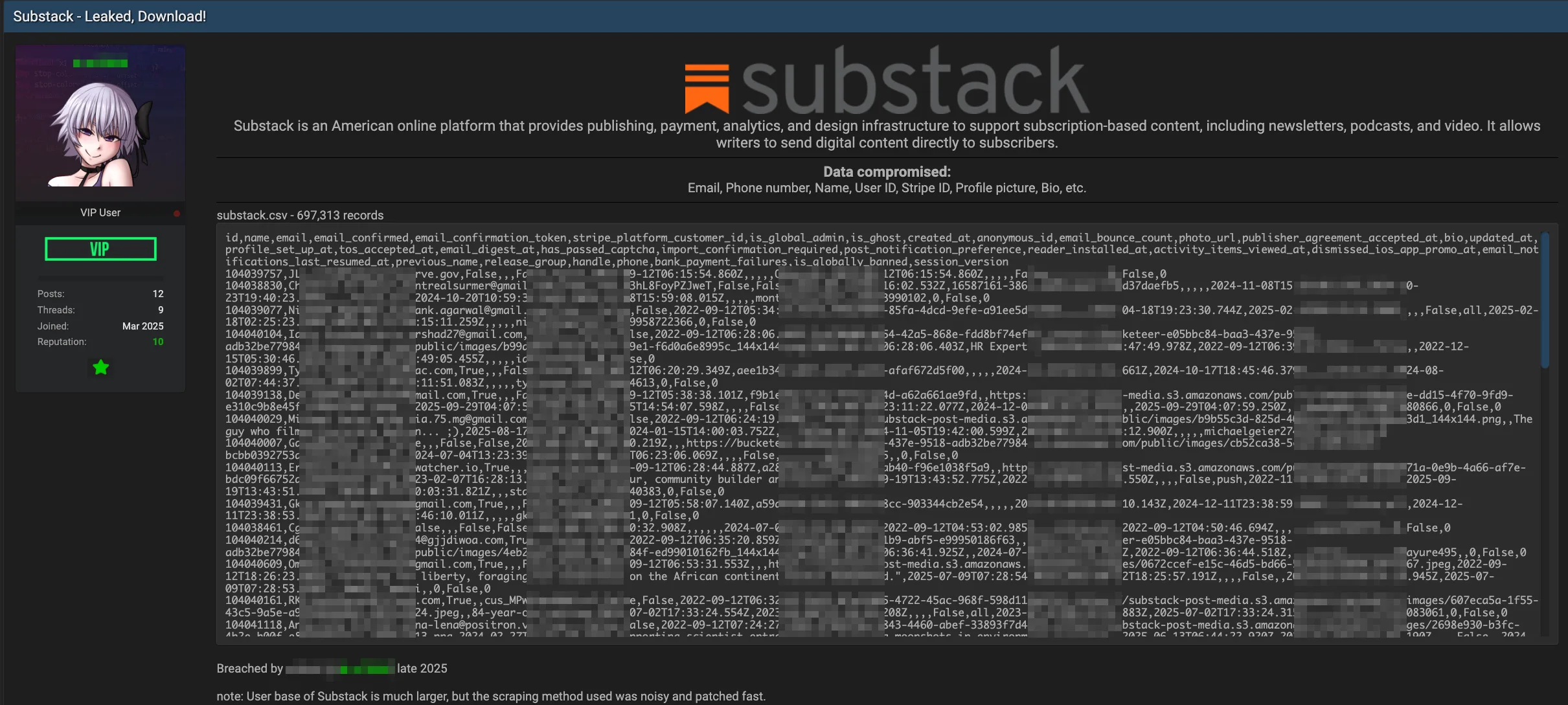
Understanding the Substack Data Breach: A Complete Security Breakdown
Imagine waking up to find that your email address and phone number—the keys to accessing countless accounts across the internet—have been stolen by a hacker. That's exactly what happened to some Substack users in October 2025, though the platform didn't publicly announce it until February 3rd, 2026. The breach wasn't some sophisticated zero-day exploit or nation-state-level attack. Instead, it was something far more common and far more preventable: an internal security failure that allowed an unauthorized third party to access limited user data without permission.
Substack, the newsletter platform that's become the go-to service for writers, journalists, and creators wanting to build direct relationships with their audiences, dropped a bombshell that reverberated through the creator economy. CEO Chris Best sent an email to affected users explaining that passwords and financial information remained secure, but the exposure of contact information opened the door to phishing attacks, SIM swapping, account takeovers, and harassment.
What makes this breach particularly frustrating is that it wasn't a sophisticated attack. It was a problem with Substack's systems that allowed unauthorized access. The company has since patched the vulnerability, but questions remain about why such a fundamental security gap existed in the first place, how long it went undetected, and what this means for the millions of creators and readers who depend on the platform.
This article breaks down everything you need to understand about the Substack breach: what happened, why it matters, what the real risks are, and most importantly, what you should do right now to protect yourself.
TL; DR
- The Breach: Substack suffered a security incident in October 2025 that exposed user email addresses and phone numbers to unauthorized parties.
- Detection Delay: The company didn't discover the breach until February 3rd, 2026, meaning the data was exposed for roughly four months.
- What's Safe: Passwords, credit card numbers, and other financial information remain secure and were not compromised.
- Who's Affected: The company hasn't disclosed the exact number of affected users, though affected individuals received notification emails.
- Immediate Actions: Substack users should watch for suspicious emails and text messages, enable two-factor authentication, and consider monitoring their accounts for unusual activity.
