Introduction: When a Single Click Compromises Millions
It started with an email. Not a suspicious-looking one from a Nigerian prince or a broken grammar scam. Just a phishing email that looked legitimate enough to fool a Tenga employee, and that's all it took.
On the surface, Tenga seems like an unlikely target for a sophisticated cyberattack. The Japanese manufacturer of sexual wellness products operates quietly, ships over 100 million units annually, and maintains roughly $67 million in yearly revenue across global markets spanning Asia, Europe, and North America. But that's exactly why this breach matters. It wasn't a flashy hack into encrypted servers or a zero-day exploit against hardened infrastructure. It was something far more insidious: a single employee falling for social engineering, which then cascaded into one of the most revealing breaches of recent memory.
The attacker didn't need to be a world-class hacker. They needed to be patient, convincing, and understand human psychology better than they understood code. And they succeeded spectacularly.
What makes the Tenga breach particularly instructive isn't just that it happened, but how it happened and what it exposed. Customer names, email addresses, and historical correspondence containing order details and customer service inquiries were compromised. The attacker didn't just steal data and disappear into the dark web. They used the compromised inbox to send spam to both employees and customers, turning a data breach into an active ongoing attack vector.
For security teams managing anything remotely sensitive, this breach reads like a case study in how fundamental security practices still fail at scale. Multi-factor authentication (MFA) hadn't been universally deployed. Phishing training apparently hadn't stuck. Inbox monitoring and anomalous access patterns went undetected long enough for meaningful data exfiltration to occur.
This article breaks down exactly what happened at Tenga, why it happened, what data was compromised, and most importantly, what you and your organization can do to avoid the same fate.
TL; DR
- The Attack Vector: A phishing email successfully targeted a Tenga employee, granting attackers access to their email inbox
- Data Compromised: Customer names, email addresses, order details, and customer service correspondence were exfiltrated
- Scope of Impact: Unclear exactly how many customers were affected, but the breach affected global markets across multiple countries
- Attacker Activity: Beyond theft, the attacker sent spam messages to employees and customers from the compromised inbox
- Company Response: Tenga reset credentials, enabled MFA, and advised customers to refresh passwords and remain vigilant
- Key Takeaway: A single employee falling for social engineering can compromise an entire customer database, making employee training and MFA deployment critical

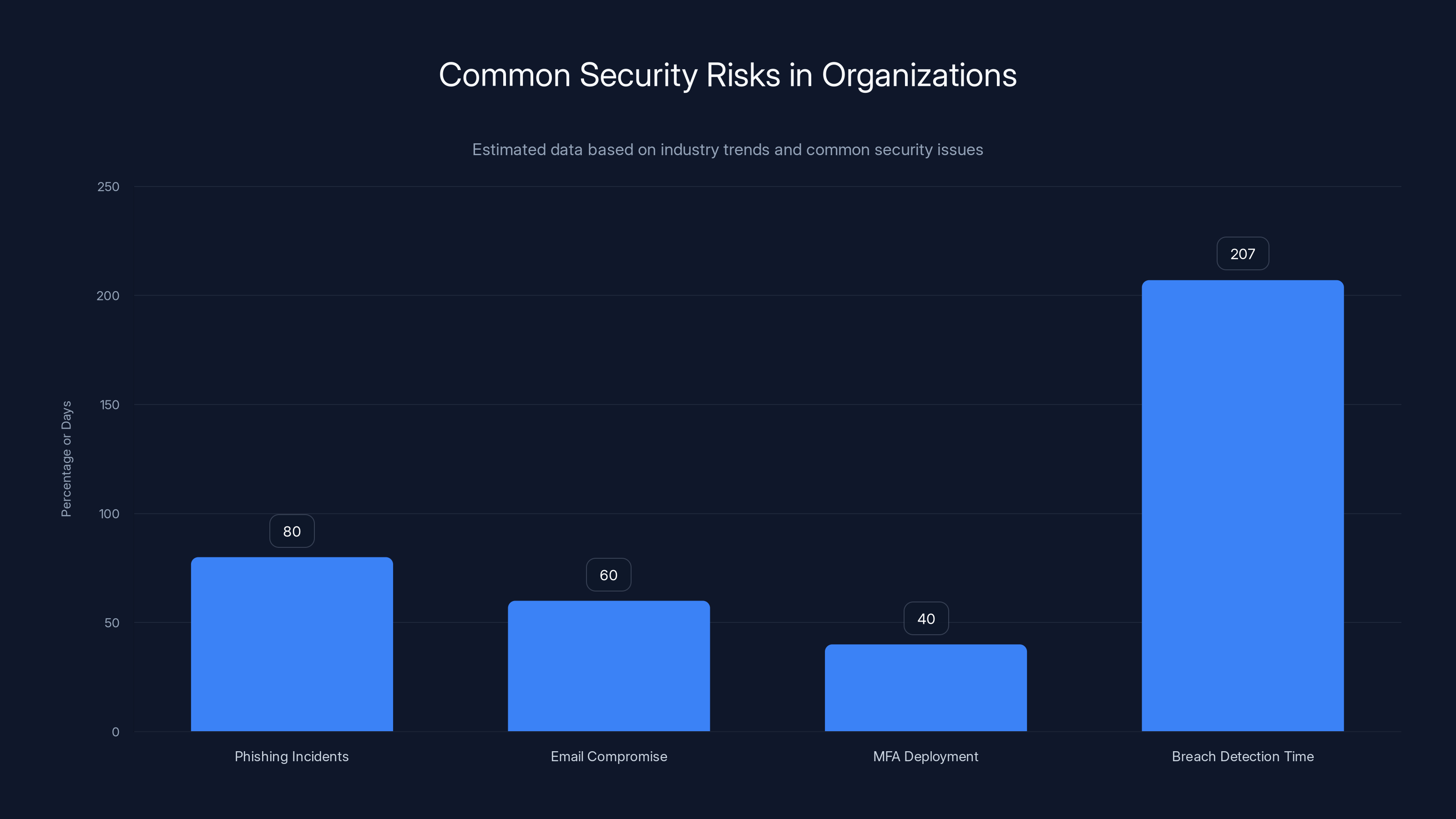
Phishing accounts for 80% of security incidents, while email compromises are rising. MFA deployment is inconsistent, and average breach detection time is 207 days. Estimated data.
Understanding the Tenga Breach: The Full Timeline
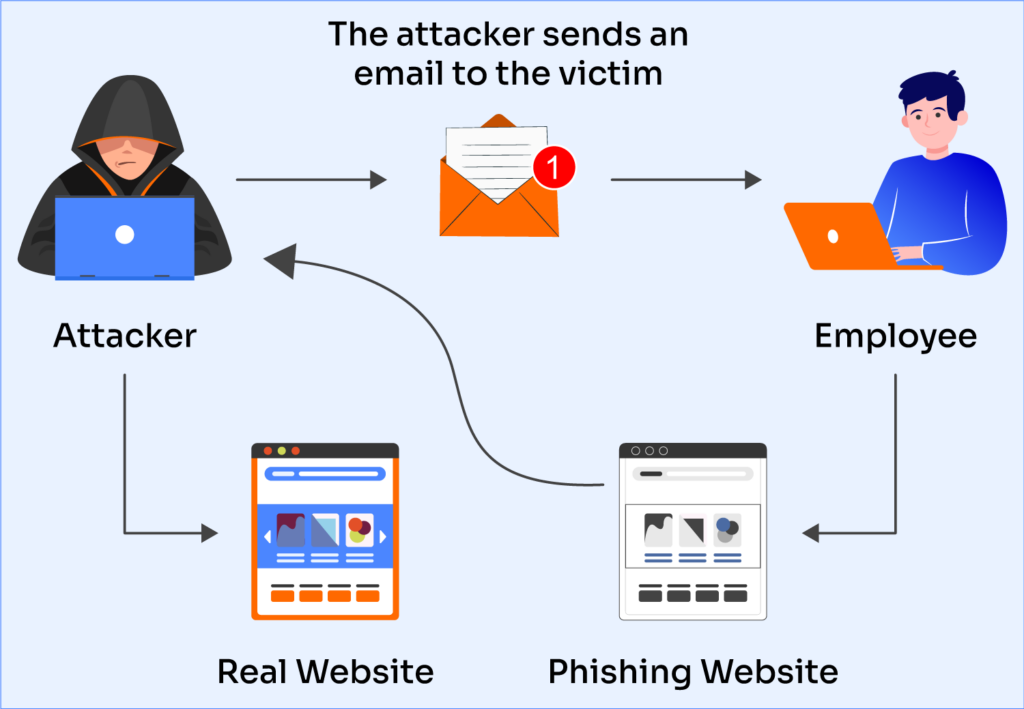
The Tenga data breach began not with a bang, but with a click. An employee, whose role in the company wasn't disclosed, received a phishing email. The email was convincing enough that they either entered their credentials into a fake login page or downloaded and executed a malicious attachment. Without knowing the exact method, we can infer it was successful enough that the attacker gained legitimate access to the employee's email account.
