Why Your Ring Camera Privacy Just Became a $10K Problem
Let's be honest: you probably didn't buy a Ring camera thinking it'd become a neighborhood surveillance dragnet. You installed it because you wanted to know when packages arrive and catch porch pirates red-handed. Simple, practical security for your home.
Then Amazon got creative. In early 2024, during one of the most watched advertising moments of the year, Ring unveiled Search Party. The feature lets users tap into a network of Ring cameras throughout their neighborhood to locate lost dogs. Adorable concept, right?
Except here's what the leaked internal emails revealed: this wasn't just about lost dogs. The infrastructure Ring built could eventually find lost cats, lost people, and pretty much anything else Amazon decides to search for. The commercial showed feel-good pet recovery, but the underlying technology built a neighborhood-scale surveillance system.
The public reaction was swift and brutal. Social media exploded with criticism. Tech publications called it out as surveillance creep masquerading as community helpfulness. People literally filmed themselves destroying their Ring cameras and posting the videos online. Ring's own CEO ended up on what's basically been a continuous apology tour.
Then something unexpected happened. The Fulu Foundation, a nonprofit founded by repair advocate and YouTuber Louis Rossmann, saw an opening. They announced a $10,000+ bounty to anyone who could figure out how to disable the data-sharing features on Ring cameras while keeping the hardware functional. No more sending footage to Amazon. No more neighborhood surveillance networks. Just a local security camera that actually respects your privacy.
But here's the problem: this isn't as simple as flipping a switch. Ring cameras are designed by a company owned by Amazon, a company that monetizes user data across basically every product it makes. Getting your device to stop talking to Amazon's servers while preserving motion detection, night vision, and local functionality? That's a genuine technical challenge. And that's why the bounty exists.
The story of this bounty reveals something much bigger about ownership, privacy, and control in the age of smart home devices. It shows us how far some of us are willing to go to take back power over the devices we buy and bring into our homes. And it exposes just how fragile that concept of ownership really is.
TL; DR
- $10,000+ bounty: Fulu Foundation pays hackers to disable Ring's Amazon data-sharing features
- The trigger: Ring's "Search Party" feature sparked outrage for building neighborhood surveillance infrastructure
- The challenge: Solution must preserve local camera functions without breaking hardware
- Legal stakes: DMCA Section 1201 creates barriers to publicly releasing such modifications
- Bottom line: It's a battle over whether you actually own and control the devices you buy

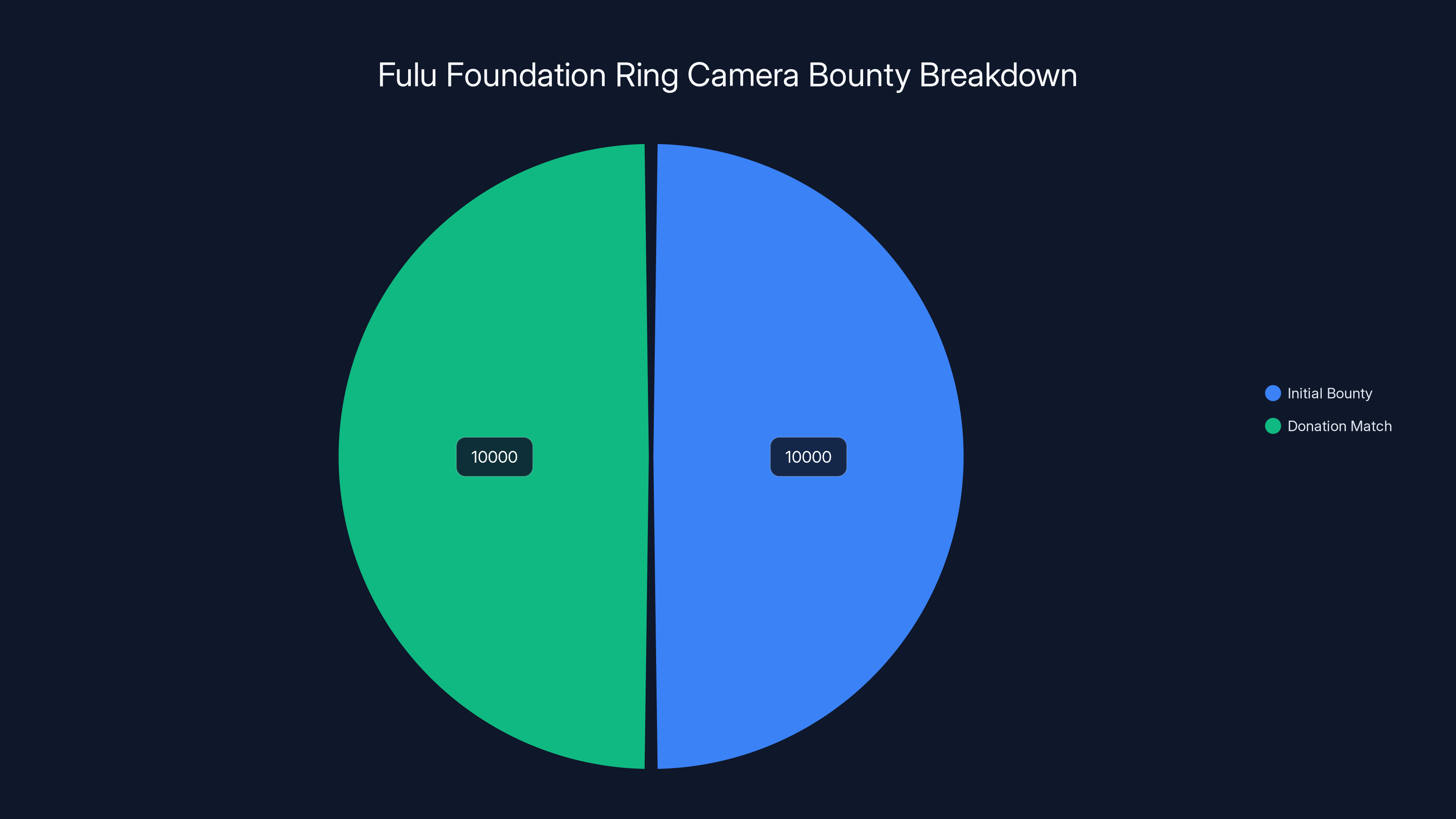
The Fulu Foundation offers a
The Ring Camera Controversy: How a Super Bowl Ad Became a Privacy Crisis
Super Bowl commercials cost millions. Ring's team probably spent weeks optimizing every second of their Search Party ad. Test audiences probably loved the premise: a girl's dog goes missing, neighborhood Ring cameras light up, footage of the lost dog appears in an app, dog gets reunited with owner, everyone cries happy tears.
Then reality set in. Within hours of the ad airing, privacy advocates, security researchers, and regular people started asking uncomfortable questions. The questions got louder when 404 Media reported on leaked internal Ring emails that showed exactly what the company was planning.
Those internal emails were devastating. They revealed that Search Party wasn't the endpoint of Ring's surveillance ambitions. The internal documentation explicitly mentioned potential future uses: finding "missing people," locating "suspects," and building out full-neighborhood search capabilities. Ring had built the infrastructure first and was now deciding what surveillance use cases to enable later.
