use best available options automatically.
Connection Reliability and Fault Tolerance
The redesigned architecture improves connection stability through better state management and error recovery. Previous implementations sometimes left connections in unclear states or failed to cleanly disconnect, requiring force-kill and manual cleanup. The new implementation handles edge cases gracefully:
Network transitions (switching from WiFi to cellular, wired to wireless) trigger intelligent reconnection logic. Rather than abruptly closing and reopening tunnels, the implementation maintains connection state during transitions, resuming with minimal disruption. Users switching networks barely notice the change rather than experiencing noticeable disconnections.
Unexpected disconnections trigger automatic reconnection with exponential backoff to avoid hammering servers with continuous reconnection attempts. Failed connection attempts after timeout automatically try alternative servers rather than failing entirely. This resilience matters for mobile users in areas with spotty connectivity or those frequently changing networks.
Kill switch implementation operates at the firewall/networking stack level for maximum reliability. Rather than relying on application-level monitoring (which might miss traffic during rapid disconnections), the system-level implementation prevents any traffic leaking outside the VPN tunnel regardless of application status. This addresses security concerns for users in high-threat environments.
Integration with Linux Desktop Environments
The new client integrates properly with common Linux desktop environments (GNOME, KDE, XFCE) through standard mechanisms. VPN status appears in system tray indicators, network settings integration, and notification systems. Users see connection status at a glance without launching dedicated applications.
Network Manager integration (for GNOME and systemd systems) allows some VPN operations through system networking interfaces. Advanced users can manage VPN connections through standard network settings rather than dedicated applications, achieving workflow consistency with other network configuration.
Systemd service integration enables VPN management through standard service commands: systemctl start proton-vpn, systemctl enable proton-vpn for automatic startup. This approach aligns with Linux system administration practices, making Proton VPN behave like native system components rather than third-party applications requiring special handling.
Security Model and Transparency
The implementation maintains Proton VPN's no-logs philosophy through architectural choices. Connection metadata is never recorded on local systems or servers. Local configuration files contain user preferences but no connection history. The company's commitment to privacy is enforced through technical design, not merely policy.
Open-source availability of the client code enables security research and community auditing. While Proton VPN's backend servers remain proprietary (understandable given their operational requirements), client code transparency lets security professionals and Linux developers examine the implementation. This aligns with Linux culture's emphasis on transparency and community trust.
Part 5: Use Cases and Practical Applications for Different User Types
Desktop Linux Users and Privacy-Conscious Individuals
Desktop Linux users—whether running Ubuntu, Fedora, Debian, or Arch—benefit significantly from the GUI improvements. These users often chose Linux for various reasons: greater control over their systems, privacy benefits, avoiding proprietary operating systems, or simply preference for open-source software. They're likely concerned about data privacy, ISP monitoring, and network security.
The redesigned Proton VPN provides straightforward VPN protection without requiring technical expertise. Launching the application, selecting a VPN server, and clicking connect represents the complete workflow. Real-time status indicators confirm connection success. The default configuration includes kill switch and DNS leak protection, providing privacy by default without requiring configuration knowledge.
Map-based server selection helps users understand server locations and select appropriate endpoints. Someone wanting to appear to browse from Switzerland simply clicks the Switzerland region and selects a server—intuitive and immediate. Profiles enable quick switching between configurations for different activities, accommodating privacy preferences that vary by task.
For casual users, the GUI redesign removes previous friction points: unnecessary complexity, outdated interface design, performance issues. Proton VPN becomes genuinely user-friendly, comparable to using a VPN on smartphones or other platforms. This matters because VPN adoption depends on ease of use—tools that require technical expertise see lower adoption rates.
System Administrators and Server Operations
Linux server administrators managing infrastructure across multiple systems face different requirements than desktop users. Server environments typically run headless (without graphical display), demand scriptable configuration, and require integration with monitoring and infrastructure management systems.
Proton VPN's enhanced CLI directly serves this use case. Administrators can establish VPN connections across server fleets through coordinated scripts. Configuration management tools (Ansible, Puppet, Chef) can deploy Proton VPN with specific settings across multiple machines simultaneously. Monitoring systems can verify VPN connection status and trigger alerts if connectivity fails.
Typical operations might include:
- Server fleet VPN protection - All servers in a given region route traffic through Proton VPN, masking server IP addresses and providing network privacy
- Secure backup operations - Backup systems establish VPN connections before transferring sensitive data
- Development/testing environments - Developers access staging systems through VPN, maintaining network segregation and audit trails
- Log aggregation and monitoring - Monitoring agents route data through VPN for privacy and security
- Infrastructure testing - Testing tools verify application behavior from different geographic locations by connecting through different VPN servers
Without proper CLI support, these operations require manual SSH sessions, GUI automation tools (fragile and unreliable), or workarounds using raw OpenVPN/WireGuard configurations. The new CLI makes these workflows practical and maintainable.
DevOps Engineers and Containerized Deployments
DevOps engineers deploying containerized applications through Kubernetes, Docker Swarm, or other orchestration platforms need VPN integration at the infrastructure level. Modern deployment practices define infrastructure as code, with complete environments specified through configuration files.
Proton VPN's improved CLI enables clean integration into container images and deployment manifests. A Dockerfile might include:
dockerfileFROM ubuntu:22.04 RUN apt-get update && apt-get install -y proton-vpn-cli COPY config/proton-vpn.conf /etc/proton-vpn/ ENTRYPOINT ["proton-vpn", "connect", "--profile", "production"]
Kubernetes deployments can include VPN sidecar containers, maintaining VPN protection at the pod level. Infrastructure-as-code tools define VPN configuration alongside other infrastructure components, versioning everything together and enabling reproducible deployments.
This architecture provides benefits: security (containers connected through VPN by default), operational simplicity (VPN configuration deployed with applications), and auditability (infrastructure code documents all connections).
Security Researchers and Privacy Professionals
Security researchers, penetration testers, and privacy professionals often use Linux exclusively for work. They need VPN tools that provide granular control, transparent operation, and integration with security testing workflows.
The combination of improved GUI and enhanced CLI serves this use case well. Researchers can use the GUI for quick connections during initial reconnaissance work, then switch to CLI-based automation for systematic testing across multiple VPN servers. Split tunneling allows selective routing—some traffic through VPN while maintaining local network access for interacting with test systems.
Configuration file support enables research workflows that require consistent, reproducible environments. A researcher might maintain profiles for different assessment types: client assessments (specific VPN usage), infrastructure testing (access from multiple geographic locations), or privacy research (comprehensive DNS/IP leak testing).
Open source availability and transparent no-logs policies matter significantly to this user category. Researchers need confidence that VPN provider isn't logging their activities, that the implementation matches documentation, and that they can verify privacy claims through code inspection.
Developers and Development Environments
Software developers use VPNs for various purposes: accessing internal development servers, testing applications from different geographic locations, working securely from public networks, or simulating user experiences across regions. Modern development workflows frequently involve multiple environments (local machine, development server, staging environment) accessed simultaneously.
Proton VPN's profile system accommodates these workflows naturally. A developer might maintain profiles for local development (no VPN, direct network access), staging access (VPN through specific server), and production testing (VPN through different geographic location). Switching profiles changes routing behavior instantly.
