Proton VPN Windows Split Tunneling + Kill Switch + Net Shield: The Complete 2025 Guide
Introduction: A Major Security Breakthrough for Windows Users
For months, Windows users running Proton VPN faced a frustrating technical limitation: they couldn't simultaneously enable three critical security features that worked perfectly on other platforms. Split tunneling, the kill switch, and Net Shield (Proton's ad-blocking and malware protection layer) operated in isolation, forcing users to choose between comprehensive security, selective routing, and privacy protection.
This constraint created real-world security gaps. Users wanting to route sensitive applications through the VPN while maintaining local network access for printers or smart home devices couldn't simultaneously activate emergency kill switch protection. Those prioritizing malware defense had to disable split tunneling functionality. The limitation represented a significant vulnerability in Proton's Windows implementation compared to its macOS and Linux counterparts.
Then came the fix. Proton VPN engineers resolved the underlying architectural conflict, enabling Windows users to activate all three features concurrently for the first time. This development marks a watershed moment for users seeking enterprise-grade security on consumer-friendly VPN platforms.
What does this actually mean for your security posture? For your privacy architecture? For your ability to maintain seamless local network functionality while traveling? This comprehensive guide explores every dimension of this breakthrough, examining the technical foundations, practical implications, setup procedures, and strategic considerations that matter.
Whether you're a remote worker managing sensitive client data, a privacy-conscious traveler, a developer testing geographically-restricted applications, or a security professional managing organizational VPN policies, understanding this convergence of features fundamentally changes how you approach Windows-based security. Let's explore why this matters more than a simple feature activation might suggest.
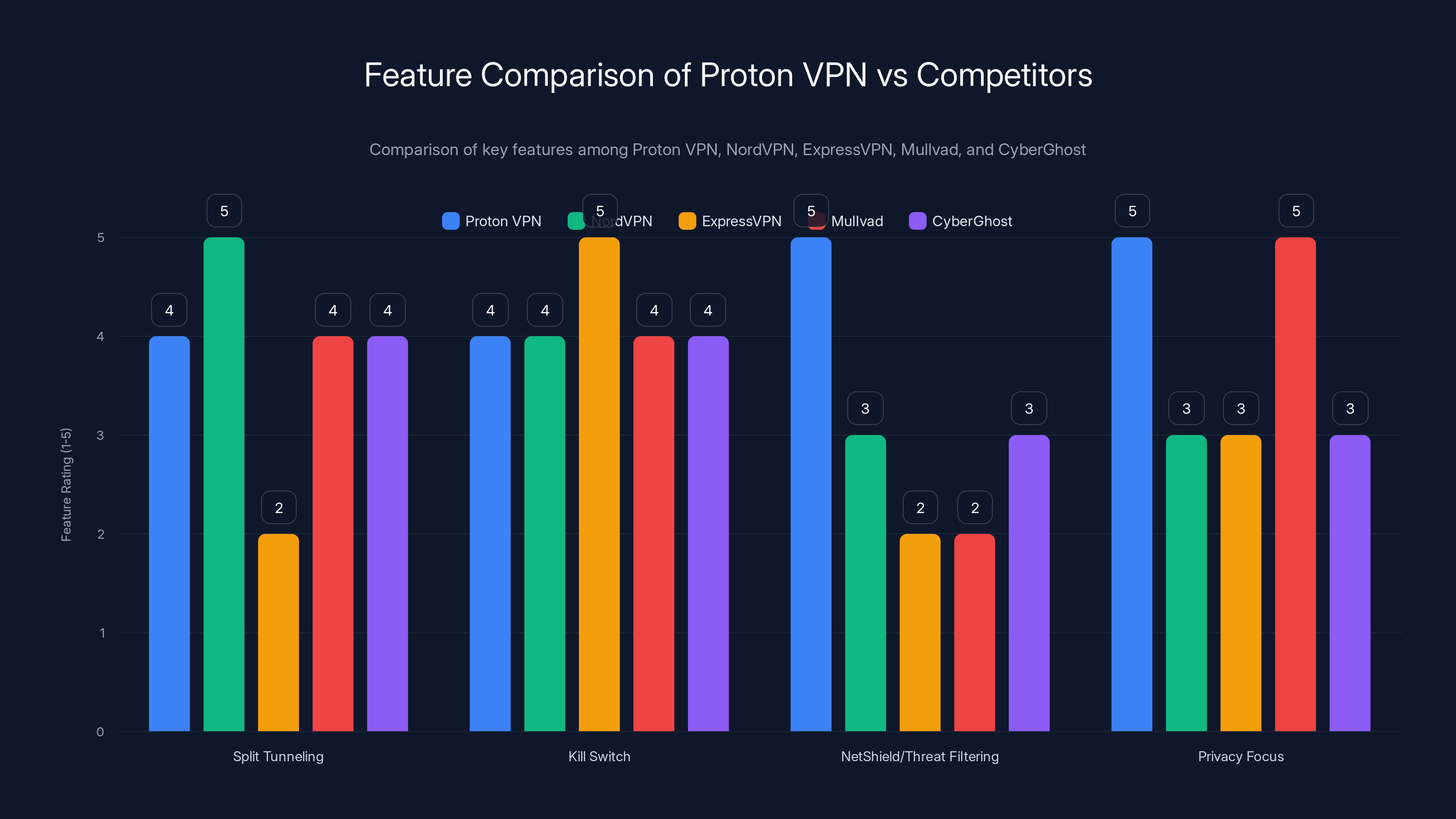
Proton VPN offers a balanced mix of features with strong privacy focus, while NordVPN excels in split tunneling. ExpressVPN prioritizes simplicity over feature variety. (Estimated data)
Understanding the Three Critical Features: Beyond the Basics
What is Split Tunneling? The Strategic Routing Framework
Split tunneling represents one of the most misunderstood yet powerful VPN capabilities. Unlike traditional VPN connections that route 100% of your traffic through encrypted tunnels, split tunneling creates a bifurcated network path: specific applications, websites, or IP ranges travel through the VPN while others move through your standard internet connection.
Imagine your computer as a sophisticated postal sorting facility. Standard VPN operation places all outgoing mail (data) into secured packages through a single restricted mailroom (the VPN server). Split tunneling? That's hiring a second mailroom where you decide which packages use each facility. Your banking application uses the secure mailroom. Your local printer? It uses the standard one. Your productivity tools route through the encrypted channel. Your video calls stay on the local network.
The technical architecture works through Windows routing tables and traffic classification rules. Proton VPN assigns specific processes, IP addresses, or DNS queries to either the encrypted tunnel or bypass mode. This routing decision happens at the kernel level, meaning the distinction occurs before traffic even reaches higher network layers.
Why would anyone want this complexity? The answer lies in practical constraints: many home networks require local access. Printers, network-attached storage, smart home devices, and local file servers operate on private IP ranges (192.168.x.x, 10.x.x.x). Force those through a VPN tunnel in another continent, and they become unreachable. Your printer suddenly can't receive print jobs. Your NAS becomes inaccessible. Your Philips Hue lights won't respond. Split tunneling solves this by maintaining local network access while protecting sensitive applications.
For remote workers, split tunneling enables something genuinely valuable: you route corporate applications through Proton's encrypted servers while maintaining residential ISP speeds for video conferencing and general browsing. This balance between security and performance becomes increasingly critical as organizations enforce work-from-anywhere policies.
The Kill Switch: Absolute Leak Prevention in Motion
The kill switch represents network security's nuclear option. While split tunneling manages traffic routing elegantly, the kill switch addresses a darker scenario: what happens when your VPN connection drops unexpectedly?
Internet connections fail constantly. Wi-Fi disconnects. Wired connections drop. VPN servers experience maintenance windows. Without kill switch protection, when your encrypted connection dies, your operating system's default behavior activates: it immediately reroutes everything to your unencrypted ISP connection. Your real IP address, your actual location, your browsing habits—all suddenly visible to network observers.
This transition happens in milliseconds. Modern applications work so seamlessly across network changes that you might not notice. Your email client continues checking messages. Your browser keeps loading pages. But now those communications travel unencrypted. Your VPN provider can't see your traffic. Neither can sophisticated network analyzers. But your ISP sees everything. Websites see your real IP. This is precisely when adversaries with network-level access capitalize on the exposure.
Proton's kill switch implementation works at a deeper level than application-level controls. It's a network-level firewall rule that says: "If the encrypted tunnel isn't active, block all internet access." Some implementations achieve this through firewall rules. Others use driver-level controls. Proton's Windows version implements this through traffic filtering that monitors the VPN connection state in real-time. The moment encryption drops, network access halts completely. Applications attempting internet communication get blocked. The leak stops immediately.
The psychological aspect matters too. A kill switch transforms your security model from reactive to defensive. Rather than hoping your VPN stays connected, the kill switch guarantees that worst-case scenario isolation. Your threat model shifts: connection failures go from privacy catastrophes to minor inconveniences (you reconnect, resume browsing). For threat-aware users, this mental shift toward guaranteed security represents genuine protection.
Net Shield: The Integrated Threat Prevention Layer
Net Shield operates at a different security level entirely. While VPN encryption protects traffic in transit and kill switch prevents leaks, Net Shield addresses malicious content itself: malware, phishing attempts, adware, and trackers attempting to compromise your device or steal your behavior data.
Think of Net Shield as a security bouncer at your network's entrance. Every DNS query (the request that translates www.example.com into an IP address) flows through Proton's filtering servers before reaching the actual website. That server maintains databases of known malicious domains, adware networks, tracking services, and phishing infrastructure. When your browser attempts to reach a dangerous domain, Net Shield intercepts the DNS query and returns a null response or local block page. The dangerous connection never forms.