This wasn't paranoia or speculation. These were Ring's own internal projections about what their surveillance network could eventually do.
The public reaction crossed a threshold that most tech controversies never reach. This wasn't just think piece criticism or angry tweets that fade in 48 hours. People were viscerally uncomfortable. Homeowners started seeing their Ring cameras not as security devices but as nodes in a surveillance network they never consented to join. Ring users posting in online forums reported feeling genuine betrayal. Some started destroying their cameras on video.
Ring's CEO Jamie Siminoff, who had built the company's entire brand on being approachable and trustworthy, immediately went into damage control. He made statements. He did interviews. He expressed that Ring "understood the concerns." The company severed ties with Flock AI, a controversial AI surveillance company, as if removing one controversial partner could wash away the entire concern.
But here's what Ring couldn't do: they couldn't actually change the hardware architecture. The cameras were already built to send data to Amazon servers. That design choice was baked into the firmware. Making Search Party "opt-in" didn't change the fact that the infrastructure existed. And once surveillance infrastructure exists, the temptation to use it tends to be overwhelming.
That's the moment the Fulu Foundation decided this had to move to the top of their bounty list.
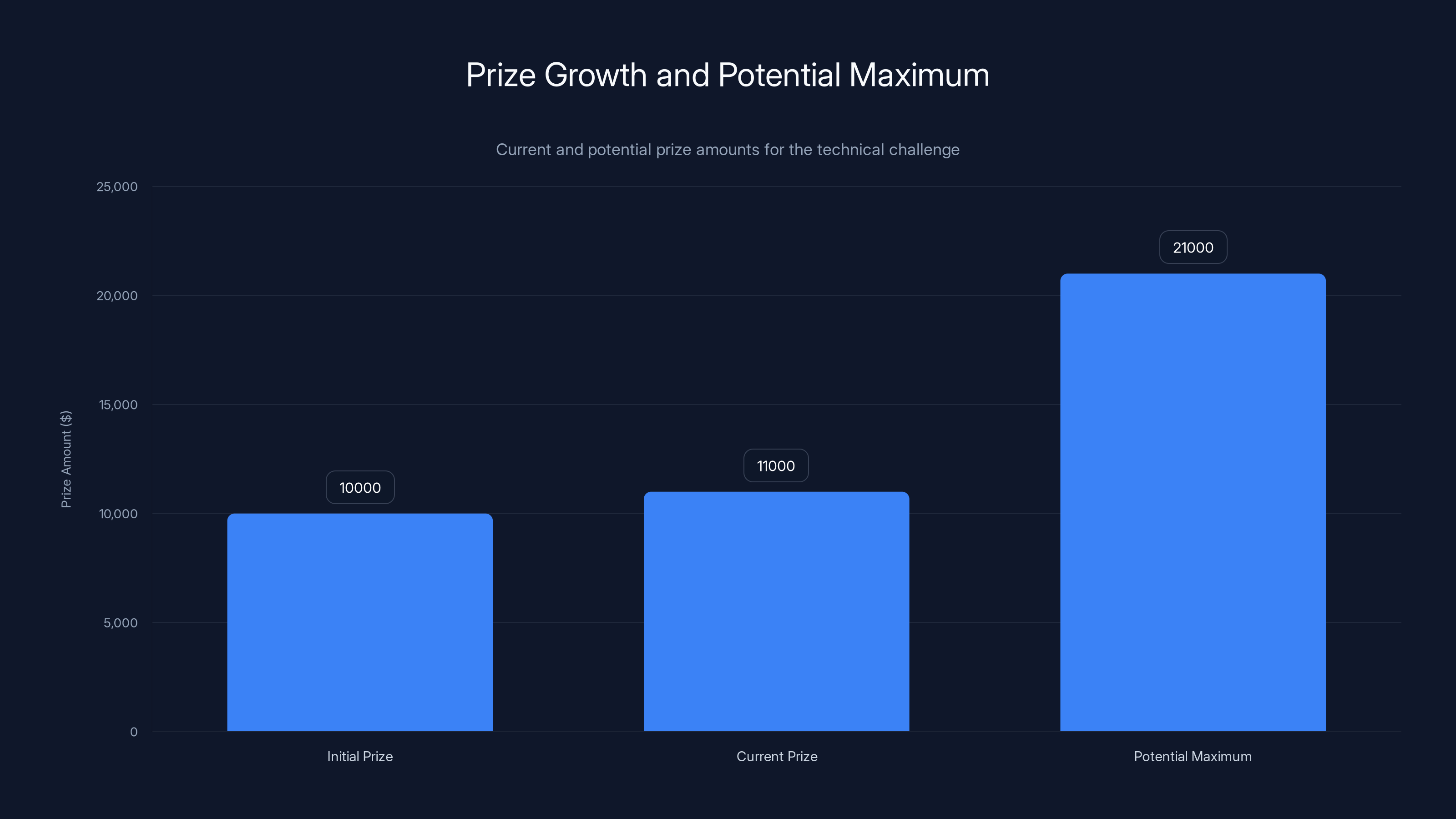
The prize for the technical challenge started at
Meet the Fulu Foundation: Paying for Your Right to Control Your Devices
Louis Rossmann is not your typical foundation founder. He started as a YouTuber fixing old Apple computers and electronics. His channel exploded because he was willing to criticize major tech companies for making their products impossible to repair. He'd tear down a MacBook, show viewers the soldered components, and explain exactly why Apple's design choices prevented normal people from fixing their own devices.
That audience and that ethos became the Fulu Foundation. The concept is straightforward but radical: they pay money to people who can remove "user-hostile features" from devices people own. The idea is that if you bought something, you should be able to modify it, repair it, and control how it works.
Fulu's previous bounties have covered everything from removing biometric requirements on hardware to disabling forced software updates. They've paid out bounties for removing digital locks that prevent independent repairs. Each bounty is designed around a specific user-hostile feature that manufacturers built into their products.
Kevin O'Reilly, a cofounder of Fulu, articulated the philosophy perfectly when discussing the Ring bounty: "People who install security cameras are looking for more security, not less. At the end of the day, control is at the heart of security. If we don't control our data, we don't control our devices."
That statement captures something profound. Security isn't just about preventing break-ins or catching package thieves. Real security means knowing who has access to your data, how it's being used, and whether you can stop it. A camera that sends footage to Amazon's servers without your ability to disable that transmission? That's not actually providing you security. It's providing Amazon with data.
The Fulu Foundation exists because mainstream companies have largely abandoned the concept of user control. They've optimized instead for corporate benefit. They've embedded proprietary features, locked down firmware, and designed systems that serve corporate interests rather than user interests.
Fulu's approach is simple: if the market won't provide what users need, they'll pay someone to build it.
The $10,000+ Prize: What Would It Take to Win?
The bounty started at
That's real money for a real technical challenge. And Fulu was extremely specific about what would qualify.
First, the core requirement: the winner must demonstrate a method to disable software features on Ring cameras that require data transmission to Amazon. The device must continue working with a local PC or server. It must be capable of halting data sent to Amazon's infrastructure without requiring connection to other Amazon hardware.
