The RAMP Takedown: How the FBI Dismantled a Major Cybercrime Hub
In early 2024, the FBI executed one of its most significant takedowns of underground cybercriminal infrastructure in years. RAMP, an infamous darknet forum that had operated since 2021, was seized across both clearnet and Tor network domains. The operation exposed what law enforcement had quietly been building: a comprehensive intelligence picture of one of the internet's most active criminal marketplaces.
What makes this takedown particularly significant isn't just the shutdown itself. It's what it reveals about how modern ransomware operations are organized, how cybercriminals communicate and collaborate, and the growing sophistication of federal law enforcement's approach to dismantling digital crime networks. One of RAMP's operators, posting under the alias "Stallman" on another forum called XSS, confirmed the seizure in a remarkably candid message: "This event has destroyed years of my work building the freest forum in the world."
That single statement encapsulates the problem cybercriminals now face. What they've built over years can disappear in hours. And more importantly, all the data they've accumulated—user identities, transaction records, communications, IP addresses—falls into law enforcement hands. For criminals who thought they were operating in the shadows, that's an existential threat.
But the RAMP seizure is more than just a single victory for law enforcement. It represents a fundamental shift in how the FBI and international partners are approaching cybercriminal infrastructure. They're not just arresting individual hackers anymore. They're identifying the platforms that enable criminal economies, mapping the relationships between operators, and dismantling entire ecosystems in coordinated strikes.
Understanding RAMP: What It Was and How It Functioned
RAMP didn't start as a massive criminal marketplace. It emerged in 2021 as a response to enforcement actions against other forums. When XSS and Exploit—two prominent hacking forums—banned ransomware-related content and hosting services, RAMP filled the gap. The forum's operators positioned it as the "freest forum in the world," a platform with minimal content moderation and maximum anonymity protections.
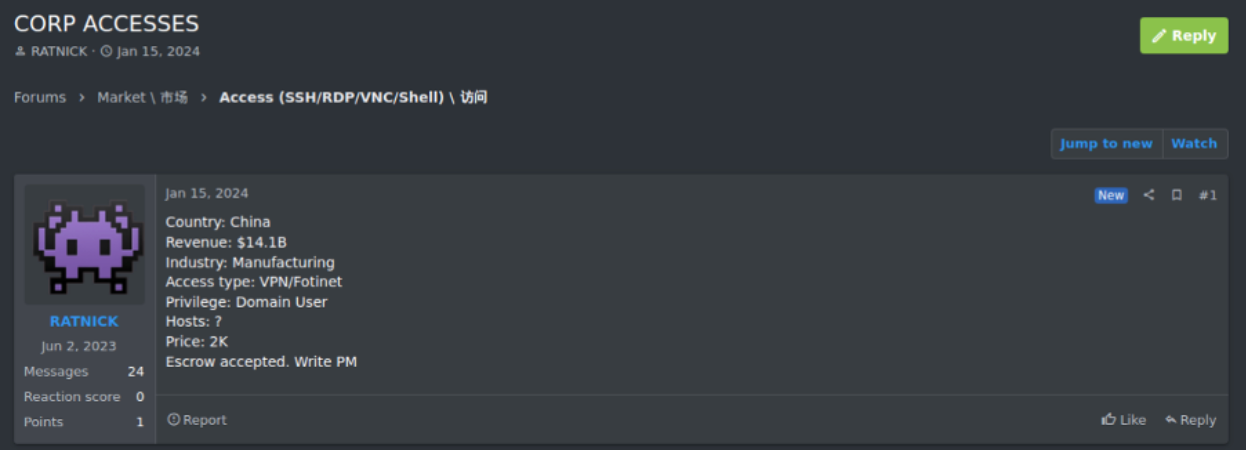
This positioning was deliberately different from early darknet marketplaces. RAMP wasn't primarily about buying and selling drugs or stolen goods, like Silk Road had been. Instead, it specialized in being a meeting place and service marketplace for professional cybercriminals. If you were a ransomware operator looking for initial access brokers—hackers who sell ways into corporate networks—RAMP was where you went. If you were developing malware and wanted feedback from experienced coders, RAMP had the community.
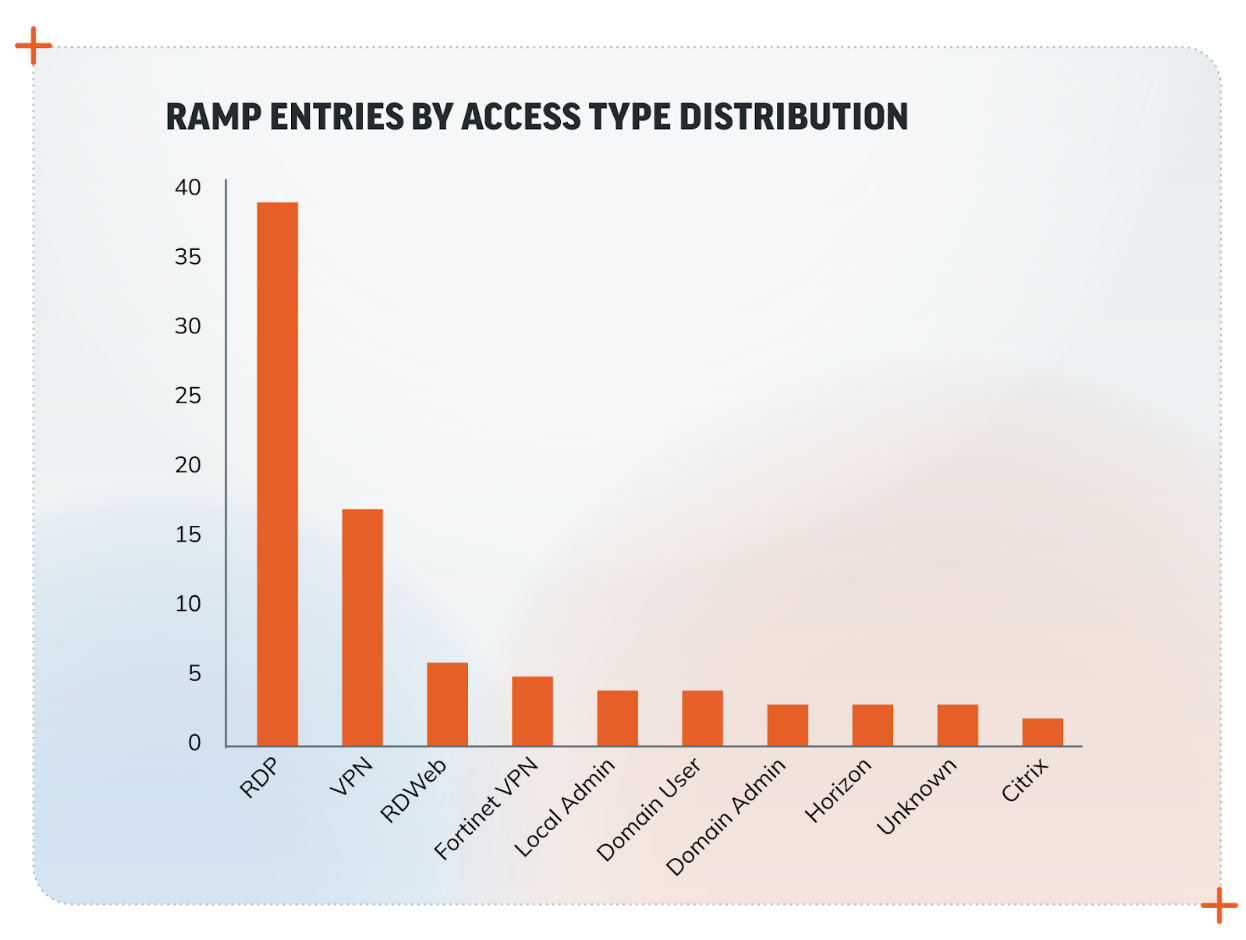
The forum operated two distinct presences simultaneously. The clearnet version (accessible via regular browsers) existed in a legal gray area, relying on hosting providers willing to tolerate its content. This version was primarily for reconnaissance and recruitment. The Tor version offered the enhanced privacy that serious cybercriminals demand. Users could browse listings for malware, hacking services, stolen data, and compromised credentials. Transactions typically occurred through cryptocurrency, offering further anonymity.
What differentiated RAMP from purely anarchic darknet markets was its infrastructure for trust and reputation. Like eBay or Amazon, the forum implemented seller ratings, escrow services, and dispute resolution mechanisms. This might seem contradictory—why would criminals use structured systems? The answer reveals something crucial about modern cybercrime: it's become industrialized. Professional ransomware gangs operate like businesses. They have supply chains, customer service, quality control, and reputational concerns. They need trust mechanisms to function effectively.
