Microsoft Office CVE-2026-21509 Security Flaw: What You Need to Know [2025]
Introduction: A Silent Threat in Your Office Suite
Last month, Microsoft did something it doesn't do often. It issued an emergency security patch outside of its normal Tuesday patch schedule. Not because of a theoretical vulnerability some researcher found in a lab. But because hackers were already actively exploiting a serious flaw in Microsoft Office. Real people, right now, were being targeted.
The vulnerability? It's tracked as CVE-2026-21509, and it's a security bypass that lets attackers do something pretty terrifying: they can execute malware on your computer by tricking Office into running code it shouldn't run at all. This isn't about stealing passwords or hijacking accounts. This is about someone potentially gaining complete control of your machine and everything on it.
What makes this different from the dozens of other Office vulnerabilities Microsoft patches every year is the active exploitation part. The US Cybersecurity and Infrastructure Security Agency (CISA) wasted no time adding this to its Known Exploited Vulnerabilities catalog, which means government agencies, critical infrastructure operators, and security teams are treating this as an immediate threat.
Here's what's critical to understand: if you're running Office 2021 or the Microsoft 365 subscription model, you likely got the patch automatically when Microsoft pushed it server-side. Restart your Office applications, and you're covered. But if you're still using Office 2016 or 2019 (and plenty of organizations still do), you need to take action today. Not tomorrow. Today.
This guide breaks down exactly what CVE-2026-21509 is, why it's dangerous, who's being targeted, and what you need to do right now to protect yourself. We'll walk through the patch process, discuss workarounds if you can't patch immediately, and explain what this vulnerability means for your organization's security posture going forward.

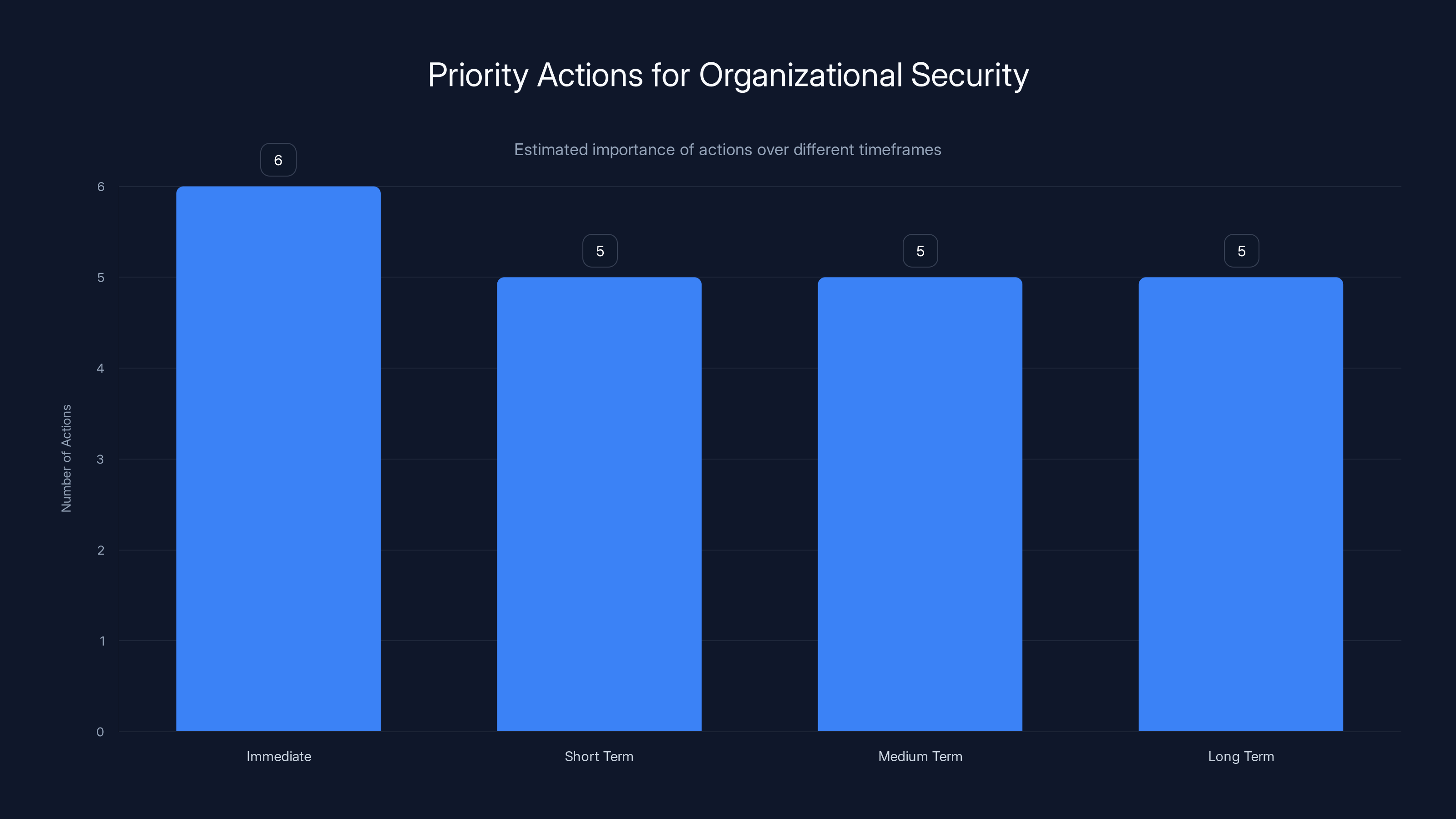
Immediate actions have the highest number of tasks, indicating a critical need for swift response. Estimated data based on task count.