Second, the hardware itself has to remain intact. This isn't about brute-forcing the camera or destroying it to prove a point. Motion detection needs to work. Color night vision needs to work. All the actual security features need to remain operational. You're not trading functionality for privacy. You're just removing the corporate surveillance component.
Third, the solution needs to be accessible to normal people. Fulu specified "readily available and inexpensive tooling" and "instructions that a moderately technical user could carry out." As O'Reilly put it: "This needs to be a weekend project. Someone who was creeped out by a commercial and wants to take back control can take care of it, get it done, and be able to sleep soundly at night knowing that they're the only ones who can see their footage."
The solution had to be accomplishable in under an hour. Not a weekend of learning new programming languages. Not weeks of research. Under an hour, with straightforward tools, by someone with moderate technical skills.
Fourth, the winner needs to prove it works. They need to provide documentation showing that the modification actually prevents data transmission to Amazon while maintaining local functionality. They need to provide step-by-step instructions. They need to demonstrate the camera still functions normally for its intended purpose.
What makes this bounty interesting is what it doesn't require: public release. Winners don't have to publish their findings or make the hack widely available. That's intentional, because of something called Section 1201 of the Digital Millennium Copyright Act.
If someone figures out how to modify Ring cameras to stop sharing data with Amazon, publishing that method publicly could open them to legal action from Amazon. Amazon could argue that the method violates Section 1201 by circumventing their copy protection mechanisms. The irony is brutal: you own the hardware, but the law might prevent you from sharing how to control it.
Fulu explicitly allows winners to choose. Win the money, solve the problem for yourself and keep it private, or publish and potentially face legal consequences. Most winners have chosen to stay quiet, which is why the bounty model exists in the first place.
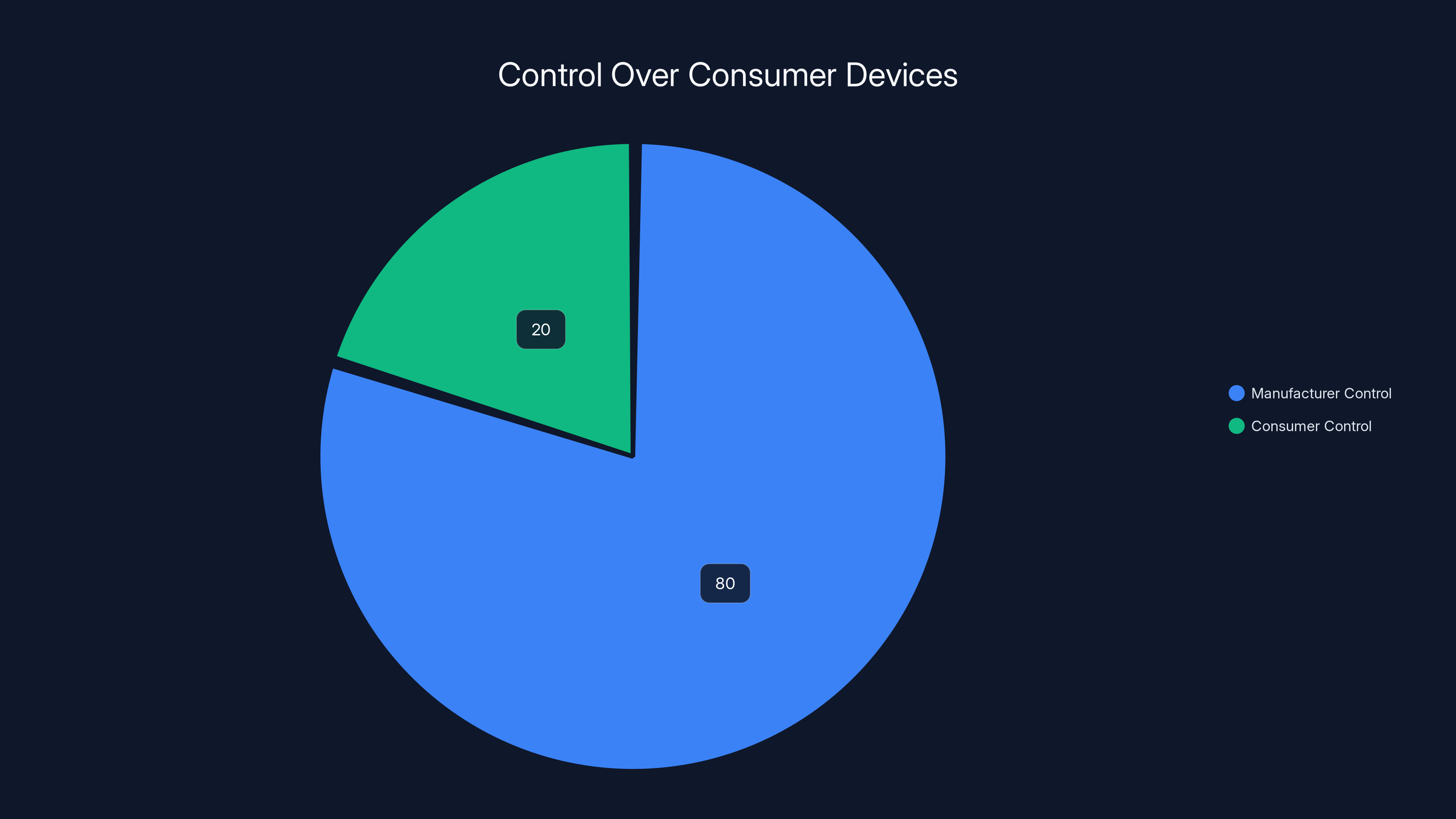
Estimated data suggests that manufacturers retain approximately 80% control over consumer devices, leaving only 20% for consumers, highlighting the shift from ownership to controlled usage.
The Technical Barrier: Why Disabling Amazon Integration Is Harder Than You'd Think
On the surface, it sounds simple. Ring cameras connect to Amazon's servers. Find where that connection happens in the firmware and disable it. Problem solved.
Reality is messier.
Ring cameras have a closed architecture. The firmware isn't open source. Users don't have direct access to modify it. The devices connect to Amazon through encrypted channels. The company has implemented various checks to prevent tampering.
The first barrier is physical access. To modify the firmware, you need to access the device at a hardware level. That typically means opening the camera, locating the right components, and potentially using specialized equipment like JTAG interfaces or serial connections to interact with the device's boot process. Most consumer devices are designed to prevent this. Ring cameras are no exception.
The second barrier is cryptographic. Modern devices use secure boot processes that verify firmware signatures before allowing execution. If you modify the firmware, the signature no longer matches. The device refuses to run the modified code. Breaking this requires either finding vulnerabilities in the boot verification process or circumventing the cryptographic checks entirely.
The third barrier is architectural. Ring cameras are designed with a specific assumption: they connect to Amazon's cloud infrastructure. The firmware probably includes hardcoded IP addresses, API endpoints, and authentication mechanisms that are deeply integrated into the system's operation. Removing Amazon connectivity without breaking something else requires understanding the entire architecture.
The fourth barrier is the moving target. Ring regularly updates firmware. Any solution that works today might break with the next update. A successful bounty winner would need to create a solution that remains viable even as Ring modifies their software.