Once inside that inbox, the attacker had access to everything flowing through that account. Depending on the employee's role and permissions, this could include sensitive customer data, internal communications, and other proprietary information. The attacker didn't waste time. They systematically exfiltrated customer names, email addresses, and historical correspondence that included order details and customer service inquiries.
What's particularly damaging about email account compromise is the dual nature of the attack. The data theft is bad enough, but the attacker had access to a legitimate communication channel. They used this to send spam messages impersonating Tenga to both employees and customers. This turns a confidentiality breach into an active, ongoing threat vector. Customers might receive phishing emails they believe came from Tenga. Employees might receive fraudulent communications they trust.
Tenga discovered the breach at an undisclosed point after initial compromise. The company's response was methodical: they reset the compromised user's credentials, enabled multi-factor authentication, and sent notification letters to employees and customers explaining the situation and recommending password resets.
However, several critical questions remain unanswered. How long was the attacker inside the system before detection? How much data was actually exfiltrated? How many customers were affected? Was the attacker identified? Did they sell the data, publish it, or keep it for future use? The lack of transparency in Tenga's public statements suggests either ongoing investigations, negotiation, or simply poor communication.
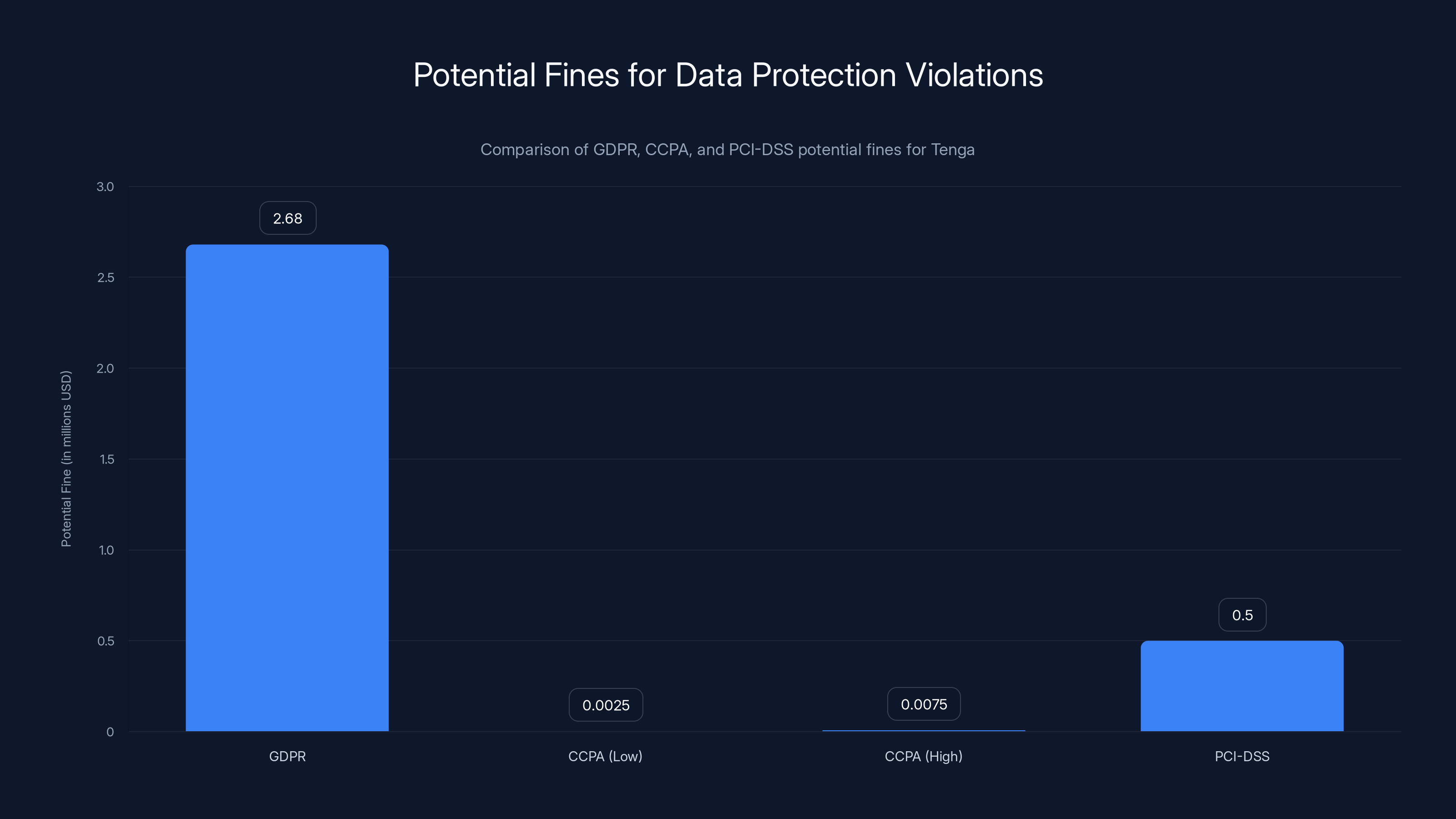
GDPR fines could reach up to
How Phishing Actually Works: The Psychology Behind the Click
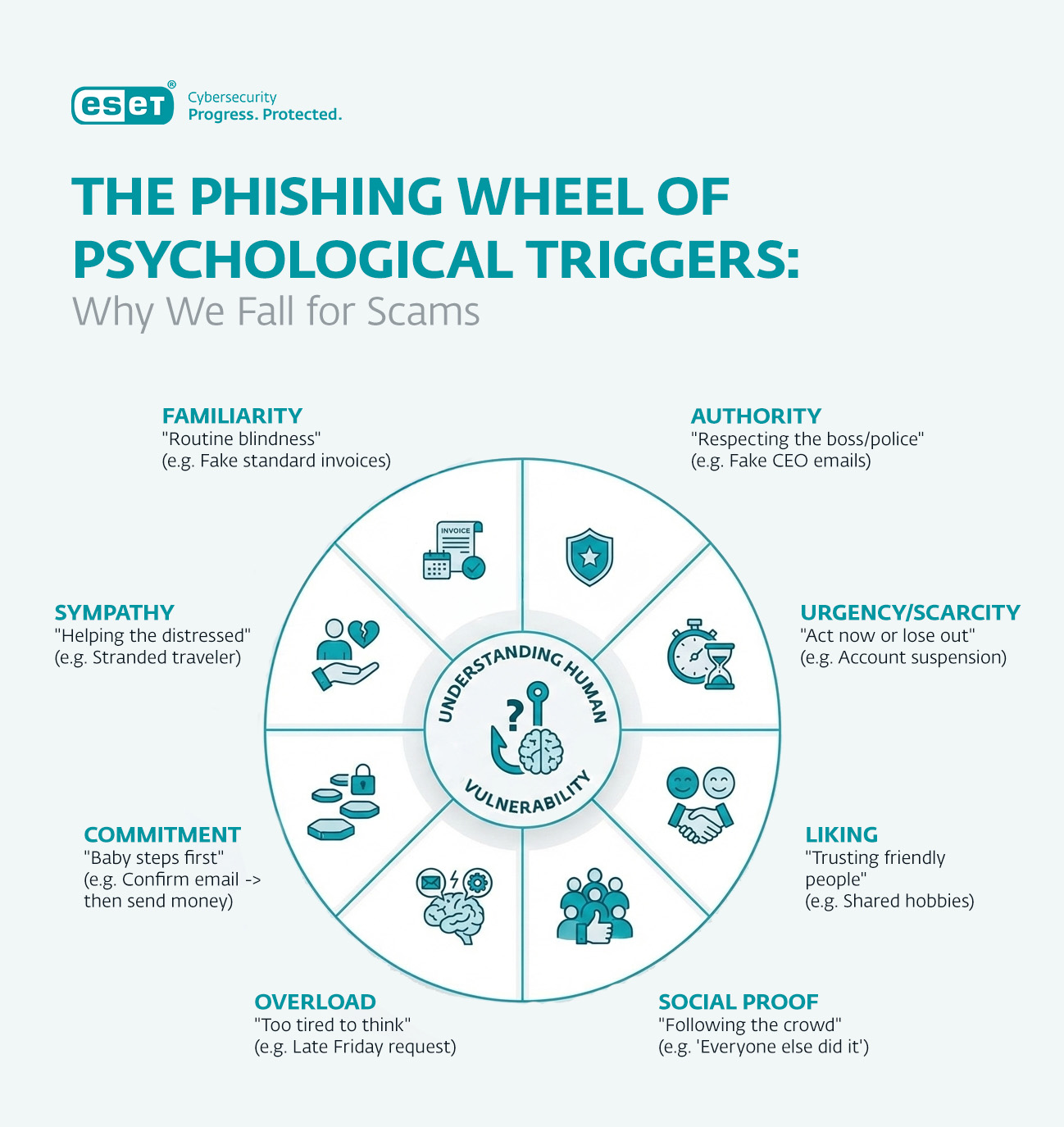
Phishing gets treated as a technical problem, but it's fundamentally a psychology problem. The attacker didn't need to exploit a zero-day vulnerability. They needed to understand what would make a Tenga employee trust an email enough to take action.