The forum's membership reportedly numbered in the thousands. Not all were sophisticated hackers—many were lower-level participants purchasing tools, asking for technical advice, or attempting to sell stolen information without possessing significant technical skills themselves. This breadth created both opportunity for law enforcement and operational risk for the criminals involved.

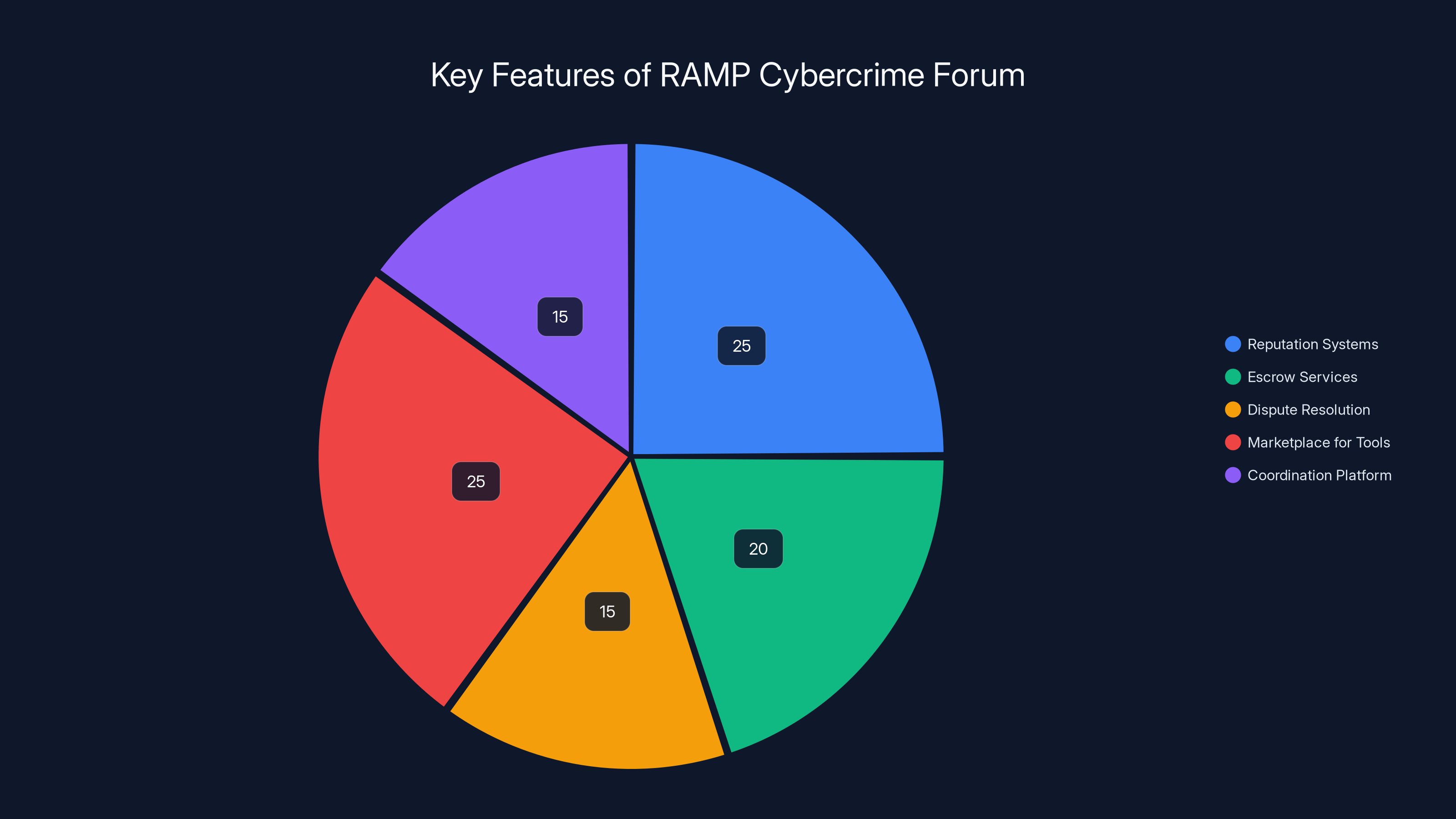
RAMP's infrastructure included reputation systems, escrow services, and dispute resolution, each playing a crucial role in facilitating cybercriminal activities. Estimated data.
How the FBI Gathered Intelligence on RAMP
Law enforcement agencies don't simply decide one day to seize a darknet forum. The RAMP takedown was the culmination of what likely took 18 to 24 months of investigation, intelligence gathering, and coordination between multiple agencies. Understanding how they actually pulled this off is critical to understanding modern cybercrime law enforcement.
The FBI's approach typically begins with informant networks. Someone on the inside—either a criminal seeking a reduced sentence, an undercover agent, or someone compromised through other investigations—provides initial intelligence. That tip might be something simple: "This person I know just joined RAMP using this username." From that single data point, investigators can map connections.
Cyber forensics specialists then examine the forum's technical infrastructure. RAMP operated on servers, and those servers had to be registered with domain registrars, hosted by providers, and connected to the internet. Each of these touchpoints leaves traces. Even on Tor, where traffic is encrypted and routed through multiple nodes, the actual servers still need to physically exist somewhere in the world. Finding those servers is painstaking but possible. Law enforcement has become skilled at identifying the actual hosting locations of darknet infrastructure by examining traffic patterns, timing, and other forensic indicators.
Once the servers were identified, investigators obtained warrants. In the case of the RAMP seizure, the warrant came from the U.S. Attorney's Office for the Southern District of Florida, in coordination with the Computer Crime and Intellectual Property Section (CCIPS) of the Department of Justice. These warrants authorize law enforcement to access the servers and extract data.
The intelligence gathering phase often involves some degree of infiltration. Law enforcement agencies place undercover agents or confidential informants into these forums. They establish reputation, participate in conversations, and document activity. This phase helps identify the most active participants, understand the forum's operations, and identify key targets for prosecution.
One aspect that often goes unnoticed is international coordination. The servers might be hosted in one country, the operators in another, and the victims in yet another. Extradition treaties, mutual legal assistance agreements, and intelligence sharing arrangements between countries all factor into the timeline. The RAMP seizure involved coordination with authorities in multiple countries, which typically delays operations but increases their effectiveness.
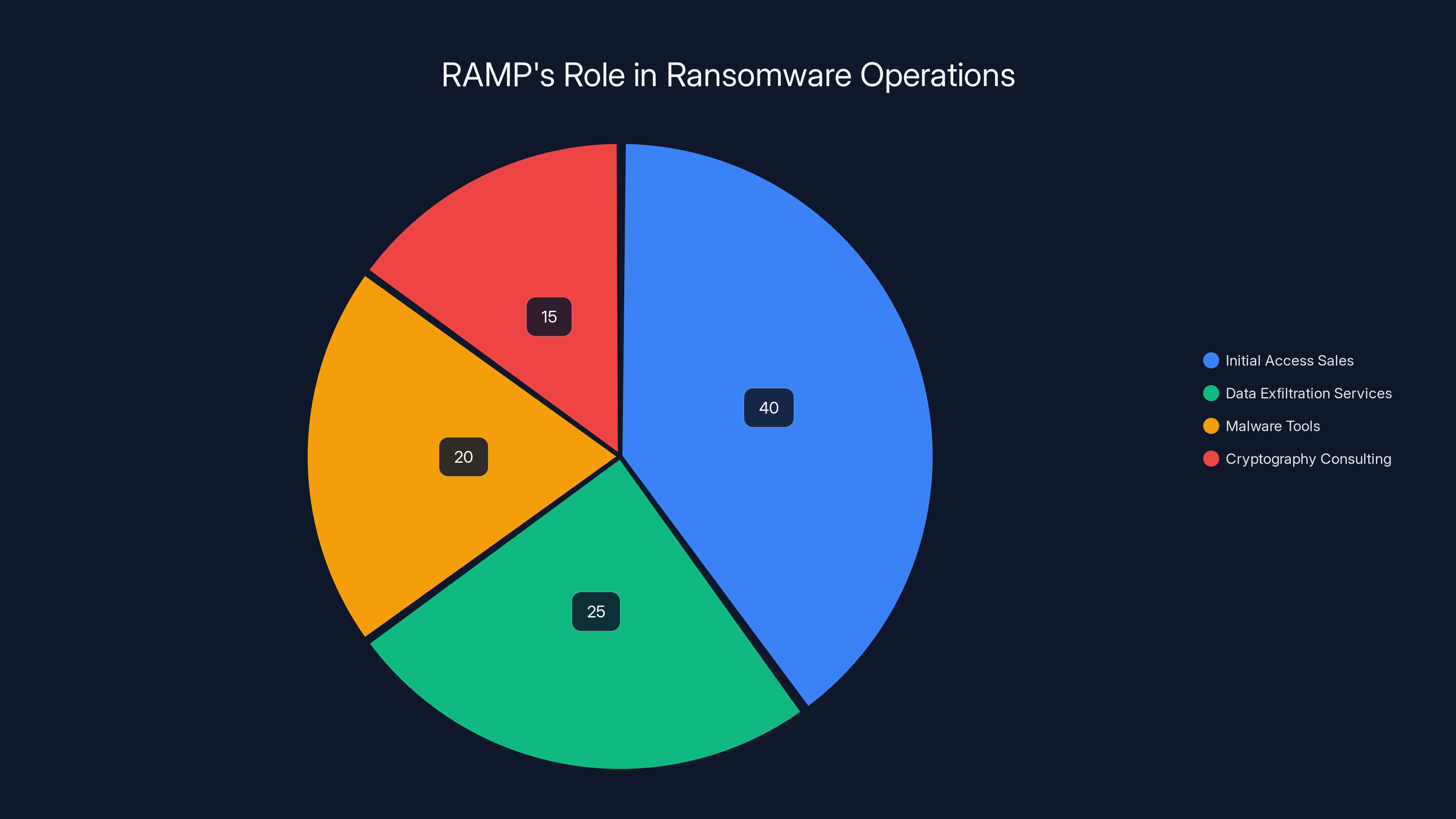
RAMP facilitated various activities in ransomware operations, with initial access sales being the most significant. Estimated data.
