The Firewall Crisis Nobody Saw Coming
Your network's first line of defense is under siege. Not from sophisticated zero-day exploits or cutting-edge AI-powered attacks, but from vulnerabilities so old they predate your company's founding.
This isn't hyperbole. Security researchers just dropped a report that's making CISOs across every industry collectively hold their breath. The finding? Almost every ransomware incident in 2025 started the same way: through a compromised firewall.
Here's what shook the security world. Barracuda's Managed XDR team analyzed over two trillion IT events and 600,000 security alerts throughout 2025. Their conclusion was unambiguous: 90% of all ransomware incidents exploited firewalls, either through known vulnerabilities or compromised credentials. Not 50%. Not 75%. Ninety percent.
The implications are staggering. Your firewall isn't just another box on your network. It's the skeleton key to your entire infrastructure. Once an attacker gets through, they've got a direct line to everything behind it. Every server. Every database. Every file. The ransomware part? That's just the endgame.
What makes this worse is timing. We're in an era where ransomware groups are operating at peak efficiency. Active ransomware groups hit record numbers in the second half of 2025, with victim counts doubling since 2024. The infrastructure is there. The motivation is there. And most importantly, the vulnerabilities are wide open.
The question isn't whether your firewall will be targeted. The question is when, and whether you'll be ready.
TL; DR
- 90% of ransomware incidents in 2025 started through firewall exploits, according to Barracuda's analysis of 2 trillion IT events
- The oldest vulnerability being exploited is 13 years old (CVE-2013-2566), proving attackers go after easy targets first
- One in every 10 detected vulnerabilities already had public exploits available, making them immediately exploitable
- Firewall attacks now account for nearly 30% of initial network compromises, per Sophos research
- Ransomware groups reached record numbers in 2025, with victim counts doubling year-over-year
- Bottom Line: Patch your firewalls immediately, enforce MFA on firewall accounts, and monitor edge devices for suspicious activity
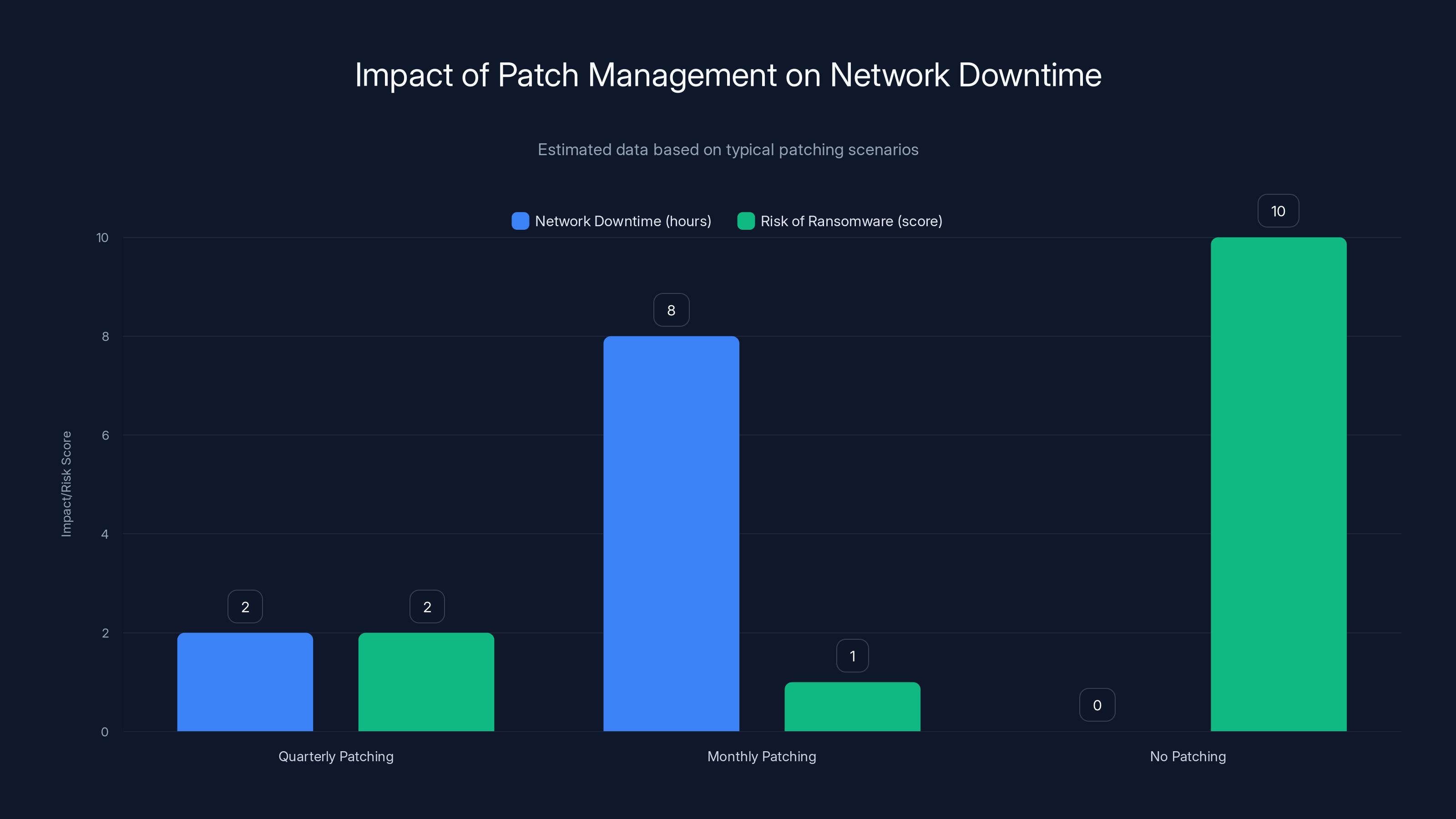
Quarterly and monthly patching reduce ransomware risk significantly compared to no patching, despite some network downtime. Estimated data.
Why Firewalls Have Become Ground Zero for Ransomware
Firewalls weren't always the prime target. Ten years ago, attackers focused on endpoints—laptops, desktops, user machines. But the threat landscape shifted. Endpoint protection got better. EDR tools got smarter. Multi-factor authentication became standard. So attackers did what they always do: they found the gap.
The firewall sits at a unique intersection of access and invisibility. It controls all ingress and egress traffic, meaning it's the gateway to your entire network architecture. Yet most organizations treat firewall security like a set-it-and-forget-it proposition. Deploy the device, configure the rules once, and move on to sexier security concerns.
This is the golden ticket for attackers.
When you compromise a firewall, you don't need to breach individual endpoints or fool users with phishing emails. You've already got administrative access to the network's most critical control point. From there, lateral movement is trivial. You can disable alerts, create backdoors, exfiltrate data, or deploy ransomware to every connected device simultaneously.
Moreover, firewalls run older operating systems and software stacks. They're embedded devices, often running firmware versions from years ago. Legacy security patches take forever to deploy because downtime isn't an option. A rebooting firewall means your entire network is offline. So companies delay updates, and delays become years.
Attackers know this. They've built their entire operational playbook around it.
The other factor: firewalls are harder to monitor than endpoints. Your security team can see when someone logs into a user workstation. Firewall logins? Those often go unnoticed, especially if attackers leverage stolen credentials from a legitimate admin account. The activity looks normal. The traffic pattern looks normal. By the time you realize something's wrong, the ransomware is already encrypting your systems.
This is why security vendors are now calling firewalls the "new perimeter." Except the perimeter doesn't feel new. It feels old, unpatched, and vulnerable.