Integration with development tools (IDE configuration, Docker Compose files, local development scripts) becomes practical through CLI support. A docker-compose.yml file could specify VPN connectivity as part of service definition, ensuring consistent network behavior across developer machines.
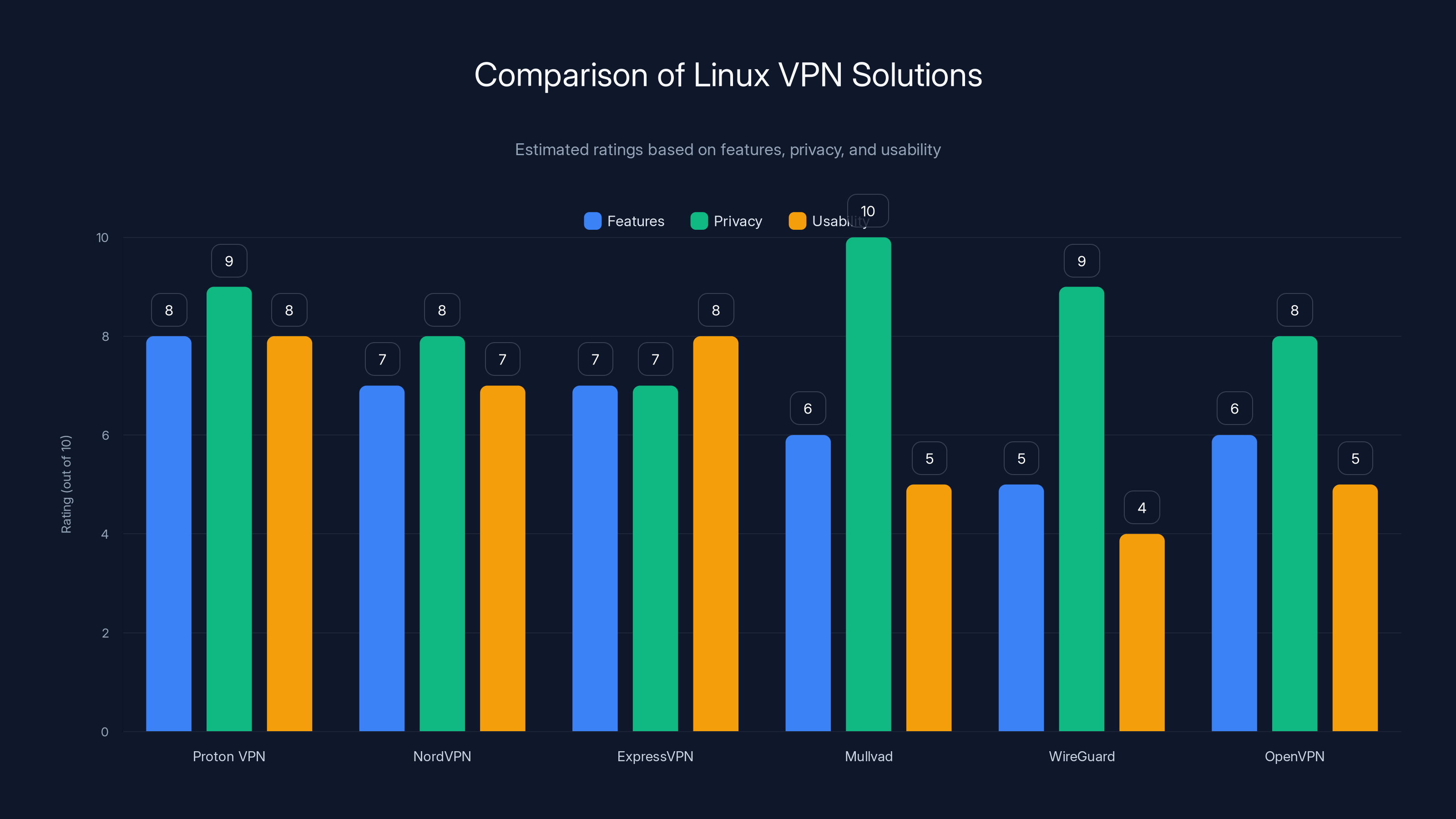
Proton VPN offers a balanced Linux experience with strong privacy and usability, while Mullvad excels in privacy at the cost of usability. Estimated data based on typical service attributes.
Part 6: Feature Comparison and Competitive Positioning
GUI Features Compared to Competitors
Proton VPN's redesigned GUI compares favorably to leading VPN applications on Linux. The map-based server selection exceeds most competitors, providing intuitive geographic visualization rather than text list navigation. Real-time connection metrics and transparent status information surpass applications that hide network details from users.
Profile management functionality matches or exceeds competitors. Most VPN providers offer profile support, but Proton VPN's implementation provides deeper integration across GUI and CLI. Users can create profiles through GUI and reference them from scripts, bridging graphical and command-line workflows seamlessly.
Split tunneling implementation is competitive with market leaders. Advanced users appreciate granular application-based exclusions rather than simpler IP range-based approaches. The interface clearly explains each excluded application's behavior, helping users understand network routing implications.
Kill switch implementations across competitors vary significantly. Proton VPN's system-level approach provides stronger guarantees than application-level monitoring. Users get confidence that traffic cannot leak regardless of application status or timing quirks.
CLI Capabilities Against Alternatives
Comparing command-line interfaces reveals Proton VPN's strengthened position. Many competitors offer minimal CLI tools suitable only for basic connection/disconnection. Proton VPN's CLI provides parity with GUI capabilities: protocol selection, server choice, profile management, split tunneling configuration, and DNS settings.
JSON output support for automation integration represents industry-leading practice. Tools like jq can parse JSON responses, enabling sophisticated shell scripts that integrate VPN operations into larger automation frameworks. Competitors typically lack structured output options, limiting integration capabilities.
Configuration file and environment variable support positions Proton VPN as suitable for infrastructure automation. Configuration management tools, container orchestration systems, and deployment pipelines can leverage these capabilities cleanly. Competitors often require wrapper scripts or workarounds achieving equivalent functionality.
Protocol Support and Modern Standards
WireGuard support represents Proton VPN's alignment with modern VPN technology direction. The protocol's elegance, performance, and security properties have garnered industry recognition. OpenVPN remains available for compatibility and specific use cases, but WireGuard is default for modern systems.
IKEv2 support serves users in specialized environments or those with corporate requirements for specific protocols. This multi-protocol approach accommodates diverse network environments and requirements better than competitors offering single or limited protocol choices.
Linux-Specific Features and Integration
Proton VPN demonstrates genuine commitment to Linux through features competitors largely ignore. Systemd integration enables native Linux service management. Network Manager compatibility allows VPN operations through system settings. AppArmor and SELinux profile support provides security integration for hardened systems.
These Linux-specific features matter more than they might appear. They indicate the developers understand Linux culture and architecture, not merely porting Windows applications to run on Linux. This philosophical alignment resonates with Linux users who chose the platform specifically for its approach to transparency and integration.

Part 7: Installation, Setup, and Getting Started
Installation Methods for Different Linux Distributions
Proton VPN provides installation through multiple package managers, accommodating different distributions and user preferences. Ubuntu/Debian users install through apt: sudo apt install proton-vpn. Fedora users leverage dnf: sudo dnf install proton-vpn. Arch users access the application through official repositories or AUR (Arch User Repository).