The Data Windfall: What the FBI Now Possesses
When federal agents took control of RAMP's servers, they inherited an unprecedented dataset of cybercriminal activity. This data represents months or years of evidence about how modern criminal networks operate. The implications are profound—and terrifying for the criminals involved.
The server databases likely contain user registration information, including email addresses used during signup. While many sophisticated criminals use temporary or anonymous email accounts, many don't. Investigators can cross-reference these email addresses with data breaches, financial records, and other law enforcement databases. A single careless signup email can unravel an entire pseudonymous identity.
IP address logs reveal where users actually connected from. While Tor obscures traffic, IP logs might reveal when users accessed the forum without Tor protection, or during periods when Tor circuits had technical issues. They might show which users accessed the forum from the same physical locations or network ranges, indicating group members or associates.
Private messages between users are perhaps the most valuable asset. Cybercriminals discussing jobs, sharing techniques, arranging transactions, or coordinating attacks leave detailed records. A private message thread between a ransomware operator and an initial access broker discussing a specific victim can become direct evidence of conspiracy. Payment records show transaction history, even if cryptocurrency was used—blockchain transactions are pseudonymous but traceable to anyone with the right technical skills.
Transaction data reveals relationships between users. If User A repeatedly buys services from User B, investigators can infer operational relationships. If User C regularly appears in disputes with User D, they might be competitors or failed partners. These relationship maps are valuable not just for identifying individuals, but for understanding how different criminal groups interact.
Forums also contain metadata beyond the obvious text content. File uploads have timestamps and sometimes metadata embedded within them. Posts are timestamped, allowing investigators to correlate RAMP activity with known attacks or breaches. A particularly valuable piece of intelligence is any correlation between forum activity and real-world incidents: "This user posted about compromising a specific company 3 hours before a ransom demand was sent to that company's CEO."
The exposure risk for forum members who weren't careful about anonymization is extreme. If someone used a username they've used elsewhere on the internet, investigators can potentially trace them. If someone posted in a timezone matching their home country, or used language patterns distinctive enough to be identified, they're exposed. Forum archives are now in the hands of the FBI, accessible to prosecutors, joint task forces, and international law enforcement partners.
Prosecuting RAMP Users: The Legal Path Forward
The seizure itself is just the beginning of the legal process. Federal prosecutors now face the challenge of translating a massive digital archive into prosecutable cases against specific individuals. This process takes years and requires specialized expertise in cybercrime law, evidence handling, and international cooperation.
The charge most likely to be leveled against RAMP operators and moderators is conspiracy in furtherance of computer fraud and abuse. This statute, codified under 18 U.S.C. section 1030, carries sentences up to 10 years per conspiracy count. If RAMP administrators knowingly facilitated ransomware attacks, additional charges become possible: wire fraud, money laundering, or—in the most serious cases—charges related to RICO (Racketeer Influenced and Corrupt Organizations).
RAMP was allegedly used to advertise and facilitate ransomware operations that targeted critical infrastructure. Some victims were hospitals, energy companies, or government entities. Those cases can trigger enhanced penalties and can result in charges related to critical infrastructure protection. If any victim died as a result of a ransomware attack (hospitals losing access to critical systems have in rare cases resulted in patient deaths), charges could escalate to include serious bodily injury or even involuntary manslaughter.
The challenge for prosecutors is establishing individual culpability. Participation in a darknet forum doesn't automatically equal criminal liability. Someone who simply lurked and read posts would be difficult to prosecute. Someone who sold a tool or offered advice would be easier. Someone who actively facilitated transactions, moderated the forum, or profited from admin fees is clearly culpable. Prosecutors will prioritize cases with the clearest evidence of active participation in criminal activity.
Expectations based on historical precedent suggest that some RAMP operators will eventually face prosecution. The operators of Silk Road, Alpha Bay, and other major darknet markets have been pursued, identified, and prosecuted—sometimes years after the markets were taken down. The data preserved by the FBI provides investigative leads that will fuel prosecutions for years. Some might occur in 2025 or 2026. Others might not come to fruition until 2027 or 2028.
International cooperation adds complexity but also increases chances of apprehension. If RAMP operators are Russian, Chinese, or from countries without extradition treaties with the U.S., prosecution becomes difficult. But many are from countries with strong law enforcement relationships with the U.S. or other Western nations. EUROPOL and law enforcement agencies in the UK, Germany, Netherlands, and other countries have become increasingly aggressive about pursuing cybercriminals. A Russian operator might evade U.S. prosecution but face charges in Estonia or Latvia.
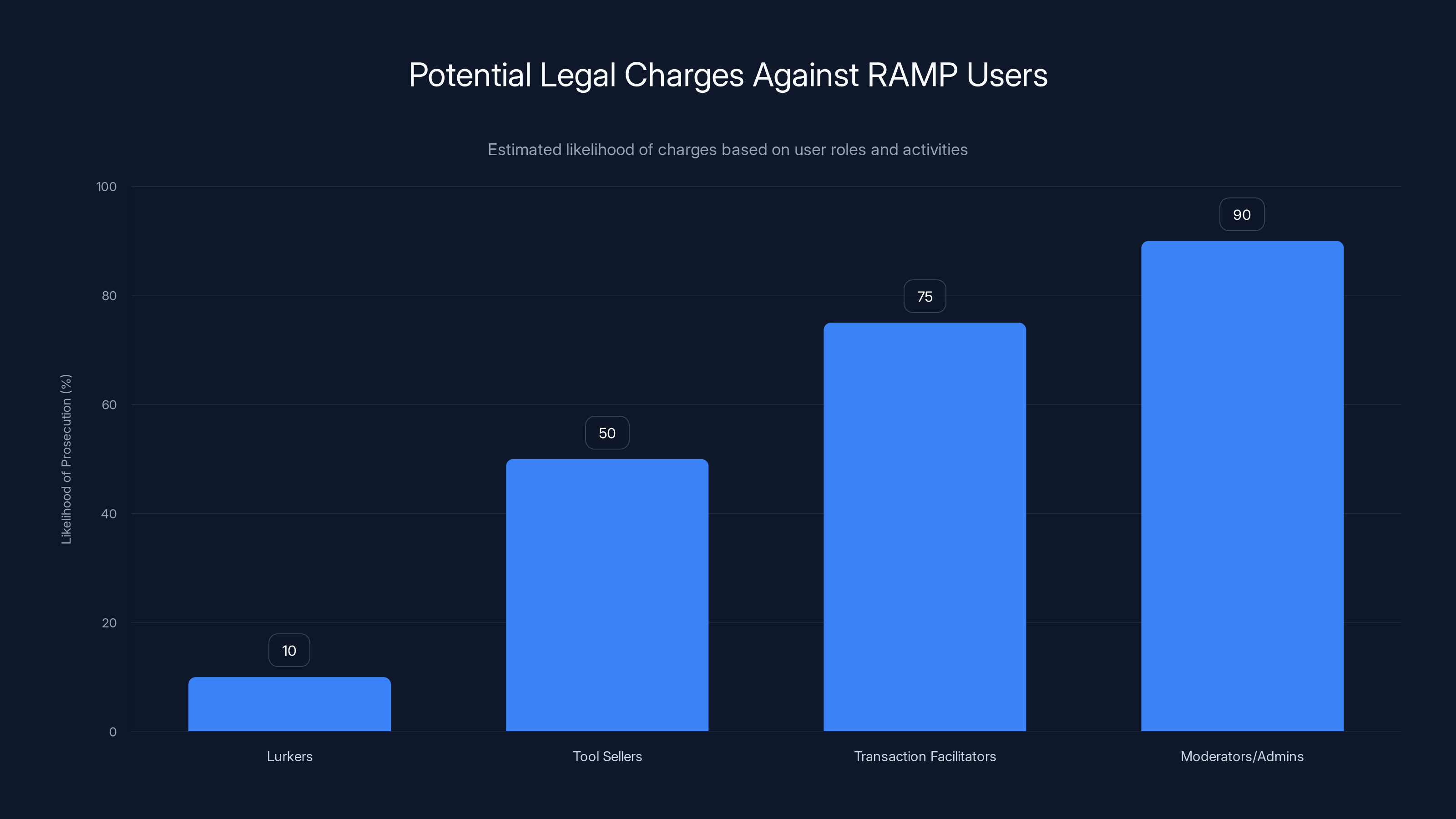
Estimated data shows that RAMP moderators/admins have the highest likelihood of prosecution due to clear evidence of active participation in criminal activities.