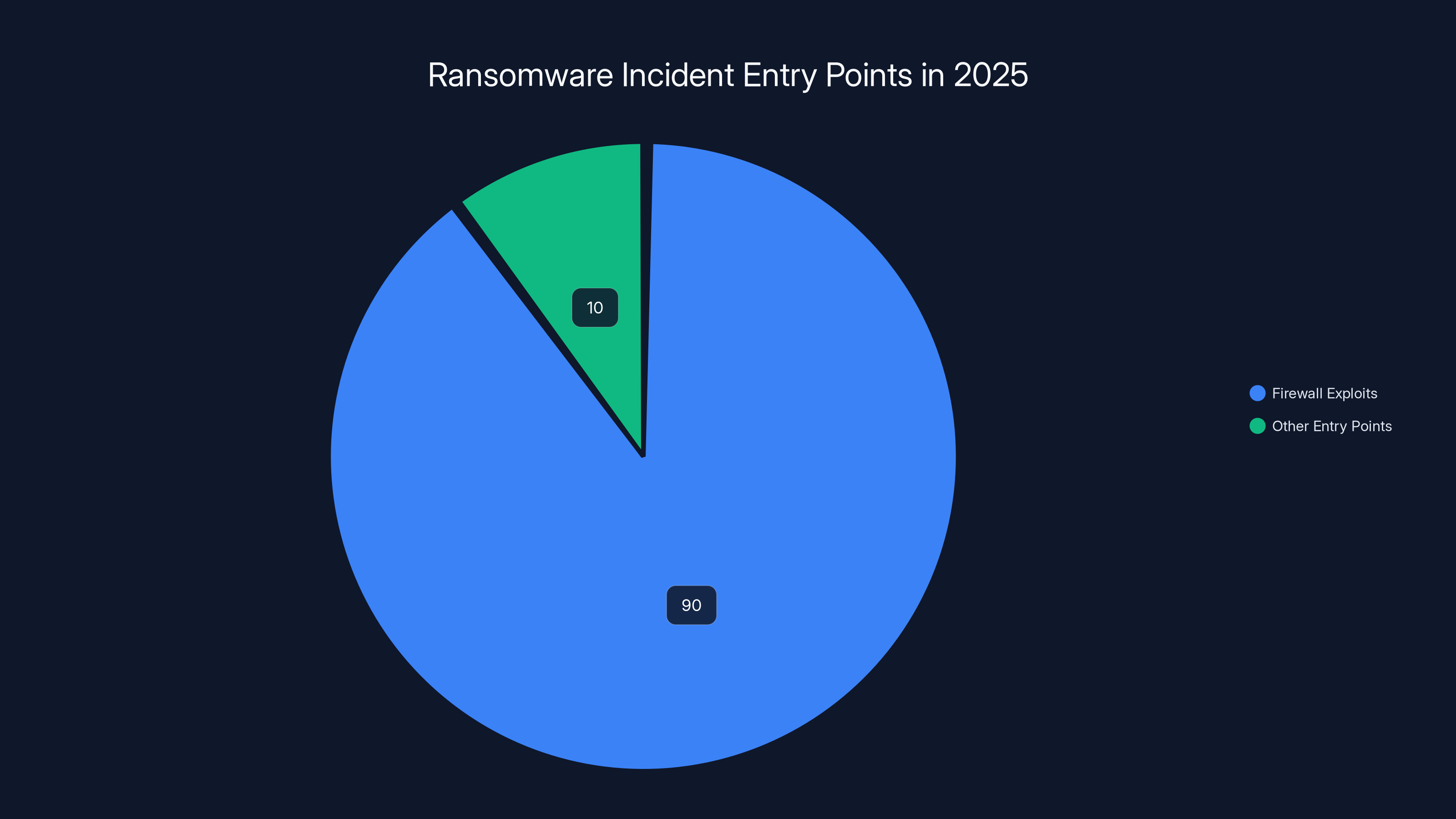
A staggering 90% of ransomware incidents in 2025 exploited firewalls, highlighting critical vulnerabilities in network defenses.
The Scale of the Problem: Data-Driven Reality
Let's talk numbers, because they paint a picture that's hard to ignore.
Barracuda's 2025 analysis wasn't a small sample. They were working with 2 trillion IT events. That's 2,000,000,000,000 individual data points. That's not theory or extrapolation. That's a massive dataset showing what's actually happening in real networks right now.
Out of that ocean of data, they found 90% of ransomware incidents exploited firewall vulnerabilities or compromised accounts. Think about that statistic. Out of every ten ransomware incidents you hear about, nine of them got in through your firewall.
But it gets worse. One in every ten detected vulnerabilities already had a public exploit available. This isn't about zero-days or sophisticated hacking. This is about attackers running automated scanners, finding old flaws, and using publicly available exploit code. It's lazy. It's effective. It works almost every time.
Why? Because organizations haven't patched.
Searchlight Ransomware's H2 2025 report added another troubling data point: the number of active ransomware groups reached unprecedented levels. More groups. More sophistication. More infrastructure. And victim counts doubled year-over-year. The ecosystem is thriving.
Sophos' Annual Threat Report looked at it from another angle. Incidents involving network edge devices (routers, VPNs, firewalls) accounted for nearly 30% of initial compromises. That's almost one in three breaches starting at your network's front door.
Put these datasets together, and the picture emerges: ransomware as an industry is optimizing around firewall attacks because firewalls are optimized for everything except defending themselves.
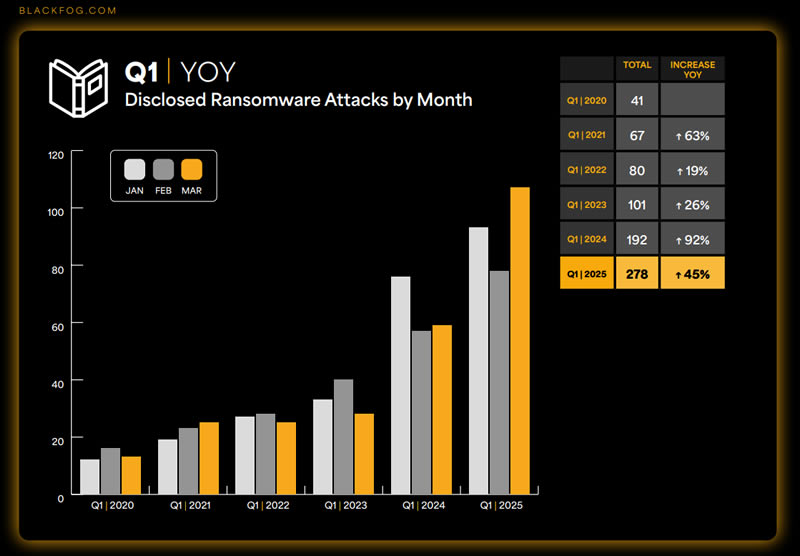
The Vulnerability Landscape: Old Threats, New Victims
The most shocking finding from Barracuda's research isn't the 90% figure. It's which vulnerabilities are being exploited.
CVE-2013-2566 is the poster child. This vulnerability was discovered in 2013—thirteen years ago. For context, that's before most current security professionals even entered the field. The flaw is in RC4, an encryption algorithm that cryptographers have warned against for over a decade. Yet in 2025, this ancient vulnerability is still being actively exploited in ransomware attacks.
Why is a 13-year-old flaw still dangerous? Legacy systems. Your organization almost certainly has embedded devices, servers, or applications still running old encryption algorithms. Routers from 2010. Firewalls from 2012. Network appliances that were cutting-edge a decade ago and have been forgotten ever since.
These devices often can't be patched without replacing entire hardware. Upgrading means downtime. Downtime means business interruption. So IT teams make a calculation: keep running the old device, accept the risk. Most of the time, nothing happens. Once in a while, you get ransomware.
Other common firewall vulnerabilities follow similar patterns. Many are in features that were enabled by default during deployment. Maybe it's SSL-VPN that nobody uses anymore. Maybe it's a default account that was never changed. Maybe it's a protocol that's been outdated for years but was never disabled.
Attackers have weaponized these forgotten configurations. They scan the internet for common firewall models, check for known vulnerabilities, try default credentials, and move down the list. Automated. Scalable. Effective.
The really insidious part? Many organizations don't even know they have these vulnerabilities. If your firewall is running firmware from 2021 and you haven't checked the vendor's security bulletin since then, you're flying blind. Patches were released. Maybe you saw the notification. Maybe it went to the wrong inbox. Either way, you're running old code with known exploits.