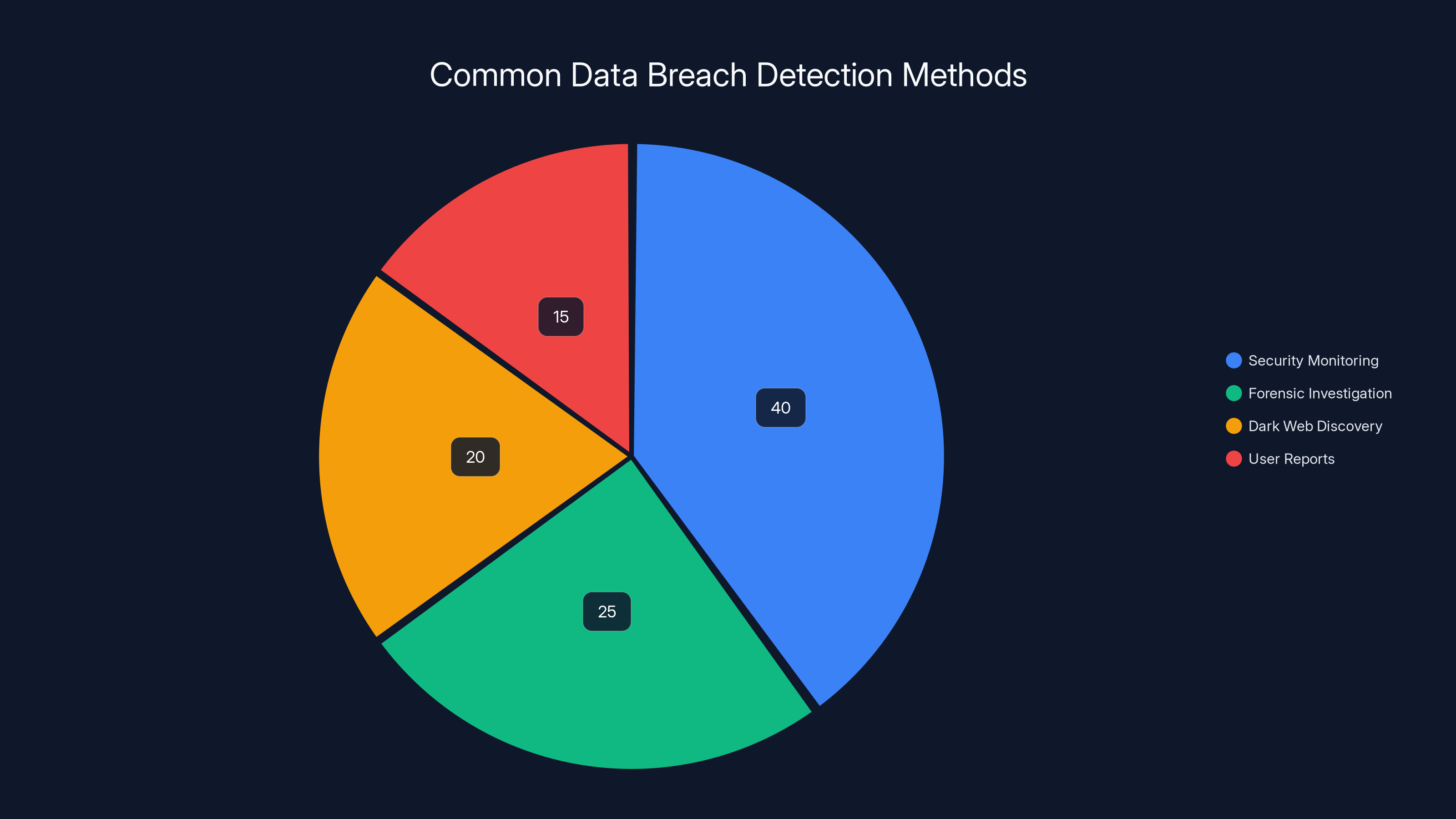
Security monitoring is the most common method used by companies to detect data breaches, accounting for an estimated 40% of detections. (Estimated data)
The Timeline: How the Breach Unfolded
Understanding when things went wrong is crucial to grasping the full scope of this breach. The timeline reveals both a security failure and a detection lag that extended the window of exposure.
The actual breach occurred in October 2025. During this month, a hacker found a vulnerability in Substack's systems that allowed them to access internal user data without authorization. The exact nature of this vulnerability hasn't been publicly disclosed by Substack, which is standard practice for companies dealing with active threats. However, the fact that it was discoverable at all suggests it wasn't a zero-day vulnerability requiring cutting-edge exploit techniques. It was more likely an authentication bypass, misconfigured access controls, or an unpatched known vulnerability.
For four months, the exposed data sat in the hands of the attacker or attackers. This is the truly alarming part. The data wasn't immediately used for widespread fraud or sold on dark web marketplaces that Substack detected. Instead, it simply existed outside of Substack's systems, accessible to whoever had obtained it.
On February 3rd, 2026, Substack finally detected evidence of the breach. The company identified suspicious activity or anomalies in their systems that indicated unauthorized access had occurred. This detection marks when the clock started on their response: notifying users, conducting a full investigation, and implementing fixes.
Within days, Substack began sending notification emails to affected users. CEO Chris Best's email to account holders was marked with an apology and an explanation of what had happened. The company stated it had "since fixed the security problem" and was working to "bolster its systems to prevent this type of issue from happening in the future."
The four-month gap between the October breach and February detection is significant. It means anyone who had the data during those months could have used it for phishing, social engineering, or other attacks. The real question is whether they did.
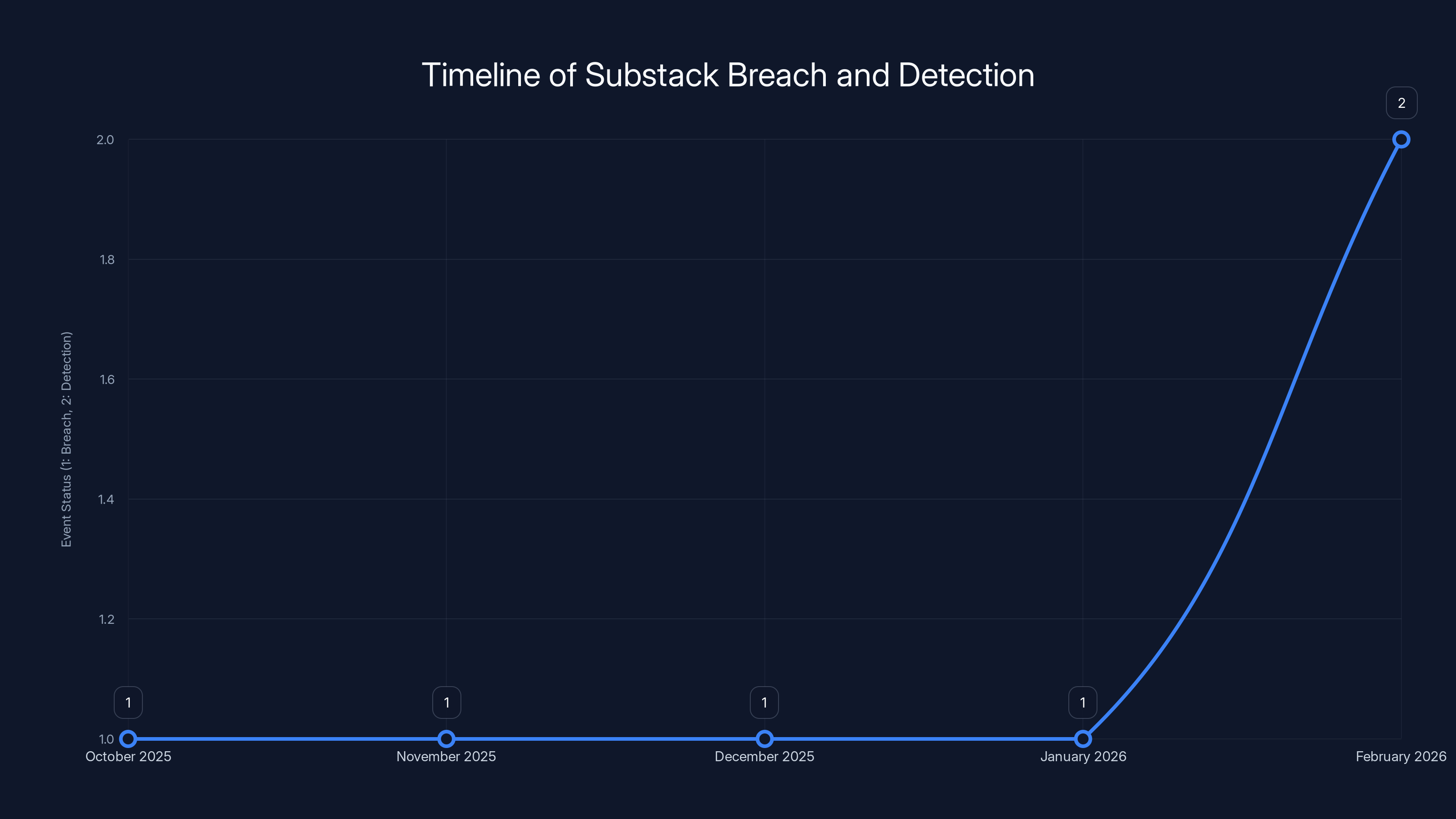
The breach occurred in October 2025 and went undetected until February 2026, highlighting a significant detection lag of four months. Estimated data.