The Ransomware Connection: Why RAMP Mattered to Threat Actors
Understanding why RAMP was specifically important for ransomware operators requires understanding how ransomware campaigns actually work. Most people assume ransomware operates like a direct attack: hackers break into a network, encrypt files, and demand payment. The reality is far more complex and deliberately orchestrated.
A typical ransomware campaign involves multiple specialized groups operating on a supply chain model. The initial access broker is often a separate entity from the ransomware operator. Access brokers specialize in breaking into networks—they use phishing, exploit unpatched vulnerabilities, or abuse stolen credentials. Once inside, they either maintain access for future use or immediately sell that access to someone else.
RAMP was a primary marketplace where initial access brokers posted their wares. A typical listing might read: "Access to major manufacturing company's network. 500+ employees. Windows domain admin credentials included. $15,000 OBO." Ransomware operators would browse these listings, identify valuable targets, and make purchases. Payment was fast, reputation systems provided quality assurance, and disputes were mediated. It was eBay for crime.
Once a ransomware operator purchased access, they would spend days or weeks inside the victim's network, learning the environment and identifying the most valuable data. This reconnaissance phase is where the real money lives. Ransomware operators aren't interested in locking up files for a $50,000 ransom. They're interested in exfiltrating terabytes of sensitive data—medical records, financial information, trade secrets, personal information of customers—and threatening to sell or publish it unless the victim pays millions.
RAMP served as coordination point for this entire economy. Operators could hire data exfiltration specialists, purchase custom malware tools, contract with network cryptography experts, and consult with people who'd previously breached similar companies. Someone planning to attack a hospital system could post a question about the typical security posture of hospital networks and get answers from people who'd breached dozens of them.
The forum also provided crucial services for monetization. Converting cryptocurrency payments into usable funds requires money laundering infrastructure. While RAMP wasn't a financial service itself, it was a gathering place where money laundering specialists advertised their capabilities. The forum effectively connected every part of the ransomware value chain.

The Operator's Lament: Understanding the Criminal Perspective
When the alleged RAMP operator calling themselves "Stallman" posted their confirmation of the seizure, they included a poignant reflection: "This event has destroyed years of my work building the freest forum in the world." That statement deserves analysis because it reveals how cybercriminals think about their operations.
To Stallman, RAMP wasn't a criminal enterprise—it was a project, an achievement, a contribution to internet freedom. This perspective is common among certain cybercriminals, particularly those who view themselves as ideological actors rather than straightforward thieves. They genuinely believe they're providing valuable infrastructure for legitimate purposes—enabling speech, protecting privacy, resisting surveillance.
The obvious counterargument is that RAMP was explicitly used to facilitate ransomware attacks that caused measurable harm. Hospitals couldn't serve patients. Companies couldn't meet payroll. Families lost access to irreplaceable digital photos and documents. The financial costs of ransomware attacks exceed $30 billion annually, with RAMP directly implicated in facilitating a meaningful portion of that damage.
But Stallman's perspective matters because it explains the motivational profile of people building this infrastructure. They're not simply mercenaries looking for profit. Many genuinely believe they're building tools for freedom. They might rationalize that they're not responsible for how those tools are used, similar to how an arms manufacturer might claim they're not responsible for how weapons are used by purchasers.
This psychological frame has implications for law enforcement strategy. If you want to disrupt cybercriminal operations, simply arresting individual users isn't sufficient. You need to remove the infrastructure that enables the community. The RAMP seizure wasn't just about catching criminals—it was about pulling out the foundation they'd built.
Stallman's post also reveals an operational security failure. By confirming the seizure and mourning the loss in a public forum, Stallman revealed themselves as someone with direct administrative knowledge of RAMP. This post becomes evidence in any prosecution—an admission of operational involvement. This is a common pattern: even when criminals use sophisticated anonymization techniques, they sometimes undermine their own security through emotional responses to significant events.
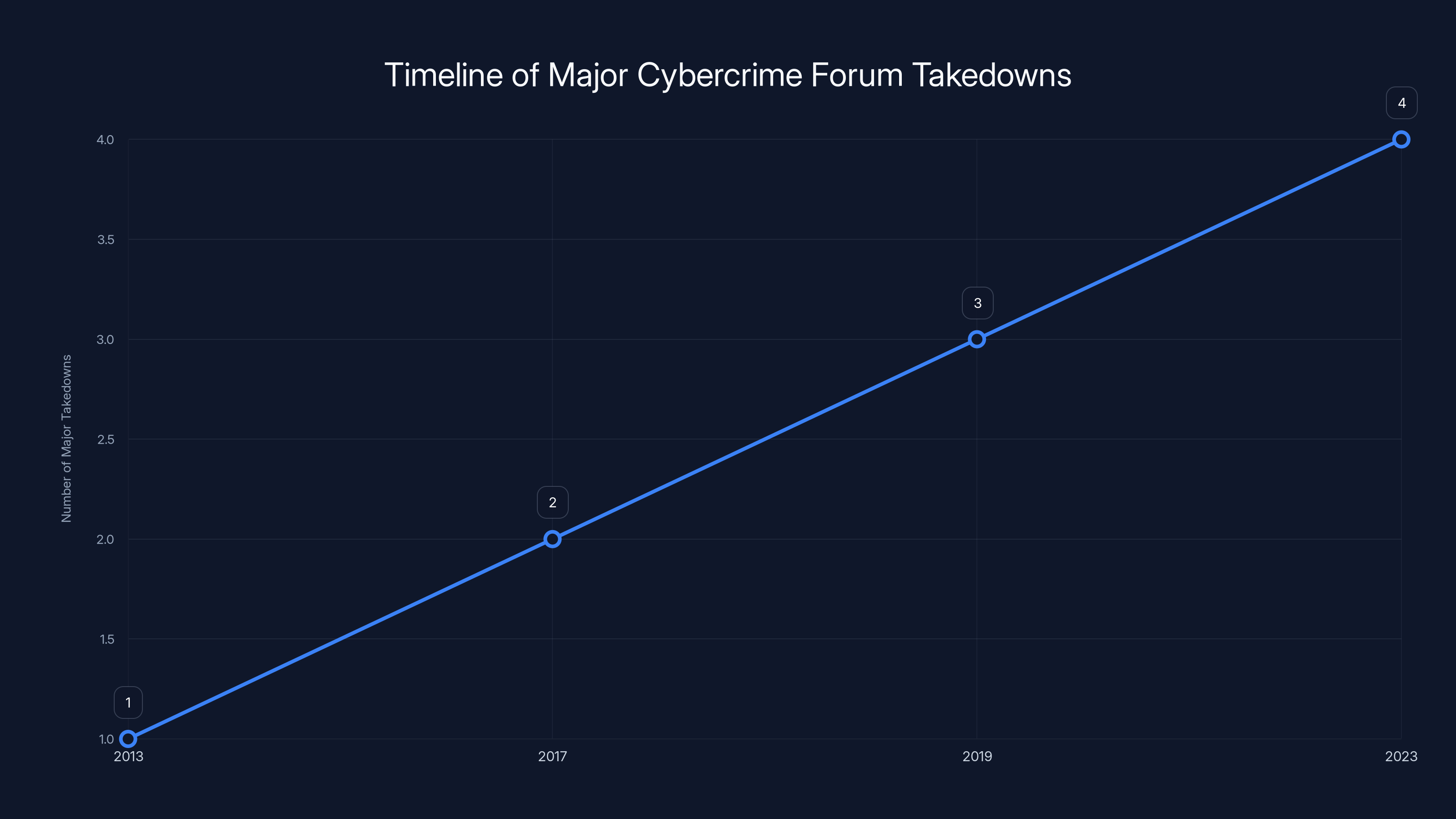
The timeline shows an increasing trend in the number of major cybercrime forum takedowns from 2013 to 2023, highlighting the growing sophistication and coordination of law enforcement efforts. (Estimated data)
Lessons from Previous Forum Takedowns
The RAMP seizure isn't the first major cybercrime forum disruption, and historical precedent provides insights into what typically happens after such operations. Law enforcement has learned from previous takedowns, and each successive operation becomes more sophisticated.