Modern phishing is sophisticated. Attackers use email spoofing to make messages appear to come from trusted sources. They might impersonate internal IT departments requesting urgent password updates. They might pose as executives requesting urgent wire transfers. They might pretend to be security teams conducting "verification." The success rate depends entirely on how convincingly they can trigger the right emotional response: urgency, fear, curiosity, or compliance.
In Tenga's case, we don't know the exact phishing message. But we can infer it was compelling enough to bypass whatever training and awareness the employee had received. This is important because it suggests that generic security training isn't sufficient. Most employees sit through annual security awareness modules that feel disconnected from their actual work. A phishing email that mimics something they actually interact with (password reset flows, team communications, vendor requests) will outperform generic warnings.
The success rate of phishing attacks globally hovers around 3-5%, which sounds low until you realize that most organizations have hundreds or thousands of employees. In a company with 50-200 employees like Tenga, even a 3% click rate means you're likely to have at least one person falling for a targeted attack. The attacker in this case only needed one.
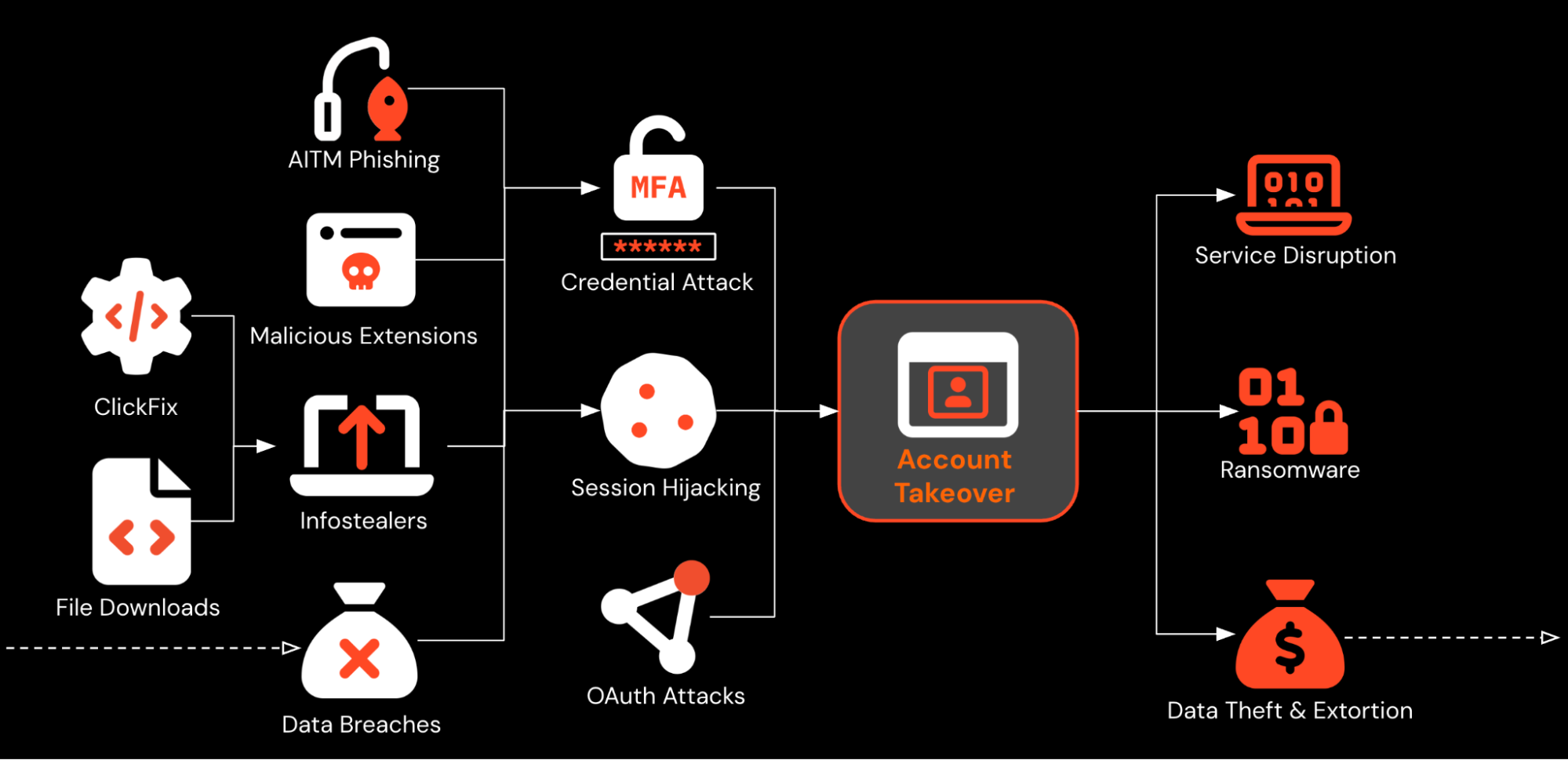
What makes phishing particularly insidious is that it combines several threat vectors simultaneously. First, there's the initial compromise via credential theft or malware installation. Second, there's the lateral movement phase where the attacker explores what they have access to. Third, there's the data exfiltration phase. And fourth, there's the post-breach activity phase where they continue using the compromised account for spam, additional attacks, or data sale.
Tenga's case involved all four phases. They only detected the compromise after phases one through three were already complete, which is typical. Most organizations discover breaches weeks or months after initial compromise.
The Data That Was Stolen: What Exactly Was Compromised
Tenga's breach notification letter lists several categories of compromised data, and understanding what each category means is crucial for assessing the actual risk.
Customer Names and Email Addresses
This seems basic, but customer names and emails are the foundation of targeted phishing attacks. An attacker with this information can craft convincing follow-up emails impersonating Tenga or other trusted brands. They can target customers with social engineering, claiming there's an issue with their account or payment method. They can sell the list to spammers or other criminals. They can use it for traditional identity theft or account takeover attacks against customers' other online accounts.
Order Details
This is where the breach becomes particularly invasive. Order details reveal what customers purchased. For a sexual wellness manufacturer, this means intimate details about customer preferences. This information is valuable not just for fraud purposes, but because it enables highly targeted phishing and social engineering. An attacker can contact a customer claiming there's an issue with their "recent order" of a specific product, asking them to "verify" their payment information. The specificity makes the attack far more convincing.
Customer Service Inquiries
Customer service correspondences are a goldmine of personal information. These emails might contain payment information, shipping addresses, phone numbers, answers to security questions, personal health information (if customers discussed issues or requests), and narrative details about the customer's life and interests. Someone contacting customer service about a product might reveal far more than they'd share on a public profile.
The Spam Phase
After exfiltrating this data, the attacker sent spam to both employees and customers. This serves multiple purposes. First, it confirms that the attack worked and that communications can be sent from a trusted sender. Second, it's a crude way to monetize the breach if the spam includes affiliate links or malicious domains. Third, it damages Tenga's reputation, as customers receive spam they believe came from Tenga. Fourth, it tests which employee and customer addresses are active, which information can be resold more confidently.
The true scope of what was compromised remains unclear. Tenga hasn't disclosed the number of affected customers or the exact timeframe of the compromise. This lack of transparency is frustrating but also typical. Companies often under-report breach scope to minimize regulatory consequences and reputation damage.