TL; DR
- The Vulnerability: CVE-2026-21509 is a high-severity (7.8/10) security bypass in Microsoft Office that allows attackers to execute malware locally
- Active Exploitation: Hackers are already exploiting this in the wild, which is why Microsoft issued an emergency patch
- Who's Affected: Office 2016, Office 2019, and Microsoft 365 users—though 365 users got patched automatically
- What You Need to Do: Install the patch immediately for Office 2016/2019, or restart Office apps if using Office 2021/365
- The Real Risk: Attackers can bypass OLE mitigations, meaning malicious COM controls can run without restrictions, potentially giving them full system access
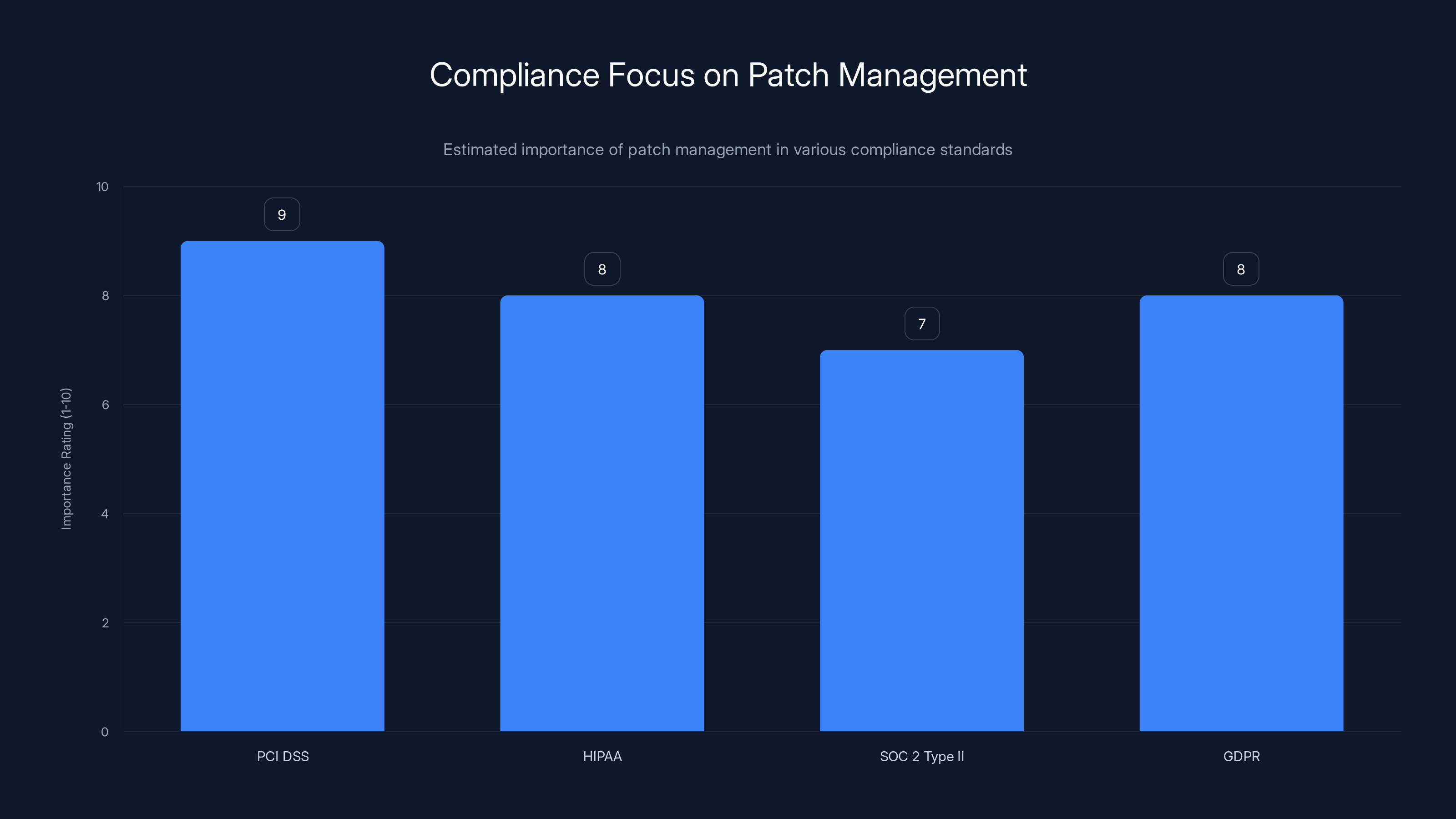
Estimated data shows that patch management is crucial across various compliance standards, with PCI DSS and GDPR placing significant emphasis on it.
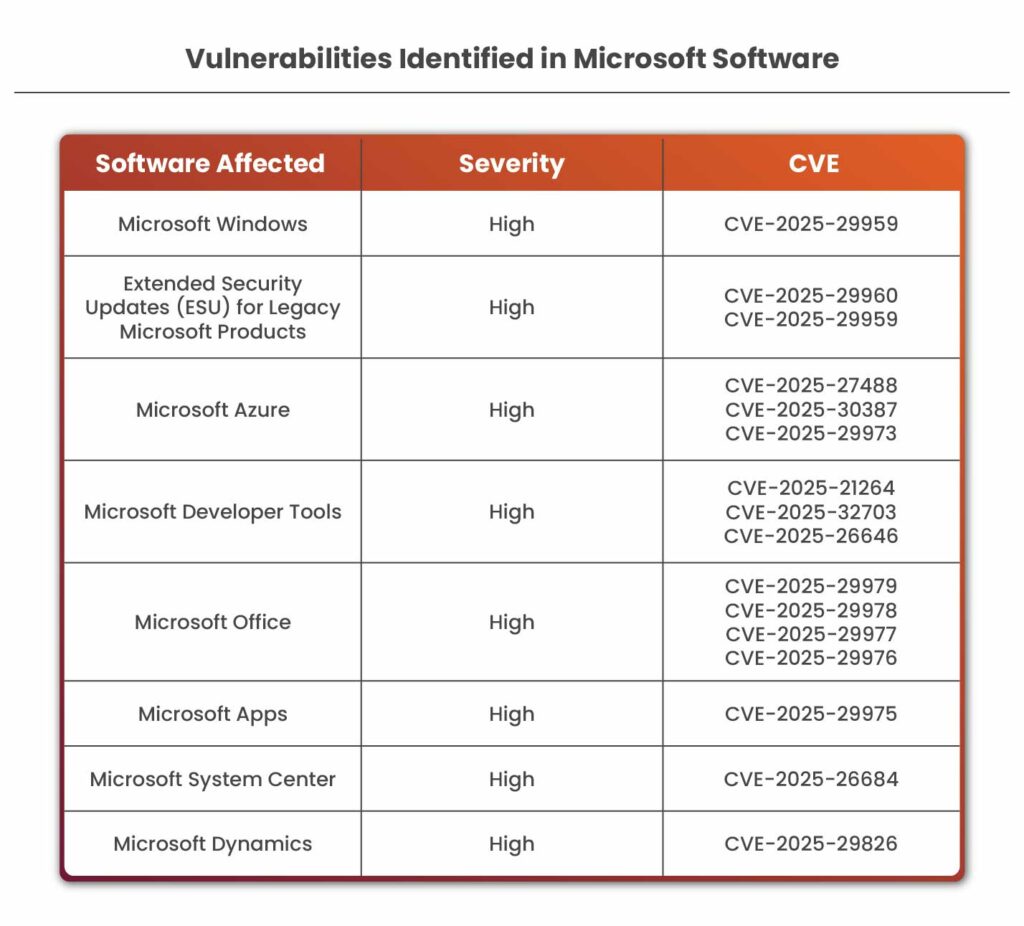
Understanding CVE-2026-21509: The Technical Breakdown
Okay, let's talk about what this vulnerability actually is, because the marketing speak from Microsoft doesn't really explain the danger clearly.
OLE stands for Object Linking and Embedding. It's a technology that's been part of Windows and Office for decades. The basic idea is solid: you can embed objects from one application into another. Embed a chart from Excel into a Word document. Embed a video into a presentation. It's a powerful feature that makes Office documents more interactive and useful.
The catch? OLE relies on COM controls, and COM controls are basically little pieces of code that can run on your system. Some of those COM controls are vulnerable. They have security holes. Microsoft knows this, so it built protections called OLE mitigations. These mitigations are supposed to block Office from loading dangerous COM controls.
But here's where CVE-2026-21509 comes in. This vulnerability is a bypass of those mitigations. Attackers found a way to trick Office into thinking a malicious COM control is safe when it isn't. It's like someone finding a backdoor in your security system and just walking in without triggering the alarm.
The severity score of 7.8 out of 10 puts this in the "high" category. It's not the absolute worst (those are 9.0+), but it's serious enough that Microsoft dropped everything and patched it outside the normal schedule. Why? Because the attack vector is local—meaning the attacker needs to get a malicious file onto your computer first, usually through email or a compromised website.
But here's the critical part: once that file is on your system, the attacker doesn't need any user interaction beyond opening a document. They don't need you to click "Enable Macros" or answer any security prompts. The vulnerability is triggered just by opening the file.
What's particularly nasty about this bypass is that it defeats the whole point of OLE mitigations. Microsoft spent years building protections against exactly this kind of attack. Defender Smart Screen tries to block suspicious files. Application Guard runs Office in a sandboxed environment on some systems. And OLE mitigations block dangerous COM controls from loading. This vulnerability bypasses one of those three layers, which means it increases the attack surface significantly.
From a technical standpoint, the vulnerability exists because Microsoft Office relied on untrusted inputs in a security decision. Translation: Office was making security choices based on information that wasn't properly validated. An attacker could manipulate that information to bypass the intended security controls.