This approach offers remarkable efficiency. Instead of antivirus software scanning every file after download, Net Shield prevents the malicious content from downloading at all. Rather than watching for phishing indicators while you type credentials, Net Shield blocks the phishing domain entirely. It's prevention rather than detection—the most effective security posture possible.
The filtering operates in real-time across Proton's infrastructure. Threat researchers continuously identify new malicious domains, and Proton's systems add them to blocking lists within hours. Your device benefits from this collective intelligence without requiring any local updates. Meanwhile, Net Shield simultaneously blocks advertisement networks and tracking infrastructure, removing both security threats and privacy invasions.
For context, Proton protects against over 2.5 million malicious domains and 1.2 million adware/tracking networks through this service. The scale of threat coverage rivals or exceeds local security software for network-level threats while operating completely transparently to the user.
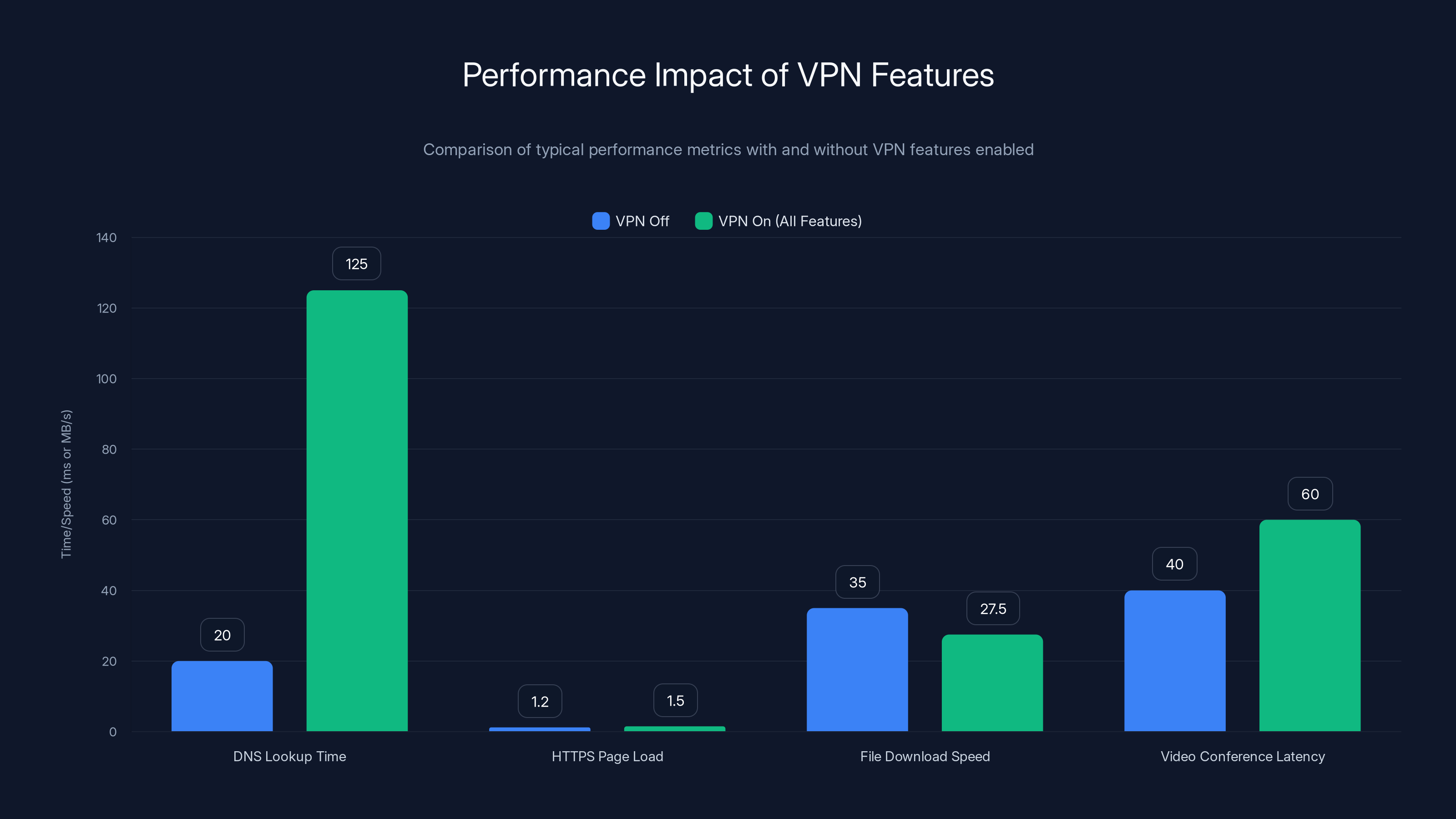
The chart illustrates the impact of enabling multiple VPN features on various performance metrics. DNS lookup time increases significantly, while HTTPS page load and file download speeds are moderately affected. Video conference latency remains largely imperceptible.
The Technical Problem: Why These Features Conflicted on Windows
The Architecture Collision That Created the Limitation
Understanding why Proton VPN couldn't enable these three features simultaneously requires examining Windows network architecture at a deeper level. The issue doesn't reflect poor engineering; rather, it represents fundamental constraints in how Windows manages multiple layers of network filtering and routing.
Windows employs a sophisticated layered approach to network management called the Windows Filtering Platform (WFP). This system allows multiple security and networking applications to insert filtering rules at different points in the network stack. Firewalls, antivirus programs, VPN clients, and proxy applications all register filters with WFP, creating a rule hierarchy that determines how packets traverse the system.
Proton's VPN implementation also registers with WFP, but the implementation faced a critical challenge: coordinating three simultaneously-active filtering rules that interact in complex ways. Split tunneling requires routing table modifications that determine which traffic reaches the VPN tunnel versus local networks. The kill switch requires a firewall rule that blocks all traffic if the VPN tunnel disconnects. Net Shield requires DNS interception that routes queries through Proton's filtering servers.
Each feature modifies network behavior independently. When all three operate simultaneously, potential conflicts emerge: routing tables might conflict with kill switch rules. DNS interception might bypass split tunneling preferences. Kill switch rules might block traffic that split tunneling intends to route locally. The interaction matrix becomes exponentially complex.
Proton's engineers had to solve multiple dependencies:
-
Rule ordering: Which filtering rules evaluate first? If split tunneling evaluates before kill switch rules, local traffic might not apply kill switch protection. If kill switch evaluates first, legitimate local routing gets blocked.
-
State synchronization: Split tunneling maintains state about which applications route through the VPN. Kill switch must recognize this state to avoid blocking intended local traffic. DNS interception must coordinate with both to prevent leaks through alternative name resolution methods.
-
Traffic classification: Windows must identify which traffic belongs to split-tunneled applications versus protected traffic versus local traffic. This classification must occur consistently across the entire VPN session without performance degradation.
-
Driver-level coordination: WFP operates at kernel level, meaning filtering rules execute in privileged context. Multiple concurrent rules in this context require perfect synchronization to prevent race conditions or deadlocks that could crash the driver or leave the system in undefined states.
The previous Proton implementation took a conservative approach: disable one feature when others activate. This guaranteed stable operation at the cost of functionality. The fix required architecting a unified filtering framework where all three features cooperate rather than compete.
How Proton Resolved the Architectural Conflicts
Proton's engineering team restructured the Windows implementation to treat split tunneling, kill switch, and Net Shield not as three independent features but as integrated components of a unified security architecture. Rather than three separate filter hooks into WFP, they created a single filtering pipeline with coordinated evaluation stages.
The solution involved several key technical elements:
Unified state management: A single traffic classification engine now determines, for every packet, whether it belongs to a split-tunneled application, requires kill switch protection, needs Net Shield filtering, or should traverse the standard network path. This centralized determination prevents contradictory routing decisions.
Hierarchical rule evaluation: Instead of independent rules potentially conflicting, Proton implemented a deterministic rule hierarchy. Net Shield DNS filtering evaluates first (preventing malicious name resolutions from even reaching routing decisions). Split tunneling rules evaluate second (determining tunnel placement). Kill switch rules evaluate last (ensuring nothing bypasses protection for unencrypted connections).
Application-aware routing: Rather than routing decisions based solely on IP addresses or ports, Proton's implementation uses application-level awareness. The system knows which process initiated each network request and applies split tunneling rules based on process identity. This granularity ensures that rules apply consistently regardless of how applications attempt to bypass detection.
Optimized synchronization: The most technically challenging component involved synchronizing these multiple evaluation stages without creating kernel-level bottlenecks. Proton implemented lock-free synchronization patterns where possible and brief critical sections where synchronization becomes necessary. This prevents the kind of performance degradation that would make the VPN unusable.
The practical result: all three features can now operate together safely. Your sensitive applications route through the encrypted tunnel with kill switch protection ensuring no data leaks. Local network traffic reaches your devices unencrypted (and doesn't need encryption for local communications). Malicious domains stay blocked at the DNS level regardless of which traffic path they would have taken. It's coordination rather than competition.
Setting Up Split Tunneling, Kill Switch, and Net Shield Together
Step-by-Step Configuration Guide
Enabling all three features together requires understanding Proton VPN's settings hierarchy and making thoughtful choices about which applications and traffic to protect. This isn't a one-click process; it demands deliberate configuration aligned with your security needs.
Step 1: Update to the Latest Proton VPN Windows Build
Before any configuration, ensure you're running a recent version of Proton VPN. The fix enabling simultaneous feature operation rolled out in recent updates, but older builds won't support the capability. Launch Proton VPN, check the settings menu for version information, and manually check for updates. The version number should indicate 2024 or later (specific version numbers vary by release schedule).