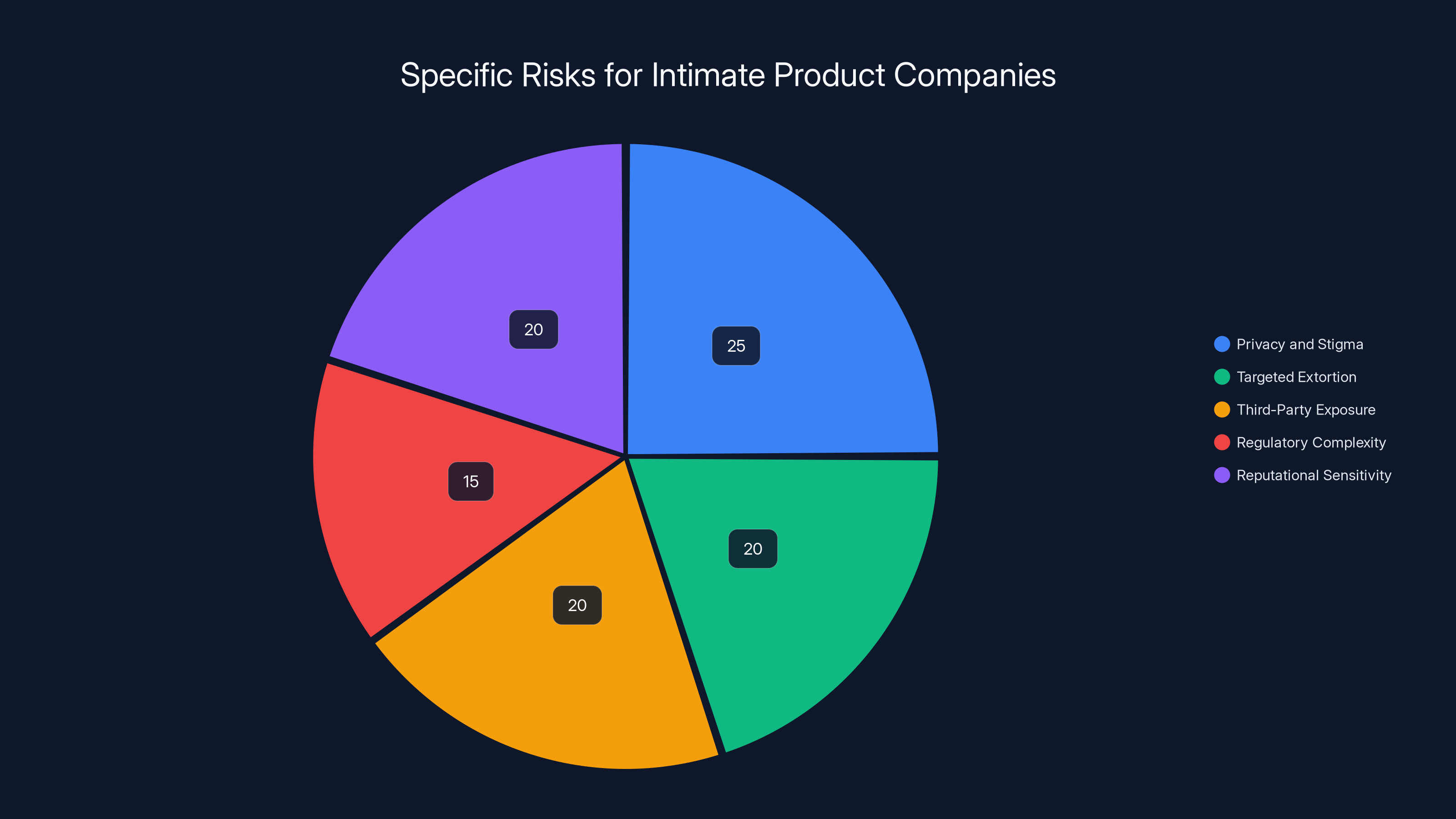
Privacy and stigma, along with targeted extortion, represent significant risks for intimate product companies, each accounting for around 20-25% of the overall risk profile. (Estimated data)
Why Tenga's Security Posture Failed: The Missing Layers
Every organization has layers of security. When one layer fails, the others should catch the attack. At Tenga, multiple layers failed simultaneously.
Layer 1: Phishing Detection and Prevention
Most organizations use email security gateways that scan incoming messages for phishing indicators. These systems look for suspicious sender addresses, domain spoofing, unusual reply-to headers, malicious links, and attachment types. However, sophisticated phishing emails can bypass these systems, especially if they target specific individuals with customized messages based on public information about that person or their role.
Tenga apparently didn't have effective phishing detection in place, or the specific phishing email wasn't detected as malicious. Given that Tenga is a relatively small company with 50-200 employees, they might not have invested in enterprise-grade email security infrastructure.
Layer 2: Employee Security Training
Security awareness training is the human firewall. When done well, it teaches employees to recognize phishing tactics, verify sender identities, and report suspicious emails. When done poorly (which is most of the time), it's a checkbox exercise that employees forget within days.
Tenga apparently had some level of training (given that they responded to the breach with technical controls), but it clearly wasn't effective enough to stop this particular attack. This could mean the training was generic rather than role-specific, or it could mean the phishing email was particularly well-crafted and targeted.
Layer 3: Multi-Factor Authentication (MFA)
This is where Tenga's failure becomes most glaring. The company only enabled MFA in response to the breach, which means it wasn't universally deployed beforehand. If MFA had been mandatory, the attacker's stolen credentials would have been useless without access to the employee's second factor (phone, hardware key, app). The attacker might have still gotten the credentials, but they couldn't have actually logged in.
Tenga's lack of universal MFA deployment is indefensible in 2025. This is basic hygiene for any organization handling customer data. The fact that they had to be breached to implement it suggests a reactive rather than proactive security posture.
Layer 4: Inbox Monitoring and Anomalous Access Detection
A modern email system should detect when an account is accessed from a new location, at unusual times, with unusual patterns (like mass forwarding or large exports). Tenga either didn't have these monitoring systems in place, or they weren't configured to alert on suspicious activity. If they had been, they might have detected the attacker exfiltrating data and prevented the spam phase.
Layer 5: Data Segmentation and Access Controls
Why did a single employee's email account have access to the entire customer database? Even if the attacker compromised that account, the damage should have been limited by proper access controls. The attacker should have needed additional credentials or permissions to access customer data. The fact that they could exfiltrate everything from a single compromised inbox suggests inadequate data segmentation.
This is a common problem in small to mid-sized organizations that grow quickly. Access controls evolve organically rather than by design. Someone gets permission to do their job, and that permission includes access to far more data than necessary. When they stay in that role or get promoted, the access persists.
The Attack Lifecycle: From Compromise to Detection
Understanding the complete lifecycle of the Tenga breach helps explain why it succeeded and what warning signs were probably missed.
Stage 1: Reconnaissance (Unknown Duration)
Before sending the phishing email, the attacker likely researched Tenga employees. They might have found names on the Tenga website, LinkedIn profiles, or job posting sites. They studied how Tenga communicates internally and externally. They might have researched the employee they targeted specifically, learning about their role and responsibilities. This reconnaissance phase could have taken anywhere from days to months.
Stage 2: Phishing Delivery (Specific Date Unknown)
The attacker sent a phishing email to the target employee. Without knowing the exact content, we can speculate it was either a credential harvesting email (fake login page) or a malware delivery (malicious attachment). The employee clicked, entered credentials, or executed the attachment. This single action gave the attacker initial access.
Stage 3: Lateral Movement and Privilege Escalation (Days to Weeks)
Once inside the email account, the attacker explored what was available. They might have reset the password to maintain access. They might have set up email forwarding rules to stay informed about communications. They identified what data was accessible and where it was stored. If the employee had VPN access or access to internal systems, the attacker used those credentials to move laterally throughout the network.
Stage 4: Data Exfiltration (Days to Weeks)
The attacker began downloading customer data. This could have involved exporting contact lists, forwarding entire email conversations to external email accounts, or using data gathering tools. The amount of data exfiltrated likely wasn't enormous—even a few thousand customer records with associated order details and communications is massive. The attacker might have used encryption or compression to evade detection.
Stage 5: Post-Breach Activity (Unknown Duration)
The attacker sent spam using the compromised account. This served multiple purposes: testing the compromise, monetizing it, and damaging Tenga's reputation. The attacker might have also set up persistence mechanisms like rules in the email system or secondary accounts to maintain access even if the primary compromise was discovered.
Stage 6: Detection and Response (Unknown Trigger)
Tenga eventually detected the compromise. This could have been triggered by customer complaints about spam, IT discovering unusual activity, or a security audit. The company's response was relatively standard: reset credentials, enable MFA, notify affected parties. However, the lack of transparency about detection methodology and timeline suggests either incomplete forensics or ongoing law enforcement involvement.
The most telling detail is that MFA wasn't enabled until after the breach. This means Tenga's security team understood the risk but didn't treat it as urgent until something bad happened. It's a pattern that repeats across organizations of all sizes.