The Active Exploitation Problem: Why This Matters Right Now
Let's be clear about something. Microsoft doesn't just patch every vulnerability the moment it finds it. They have a schedule, a process, a testing protocol. Patches go out on the second Tuesday of every month. It's predictable. It's controlled.
When Microsoft breaks that pattern and issues an emergency patch, it's because something bad is happening in the real world.
With CVE-2026-21509, that something bad is active exploitation. Attackers have already weaponized this vulnerability. They're not just theoretically able to exploit it in a lab environment. They're actually using it. Right now. Against real organizations.
CISA added this to its Known Exploited Vulnerabilities catalog within days of the patch release. CISA doesn't add things to that list based on speculation. They add them when there's confirmed evidence of exploitation. When the Federal government issues guidance telling all federal agencies to patch a vulnerability, you know it's serious.
Here's what we don't know: Microsoft hasn't disclosed who's being targeted, what the scope of the attacks is, or whether any data theft or ransomware deployment has already occurred. This information blackout is actually pretty typical for active exploits. Releasing details about who's vulnerable helps attackers refine their attacks. But it also means organizations are flying blind, not knowing if they're already compromised.
The exploitation details remain undisclosed, which is another sign of how serious this is treated. If Microsoft disclosed the exact technical steps needed to exploit the vulnerability, every attacker on the internet could immediately start using it. So they're keeping that information close, releasing it only to people with a legitimate need to know.
What we do know is that the attack vector is local. The attacker needs to get a malicious Office document onto your computer. They can do that through email, through a compromised website offering a "free template," through a USB drive, through file sharing services, or through any number of social engineering tactics. Once the file is there, opening it in Office is enough to trigger the vulnerability and execute malware.
That local attack vector means the threat is different depending on your environment. Home users? You're at risk if you open suspicious email attachments or download templates from untrusted sources. Enterprise organizations? Your risk profile is much higher because you have thousands or tens of thousands of people receiving email every day, any one of whom might accidentally open a malicious attachment.

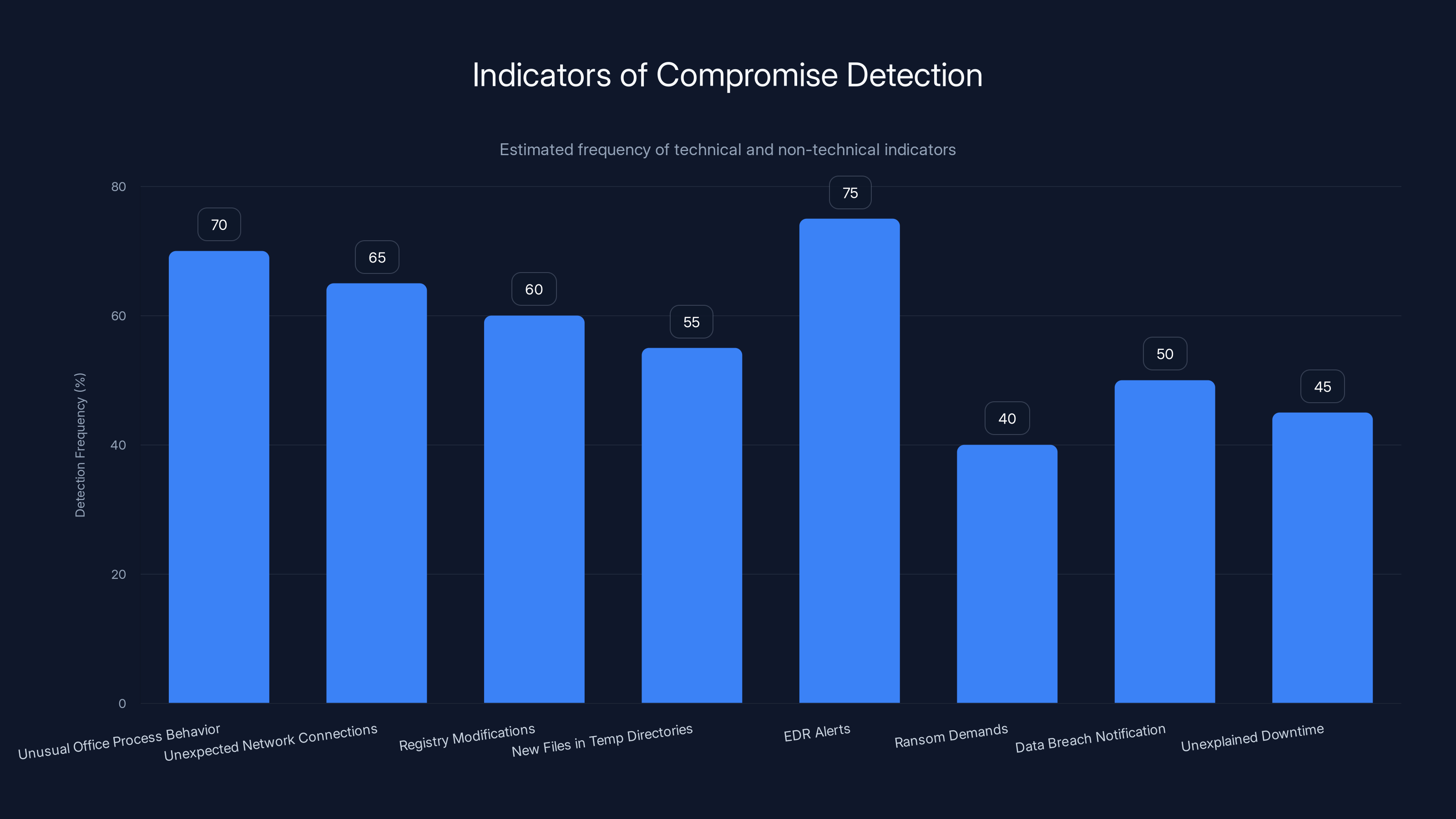
Technical indicators like EDR alerts and unusual Office behavior are more frequently detected than non-technical indicators like ransom demands. Estimated data based on typical detection scenarios.
Who's Actually at Risk? The User Matrix
Not everyone is equally at risk from CVE-2026-21509. The vulnerability affects different Office versions in different ways, and your risk level depends on several factors.
Microsoft 365 Subscribers (Lowest Risk)
If you're paying a subscription for Microsoft 365 (formerly Office 365), you're actually in the best position. Microsoft deployed the patch server-side, meaning the fix was deployed to their servers without requiring any action from you. You just need to restart your Office applications, and you're protected. If Office is running in the background constantly, you might already be patched without knowing it.
Why the difference? Because Microsoft 365 applications frequently update automatically from Microsoft's servers. They check for updates and install them in the background. The patch was deployed this way, which means subscribers got protected quickly without needing to know anything was wrong.
Office 2021 Users (Low Risk, But Action Required)
Office 2021 is the "perpetual" version that doesn't require a subscription, but it still gets critical security updates. If you're running Office 2021, you're not at immediate risk because Microsoft is actively patching this version. However, you do need to restart your Office applications to load the new patch. If you've had Office open for weeks without restarting, you're still running the vulnerable code.
Office 2019 Users (Moderate-High Risk)
Office 2019 is where the real vulnerability exposure exists. It's old enough that a lot of organizations still use it, but it's not getting the same level of support as Office 2021. If you're running Office 2019, you need to manually install patches. Microsoft released specific version numbers that include the fix, but getting those updates onto machines requires actual work. Organizations still running Office 2019 in 2025 likely have patch management processes, but there's always a gap between patch release and deployment.