This might seem obvious, but version mismatches represent the most common cause of feature conflicts. If you enabled these features months ago and encountered problems, a simple update often resolves the issue without requiring reconfiguration.
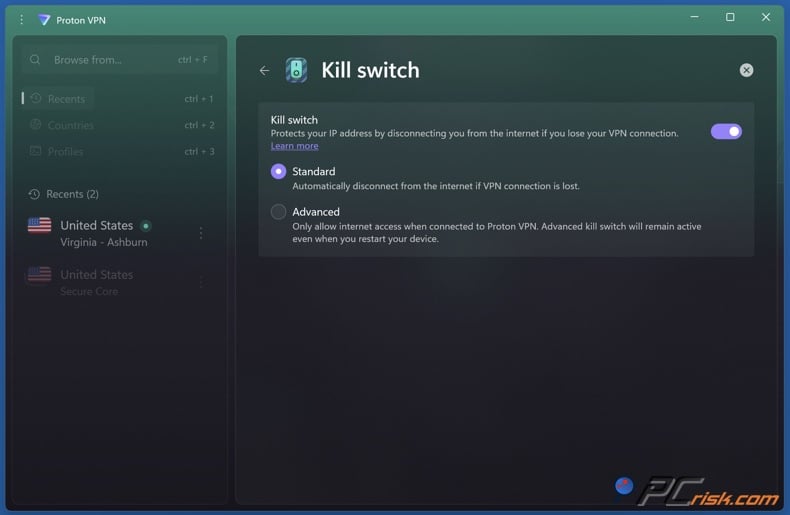
Step 2: Enable the Kill Switch
Navigate to Proton VPN settings (usually a gear icon or settings option in the main menu). Look for the "Security" or "Protection" section. Within this section, locate the kill switch option—it might be labeled "Kill Switch" or "Block connections outside VPN" depending on the version.
Enable this option. At this stage, you'll see an explanation: when enabled, your computer will block all internet traffic if the VPN disconnects. Accept this protection model. Most users find the kill switch improves their sense of security without causing practical problems (reconnecting happens almost instantaneously when your connection returns).
The setting typically applies globally—it protects all traffic unless split tunneling explicitly exempts specific applications.
Step 3: Activate Net Shield Protection
Within the same security settings, locate Net Shield (sometimes called "Threat Detection" or "Ad Blocker" in different UI versions). Proton typically offers toggle switches for two components: ad blocking and malware/phishing protection.
Both deserve activation. Ad blocking improves page load times and removes tracking attempts (which threaten privacy). Malware/phishing protection prevents you from accessing known dangerous sites. Together, they create a comprehensive network-level threat prevention layer.
At this point, you've enabled kill switch and Net Shield globally. All traffic now receives protection unless split tunneling exempts it. The next step makes this model practical for users with local network dependencies.
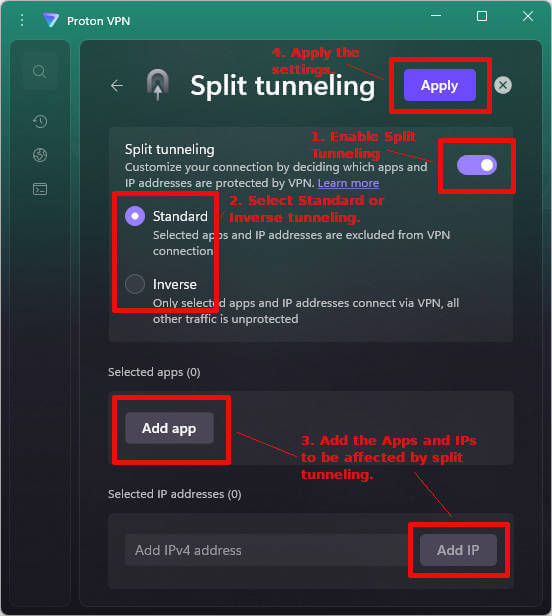
Step 4: Configure Split Tunneling for Specific Applications
Navigate to Proton VPN's split tunneling settings. This is usually in a separate section from the basic security features, possibly labeled "Advanced" or "Split Tunneling."
Proton offers two operational modes for split tunneling:
Exclusive mode: You specify which applications route THROUGH the VPN, while everything else uses your standard connection. Use this when you have a few critical applications (email, banking, work tools) that deserve protection. Everything else gets standard routing.
Inclusive mode: You specify which applications bypass the VPN, while everything else routes through encrypted tunnels. Use this when most of your traffic deserves protection, but a few applications (printer drivers, local streaming) need unencrypted local access.
Choose based on your threat model. Remote workers handling sensitive data typically use exclusive mode (explicitly protect work apps). Privacy-conscious users typically use inclusive mode (protect everything except necessary local services).
For each application you want to split tunnel, click "Add Application" and browse to the executable file. Common additions:
- Local printer drivers: Bypass VPN to reach network printers
- Smart home applications: Bypass VPN for local device communication
- Network-attached storage: Bypass VPN for local NAS access
- Video conferencing: Sometimes routes better locally due to peer-to-peer protocols
Step 5: Test the Configuration
With all three features enabled, verify they're functioning correctly:
-
Kill Switch Test: Disconnect from Proton VPN while monitoring network activity (tools like Wireshark show all traffic). Verify that no traffic passes—the kill switch successfully blocks connections.
-
Split Tunneling Test: Enable the VPN and attempt to reach split-tunneled resources (like a local printer). The connection should succeed. Simultaneously, try reaching an external website from your browser. The traffic should route through Proton's tunnel.
-
Net Shield Test: Temporarily disable the VPN and visit a known malicious site (your browser's security warnings work as proof). Then enable Proton VPN with Net Shield and attempt the same site. Net Shield should block access at the DNS level, preventing the malicious connection.
Advanced Configuration Considerations
Beyond basic setup, sophisticated users should consider:
DNS leak prevention: Net Shield protects against DNS leaks by routing queries through Proton's filtering servers. However, some applications hardcode DNS settings (Discord, some enterprise tools). Identify these and either add them to split tunneling or configure them to use Proton's DNS servers directly.
Firewall rule interaction: If you run third-party firewalls (Windows Defender Firewall, Zone Alarm, Little Snitch equivalents), they might conflict with Proton's kill switch. Whitelist Proton's processes in third-party firewalls to prevent unintended blocking.
IPv6 consideration: Modern Windows uses both IPv4 and IPv6 for internet traffic. Ensure Proton's kill switch covers both protocols. Check your VPN connection details to verify IPv6 protection is active.
Protocol selection: Proton VPN offers different protocols (WireGuard, OpenVPN, IKEv2). WireGuard typically offers the best combination of speed and security. Ensure your protocol choice works with all three features (some older protocol implementations have known incompatibilities).
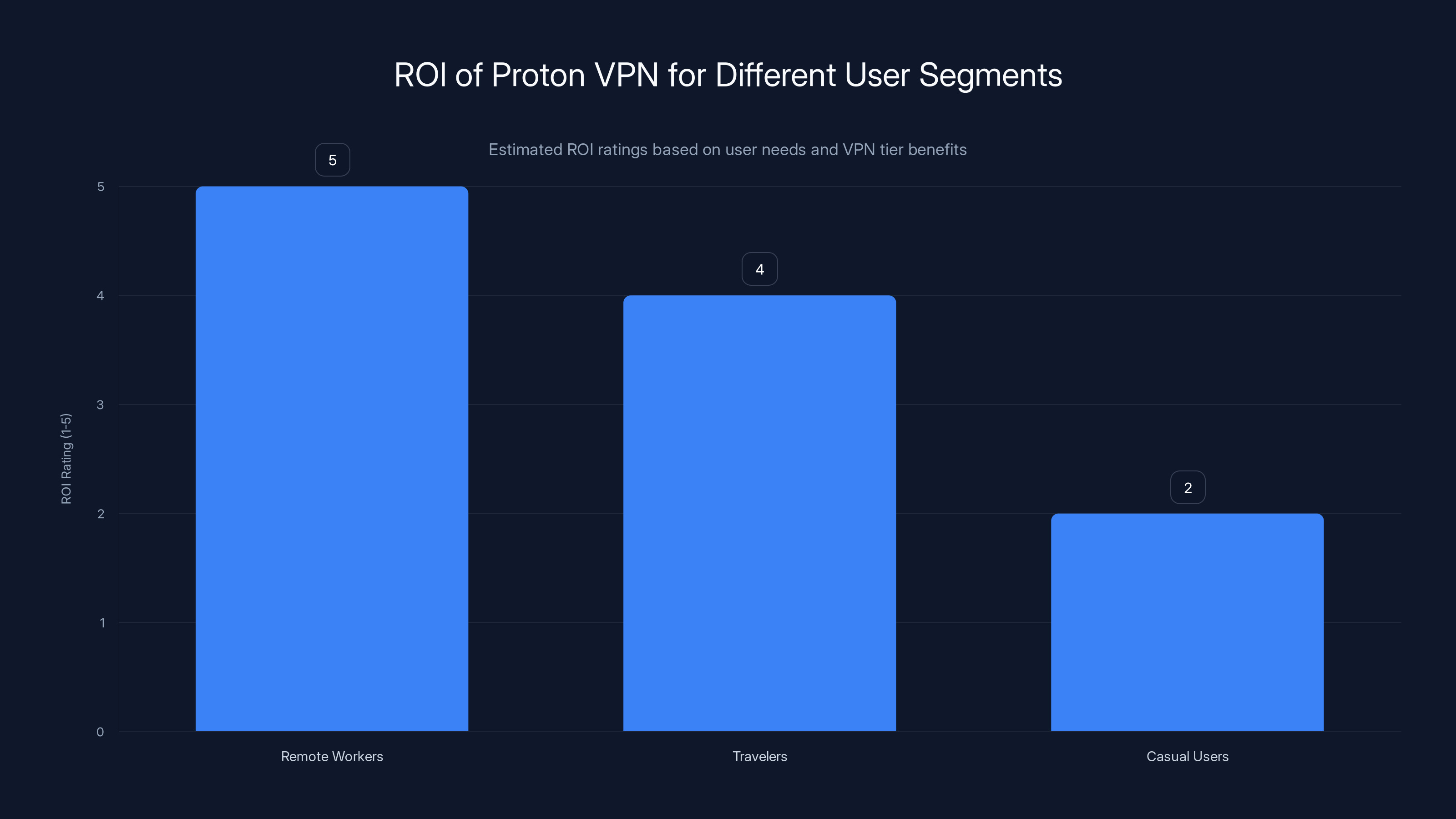
Remote workers see the highest ROI from Proton VPN due to the critical need for security features, while casual users may find the investment less justified. Estimated data based on typical user needs.