What Data Was Actually Exposed
This is where precision matters. Substack has been explicit about what was compromised and what remains secure. Understanding the distinction could literally save you from identity theft.
Exposed Data:
- Email addresses linked to accounts
- Phone numbers associated with accounts
- Internal metadata (the nature of this remains vague)
Not Exposed:
- Passwords (even old, potentially reused ones)
- Credit card numbers and payment information
- Bank account details
- Subscription information or billing addresses
- Published content or draft newsletters
This distinction is critical. Your email address and phone number, while sensitive, are far less dangerous than your password. Passwords are keys to everything. If your Substack password had been exposed, attackers could have used it to attempt access to your account, and if you'd reused that password elsewhere (and statistically, you probably have), they could have accessed those accounts too.
Email addresses are valuable for phishing attacks. A hacker with your email address can send convincing-looking emails pretending to be Substack, your bank, your email provider, or any service you use. They might ask you to "verify your account" by clicking a link and entering your password. They might claim suspicious activity requires immediate action. These social engineering attacks are far more dangerous than the raw exposure of the email address itself.
Phone numbers enable SIM swapping attacks. This is where an attacker convinces your mobile carrier that they're you, and asks them to port your phone number to a new SIM card. Once they have your number, they can receive the two-factor authentication codes that protect your most important accounts. This is how cryptocurrency wallets get drained, email accounts get taken over, and financial accounts get compromised.
The internal metadata that Substack mentions is vaguer. This could include account creation dates, subscription tier information, or other contextual data. Without knowing exactly what's in this category, it's harder to assess the risk. But based on Substack's description, it seems to be non-sensitive operational data rather than personal information.
The Real Risk: Phishing, SIM Swapping, and Account Takeover
Knowing what was exposed is one thing. Understanding what attackers can do with that information is another entirely.
With your email address and phone number, attackers have the raw materials for several devastating attack vectors.
Phishing and Social Engineering
Your email address is now on an attacker's list. They know you're a Substack user. They can craft highly convincing emails claiming to be Substack support, reporting suspicious activity, asking you to verify payment information, or requesting you update your security settings. These emails might include Substack's actual branding, links that look legitimate, and messages tailored to how Substack actually communicates. A percentage of recipients will fall for these emails. They'll click the link, land on a fake login page, and enter their credentials. That's how phishing works, and the breach has essentially given attackers a pre-qualified list of potential victims.
The risk extends beyond Substack itself. An attacker with your email address can attempt to access your other accounts through "forgot password" flows. They can request password resets, hoping you won't notice the email before they access the account. This is particularly dangerous for email addresses tied to important accounts like banking, cryptocurrency exchanges, or email providers themselves.
SIM Swapping and Phone-Based Attacks
Your phone number is now known to attackers. SIM swapping is a sophisticated but increasingly common attack. Here's how it works: An attacker calls your mobile carrier and convinces them they're you. They've "lost" their SIM card and need a replacement. They provide your phone number, some personal information they've gathered, and request that the carrier port your number to a new SIM card they control.
Once successful, they have your phone number. Every two-factor authentication code sent via SMS is intercepted. Every voice call meant for you gets routed to them. They can now reset passwords for any account that uses SMS-based authentication.
This attack has made headlines because it's responsible for stealing millions from cryptocurrency traders, high-profile Twitter account takeovers, and complete account compromises across multiple platforms. Substack users might be particularly attractive targets because the platform is associated with creators, some of whom may have valuable email accounts or cryptocurrency holdings.
Account Takeover Through Account Recovery
With your email and phone number, attackers can try to recover access to your Substack account itself. If Substack uses either of these as authentication mechanisms in their password reset flow, attackers could potentially regain control. Substack's notification suggested they've secured these mechanisms, but the breach itself proves their security wasn't what it should have been.

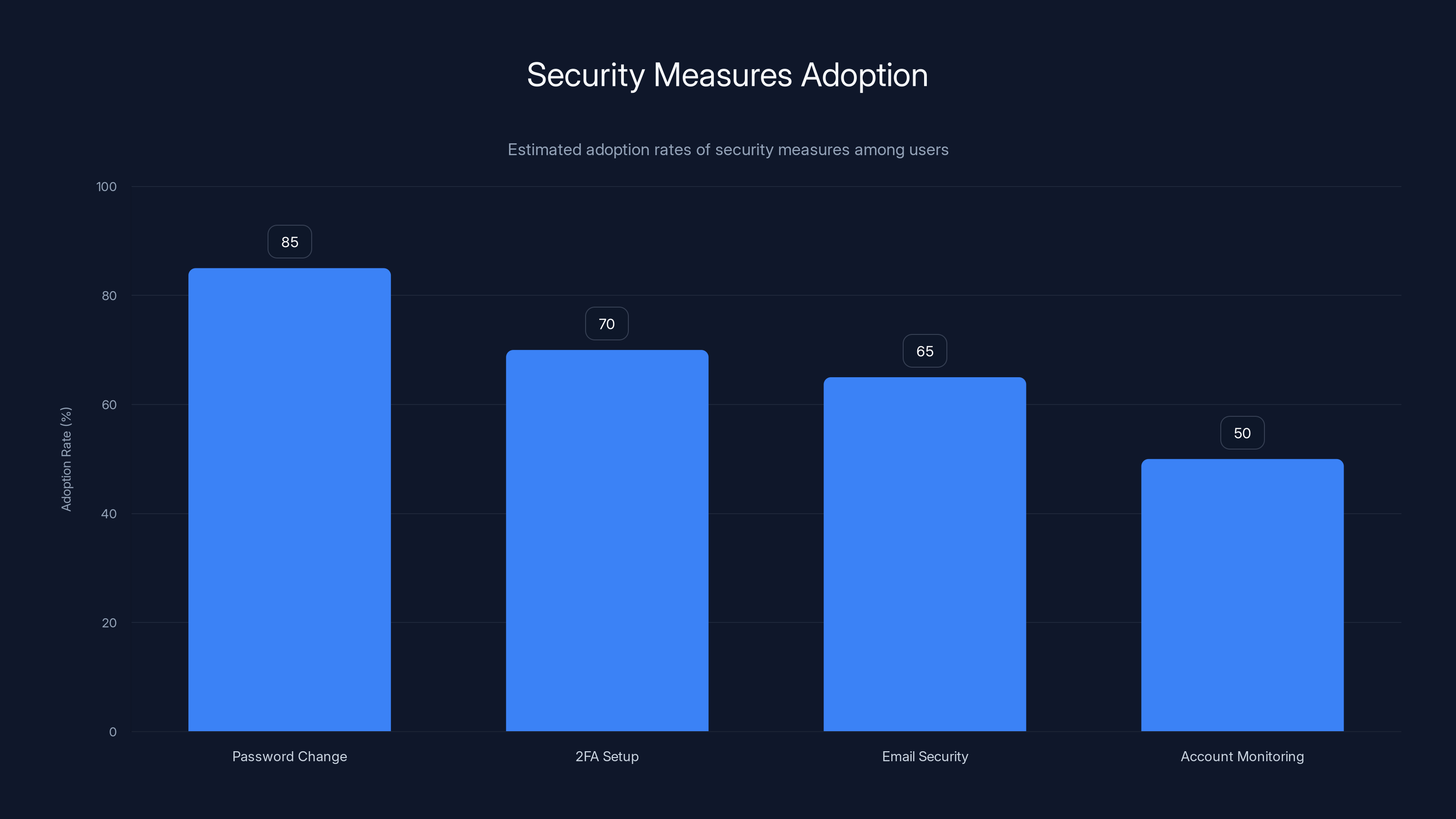
Estimated data suggests that while most users change passwords, fewer set up 2FA or monitor accounts regularly. Estimated data.