Office 2016 Users (High Risk)
Office 2016 is ancient in software terms. It was released in 2015. Most organizations have migrated away from it. But plenty haven't. If you're running Office 2016, you're in a precarious situation. Microsoft still releases security patches for it, but support is winding down. You need to manually install the patch, and if your organization doesn't have a strong patch management process, you might stay vulnerable for months.
Older Versions (Not Directly Supported)
If you're somehow still running Office 2013 or older, you're not getting patched at all. Microsoft has ended support for these versions. You need to upgrade. Period. Not just because of this vulnerability, but because running unsupported software in 2025 is a security and compliance nightmare.
Industry-Specific Risk Factors
Some industries face higher risk from this vulnerability than others. Healthcare organizations that heavily use Office for patient documentation are a high-value target. Financial services firms using Office for transaction records and compliance documentation. Government agencies. Critical infrastructure operators. Any organization where a ransomware infection could cause significant disruption or data breach.
Small businesses and nonprofits aren't immune, but they're not typically the focus of sophisticated attack campaigns. Attackers usually go after high-value targets first. But smaller organizations are often easier to compromise because they have weaker security infrastructure.
The Technical Patch Path: Version Numbers and Installation
Let's get into the specifics of what you need to do. This is where the rubber meets the road.
For Office 2019 Users
If you're running Office 2019 32-bit edition, you need to update to version 16.0.10417.20095 or later. If you're running the 64-bit edition, same version number applies. You can check your current version by opening any Office application, clicking File, then Account, then checking "About [Application Name]." It'll show your current version.
How do you get the patch? You have a few options:
-
Windows Update: If you have Windows Update configured to install optional updates, it might download this automatically. Check Settings > Update & Security > Update History to see if it's already installed.
-
Microsoft Update: Enable Microsoft Update in Windows Update settings, and it will push Office patches along with Windows updates.
-
Manual Download: Go to Microsoft's Update page and manually download the appropriate patch for your version and architecture.
-
Office Update Directly: Open any Office application and go to File > Account > Update Options > Update Now.
The installation process is usually automatic once you've downloaded the patch. You might need to restart Office, but Windows will usually handle that without requiring a full system restart.
For Office 2016 Users
Office 2016 32-bit edition needs to be updated to version 16.0.5539.1001 or later. The 64-bit edition requires the same version number. The process is identical to Office 2019, but here's the catch: Office 2016 support is ending soon. Microsoft's mainstream support for Office 2016 ended in October 2020, and extended support ends in October 2025. If you're still running Office 2016 in late 2025, you're on borrowed time.
For Microsoft 365 Users
You don't need to do anything except restart Office. The patch is already deployed server-side. The next time you restart Word, Excel, Power Point, or Outlook, you'll be running the patched version. To force an immediate update, go to File > Account > Update Options > Update Now, but this usually isn't necessary because Office checks for updates frequently.
Verification Steps
After you've patched, verify that the patch actually installed correctly. Go to File > Account > Product Information, and check the version number. It should match or exceed the patched versions listed above. If it doesn't, the patch didn't install correctly and you need to try again.
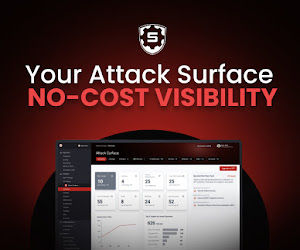
CVE-2026-21509 has a high severity score of 7.8, indicating significant risk, though not as critical as some other recent vulnerabilities.
The Mitigation Workaround: What to Do If You Can't Patch Immediately
Ideal world? Everyone patches immediately. Real world? Organizations have complex systems, legacy applications that break with updates, change management processes that slow down deployments, and sometimes patches cause more problems than they solve.
If you can't patch right away, Microsoft provides a registry-based mitigation. This doesn't fix the vulnerability, but it reduces your risk by blocking the attack vector.
The mitigation works by modifying Windows Registry settings to disable loading of untrusted COM controls in Office. It's not a perfect solution—it might break some legitimate Office functionality if your organization uses certain COM controls—but it's better than staying completely unpatched.
Microsoft's security advisory includes detailed step-by-step instructions for implementing this mitigation. The basic process involves:
- Opening Registry Editor (regedit.exe) with administrator privileges
- Navigating to a specific registry path
- Creating or modifying specific registry values
- Restarting Office applications
The exact registry changes are different for different Office versions, which is why you need to follow Microsoft's official guide rather than trying to improvise.
Important caveat: This mitigation should be temporary. It's a holding pattern until you can properly patch. Some Office features might break. Some legitimate add-ins might stop working. You're trading functionality for security, which is a reasonable short-term trade but not sustainable long-term.
For organizations using Group Policy to manage computers in an Active Directory environment, Microsoft also provides Group Policy templates that enforce this mitigation across hundreds or thousands of computers simultaneously. This is the preferred approach for enterprises because it's centrally managed and auditable.
Timeline Expectations
Small organizations with good patch management processes should deploy this patch within days. Medium-sized organizations typically take 1-2 weeks. Large enterprises with complex change management procedures might take 3-4 weeks. During this window, the mitigation provides a safety net.
If your organization can't patch within a month of the patch release, you have a much bigger problem than this one vulnerability. You have a broken security process.

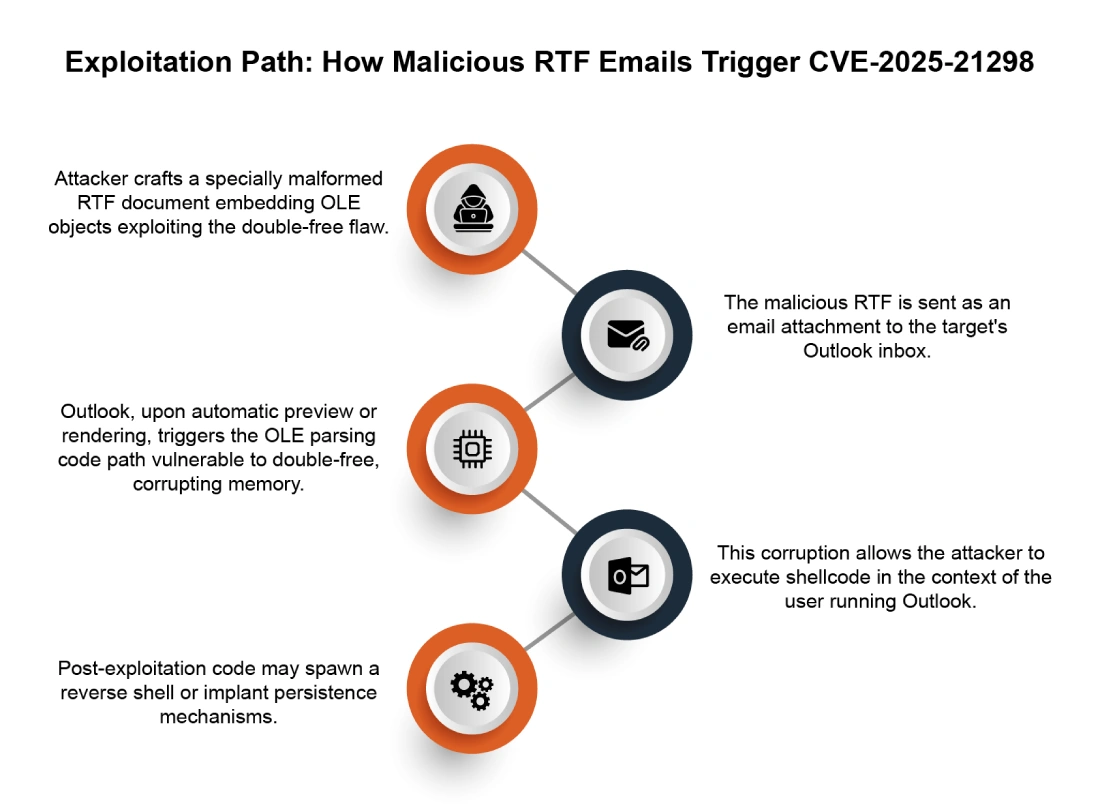
How This Vulnerability Was Likely Exploited: The Attack Chain
Understanding how attackers actually weaponized this vulnerability helps explain why it's so dangerous and why you need to take it seriously.