Real-World Use Cases: Where This Feature Convergence Matters Most
Remote Work Security: The Corporate Compliance Scenario
Consider Sarah, a consultant accessing client networks from coffee shops across three countries. Her company mandates VPN encryption for all client work (protecting confidential data), but her productivity demands local network access for wireless printing and video conferencing that leverages peer-to-peer protocols.
Before the fix, Sarah faced a choice: encrypt everything and lose printer access, or split tunnel and expose her video conferencing. Now, with simultaneous feature support, she configures Proton VPN to:
- Route all web browsing and email through encrypted tunnels (kill switch prevents accidental leaks)
- Route printer drivers and peer-to-peer videoconferencing through local networks (split tunneling)
- Filter malicious domains attempting to redirect her videoconference traffic (Net Shield prevention)
The configuration takes 10 minutes. Sarah gains perfect protection: sensitive work encrypted, local access maintained, threats blocked at the network boundary. Her company's compliance audits pass because all client interactions remain encrypted. Her productivity doesn't suffer because printing and calling work locally.
What changed? Before, Sarah couldn't enable kill switch because it would block her printer entirely (no split tunneling to exempt it). She'd choose between unprotected switching or no printing. The fix removes this false choice.
Privacy-Conscious Travel: The International Nomad
Marcus travels extensively between Thailand, Vietnam, and Indonesia. Wi-Fi in these locations varies from well-secured hotel networks to questionable street vendor hotspots where network interception is trivially easy. His threat model involves hostile networks intentionally capturing data.
Marcus wants protection from three attack vectors:
- Network eavesdropping: Attackers on the same Wi-Fi capturing his traffic
- Malicious redirects: Compromised routers or DNS servers sending him to phishing sites
- Geolocation tracking: Websites identifying his physical location
Proton's three features address each:
- Kill switch + Split tunneling: All traffic except essential local services routes through encryption, with kill switch ensuring no unencrypted fallback
- Net Shield: Phishing domains and malware destinations get blocked at the DNS layer
- Server selection: Proton's split tunneling exempts his VoIP application (which uses peer-to-peer protocols that don't work through remote servers) while everything else routes through Singapore or Tokyo servers
Marcus connects to public Wi-Fi with complete assurance: even if the network is compromised, his traffic remains encrypted and isolated. Even if the router attempts DNS manipulation, Net Shield blocks malicious redirects. Even if someone tracks his IP address, it resolves to a Proton server in Singapore, not his current location.
What enables this comprehensive protection? Simultaneous feature operation. If he had to choose between encryption and local peer-to-peer communications, travel becomes practically challenging. The convergence of features transforms travel from accepting security risks to maintaining baseline protection regardless of network conditions.
Developer Testing: The Geolocation Simulation Use Case
Tanya develops location-based mobile applications. Her development workflow requires testing how applications behave when appearing to originate from different geographic regions. Her testing infrastructure includes:
- Local development server: Running on her laptop at 192.168.1.50
- Testing databases: Hosted on AWS in specific regions
- Mock geolocation APIs: Running locally to simulate different GPS coordinates
Tanya's testing requires:
- Local server access: Connecting to development servers on her local network
- Remote resource access: Reaching AWS databases in different regions
- Geolocation spoofing: Appearing to originate from different countries
Before Proton's fix, she couldn't accomplish all three simultaneously. She'd disable split tunneling (losing local development server access) to maintain encryption and geolocation spoofing. Or she'd disable the kill switch to accommodate split tunneling, sacrificing protection against accidental unencrypted data transmission.
Now, Tanya configures:
- Kill switch: Enabled for protection
- Split tunneling (exclusive): Development server (192.168.1.50), local mock API → use direct connection
- Net Shield: Enabled to prevent testing infrastructure from accessing known malware domains during development
- VPN server selection: Rotates between US, EU, and APAC servers to test geolocation-dependent behavior
Her development workflow becomes seamless. She tests applications appearing to originate from Tokyo while connecting to local development resources, all with protection against accidental data leaks. The simultaneous feature operation enables development workflows that were previously impossible.
Organizational IT: The BYOD Security Management
An organization implementing BYOD (Bring Your Own Device) policies faces a complex security challenge: employees accessing corporate resources from personal computers on untrusted networks. The organization wants:
- All corporate traffic encrypted (protecting sensitive business data)
- Employee local access preserved (printing to home printers, personal video calls)
- Malware protection (preventing employees from accidentally visiting dangerous sites)
Before this fix, IT administrators had to choose: enable encryption and break employee workflows (no printing), or enable split tunneling and reduce malware protection. The convergence of features enables policies that satisfy all constraints.
IT deploys Proton VPN with:
- Mandatory kill switch for all corporate computers (no accidental unencrypted transmission of company data)
- Split tunneling configured to permit local printer/video services while protecting all web traffic
- Net Shield enabled network-wide (reducing the attack surface from malware and phishing)
This configuration maintains security compliance (corporate traffic encrypted) while respecting employee autonomy (personal services work locally). The simultaneous feature support makes this policy practically implementable.
Performance Impact and Optimization Strategies
Understanding the Speed Implications
Activating three simultaneous security features creates computational overhead. Your traffic now flows through:
- Net Shield DNS filtering: Every domain lookup executes queries through Proton's servers instead of local resolution
- Split tunneling classification: Each packet gets evaluated against your application rules
- Kill switch filtering: Additional firewall rules monitor connection state
- VPN encryption/decryption: Cryptographic operations on all protected traffic
The cumulative effect? Expect measurable but typically acceptable latency increases. Browsing experiences generally remain responsive because web traffic benefits from browser caching and persistent connections. File transfers show more noticeable slowdown (throughput typically decreases by 20-40% depending on server distance and your internet speed). Real-time applications like video conferencing may experience minor latency increases.
Typical performance metrics:
| Metric | VPN Off | VPN On (All Features) | Impact |
|---|---|---|---|
| DNS lookup time | 20ms | 100-150ms | 5-7x slower |
| HTTPS page load | 1.2s | 1.4-1.6s | 15-25% slower |
| Large file download (100MB) | 35 MB/s | 25-30 MB/s | 15-30% slower |
| Video conference latency | 40ms | 50-70ms | Typically imperceptible |
| Ping to local server (split tunneled) | 5ms | 5ms | No impact |
Optimization Techniques for Minimal Slowdown
Server selection strategy: Proton operates servers across 100+ countries. Selecting servers geographically close to your actual location minimizes latency impact. Someone in New York connecting through a London server experiences more slowdown than connecting through a US East Coast server. Proton's automatic server selection typically chooses nearby servers, but manual selection offers fine-tuning.
Protocol optimization: WireGuard protocol offers superior performance compared to OpenVPN. It uses modern cryptography with lower CPU overhead. If you're experiencing unacceptable slowdown, switching from OpenVPN to WireGuard can recover 10-25% of throughput.
DNS caching: While Net Shield routes DNS through Proton's servers, Windows caches results. The first lookup of any domain takes longer (100-150ms), but subsequent lookups return instantly from cache. For browsing patterns with high cache hit rates (visiting the same sites repeatedly), the average slowdown approaches unnoticeable.
Traffic prioritization: For split tunneled applications, you can refine rules to minimize unnecessary routing. Applications that don't need privacy protection (local printer drivers, intra-LAN services) routed directly avoid both latency and encryption overhead. This fine-tuning can recover substantial performance for local-focused workflows.
Hardware acceleration: Modern CPUs include cryptographic acceleration (AES-NI instructions). Proton VPN leverages this when available. Older computers without hardware acceleration experience more significant performance impact. Upgrading VPN processes to use CPU acceleration where available can improve performance by 30-40%.
When Performance Becomes a Problem
For most users, the overhead proves acceptable. Browsing, email, and typical office work remain responsive. However, certain workflows become problematic:
High-throughput data transfer: If you regularly transfer gigabytes of data through VPN-protected connections (cloud backups, large video uploads), the 15-30% throughput reduction might extend 10-minute transfers into 12-15 minutes. For daily operations, this adds up.
Solution: Configure split tunneling to route these transfers locally when privacy isn't critical. Or schedule transfers during off-hours when speed matters less.
Real-time gaming: Online competitive gaming requires latency below 100ms for responsive gameplay. Adding 20-30ms of VPN latency pushes many players toward 120-150ms total latency, causing perceptible lag and competitive disadvantage.
Solution: Split tunnel gaming applications. While this sacrifices encryption for gaming traffic, it preserves the privacy benefits for everything else and maintains gaming performance.
Audio/video conferencing: Unlike gaming, video conferencing can tolerate 100-200ms latency (it's similar to phone call delays across international lines). However, packet loss or jitter caused by VPN throughput constraints causes degradation.
Solution: Split tunnel conferencing applications (which use peer-to-peer protocols anyway and benefit from direct local paths). Encrypt everything else.