What Substack Did Right and Wrong
No response to a breach is perfect, but some responses are better than others. Let's assess Substack's handling of this incident.
What They Did Right:
Substack's CEO personally communicated about the breach. Chris Best didn't hide behind corporate PR speak or legal language. He said "I'm incredibly sorry this happened" and acknowledged that "we came up short." This personal accountability matters. It shows the company is taking the breach seriously rather than treating it as a legal obligation.
The company provided clarity on what was and wasn't exposed. Too many breach notifications leave users confused about what actually happened. Substack's email spelled out exactly what data was compromised and, just as importantly, what remained secure.
They acted quickly on the technical side. "We have since fixed the security problem" is a statement that requires verification, but the timeline suggests action was taken once the breach was detected.
They indicated they're conducting a full investigation alongside security improvements. This suggests they're not just applying a bandage but actually understanding what went wrong.
What They Did Wrong (Or Poorly):
The four-month detection window is indefensible. A company of Substack's size and maturity should have security monitoring that detects unauthorized data access far faster than February detection of an October breach. Did they not have proper logging? Did they not have anomaly detection in place? The lack of explanation is concerning.
No disclosure of affected user count. Substack hasn't said how many users were impacted. This is often withheld to avoid additional liability, but it makes it impossible for users to assess whether their specific account was affected.
No clear explanation of what the security vulnerability was. While it's reasonable not to publicize zero-day vulnerabilities, once fixed, a brief explanation of the vulnerability type (misconfigured access controls, authentication bypass, unpatched known vulnerability, etc.) would help users understand how to assess risk.
No proactive credit monitoring or incident response support offered. Some companies breached this badly offer credit monitoring services for a period. Substack's response didn't mention such measures.
No clear timeline for the investigation results. Substack said they're conducting an investigation, but didn't provide a timeline for when users can expect detailed findings.
Immediate Steps to Protect Yourself
If you're a Substack user, or even if you're not sure whether you're affected, here are the concrete actions you should take right now.
Step 1: Change Your Substack Password
Even though passwords weren't exposed in this breach, change your Substack password immediately. Use a strong, unique password you haven't used anywhere else. This is baseline hygiene after a breach that compromised contact information.
A strong password is at least 16 characters long and includes uppercase letters, lowercase letters, numbers, and symbols. Something like "Tr 0pic@l Thunder#2026" is strong. Something like "substack 123" is not.
Step 2: Enable Two-Factor Authentication on Substack
Two-factor authentication (2FA) adds a second layer of security. Even if someone has your password, they can't access your account without the second factor. Substack supports 2FA via authenticator apps. Set this up immediately.
When configuring 2FA, use an authenticator app (Google Authenticator, Authy, Microsoft Authenticator) rather than SMS-based 2FA. SMS is vulnerable to SIM swapping. Apps aren't. Write down your backup codes and store them in a safe place.
Step 3: Secure Your Email Account
Your email address is the master key to everything. If an attacker takes over your email account, they can reset passwords for every account linked to it. Implement these protections immediately:
- Change your email password to something unique and strong
- Enable two-factor authentication on your email account (use an authenticator app, not SMS)
- Review your account recovery options (backup email, phone number) to ensure they're accurate and under your control
- Check your email forwarding rules to ensure attackers haven't set up forwarding to capture your messages
- Review recently active devices and sessions, and sign out anything unfamiliar
Step 4: Monitor Your Accounts for Suspicious Activity
Watch for signs of attempted or successful account compromise:
- Login notifications from unfamiliar locations or devices
- Password reset emails you didn't request
- Changes to account settings you didn't make
- Unexpected charges on any accounts
- Spam or phishing emails increasing in volume
If you notice any of these, take immediate action to secure the account.
Step 5: Watch for Phishing Attempts
Be extremely suspicious of any emails claiming to be from Substack in the coming weeks. Look for:
- Requests to click links and "verify" information
- Urgent language about account security
- Requests for passwords or personal information
- Generic greetings ("Dear User" instead of your name)
- Misspelled domain names in sender addresses or links
If you receive a suspicious email allegedly from Substack, go directly to substack.com in your browser rather than clicking links in the email. Check your actual account to see if there are legitimate issues.
Step 6: Consider Using a Credit Monitoring Service
While your financial information wasn't directly exposed, attackers with your email and phone number could potentially open accounts in your name. Consider a credit monitoring service to watch for fraudulent activity:
- Credit freezes with the three major bureaus (Equifax, Experian, Trans Union)
- Credit monitoring services that alert you to new account openings
- Identity theft protection services
Many of these are free or low-cost.