The attack probably starts with a social engineering email. It's not particularly sophisticated. It might be a spoofed message that looks like it comes from a colleague, a customer, or a trusted vendor. It might include a subject line designed to create urgency ("Updated Invoice," "Q4 Budget Report," "Important Client Documents").
The email includes an attachment: a seemingly innocuous Office document. Maybe a Word document. Maybe an Excel spreadsheet. Maybe a Power Point presentation. The file has a normal name and comes from a trusted-looking sender address.
When the recipient opens the document in Office, the vulnerability is triggered. The document contains a malicious OLE object—a COM control that, under normal circumstances, Office would block from loading. But because of CVE-2026-21509, Office doesn't block it. It loads the malicious control.
Once the malicious control runs, it has local code execution on the victim's computer. That's a computer where the user is logged in, where Office is running with the user's permissions, where the user has access to files and network resources.
From there, the attacker can:
- Deploy ransomware that encrypts all files on the computer and connected network shares
- Install malware like info-stealers that exfiltrate passwords and credentials
- Create backdoors that allow persistent access to the system
- Pivot to network using the compromised computer as a jumping-off point to attack other systems
- Steal data from the user's computer and the documents they have access to
The whole thing happens silently. The user doesn't see an error message. They don't see any indication that something went wrong. The document might display normally while the malicious code runs in the background.
This is why the "active exploitation" part of this vulnerability is so serious. It's not a theoretical attack. It's happening. Right now. Against real organizations. And they might not even know they've been compromised yet.

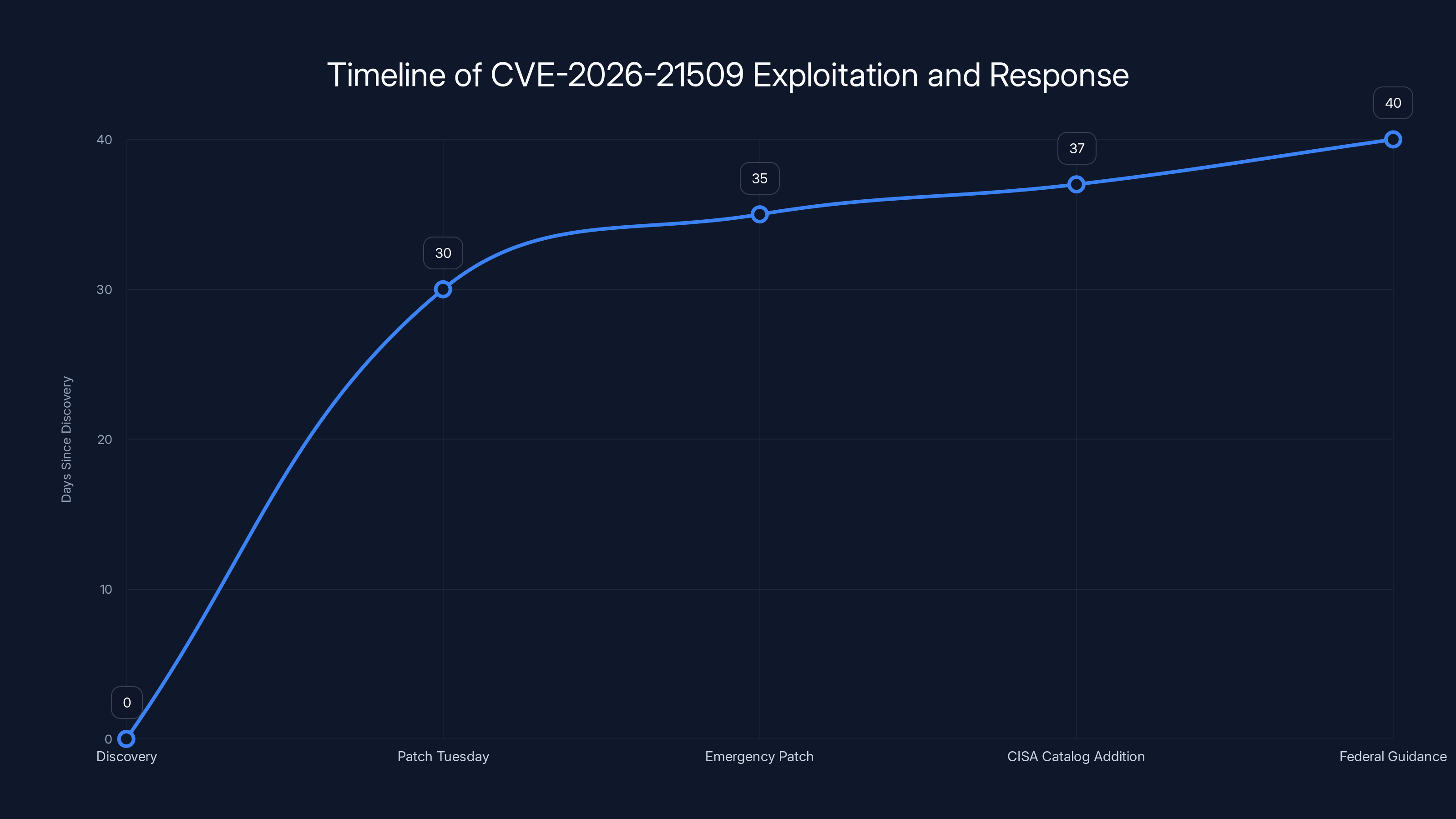
Estimated timeline shows rapid response from discovery to federal guidance within 40 days, highlighting the urgency of CVE-2026-21509 exploitation. Estimated data.
The Larger Security Context: OLE Has a History
OLE vulnerabilities aren't new. They're not even rare. They're a recurring problem that Microsoft has been dealing with for decades.
Why? Because OLE is fundamentally at odds with security. It's a feature that prioritizes functionality and integration over security. When you let objects from one application run code in another application, you inherit all the vulnerabilities from both applications.
Historically, OLE vulnerabilities have been exploited in some of the most sophisticated cyber attacks. The Fancy Bear attacks attributed to Russian intelligence used Office OLE exploits. The Wanna Cry ransomware used OLE vulnerabilities in older systems. The Equations Group, linked to NSA operations, used OLE vulnerabilities extensively.
Microsoft has tried to secure OLE multiple times. They added OLE mitigations. They added Defender Smart Screen checks. They added Application Guard sandboxing. They deprecated OLE in newer versions of Office.
But each time they add a new security layer, attackers find ways around it. Not because Microsoft is bad at security, but because OLE is fundamentally vulnerable. You're essentially running code from a source you don't control in an application that handles sensitive data.
The long-term solution is deprecation: removing OLE entirely from Office. Microsoft has been slowly moving in that direction, but it's a multi-year process because too many organizations depend on OLE for legitimate business purposes.
In the short term, patches like CVE-2026-21509 are the best we can do. Find the current vulnerability, patch it, and prepare for the next one.
Historical OLE Vulnerabilities
If you want to see how recurring this problem is, here are just a few notable OLE-related CVEs from recent years:
- CVE-2021-21224: An OLE automation vulnerability in Excel
- CVE-2020-1193: An Office memory corruption vulnerability related to OLE objects
- CVE-2019-1199: Another Office OLE automation vulnerability
- CVE-2017-8625: An OLE related vulnerability in Windows that affected multiple Office exploits
Each of these had patches. Each of these had a window where they were actively exploited. Each of these taught attackers something about how to bypass Office's security controls for the next exploitation attempt.