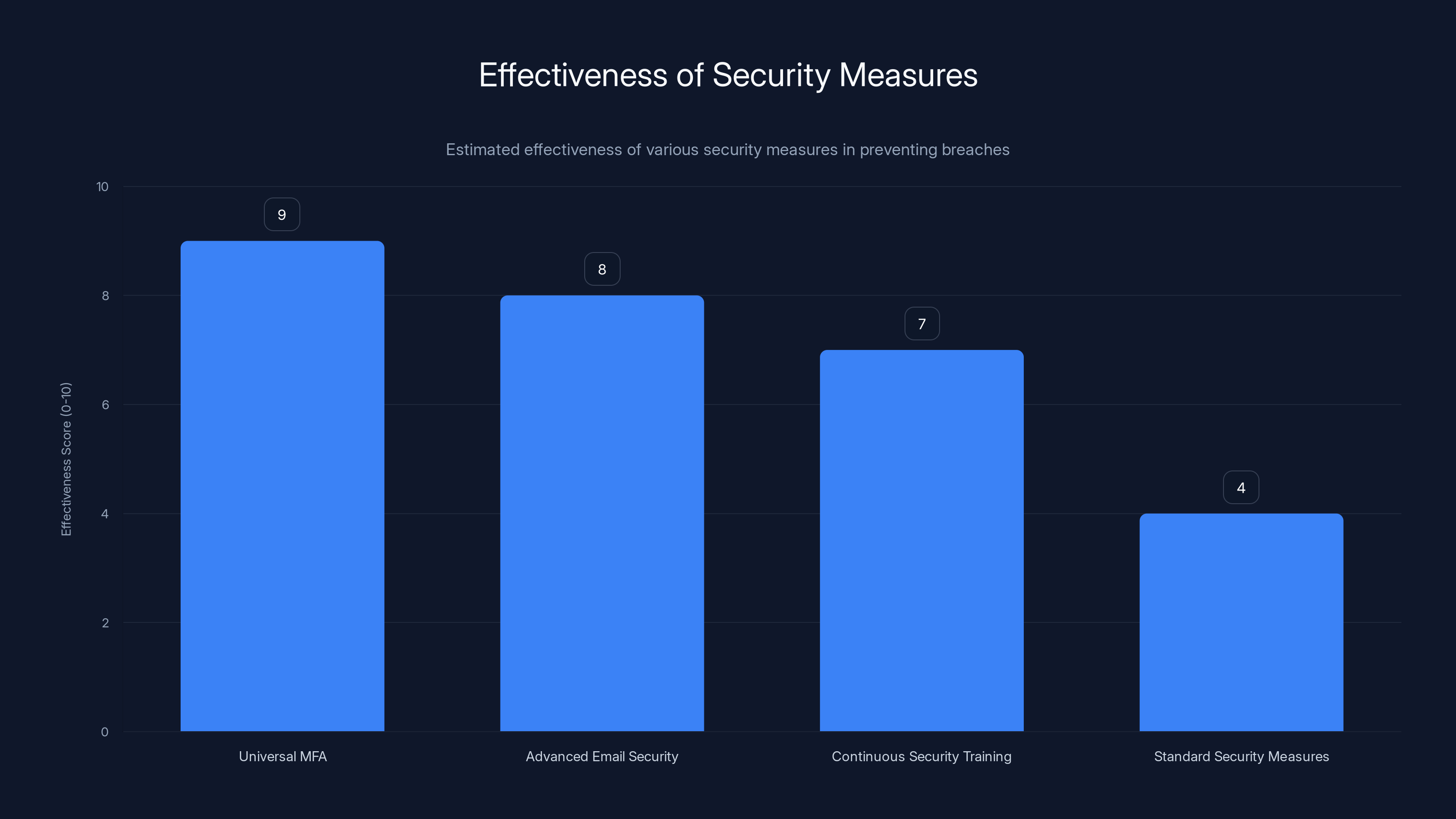
Implementing universal MFA and advanced email security are highly effective measures, scoring 9 and 8 respectively, in preventing breaches. Estimated data based on typical security assessments.
Tenga's Response: What They Did Right and Wrong
Tenga's response to the breach shows both competence and significant gaps.
What Tenga Did Right
First, they detected the breach and acknowledged it rather than hoping nobody noticed. Many companies try to quietly clean up breaches without public disclosure, which is both unethical and often illegal. Tenga sent breach notification letters to employees and customers, which aligns with regulatory requirements.
Second, they reset credentials for the compromised account and enabled MFA system-wide. These are appropriate remediation steps that prevent immediate re-compromise using the same credentials.
Third, they advised customers and employees to reset passwords and remain vigilant. This is basic but necessary guidance that makes sense given the nature of the breach.
Where Tenga's Response Falls Short
First, they didn't disclose the number of affected customers. This makes it impossible for customers to assess their personal risk. A breach affecting 100 customers is fundamentally different from one affecting 1 million customers, yet Tenga treats them the same way.
Second, they didn't explain how the breach was discovered or how long the attacker had access. This information is crucial for customers trying to understand whether their most recent orders or communications were compromised, or if the breach predates their account creation.
Third, they didn't announce enhanced security measures beyond MFA. What about email security tools? What about incident response procedures? What about forensics to ensure the attacker is completely removed? The response feels like the minimum required rather than demonstrating genuine commitment to security improvement.
Fourth, they didn't offer identity theft protection services or credit monitoring to affected customers. This is increasingly common after major breaches, especially those exposing payment information or customer service inquiries.
Fifth, they didn't explain why MFA wasn't universal before the breach. Acknowledging this oversight and committing to improved security governance would build more trust than pretending this was an unavoidable incident.
Tenga's response is typical of companies caught in a data breach: reactive rather than proactive, minimal transparency, and doing the bare legal minimum rather than going above and beyond to restore customer trust.
Industry Context: Is Tenga's Breach Unique?
Tenga's breach isn't an outlier. It's part of a pattern that repeats across industries and company sizes.
Phishing as the Primary Attack Vector
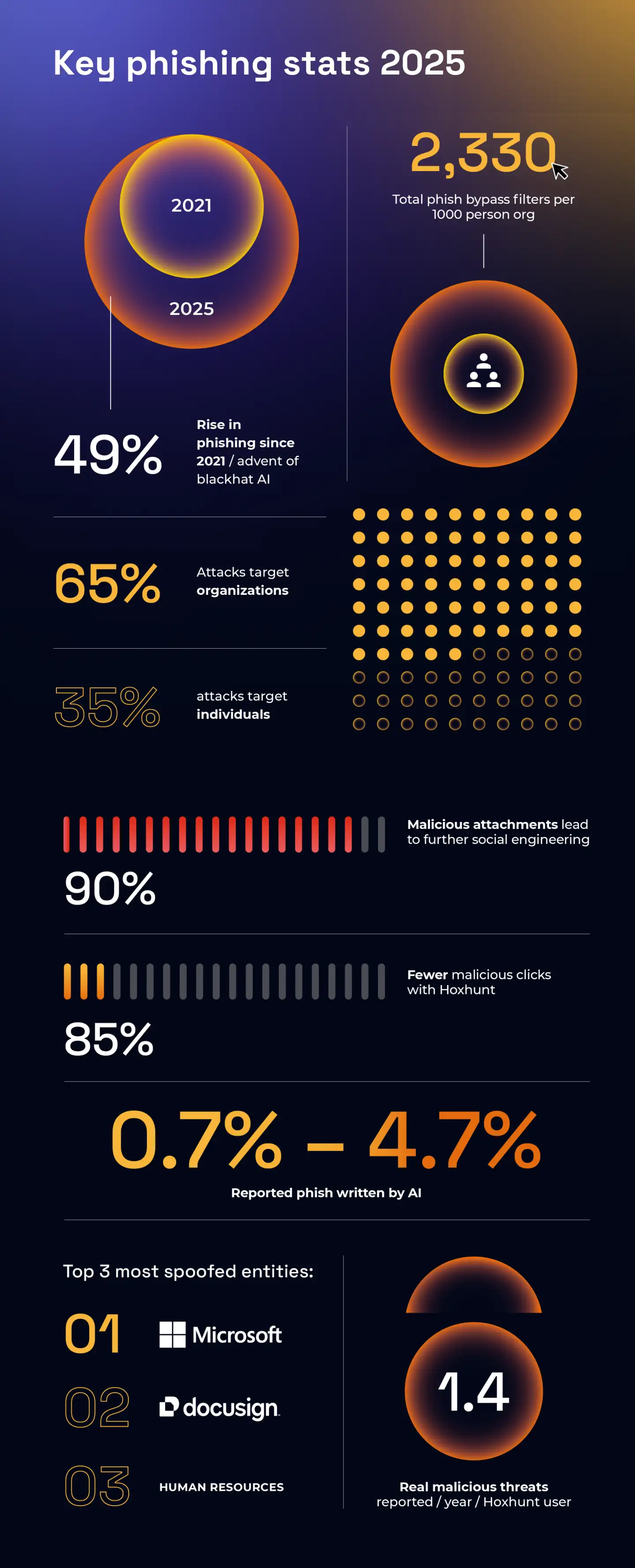
Phishing is responsible for approximately 80% of reported security incidents. Not sophisticated zero-day exploits, not insider threats, not supply chain compromises. Human error. A single employee making a single mistake. This statistic never changes year after year because fixing the problem requires sustained effort across multiple dimensions: technology, training, culture, and process.