Silk Road's shutdown in 2013 demonstrated that even supposedly secure darknet markets could be penetrated and dismantled. FBI agent Jay Grajski successfully identified founder Ross Ulbricht, leading to his arrest and conviction. The seizure of Silk Road's data led to prosecutions spanning over a decade as investigators worked through the massive database of transactions and user information.
Alpha Bay's shutdown in 2017 involved coordination between multiple countries and resulted in the arrest of its administrator, Alexander Cazes. Law enforcement learned from that operation that international coordination significantly increased the probability of successfully identifying and apprehending forum operators.
Wall Street Market's seizure in 2019 was noteworthy because it revealed just how much data could be extracted from forum servers. Over 500 gigabytes of data was seized, containing user information, transaction records, and communications. That data has fueled investigations and prosecutions ever since.
The pattern that emerges from these precedents is clear: forum operators cannot remain anonymous indefinitely. Eventually, investigative techniques identify them. They're arrested, prosecuted, and sometimes convicted. But the process takes years. In the meantime, operators who recognize the risk begin moving to alternative platforms or developing new forums.
One concerning trend is that new forums emerge faster than old ones are dismantled. When Silk Road was shut down, Alpha Bay and other platforms filled the gap within weeks. When Alpha Bay was seized, successor platforms emerged. This hydra effect means that law enforcement victories against specific forums are important but ultimately insufficient without broader strategy changes.
The Infrastructure Behind the Seizure: Technical Execution
Executing a forum seizure involves technical complexity that often goes unappreciated in news reports. Law enforcement agencies must precisely coordinate to take control of servers, preserve evidence, and prevent criminals from deleting data or moving operations.
The initial step involves locating physical servers. RAMP's clearnet domain was likely hosted with a bulletproof hosting provider—companies that specialize in hosting content that mainstream providers ban. These providers often operate in countries with weak law enforcement relationships with the U.S., or have owners directly connected to criminal organizations. Locating such servers requires international cooperation and sometimes involves law enforcement reaching out to hosting providers in friendly countries.
Once located, law enforcement obtains warrants that authorize them to take control of the servers. This is typically done through a coordinated action. All servers are accessed simultaneously to prevent the person managing RAMP from noticing the seizure on one server and immediately scrubbing or moving others.
The moment agents take control, they deploy legal notices. The defaced pages seen on RAMP's clearnet domain—the FBI seizure notices—are those legal requirements in action. These notices inform users that the domain has been seized and that accessing the forum might result in criminal liability.
Preserving evidence from the servers is critical. Investigators use forensic imaging techniques to create bit-for-bit copies of hard drives, maintaining the integrity of the evidence for potential trials. They document metadata about when data was stored, when it was modified, and in what order. All of this becomes important if a case goes to trial and defense attorneys challenge the authenticity or integrity of digital evidence.
The Tor domain presents additional challenges. Tor hidden services don't need to be hosted in specific countries the way clearnet domains do. However, they still require server infrastructure. The FBI eventually revealed Tor address information and took control of those services as well. This likely involved sophisticated technical work to identify the actual servers providing the Tor service.
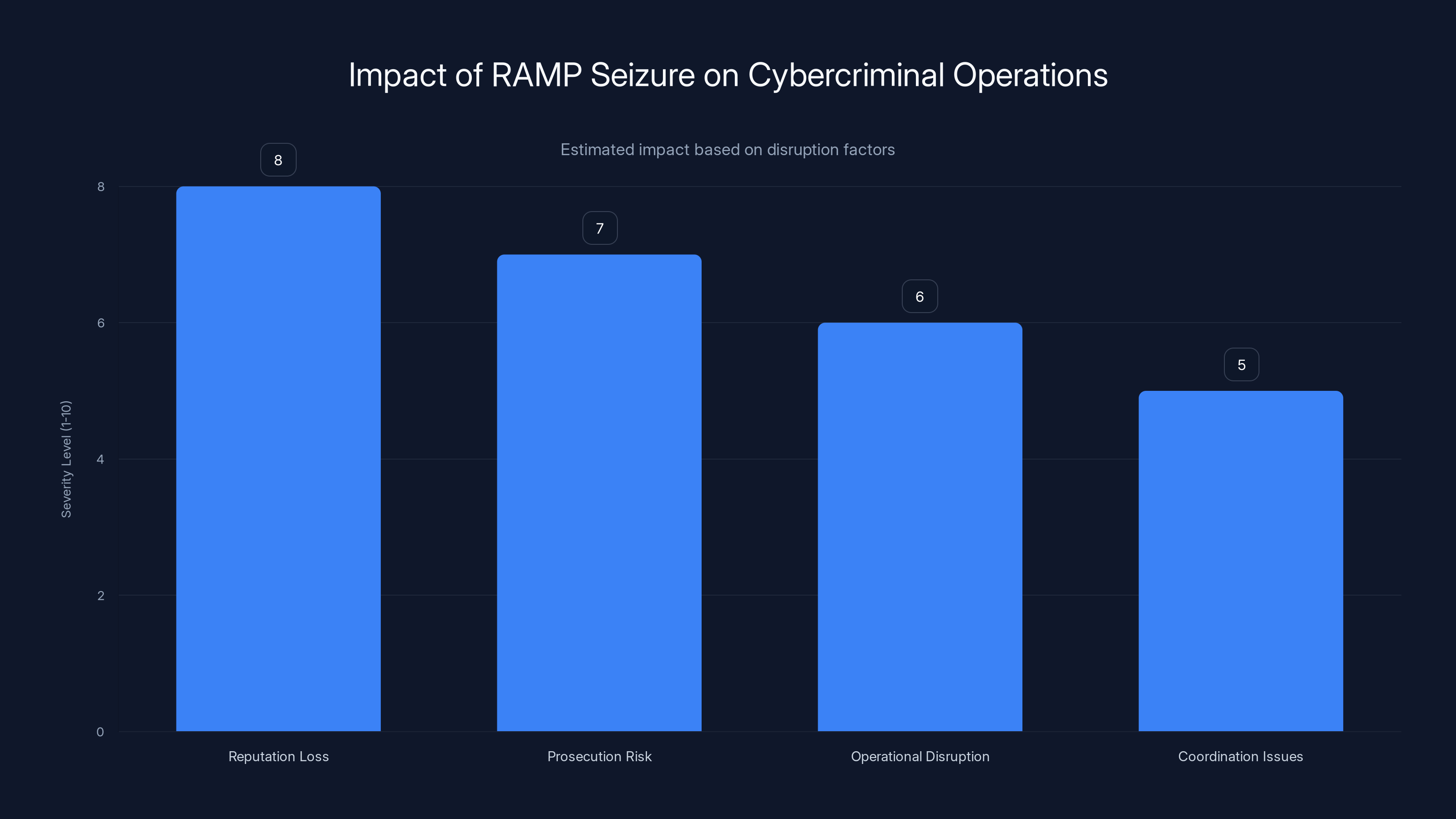
The seizure of RAMP significantly impacted cybercriminal operations, with reputation loss being the most severe consequence. Estimated data based on narrative insights.
Impact on Cybercriminal Operations: The Cascading Effects
When RAMP was seized, the immediate impact was disruption—criminals lost access to a familiar platform where they'd built reputation and relationships. But the cascading effects have been more significant than just inconvenience.