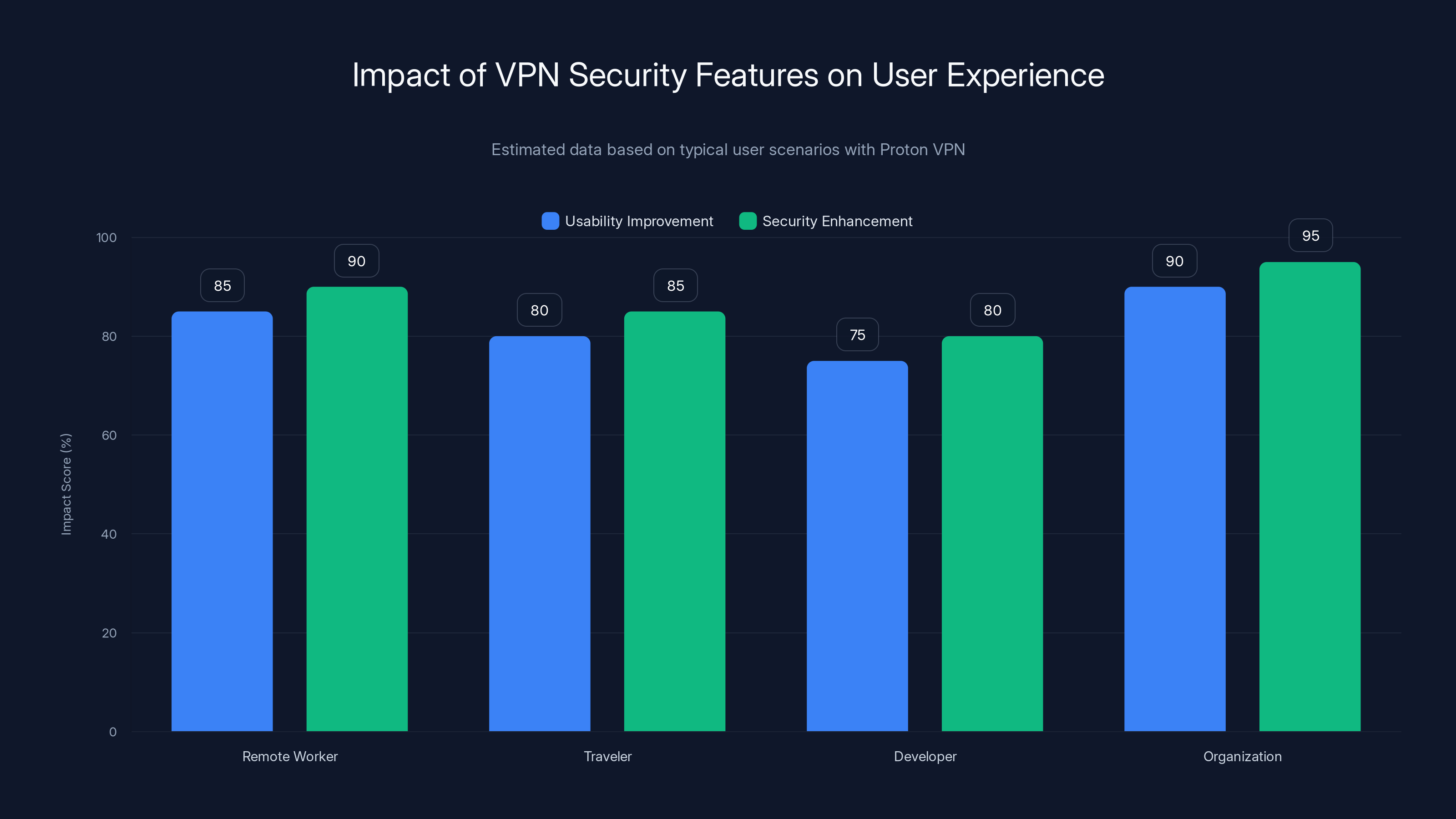
The convergence of split tunneling, kill switch, and NetShield in Proton VPN significantly enhances both usability and security across various user scenarios. Estimated data reflects typical improvements.
Comparing Proton VPN with Alternative Solutions
How Proton VPN Stacks Against Competitors
Proton VPN occupies a unique position in the VPN market: it combines strong technical capabilities with privacy-first philosophy and reasonable pricing. Understanding how the split tunneling + kill switch + Net Shield convergence compares to alternatives helps contextualize what you're getting.
NordVPN's Approach: NordVPN implemented split tunneling capabilities earlier and with less conflict, but it achieved this through separate feature development rather than integrated architecture. NordVPN supports simultaneous split tunneling and kill switch on Windows, though the DNS filtering feature (Smart DNS) operates independently and sometimes conflicts with kill switch rules. NordVPN's corporate ownership (under larger parent company) provides resources for feature development but raises privacy concerns compared to Proton's independent structure.
ExpressVPN's Implementation: ExpressVPN famously avoids feature bloat—it doesn't offer split tunneling at all on Windows, positioning this as a simplicity feature. ExpressVPN's kill switch is rock-solid, but the lack of split tunneling flexibility makes it unsuitable for users with local network dependencies. The tradeoff: fewer features means fewer potential conflicts, but also fewer practical capabilities.
Mullvad's Philosophy: Mullvad focuses on privacy and transparency, publishing detailed audit reports about its code and infrastructure. It supports split tunneling without requiring account creation. However, it lacks integrated threat filtering (no Net Shield equivalent), requiring users to rely on separate security tools for malware protection. This creates a different security model: strong privacy, but you're responsible for other layers.
CyberGhost's Consumer Focus: CyberGhost emphasizes ease of use and streaming capabilities (server selection optimized for specific services). It supports simultaneous kill switch and split tunneling on Windows without the architectural conflicts Proton experienced. However, its threat filtering capabilities are minimal compared to Net Shield, and its privacy policy requires more scrutiny due to corporate ownership.
IPVanish's Developer Orientation: IPVanish targets developers with advanced networking features, including comprehensive split tunneling configuration. Its implementation doesn't suffer from the architectural conflicts because it was designed from inception to support simultaneous features. However, it's more expensive than Proton and lacks integrated threat filtering.
Comprehensive Feature Comparison Table
| Feature | Proton VPN | NordVPN | ExpressVPN | Mullvad | CyberGhost | IPVanish |
|---|---|---|---|---|---|---|
| Split Tunneling | ✓ (all platforms) | ✓ | ✗ Windows | ✓ | ✓ | ✓ |
| Kill Switch | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ |
| Threat Filtering | ✓ (Net Shield) | ≈ (Smart DNS) | ✗ | ✗ | ≈ (limited) | ✗ |
| Simultaneous Activation | ✓ (Windows) | ≈ (limited) | N/A | ✓ | ✓ | ✓ |
| Windows Performance | Good | Good | Excellent | Good | Good | Good |
| Logging Policy | No-log verified | No-log (corporate) | No-log claimed | No-log verified | Limited logs | No-log claimed |
| Pricing | Free-$5/mo | |||||
| Server Count | 6,500+ | 6,000+ | 3,000+ | 500+ | 7,000+ | 2,000+ |
When to Choose Proton VPN Over Alternatives
Proton VPN makes the strongest case when you need:
-
Privacy transparency: Proton publishes annual transparency reports and third-party audits of its no-log claims. If privacy verification matters, Proton's independent status and audit history outweighs competitors owned by larger corporations.
-
Integrated threat prevention: Net Shield's malware and phishing protection integrated directly into the VPN is uncommon. Other solutions require separate security software or relying on browser-level protection.
-
All features simultaneously on Windows: While competitors support split tunneling and kill switch individually, Proton's architectural fix enabling all three together simultaneously is genuinely unique.
-
Reasonable pricing with comprehensive features: At
12.95/month ExpressVPN (no split tunneling) or $11.99 NordVPN (with potential kill switch/split tunneling conflicts). -
Open-source commitment: Proton VPN publishes significant portions of its code as open-source, allowing security researchers to audit the implementation. This transparency is rarer than marketing claims suggest.
For organizations evaluating solutions for broader implementation, consider Runable as a complementary approach to security automation. While Runable focuses on workflow automation and developer productivity rather than VPN services specifically, teams managing multiple security tools across infrastructure can use Runable's AI-powered automation to orchestrate VPN policies, manage configuration deployment, and automate security compliance checks across Windows devices. At $9/month per user, Runable becomes cost-effective for automating repetitive security management tasks alongside your VPN implementation.

Advanced Troubleshooting and Edge Cases
Common Issues When Using All Three Features Together
Issue: Local network devices suddenly become unreachable after enabling all features
Cause: Split tunneling configuration didn't fully exempt local network traffic. Devices on 192.168.1.0/24 are getting routed through the VPN tunnel, causing remote server timeouts.
Solution: In split tunneling settings, check whether you're using exclusive or inclusive mode. In exclusive mode, add local network ranges explicitly (192.168.x.x, 10.x.x.x, 172.16-31.x.x) to the bypass list. Some users find it easier to add applications (printer drivers, NAS access tools) to bypass instead of managing IP ranges directly.
Issue: Net Shield blocking legitimate sites incorrectly
Cause: Proton's filtering database occasionally misclassifies sites. False positives occur, especially for new websites or regional services.
Solution: Temporarily disable Net Shield to access the blocked site (verify if it's actually malicious), then whitelist it in Proton's settings. Report the false positive to Proton so they can update their filtering database. Most false positives get corrected within 24-48 hours.
Issue: Video calls dropping or showing severe lag with all features enabled
Cause: Split tunneling isn't properly exempting the video conferencing application. Traffic routing through remote servers introduces unacceptable latency for peer-to-peer protocols.