The fifth barrier is the legal one. The moment someone figures out how to modify Ring firmware, they've potentially violated Section 1201. If they publish their findings, they face potential legal consequences. This creates a perverse incentive: the people most capable of solving this problem are the ones most exposed to legal risk if they share their solution.
This is why the bounty model makes sense. It provides financial compensation that acknowledges both the technical difficulty and the legal risk. It allows someone to solve the problem, earn legitimate compensation, and keep the solution private if publishing would be dangerous.

How Smart Home Manufacturers Lock You Into Their Ecosystem
Ring is far from alone in this approach. The smart home industry has largely converged on a specific business model: sell devices cheaply, monetize user data aggressively.
Amazon Alexa devices, Google Nest cameras, Apple HomeKit, Samsung SmartThings, and dozens of other platforms all follow similar patterns. The devices themselves are commoditized. The real money comes from understanding user behavior, selling that data to advertisers and third parties, integrating with Amazon's broader e-commerce ecosystem, or leveraging the devices to provide other services.
To protect this business model, manufacturers lock down their devices. They disable manufacturer reset options. They prevent firmware modifications. They prohibit third-party integrations without approval. They design the devices to be completely dependent on cloud connectivity.
Some do this transparently in their terms of service. Others do it through technical barriers that most consumers never realize exist. Most do both.
The result is that you don't really own a Ring camera the way you own a bicycle. You don't own it the way you own a pair of shoes. You own a restricted license to use Ring's hardware according to Ring's terms. Ring maintains control over the software. Ring maintains the right to modify how the device works with future updates. Ring maintains access to all data flowing through the device.
Amazon, as Ring's parent company, has institutional interest in maximizing data collection. They want to know about package deliveries so they can optimize last-mile logistics. They want to understand neighborhood patterns for retail analytics. They want to integrate Ring data with Alexa data with shopping data with Prime data to build comprehensive consumer profiles.
That's not evil in the abstract sense. It's just business optimization. But from a user perspective, it means you've invited a surveillance system into your home.
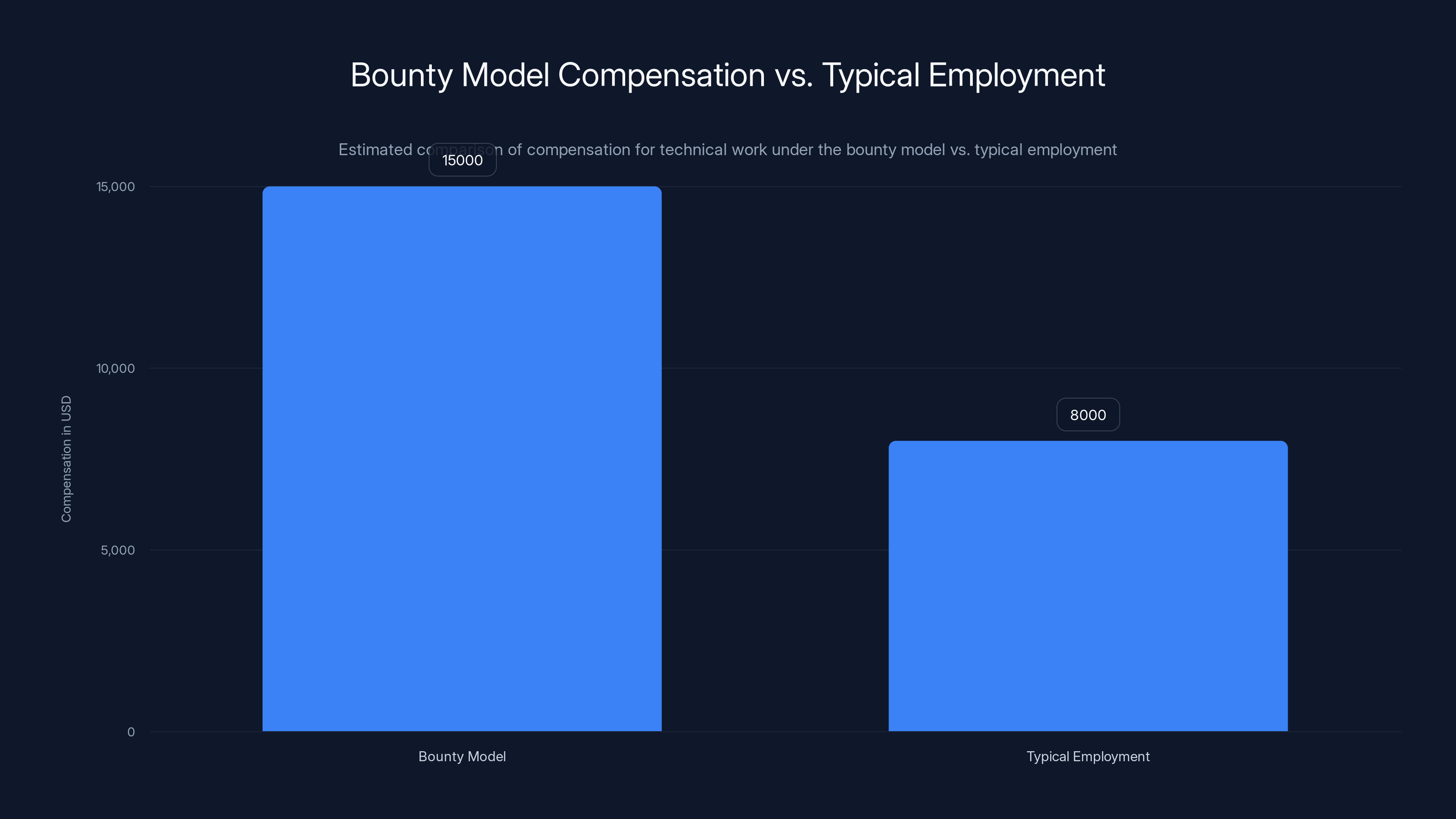
The bounty model offers higher compensation (
The DMCA Problem: Why Innovation Happens in Legal Gray Zones
Section 1201 of the Digital Millennium Copyright Act was passed in 1998. At the time, the internet was young, digital rights management was a new concept, and lawmakers were genuinely concerned about copyright piracy. They passed a law that made it illegal to circumvent any technological protection measure, regardless of whether you owned the device or whether the circumvention itself was for a legal purpose.
The law's consequences have proven far more expansive than originally intended. Courts have ruled that it applies not just to copyright protection, but to any "technological measure that effectively controls access" to a work. That includes access to devices you own.
This creates a bizarre legal landscape. You can own a Ring camera outright. You paid money for it. It's physically in your home. But the moment you try to modify its firmware or disable its cloud connectivity, you've potentially violated federal law. Not because you're stealing anything. Not because you're distributing copyrighted material. Just because you're circumventing a digital protection measure.
The consequences are real. Companies have sued researchers for publishing vulnerabilities. The threat of legal action has prevented legitimate security researchers from disclosing bugs they found. Independent repair shops have been threatened with lawsuits for fixing devices in ways manufacturers didn't approve of.