CVE-2026-21509 is just the latest in a long line. It won't be the last.
Enterprise Patch Management: The Real-World Challenges
Theoretically, patching is simple. Download update, install update, restart. In practice, especially for large organizations, it's incredibly complex.
Enterprise IT teams need to:
- Test the patch on a representative sample of their infrastructure to make sure it doesn't break business-critical applications
- Schedule the patch during maintenance windows that don't disrupt business operations
- Deploy the patch across potentially thousands of computers in a coordinated way
- Verify the patch was installed correctly on all systems
- Document the deployment for compliance purposes
- Handle exceptions for systems that break with the patch and need custom solutions
This process can take weeks even for a critical vulnerability. That's why the mitigation option is important—it gives organizations a way to reduce their risk while they're working through their patch management process.
For organizations using cloud-based Office (Microsoft 365), this is much simpler because Microsoft handles the patching. For organizations using perpetual versions (Office 2019, 2021), the process is more manual and more error-prone.
The Skills Gap Problem
Here's something else that complicates this: many smaller organizations don't have dedicated IT staff who understand patch management. They have a generalist who handles multiple roles. That person might be 80% occupied with user support, email management, and backup procedures. They're not spending 4 hours a day staying current with security vulnerabilities and patch management strategies.
These organizations are at higher risk, not because they don't care about security, but because they don't have the resources to respond quickly to emergencies like this.
This is exactly why cloud-based solutions like Microsoft 365 are attractive to smaller organizations. Not because the cloud is inherently more secure, but because it puts the responsibility for patch management on Microsoft rather than the organization's overwhelmed generalist.

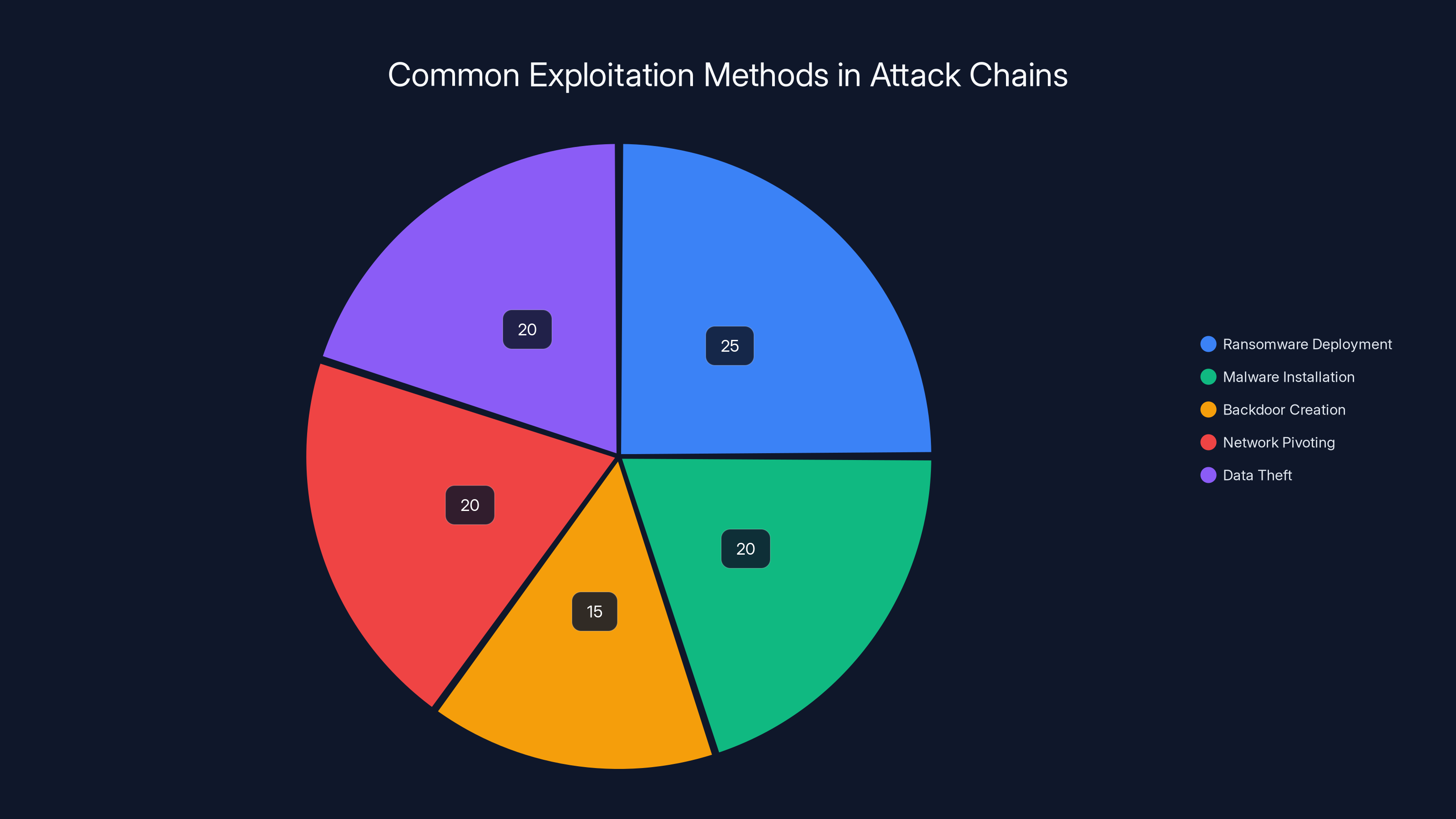
Estimated data shows that ransomware deployment and data theft are the most common methods in attack chains, each accounting for 20-25% of exploitation methods.
Detection and Incident Response: Knowing If You've Been Compromised
Let's address the uncomfortable reality: some organizations might already be compromised by CVE-2026-21509 and not know it yet.
Malware deployed through this vulnerability might sit dormant for days or weeks before it becomes active. The attacker might be using the compromised system to scout your network, identify valuable data, and plan a larger attack before actually stealing anything.
So how do you know if you've been compromised?
Technical Indicators
If your security team knows what to look for, there are some technical indicators:
- Unusual Office process behavior: Office applications spawning child processes they normally don't spawn
- Unexpected network connections: Outbound connections from Office applications to suspicious IP addresses
- Registry modifications: Changes to registry keys that control security settings
- New files in temporary directories: Suspicious executable files in Windows temp folders
- Endpoint Detection and Response (EDR) alerts: Modern EDR tools might flag the malicious COM control loading
But here's the catch: a sophisticated attacker might go to great lengths to hide this activity. They might use encrypted channels for command and control. They might only execute the attack during business hours when network traffic is high and anomalies harder to detect. They might focus on memory-only malware that leaves fewer artifacts on disk.
Non-Technical Indicators
Non-technical indicators are sometimes more useful:
- Ransom demands: If you receive a ransom note on your screen, congratulations, you've been compromised. Not really congratulations.
- Data breach notification: When attackers steal data, they often leak it or try to extort organizations. You'll find out from threat intelligence, news reports, or the attacker's ransom note.
- Unexplained downtime: If systems suddenly went offline or performance degraded sharply, that could indicate an active attack.
- User complaints: Sometimes users notice suspicious emails sent from their own accounts or accounts with names similar to theirs.