First, the loss of reputation is substantial. A user who'd spent months or years building a positive rating on RAMP can't instantly transfer that reputation to alternative platforms. New forums don't recognize RAMP reputation scores. A user forced to start over on a different platform is treated as an unknown entity. This dramatically reduces their ability to command high prices for services or goods, and makes it harder for legitimate customers (from the criminals' perspective) to trust them.
Second, the capture of user data creates perpetual prosecution risk. Even if an individual criminal successfully moves to alternative platforms, law enforcement now has their email address, IP addresses, transaction history, and private communications. Prosecutors can use this information to build cases that take years to mature. The psychological effect is significant—every seized forum reinforces the message that law enforcement is building cases against users that might not come to fruition for years.
Third, the seizure disrupts ongoing operations. Ransomware campaigns in development might have been coordinated through RAMP private messages. Access to those messages is now gone, and criminals don't know if law enforcement has read them. This uncertainty creates operational friction. Criminals begin assuming their communications were compromised.
Fourth, the seizure creates a coordination problem for the criminal ecosystem. RAMP wasn't just a marketplace—it was a trust layer that enabled transactions between strangers. When an initial access broker in Russia wants to sell network access to a ransomware operator in Romania, they need some mechanism to ensure fair dealing. RAMP provided that. Alternative platforms exist, but switching to a new platform requires network-building effort and introduces trust concerns.
Fifth, the data windfall improves law enforcement's broader intelligence picture. Investigators can now analyze patterns of how ransomware campaigns are planned and executed. They can identify common cryptocurrencies used for payments. They can map relationships between users. All of this intelligence improves their ability to disrupt future criminal activity.

Ransomware Gangs' Response: Adaptation and Evolution
Historically, cybercriminal groups have proven remarkably adaptable. When their tools are blocked, they develop new ones. When their platforms are seized, they migrate to alternatives. The RAMP seizure hasn't stopped ransomware operations—but it has forced adaptation.
Many ransomware groups have migrated to existing platforms like XSS (the forum where Stallman made their announcement). XSS existed before RAMP was seized, and it continues operating. Some groups have built their own private communication infrastructure, using encrypted messaging apps and private servers rather than public forums. This increases operational security but reduces the efficiency of dealing with the open market.
Some ransomware operators have implemented more aggressive strategies to protect their organizational knowledge. Rather than relying on forums for coordination, leading groups like Lock Bit and Black Cat operate with core teams of trusted members. They recruit through invitation only rather than building public reputations. This reduces the attack surface that law enforcement can exploit.
There's also a concerning development: forums becoming more private and exclusive. Rather than public marketplaces like RAMP, newer platforms restrict membership based on demonstrated experience or reputation on predecessor forums. This creates a barrier to entry that might actually benefit established criminal groups while reducing the "supply" of low-level criminals entering the ecosystem.
Another adaptation involves using legitimate infrastructure for coordination. Some groups use encrypted messaging apps like Telegram or Signal, hosted on legitimate platforms they can't directly seize. This requires more operational discipline (anyone talking too openly about crimes in a Telegram group risks exposure) but provides better resilience against law enforcement.

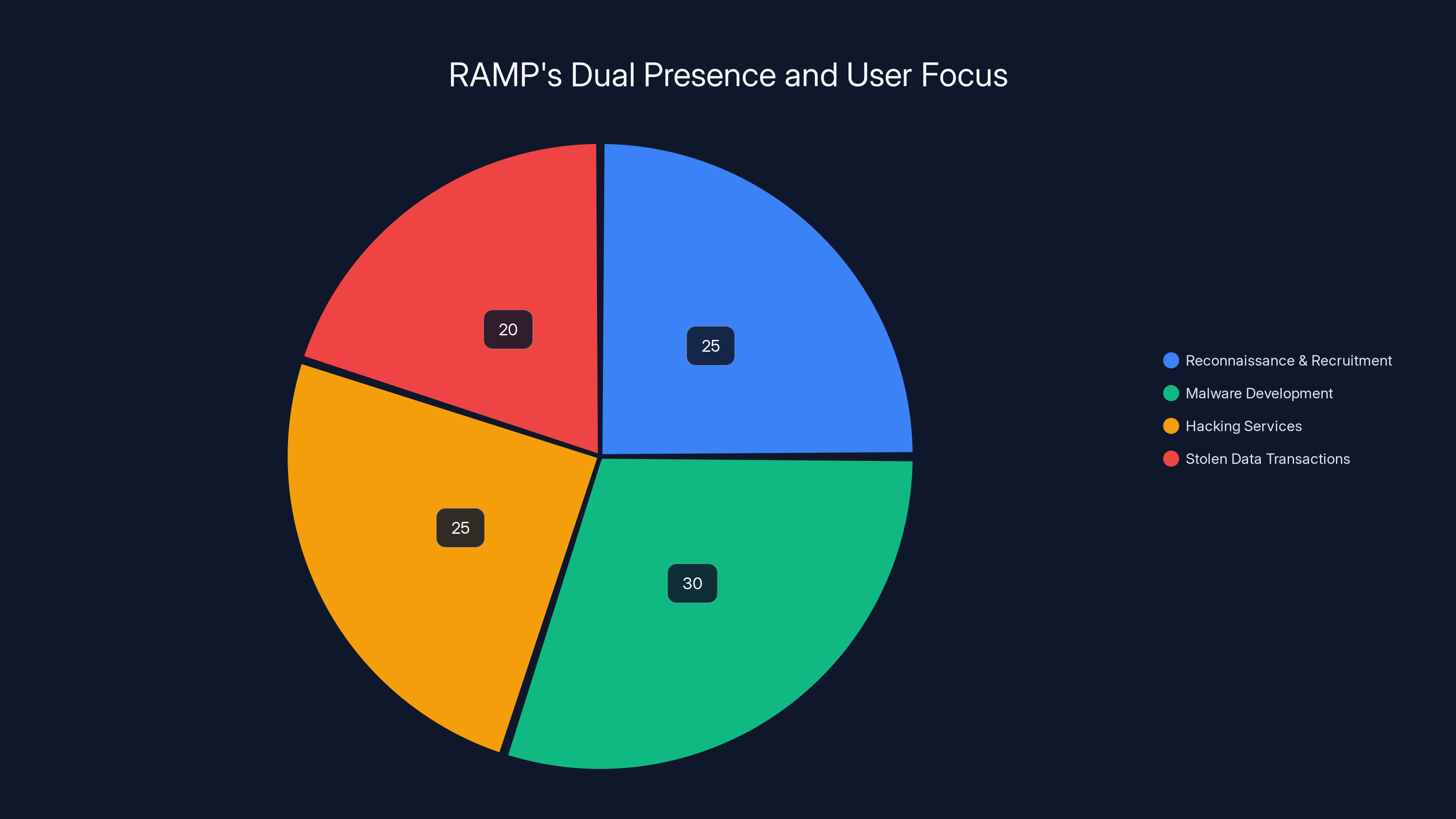
RAMP's user activities were distributed across reconnaissance, malware development, hacking services, and stolen data transactions, reflecting its role as a professional cybercriminal marketplace. (Estimated data)
Detection and Attribution: Connecting Operations to RAMP
Understanding which ransomware attacks were facilitated through RAMP requires investigating the connections between criminals and the forum. Security researchers have begun that work, analyzing forum posts and correlating them with known attack campaigns.
One method involves analyzing timestamps. If a particular access was posted on RAMP on July 15 at 2:00 AM UTC, and a company was breached on July 16 at 3:00 AM UTC with indicators matching that access listing, the connection is likely. Researchers can search through forensic logs from victim networks for signs that attackers were in the system during or after the posting date.
Another method involves linguistic analysis. Forum usernames, writing styles, and patterns of communication in private messages sometimes match the writing found in ransom notes or communications with victims. A researcher familiar with a particular gang's communication patterns might recognize similar phrasing or structure in RAMP posts.
Cybersecurity researchers have also published analyses of RAMP data shared by journalists and law enforcement. These analyses track which gangs were most active on the platform and attempt to estimate their activity levels. One published report estimated that RAMP contained thousands of initial access offerings per year, with an estimated value in the hundreds of millions of dollars.
The intelligence value of RAMP data extends beyond specific cases. Law enforcement can analyze trends in ransomware tactics, identify emerging vulnerabilities being exploited, and predict future attack vectors. If RAMP data shows an sudden increase in posts about exploiting remote access vulnerabilities in specific software, that's a warning signal that victims of that software should expect increased attacks.

International Coordination: How Law Enforcement Actually Works
The RAMP seizure involved coordination between multiple countries, but the specific nature of that coordination is worth examining because it reveals how modern international law enforcement actually functions.