Step 7: Be Cautious of Phone-Based Attacks
Call your mobile carrier and ask about their authentication requirements for account changes. Some carriers require in-person identification and a PIN to port a phone number. Set up additional security measures that make SIM swapping harder:
- Create a carrier PIN (requires entering the PIN to make account changes)
- Add a note to your account flagging it for additional verification
- Avoid posting your phone number on social media or public platforms
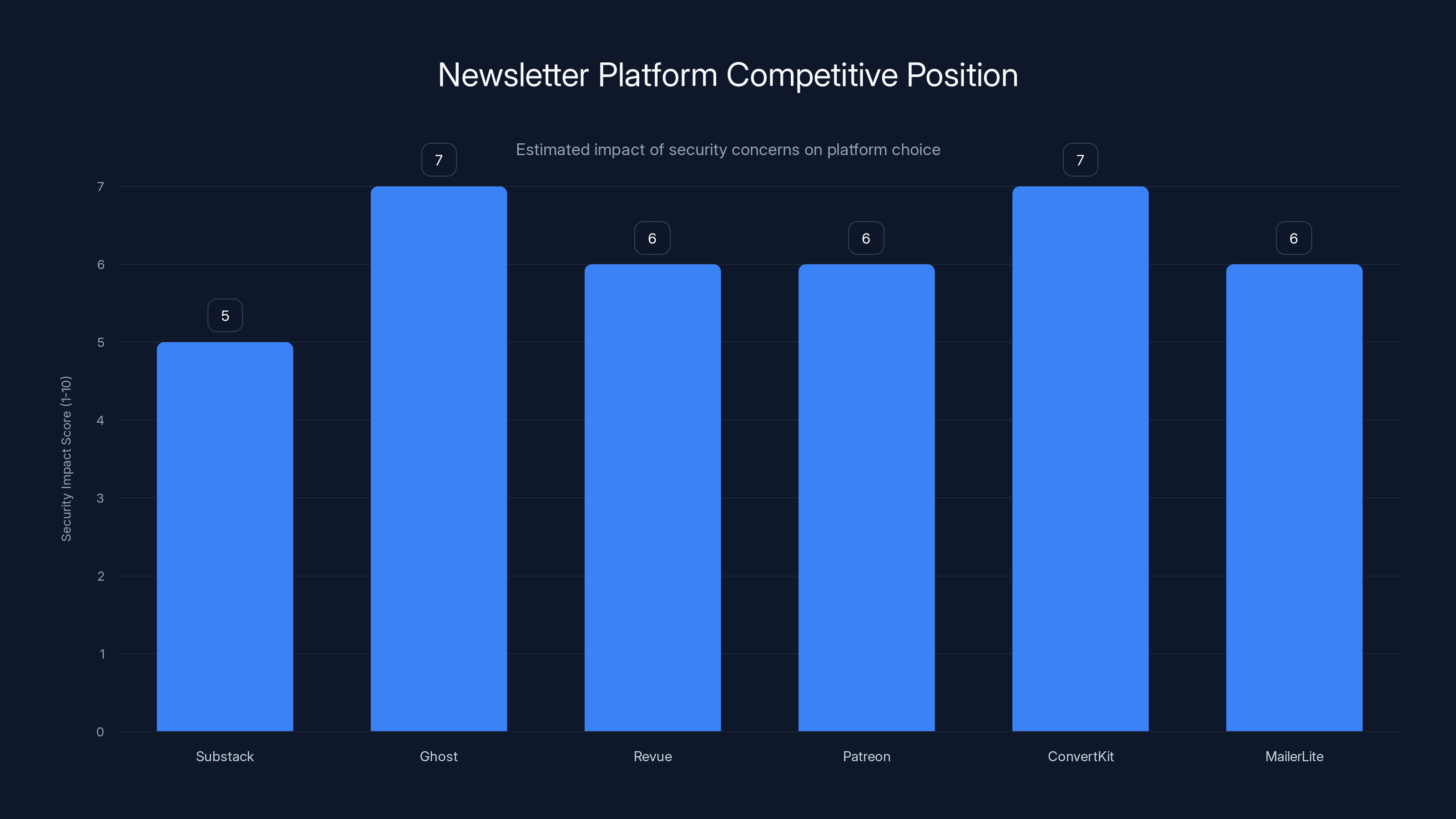
Estimated data suggests that security concerns could influence creators' platform choices, with Substack potentially losing ground if it doesn't address security effectively.
The Broader Security Context: Why This Breach Matters
Substack isn't the first platform to suffer a breach, and it won't be the last. But this breach illuminates larger security issues across the tech industry.
The creator economy has become increasingly centralized around platforms like Substack. Millions of writers, journalists, podcasters, and creators depend on Substack to reach their audiences and generate income. When Substack's security fails, the impact cascades through the creator community and their audiences.
This breach also reflects a common pattern: companies don't invest adequately in security until something goes wrong. Security infrastructure—intrusion detection, anomaly detection, security logging—costs money and doesn't generate revenue. So many companies under-invest until a breach forces them to explain why they didn't spend that money earlier.
The four-month detection window is particularly telling. This wasn't a sophisticated nation-state attack. It was a vulnerability in Substack's systems that could have been exploited by relatively unsophisticated attackers. Yet it went undetected for four months. This suggests Substack either didn't have adequate logging and monitoring in place, or didn't have the personnel to analyze that data.
This is a reminder that no platform is immune from breaches. Even well-funded, reputable companies with resources to invest in security can have fundamental vulnerabilities. The goal isn't to find a platform that's never had a breach (impossible) but rather to use platforms with strong security practices, monitor your own accounts, and take responsibility for your own security.

Lessons for the Broader Tech Industry
The Substack breach offers lessons that extend far beyond Substack itself.
Transparency Matters
Substack's direct communication from the CEO was refreshing compared to many corporate responses to breaches. Companies that acknowledge failures and take responsibility build trust. Companies that hide behind legal language and minimize the breach lose credibility.
Breach Detection Speed is Critical
The four-month detection window should be unacceptable by industry standards. Companies should have real-time security monitoring that detects unauthorized access within hours or days, not months. The industry needs to raise the bar.
Security Logging is Non-Negotiable
You can't detect what you don't log. Substack apparently didn't have adequate logging of data access, which is why they took so long to discover the breach. This is a baseline security requirement.
Contact Information is Sensitive Data
Email addresses and phone numbers should be protected with the same rigor as passwords. They're keys to account recovery and 2FA mechanisms. Companies need to minimize access to this data and monitor access closely.
User Communication Should Be Honest
Tell users exactly what happened, what was exposed, and what they should do. Vague language and legal minimization erodes trust. Honest communication about failures builds it back up.

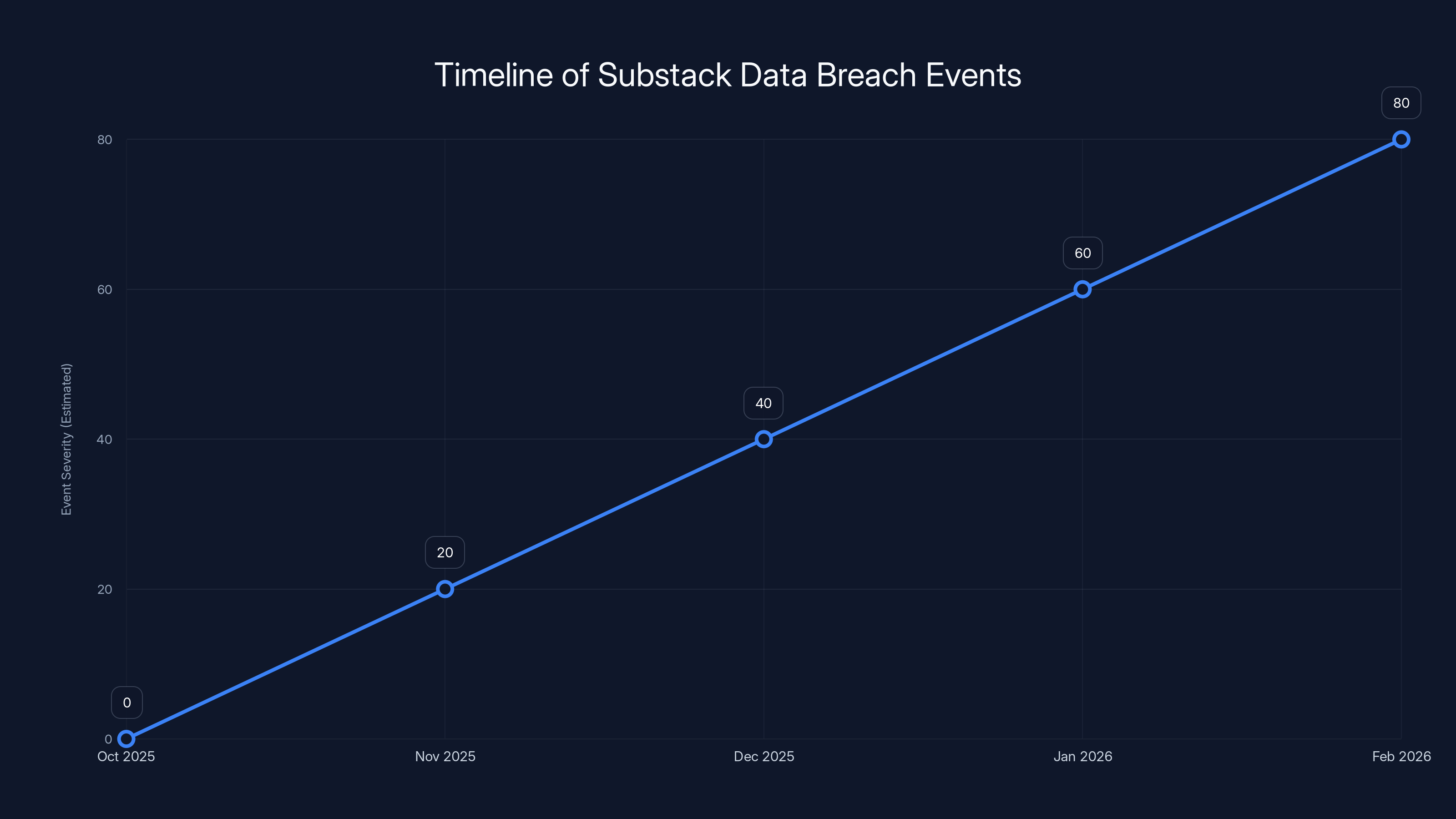
The Substack data breach was discovered in October 2025 but wasn't publicly announced until February 2026. This timeline illustrates the progression of events leading up to the public disclosure. Estimated data.