Email Account Compromise as a Critical Risk
Email account compromise incidents have increased dramatically. A compromised email account is like stealing the master key to a building. Once inside, the attacker can access everything the account holder accessed, impersonate that person, and maintain persistent access through backup accounts and rules.
Small to Mid-Sized Organizations as High-Risk
Small organizations like Tenga (50-200 employees) typically have fewer security resources than enterprises but handle sensitive data just as extensively. They often lack dedicated security teams, proper access controls, and advanced threat detection. This makes them attractive targets for attackers: valuable data but minimal defensive capabilities.
Inconsistent MFA Deployment
MFA adoption has improved significantly over the past five years, but many organizations still don't require it universally. Finance and banking sectors have largely adopted MFA, but healthcare, manufacturing, and retail lag behind. Tenga's lack of universal MFA deployment before their breach wasn't unusual, but it was indefensible.
Delayed Breach Detection
Tenga's timeline for detection remains unclear, but the global average is still around 207 days. Some organizations detect breaches immediately; others discover them months later during security audits or when data appears on the dark web. Tenga likely discovered their breach through external indicators rather than internal monitoring.
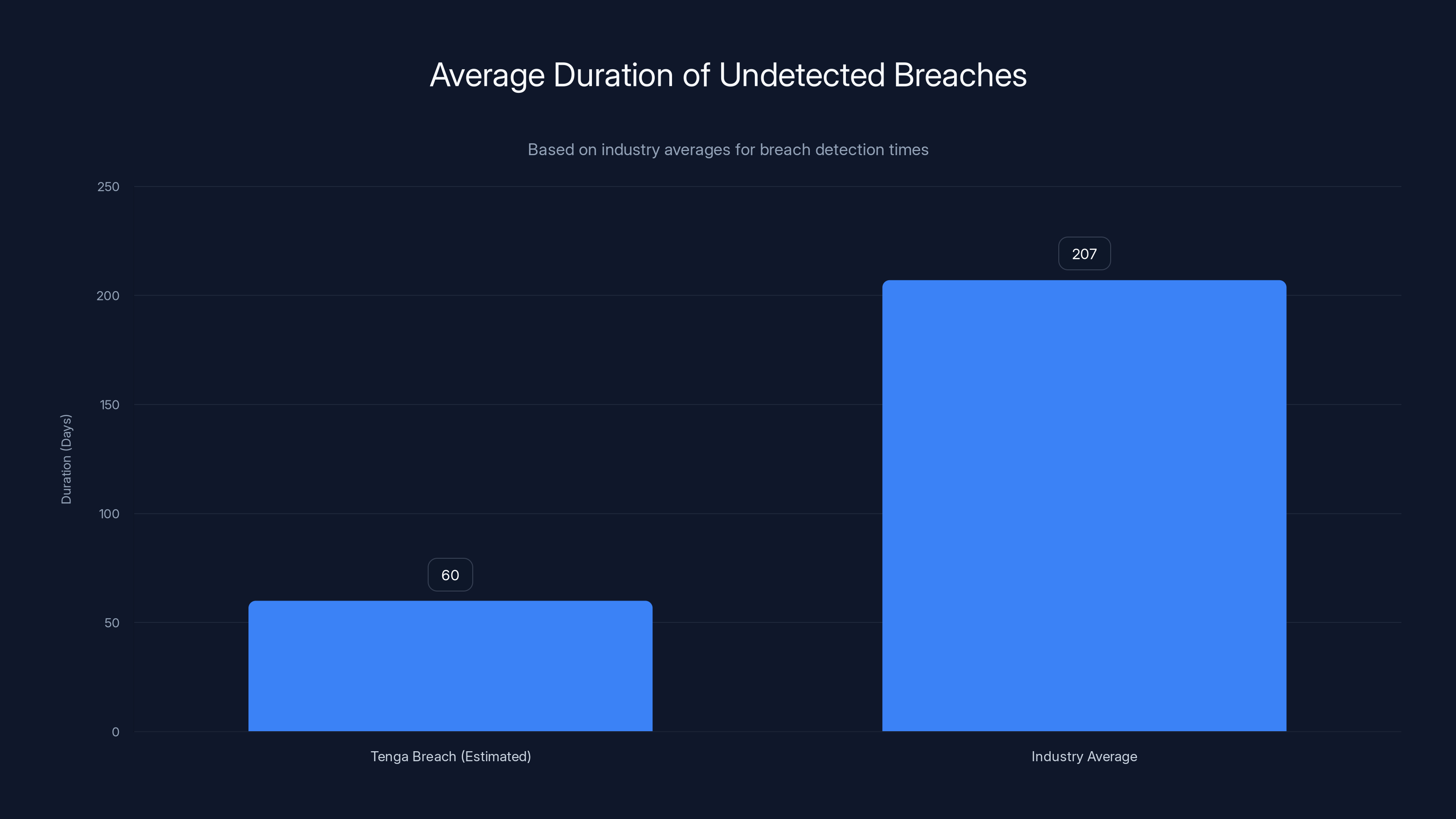
Estimated data suggests Tenga's breach went undetected for at least 60 days, compared to the industry average of 207 days. Estimated data.
Specific Risks for Intimate Product Companies
Tenga operates in a unique market segment that amplifies certain breach risks.
Privacy and Stigma
Customers of sexual wellness products face stigma and privacy concerns that don't apply to customers of, say, office supply companies. A data breach exposing intimate product purchases isn't just about fraud risk; it's about privacy violation and potential embarrassment. This makes targeted phishing and blackmail more effective vectors for attackers.
Targeted Extortion
An attacker with customer names and order details could conduct targeted extortion, threatening to contact the customer's employer or family members if payment isn't made. This is particularly effective in countries or cultures with significant stigma around sexual wellness products.
Third-Party Exposure
Tenga's distribution network spans retail outlets and online channels across multiple countries. A breach doesn't just affect direct customers; it potentially affects partner retailers, logistics companies, and payment processors that handle Tenga data.
Regulatory Complexity
Tenga operates globally, which means they're subject to different privacy regulations in different countries. GDPR in Europe, CCPA in California, PDPA in Singapore, and others. Each jurisdiction has different breach notification requirements, timeline requirements, and customer rights. Tenga's notification letter must comply with all applicable regulations, which requires careful legal analysis.
Reputational Sensitivity
Many companies operate in industries where privacy is critical, but sexual wellness is particularly sensitive. A major company in healthcare, finance, or technology might recover relatively quickly from a phishing-based breach. Tenga must navigate both legitimate security response and the reality that some customers will stop purchasing simply because their privacy was violated.
Lessons for Organizations: How to Prevent This Breach at Your Company
Tenga's breach provides a clear roadmap of what not to do. Here's how to implement stronger defenses.
Implement Universal MFA
Every account with access to sensitive data must require multi-factor authentication. Not "eventually." Not "for IT staff." Not "for executives." Now. For everyone. The cost is minimal, the implementation is straightforward, and it would have prevented Tenga's breach entirely.
MFA comes in multiple forms: SMS-based (weakest), app-based like Google Authenticator (strong), hardware keys (strongest), and biometric (depends on implementation). For sensitive systems, require hardware keys or app-based authenticators. SMS-based MFA is better than nothing, but it's vulnerable to SIM swapping attacks.
Implement Advanced Email Security
Standard email security isn't sufficient. Layer in advanced threat protection that uses machine learning to detect targeted phishing emails based on recipient patterns, sender reputation, and content analysis. These systems aren't perfect, but they catch many attacks that traditional email filters miss.
Beyond detection, implement email authentication standards: SPF (Sender Policy Framework), DKIM (Domain Keys Identified Mail), and DMARC (Domain-based Message Authentication, Reporting, and Conformance). These prevent attackers from spoofing your domain, which makes phishing emails originating from your own company's domain much harder to execute.
Deploy Continuous Security Training
Annual security training is theater. Employees forget it within days. Instead, implement continuous training: monthly phishing simulations that test employees and provide immediate feedback, micro-training modules about current threats, and role-specific training for people with access to sensitive data.
Make security training relevant to people's actual jobs. A customer service representative should learn about threats they might encounter in customer communications. A finance person should learn about wire fraud and invoice manipulation. A marketer should learn about business email compromise. Generic training about "strong passwords" doesn't stick because it's disconnected from actual work.