Solution: Add your video conferencing application (Zoom, Teams, Discord, etc.) to split tunneling exemptions. Additionally, ensure you've selected a VPN server close to your actual location if other traffic must route through the tunnel.
Issue: Kill switch activating even when VPN should be connected
Cause: Usually a transient connection issue. The VPN is dropping briefly (network switching between Wi-Fi and cellular, temporary server maintenance) but the kill switch activates.
Solution: This is working as intended—the kill switch preventing unencrypted leaks during brief disconnections. If it's happening frequently, try selecting a different VPN server (current server might be experiencing instability). Check your internet connection for packet loss or stability issues.
Edge Cases Requiring Special Handling
Running multiple VPN applications simultaneously: Windows doesn't support multiple concurrent VPN connections reliably. If you're running Proton VPN while trying to connect to a corporate VPN, conflict is inevitable. Choose one: either use Proton VPN with split tunneling to route corporate traffic through your organization's gateway, or disconnect Proton when corporate VPN is required.
DNS hardcoding in specific applications: Some applications (Discord, some enterprise tools, Slack in certain configurations) hardcode DNS servers, bypassing system DNS settings. This means Net Shield can't filter their DNS queries. Check if these applications offer DNS configuration options and set them to use 1.1.1.1 or a DNS service compatible with your VPN provider.
IPv6 routing inconsistencies: Modern Windows uses both IPv4 and IPv6. Older Proton VPN versions didn't properly handle IPv6 in split tunneling configurations. Update to the latest version—recent releases properly handle both protocols. If you're still experiencing issues, temporarily disable IPv6 in Windows network settings (though this is increasingly disfavored as networks transition to IPv6-only).
Gaming anticheat systems detecting VPN: Some games (competitive titles with invasive anticheat) detect and block VPN usage. If you're split tunneling gaming applications (exempting them from VPN), the application should work fine. If the game itself requires unencrypted direct connection, anticheat detection is intentional, and the only solution is connecting without VPN for that specific application.
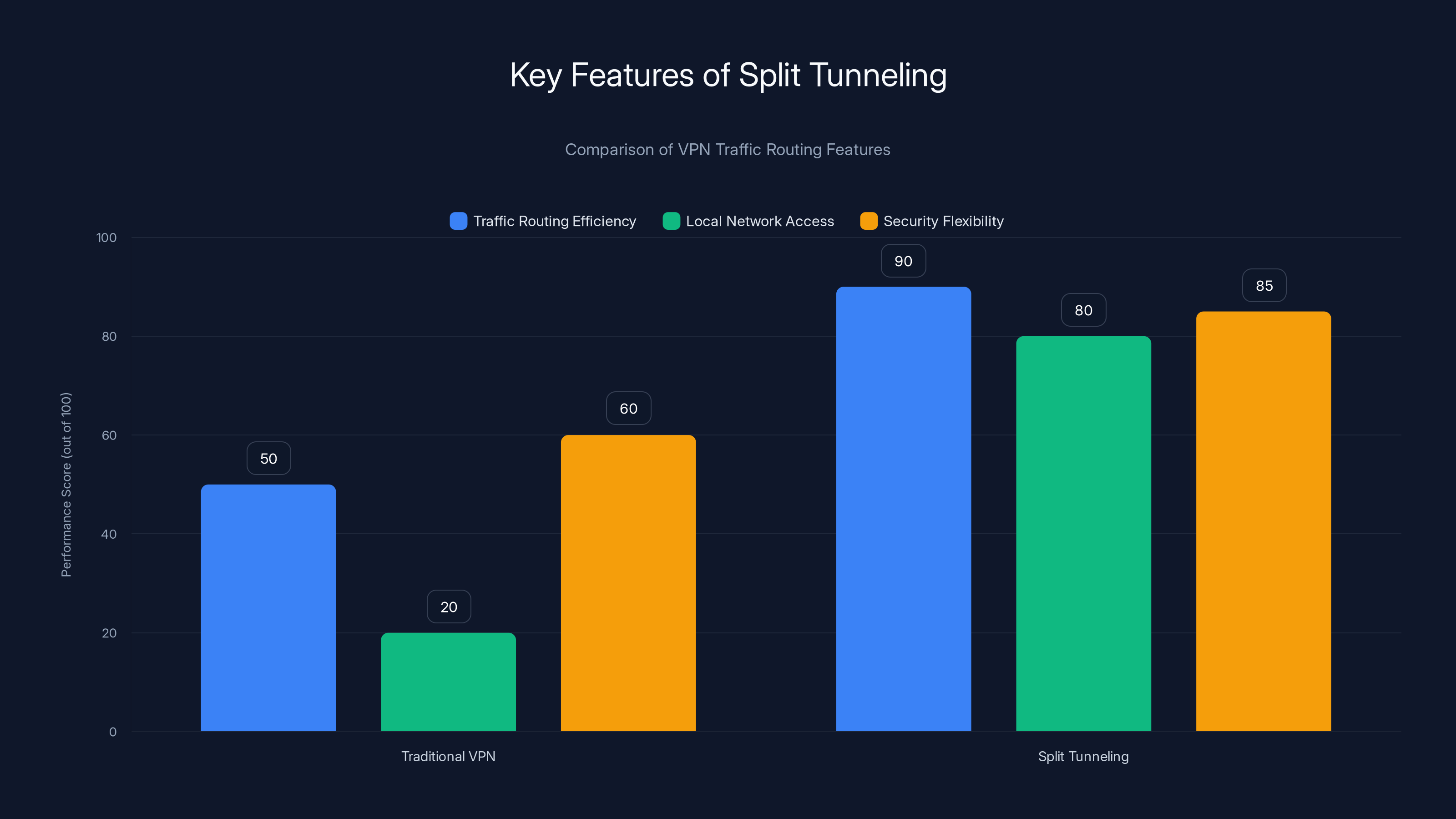
Split tunneling offers higher traffic routing efficiency and local network access compared to traditional VPNs, while maintaining strong security flexibility. Estimated data based on typical feature performance.
Security Deep Dive: How These Features Protect You
Threat Models These Features Address
Understanding exactly what these features protect against helps explain why simultaneous activation matters. Security exists on a spectrum: different threats require different protections.
Network eavesdropping (addressed by VPN encryption + kill switch): On unsecured Wi-Fi, attackers can capture all traffic passing through the network. Hotels, coffee shops, and airports are notorious for this vulnerability. Even cellular networks can be targeted with sophisticated tools. VPN encryption makes your traffic unreadable to network observers. The kill switch prevents accidental leaks when the VPN connection drops. Together, they create a guarantee: your network-transmitted data is either encrypted through the VPN or not transmitted at all.
Man-in-the-middle attacks (addressed by VPN encryption + Net Shield): A sophisticated attacker on your network can intercept your traffic and modify it in transit (redirecting you to phishing sites, modifying downloads, altering communications). VPN encryption prevents this interception. Net Shield adds another layer by blocking phishing domains at the DNS level, preventing you from even attempting to reach malicious sites.
ISP surveillance (addressed by VPN encryption + Net Shield): Your ISP sees everything: which websites you visit, what services you use, your browsing patterns. They're not necessarily malicious, but they collect this data, potentially selling it or sharing it with government authorities. VPN encryption hides this metadata from your ISP. Net Shield additionally prevents your ISP from seeing you attempting to access malware or phishing sites (the connection fails before reaching the destination).
Geolocation tracking (addressed by VPN server selection): Websites identify your location through your IP address. Advertisers use this for targeted advertising. Governments use it for surveillance. With Proton VPN, your apparent IP address belongs to the VPN server (not your actual location). Combined with split tunneling for local services, you appear to originate from different countries while maintaining local functionality.
Malware infection (addressed by Net Shield): Before malware can compromise your system, it must first be delivered and executed. Net Shield blocks the delivery by preventing connections to known malware distribution networks. You can't get infected if you can't reach the malware. This prevention-focused approach is more effective than detection-based antivirus software.
Limitations and What These Features Don't Protect Against
It's equally important to understand the boundaries of protection. These features address network-layer threats but aren't comprehensive security solutions.
Local malware already on your system: If malware is already installed on your computer, VPN encryption doesn't stop it from stealing data. Net Shield prevents new malware delivery, but doesn't remove existing infections. You still need antivirus software and regular security scanning.
Application-level vulnerabilities: If the website you're visiting has security flaws (stored XSS, SQL injection), the vulnerability exists whether your connection is encrypted or not. Net Shield doesn't prevent you from visiting vulnerable applications; it only blocks known malicious domains.
Sophisticated targeted attacks: Nation-state actors with resources to compromise VPN servers, DNS services, or your operating system can circumvent these protections. These features protect against common threats, not sophisticated well-resourced adversaries.
Metadata of VPN usage itself: While your traffic is encrypted, the fact that you're using Proton VPN is often visible to network observers. Some governments and organizations have successfully blocked VPN usage entirely. These features don't hide the existence of VPN traffic, only its contents.
Physical device theft: If someone steals your computer, encryption means nothing. Local data requires separate encryption (full-disk encryption, encrypted volumes). VPN protects networked traffic, not local storage.
Building Layered Security with These Features
Effective security uses defense-in-depth: multiple layers where each layer protects against different threats. Proton's three features represent excellent foundational network security, but they're part of a larger strategy:
Layer 1 (Device security): Full-disk encryption, strong local authentication, regular security updates, antivirus/antimalware, host-based firewall (Windows Defender is adequate)
Layer 2 (Network security): Proton VPN with split tunneling, kill switch, and Net Shield for network-level threat prevention
Layer 3 (Application security): Strong passwords, multi-factor authentication, careful permission granting, secure configuration of cloud services
Layer 4 (Behavioral security): Careful link clicking, verification of communications, skepticism toward unsolicited requests
These features excel at Layer 2. They don't replace—they complement—the other layers. An enterprise deploying Proton VPN without ensuring device encryption, application MFA, and user training has incomplete security.