Fulu Foundation exists partially because of this legal landscape. They can't rely on normal market mechanisms to push manufacturers toward giving users more control. Companies profit more from locked devices. So Fulu uses bounties to create alternative incentives. Win money, solve the problem, keep it private if publishing would be legally dangerous.
The irony is that this might actually be less effective than public knowledge. If everyone could modify their Ring cameras to prevent Amazon data sharing, Ring would need to fundamentally change their business model. But if only a few people have the knowledge, and they keep it private, the surveillance network continues functioning for everyone else.

Privacy vs. Features: The Trade-Off That Shouldn't Exist
One of the smartest things Kevin O'Reilly said about the Ring bounty deserves emphasis: "Control shouldn't require a trade-off of all the features that you like. You shouldn't have to sacrifice the smart capabilities of your device if you don't want to."
This articulates the core problem. Currently, if you want the security benefits of a modern camera, you have to accept corporate surveillance. If you want privacy, you have to accept older technology or expensive alternative solutions. The market has essentially decided that surveillance is a mandatory feature.
But it doesn't have to be this way. A Ring camera could easily support local-only operation. The technology is straightforward. You'd set up the camera, connect it to your local network, install a local server or integrate it with existing NAS systems, and access your footage locally. Motion detection, night vision, all the core features would work exactly the same way.
The only difference would be that Amazon wouldn't be storing your footage. Amazon wouldn't be building neighborhood surveillance networks. Amazon wouldn't be able to sell data about your home and habits to third parties or law enforcement.
Ring doesn't offer this option not because it's technically impossible but because it's not profitable. Surveillance is the feature Ring's parent company actually wants to sell.
The Fulu Foundation bounty represents users saying: we'll accept this trade-off for ourselves if we have to, but we want the option to choose. We want to be able to have a functional security camera without mandatory cloud surveillance.
This is a reasonable position. It respects that some people might actually want Ring's cloud features. But it also respects that other people might not.
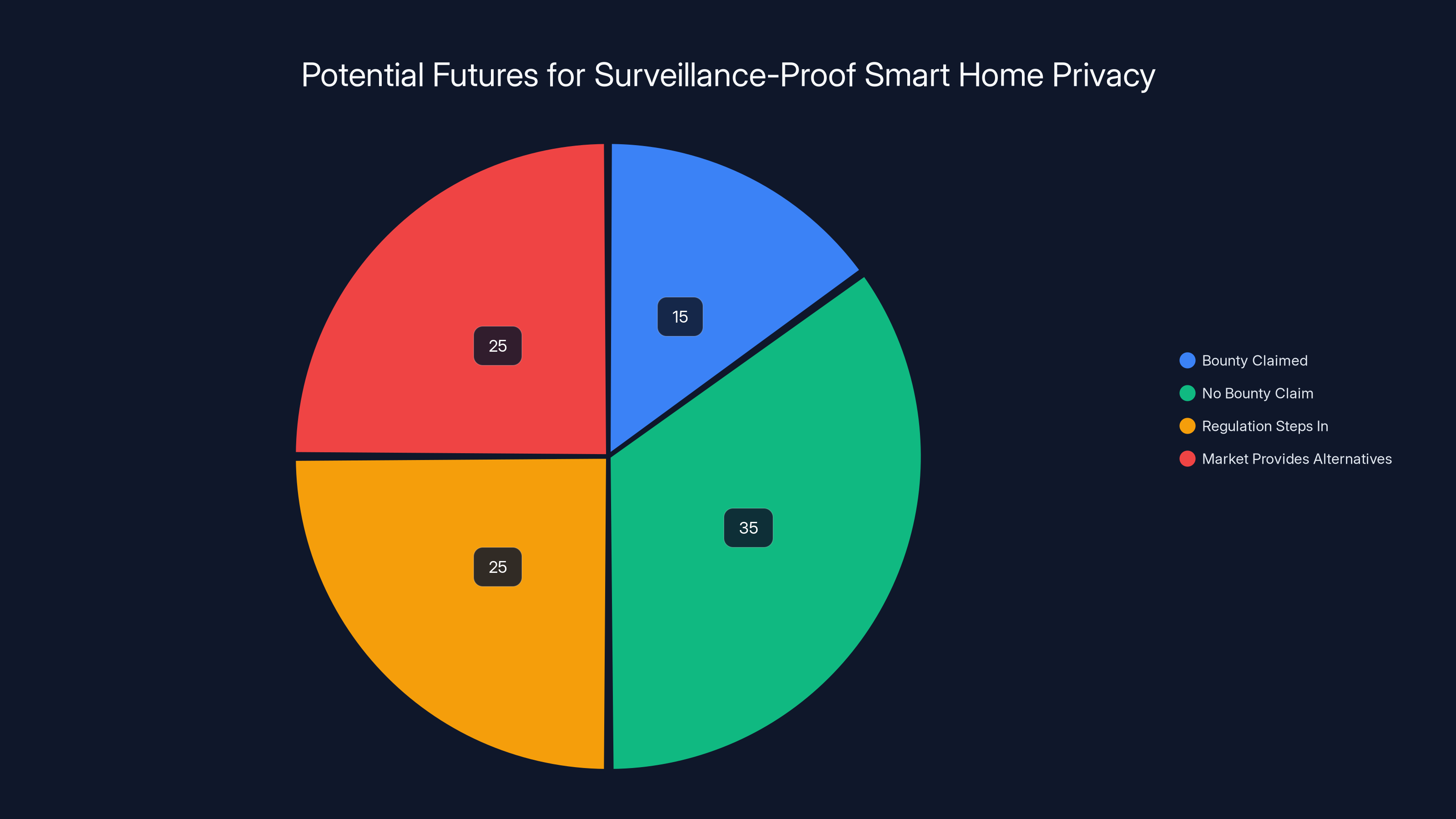
Estimated data suggests that the most likely future involves no bounty claim (35%), followed by regulation and market alternatives (25% each), with a smaller chance of the bounty being claimed (15%).
What the Bounty Says About Ownership and Control
The fact that Fulu Foundation needs to offer $10,000+ to make this happen tells you something profound about the current relationship between consumers and the products they buy.
A generation ago, you could buy a device and modify it freely. You could crack open a computer, replace components, install custom operating systems. Nobody had to hire lawyers or pay bounties. You just modified your own stuff.
That era collapsed with digitalization. As more functionality moved into software, manufacturers realized they could maintain control over devices even after the sale. They could disable features remotely. They could prevent modifications. They could change functionality with software updates. They could monitor usage and extract data.
For manufacturers, this is ideal. It allows long-term monetization of every device sold. It prevents competition from people who might modify devices for alternative purposes. It ensures that every data stream flows through corporate infrastructure where it can be captured and monetized.
For consumers, it means you don't actually own your devices the way previous generations owned their stuff. You lease a restricted license to use them.
This is profitable enough that it's become the standard. With Ring, with Alexa, with Nest, with most smart home devices, you're getting a product that the manufacturer retains control over. That control is enforced technically through locked firmware and legally through copyright law and terms of service.
The Fulu bounty is a referendum on whether users should have the right to challenge this arrangement. It's saying: maybe we should be able to own our devices again. Maybe we should be able to modify them. Maybe corporate control shouldn't be the default.