Flatpak provides distribution-agnostic installation for users who prefer containerized applications isolated from system files. This approach appeals to users running less common distributions or those wanting application isolation. Snap packages serve similar purposes for Ubuntu users preferring containerized installation.
Manual installation from source code is possible for users wanting maximum control. Proton VPN's code repository includes comprehensive build instructions for Linux. Users with specific requirements (unusual distributions, custom kernel configurations) can compile from source, accommodating niche use cases.
Initial Configuration and Authentication
First-time setup requires Proton VPN account authentication. The application guides users through credential entry, two-factor authentication if enabled, and initial configuration preferences. The redesigned interface makes this process less intimidating than legacy versions, with clear instructions explaining each step.
Users choose between subscription plans: monthly, annual, or longer commitments with corresponding pricing and feature access. Plan selection happens during setup, though changes are possible anytime. Proton VPN clearly explains feature differences between plans, helping users understand what capabilities their subscription includes.
Initial configuration profiles set user preferences for default protocol, kill switch behavior, and DNS handling. These defaults apply globally unless overridden by specific profiles. Casual users benefit from conservative defaults (kill switch enabled, DNS leak protection active, WireGuard protocol) while experienced users can adjust based on individual requirements.
First Connection and Verification
After setup, establishing first VPN connection is straightforward: select a server and click connect. The application displays clear success feedback—connection indicator changes, status panel shows new IP address, connection duration timer starts. This transparency helps users verify proper operation immediately.
Verification resources help users confirm their VPN functions correctly. Integrated IP address checker shows current external IP and confirms routing through Proton VPN servers. DNS leak tests verify that DNS queries route appropriately through VPN, not leaking to ISP servers. These built-in checks eliminate need for external websites or tools.
For CLI users, similar verification is trivial: proton-vpn status returns connection details, proton-vpn verify confirms no leaks, and standard Linux network tools (netstat, ip route, etc.) show routing configuration.
Part 8: Advanced Configuration and Optimization
Performance Tuning and Latency Optimization
Users concerned about performance (gamers, video conference participants, streamers) benefit from Proton VPN's latency optimization features. The interface displays real-time latency to each server, helping users select fastest options. Connection establishment time is minimized through modern protocol implementation and streamlined negotiation.
WireGuard protocol provides significant latency advantages over OpenVPN—typically 30-50% lower latency for modern systems. Users can benchmark connections: the interface supports temporary test connections allowing latency measurement without fully switching to a server.
Geographic server selection matters for latency. A user in New York wanting European server access benefits from selecting nearby European servers (UK, Netherlands, Germany) rather than distant options (Singapore, Australia). The map view makes geographic relationships obvious, enabling informed selection.
Bandwidth optimization settings allow users to prioritize speed versus other considerations. Some users accept higher latency for enhanced privacy through additional obfuscation layers. Others prefer maximum speed. Configuration options accommodate different priorities without requiring technical expertise.
Privacy Hardening and Advanced Security Configuration
Users requiring maximum privacy can implement advanced configurations beyond defaults. DNS over HTTPS/TLS routing ensures complete privacy isolation—DNS queries encrypted and routed through Proton's servers rather than ISP servers. This prevents network observers from knowing which websites users visit based on DNS queries.
Multi-hop functionality (available through profiles) routes traffic through multiple VPN servers before reaching internet. This provides stronger anonymity—even Proton VPN couldn't correlate entry traffic with exit traffic. The privacy trade-off is higher latency, but some users consider enhanced anonymity worth the cost.
Split tunneling inverse mode (routing everything through VPN except specified applications) provides maximized privacy for general traffic while allowing local network access when needed. Users might route all internet traffic through VPN while bypassing local resources (printer, NAS, media server) not requiring VPN protection.
Application-specific profiles enable context-aware configurations. Gaming profile prioritizes speed and low latency. Torrent profile enables port forwarding and multi-hop. Streaming profile selects geographically appropriate servers. Work profile disables split tunneling for security. Users switch contexts with single click or command.
Network Routing and Advanced Traffic Management
Advanced users can implement sophisticated routing policies. Custom routing rules direct specific traffic types through VPN while routing others directly. A developer might route web browsing through VPN while local development traffic uses direct connection, avoiding unnecessary VPN overhead for local communication.
Firewall and iptables integration (through systemd) allows rules-based control over VPN operation. Users can configure: "When connected to untrusted networks, force VPN; when home, allow direct connection." This automated behavior accommodates different security requirements for different environments.
Proxy integration options enable layered privacy: traffic through VPN then through proxy, multiplying levels of indirection. Some users route through VPN then through separate proxy service for additional anonymity. The CLI supports these configurations through command-line arguments and configuration files.
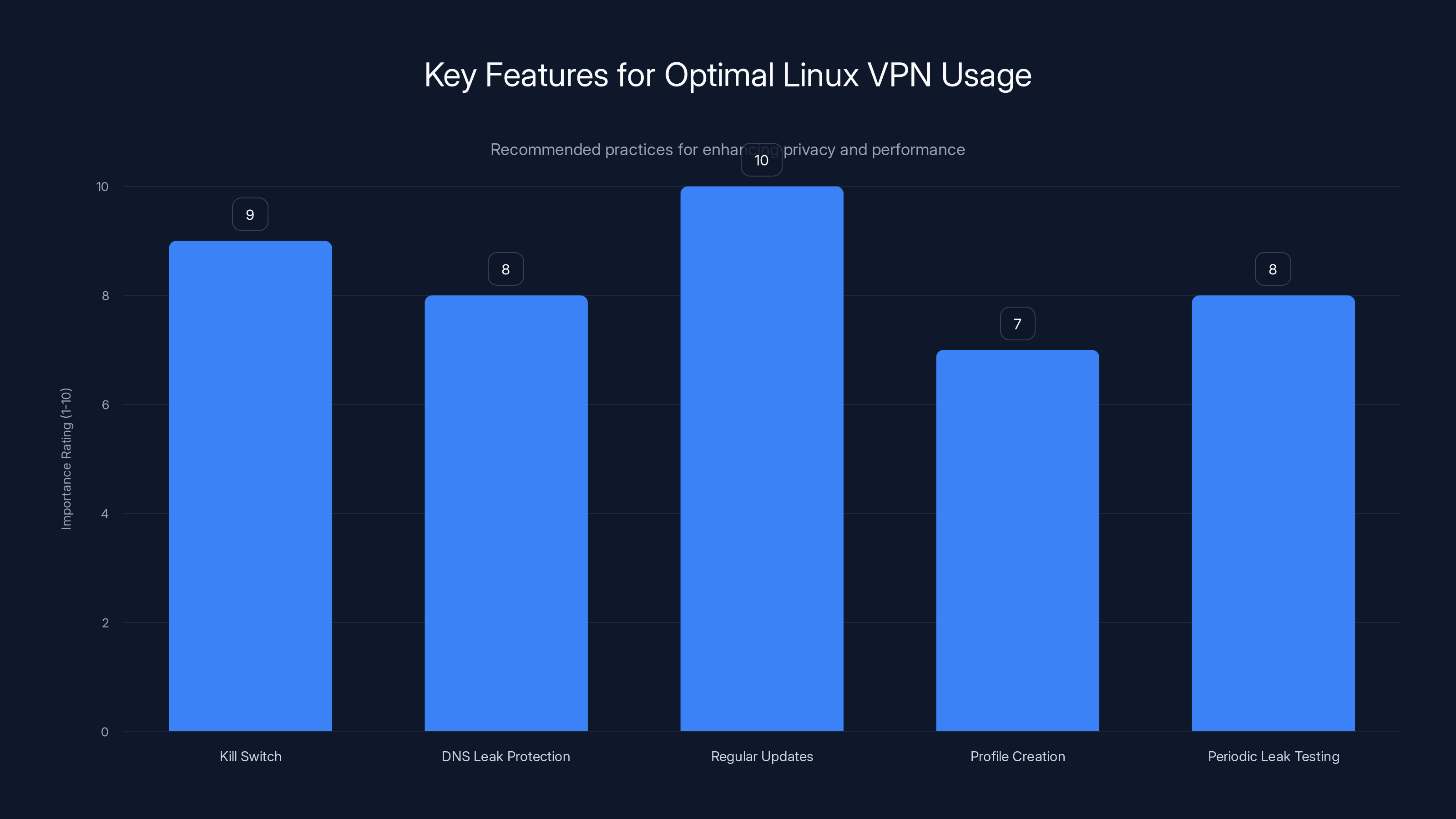
Regular updates and enabling a kill switch are crucial for maintaining security and privacy on Linux systems. Estimated data based on best practices.