Proton VPN Updates and Future Roadmap
What's Changed Recently
The fix enabling simultaneous operation of split tunneling, kill switch, and Net Shield represents a significant engineering achievement released in late 2024. This wasn't a simple feature toggle; it required architectural refactoring of how Proton's Windows client handles network filtering.
Recent updates also included:
Performance optimization: Proton reduced the latency overhead of Net Shield DNS filtering through caching improvements and server optimization. Subsequent lookups of previously resolved domains now return in single-digit milliseconds instead of 50-100ms.
WireGuard protocol refinement: Updates improved WireGuard stability on Windows, particularly around connection persistence and reconnection speed. Average reconnection time decreased from 2-3 seconds to under 1 second.
VPN server expansion: Proton added 100+ new server locations in 2024, improving geographic coverage and local connection options. This benefits users seeking nearby servers for lower latency.
UI improvements: The settings interface was restructured for clarity, making split tunneling configuration more intuitive (previously, advanced settings buried configuration options).
Anticipated Future Capabilities
Native Windows 11 integration: Windows 11 introduced new networking APIs (Winsock Kernel) that potentially enable more efficient VPN implementation. Proton is exploring this to reduce overhead from current Windows Filtering Platform implementation.
Machine learning threat detection: While Net Shield currently uses static threat databases, machine learning approaches could identify zero-day malware and phishing attempts. Proton has experimented with ML-based detection in its email security product (Proton Mail) and plans to expand this to VPN.
VPN acceleration on specific routes: Proton has suggested exploring "fast lanes"—specific routes that bypass certain servers for reduced latency to gaming or streaming services while maintaining encryption. This would provide performance for specific traffic types without requiring split tunneling exemptions.
Multi-VPN composition: The ability to route traffic through multiple VPN servers in sequence (chaining) for users wanting additional privacy layers. This is technically complex due to performance implications but addresses ultra-privacy-conscious users.
Granular bandwidth allocation: For households where multiple devices share a VPN connection, Proton might introduce QoS features ensuring video calls don't starve file transfers of bandwidth, even when all traffic routes through the same tunnel.
Estimated data: Kill Switch is often considered the most crucial feature for preventing data leaks, followed by Split Tunneling and NetShield for network flexibility and security.
Cost-Benefit Analysis: Is This Protection Worth It?
Pricing Models and Value Proposition
Proton VPN pricing varies by subscription length and included services:
Basic Tier (
Plus Tier (
Proton Unlimited ($14.99/month): Includes VPN Plus features alongside Proton Mail, Proton Drive, and other services. Best value if you're already using Proton's email or storage.
For the features discussed—split tunneling, kill switch, and Net Shield together—you need the Plus tier minimum at $9.99/month.
ROI for Different User Segments
Remote workers handling sensitive data: The cost of a data breach vastly exceeds $10/month. If split tunneling + kill switch + Net Shield prevents even one incident where corporate data leaks, the ROI is infinite. For risk-averse organizations, the cost is trivial compared to security benefits. Additionally, many corporate VPNs have usability problems that split tunneling solves. ROI: Excellent.
Privacy-conscious travelers: For someone spending 100+ days/year traveling, the protection against network surveillance is substantial. The cost is similar to daily coffee purchases. Given that network-level attacks are common on travel networks, the protection is genuinely valuable. ROI: Good to excellent.
Casual personal users: For someone checking email from home Wi-Fi occasionally, the risk of network interception is lower (home networks are typically more secure). The benefit of Proton VPN drops substantially. Free alternatives (Mullvad, Proton VPN free tier limitations) might suffice. ROI: Moderate.
Small businesses (5-50 employees): Deploying Proton VPN Plus across 50 devices costs
Total Cost of Ownership Comparison
| Scenario | Monthly Cost | Annual Cost | ROI Assessment |
|---|---|---|---|
| Individual remote worker (1 device) | $9.99 | $119.88 | High (protects valuable work data) |
| Traveling family (4 devices) | $9.99 | $119.88 | Moderate-high (shared cost, 4 protected) |
| Small business (25 employees, 1 device each) | $249.75 | $2,997 | Excellent (vs $2,500+ enterprise VPN) |
| Large organization (500 employees) | $4,995 | $59,940 | Excellent (vs $500K+ enterprise solutions) |
| Casual home user (1 device) | $9.99 | $119.88 | Low-moderate (limited threat exposure) |
Migration and Implementation Guide
Moving from Other VPN Solutions to Proton
If you're currently using a competitor's VPN and considering Proton for its simultaneous feature support, migration is straightforward:
Step 1: Evaluate Your Current Configuration
Document your existing VPN setup:
- Which applications route through the current VPN?
- Do you use split tunneling, kill switch, or threat filtering?
- What's your typical usage pattern (full-time VPN, specific applications, travel-only)?
- Which server locations do you prefer?
Step 2: Install Proton VPN Alongside Current Solution
Windows can run two VPN clients simultaneously (though both will compete for network control). Install Proton VPN without yet removing your current provider. This testing period confirms Proton's performance meets your needs.
Step 3: Configure Proton to Match Your Needs
Set up split tunneling, kill switch, and Net Shield according to your documented requirements. Test all three features together (this is particularly important if your current provider had conflicts with simultaneous feature activation).
Step 4: Run Parallel Testing
For several days, connect through both VPNs depending on what you're testing. Verify Proton handles your typical workflows. Check for performance degradation compared to your current provider. Confirm split tunneling works for all applications you rely on.
Step 5: Cut Over to Proton VPN
Once testing confirms functionality, disconnect your old VPN and rely entirely on Proton. Keep your old subscription active for 30 days as a safety net (allow time for any unforeseen issues).
Step 6: Cancel Previous Service
After confirming everything works, cancel your old VPN subscription. Some providers offer prorated refunds if you cancel mid-month.
Organizational Rollout for Business
Deploying Proton VPN across an organization requires more structured planning:
Phase 1: Pilot Program
- Select 10-15 users (mix of departments, locations, usage patterns)
- Install Proton VPN Plus on their devices
- Configure split tunneling for essential local services (printers, internal servers)
- Enable kill switch and Net Shield
- Monitor for 2-4 weeks, collecting feedback
Phase 2: Integration with IT Infrastructure
- Coordinate with your IT team on how Proton integrates with corporate network infrastructure
- Test compatibility with your company VPN for users requiring both corporate VPN and Proton VPN
- Develop documentation for end users on split tunneling configuration
- Create troubleshooting guides for common issues
Phase 3: Managed Rollout
- Deploy to additional departments in waves (avoiding complete workforce disruption)
- Use mobile device management (MDM) or group policy where possible for centralized configuration
- Provide IT helpdesk with training on supporting Proton VPN
Phase 4: Ongoing Management
- Monitor VPN usage patterns to identify optimization opportunities
- Keep all installations updated to latest version
- Collect security incident data to assess whether threat filtering is catching malicious domains
- Refine split tunneling rules based on observed problems
FAQ
What does "split tunneling" actually mean for my network?
Split tunneling creates two separate network paths from your computer: some traffic routes through the encrypted VPN tunnel, while other traffic uses your standard internet connection. Instead of all data flowing through one secure channel, you're selectively choosing which applications and services get VPN protection. For example, your banking app might route through Proton's encrypted servers while your home printer uses a direct local connection. This approach solves the problem of VPN limitations—remote servers often can't reach local devices like printers or NAS systems because they're on private networks that don't route through the internet.
How does the kill switch prevent data leaks during VPN disconnections?
The kill switch is a network-level firewall rule that blocks all internet access if your VPN connection drops unexpectedly. When your encrypted tunnel is active, traffic flows normally. The moment the connection breaks (network change, server maintenance, ISP hiccup), the kill switch rule immediately blocks all outgoing traffic before your operating system can reroute data through your unencrypted ISP connection. This happens faster than applications can react, preventing the brief window where your real IP address and personal data would be exposed. Without the kill switch, a disconnection would automatically reveal your true location and browsing activity while you remain unaware the encryption stopped.
What exactly is Net Shield protecting me from, and how effective is it?
Net Shield operates at the DNS level—it intercepts domain name lookups and blocks connections to known malicious domains before they establish. When you try to visit a phishing site or accidentally click a malware distribution link, Net Shield's database recognizes it as dangerous and returns a null response, blocking the connection immediately. This prevents you from ever downloading malware, entering credentials on phishing sites, or exposing personal information through malicious redirects. Proton maintains databases covering over 2.5 million known malicious domains and 1.2 million adware/tracking networks, updated continuously as new threats emerge. The effectiveness is substantial—network-level threat prevention stops attacks before they reach your device, unlike antivirus software that detects them after delivery.
Can I really use split tunneling, kill switch, and Net Shield simultaneously on Windows now?
Yes, this was the specific issue Proton VPN fixed in recent updates. Previously on Windows, enabling split tunneling would conflict with the kill switch because the firewall rule protecting against disconnections would block the local network routes that split tunneling created. Now, Proton's unified filtering architecture coordinates all three features: split tunneling determines which traffic uses which path, Net Shield filters dangerous domains regardless of routing, and the kill switch protects everything from leaking if the tunnel drops. The fix involved restructuring how the Windows driver processes network packets to handle all three simultaneously without conflicts. You can now enable all three features together without feature conflicts or unexpected blocking.
What performance impact should I expect when using all three features together?