Large technology companies, predictably, disagree. Their entire business models depend on maintaining control. Every bounty that gets paid out, every device that gets modified to remove surveillance features, every user who takes back control, represents a threat to those business models.

The Role of Public Outcry in Forcing Change
The Fulu Foundation's decision to prioritize the Ring bounty wasn't random. It was a direct response to the fact that Ring's Search Party feature generated genuine public anger.
This is important because it shows that public pressure still matters. Ring could have ignored the criticism. Most tech companies do. They wait out the news cycle, release a statement saying they're "committed to privacy," maybe make superficial changes, and move on.
But Search Party hit differently. The fact that Ring internally documented plans for surveillance uses beyond finding lost dogs struck people as a betrayal. The infrastructure wasn't being built for feature creep. It was being built for surveillance expansion, and Ring was just waiting for the right moment to enable it.
Public understanding of that intention created enough pressure that Ring had to take action. They severed ties with Flock AI. They made statements about their commitment to privacy. But they couldn't undo the fundamental architecture of their product.
That's where the Fulu bounty came in. The Foundation saw an opening created by public pressure and immediately moved to give people a technical option to resist the surveillance architecture Ring had built.
This matters because it shows that the relationship between consumers and manufacturers isn't entirely one-directional. If consumers actually care, if they make their preferences visible, if they're willing to take action, companies do respond. Not because they suddenly become ethical, but because the cost of ignoring them exceeds the benefit of surveillance expansion.
For Ring, that threshold was probably measured in lost sales, negative brand perception, and the risk that privacy advocates would push for regulation. Allowing people to disable cloud connectivity doesn't cost Ring money if it's done outside their official channels, because then it's not their responsibility.
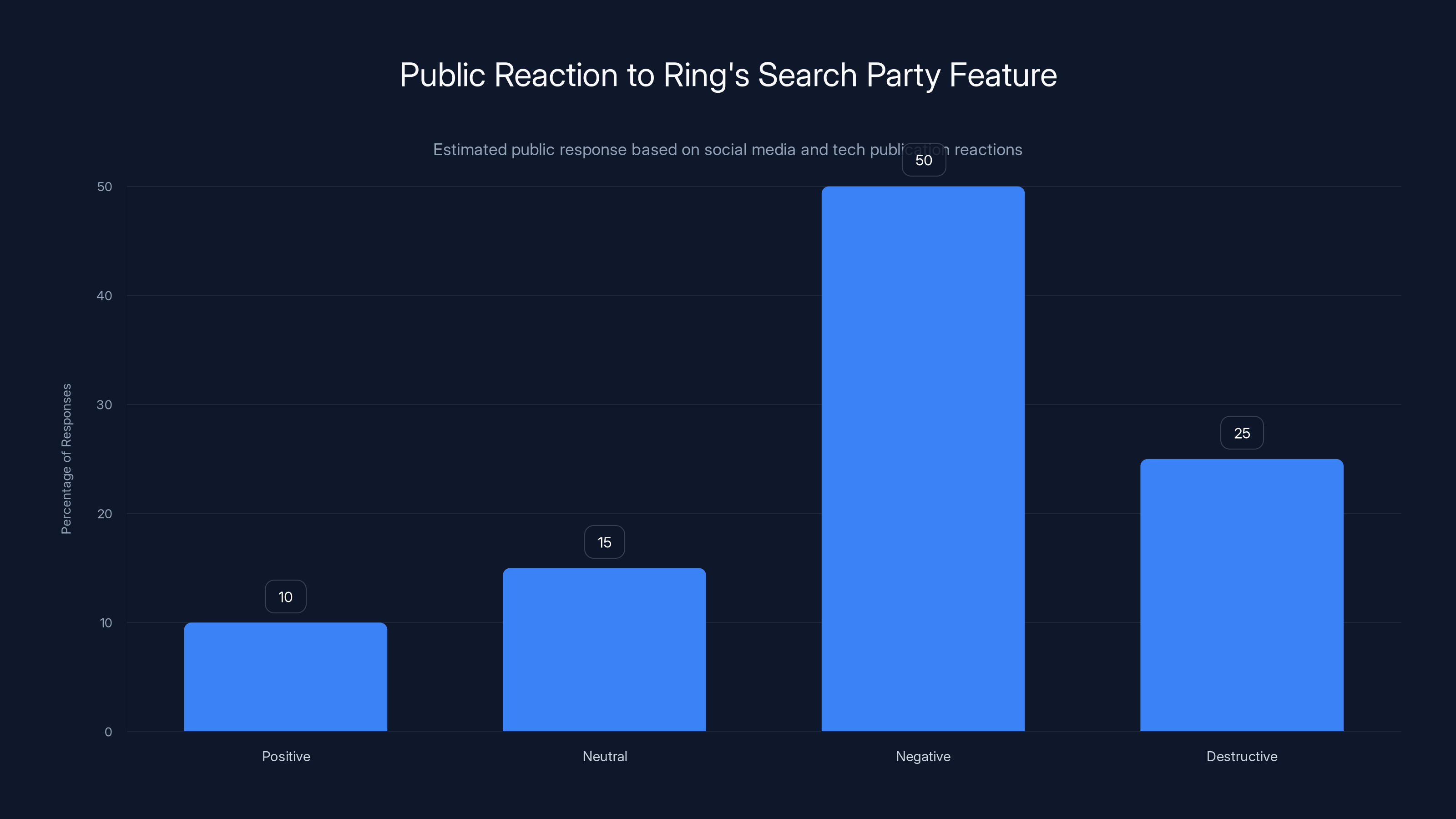
Estimated data shows a significant negative reaction to Ring's Search Party feature, with a notable portion of users taking destructive actions against their devices.
Alternative Solutions: Local-Only Smart Home Options
If you want to avoid the Ring dilemma altogether, alternatives exist. They're less convenient and less polished than Ring, but they don't require you to surrender surveillance data to Amazon.
Unifi Protect, made by Ubiquiti, provides professional-grade cameras with local storage and cloud integration that's entirely optional. You can set up a Unifi controller on your local network and operate completely independently of Ubiquiti's cloud services. The cameras work offline and store footage locally. If you want to access them remotely, you can set up a VPN.
HomeKit cameras from companies like Logitech and Arlo offer similar local-first architecture, particularly if you set up an Apple TV as a hub. Footage can be stored in iCloud, but local storage is an option.
Wyzecam makes extremely affordable cameras that can be configured for local operation, though their default configuration sends data to Wyze's cloud services.
For users willing to spend more, security companies like Hanwha and Hikvision provide professional surveillance systems with no cloud requirements at all. These are overkill for home users but demonstrate that local-only operation is entirely feasible at scale.
The reason most smart home companies don't emphasize local operation is that it eliminates the data collection opportunity. But technically, it's straightforward. The infrastructure exists.
The reason the Fulu bounty matters is that it forces that conversation. If Ring ignores the bounty entirely and someone figures out how to modify Ring cameras for local operation anyway, it demonstrates that the surveillance requirement is a choice, not a necessity.
Choices can be changed.
The Future of Surveillance-Proof Smart Home Privacy
Looking forward, there are a few possible futures.