Long-Term Security Strategies for Users
Beyond immediate actions, how should users think about security in the context of breaches like this?
Embrace Passwordless Authentication
As long as passwords exist, they can be breached. Passwordless authentication using methods like hardware keys, biometrics, and cryptographic proofs is more secure. Support platforms that offer these options.
Diversify Your Risk
Don't keep all your important accounts on one platform. For critical services, consider maintaining multiple email addresses—one for high-value accounts (banking, cryptocurrency), one for general use, and potentially one throwaway email for services you don't trust as much.
Use Email Aliases
Many email providers allow you to create aliases or temporary email addresses. Use unique aliases for different services so that if one service is breached, attackers can't immediately link your multiple accounts.
Regular Account Audits
Monthly, review your active sessions and devices on important accounts. Check where you're logged in, review recent activity, and log out of anything unfamiliar. This catches compromises before they cause major damage.
Assume Breaches are Inevitable
Don't ask "if" your account will be breached but "when." Build your security posture with this assumption in mind. This mindset drives you to implement protective measures that mitigate damage when (not if) your data is exposed.
What Substack Users Should Monitor Going Forward
The breach notification is the beginning of the story, not the end. Here's what to watch for in the coming months.
Substack's Investigation Results
Substack said they're conducting a full investigation. When results are published, review them carefully. Look for:
- What specifically was the vulnerability? (Authentication bypass? Misconfigured access controls? Unpatched known vulnerability?)
- How many users were actually affected?
- What data was exposed to how many people?
- What preventive measures are being implemented?
- What monitoring improvements are being made?
These details will tell you whether Substack is genuinely addressing the root cause or just applying surface-level fixes.
Changes to Substack's Security Features
Watch for announcements about new security features: improvements to 2FA, security notifications, activity logs, etc. Strong platforms invest in security after breaches.
Your Own Account Activity
Continue monitoring your Substack account and linked accounts for suspicious activity even months after the breach. Attackers sometimes hold onto data before exploiting it.
Industry Response and Regulation
Breaches often drive regulatory action. Watch for new requirements around data breach notification, mandatory security measures, or liability for companies that suffer breaches. This could reshape how platforms like Substack operate.
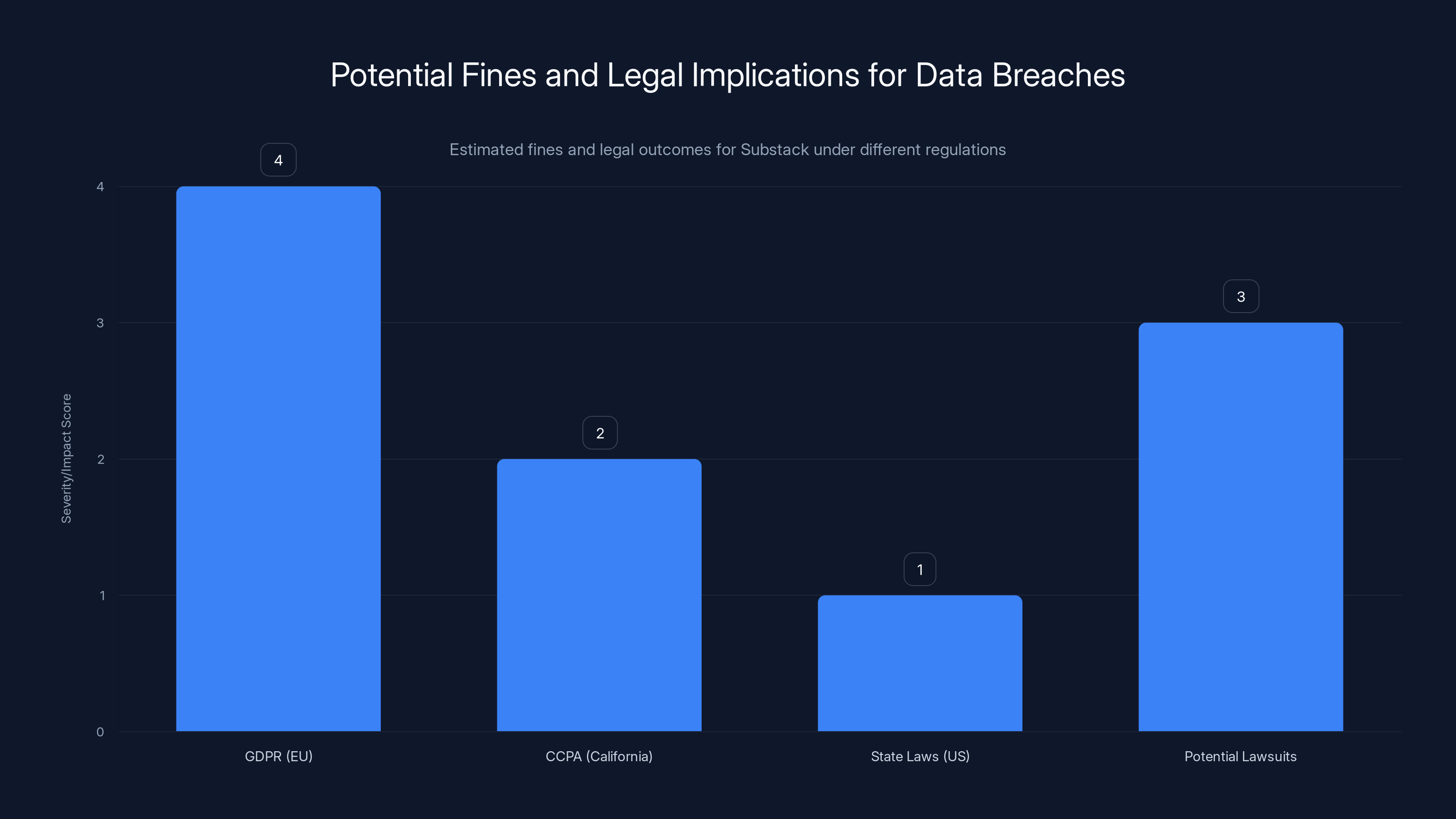
Estimated data shows GDPR poses the highest potential fine for Substack, followed by potential lawsuits. CCPA and state laws also present significant implications. Estimated data.