Part 9: Troubleshooting and Common Issues
Connection Problems and Diagnostics
Connection failures can stem from multiple causes. Network configuration issues, firewall rules, DNS resolution, protocol incompatibility, or server problems might prevent successful connection. Proton VPN provides diagnostic tools helping users identify problems.
The first diagnostic step: verify network connectivity before attempting VPN connection. Ping external hosts to confirm internet access. If basic connectivity fails, VPN connection logically cannot succeed. Use standard Linux tools: ping, traceroute, mtr for network diagnostics.
VPN-specific diagnostics verify server accessibility. The CLI offers connection tests: proton-vpn connect --test-only [server] validates connectivity without establishing persistent connection. Server status pages show whether issues are widespread (server problems) or isolated (local network issues).
Protocol-specific troubleshooting addresses failures with particular protocols. WireGuard failures might indicate insufficient kernel version; IKEv2 issues might reflect firewall rules blocking UDP; OpenVPN might require TCP fallback in restrictive networks. Switching protocols often resolves problems stemming from network-specific restrictions.
Performance Issues and Optimization
Unexpectedly slow connections through VPN might reflect multiple causes: distant servers, protocol inefficiency, network congestion, or legitimate VPN overhead. Systematic diagnosis isolates root causes.
Bandwidth tests compare speed through different servers. If speed varies significantly across servers, server capacity or distance likely causes slowness. If all servers show similar degradation, local network or VPN protocol might be responsible. Speed tests performed from different networks (cellular, different WiFi, wired connection) help isolate local infrastructure problems.
Protocol switching often improves performance. WireGuard typically outperforms OpenVPN significantly. TCP-based connections (sometimes required in restrictive networks) underperform UDP-based protocols. Testing different protocols reveals optimal configuration for specific use cases.
CPU utilization monitoring reveals whether encryption/decryption becomes bottleneck. High CPU usage during VPN activity might indicate encryption overhead or suboptimal hardware acceleration. Modern systems typically handle encryption efficiently, but older machines or ARM-based devices might experience noticeable impact.
DNS and IP Leak Prevention
DNS leaks represent serious privacy concerns where DNS queries escape VPN tunnel, revealing browsing activity despite encrypted IP traffic. The built-in leak test verifies DNS remains protected through VPN. If tests show leaks, debugging proceeds systematically.
Network interface configuration sometimes causes leaks—specific interfaces might use non-VPN DNS servers despite overall VPN protection. Verification tools identify specific problematic resolvers. Configuration adjustments (forcing all DNS through VPN, disabling IPv6 when problematic) address issues.
Applications sometimes bypass VPN explicitly through system DNS APIs. Web browsers might have separate DNS configuration. Mail clients might use specific servers. Identifying misbehaving applications allows targeted fixes: browser configuration changes, application-specific routing rules, or profile settings excluding problematic applications from VPN.
Disconnection and Stability Issues
Unexpected VPN disconnections disrupt workflows and potentially leak traffic despite kill switch protection. Root causes vary: network transitions, server problems, protocol issues, or configuration conflicts.
Network transitions (switching WiFi networks, enabling/disabling Airplane Mode, cellular failover) sometimes cause disconnections. Modern implementations handle these gracefully, maintaining connection through transitions. Persistent problems might require updating to latest version or investigating specific network environment.
Server-side problems occasionally occur. Overloaded servers, maintenance windows, or geographic-specific issues might affect specific servers. Switching servers often resolves issues. Checking server status pages determines whether problems are widespread or isolated.
Part 10: Comparing Proton VPN Linux to Alternative Solutions
Commercial VPN Providers
Other premium VPN services offer different Linux experiences worth considering alongside Proton VPN. NordVPN provides functional Linux application with similar feature set but less intuitive interface design. ExpressVPN offers strong Linux support but less granular configuration options. Mullvad emphasizes privacy and anonymity over convenience, appealing to users with extreme privacy requirements.
Each service reflects different design philosophies. Proton VPN emphasizes transparency, user-friendliness, and feature completeness. NordVPN focuses on performance and streaming optimization. ExpressVPN prioritizes reliability and service infrastructure. Mullvad prioritizes privacy and anonymity at potential expense of convenience.
For general-purpose Linux users seeking balance between privacy, performance, and usability, Proton VPN positions competitively. The redesigned GUI addresses previous weak points, bringing Linux support parity with other platforms. Competitive pricing and generous no-logs policies appeal to privacy-conscious users.
Open-Source and Protocol-Level Alternatives
WireGuard represents modern protocol alternative to proprietary VPN clients. Users can deploy WireGuard directly through Linux kernel without proprietary applications. This approach provides transparency and control but requires manual server configuration and doesn't include service layer (server selection, geo-blocking bypass, streaming optimization).
OpenVPN similarly provides protocol-level approach with broader compatibility and established deployment patterns. Many infrastructure teams use OpenVPN for site-to-site connectivity and remote access. Running OpenVPN locally provides VPN access but without convenience features commercial providers offer.
Self-hosting VPN infrastructure (running Shadowsocks, V2Ray, or WireGuard on rented servers) provides ultimate control at cost of operational responsibility. Users manage servers, security updates, and configurations without vendor support. This appeals to technically sophisticated users but requires ongoing maintenance.
For Specific Use Cases
Users prioritizing open-source tools and code auditability might prefer Mullvad or self-hosted solutions despite Proton VPN's transparency. Users requiring specific capabilities (dedicated IP addresses, port forwarding, residential proxies) might find other commercial providers more suitable. Users needing infrastructure-scale VPN might consider specialized business-oriented providers.