In one scenario, the Fulu bounty gets claimed. Someone figures out how to disable Ring's cloud connectivity while preserving local functionality. They provide instructions that a moderately technical person could follow. They take the
In another scenario, nobody claims the bounty. The technical barrier proves insurmountable, or people who could solve it decide it's not worth the legal risk or effort. Ring's surveillance network continues functioning unchanged. This probably becomes the default outcome, because the technical barriers are genuinely high.
In a third scenario, regulation steps in. Governments begin requiring that consumer devices support local-only operation, or they begin restricting how companies like Ring can share or use surveillance footage. This could happen in the EU where privacy regulations are stronger, or potentially in the US if enough political will accumulates around the issue.
In a fourth scenario, the market eventually provides alternatives. Companies realize that some customers deeply care about privacy and are willing to pay premium prices for devices that respect it. A market for privacy-first smart home devices develops. These devices emphasize local operation, minimize cloud connectivity, and market themselves explicitly against the Ring model.
All of these futures are possible. The actual future will probably be a combination of all four: some technical solutions developed, some regulatory pressure, some market differentiation, and most people continuing to use Ring and accepting the surveillance trade-off because convenience still wins.
But the bounty itself represents something valuable: a refusal to accept that surveillance is mandatory. It's a statement that control matters. It's a recognition that you should be able to modify devices you own.
Whether or not the bounty gets claimed, it signals that some people are serious about taking back control.
What This Means for Other Manufacturers
Ring isn't unique. The surveillance business model that Ring pioneered is spreading across the smart home industry. Every camera manufacturer is considering similar data monetization strategies. Every connected device represents an opportunity for telemetry collection.
If the Fulu Foundation successfully funds a bounty solution for Ring, it creates a precedent. It demonstrates that determined users will find ways to resist surveillance if given financial incentive and technical opportunity.
That has downstream implications. Other manufacturers have to consider whether building mandatory surveillance architecture into their devices is worth the risk that users will work around it. They have to calculate whether the data they'd collect is worth the brand damage and the technical arms race that might follow.
This doesn't necessarily mean they'll decide against surveillance. It just means they'll have to factor in a new cost: the possibility that users will take back control.
Some manufacturers might respond by being more transparent about data collection and giving users real options for local operation. Some might invest more heavily in technical barriers to prevent modification. Some might embrace the surveillance model completely, betting that most users won't care enough to resist.
The market will eventually sort out which approach works. But the Fulu bounty is pushing that market calculation in the direction of user control.
The Philosophical Question: Who Really Owns Your Smart Home?
Underlying all of this is a question that feels increasingly urgent: when you buy a device, do you own it?
This question has become contentious because technology companies have largely decided the answer is no. You buy hardware that you possess physically, but you license software that you don't truly control. The hardware without the software is a brick. So the company that owns the software owns your device, even if you own the physical components.
This is a relatively new arrangement. For most of human history, ownership was straightforward. You bought something, it was yours, you could do whatever you wanted with it. You could modify it, repair it, sell it, give it away.
Digital goods changed that equation. Software is different from physical property. It can be copied infinitely. It can be updated remotely. It can be disabled on company whim. It can be controlled in ways that physical property cannot.
Manufacturers have exploited that difference ruthlessly. They've built business models that depend on controlling the software even after customers paid for the hardware.
The Fulu Foundation is essentially asking: should ownership mean anything at all? If you bought a device, should you have the right to modify it? To repair it? To control how it functions and where your data goes?
These aren't abstract philosophical questions. They have concrete consequences. Farmers can't repair their own tractors because of DMCA-style restrictions. People who buy medical devices can't modify them. Smart home owners can't prevent their devices from functioning as surveillance nodes.
The Ring bounty is a small battle in a much larger war over ownership and control in an increasingly digital world.
When Private Companies Build Public Surveillance
There's another angle to this that deserves attention: Ring isn't just building surveillance for individual users. It's building surveillance infrastructure that law enforcement can access.
Ring has a formal partnership program with police departments. Cops can request footage from Ring cameras in specific neighborhoods to investigate crimes. In many cases, users aren't notified that their footage was requested or shared. The police get access to a surveillance network without having to build or maintain it themselves.
This creates a weird arrangement where private companies have built the backbone of neighborhood surveillance systems that government agencies can tap into whenever they want. Ring users, by accepting Ring's terms of service, have implicitly consented to being part of a law enforcement surveillance network.
Is that a problem? Opinions differ. If the choice is between police having no footage of crimes or having access to Ring footage, some people say police access is justified. Others say that allowing companies to monetize your data while also making it available to law enforcement without your explicit consent crosses a line.
This is another reason the Fulu bounty matters. It's not just about preventing Amazon from analyzing your home. It's about preventing your home from becoming part of a law enforcement surveillance grid built and operated by private companies.
If you can disable Ring's cloud connectivity, your camera stops participating in that larger network. Your footage stays local. Police can't tap into your device as part of neighborhood-wide investigations.
Again, opinions on whether that's good or bad will differ. But it's another layer of control that users should potentially have.

The Economics of the Bounty Model
Fulu Foundation's approach is clever economically. They're funding bounties using donations. The bounties are large enough to incentivize genuine technical work but not so large that they're unsustainable.
The
At the same time, $10,000 is small enough that Fulu can realistically fund it through donations from privacy advocates and concerned users. It's not like they need millions of dollars.
The genius of the bounty model is that it aligns incentives perfectly. Fulu gets the solution funded. The person who solves it gets compensated. Ring doesn't have to do anything (though they're exposed to criticism and brand damage). Users get the knowledge that a solution is theoretically possible.
This model could theoretically scale to other devices and other manufacturers. As Fulu builds credibility and funding, they could offer bounties for disabling surveillance on other smart home devices, on phones, on laptops, on anything where user control has been restricted.
The model also creates interesting pressure on manufacturers. If a bounty gets claimed repeatedly, it signals that users care about that specific feature. It gives manufacturers market information about what people actually want.
Practical Steps: What You Can Do Today
If you own a Ring camera and you're uncomfortable with Amazon's data practices, you have options that don't require waiting for someone to claim the Fulu bounty.
First, be aware of Ring's own privacy controls. The app allows you to disable some features and modify how footage is shared. These aren't perfect solutions—your footage still goes to Amazon—but they give you some control over visibility and access.
Second, consider your network. You can set up a separate network for smart home devices and restrict their ability to communicate with other devices or systems. This limits but doesn't eliminate cloud communication.
Third, consider replacing Ring entirely with a device that supports local-only operation. Yes, you'd lose your existing investment. But if privacy matters enough to you, it might be worth it.
Fourth, support organizations like Fulu Foundation that are pushing for user control. Donations directly fund bounties. Awareness spreads the message that people care about these issues.
Fifth, contact your elected representatives. Privacy in the smart home space isn't heavily regulated in the US. Pushing for regulation that requires local-only operation as a default could change the economic calculus for manufacturers.
None of these options are perfect. They all involve some compromise or effort. But they're better than passively accepting the current surveillance model.