Implement Email Account Compromise Detection
Set up monitoring and alerting for suspicious email account activity. Red flags include: access from unusual locations, access at unusual times, mass forwarding of emails, exports of large datasets, deletion of emails in bulk, and configuration changes to forwarding rules or recovery email addresses.
When these activities are detected, trigger automatic alerts and, in severe cases, force a password reset and require MFA before the account can be accessed again. The goal is to make account compromise visible and actionable, not allowing attackers to quietly operate for weeks.
Implement Zero-Trust Access Controls
Stop assuming that if someone has access to email, they should automatically have access to everything. Implement role-based access controls that limit each employee to the minimum data necessary for their job. A customer service representative doesn't need access to all customer emails; they need access to emails relevant to customers they support. A developer doesn't need access to customer payment information.
This principle, called the principle of least privilege, significantly limits the damage from a compromised account. The Tenga breach was so damaging because a single compromised account had access to the entire customer database.
Implement Data Loss Prevention (DLP)
Data Loss Prevention tools monitor and control how sensitive data moves within and out of your organization. They can detect when someone tries to export large quantities of customer data, when files are moved to external accounts, or when sensitive information is attached to emails to external recipients.
DLP isn't foolproof, but it makes large-scale data exfiltration harder. An attacker can still steal data, but they have to be more careful and take longer, which increases the risk of detection.
Monitor and Alert on Credential Compromise
Subscribe to services that monitor the dark web, breach databases, and other sources for compromised credentials belonging to your organization. When credentials appear, immediately force a password reset and investigate whether the account has been compromised.
Conduct Regular Security Assessments
Tenga apparently didn't have a comprehensive security assessment program, or they ignored findings about MFA. Third-party security assessments and penetration testing reveal gaps in your defenses before attackers find them. At minimum, conduct annual comprehensive assessments. For high-risk companies, quarterly assessments are more appropriate.
Create an Incident Response Plan
Tenga's response to the breach was relatively competent, but it clearly wasn't based on a well-developed plan. Having a documented incident response plan improves your speed and quality of response when a breach occurs. The plan should document: who to contact, notification procedures, evidence preservation, forensics processes, communication templates, and post-breach improvements.


Estimated data suggests that urgency is the most common emotional trigger used in phishing emails, followed by fear, curiosity, and compliance.
The Role of Regulation and Compliance
Tenga's breach response was shaped not just by best practices but by legal requirements. Understanding these regulations is important because they establish minimum standards that companies must follow.
GDPR (General Data Protection Regulation)
Since Tenga operates in Europe and collects data from European customers, GDPR applies. GDPR requires data breach notification within 72 hours of discovery. It also gives customers the right to request deletion of their data, the right to know what data is collected, and the right to move data to competitors (data portability).
GDPR violations can result in fines up to €20 million or 4% of annual revenue, whichever is higher. For Tenga with roughly
CCPA (California Consumer Privacy Act)
For customers in California, CCPA provides similar rights and requirements. CCPA requires data breach notification without unreasonable delay. It gives customers the right to know what personal information is collected, the right to delete their data, and the right to opt-out of data sales.
CCPA violations can result in fines of
PDPA and Other Jurisdictional Laws
Tenga also operates in Singapore (PDPA), Brazil (LGPD), and other jurisdictions that each have their own data protection laws. This creates a complex compliance landscape where Tenga must follow the most restrictive requirements for each relevant jurisdiction.
Industry-Specific Regulations
While sexual wellness isn't regulated like healthcare or finance, companies handling payment information are subject to PCI-DSS (Payment Card Industry Data Security Standard). Tenga likely processes credit cards for purchases, which means they must maintain PCI-DSS compliance. A breach exposing customer payment information or service inquiries that might include payment details could also violate PCI-DSS.
Regulation is important because it creates minimum security standards and consequences for violations. However, it's also a minimum bar, not a target. A company complying with GDPR isn't necessarily secure; it's meeting a legal minimum. Real security requires going beyond compliance.
Indicators That Your Organization Might Be Next
If your organization shares characteristics with Tenga, you're at higher risk of a similar breach. Here are warning signs to watch for.
No Universal MFA
If MFA is optional, delegated to individual choice, or limited to certain roles, you're vulnerable. The lack of universal MFA is the single biggest indicator that an organization hasn't taken security seriously.
Outdated Security Awareness Training
If your security training is delivered once annually in a single session, it's ineffective. If training content doesn't relate to actual employee work, employees won't internalize it. If phishing simulations don't exist or don't result in improved behavior, your defenses are weak.
No Email Security Beyond Standard Filtering
Standard email security (which filters for malware and known phishing patterns) is insufficient. If you don't have advanced threat protection, you're relying on traditional tools that miss many targeted phishing attacks.
Unclear Access Controls
If you can't immediately answer "What data does this employee have access to?" you have an access control problem. Employees should have access to minimum data necessary for their role, and this should be formally documented and reviewed regularly.
No Incident Response Plan
If you haven't documented what to do if a breach occurs, you're not ready. An incident response plan doesn't prevent breaches, but it dramatically improves your response quality when a breach happens.
No Regular Security Assessments
If you're not regularly testing your security posture through penetration testing or security assessments, you're not learning about your vulnerabilities before attackers do.
Handling Sensitive Customer Data Without Extra Protections
If you're collecting and storing sensitive customer data (payment information, health information, intimate product purchases) without implementing additional protections like encryption, data loss prevention, and enhanced access controls, you're taking unnecessary risk.
The Future: What Security Needs to Look Like
Tenga's breach shows that traditional security models—strong perimeter, internal trust—are broken. The future requires a different approach.
Zero-Trust Architecture
Zero-trust security assumes that no user or system is trustworthy by default, even if they're inside the network. Every access request is authenticated, authorized, and encrypted. User identity is continuously verified. Lateral movement is restricted. This would have prevented Tenga's breach from resulting in full database exfiltration.
Passwordless Authentication
Passwords are the weakest link in security. They're easy to phish, easy to crack, and hard to manage. The future uses passwordless authentication: hardware keys, biometric authentication, certificate-based authentication. Tenga's attacker wouldn't have needed the employee's password at all; they could have stolen a hardware key or found another authentication vector.
AI-Powered Threat Detection
Machine learning and AI can detect anomalous behavior that humans can't. An AI system trained on normal email patterns can detect when an account is suddenly forwarding large amounts of data or accessing it from unusual locations. These systems won't catch everything, but they improve detection speed and accuracy.
Implicit Trust Verification
Instead of trusting that someone is who they claim based on a password, modern systems verify context: device health, location patterns, access patterns, typing biometrics, behavioral analytics. If someone's normal pattern is accessing email from an office in Tokyo and suddenly accessing it from Russia, that's a signal that something is wrong.
Encrypted Data Stores
When attackers access a database, they should encounter encrypted data that's useless without encryption keys. Tenga's customer data wasn't encrypted against the employee who compromised it, which means the attacker got plaintext access. Proper encryption means that even if the database is stolen, the data is protected.
Automated Incident Response
When a breach is detected, response should be partially automated. Suspicious accounts should be automatically locked. Suspicious processes should be automatically killed. Suspicious files should be automatically quarantined. This doesn't replace human investigation, but it dramatically reduces the window that attackers have to operate.

What Customers Can Do Right Now
If you were affected by Tenga's breach or any similar breach, here's what you should do immediately.
Change Your Password
Not just on Tenga's website, but on any other site where you use the same password. Password reuse across sites means a breach in one place compromises you everywhere. If you were using the same password on your email, bank, or other sensitive accounts, change those immediately.
Enable Two-Factor Authentication
On Tenga's site (if available) and on every other important account: email, banking, social media, healthcare, anything containing sensitive information. Two-factor authentication means even if your password is stolen, the attacker can't log in without also accessing your second factor.
Monitor Your Email for Phishing
Attackers have your email address and knowledge that you're a Tenga customer. Expect targeted emails impersonating Tenga, payment processors, financial institutions, or other companies trying to harvest additional information or credentials. When you get emails claiming to be from Tenga, go directly to Tenga's website rather than clicking links in the email.
Monitor Your Credit and Bank Accounts
Look for unauthorized transactions. If Tenga has your payment information (credit card number, bank account number), monitor those accounts closely for the next several months. Most credit card companies offer fraud protection, but it's still disruptive to deal with fraudulent charges.
Consider a Credit Freeze
If the breach exposed your full name and personal information that could be used for identity theft, consider placing a credit freeze with the major credit bureaus (Equifax, Experian, TransUnion). This prevents anyone from opening new accounts in your name without your explicit approval.
Register with Credit Monitoring Services
Some companies offer free credit monitoring for a limited time after a breach. If Tenga offers this, enroll. Otherwise, credit monitoring services like Credit Karma or Experian's free monitoring can give you visibility into whether someone is trying to use your information fraudulently.