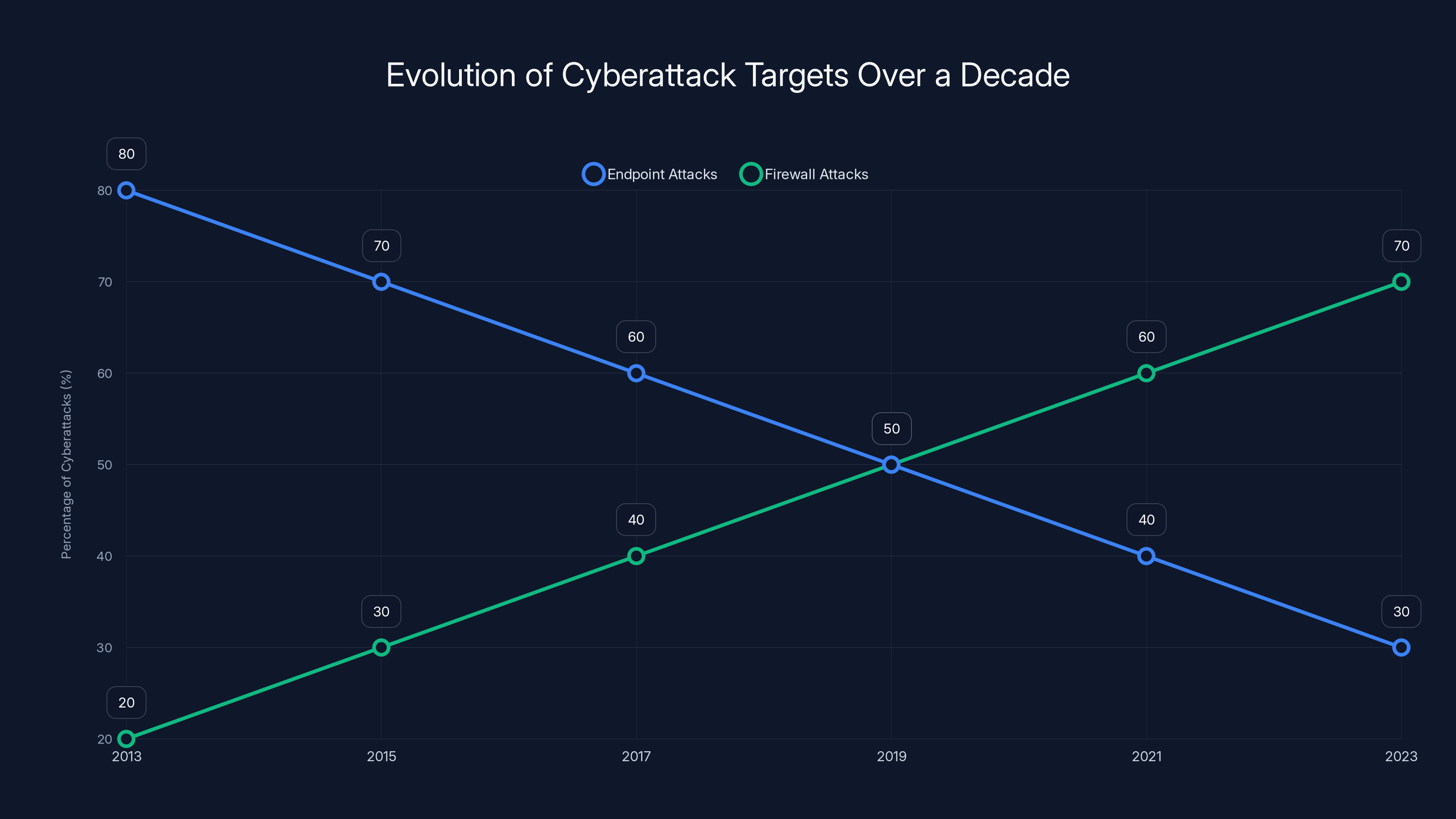
Over the past decade, there has been a significant shift in cyberattack targets from endpoints to firewalls, highlighting the evolving threat landscape. (Estimated data)
Real-World Attacks: The Sonic Wall Case Study
Theory is important, but what about real attacks?
In late 2025, Sonic Wall firewall appliances became the focus of coordinated, sophisticated attack campaigns. The vulnerable models had SSL-VPN enabled across multiple generations. SSL-VPN is a legitimate feature used for remote access. It's also a direct tunnel into your network that, if compromised, gives attackers exactly what they want.
The threat actors leveraging these vulnerabilities? The Akira ransomware group. Not some random opportunist, but one of the most organized, professional ransomware operations active today. They weren't blindly scanning for easy targets. They were running a precision campaign against a known, exploitable vulnerability.
The attack pattern went like this. Scan for Sonic Wall devices with SSL-VPN exposed to the internet. Attempt exploitation. Gain access. Create rogue administrative accounts. These fake accounts looked legitimate, so monitoring systems didn't flag them. Then, the group had persistent access to dozens of customer environments simultaneously.
Reports indicate that across roughly 16 different customer environments, more than 100 SSL-VPN accounts were compromised and used for follow-on activity. That's not one company getting hit. That's an entire ecosystem of organizations falling victim to the same vulnerability.
The impact cascaded from there. Once inside, attackers had several paths. They could steal data for extortion. They could deploy ransomware to every system. They could establish persistent backdoors for future attacks. The firewall breach was the initial entry point. Everything that followed was inevitable.
What's concerning is that many organizations didn't even realize they were compromised until security researchers or law enforcement made contact. The Akira group doesn't always deploy ransomware immediately. Sometimes they sit quietly, gathering intelligence, mapping networks, identifying valuable assets. Months later, they strike. Or they don't. Or they sell access to other threat actors. The uncertainty itself is a form of extortion.
The Sonic Wall situation wasn't an isolated incident. Fortinet Forti Gate devices have been hit by similar campaigns creating rogue accounts and stealing firewall configuration data. Palo Alto Networks' Global Protect gateways have been targeted. Cisco ASA appliances have vulnerabilities being actively exploited. The trend is clear: firewalls are the new front line, and nobody's defending it properly.
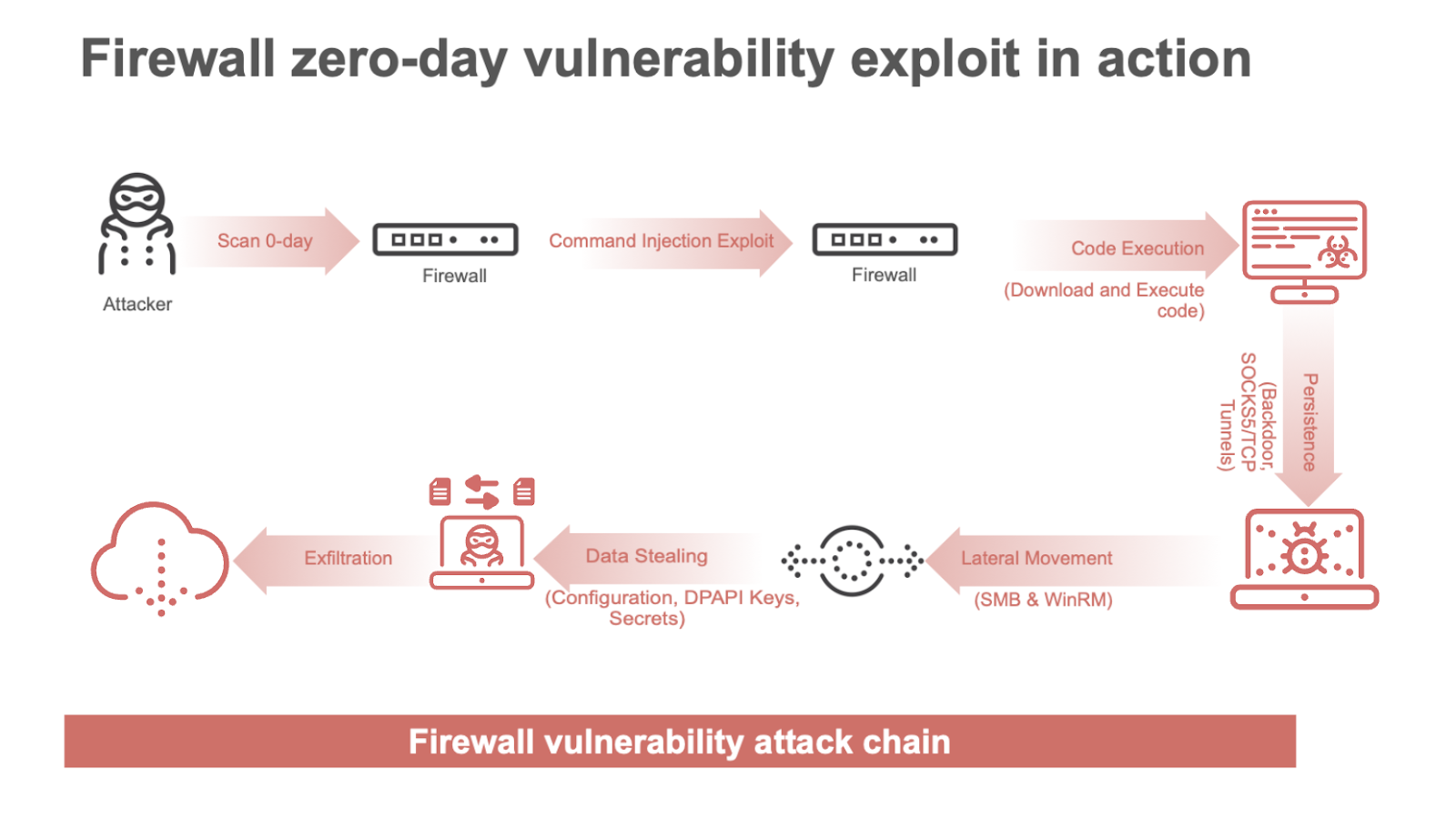
The Mechanics of Firewall Compromise: How It Happens
Understanding how attacks actually work is the first step to preventing them.