The operation was led by the FBI with support from the U.S. Attorney's Office for the Southern District of Florida. But RAMP users were distributed globally—operators in Russia and Eastern Europe, users in Western Europe, victims on every continent. This meant the operation required international cooperation beyond the U.S.
EUROPOL (the European Union's law enforcement agency) coordinates major cybercrime operations involving EU member states. When the RAMP seizure was executed, it likely involved simultaneous arrests or investigations of RAMP users and administrators across multiple European countries. These operations are typically coordinated to prevent subjects from fleeing or destroying evidence.
Bilateral agreements between countries are also crucial. The U.S. has formal mutual legal assistance treaties (MLATs) with most countries that enable evidence sharing and coordinated investigations. If a RAMP administrator is believed to be in France, the FBI works with French authorities to obtain local warrants and conduct searches under French law.
The challenge with international law enforcement is jurisdictional complexity. If the actual RAMP administrator is in Russia, extradition to the U.S. is impossible absent exceptional circumstances. Russia has no extradition treaty with the U.S. Russian prosecutors could theoretically pursue charges under Russian law, but Russian law enforcement has shown little interest in prosecuting cybercriminals whose victims are primarily outside Russia.
This jurisdictional gap explains why some dangerous cybercriminals operate with relative impunity from certain countries. Law enforcement in the U.S. and EU can prosecute users within their jurisdictions, but the operators themselves might remain beyond reach if they're careful about which countries they're physically located in.
The Bigger Picture: Ransomware as a Business Model
Understanding the RAMP seizure requires understanding why ransomware has become the dominant form of cybercrime. It's profitable, relatively low-risk for operators compared to other crimes, and RAMP provided crucial infrastructure that made it viable at scale.
Ransomware works because it exploits the fundamental economics of cybersecurity. Installing proper security, maintaining backups, and keeping systems patched is expensive and requires sustained investment. A ransomware attack exploits a single vulnerability that shouldn't exist but does. From a purely economic perspective, paying a ransom is sometimes the rational choice for organizations with poor backup strategies.
The business model also benefits from cryptocurrency. Traditional crimes like bank robbery or drug trafficking involve physical currency or transfers that leave traces in banking systems. Cryptocurrency enables value transfer that's harder to trace. A victim can wire millions of dollars directly to an attacker's digital wallet without traditional banking controls and monitoring.
RAMP accelerated this business model's evolution by reducing friction. Rather than individual criminals developing their own capabilities, they could purchase components from specialists. Rather than ransomware gangs working entirely in isolation, they could collaborate and share intelligence on effective tactics. RAMP essentially created an economy of scale in ransomware operations.
The seizure won't end ransomware, but it has created friction in the supply chain. Going forward, cybercriminals will need to find alternative coordination mechanisms. Some will move to private infrastructure. Some will use smaller, less efficient forums. Some will attempt to rebuild on new public platforms. None of these options will be as efficient as RAMP was.

Law Enforcement's Evolving Strategy: From Takedowns to Ecosystem Disruption
Early law enforcement responses to cybercrime focused on arresting individual hackers or shutting down specific operations. That approach provided important symbolic victories but didn't fundamentally disrupt the criminal ecosystem.
More recent strategies recognize that the infrastructure enabling cybercrime is the actual target. By dismantling forums like RAMP, law enforcement makes it harder for specialized criminals to find each other and coordinate activities. By pursuing money laundering networks that convert cryptocurrency into usable funds, law enforcement attacks the economic incentives. By targeting bulletproof hosting providers, they limit the safe havens where criminal infrastructure can hide.
This ecosystem-level approach is slower and requires more patience than individual prosecutions. It involves building cases against entire organizations rather than just the most visible operators. It requires international coordination that can take months to arrange. But it has proven more effective at actually reducing crime rates.
The FBI's approach has become increasingly sophisticated. Rather than simply seizing a forum and moving on, they're using seized data to build long-term investigations. They're identifying the most dangerous operators and prioritizing them for prosecution. They're cooperating with international partners to ensure that criminals can't simply move their operations to friendly jurisdictions.
Looking forward, expect continued evolution in law enforcement techniques. Artificial intelligence and machine learning are beginning to play roles in analyzing massive datasets from seized forums. Behavioral analysis can help identify operators' real-world locations based on activity patterns. International coordination is becoming more sophisticated as countries recognize that cybercrime requires coordinated responses.

What Organizations Should Take Away from RAMP's Demise
For cybersecurity professionals and organizational leaders, the RAMP seizure carries important lessons. First, it confirms that law enforcement can successfully identify, prosecute, and dismantle major cybercriminal infrastructure. This is important context when evaluating the threat landscape. Ransomware remains significant, but the tools and forums enabling it are increasingly fragile.
Second, it reinforces that cybersecurity is not purely a technical problem. The humans designing, implementing, and orchestrating attacks have identifiable patterns. Law enforcement is becoming better at linking those patterns to real-world individuals. The assumption that cybercriminals can operate indefinitely in the shadows is increasingly invalid.
Third, it highlights the importance of incident reporting and coordination with law enforcement. Every ransomware attack that's reported to law enforcement provides data points that help build cases. Every ransom payment that can be traced improves investigators' understanding of money flows. Organizations that treat ransomware as purely a business problem and quietly pay without reporting miss the opportunity to contribute to collective security.
Fourth, it emphasizes that ransomware is fundamentally an availability and resilience problem. Organizations with proper backups, segmented networks, and disaster recovery plans can survive ransomware attacks even if attackers successfully encrypt systems. Organizations reliant on the assumption that they won't be attacked are most vulnerable.
Looking Forward: The Future of Darknet Enforcement
The RAMP seizure likely won't be the last major forum takedown. Law enforcement has demonstrated capability and commitment to disrupting cybercriminal infrastructure. Successors to RAMP will eventually be identified, investigated, and dismantled.
The question isn't whether law enforcement can shut down forums—they've proven they can. The question is whether they can do it faster than criminals can rebuild. That's where the real battle lies. If criminals can launch replacement forums every few months faster than law enforcement can build cases and execute seizures, the disruption is merely temporary.
The cryptocurrency ecosystem is also under increasing scrutiny. As governments develop stronger digital asset regulations and law enforcement learns better techniques for tracing blockchain transactions, the anonymity that made cryptocurrency attractive for criminals is eroding. This won't eliminate cryptocurrency use in crime, but it will make it less attractive.
One wild card is the development of fully decentralized platforms that don't rely on central servers. If cybercriminals build forums on distributed networks like blockchain-based systems, traditional seizure operations become impossible. Law enforcement will need to develop entirely new techniques to address that scenario.
Another consideration is automation and AI. As artificial intelligence becomes more sophisticated, it might be used by both criminals and law enforcement. Criminals might use AI to identify law enforcement investigations earlier. Law enforcement might use AI to analyze seized data more quickly. The technological arms race will likely accelerate.

The Human Element: Why Cybercriminals Get Caught
Despite sophisticated anonymization and operational security, cybercriminals consistently make mistakes that lead to identification. The RAMP case is no exception—Stallman's public confirmation of the seizure is itself a security failure that could assist in identification.
Common mistakes include emotional responses that override operational discipline. When something significant happens (like a forum seizure), criminals often can't resist posting about it. They're proud of what they've built, even if it's criminal. That pride becomes their undoing.
Another common mistake is maintaining consistent identity across platforms. A user who called themselves "Stallman" on RAMP and uses the same or similar usernames elsewhere creates a digital trail. Experienced investigators can follow that trail across multiple platforms.
Operational security is also surprisingly difficult to maintain consistently. It only takes one slip-up—one moment where someone forgets to use a VPN, one payment from an account linked to their real identity, one communication sent without encryption—and the careful anonymity they've built can collapse.
Law enforcement also exploits the fundamental interpersonal dynamics of criminal groups. Criminals working together must trust each other. That trust is often misplaced. Informants infiltrate groups. Undercover agents pose as fellow criminals. People facing serious charges cooperate with law enforcement in exchange for reduced sentences. These human elements are often more effective at disrupting criminal operations than technical tools.

Conclusion: A Watershed Moment in Cybercrime Law Enforcement
The seizure of RAMP represents a watershed moment in the law enforcement response to cybercrime. For the first time, major international law enforcement agencies have demonstrated that they can identify, infiltrate, investigate, and dismantle one of the largest cybercriminal forums without that forum successfully relocating or operating uninterrupted. The operation captures years of accumulated criminal data, provides investigative leads for future prosecutions, and sends a clear signal to cybercriminals that their infrastructure is not as secure as they believe.