The Response Process
If you think you've been compromised, the incident response process should be:
- Isolate affected systems from the network immediately
- Contact your IT security team or external incident response firm
- Preserve evidence (don't reboot systems, don't delete logs)
- Notify relevant parties (CEO, board, legal, depending on severity)
- Begin forensic investigation to determine scope and impact
- Communicate with stakeholders (customers, regulators, insurance company)
- Implement remediation based on what the investigation reveals
This is exactly why security investments pay off. Every hour you save on incident response, every piece of evidence you successfully preserve, every gap in your network that doesn't exist because you implemented proper segmentation, all of these things matter when a breach happens.
Best Practices: Beyond Just Patching
Patching CVE-2026-21509 is necessary but not sufficient. It's one piece of a comprehensive security strategy.
Email Security
Most Office-based attacks come through email. So email security is critical:
- Enable sandboxing for email attachments, so potentially malicious files are detonated in a safe environment before they reach users
- Implement link rewriting so that URLs in emails are scanned when clicked, not just when received
- Use authentication protocols like DMARC, SPF, and DKIM to prevent spoofed emails
- Block dangerous file types at the email gateway (executable files, macros, etc.)
- Train users to recognize suspicious emails (this is unglamorous but statistically one of the most effective controls)
Application Hardening
Beyond just patching:
- Disable OLE entirely if your organization doesn't use it
- Disable macros by default and require explicit user approval to enable them
- Use Application Guard to sandbox Office in a virtual container, isolating it from the rest of the system
- Implement App Locker or similar application whitelisting to control what can run on systems
Network Segmentation
If an attacker does get in through Office, network segmentation limits what they can access:
- Separate critical systems (databases, file servers, backup systems) onto their own network segments
- Implement Zero Trust architecture where every connection is verified regardless of source
- Monitor network traffic to detect lateral movement attempts
Backup and Recovery
Ransomware often targets backups. Make sure yours are secure:
- Keep offline backups that can't be accessed by malware
- Test recovery procedures regularly to make sure backups actually work
- Monitor backup systems for suspicious access
- Use immutable backups that can't be modified or deleted
Logging and Monitoring
You can't defend against what you don't see:
- Enable logging for Office applications, Windows events, and network traffic
- Aggregate logs into a SIEM (Security Information and Event Management) system
- Create alerts for suspicious patterns (Office creating child processes, unusual file access, etc.)
- Review logs regularly looking for indicators of compromise

Compliance and Regulatory Considerations
If your organization operates in regulated industries (healthcare, financial services, government), there are specific compliance implications to consider.
PCI DSS (Payment Card Industry Data Security Standard)
If you process credit card payments, PCI DSS requires maintaining an up-to-date patch management process. Failing to patch known vulnerabilities is a compliance violation. If you get breached and it's discovered that you didn't patch a known vulnerability, your compliance status is revoked and fines are assessed.
HIPAA (Health Insurance Portability and Accountability Act)
Healthcare organizations operating under HIPAA must maintain comprehensive patch management programs and document their vulnerability management process. The same principle applies: failing to patch known vulnerabilities is a compliance violation.
SOC 2 Type II
If your organization is audited for SOC 2 compliance, auditors specifically look at patch management processes. They want to see evidence that critical patches are deployed within a documented timeframe.
GDPR and Data Protection Regulations
Under GDPR and similar regulations, you have a legal responsibility to protect personal data you hold. Failing to patch known vulnerabilities that could lead to a data breach is a failure to take appropriate technical measures, which is a regulatory violation.
The regulatory implication is simple: patch CVE-2026-21509 not just for security reasons, but for compliance reasons. Document when you patched it and how you verified the patch was successful.

Forward-Looking: What This Vulnerability Tells Us About Office Security
CVE-2026-21509 is one vulnerability. It will be patched. It will be forgotten. Until the next OLE vulnerability gets discovered.
This cycle suggests some uncomfortable truths about Office security:
OLE Is Fundamentally Vulnerable
Microsoft has been trying to secure OLE for decades. They've built layer after layer of mitigations. And attackers keep finding ways around them. At some point, the question becomes: why keep trying to patch a technology that's fundamentally at odds with security?
The answer is that too many organizations still depend on OLE for legitimate business purposes. Microsoft can't just remove it. They have to maintain backward compatibility. So we get patches instead of removal.
The Attack Surface Is Still Large
Even with this patch, Office still has a large attack surface. Macros can still be exploited. COM controls can still be vulnerable. Embedded objects can still contain malicious code. Any of these could be the basis for the next vulnerability.
Microsoft is slowly moving toward a more secure future (Power Point no longer allows macros by default, for example), but the process is glacial.
Patching Is Not a Complete Solution
This vulnerability makes clear that patching alone isn't sufficient. You need defense in depth. Email security. Endpoint detection and response. Network segmentation. Backup and recovery procedures. User training.
Patching is the foundation, but it's not the entire structure.
The Human Element Is Critical
No amount of patching prevents social engineering. If attackers can get users to open malicious documents, they've bypassed all the technical security controls.
The most effective security organizations invest heavily in user training and awareness. They create security cultures where employees understand that they're the first line of defense.
Microsoft's long-term strategy seems to be moving away from traditional Office entirely, toward web-based Office 365 applications that have smaller attack surfaces and can be updated instantly without user interaction. But that transition is still years away from being complete.
The Bigger Picture: Software Supply Chain Risk
CVE-2026-21509 also highlights a broader concern: software supply chain risk.
Microsoft Office isn't just some niche application. It's fundamental infrastructure for most organizations. Billions of people use it. When Office has a vulnerability, it affects a huge swath of the internet.
This creates incentives for attackers to focus on Office vulnerabilities. They know that every organization, in every industry, uses Office. They know that patching Office takes time. They know that some organizations won't patch for months.
For attackers, Office vulnerabilities are high-value targets because the attack surface is so large.
This raises questions about concentration of risk. When a single company's software is this critical to so much of the world's infrastructure, a vulnerability in that software affects everyone. There's no way to completely mitigate that risk as an individual organization. You're relying on Microsoft to patch vulnerabilities and patch them correctly.
Which is why the relationship between organizations and software vendors is becoming increasingly important. Microsoft's commitment to security, their speed in patching vulnerabilities, their transparency about security issues—all of these matter.
And when vendors are slow to patch, or when they minimize security issues, or when they hide vulnerabilities, it cascades across the entire ecosystem.

How to Stay Informed: Monitoring Security Vulnerabilities Going Forward
Okay, you've patched CVE-2026-21509. Now what? How do you stay on top of the next vulnerability?
CISA Alerts
CISA publishes alerts about vulnerabilities that are being actively exploited or that pose significant risk. Subscribe to their alerts at cisa.gov. They're free and they come directly from the agency responsible for cybersecurity in the US government.
Vendor Security Bulletins
Microsoft publishes security updates every month, and critical updates outside the normal cycle. Subscribe to Microsoft's security notifications or check their security update portal regularly.
Security News Aggregators
Websites like Krebs on Security, Ars Technica's security section, and The Verge's security coverage report on important vulnerabilities in accessible language.
Security Tools with Vulnerability Scanning
Vulnerability scanners like Nessus or Qualys automatically scan your infrastructure for known vulnerabilities. They check your systems against databases of known CVEs and report what you're vulnerable to.
Your Patch Management Tool
If your IT team uses a patch management tool (like Windows Server Update Services, Manage Engine Patch Manager Plus, or others), these tools include vulnerability tracking features.
Internal Communication
Most importantly, make sure your IT and security teams communicate vulnerabilities internally. A vulnerability doesn't matter if your development team finds out about it but your infrastructure team doesn't.