Most firewall compromises follow a predictable sequence. First, reconnaissance. Attackers use internet-wide scanning tools like Shodan or Censys to identify exposed firewall management interfaces. These tools can fingerprint devices, identify firmware versions, and flag known vulnerabilities in bulk. An attacker can potentially identify thousands of vulnerable targets in minutes.
Second, exploitation or credential stuffing. If a known vulnerability exists, the attacker attempts it automatically. If no vulnerability works, they try common default credentials: admin/admin, admin/password, netadmin/netadmin. These credentials still work shockingly often because nobody changed them during initial setup. The credentials might also be obtained from previous breaches. If your email was in a data dump from years ago, attackers have tried those credentials against your firewall.
Third, persistence. Once inside the firewall's management interface, the attacker's goal is to ensure they can come back later. They create rogue administrative accounts, often giving them generic names that blend in with legitimate users. Maybe "svc-admin" or "backup-admin." They're designed not to trigger alerts. Some attackers install webshells in the firewall's HTTP interface, allowing them to maintain access even if passwords are changed.
Fourth, lateral movement and data gathering. With the firewall compromised, the attacker now has visibility into all network traffic and the ability to modify firewall rules. They can disable logging to cover their tracks. They can route traffic through exfiltration channels. They can set up forwarding rules to tunnel into internal systems. They study the network architecture, identify valuable targets, and plan the next phase.
Fifth, either extortion or encryption. Some groups pursue a simple encryption and ransom model: deploy ransomware, demand payment. Others steal data first, establishing a double-extortion scenario: "Pay us or we encrypt your systems AND publish your data." Still others simply have access and wait, selling that access to other threat actors or holding it as leverage.
The timeline from initial compromise to full ransom demand can be weeks, months, or even years. By the time the alert goes out, the damage is already done.

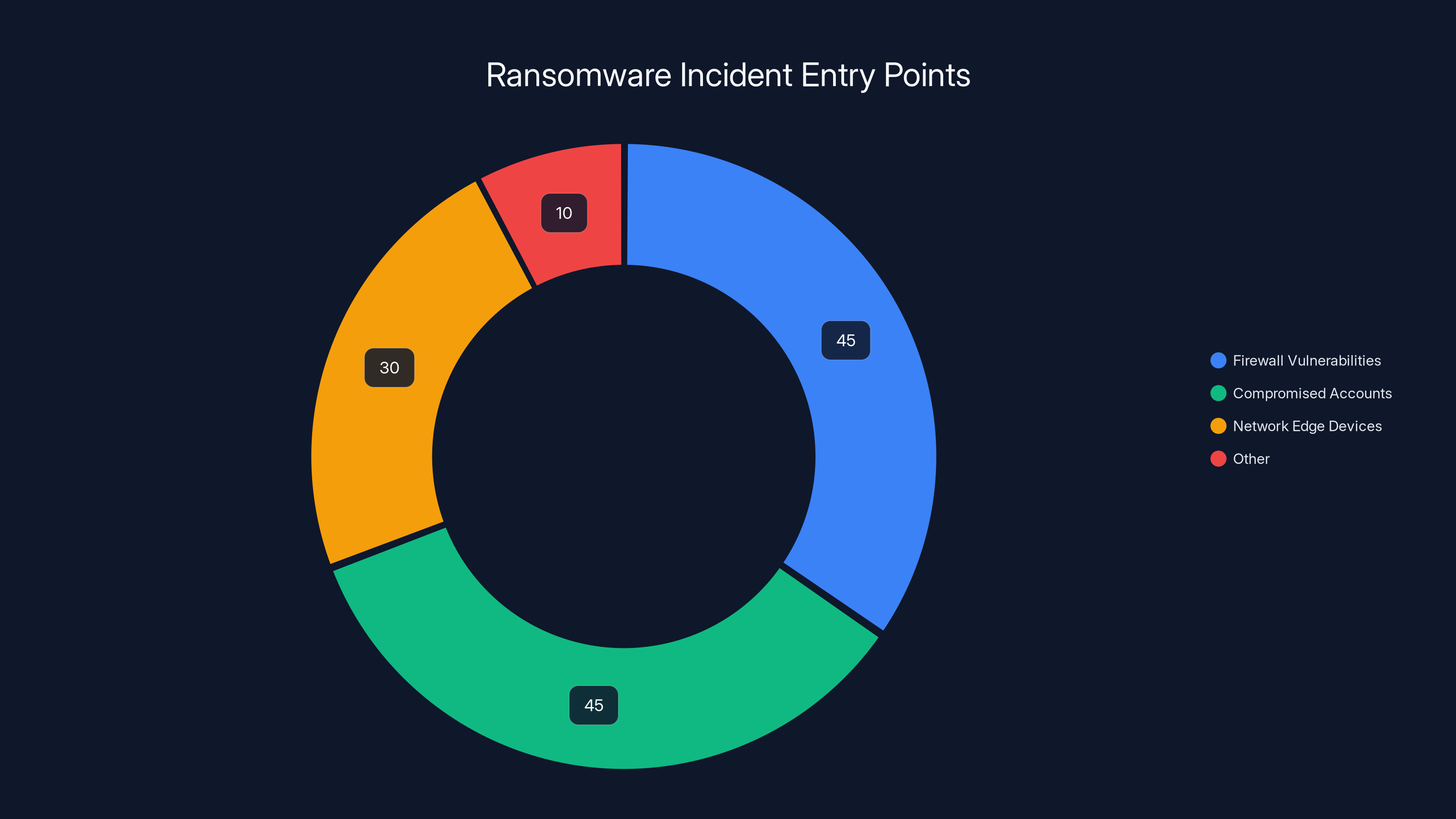
90% of ransomware incidents exploited firewall vulnerabilities or compromised accounts, while 30% involved network edge devices. Estimated data based on reports.
Why Traditional Security Controls Fail at the Firewall
You'd think we'd have this solved by now. We have endpoint detection and response. We have intrusion prevention systems. We have advanced threat intelligence. Yet firewalls keep getting compromised.