But the victory is incomplete. RAMP's seizure is disruptive but not eliminatory. Ransomware operations will continue. Cybercriminals will migrate to alternative platforms. The fundamental economics that make cybercrime profitable remain unchanged. Law enforcement has won an important battle, but the broader conflict continues.
For organizations, the RAMP case provides important context for cybersecurity strategy. It confirms that law enforcement is actively working to disrupt the infrastructure enabling cyberattacks. It demonstrates that sophisticated anonymization doesn't guarantee safety. And it reinforces that organizational resilience—the ability to survive and recover from attacks—is ultimately more valuable than perfect prevention.
The cybercriminal ecosystem is evolving rapidly in response to law enforcement pressure. More sophisticated criminals are building private infrastructure rather than relying on public forums. Groups are becoming more selective about recruitment. Operational security is improving. This creates a new problem for law enforcement: criminals who are harder to identify and investigate because they're less visible.
But law enforcement is also evolving. The techniques used to investigate RAMP—international coordination, data forensics, behavioral analysis, long-term intelligence gathering—are becoming more sophisticated. Future operations will likely be more effective, targeting not just platforms but the entire ecosystem that enables them.
The RAMP seizure is ultimately a reminder that the internet, despite its potential for anonymity, isn't actually a lawless frontier. Law enforcement agencies worldwide have developed genuine expertise in investigating digital crime. They're willing to invest years in building cases. They're cooperating across borders to pursue criminals. That doesn't mean cybercrime will disappear—the economics are too attractive. But it does mean that cybercriminals should expect that law enforcement is watching, building cases, and moving methodically toward disruption and prosecution.

FAQ
What was RAMP and why was it important to cybercriminals?
RAMP was an underground cybercrime forum that operated from 2021 until its seizure by the FBI. It functioned as a marketplace where ransomware operators, initial access brokers, and other cybercriminals could advertise services, buy tools, and coordinate attacks. The forum was important because it provided professional infrastructure—reputation systems, escrow services, and dispute resolution—that made it easier for criminals to collaborate and execute high-value attacks. It essentially operated like eBay but for crime, creating a supply chain where different specialists could buy and sell access, tools, and services needed for ransomware campaigns.
How did the FBI actually seize RAMP if it was on the dark web?
The FBI located RAMP's physical servers through a combination of techniques including informant intelligence, forensic analysis of traffic patterns, and international cooperation. Once located, federal agents obtained warrants and accessed the servers simultaneously across all domains (both clearnet and Tor). They created forensic copies of all data on the servers to preserve evidence, then deployed legal seizure notices on the websites. The actual servers had to exist somewhere in the physical world, and finding those locations was the key to the operation. The seizure required coordination with international law enforcement agencies and hosting providers.
What happens to the criminals whose data was on RAMP servers after the seizure?
The captured data provides law enforcement with years of evidence about individual cybercriminals' activities, communications, and relationships. Prosecutors will use this information to build cases against identified subjects, though prosecutions can take years to develop and execute. Users who weren't careful about anonymization are at highest risk—those who used linked email addresses, consistent usernames, or whose IP addresses can be traced. Law enforcement has shown it's willing to pursue cases years after forum seizures, so captured users should expect potential future prosecution. Additionally, the data helps law enforcement identify relationships and organizational structures within criminal groups, improving their ability to disrupt future operations.
Will this affect ransomware attacks going forward?
The RAMP seizure will cause operational friction but won't eliminate ransomware attacks. Ransomware remains profitable and will continue, but cybercriminals now need alternative coordination mechanisms. Some will migrate to surviving forums like XSS, while others will build private infrastructure. The seizure effectively raises the cost and complexity of coordinating ransomware operations, which might reduce the frequency of lower-level attacks. However, well-organized groups with established relationships will be less affected and may actually benefit from reduced competition as newer criminals find it harder to enter the ecosystem.
How does RAMP compare to other seized cybercrime forums?
RAMP is one in a long line of seized forums, but among the most significant. Silk Road's seizure in 2013 demonstrated law enforcement's capability but mainly targeted drug sales. Alpha Bay's shutdown in 2017 captured similar operational data but was less specialized in ransomware. RAMP was significant because it was explicitly designed to facilitate ransomware operations at a professional scale, making it arguably the most dangerous forum to the U.S. economy. The seized data from RAMP is likely more immediately actionable for prosecuting active ransomware operators than previous forum seizures.
What should organizations do differently based on the RAMP seizure?
Organizations should recognize that law enforcement is actively disrupting the infrastructure enabling cyberattacks, which validates investment in resilience over perfect prevention. Focus should remain on maintaining current backups, segmenting networks, patching vulnerabilities, and practicing disaster recovery. Additionally, organizations should coordinate with law enforcement by reporting ransomware attacks and payments, contributing data that helps build prosecutions. Finally, understand that while ransomware threats will persist, the ecosystem enabling these attacks is under sustained pressure, gradually increasing the friction and cost for attackers.
How are cybercriminals adapting after the RAMP seizure?
Cybercriminals are adapting by moving to private or more exclusive platforms rather than public forums, using encrypted messaging apps for coordination, implementing stricter access controls, and building invite-only communities based on established reputation. Leading ransomware groups like Lock Bit and Black Cat have already shifted toward closed-network models where membership is by invitation only. While these adaptations increase operational security, they also reduce efficiency by limiting access to the open marketplace and making it harder for new entrants to find services and collaborators.
Could law enforcement seize Tor-hosted forums more easily in the future?
Tor-hosted forums present technical challenges different from clearnet forums, but seizure is possible once physical servers are located. Law enforcement's ability to identify Tor hidden services has improved over time. However, criminals are developing more sophisticated hosting techniques, potentially using truly distributed infrastructure in the future that would be harder to seize. This is an ongoing technological arms race where law enforcement develops new techniques to identify and dismantle criminal servers, while cybercriminals develop increasingly sophisticated methods to hide their infrastructure and distribute their operations across multiple jurisdictions.
What international cooperation was required for the RAMP seizure?
The RAMP seizure required coordination between the FBI, the U.S. Attorney's Office for the Southern District of Florida, EUROPOL (the EU law enforcement agency), and individual law enforcement agencies in multiple countries where RAMP users or servers were located. International cooperation involves sharing intelligence, coordinating timing of investigations, obtaining local warrants under each country's laws, and sometimes conducting simultaneous arrests to prevent suspects from fleeing or destroying evidence. Bilateral mutual legal assistance treaties (MLATs) facilitate the formal cooperation needed for international cybercrime investigations.

TL; DR
- RAMP Seized: The FBI shut down RAMP, a major darknet forum used by ransomware gangs and cybercriminals to buy and sell hacking services, malware, and network access
- Massive Data Capture: Law enforcement now possesses the forum's complete database including user information, private messages, transaction records, and operational communications spanning years of activity
- Prosecution Risk: Users who weren't careful about anonymization face severe prosecution risk, with law enforcement building cases that could result in charges years after the seizure
- Operational Disruption: The seizure forces cybercriminals to migrate to alternative platforms and private infrastructure, increasing operational costs and reducing collaboration efficiency
- Long-term Impact: While ransomware will continue, the seizure demonstrates law enforcement's growing capability to identify, infiltrate, and dismantle major cybercriminal infrastructure supporting multi-billion-dollar criminal economy

Key Takeaways
- The FBI successfully seized RAMP, a darknet forum that facilitated ransomware operations by providing infrastructure for cybercriminals to buy and sell hacking services.
- The seizure captured massive amounts of user data including emails, IP addresses, private messages, and transaction records that law enforcement will use to build prosecutions over years.
- Cybercriminals are adapting by moving to more private platforms and encrypted channels, reducing operational efficiency but making detection harder.
- International law enforcement coordination proved essential to identifying and dismantling the forum across both clearnet and Tor domains.
- The RAMP seizure represents a shift from prosecuting individual hackers toward disrupting entire criminal ecosystems and the infrastructure that enables them.
Related Articles
- FBI Seizes RAMP: The Collapse of Ransomware's Last Stronghold [2025]
- Microsoft Office CVE-2026-21509 Security Flaw: What You Need to Know [2025]
- Grubhub Data Breach 2025: What Happened and How to Protect Yourself [2025]
- RedDVS Phishing Platform Takedown: How Microsoft Stopped a $40M Cybercrime Operation [2025]
- Major Shipping Platform Exposed Customer Data, Passwords: What Happened [2025]
- NordVPN Salesforce Breach Claim: What Really Happened [2025]
![FBI Seizes RAMP Cybercrime Forum: What Happened & What It Means [2025]](https://tryrunable.com/blog/fbi-seizes-ramp-cybercrime-forum-what-happened-what-it-means/image-1-1769701218355.jpg)