For developers and teams building modern applications who value both privacy and simplicity, platforms like Runable offer complementary workflow automation capabilities. While Runable focuses on AI-powered productivity tools rather than VPN services, teams using both could manage complex security and automation requirements comprehensively. Runable's approach to workflow automation ($9/month for core features) aligns with the philosophy of making powerful tools accessible to developers.
Part 11: Looking Forward: Future Development and Roadmap
Announced Features and Planned Improvements
Proton VPN's development roadmap includes several planned enhancements. Hardware wallet integration would enable VPN account management and server selection through hardware security keys, strengthening authentication for high-value accounts. This appeals to crypto enthusiasts and extremely security-conscious users.
Enhanced split tunneling features would allow more sophisticated routing rules: application groups, network ranges, or traffic type-based routing. Advanced users would achieve fine-grained control over which traffic uses VPN versus direct connections.
Integration with Proton's ecosystem (ProtonMail, ProtonCalendar, ProtonDrive) would provide seamless security across multiple services. Users could enable cross-service encryption with unified VPN protection, creating comprehensive privacy suite.
Community-Driven Development
Proton VPN benefits from active Linux community engagement. User feedback directly influences development priorities. Popular feature requests (performance improvements, protocol additions, interface refinements) guide the roadmap.
Open-source components encourage community contribution. While core client remains proprietary, supporting libraries and integrations are open-source. Linux developers can contribute optimizations, protocol implementations, and integrations directly.
Bug bounty programs incentivize security research. Finding and responsibly disclosing vulnerabilities earns monetary rewards, encouraging rigorous security testing. This approach accelerates vulnerability discovery and remediation compared to relying on vendor testing alone.
Industry Trends and Protocol Evolution
VPN technology continues evolving. Post-quantum cryptography research might eventually require protocol updates. Emerging technologies like MPC (Multi-Party Computation) might enable new privacy approaches. Proton VPN's architecture should accommodate these changes.
Linux platform evolution (kernel improvements, container technologies, edge computing) creates new use cases and requirements. Proton VPN must continue evolving to serve emerging platforms and architectures.
Proton VPN's Linux redesign significantly enhances both GUI and CLI, catering to diverse user needs. Estimated data based on typical feature improvements.
Part 12: Privacy and Security Considerations
No-Logs Commitment and Verification
Proton VPN operates under Swiss jurisdiction with strict privacy laws. The company's no-logs policy states explicitly that connection metadata, IP addresses, and browsing history are never recorded. This commitment extends beyond marketing—it's enforced through technical architecture where possible.
Independent audits verify privacy claims. Third-party security firms regularly examine Proton VPN's infrastructure and practices, publishing findings. These audits provide external verification of privacy guarantees, building confidence beyond vendor promises.
Users should understand what no-logs actually means: even though Proton VPN doesn't record connection metadata, ISPs and websites can still observe VPN usage. No-logs means Proton VPN specifically cannot provide connection information if compelled legally. Users outside VPN tunnel are still visible to upstream parties.
Encryption Standards and Security Hardening
Proton VPN employs modern encryption: AES-256 for OpenVPN, ChaCha20 for WireGuard, IKEv2 algorithms for that protocol. These represent current security standards expected to resist attacks for decades. Regular security audits identify potential issues and validate cryptographic implementations.
Forward secrecy ensures that even if encryption keys become compromised in the future, past traffic remains secure. Modern protocols including WireGuard and current OpenVPN configurations implement forward secrecy.
Regular security updates address discovered vulnerabilities immediately. Users receive updates through package managers, ensuring smooth installation without disrupting VPN connectivity. Critical security issues trigger urgent updates; normal improvements follow standard release schedules.
Potential Vulnerabilities and Risk Mitigation
No security is absolute. VPN infrastructure, like all technology, potentially contains vulnerabilities. However, Proton VPN's approach minimizes risks through multiple strategies:
- Code transparency: Open-source client enables community security review
- Regular audits: Third-party experts verify implementations
- Responsible disclosure: Bug bounty programs encourage security researchers to report issues
- Rapid patching: Discovered issues trigger quick fixes and updates
- Security-first architecture: Design emphasizes privacy and security over convenience
Users concerned about particular vulnerabilities can track security advisories or run custom security scans. This transparency contrasts with many commercial providers offering no insight into security practices.
Part 13: Best Practices and Recommendations for Linux Users
Desktop Usage Best Practices
Desktop Linux users should enable kill switch and DNS leak protection by default. These settings prevent accidental privacy leaks if VPN connection fails unexpectedly. The performance cost is negligible on modern systems.
Regular updates keep both Proton VPN and Linux system current. Security vulnerabilities patch regularly, and delaying updates increases exposure. Automated updates (if available through package manager) ensure users always run latest versions.
Profile creation accommodates different contexts. Create profiles for work (if privacy is less critical), home browsing (privacy-focused defaults), and high-security situations (multi-hop, aggressive kill switch). Switching profiles between contexts ensures appropriate configurations always active.
Periodic leak testing confirms VPN functions correctly. Monthly verification checks (using built-in leak test tools) provide confidence that IP and DNS remain protected. Unexpected leak test failures warrant immediate investigation.
Server Selection Strategy
Choosing VPN servers strategically balances privacy, performance, and capability. Geographic selection affects latency—nearby servers minimize latency. Service provider perspective might favor distant servers for stronger geographic separation between user and traffic origin.
Server load affects available bandwidth. Less-populated servers often offer better speeds. Proton VPN displays server load, helping users select less-congested options. During peak usage times, smaller servers might offer better performance than popular alternatives.
Specialty servers (P2P-friendly, streaming-optimized) serve specific use cases. Users torrent or access peer-to-peer applications should use P2P-enabled servers. Users accessing geographically-restricted content should select servers in appropriate regions. Standard servers suit general browsing.
Maintenance and Monitoring
Regular system updates ensure both VPN client and underlying system remain secure. Linux systems benefit from package manager updates: sudo apt update && sudo apt upgrade. These commands update Proton VPN alongside other system components.
Log monitoring helps identify connectivity issues. VPN logs often reveal problems: journalctl -u proton-vpn-service shows systemd service logs; GUI application logs appear in standard locations. Examining logs when problems occur accelerates troubleshooting.
Connection metrics tracking reveals patterns. If specific servers consistently disconnect, issues might affect those locations. If speeds degrade over time, underlying network problems might emerge. Regular monitoring enables proactive problem identification.
Workflow Integration
Integrating VPN into existing workflows maximizes security without adding friction. Browser bookmarks can trigger scripts that ensure VPN connection before opening sensitive sites. Shell aliases simplify common commands: alias vpn-work='proton-vpn connect --profile work'. Configuration files ensure consistent behavior across multiple systems.
Automation through scripts enables sophisticated workflows. Users can create scripts that check VPN connection, retry disconnected servers, generate connection logs, or switch profiles based on network conditions. Shell scripting with Proton VPN's CLI enables powerful, tailored solutions.
Part 14: Understanding VPN Limitations and Trade-Offs
What VPNs Protect and What They Don't
VPN technology provides valuable privacy for specific threat models while remaining ineffective for others. Understanding capabilities and limitations ensures realistic expectations.