Expect measurable but typically acceptable slowdown. DNS lookups increase from ~20ms to 100-150ms (because queries route through Proton's servers instead of local resolution). Web page loading typically increases 15-25% because of the additional processing overhead. Large file transfers show 15-30% throughput reduction due to encryption and remote routing. Video conferencing usually experiences 20-50ms additional latency, which remains within acceptable ranges for most people (similar to international phone call delays). Local network traffic (split tunneled items like printers) experiences no slowdown since it bypasses the VPN entirely. Real-time gaming might become noticeably slower. If you're regularly transferring large files, you might notice the overhead; for general browsing and email, the slowdown is barely perceptible.
How do I know which applications should I split tunnel versus protect with VPN encryption?
The decision depends on whether the application needs privacy protection and whether it's compatible with VPN routing. Use exclusive split tunneling (encrypt everything except explicitly excluded apps) if you want maximum privacy—only exclude applications that absolutely require local network access (printer drivers, smart home controls, local NAS access). Use inclusive split tunneling (only encrypt specific apps) if you want to minimize overhead—encrypt only applications handling sensitive data (banking, email, work tools) while everything else routes locally. A practical approach: enable kill switch and Net Shield on everything, then split tunnel only services that genuinely need local network access. This balances privacy, performance, and practical functionality. Test the configuration with your typical workflow to confirm nothing breaks.
Does Proton VPN keep logs that could identify my activity if requested by authorities?
Proton VPN operates under Switzerland's jurisdiction with privacy laws stronger than most countries. The company publishes annual transparency reports and has undergone third-party security audits confirming their no-logging claims. Proton's infrastructure is designed architecturally to avoid logging: VPN servers don't store connection records, IP assignments, bandwidth usage, or browsing history. However, no-logging claims require trust—you're ultimately trusting Proton's statement and audit results. For absolute certainty, some users combine Proton VPN with other privacy measures (Tor, proxies) to reduce reliance on any single provider. Proton's independent ownership and published audits provide stronger assurance than competitor VPNs owned by larger surveillance-vulnerable corporations, but perfect anonymity requires deeper technical analysis.
Is Proton VPN sufficient for complete online privacy, or do I need additional tools?
Proton VPN is excellent network-level privacy (hiding your traffic and location from network observers) but doesn't provide complete anonymity. Websites can still identify you through login credentials, browser fingerprinting, and behavioral patterns even with a VPN. Your ISP can't see your traffic, but Proton technically could (though their no-logging architecture should prevent collection). For complete privacy, combine Proton VPN with Tor for ultimate anonymity, use separate email identities for different services to prevent correlation, employ HTTPS everywhere, disable JavaScript in browsers, manage cookies carefully, and maintain awareness of digital footprints. Proton VPN handles the "hide from your ISP and network observers" layer well, but privacy is multifaceted requiring different tools for different threats.
How does Proton VPN's simultaneous feature support compare to other providers?
Most competitors support kill switch well, but simultaneous split tunneling + kill switch + threat filtering is uncommon. NordVPN supports split tunneling and kill switch together but has occasional conflicts with its DNS filtering feature. ExpressVPN skipped split tunneling entirely, prioritizing simplicity. CyberGhost supports simultaneous split tunneling and kill switch but lacks robust threat filtering. Mullvad supports simultaneous features well but doesn't include threat filtering. Proton's advantage: all three features integrated into a unified architecture that coordinates rather than conflicts. This is technically valuable—you get comprehensive protection without choosing between features. For users prioritizing simplicity over features, other VPNs might suffice. For users wanting maximum protection with local network flexibility, Proton's integration is genuinely superior.
What happens to my internet connection if Net Shield incorrectly blocks a legitimate site?
Net Shield returns a blocked page or null DNS response for dangerous domains, preventing the connection from establishing. If it incorrectly blocks something legitimate (false positive), you'll see an error page stating the domain is blocked. You can temporarily disable Net Shield to access the site, then report the false positive to Proton so they update their database. Proton typically corrects false positives within 24-48 hours based on manual review. Alternatively, some VPN apps allow whitelisting specific domains to override the block. The blocking is never permanent or unrecoverable—you always have options to access the site if you determine it's actually legitimate. False positives are rare (less than 1% of typical browsing) because Proton's blocking database is aggressively validated before deployment.
Conclusion: The Convergence That Changes Windows VPN Security
The simultaneous activation of split tunneling, kill switch, and Net Shield on Proton VPN for Windows represents more than a software update—it's the resolution of an architectural conflict that forced users to choose between security layers. For months, Windows users faced an impossible situation: enable comprehensive privacy at the cost of local network functionality, or preserve practical usability at the cost of security completeness. That false choice has ended.
What makes this convergence genuinely meaningful? It enables security that actually works with real-world infrastructure. The remote worker no longer disconnects from Proton VPN to print documents. The privacy-conscious traveler doesn't disable kill switch protection to use local peer-to-peer video calling. The developer testing geolocation-dependent applications doesn't sacrifice encryption to access local development servers. The organization deploying BYOD security policies can now protect corporate data while respecting employee workflows. The practical security model transforms from compromise-based to comprehensive.
The technical achievement underlying this simplicity shouldn't be overlooked. Proton's engineering team solved genuine architectural challenges in how Windows manages network filtering. They coordinated three independent subsystems—split tunneling routing, kill switch firewall rules, and DNS filtering—into a unified framework where each component understands the others' state and constraints. This coordination occurs at the kernel level where timing and state synchronization become extraordinarily complex. The fact that it works reliably across diverse Windows configurations (home networks, enterprise infrastructure, various driver versions, different network conditions) represents careful engineering that rarely gets recognition outside technical circles.
For professionals, organizations, and security-conscious users, this update fundamentally changes the security/functionality tradeoff. You're no longer choosing between protection and practicality. You're not sacrificing one security layer to enable another. Instead, you're implementing defense-in-depth where multiple protections operate in concert: encryption prevents network interception, split tunneling maintains practical functionality, kill switch prevents accidental leaks, Net Shield blocks malicious domains before they matter.
The protection you gain:
- Network privacy: Your ISP, network observers, and websites can't see your traffic or identify your location
- Functional flexibility: Local network services (printers, NAS, smart home devices) work seamlessly despite VPN encryption
- Leak prevention: Connection failures can't expose your real IP or create unencrypted windows
- Threat prevention: Malicious domains get blocked before your browser even attempts connection
This layered protection is particularly valuable for remote workers whose data determines their organization's security posture, for travelers crossing networks of varying trustworthiness, and for organizations scaling privacy infrastructure across employees without requiring them to become networking experts.
The performance cost remains acceptable. Yes, encryption and remote routing introduce latency. DNS lookups take longer. File transfers proceed slower. But these costs—typically 15-30% throughput reduction, 20-100ms latency increases—have become normalized in professional environments. The security benefit justifies the performance sacrifice. Organizations already accept this tradeoff when using HTTPS (universally encrypted web traffic despite overhead) and corporate VPNs (despite throughput cost). Proton VPN's overhead is similar or better, with the added advantage of simultaneous feature operation that was previously impossible.
For teams evaluating comprehensive security infrastructure, consider complementary automation tools like Runable to orchestrate VPN policy deployment and automate compliance verification across devices. Runable's AI-powered automation can manage Proton VPN configuration across teams, automate security compliance checks, and integrate VPN status into broader security workflows—turning manual VPN management into systematic, automated processes at just $9/month per user.
Looking forward, the implications of this fix extend beyond Proton VPN. It demonstrates that architectural conflicts aren't insurmountable limitations but engineering challenges requiring creative solutions. Other VPN providers facing similar split tunneling/kill switch conflicts now have a proven path to resolution. Users of competitor VPNs suffering from feature limitations can now demand similar fixes, knowing they're technically feasible.
As VPN technology matures, security features will increasingly need to coexist. The era of "choose one protection layer" is ending. The future belongs to VPN implementations that coordinate multiple protections intelligently, eliminating false choices between security and functionality. Proton's fix is a milestone on this path—not necessarily the destination, but unmistakably progress.
For Windows users seeking comprehensive privacy protection without sacrificing practical network functionality, this update transforms Proton VPN from a good option to a genuinely superior choice. The convergence of split tunneling, kill switch, and Net Shield finally enables the security model that users were demanding: protection that works with reality rather than against it.
Key Takeaways
- Proton VPN fixed Windows architectural conflict enabling split tunneling, kill switch, and NetShield simultaneous operation
- Split tunneling routes specific traffic through VPN while maintaining local network access for printers and devices
- Kill switch prevents data leaks by blocking all traffic if VPN connection drops unexpectedly
- NetShield provides network-level malware and phishing protection by blocking dangerous domains at DNS layer
- Performance impact is acceptable (15-30% throughput reduction, 20-100ms latency) for security benefit
- Proton VPN competes favorably with NordVPN, ExpressVPN, and alternatives with unique simultaneous feature support
- Configuration requires deliberate choices about which applications route through VPN versus local networks
- Remote workers, travelers, and organizations benefit most from comprehensive protection with practical functionality
- Alternative solutions like Runable can automate VPN policy deployment and compliance verification across teams
- Security is layered—these VPN features address network-level threats but complement rather than replace device security
Related Articles
- Flickr Data Breach 2025: What Was Stolen & How to Protect Yourself [2025]
- Digital Squatting: How Hackers Target Brand Domains [2025]
- Quishing: The QR Code Phishing Scam Taking Over [2025]
- Network Modernization for AI & Quantum Success [2025]
- CISA End-of-Life Edge Device Replacement Guide [2025]
- Best VPNs for Super Bowl LIX: Complete Streaming Guide 2025
![Proton VPN Windows Split Tunneling + Kill Switch: Complete Guide [2025]](https://tryrunable.com/blog/proton-vpn-windows-split-tunneling-kill-switch-complete-guid/image-1-1770653402162.jpg)