The Creator Economy and Platform Risk
The Substack breach has particular implications for creators who depend on the platform for their livelihoods.
Creators often tie together multiple platforms: Substack for newsletters, Twitter/X for promotion, Stripe or other payment processors for payments, and various analytics tools. A breach on one platform can have cascading effects across this ecosystem.
For creators to reduce their risk, they should:
- Maintain direct relationships with their audience (email lists they own)
- Diversify revenue streams across multiple platforms
- Implement strong authentication on all connected accounts
- Monitor their linked accounts for suspicious activity
- Consider what data they expose through their Substack profiles
Substack makes this easier than many platforms by providing export tools and APIs. Creators should periodically export their subscriber lists (where possible) and understand how to migrate their content if they ever need to leave the platform.
Comparative Analysis: How This Breach Compares to Others
Understanding how Substack's breach compares to other notable breaches provides context.
Twitter/X (2023): A massive breach exposed the email addresses of at least 235 million users. The scale made Substack's breach look small, but the response was also comparatively poor.
Discord (2021): Exposed user tokens and authentication cookies. This is arguably more dangerous than email addresses because tokens can grant immediate access. Discord's response was similarly brief.
Last Pass (2022): Multiple breaches compromised master passwords and encrypted vaults. The cascading revelations (initial breach, then larger breach) eroded trust significantly.
Substack (2025): Limited data exposure (email and phone), relatively prompt notification (once discovered), and direct communication from leadership. By industry standards, this is actually a more transparent response than many breaches, even though the four-month detection window is problematic.
The pattern across all these breaches is the same: companies under-invest in security, breaches happen, then companies scramble to respond. The hope is that increased scrutiny and regulatory pressure will push companies to invest in security before breaches occur rather than after.

Tools and Services for Breach Monitoring
Several services can help you monitor whether your information appears in breaches.
Have I Been Pwned is the most widely used service. You can enter your email address and see if it's appeared in known breaches. The service is maintained by Troy Hunt, a respected security researcher.
Breach Alert Services from major email providers (Gmail, Outlook, etc.) now notify you if your address appears in known breaches. Enable these if available on your email provider.
Credit Monitoring Services like Experian Identity Works or Equifax Complete Premier monitor credit bureaus for suspicious activity and new accounts opened in your name.
Password Managers like Bitwarden and 1Password include breach monitoring as a built-in feature. They'll alert you if your passwords appear in known breaches.
VPN Services with data breach monitoring (some paid VPNs offer this) scan the dark web for your exposed data.
These tools are complementary. Using multiple sources of breach monitoring gives you better coverage.
Substack's Competitive Position and This Breach's Impact
Substack faces competition from other newsletter platforms. How does this breach affect its competitive position?
Competitors
- Ghost: Offers newsletter hosting with a focus on creator independence
- Revue: Previously owned by Twitter, now Elon is shuttering it
- Patreon: Newsletter features alongside membership platform
- Convert Kit: Email and creator platform focused on solopreneurs
- Mailer Lite: More of a general email marketing tool
Creators considering these alternatives might now factor security into their decision. If competitors emphasize superior security practices, they could capture market share from Substack.
That said, Substack's strength isn't just security—it's the audience already on the platform. Creators with large Substack audiences are unlikely to migrate because of this breach unless Substack's response is demonstrably inadequate. This gives Substack some runway to address the security issues.
The real danger for Substack is if this becomes a pattern. One breach could be dismissed as inevitable. Multiple breaches or poor handling of the investigation would be far more damaging.

Technical Deep Dive: What Might Have Gone Wrong
While Substack hasn't disclosed the specific vulnerability, we can reasonably speculate about categories of vulnerabilities that could allow the described access.
Possibility 1: Authentication Bypass
A vulnerability that allows attackers to access internal systems without proper credentials. This could be an insecure direct object reference (IDOR), where incrementing a user ID in a URL grants access to different users' data. Or it could be broken authentication where session tokens aren't properly validated.
Possibility 2: Misconfigured Access Controls
Amazon S3 buckets and similar cloud storage services are frequently left publicly accessible due to misconfiguration. If Substack stores user data in cloud storage and misconfigured permissions, attackers could access it directly. This is increasingly common and often the root cause of breaches.
Possibility 3: Unpatched Known Vulnerability
Substack uses various open-source libraries and frameworks. If a vulnerability was discovered in one of these dependencies and Substack didn't patch it, attackers could exploit the known vulnerability.
Possibility 4: Insider Threat
Less likely but possible, an employee with system access could have exported the data. Substack would probably emphasize this wasn't the case if it were true, because it's even more damaging to trust in the company.
Possibility 5: Supply Chain Attack
A third-party service that Substack relies on could have been compromised, allowing attackers to access Substack's data through that third party. This is increasingly common.
Without details from Substack, we can't know which of these (or combination of these) was responsible. But the fact that it was discoverable and took four months to find suggests it wasn't an advanced persistent threat from nation-states, but rather a fundamental vulnerability that competent security monitoring should have caught far faster.
Regulatory and Legal Implications
Breaches trigger regulatory obligations that vary by jurisdiction.
GDPR (EU)
Substack is likely subject to GDPR if it has EU users (it almost certainly does). GDPR requires notification of affected individuals "without undue delay." The February notification of an October breach is pushing the limits of "without undue delay." Substack could face fines up to 4% of annual revenue for GDPR violations.
CCPA (California)
For California users, Substack is required to notify without unreasonable delay. The timeline here is also stretched. California has seen increasing enforcement, so Substack should expect regulatory attention.
State Breach Notification Laws
Most US states have breach notification laws requiring notification of affected residents. Substack is probably complying with these, but the timeline might come under scrutiny.
Potential Lawsuits
Substack will likely face class-action lawsuits from affected users. The question is whether they succeed. Recent trends have made it harder for plaintiffs to prove damages from a breach of email addresses and phone numbers (as opposed to financial data or passwords). But the lawsuits will happen regardless.
The regulatory and legal pressure might actually be beneficial long-term. It forces companies to take security seriously because there's now a financial and legal cost to breaches.

Recommendations for Substack Going Forward
If Substack is serious about preventing future breaches, they should implement these improvements.
Security Infrastructure
- Implement comprehensive security logging for all data access
- Deploy real-time anomaly detection to flag unusual access patterns
- Conduct regular penetration testing and red team exercises
- Implement intrusion detection systems
- Set up SOC (Security Operations Center) monitoring 24/7
Development Practices
- Implement secure SDLC (Software Development Life Cycle) practices
- Regular code reviews with security focus
- Dependency scanning to identify vulnerable libraries
- Automated security testing in the CI/CD pipeline
Access Control
- Implement principle of least privilege (employees only access data they need)
- Regular access reviews to revoke unnecessary permissions
- Multi-factor authentication for all internal systems
Data Protection
- Encryption of sensitive data at rest and in transit
- Data minimization (don't collect or store more data than necessary)
- Regular backups and tested disaster recovery
Transparency
- Detailed public disclosure of what went wrong
- Timeline for security improvements
- Regular security updates to users
- Consider a bug bounty program to get external security researchers testing your systems
Implementing these measures would signal to users and creators that Substack is serious about security.