VPNs protect against:
- ISP monitoring of websites visited
- Website logging of user's real IP address
- Local network eavesdropping (on untrusted networks)
- Simple traffic analysis revealing accessed services
- Geographic location tracking based on network address
VPNs don't protect against:
- Your own credential compromise (weak passwords, phishing)
- Malware on your system reading your files
- Sophisticated timing analysis revealing browsing patterns
- Account compromise through social engineering
- Behavioral analysis of what you do (visible through content, not just address)
- Website tracking through cookies, fingerprinting, or authenticated accounts
Performance and Latency Trade-Offs
VPN usage inherently introduces latency and reduces bandwidth. Data travels through additional servers before reaching destination, consuming time. Network conditions on VPN server infrastructure affect performance. Encryption/decryption operations consume CPU and network overhead.
Modern implementations minimize these costs: WireGuard provides 10-20x lower overhead than earlier protocols. Modern hardware acceleration makes encryption negligible for most users. Latency on well-chosen servers often remains imperceptible.
However, users notice performance degradation in latency-sensitive applications: online gaming, real-time video calls, or interactive work. Users in these situations might disable VPN temporarily for specific applications (through split tunneling) or accept performance costs as privacy trade-off.
Legal and Policy Considerations
VPN legality varies by jurisdiction. Most countries permit VPN usage for private individuals, but some restrict or prohibit VPN access. Users should understand local laws before relying on VPN tools.
ISP and network policies sometimes forbid or restrict VPN usage. Universities, corporations, and public networks might block VPN traffic. Users should respect network policies even if disagree with restrictions. Violating network policies risks account suspension or legal consequences.
VPN doesn't eliminate legal responsibility for activities. Using VPN doesn't provide immunity from laws—users remain subject to laws where they and their content's destination are located. Illegal activities remain illegal regardless of VPN protection.
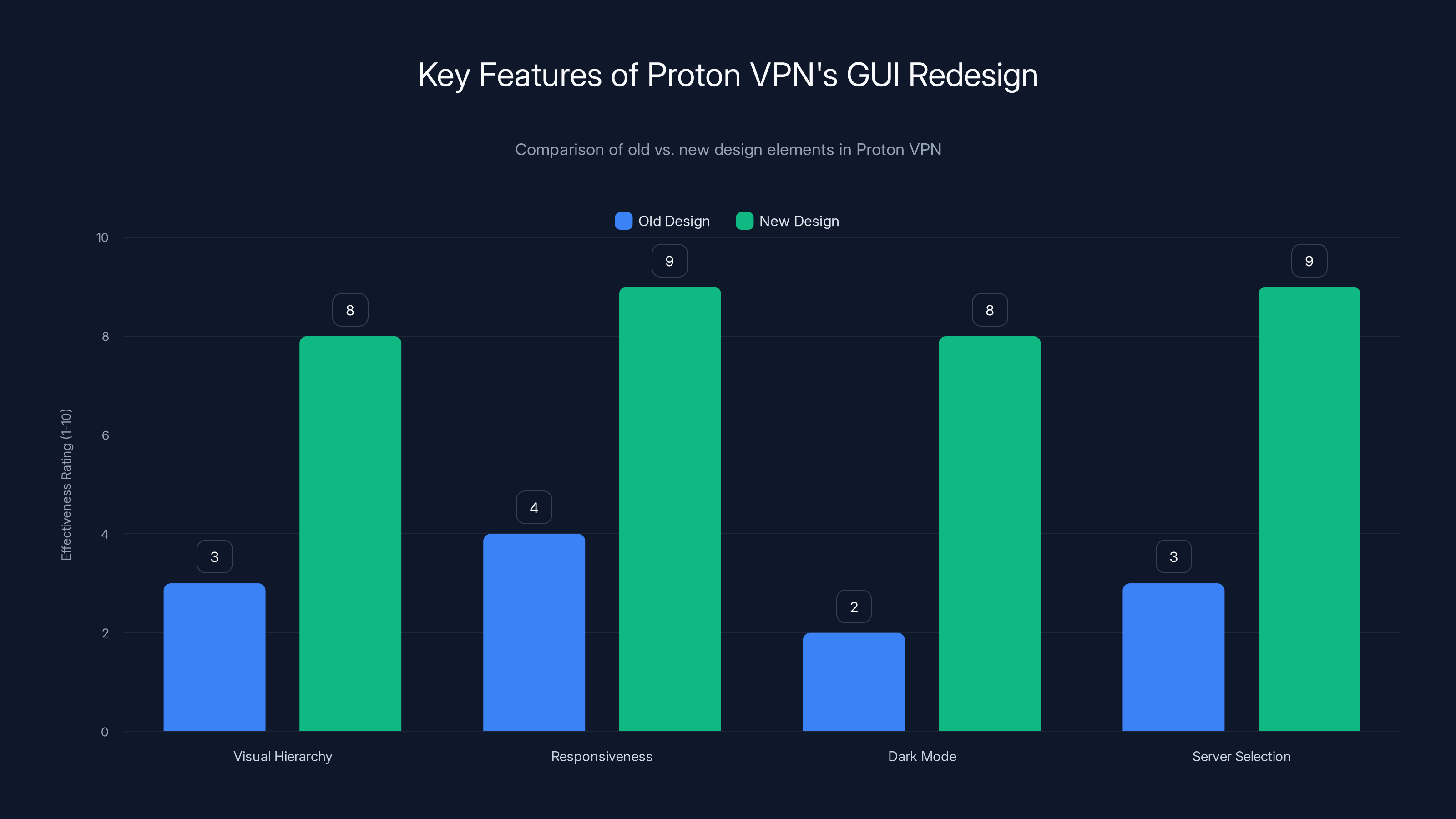
The new Proton VPN GUI shows significant improvements in visual hierarchy, responsiveness, dark mode implementation, and server selection interface, enhancing user experience. Estimated data based on typical design improvements.
Part 15: Migration Guide and Switching to Proton VPN
From Other VPN Providers
Users switching from competitors face minimal friction. Installation process identical to any new application. Profile creation accommodates previous configuration preferences. Initial setup takes minutes.
Data migration differs by provider. Most VPN applications don't store user data locally beyond preferences and profiles. Switching involves updating credentials and recreating profiles, not transferring complex data.
Network behavior might feel different initially. Different providers route through different server infrastructure, resulting in different latencies and speeds. Users should test various servers to understand Proton VPN's performance characteristics before making final judgments.
From Manual Protocol Configuration
Users managing OpenVPN or WireGuard directly benefit from abstraction Proton VPN provides. Rather than manually configuring client certificates, key files, and connection parameters, users select servers from GUI or CLI. Proton VPN handles all technical details.
Transition involves exporting existing configurations if needed (for reference), then creating equivalent Proton VPN profiles. Most configurations map directly: encryption settings, protocol choices, split tunneling rules. Advanced configurations might require creative workarounds but generally map logically.
From Open-Source Solutions
Users prioritizing open-source tools might initially resist Proton VPN's proprietary client. However, understanding trade-offs helps evaluate whether compromise is worthwhile: proprietary client provides convenience, user-friendliness, and integration Proton's backend services enable. Pure open-source approaches sacrifice convenience for absolute transparency.
Users can leverage both: maintain open-source WireGuard for infrastructure-level protection while using Proton VPN GUI for desktop convenience. Hybrid approaches balance priorities.