The reason is architectural. Firewalls are designed to control traffic. They're not designed to be monitored like endpoints. Your EDR tool watches what processes are running, what files are being accessed, what network connections are being made. A firewall? You can see management logins and rule changes, but the visibility is limited.
Many organizations also lack proper alerting on firewall anomalies. A new administrative account being created on your firewall should trigger an immediate alert. Does it? Not in most deployments. Configuration changes should be logged and reviewed. Are they? Rarely. SSH access to the firewall at 3 AM from an IP address in Eastern Europe should be flagged. But if there's no proper logging and monitoring in place, nobody even knows it happened.
Another critical gap: security teams don't apply the same rigor to firewalls as they do to other infrastructure. Your servers get vulnerability scans monthly. Your applications get penetration testing quarterly. Your firewall? It might get checked once a year, if that. The firewall is often considered "stable" and "not a vector" because nobody has taught people to look.
There's also the compartmentalization issue. The firewall team might be separate from the security team. The firewall team's job is to keep the network running, not to hunt threats. The security team focuses on endpoints and applications. The firewall exists in the middle, owned by nobody and monitored by nobody. It's a gap that attackers have learned to exploit ruthlessly.
Patch Management: The Unsexy Solution That Saves Lives
If ransomware via firewall compromise is the disease, patching is the cure. It's not sexy. It doesn't generate conference talks or funding rounds. But it works.
The challenge is operational. Patching a firewall isn't like patching a laptop. When you reboot a firewall for a patch, your entire network goes down. Connections drop. VPNs disconnect. Traffic grinds to a halt. So organizations delay patches, sometimes indefinitely.
The math is simple from a business perspective. "If we patch, we lose two hours of network access and impact five thousand employees. If we don't patch and get breached, we might lose a few gigabytes of data." Risk assessment pushes toward the status quo.
But this calculus is broken. The real cost of a ransomware compromise is astronomical. Barracuda found that 90% of incidents exploited firewall vulnerabilities. Even if the probability of your specific firewall being targeted is 5%, the expected value of a ransomware attack (probability times damage) is almost certainly higher than the cost of scheduled downtime for patching.
Here's a better approach: planned, scheduled, tested firewall patches. Not emergency response, but scheduled maintenance. Perhaps quarterly. You communicate with stakeholders that on the second Tuesday of each quarter, firewalls will be updated between 2 AM and 4 AM. You test patches in a lab environment first. You have rollback procedures ready. You document everything.
The patches themselves shouldn't take long if you've done the work. A modern firewall can often patch and reboot in under 30 minutes. If your firewall takes two hours to patch, that's a sign the device is out of date or misconfigured.
For critical vulnerabilities, you might patch more frequently. If a zero-day is announced affecting your specific firewall model, you prioritize it. But for standard updates? Quarterly is reasonable for most organizations. Monthly is better. Anything less than quarterly is deferring risk until it becomes a crisis.
One more thing: document your baseline. Know what version your firewall should be running. Know what features should be enabled and what should be disabled. When you apply patches, verify the baseline hasn't changed. If you find unexpected modifications, you've got a detection mechanism.

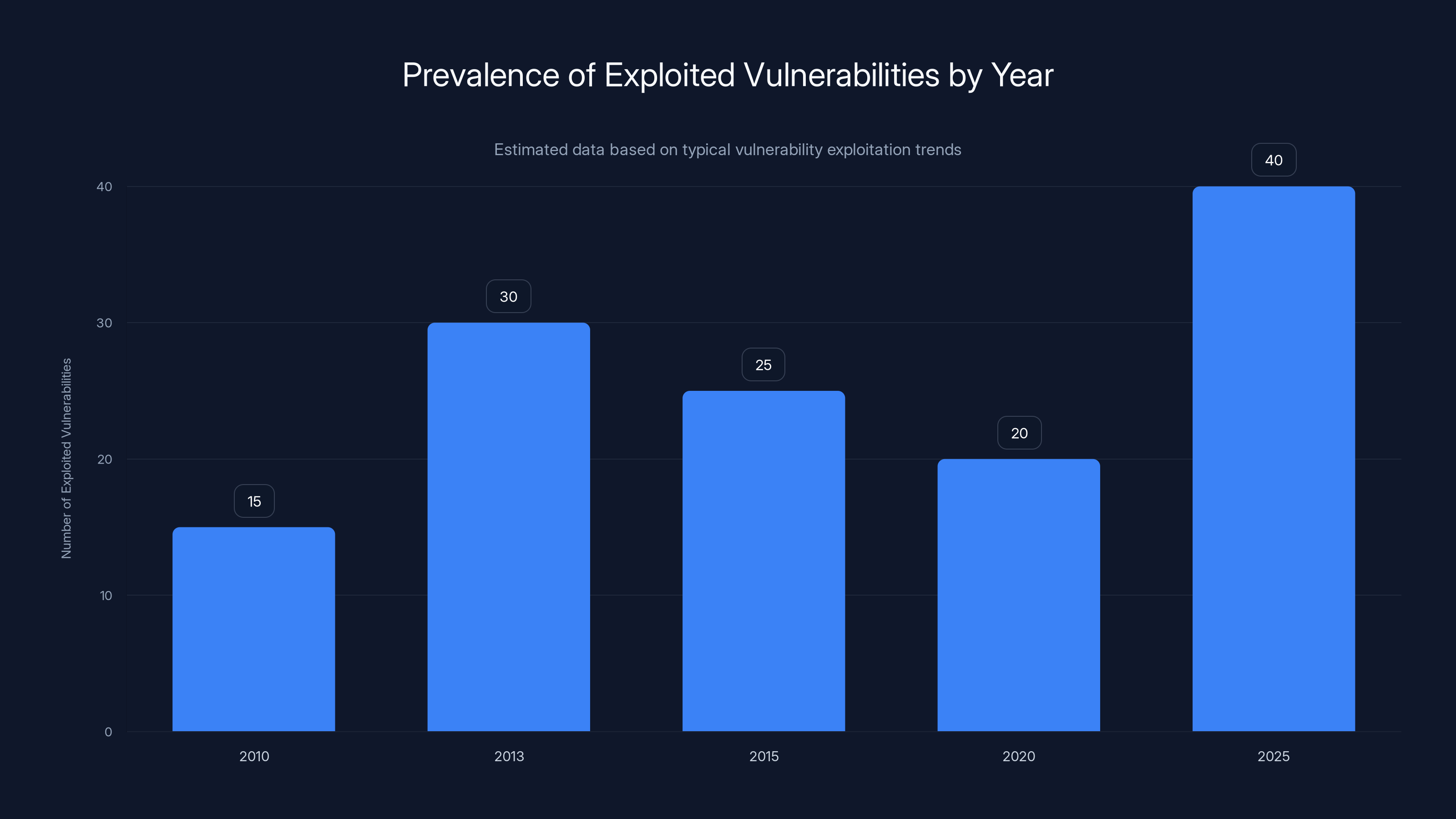
The chart illustrates the estimated number of vulnerabilities from different years being exploited in 2025, highlighting the persistence of older vulnerabilities like CVE-2013-2566. Estimated data.
Multi-Factor Authentication on Firewall Accounts
Half the compromises come from credential compromise, not zero-days. So if you can't patch immediately, at least make it harder to get in.
Multi-factor authentication on firewall management interfaces is table stakes. Yet many organizations haven't implemented it. The reasoning is usually convenience: IT staff already knows their firewall credentials, why add the friction of a second factor?
The answer is that if a firewall admin's credentials are compromised (and they likely are, considering the number of data breaches), attackers can walk right in without a second factor. They don't need to crack anything. They don't need sophisticated tools. They just use the stolen password.
MFA changes that. Even with a compromised password, attackers can't get in without the second factor. They'd need the phone associated with the admin account, or access to the TOTP generator, or something else that's harder to obtain at scale.
Implementing MFA on firewalls isn't complicated from a technical standpoint. Most firewall vendors support it. The challenge is cultural: getting your firewall team comfortable with the change. But this is non-negotiable. Any firewall accessible over the network (which is all of them) needs MFA on administrative accounts.