The Future of Platform Security
The Substack breach is one incident in a larger pattern of platforms struggling with security. What does the future hold?
Increased Regulation
Governments are slowly increasing regulations around data protection and breach notification. This will drive companies to invest more in security.
Security as a Competitive Differentiator
As users become more aware of breaches, security claims will become a marketing tool. Platforms will compete on security the way they currently compete on features.
Shift to Decentralized Platforms
Some creators are exploring decentralized alternatives to centralized platforms like Substack. The theory is that decentralized systems are harder to breach because there's no central database of user data. This is oversold—decentralized systems have their own security challenges—but the concept is gaining traction.
Passwordless Authentication
Passwords will eventually become obsolete, replaced by cryptographic methods that are inherently more secure and can't be breached the way passwords are.
AI-Powered Security
Machine learning will increasingly be used for anomaly detection, threat identification, and automated response to security incidents.
The future of security isn't "never get breached" (impossible) but rather "detect breaches faster, respond better, and minimize damage when they occur."

FAQ
What exactly is a data breach?
A data breach is when unauthorized individuals gain access to sensitive information they shouldn't have access to. In Substack's case, the breach gave hackers access to email addresses and phone numbers associated with user accounts. The data either gets stolen by the attacker or inadvertently exposed due to misconfiguration or vulnerability. Breaches can range from a single person's information being exposed to millions of records being compromised.
How does a company detect a data breach?
Companies can detect breaches through security monitoring tools that watch for unusual access patterns, suspicious downloads of large amounts of data, unauthorized login attempts, or changes to systems they shouldn't change. Some breaches are discovered through forensic investigation after the company notices signs of compromise. Others are discovered when the stolen data appears for sale on dark web marketplaces, or when affected users report suspicious activity. Substack apparently used the first method, detecting evidence of unauthorized access through their monitoring systems in February 2026.
What should I do if my email was exposed in the Substack breach?
You should immediately change your Substack password to something unique and strong, enable two-factor authentication on Substack (using an authenticator app rather than SMS), and review your email account security. Enable two-factor authentication on your email account as well, check for unauthorized forwarding rules, and monitor your accounts for suspicious activity. Watch for phishing emails pretending to be from Substack, and be cautious of phone calls or messages claiming to be from your bank or other services. Consider using a credit monitoring service to watch for accounts opened in your name.
Is my Substack password compromised in this breach?
No, Substack explicitly stated that passwords were not exposed in this breach. Only email addresses and phone numbers linked to accounts were compromised. That said, it's still good practice to change your Substack password after a breach involving contact information, since it reminds attackers of your account's existence. Also, if you've reused this password on other sites, you should change it everywhere immediately.
How can I protect myself from SIM swapping attacks using my phone number?
SIM swapping is a serious risk when attackers have your phone number. To protect yourself, contact your mobile carrier and set up additional authentication requirements for account changes, such as a PIN code that must be provided before your phone number can be ported to a new SIM card. Request that your account be flagged for additional verification before any major changes. Avoid posting your phone number on social media or public platforms. Enable two-factor authentication on all important accounts using authenticator apps instead of SMS, since SMS codes are what attackers actually want when they perform SIM swaps.
Should I close my Substack account because of this breach?
Closing your account is a personal decision, but it's probably not necessary if you take proper security precautions. One breach doesn't automatically mean a platform is irredeemable. Your decision should depend on whether you trust Substack's response and their commitment to fixing the underlying security issues. Monitor Substack's official statements about the investigation results and security improvements. If you decide to stay, implement all the recommended security measures. If you want to diversify your risk, consider maintaining accounts on multiple platforms rather than relying on one platform entirely.
What does "internal metadata" mean in the context of the Substack breach?
Internal metadata refers to data about data—information about the accounts themselves rather than the account content. In Substack's case, this might include account creation dates, subscription tier information, the type of newsletters you publish, publication frequency, or other operational data. Substack was intentionally vague about this category, which is frustrating because it prevents you from fully assessing your exposure. It's generally less dangerous than passwords or financial information, but the vagueness makes it hard to be certain.
Can my Substack account be taken over if attackers have my email and phone number?
It's possible if Substack's account recovery process relies solely on email or phone number verification. Attackers with your email address could potentially request a password reset and intercept the reset email. If they also have your phone number and attempt SIM swapping, they could receive SMS codes meant for you. However, if Substack requires multiple forms of verification or has other safeguards in place, account takeover becomes harder. Enabling two-factor authentication with an authenticator app on Substack significantly reduces this risk.
What's the difference between this breach and previous major tech breaches?
Substack's breach is smaller in scale than some major breaches (Twitter's 235 million users, for example) but similar in what was exposed—contact information rather than passwords or financial data. What sets Substack apart is CEO Chris Best's direct acknowledgment of the problem and apology. Many companies try to minimize breaches or hide behind corporate language. Substack's response was more transparent, which built some goodwill despite the security failure. The negative side is the four-month detection window, which is slow by modern standards.
Should I trust Substack with my information going forward?
Trust is earned through actions, not words. Substack acknowledged the breach quickly (once they detected it) and communicated clearly. However, the four-month detection window shows gaps in their security monitoring. Going forward, trust depends on whether they implement the security improvements they've promised and whether there are additional breaches. Continue using Substack if the value is worth the risk, but maintain strong security practices on your own accounts regardless. Never put all your trust in a single platform.
The Substack breach is a reminder that security breaches affect even reputable, well-funded companies. The breach of email addresses and phone numbers, while not containing passwords or financial information, opens users to phishing, SIM swapping, and account takeover attempts. The key to protecting yourself is taking immediate action: changing your password, enabling two-factor authentication, securing your email account, and monitoring for suspicious activity. Going forward, assume that your data will eventually be breached somewhere, and build your security practices with that assumption in mind. Use unique passwords everywhere, implement two-factor authentication on important accounts, and stay vigilant for social engineering attacks. The goal isn't to prevent all breaches (impossible) but to minimize damage when they inevitably occur.
Key Takeaways
- Substack exposed user email addresses and phone numbers in an October 2025 breach, but the company didn't detect it until February 2026.
- Passwords and financial information remain secure, but the exposed contact data enables phishing, SIM swapping, and account takeover attacks.
- Immediate protective actions include changing your Substack password, enabling two-factor authentication with an authenticator app, and securing your email account.
- SIM swapping is a serious attack vector enabled by exposed phone numbers; contact your mobile carrier to add authentication requirements for account changes.
- Watch for phishing emails in the coming months and monitor your accounts for suspicious activity, as attackers may leverage the exposed data for secondary attacks.
Related Articles
- Password Security Guide: Why Strong Credentials Matter in 2025
- Harvard & UPenn Data Breaches: Inside ShinyHunters' Attack [2025]
- Malwarebytes and ChatGPT: The AI Scam Detection Game-Changer [2025]
- Reclaim Your Browser: Best Ad Blockers & Privacy Tools [2025]
- 8.7 Billion Records Exposed: Inside the Massive Chinese Data Breach [2025]
- Android Privacy Tips: Protect Your Device From Prying Eyes [2025]
![Substack Data Breach Exposed Millions: What You Need to Know [2025]](https://tryrunable.com/blog/substack-data-breach-exposed-millions-what-you-need-to-know-/image-1-1770289593254.jpg)