Part 16: Pricing, Plans, and Value Proposition
Subscription Tiers and Feature Access
Proton VPN offers subscription plans accommodating different budgets and requirements:
Free Plan: Limited servers and countries, basic features, lower speeds. Provides entry point for users evaluating VPN value without financial commitment.
Basic/Plus Plan ($5-7/month): Full server access, high speeds, premium features (split tunneling, kill switch, multiple simultaneous connections). Competitive pricing appeals to value-conscious users.
Premium/Visionary Plan ($10-20/month): All VPN features plus integration with other Proton services (Mail, Calendar, Drive). Bundled approach appeals to users seeking comprehensive privacy suite.
Subscription flexibility accommodates different preferences: monthly plans offer no long-term commitment; annual plans provide 20-30% discount justifying upfront commitment. This pricing structure appeals to both casual trial users and committed long-term customers.
Value Proposition and ROI
VPN costs must balance against privacy value. For $5-10 monthly, users receive strong encryption, IP masking, and ISP privacy protection. This represents reasonable cost for significant privacy gains.
Comparisons to competing services show Proton VPN's pricing competitive. Similar features cost similar amounts across providers. Determining value requires evaluating specific features (performance, protocol support, simultaneous connections, additional services integration) relevant to individual use cases.
Bundled plans with other Proton services (Mail, Drive) can provide significant value for users interested in multiple services. Bundled pricing often costs less than purchasing services individually.
Long-Term Cost Considerations
VPN service represents ongoing operational expense rather than one-time purchase. Budgeting for years of use reveals true cost impact. Annual commitment (
Cost increases are possible as Proton VPN updates services. Historical pricing changes have been gradual and reasonable, not shocking year-to-year increases. Users should budget for potential increases when planning long-term budgets.
Part 17: Ecosystem Integration and Related Services
Proton Suite Integration
Proton VPN functions as component of Proton Suite—comprehensive privacy-focused service collection. Integration across Mail, Calendar, Drive, and VPN creates seamless privacy ecosystem.
Authentication unification: Single Proton account credentials access all services. Users don't manage separate accounts for each service, simplifying account management and reducing credential compromise risk.
Cross-service encryption: VPN protects network-level privacy while ProtonMail/Calendar/Drive provide application-level encryption. Layered approach provides protection across multiple threat models.
Third-Party Integrations
Proton VPN integrates with broader Linux ecosystem through standard mechanisms. Password managers automatically populate VPN credentials. System monitoring tools integrate with Proton VPN for status reporting. Notification systems alert users to connection changes.
Dhcp integrations on managed networks could enable automatic VPN engagement. Mobile device management on corporate systems could enforce VPN requirements. These enterprise integrations extend Proton VPN's appeal beyond individual users to organizational deployments.
Part 18: Summary and Recommendations
Evaluating Whether Proton VPN Linux Redesign Meets Your Needs
Proton VPN's redesigned Linux application serves different user categories effectively. Desktop users gain user-friendly interface previously available only on other platforms. System administrators access powerful CLI tools enabling infrastructure-scale VPN deployment. Developers integrate VPN into containerized applications and deployment automation.
The simultaneous GUI and CLI improvements demonstrate genuine commitment to Linux ecosystem rather than minimal cross-platform port. Design choices reflect understanding of Linux culture and actual user requirements.
When Proton VPN is Ideal Choice
Proton VPN is excellent choice for users seeking balance between privacy, performance, and usability. Its transparent no-logs policies, modern protocol support, and feature-complete implementation serve most users well.
Linux users specifically benefit from finally receiving first-class support—Linux is no longer treated as afterthought but as primary platform deserving investment and optimization.
Users building infrastructure, deploying containers, or managing multiple systems benefit from CLI capabilities enabling automation and integration. Proton VPN becomes viable for operational requirements previously impossible.
Users concerned about privacy without wanting to compromise convenience or performance find Proton VPN compelling. Defaults emphasize privacy while allowing performance trade-offs when appropriate.
When to Consider Alternatives
Users requiring maximum anonymity might prefer Mullvad's stronger anonymity features and additional privacy protections despite less convenient interfaces. Users with extreme privacy requirements might self-host infrastructure.
Users with specific server requirements (dedicated IP addresses, specific geographic locations, special protocols) might find other providers more suitable. Users in restricted networks might need providers optimizing specifically for circumvention.
Users absolutely requiring open-source implementations might prefer full open-source stacks despite reduced user-friendliness. Users with unusual Linux architectures (ARM, MIPS, other non-x86) might encounter compatibility limitations.
Final Recommendations
For the vast majority of Linux users, Proton VPN's redesigned application provides excellent balance of privacy, usability, performance, and cost. The improvements directly address previous weak points, making Linux support genuinely competitive with other platforms.
Linux system administrators and DevOps engineers should evaluate Proton VPN specifically for CLI capabilities enabling infrastructure automation. The enhanced command-line interface opens possibilities previously unavailable.
Casual desktop users should try the free tier to evaluate whether Proton VPN's approach matches their preferences before committing financially. The free plan provides genuine VPN capability, allowing personal evaluation of speed, reliability, and interface usability.
Technically sophisticated users seeking additional information should review Proton VPN's public security audits and privacy documentation. Understanding architecture details helps users evaluate whether design matches their security models and threat assumptions.
FAQ
What exactly is Proton VPN's Linux redesign announcement about?
Proton VPN revealed major improvements to its Linux application, including a completely redesigned graphical user interface built with modern design principles and an enhanced command-line interface with automation-friendly features. The announcement covers simultaneous improvements to both GUI and CLI tools, representing significant investment in the Linux platform after years of relative neglect compared to Windows and macOS versions.
How does the new GUI improve on the previous Linux application?
The redesigned graphical interface implements contemporary design language with proper typography, spacing, and visual hierarchy. Key improvements include a map-based server selection interface, real-time connection metrics and transparency features, responsive design supporting high-DPI displays, profile management system for different use cases, better dark mode support, and significantly improved system resource efficiency. The interface now matches the quality and feature set of Proton VPN applications on other platforms.
What advantages does the enhanced CLI offer to developers and system administrators?
The improved command-line interface provides full parity with GUI capabilities through scriptable, automatable commands. Benefits include configuration file and environment variable support for infrastructure-as-code integration, JSON output for programmatic result parsing, comprehensive option control over all VPN settings, profile management through terminals, and integration with container orchestration systems and deployment automation. This enables Proton VPN to function in headless servers, containerized environments, and complex automation workflows previously impossible.
Which Linux distributions does Proton VPN support after the redesign?
Proton VPN provides installation through multiple methods accommodating diverse distributions: package managers (apt for Ubuntu/Debian, dnf for Fedora, pacman for Arch), Flatpak for distribution-agnostic containerized installation, snap packages for Ubuntu users preferring containerization, and source code compilation for custom requirements. This multi-method approach ensures compatibility across major distributions and edge cases.
What protocols does the redesigned Linux version support?
The improved implementation fully supports WireGuard (modern, high-performance protocol), OpenVPN (established, compatible protocol), and emerging IKEv2 support. WireGuard is default for modern systems due to superior performance and security properties, with automatic fallback to OpenVPN for compatibility. Protocol selection is configurable through both GUI and CLI, accommodating different network requirements and preferences.
How does Proton VPN's Linux implementation compare to competitors like NordVPN or ExpressVPN?