The Path Forward: What Organizations Should Do Now
Let's summarize what you actually need to do, in priority order:
Immediate (This Week)
- Check what Office versions your organization uses
- If using Office 2016 or 2019, verify your current version number
- Download and install the appropriate patch
- For Office 365/Microsoft 365 users, restart your applications
- Verify the patch installed correctly by checking version numbers
- If you can't patch immediately, implement the registry-based mitigation
Short Term (Next Month)
- Review your email security controls to prevent malicious Office documents from reaching users
- If you haven't disabled macros in Office by default, do that now
- Test your backup and recovery procedures to ensure they actually work
- Consider deploying Application Guard for sensitive Office users
- Review your incident response procedures
Medium Term (Next Quarter)
- Evaluate your patch management process—does it allow you to deploy critical patches within days?
- If not, upgrade your patch management infrastructure
- Consider migrating to Microsoft 365 if you're still running perpetual Office versions
- Implement or improve email sandbox scanning for attachments
- Conduct security awareness training focused on malicious email attachments
Long Term (Next Year)
- Plan to eventually move off Office entirely for non-essential use cases
- Implement Zero Trust network architecture
- Deploy endpoint detection and response tools
- Build out SIEM logging and monitoring infrastructure
- Establish relationships with incident response firms before you need them
This isn't just about CVE-2026-21509. This vulnerability is a symptom of broader security challenges. Addressing the immediate patch is important, but building a comprehensive security practice is what actually protects you.

FAQ
What exactly is CVE-2026-21509 and why should I care about it?
CVE-2026-21509 is a high-severity security vulnerability in Microsoft Office that allows attackers to execute malware on your computer. It's a security bypass that bypasses protections Microsoft built to prevent exactly this kind of attack. You should care because attackers are already exploiting it in real attacks, not just in theory. It affects multiple versions of Office and could put your data and systems at risk.
How did Microsoft discover this vulnerability and how long have attackers been exploiting it?
Microsoft doesn't typically disclose how vulnerabilities are discovered. CVE-2026-21509 was likely discovered either through their own internal security research, a bug bounty program, or external security researchers responsibly disclosing the issue. The active exploitation in the wild suggests attackers have been using this for at least some time before Microsoft patched it, though the exact timeline isn't public. Microsoft's rapid emergency response suggests the exploitation was significant enough to warrant breaking their normal patch schedule.
If I'm using Microsoft 365, do I need to do anything?
Not much. If you're using Microsoft 365 (the subscription version of Office), Microsoft deployed the patch server-side automatically. You just need to restart your Office applications to load the patched code. You don't need to manually install anything or run any patch processes. Just close and reopen Word, Excel, Power Point, or Outlook, and you're protected.
What about Office on Mac or Office on Linux?
CVE-2026-21509 affects Windows versions of Office primarily, as the vulnerability is related to COM controls which are a Windows technology. Microsoft Office on Mac and Libre Office on Linux don't have the same vulnerability, though they have their own separate security issues. If you're using Office on Mac, you should still apply security updates, but this particular vulnerability doesn't affect you.
Can I get more technical details about how to exploit this vulnerability?
No, and that's by design. Microsoft and CISA intentionally don't release detailed exploitation information for active zero-day vulnerabilities. If they did, every attacker on the internet could immediately start using it. The full technical details will probably be published months after the vulnerability is patched and most organizations have been updated, at which point the damage potential is much lower. This is called responsible disclosure and it's standard practice in the security industry.
What if I open a document that tries to exploit this vulnerability but I've already patched?
The patch prevents the vulnerability from being exploited. If you've installed the patch correctly, opening a malicious document won't execute the malicious code. The vulnerability is fixed. The document will just open normally (or fail to open if it's malformed). This is why patching is so important.
How do I know if I've been compromised by this vulnerability?
There's no foolproof way to know without doing a forensic investigation. If you're concerned you might be compromised, check for unusual system behavior: unexpected processes running, unusual network connections, files that appeared without explanation, or performance degradation. Better yet, have a professional security team scan your systems. They have tools and expertise to detect sophisticated compromise that normal users would miss. If you think you've been compromised, don't wait—get professional help.
Will disabling macros in Office prevent this attack?
Disabling macros helps, but it's not a complete solution. This particular vulnerability doesn't rely on macros—it exploits COM controls. So disabling macros helps protect against other Office attacks but won't stop CVE-2026-21509 specifically. That's why patching is so critical. But yes, you should disable macros by default anyway because they're the vector for so many other Office attacks.
Should I stop using Office until I can confirm I'm patched?
No. If you've already patched or applied the mitigation, continuing to use Office is fine. If you haven't patched yet and you're concerned, you could switch to web-based Office temporarily, or avoid opening Office documents from untrusted sources until you patch. But the practical reality is that Office is critical business software for most people, so the right move is to patch as quickly as possible and then resume normal use.
What's the difference between this vulnerability and the OLE vulnerabilities I've heard about in the past?
This is another OLE vulnerability. OLE is old technology that's been exploited repeatedly over the years. Each time Microsoft patches one OLE vulnerability, attackers find or develop ways around the fix, and the next OLE vulnerability is discovered. CVE-2026-21509 is just the latest in a long line. The fundamental problem is that OLE prioritizes functionality over security, which creates ongoing vulnerability. Microsoft's long-term strategy is deprecating OLE entirely, but that's a years-long process.

Conclusion: Patch Today, Not Tomorrow
CVE-2026-21509 is serious, but it's manageable. Microsoft released a patch. The patch works. Organizations and individuals can deploy it. The risk goes away.
But it only works if you actually patch.
If you're reading this and you haven't patched yet, stop. Close this article. Check your Office version. Install the patch. Restart your applications. Verify the patch installed. Then come back and finish reading if you want.
I'm serious. This isn't "patch when you get around to it" territory. This is "patch today" territory. Active exploitation means attackers are actively trying to compromise systems. Every day you wait is a day you're vulnerable.
For organizations: assign someone to verify that patches are deployed. Document that it was done. Check back next week to confirm no systems were missed. Budget time for this. It's not optional.
For home users: if you're running Office 2016 or 2019, download the patch and install it. If you're running Office 365, restart your applications. If you're using Word Online or other web-based Office, you're already patched.
After you patch, take a moment to think about the bigger picture. This vulnerability is one of dozens that will be disclosed this year. Patching is necessary but not sufficient. Consider your overall security posture. Do you have email security? Backup procedures? Incident response plans? User training?
Security isn't a sprint. It's a continuous process. CVE-2026-21509 is today's problem. Next month there will be another vulnerability. Next quarter, another. The organizations that stay secure are the ones that build robust, ongoing security practices.
But first: patch. Today.

Key Takeaways
- CVE-2026-21509 is a high-severity (7.8/10) security bypass in Microsoft Office being actively exploited by attackers to execute malware
- Office 2016 and 2019 users must manually install patches immediately; Office 365 users only need to restart applications
- Active exploitation means attackers are currently using this vulnerability against real organizations, making immediate patching critical
- Defense requires multiple layers: email security, application hardening, network segmentation, backups, and monitoring—not just patching
- Organizations without formal patch management processes face significantly higher risk and should prioritize establishing patching procedures
Related Articles
- Ingram Micro Ransomware Attack: 42,000 Affected, SafePay Claims Responsibility [2025]
- Grubhub Data Breach 2025: What Happened and How to Protect Yourself [2025]
- Major Shipping Platform Exposed Customer Data, Passwords: What Happened [2025]
- NordVPN Salesforce Breach Claim: What Really Happened [2025]
- Federal Cybersecurity Crisis: Why Government Digital Defense Is Collapsing [2025]
![Microsoft Office CVE-2026-21509 Security Flaw: What You Need to Know [2025]](https://tryrunable.com/blog/microsoft-office-cve-2026-21509-security-flaw-what-you-need-/image-1-1769535849687.jpg)