I'd go further: implement MFA for everything. Firewall management logins. SSH access. Web interface access. VPN access. If it's a way into critical infrastructure, it gets MFA. The upfront work pays dividends when attackers inevitably try to walk in with stolen credentials.

Monitoring and Detection: Seeing What You Don't Want to Miss
Patch your firewalls. Enable MFA. But also, watch them like a hawk.
The challenge is knowing what to monitor. Firewall logs can be massive. Millions of denied connections daily. Thousands of allowed connections. Sort through that noise and you'll miss the signal.
Here's what actually matters: administrative access to the firewall. Every login, every logout, every configuration change. These should be logged to a centralized SIEM or security information and event management system. If your firewall keeps logs locally only, they're essentially invisible. Attackers can delete them.
Second, unexpected configuration changes. Your firewall's rules should be consistent. If someone creates a new rule allowing traffic from an unusual source to an unusual destination, that's anomalous. Firewall configurations rarely change. When they do, it should be through a controlled process with documentation and approval. Any deviation is suspicious.
Third, failed login attempts. A few failed logins happen naturally. But if there's suddenly a spike in failed attempts, someone's attacking your firewall. That's an alert-worthy event.
Fourth, new administrative accounts. Every account creation should be reviewed and approved. If you find an administrative account you don't recognize, that's a compromise indicator.
Fifth, unusual traffic patterns. Your firewall sees everything passing through your network. If normal traffic patterns suddenly shift, that might mean an attacker is exfiltrating data or accessing assets that normally aren't accessed. Changes in traffic volume, new destinations, new protocols—these are worth investigating.
Implementing this monitoring requires tools. You need a SIEM or security analytics platform. You need the firewall configured to export logs in real-time. You need rule sets tuned to your specific environment so you're not getting a thousand false positives daily. This isn't trivial. But it's essential.
For organizations lacking the expertise in-house, managed security service providers offer this as a service. They'll monitor your firewall 24/7, analyze logs, and alert on suspicious activity. The cost is real, but it's usually cheaper than dealing with a ransomware incident.

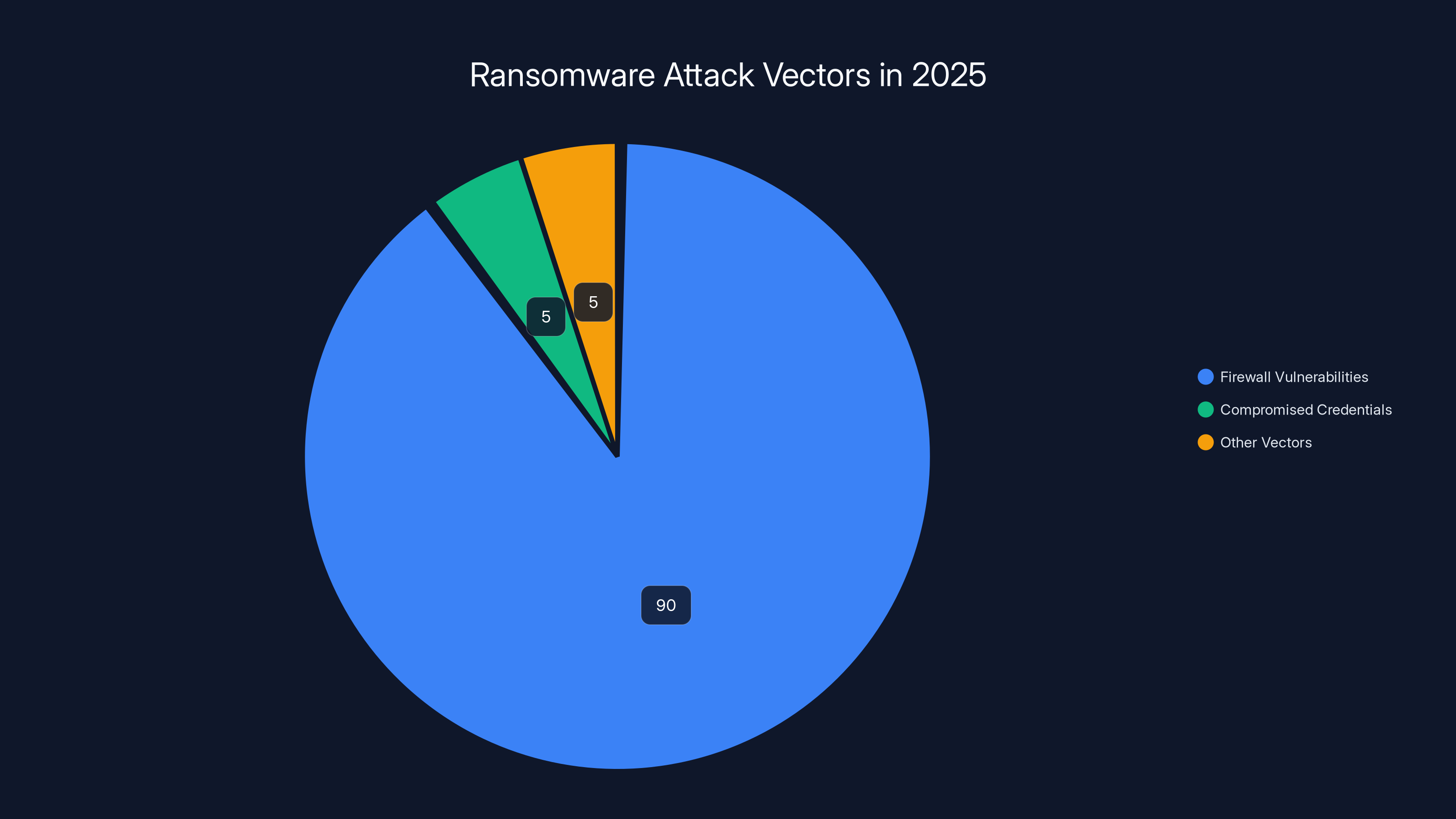
In 2025, 90% of ransomware incidents exploited firewall vulnerabilities, highlighting the critical need for robust firewall security measures.
Access Control: The Principle of Least Privilege
Not every firewall admin needs full administrative access to everything.
Yet many organizations give everyone the same credentials or the same broad permissions. The result: if one admin's account is compromised, all firewall access is compromised.
Better approach: implement role-based access control on your firewalls. Admins who manage only specific firewall rules get accounts with permissions for those rules only. Backup administrators get different access than security administrators. Network operations staff get read-only access to logs. Everyone has the minimum permissions needed for their role.
This principle of least privilege is foundational to security, but it's rarely applied properly to firewalls. It's treated as a configuration hassle. But it's a critical control that limits the blast radius if any single account is compromised.
You'd also want to separate firewall management access based on organizational needs. Perhaps your headquarters firewall is managed by a specific team. Your branch office firewall is managed by a different team. If the branch office team's credentials are compromised, the attacker gets branch office access, not the main firewall. It limits lateral movement.
Backup and Disaster Recovery for Firewall Configurations
If your firewall is compromised and modified, can you restore it to a known good state? Probably not, because most organizations don't regularly back up their firewall configurations.
This is a glaring oversight. Your firewall's configuration is critical infrastructure. It defines your entire network security posture. If it's modified by an attacker, you need to restore it to a previous version immediately. But if you don't have backups, you're rebuilding from memory or documentation that's probably out of date.
Start backing up your firewall configurations regularly. Daily is ideal. Store backups in a secure location separate from your firewall. Use encryption for backups. Version them so you can compare the current configuration to previous versions and identify what changed.
Also test your restore procedures. You need to know that if you need to restore a firewall configuration from backup, you can do it quickly and correctly. If you've never tested it, you're gambling that it'll work in an emergency. It probably won't.
For ransomware recovery specifically, having a clean backup of your firewall configuration means that even if every system on your network is encrypted, you can restore the firewall to a known good state and begin recovery operations. That's not a small thing.

Vendor Communication and Threat Intelligence
Your firewall vendor knows about new vulnerabilities before you do. But only if you're on their mailing list and actually paying attention.