The Bigger Picture: Right to Repair and Digital Ownership
The Ring bounty is part of a broader movement toward digital ownership and right to repair. This movement includes farmers fighting John Deere's restrictions on tractor repairs, independent phone repair shops arguing against Apple's monopoly on iPhone components, and everyday people wanting to control the devices they own.
These aren't isolated incidents. They're symptoms of a massive structural shift in how ownership works in the digital age. Companies have discovered that by controlling software, they can control devices even after the sale. That's incredibly profitable, which is why it's become standard.
But it's also creating backlash. Users are tired of being locked out of their own devices. Farmers need to repair their tractors. People need to fix their phones. Smart home users want control over their own security systems.
The Ring bounty is specifically about surveillance, but the underlying issue is bigger. It's about whether ownership means anything at all when companies retain legal and technical control over the products they sell.
This is probably the defining consumer issue of the next decade. It affects everyone who buys connected devices. It touches on data privacy, cybersecurity, environmental sustainability, and economic fairness.
Larger forces are building around this issue. Right to Repair legislation is gaining momentum in the EU and potentially in US states. Privacy regulations are expanding. Public opinion has turned against companies that treat users as secondary to surveillance profits.
The Ring bounty is a shot across the bow. It's saying: we're going to push back against mandatory surveillance. We're going to fund technical solutions. We're going to support users who want to take back control.
Whether this movement wins or loses will depend on whether enough people care enough to support it.
FAQ
What is the Fulu Foundation's Ring camera bounty?
The Fulu Foundation is offering a **
Why did Fulu Foundation prioritize Ring cameras for their bounty?
Ring's "Search Party" feature, revealed in a controversial Super Bowl commercial and leaked internal emails, sparked massive public outcry over neighborhood surveillance and data collection. The internal documents showed Ring's plans to eventually expand surveillance beyond finding lost dogs to tracking people and suspects. This public backlash created urgency around giving users the ability to reclaim control of their devices, which is why Fulu moved the Ring bounty to the top of their priority list.
How does Section 1201 of the DMCA affect this bounty?
Section 1201 of the Digital Millennium Copyright Act makes it illegal to circumvent digital rights management protections, even on devices you own. This means someone who figures out how to modify Ring cameras could face legal consequences if they publicly release their solution. However, Fulu bounty winners don't have to publish their findings—they can keep the solution private and still collect the bounty, protecting themselves from legal liability.
Can I modify my Ring camera today to stop Amazon data sharing?
Not easily. Ring cameras use closed firmware, encrypted cloud connections, and security measures designed to prevent modification. Physical access to the hardware would be required, likely involving specialized tools. Until someone claims the Fulu bounty and publishes instructions (if they choose to), modifying Ring cameras remains technically challenging and potentially legally risky for non-experts.
What are the technical barriers to disabling Ring's cloud connectivity?
Several barriers exist: you need physical access to the hardware and potentially specialized equipment, Ring uses secure boot processes that verify firmware signatures, cloud connectivity is deeply integrated into the system architecture, Ring regularly updates firmware (making solutions temporary), and circumventing these protections could violate the DMCA. These factors make the bounty a genuine technical challenge, not a simple software tweak.
Are there alternative security cameras that don't require cloud connectivity?
Yes, several options exist for local-only operation. Ubiquiti's Unifi Protect systems offer professional-grade cameras with optional cloud integration, HomeKit cameras from companies like Logitech prioritize local storage, and professional systems from Hanwha and Hikvision operate entirely without cloud services. These alternatives are often more expensive but provide better privacy control than Ring's cloud-dependent model.
What does it mean if I win the Fulu bounty for Ring cameras?
If you successfully develop a working solution, you must provide documentation showing it prevents Amazon data transmission while maintaining local camera functions, submit step-by-step instructions that a moderately technical person could follow in under an hour, prove the modification works, and provide reliable sources for any specialized tools needed. You then have the choice to keep the solution private and collect the bounty, or publish it and potentially face legal challenges under the DMCA.
Why doesn't Ring just offer local-only operation as an official option?
The technology is straightforward and entirely feasible—Ring could easily support local-only operation through local network storage or NAS integration. They don't offer it because Amazon's business model depends on cloud data collection. Ring's profitability comes from analyzing user data, integrating it with Amazon's broader ecosystem, and potentially selling insights to third parties. Local-only operation would eliminate these revenue opportunities, which is why it remains unavailable despite being technically simple.
How does Ring share data with law enforcement?
Ring operates a formal partnership program that allows police departments to request footage from Ring cameras in specific areas during investigations. In many cases, users aren't notified that their footage was requested or shared with authorities. This means your Ring camera participates in a law enforcement surveillance network without your explicit consent. Disabling cloud connectivity through the Fulu bounty solution would prevent your device from participating in this shared surveillance infrastructure.
What's the broader significance of the Ring bounty beyond just one camera?
The Ring bounty represents a larger battle over ownership and control in the digital age. It challenges the idea that companies can sell you devices while retaining complete control over them. It demonstrates that some users are serious about resisting mandatory surveillance. It signals to manufacturers that surveillance features carry brand risk. Most importantly, it raises the philosophical question: when you buy a device, do you actually own it, or do you merely license the right to use it according to corporate terms?
The battle over Ring cameras and the Fulu Foundation's bounty reveals something fundamental about power in the digital age. Companies have learned to lock down devices and extract value after the sale. Users are learning to push back.
The outcome of this specific fight matters less than what it represents: a refusal to accept that surveillance is inevitable. A recognition that control matters. A commitment to the idea that you should be able to own and modify the devices you bring into your home.
Whether the bounty gets claimed or not, it's already changed the conversation. It's given people permission to ask: what if I don't want Amazon in my security camera? What if I want actual control over my device?
That question, multiplied across millions of devices and hundreds of companies, might eventually force the market to offer privacy as a genuine option rather than a luxury.
That's worth $10,000. That's worth supporting. That's worth paying attention to.

Key Takeaways
- The Fulu Foundation is offering $10,000+ to disable Ring's mandatory Amazon data-sharing while preserving hardware functionality
- Ring's controversial Search Party feature sparked public outcry after internal emails revealed plans for expanding neighborhood surveillance beyond lost dogs
- DMCA Section 1201 creates legal barriers preventing researchers from publicly sharing device modification techniques, which is why bounties keep solutions private
- Ring cameras maintain constant cloud connections for Amazon's data monetization despite local-only operation being technically straightforward
- This bounty represents a broader fight over digital ownership and whether companies can retain control over devices after purchase
Related Articles
- Ring Doorbell Local Storage Bounty: The $10K Fight for Home Privacy [2025]
- Ring's Surveillance Problem: What Search Party Really Means [2025]
- Ring's AI Search Party: From Lost Dogs to Neighborhood Surveillance [2025]
- DJI Romo Hack: How One Loophole Exposed a Global Robot Army [2025]
- Online Privacy Questions People Are Asking AI in 2026 [Guide]
- Call of Duty: Warzone Mobile Shutting Down April 17, 2026 [Complete Guide]
![Ring Camera Privacy Bounty: $10K to Stop Amazon Data Sharing [2025]](https://tryrunable.com/blog/ring-camera-privacy-bounty-10k-to-stop-amazon-data-sharing-2/image-1-1771551371996.jpg)