Document the Breach
Keep records of Tenga's breach notification, your password change confirmation, and any monitoring you set up. If you're later a victim of identity theft or fraud, you have documentation that you responded appropriately to the breach notification.
The Tenga Breach in Broader Context: Why This Matters
On the surface, a phishing attack against a Japanese sexual wellness company might seem niche. But the Tenga breach illustrates something important about modern cybersecurity: sophistication doesn't matter if you forget the basics.
Tenga didn't get breached because they used outdated software or because they missed a critical security update. They got breached because a single employee fell for a phishing email and their organization didn't have basic compensating controls like universal MFA.
This breach is representative of approximately 80% of data breaches. Not sophisticated attacks. Human error combined with inadequate security controls. The pattern repeats across small companies and large companies, startups and enterprises, financial institutions and retailers. The details change, but the story is always the same.
Which means it's preventable. Not guaranteed preventable (no security is perfect), but reasonably preventable with competent implementation of basic controls. MFA. Email security. Employee training. Access controls. Incident response. These aren't advanced techniques. They're the basics.
Tenga's response to the breach was adequate but not excellent. They did the legally required things. They didn't go above and beyond to rebuild trust or implement standout security improvements. This is typical of companies that treat security as a cost center rather than a competitive advantage.
The future belongs to companies that view security not as compliance checkbox but as essential infrastructure. That means implementing controls not because regulations require them but because they make business sense. It means having security teams that are trusted and resourced. It means training that works and access controls that are maintained. It means security culture where reporting suspicious emails is rewarded rather than blamed.
Tenga's breach is a wake-up call, not because Tenga is uniquely vulnerable, but because so many organizations have similar vulnerabilities. If you're reading this and thinking "we're different," you probably aren't. The question is whether you'll implement defenses before a breach forces you to.
FAQ
What exactly did the attacker steal in the Tenga breach?
The attacker gained access to a Tenga employee's email inbox through a phishing attack and exfiltrated customer names, email addresses, order details, and customer service correspondence. The exact number of affected customers hasn't been publicly disclosed, but the breach affected global markets across multiple countries. Tenga's notification specifically warned that customer service inquiries could contain order details and sensitive information.
How long was the attacker inside Tenga's systems?
Tenga hasn't disclosed the precise timeline between initial compromise and detection. Industry averages suggest attackers remain undetected for several months after initial compromise (around 207 days on average). Given that Tenga discovered spam being sent from the compromised account, it's likely the attacker had access for at least weeks, if not longer, before detection occurred.
Why was MFA not enabled before the breach if it's so important?
This reveals a common problem in information security: controls are often implemented only after an incident makes them urgent. Many organizations treat security investments as optional until a breach forces action. Tenga apparently had the technical capability to implement MFA but hadn't made it mandatory until after discovering the breach. This reactive approach is unfortunately common and leaves organizations vulnerable to predictable attacks.
Could this breach have been prevented?
Yes, relatively easily. If Tenga had implemented universal MFA, the attacker's stolen credentials would have been useless without access to the employee's second factor (phone, hardware key, or authenticator app). Additional layers like advanced email security tools, email account compromise detection, and tighter access controls would have further reduced risk. The breach happened not because it was sophisticated but because of missing basic controls.
What should I do if I was a Tenga customer?
Immediately reset your Tenga password and enable two-factor authentication if available. Change your password on any other account where you used the same credentials. Monitor your email for phishing messages impersonating Tenga or financial institutions. Review your credit card and bank statements for unauthorized transactions. Consider enabling credit monitoring or placing a credit freeze if the breach exposed sensitive personal information.
How does this compare to other major data breaches?
Tenga's breach is typical of company-scale breaches in terms of attack vector (phishing leading to email account compromise) and data exposure (customer records with order details). Unlike breaches affecting millions of records, Tenga's impact remains limited by the number of customers affected. However, the intimate nature of products makes this breach more privacy-sensitive than a typical e-commerce breach of equal size.
Will there be lawsuits against Tenga?
Likely yes. Customers affected by the breach can pursue civil lawsuits under various consumer protection statutes. Depending on the jurisdiction and number of affected customers, this could result in class-action litigation. Regulatory fines under GDPR and CCPA are also possible. Tenga's response to the breach will influence the severity of potential penalties; companies that respond transparently and comprehensively face lower regulatory penalties than those that minimize or hide breaches.
Why is a sexual wellness company a target for hackers?
Intimate product purchases are particularly sensitive. Customer data can be used for targeted extortion, blackmail, or impersonation. The stigma around sexual wellness products makes customers particularly vulnerable to follow-up attacks that leverage their purchase history. Additionally, companies in niche markets often have smaller security teams and budgets, making them attractive targets compared to high-security financial institutions.
What industry or company is most likely to have similar vulnerabilities?
Small to mid-sized companies (50-500 employees) in any industry are at highest risk. These companies typically generate significant sensitive data but lack the security resources and expertise of large enterprises. Common vulnerable industries include healthcare (HIPAA-covered entities), legal services, accounting firms, e-commerce, SaaS companies, and any company collecting payment information or personal data.
How can I tell if my organization is vulnerable to this type of attack?
Assess whether your organization has universal MFA, advanced email security beyond standard filtering, regular security awareness training with phishing simulations, documented access controls limiting data access to minimum necessary, and a documented incident response plan. If any of these is missing or partial, you're vulnerable. Additionally, check whether your organization conducts regular security assessments and penetration testing. If security is not a regular investment, vulnerabilities are likely.
Conclusion: Learning From Tenga's Mistakes
The Tenga data breach tells a story that plays out hundreds of times daily across organizations of all sizes. An employee receives an email that looks legitimate. They click a link, enter their password, or download an attachment. An attacker gains access to one person's account. Without universal MFA, that access opens the entire organization's data to compromise.
The attacker then exfiltrates data, sends spam, potentially maintains access for future attacks. Days or weeks later, sometimes months, the organization detects the breach and responds with the basic controls that should have been in place all along.
Tenga's situation is neither unique nor particularly severe in technical terms. The breach didn't exploit zero-day vulnerabilities or require nation-state-level sophistication. It succeeded through a combination of human error and inadequate security controls. The victims are customers whose intimate purchases and personal information are now in the hands of unknown attackers.
But here's what matters: this was preventable. Not through perfect technology or impossible-to-maintain operational security, but through competent implementation of well-understood controls. MFA. Email security. Training. Access controls. Incident response. These are the blocking and tackling of cybersecurity. Not glamorous, not cutting-edge, but absolutely essential.
If you're reading this and your organization doesn't have universal MFA, that's your starting point. Not next quarter. Not after you finish the current project. This week. MFA is the most impactful security control for its cost and complexity. A single compromised email account without MFA can compromise everything your organization has built.
If your organization does have universal MFA, look at the next layer: email security, access controls, and employee training. Each layer prevents a different attack vector. None are sufficient alone, but together they make compromise far harder and detection far faster.
Tenga will recover from this breach. They'll implement security improvements, their customers will gradually return (though some won't), and the incident will fade from memory as the next crisis emerges. But the lessons remain: phishing remains the primary attack vector for a reason, and basic security controls remain effective for a reason.
The question for your organization is whether you'll learn from Tenga's example or have to learn from your own breach. The choice, as always, is yours.

Key Takeaways
- A single phishing email compromised an entire employee email account, exposing customer names, emails, order details, and service inquiries globally
- Tenga's critical security failure was lack of universal MFA deployment before the breach, which would have prevented account compromise even with stolen credentials
- Email account compromise is one of the most damaging breach types because it gives attackers access to everything the compromised employee accessed
- Phishing remains the primary attack vector for 80% of data breaches because it's cheap, effective, and requires only one employee to fail
- Organizations typically detect breaches 207 days after initial compromise, allowing attackers substantial time to exfiltrate data and establish persistence
- Layered security controls including advanced email security, access controls, monitoring, and incident response plans dramatically improve breach prevention and detection
- Universal MFA, advanced email security, and continuous employee training represent the most cost-effective security improvements for preventing phishing-based breaches
- Small to mid-sized companies like Tenga (50-200 employees) face higher relative risk due to fewer dedicated security resources despite handling equally sensitive data
Related Articles
- Tenga Data Breach: What Happened and What Customers Need to Know [2026]
- Odido Data Breach: 6.2M Customers Exposed [2025]
- Figure Technology Data Breach [2025]: What Happened and What You Need to Know
- Machine Credentials: The Ransomware Playbook Gap [2025]
- Cybersecurity & Surveillance Threats in 2025 [Complete Guide]
- DJI Romo Security Flaw: How 7,000 Robot Vacuums Were Exposed [2025]