Most firewall vendors maintain security bulletins, RSS feeds, or email notifications for critical vulnerabilities. You should have at least one person on your team subscribed to these. When a critical vulnerability affecting your specific firewall model is published, you should know about it within hours, not weeks.
You should also maintain relationships with your vendor's security team. If something feels off with your firewall, reach out. If you're seeing unexplained network behavior, reach out. Vendors often have threat intelligence about emerging attacks against their products and can tell you if you're at risk.
The bigger picture: threat intelligence on ransomware groups and attack patterns. Subscribe to reports from reputable security research firms. These reports highlight which vulnerabilities are being actively exploited, which firewall models are being targeted, and what the attack patterns look like. It's an early warning system.
If you hear that Fortinet firewalls are being targeted by a specific group, you know to check your own Fortinet firewalls more carefully, ensure they're patched, and monitor for suspicious activity. Intelligence becomes defense.

Network Segmentation: Not Putting All Your Trust in One Firewall
Here's a heretical thought: maybe we shouldn't trust firewalls to be the only thing protecting our networks.
If a firewall is compromised, everything behind it is at risk. That's the game-theoretical reality. So what if, instead of having one powerful firewall, you had multiple security layers?
Network segmentation splits your network into zones. The perimeter firewall protects the internet-facing edge. Internal firewalls protect different segments from each other. Maybe your database servers are in a segment that can only be accessed by your application servers. Maybe your file shares are in a different segment. Maybe your production environment is segmented from your development environment.
If the perimeter firewall is compromised, lateral movement is harder. The attacker can't just pivot from the internet-facing network to internal systems. They hit another firewall that's equally hardened.
This isn't just a technical control. It's an acknowledgment that any single device can fail. Treat firewalls like you treat airplane engines: you want redundancy and layered defense. If one fails, the system still functions.
Segmentation also helps with incident response. If you discover an internal compromise, you can isolate affected segments and prevent lateral spread. It contains the damage.
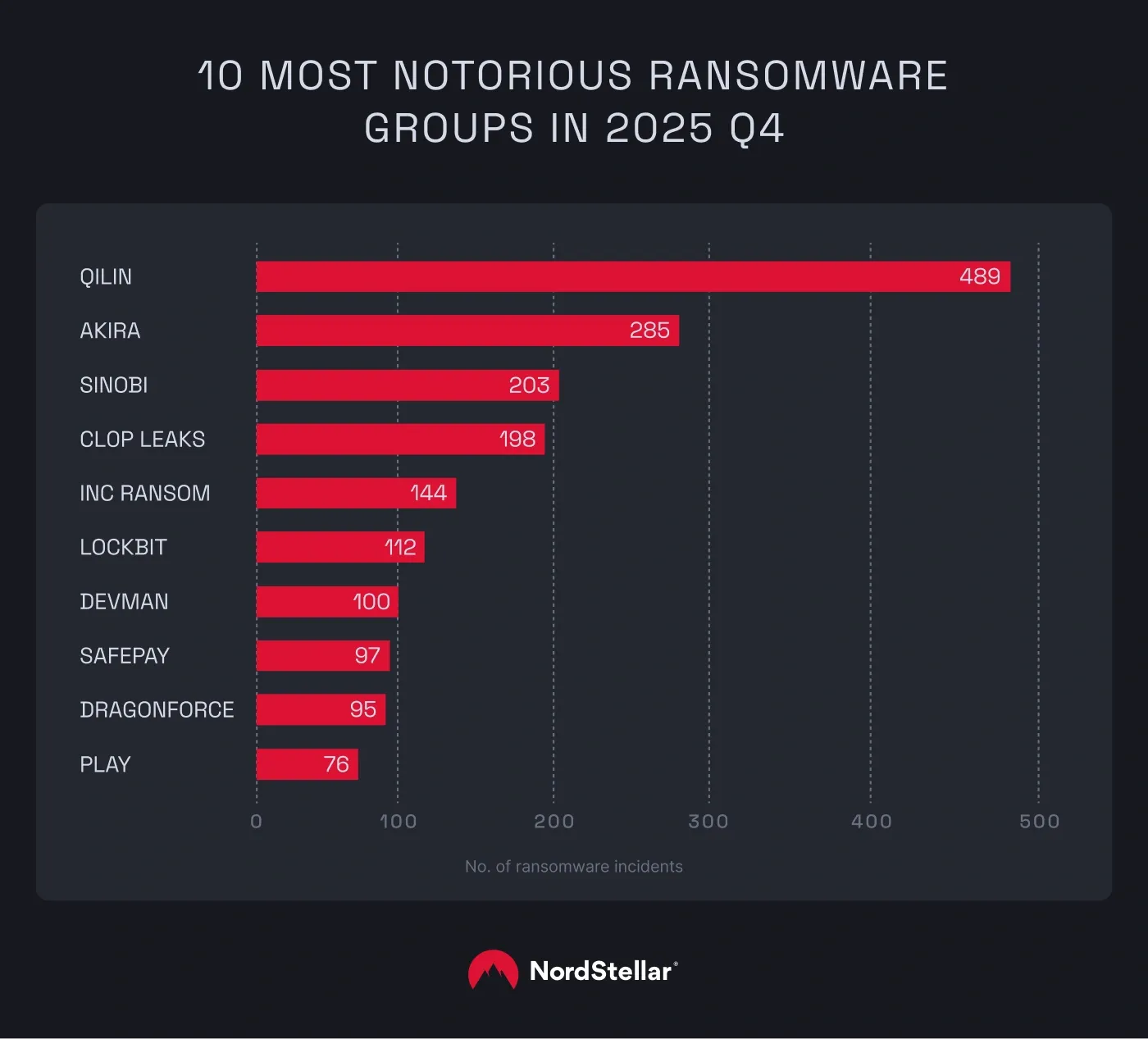
The Human Factor: Training and Awareness
All the technical controls in the world don't matter if your firewall team doesn't understand why security matters.
Many firewall teams are operations-focused. Their job is uptime. Their bonus is based on system availability. From their perspective, patching or implementing new security controls is a threat to their primary objective. It introduces risk of downtime.
Changing this requires education and culture shift. Your firewall team needs to understand that a ransomware incident isn't a theoretical risk. It's happening, right now, to organizations like theirs. They need to understand their role in prevention. They need to understand that a few hours of planned downtime for patching beats weeks of actual downtime from a compromise.
You also need to ensure that credentials aren't shared. Firewall access should be individual. Everyone logs in with their own account, so actions can be traced to a specific person. Shared accounts hide accountability and make it harder to detect when a shared credential is compromised.
And you need to foster a culture where security concerns can be raised without being shot down. If a network operations engineer notices something weird with the firewall, they should feel empowered to report it without worrying that reporting it will be seen as a weakness or a threat to their job.
This is the unglamorous work. Nobody writes case studies about "we trained our team really well and nothing bad happened." But prevention is always less exciting than response. And that's the point.

Looking Forward: The Evolution of Firewall Threats
Ransomware as an industry isn't static. It evolves. As firewalls get better security protections, attackers will evolve their tactics.
We're already seeing hints of this. Ransomware groups are moving away from brute-force approaches toward more surgical, targeted attacks. Instead of mass scanning for vulnerable firewalls, they're targeting specific organizations based on intelligence about their infrastructure. They're combining firewall attacks with supply chain compromise, where they target the vendors or contractors that integrate with those firewall models.
We're also seeing more sophisticated attacks that exploit combinations of vulnerabilities. Maybe a firewall flaw combined with a weak credential combined with a missing security control. No single issue is catastrophic, but together they create a breach chain.
Organizations that wait to address firewall security until they're compromised will find themselves playing catch-up in an adversary-advantaged game. The time to act is now.

Conclusion: The Firewall Security Imperative
Your firewall is under attack. Not tomorrow. Today. Right now. Somewhere, a threat actor is scanning for your specific model, checking for known vulnerabilities, trying default credentials.
The Barracuda report makes this unmistakably clear: 90% of ransomware incidents in 2025 exploited firewalls. That's not a prediction or a warning about what might happen. It's what's actually happening in real networks, right now, in your industry.