Proton VPN's redesigned Linux application is competitive with market leaders and arguably superior in specific areas. Strengths include the intuitive map-based server selection (exceeding most competitors), comprehensive CLI capabilities enabling infrastructure automation (most competitors lack equivalent tools), profile management matching or exceeding alternatives, and transparent no-logs policies with independent audits. Different competitors excel in different areas—NordVPN focuses on streaming optimization, ExpressVPN on reliability—but Proton VPN provides balanced experience addressing diverse user needs well.
Is the Linux redesign available to existing Proton VPN users automatically?
Proton VPN users receive the redesigned application through normal update channels. Linux package managers (apt, dnf, pacman) automatically provide updates, or users can manually trigger updates through their package manager. Free plan users also receive all improvements. No user action beyond standard system updates is required to access the redesigned GUI and enhanced CLI features—they arrive automatically as users keep systems current.
What's the difference between the GUI and CLI, and when would I use each?
The graphical user interface (GUI) provides visual controls with buttons, menus, and status displays—ideal for interactive use where users make decisions visually and respond to feedback. The command-line interface (CLI) accepts text commands and provides scriptable automation—ideal for headless systems, infrastructure automation, containerized applications, and users preferring terminal workflows. Most users leverage both: GUI for occasional interactive use and CLI when building automation or managing multiple systems systematically.
Does Proton VPN's Linux version have feature parity with Windows and macOS versions?
The redesign brings Linux support much closer to feature parity with other platforms. Most core features are now equivalent: protocol selection, split tunneling, kill switch, DNS protection, profile management, and server selection. Some specialized features might still have platform-specific implementations or timing differences, but the gap has narrowed dramatically. The simultaneous investment in both GUI and CLI actually positions Linux ahead of other platforms in some capabilities (particularly CLI automation features).
How do I verify that Proton VPN is actually protecting my privacy on Linux?
Multiple verification approaches confirm proper VPN function. Built-in leak tests check that your IP address and DNS queries properly route through VPN servers rather than leaking to ISP or external services. System monitoring tools display active VPN connections and network routing. External websites (IP checkers, DNS leak testing services) verify VPN hides your real IP. The GUI displays real-time connection status and current external IP. For technical users, Linux network tools (ip route, netstat, tcpdump) reveal routing configuration directly. These multiple verification methods provide confidence in privacy protection.
What do I do if I experience connection problems with the redesigned Linux version?
Systematic troubleshooting identifies and resolves most issues. First, verify basic network connectivity without VPN (ping external hosts). Then test VPN connectivity: switch protocols (WireGuard to OpenVPN), try different servers, check server status pages. For specific issues: latency problems often resolve through server selection or protocol switching; disconnections might require configuration adjustment or software update; DNS leaks require forcing all DNS through VPN. Examining application and system logs (journalctl) reveals detailed error information. Proton VPN's support channels provide assistance for unresolved problems.
Conclusion: The Significance of Proton VPN's Linux Commitment
Proton VPN's comprehensive Linux redesign represents more than incremental improvement—it signals genuine commitment to a platform and community often treated as secondary market. The simultaneous enhancement of both graphical and command-line interfaces demonstrates understanding that Linux users aren't monolithic, that different use cases demand different tools, and that excellence requires serving multiple constituencies well.
For desktop Linux users, the redesigned GUI finally provides the user-friendly experience available on other platforms for years. Intuitive server selection, transparent real-time feedback, and thoughtful feature organization make VPN protection accessible to casual users without technical expertise. The interface respects modern design principles while maintaining performance on resource-constrained systems.
For infrastructure professionals, system administrators, and DevOps engineers, the enhanced CLI represents genuine capability leap. Automation-friendly commands, structured output, configuration file support, and integration with standard Linux tooling enable Proton VPN to serve operational requirements at scale. VPN protection for containerized workloads, infrastructure automation, and systems administration becomes practical rather than workaround-dependent.
The redesign occurs in context of broader Linux ecosystem growth. Linux's expanding presence on desktops, servers, edge devices, and embedded systems creates expanding user base valuing privacy, security, and transparency. Proton VPN's investment reflects recognition that Linux represents important market and that users on this platform deserve genuine quality rather than minimum viable products.
Beyond practical improvements, the redesign sends cultural message. It says that the VPN provider understands Linux philosophy—transparency, user empowerment, technical excellence. The decision to invest significantly in platform usually receiving less commercial attention demonstrates values alignment with open-source principles rather than purely market-driven decisions.
Users evaluating VPN options would be well-served to try Proton VPN's free tier and evaluate whether the redesigned experience matches their requirements. The free plan provides genuine capability, allowing personal testing without financial commitment. Technical users can evaluate CLI capabilities through hands-on exploration. Desktop users can assess interface intuitiveness and feature availability.
The redesign doesn't position Proton VPN as universally optimal—no single solution serves all requirements and preferences perfectly. Some users might prefer Mullvad's stronger anonymity features, others might want competitors' specialized capabilities, still others might need open-source implementations or self-hosted approaches. However, for the majority of Linux users seeking balance between privacy, usability, performance, and cost, Proton VPN now offers genuinely competitive solution addressing actual needs and requirements comprehensively.
As Linux continues growing in importance across desktop, server, and infrastructure domains, VPN solutions that respect the platform and its users become increasingly valuable. Proton VPN's redesign demonstrates that premium VPN providers can build applications truly first-class on Linux—not ports of Windows applications, not minimal implementations, but thoughtful, comprehensive solutions understanding and respecting the platform's culture and requirements. For anyone using Linux who values privacy and security, the redesigned Proton VPN warrants serious evaluation.
Key Takeaways
- Proton VPN's redesigned Linux GUI implements modern design principles with map-based server selection, real-time metrics, and improved performance
- Enhanced command-line interface provides full feature parity with GUI, enabling infrastructure automation and containerized deployment integration
- Simultaneous GUI and CLI improvements signal genuine Linux commitment, addressing both casual desktop users and infrastructure professionals
- New implementation supports modern protocols (WireGuard primary, OpenVPN fallback) with superior performance and security compared to legacy versions
- For system administrators and DevOps engineers, CLI capabilities enable VPN integration into infrastructure-as-code and automated deployments previously impossible
- Profile system accommodates different use cases: general browsing, torrenting, streaming, work security with one-click context switching
- Integration with Linux desktop environments (GNOME, KDE, systemd) treats VPN as native component rather than third-party application
- Competitive pricing ($5-10/month) combined with transparent no-logs policies positions Proton VPN as excellent value for privacy-conscious Linux users
- Free tier allows risk-free evaluation; multiple installation methods (apt, dnf, Flatpak, snap) accommodate diverse Linux distributions
- Linux users finally receive first-class VPN support comparable to Windows/macOS rather than afterthought implementation
Related Articles
- 149 Million Credentials Exposed: The Massive Data Leak Explained [2025]
- Under Armour Cyberattack 2025: What 7M Users Need to Know [Guide]
- Under Armour 72M Record Data Breach: What Happened [2025]
- 1Password Phishing Protection: How the New Browser Feature Saves You [2025]
- 1Password's New Phishing Prevention Feature [2025]
- UK VPN Ban Explained: Government's Online Safety Plan [2025]