The good news is that most of these compromises are preventable. Not difficult. Not expensive. Preventable.
Patch your firewalls. Use the best judgment you can about balancing operational uptime against security risk. Quarterly patches are a minimum. Critical patches should be expedited. Yes, it requires planned downtime. That downtime is insurance.
Enable multi-factor authentication on every administrative account. Make it standard practice. Yes, it adds a step to the login process. That extra step stops compromised credentials from being useful.
Monitor your firewalls aggressively. Log administrative access. Alert on configuration changes. Investigate anomalies. If someone is inside your firewall doing things they shouldn't be, you want to know in minutes, not months.
Implement the principle of least privilege. Nobody needs full access to everything. Compartmentalize permissions. Limit the damage if any single account is compromised.
Back up your firewall configurations regularly and test your restore procedures. In the event of a compromise, a clean backup means you can recover quickly.
Segment your network so that if the perimeter firewall is compromised, internal systems aren't immediately accessible. Layers of defense are always better than a single wall.
Educate your team about why this matters. Make security part of the culture, not a compliance checkbox.
Do these things, and you've eliminated 90% of the attack surface that ransomware groups are currently exploiting. You're no longer the easy target. You're the hard problem.
And that's usually enough. Attackers are economically motivated. If you're harder than the organization next to you, they'll target the organization next to you instead. Security, especially firewall security, is sometimes just about not being the slowest antelope in the herd.
But here's the thing: you're never truly done. Threats evolve. New vulnerabilities emerge. Yesterday's hardened firewall might be vulnerable tomorrow. Security is a practice, not a destination. It requires continuous monitoring, continuous learning, and continuous improvement.
The organizations that survive ransomware attacks aren't usually the ones with the most sophisticated defenses. They're the ones that understand that threats are evolving faster than solutions. They're the ones that patch promptly, monitor aggressively, and treat security like it actually matters. They're the ones that treat their firewall not as a commodity network appliance, but as the critical infrastructure it actually is.
Your firewall is your first line of defense. Defend it like you mean it.

FAQ
What percentage of ransomware incidents exploit firewall vulnerabilities?
According to Barracuda's 2025 analysis of over 2 trillion IT events and 600,000 security alerts, 90% of all ransomware incidents in 2025 exploited firewalls, either through known vulnerabilities or compromised credentials. This makes firewall compromise the dominant attack vector for ransomware deployment.
How old are the vulnerabilities being exploited in firewall attacks?
Barracuda's research found that CVE-2013-2566, a vulnerability discovered in 2013 affecting an outdated encryption algorithm, was among the most actively exploited. This demonstrates that attackers prioritize easily exploitable vulnerabilities in legacy systems, often targeting flaws that predate modern security practices by over a decade.
What is the most common initial compromise vector for firewalls?
Firewall compromises typically occur through a combination of known vulnerabilities that haven't been patched, weak or default credentials that were never changed, and compromised administrative accounts from previous data breaches. Organizations that delay patching, fail to enforce strong authentication, and don't monitor administrative access create the conditions for successful attacks.
Why are firewalls becoming prime targets for ransomware groups?
Firewalls are attractive targets because they control all network traffic and provide gateway access to entire infrastructure once compromised. Unlike endpoints, which are defended by EDR tools and multiple security controls, firewalls are often treated as stable infrastructure with minimal monitoring. A compromised firewall grants attackers administrative visibility into the entire network.
What specific Fortinet and Sonic Wall vulnerabilities have been actively exploited?
Sonic Wall firewall appliances with SSL-VPN enabled across multiple generations were actively targeted by the Akira ransomware group in late 2025, compromising more than 100 SSL-VPN accounts across approximately 16 customer environments. Fortinet Forti Gate devices have also been hit by automated attacks creating rogue administrative accounts and stealing firewall configuration data.
How should organizations prioritize firewall security remediation?
First priority: patch your firewall immediately if your model has known critical vulnerabilities. Second priority: implement multi-factor authentication on all administrative accounts. Third priority: centralize and monitor all firewall administrative logs and configuration changes. Fourth priority: segment your network so that perimeter firewall compromise doesn't automatically expose internal systems. These steps address 90% of current attack vectors.
What is the cost-benefit analysis for planned firewall patching?
A few hours of planned downtime for quarterly firewall patches has a negligible business impact. A ransomware incident affecting your entire network has catastrophic impact: weeks to months of downtime, millions in recovery costs, data exposure and regulatory penalties, reputational damage, and potential business closure. The cost-benefit analysis overwhelmingly favors scheduled patching.
What role does multi-factor authentication play in preventing firewall compromise?
MFA prevents attackers who have obtained administrative credentials from logging in without also having the second factor device or authentication code. Since many firewall compromises occur through stolen credentials rather than fresh exploits, MFA eliminates this attack vector entirely. Organizations without MFA on firewall accounts accept a significant preventable risk.
How long after firewall compromise do attackers typically deploy ransomware?
The timeline varies significantly. Some attackers deploy ransomware within hours of gaining access, while others maintain access for weeks or months before striking. This "dwell time" allows attackers to study your network, identify valuable targets, steal sensitive data for extortion, and ensure their ransomware deployment will succeed. Early detection is critical because it interrupts this timeline before damage occurs.
What should be backed up to recover from firewall compromise?
Regular backups of your firewall configuration are essential. Store backups separately from the firewall itself using encryption. Version your backups so you can identify what changed when a compromise occurred. Test your restoration procedures regularly so you know the backup is valid and can be restored quickly. In a ransomware incident, a clean firewall backup allows you to restore the device to a known good state and begin network recovery operations.
How can network segmentation help with firewall security?
Network segmentation creates multiple security zones so that if the perimeter firewall is compromised, internal firewalls still protect sensitive systems. An attacker who breaches the edge firewall hits another hardened firewall protecting your database servers. Segmentation also contains lateral movement, limiting damage if any single segment is compromised. It's defense in depth applied to the network architecture itself.
The Bottom Line: Your Firewall Security Roadmap for 2025
You now understand the scope of the threat. Ransomware is targeting firewalls at unprecedented scale because it works. But you also understand the solutions, most of which are straightforward to implement.
If you implement nothing else: patch your firewalls on a regular schedule, enable MFA on administrative accounts, and monitor for suspicious activity. These three controls address the vast majority of active attacks. Everything else builds on this foundation.
Start today. Check when your firewall was last patched. Check if MFA is enabled. Check your monitoring and alerting. One of these is probably broken. Fix it first. Then the next. Then the next.
Your firewall is the gateway to your network. Secure it like it actually matters. Because it does.
Key Takeaways
- 90% of ransomware incidents in 2025 exploited firewall vulnerabilities, according to Barracuda's analysis of 2 trillion IT events
- The oldest actively exploited vulnerability is 13 years old, proving attackers target easy prey with unpatched legacy systems
- Firewall compromise grants attackers administrative access to entire network infrastructure, not just that device
- One in ten detected vulnerabilities have public exploits available, making them immediately weaponizable
- Ransomware groups reached record numbers in 2025 with victim counts doubling year-over-year
- Patch management, MFA, and centralized monitoring are the three controls that prevent 90% of firewall compromises
- Network segmentation limits damage when perimeter firewall is compromised, protecting internal systems
- Firewall credentials stolen from previous data breaches are actively exploited in brute-force attempts
Related Articles
- DJI Romo Hack: How One Loophole Exposed a Global Robot Army [2025]
- Dell Zero-Day Vulnerability: Hardcoded Credentials Exploited for 2 Years [2025]
- TP-Link Texas Lawsuit: Chinese Hackers, Security Lies, and What It Means [2025]
- Netgear Nighthawk M7 5G Router Review [2025]
- Japanese Hotel Chain Hit by Ransomware: What You Need to Know [2025]
- Tenga Data Breach 2025: How a Phishing Email Exposed Customer Data
![Ransomware Targeting Firewalls: The Critical 2025 Security Crisis [2025]](https://tryrunable.com/blog/ransomware-targeting-firewalls-the-critical-2025-security-cr/image-1-1771515377459.jpg)



