Stalkerware Data Breach: 500,000 Records Leaked by Hacktivists [2025]
A few months ago, something happened in the shadows of the internet that should concern everyone. A hacktivist with the alias "wikkid" took aim at a company operating multiple stalkerware applications and walked away with over half a million customer records. Names. Email addresses. Partial credit card details. Proof that some of the most invasive surveillance software on the planet had terrible security protecting its own users.
This wasn't sophisticated. The hacker didn't need zero-days or advanced persistent threats. They found what they described as a "trivial" bug on Struktura's website—a Ukrainian software company allegedly behind applications like Geofinder, u Mobix, and Peekviewer—and exploited it to scrape an entire customer database.
The breach matters for more reasons than just the numbers. It exposes the hypocrisy of an industry built on invasion of privacy while protecting customer data about as well as a house of cards protects against wind. It raises uncomfortable questions about who's watching the watchers, what happens when vigilante justice meets corporate negligence, and whether hacktivists fighting a morally justified battle against abusive software can justify the collateral damage they cause.
Here's what really happened, why it matters, and what you need to know about protecting yourself in a world where surveillance is just a download away.
TL; DR
- 536,000 customer records were stolen from Struktura, a stalkerware developer, through a basic website vulnerability, as reported by TechBuzz.
- Exposed data included names, emails, purchase history, partial credit card numbers (last 4 digits), and which spy app customers bought.
- Payment card dates were not included, limiting fraud risk but still exposing personal information.
- Hacktivist motivation was explicitly stated as targeting apps used to spy on people, raising ethical questions about vigilante cybersecurity.
- No official response from Struktura or its parent company at the time of the breach becoming public.
- Broader implications highlight how surveillance software companies often fail at basic security while selling invasive products.
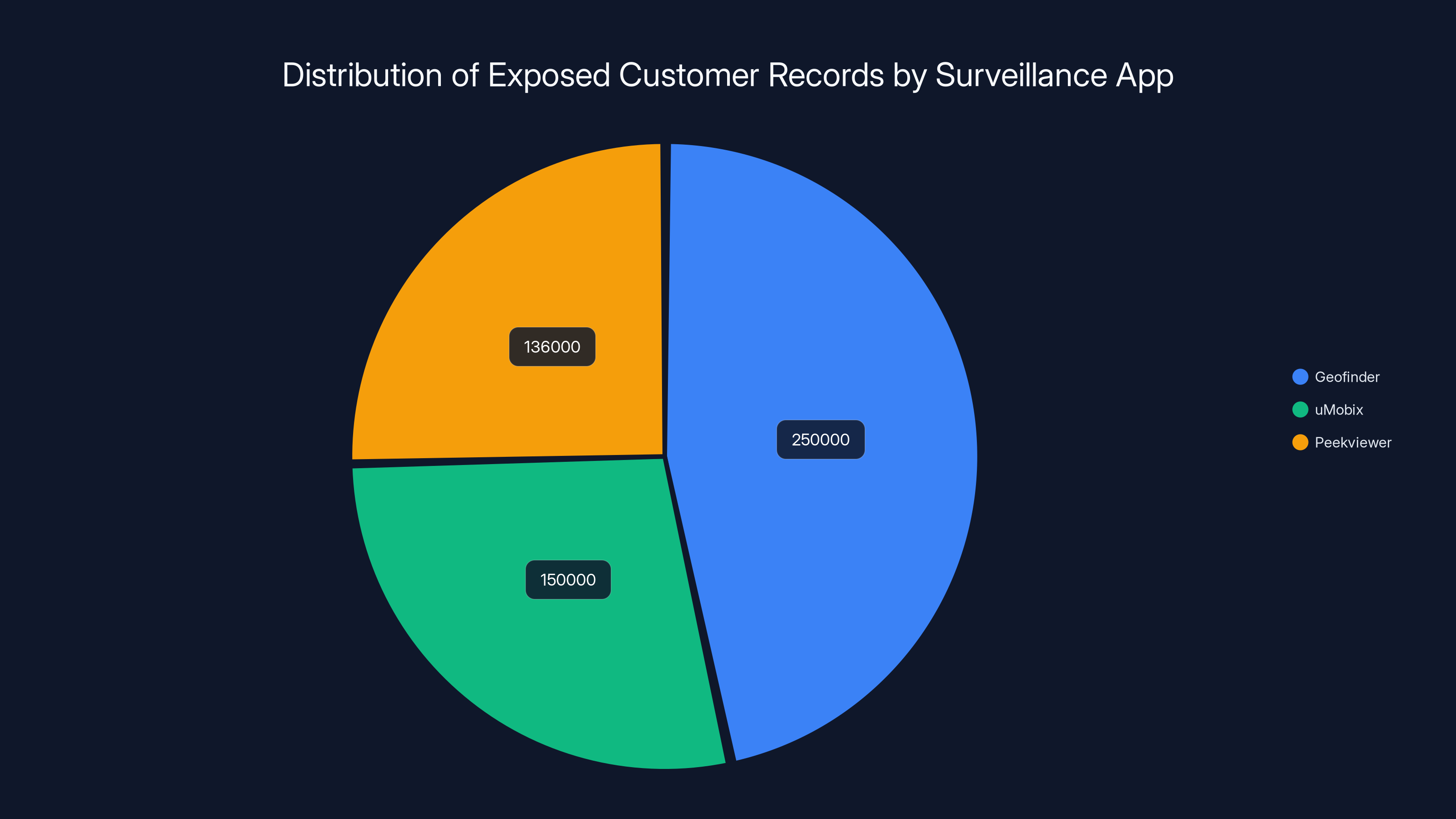
Estimated distribution of exposed records shows Geofinder had the largest share, followed by uMobix and Peekviewer. Estimated data based on typical market shares.
What Exactly Happened: The Struktura Breach Timeline
Understanding how this breach occurred requires looking at the specific sequence of events and the technical vulnerability that enabled it.
In early reports, the hacktivist "wikkid" contacted media outlets explaining their actions. They described discovering what they called a "trivial" bug in Struktura's website infrastructure. For someone not versed in web security, the word "trivial" might sound insignificant. In reality, it suggests a basic oversight that should've been caught by any competent security team.
The vulnerability allowed the hacker to scrape customer data directly from Struktura's servers without requiring authentication. This isn't some exotic exploitation technique. It's the kind of thing that security researchers find on misconfigured AWS S3 buckets, unprotected API endpoints, or improperly validated database queries.
Wikkid extracted 536,000 complete customer records in total. The dataset included names and email addresses. It included information about which application each customer had purchased—whether that was Geofinder for location tracking, u Mobix for comprehensive phone monitoring, or Peekviewer for covert surveillance. It included transaction amounts showing how much customers paid for their surveillance tools.
The database even included partial credit card information: the card type (Visa or Mastercard) and the final four digits of each card number. This alone is concerning because even partial card details can be used for targeted phishing, social engineering, or fraud.
What was notably absent? Payment dates. While this limitation reduced the potential damage from payment fraud, the hacker still had enough information to map customer spending patterns and create a comprehensive profile of who buys stalkerware and what they're willing to spend on it.
Verification of the breach's authenticity came through methodical investigation. Journalists independently triggered password reset requests using public email addresses from the leaked dataset. They received legitimate password reset emails from Struktura, confirming those accounts existed. They also matched transaction invoice numbers with data they could retrieve from the surveillance vendor's own checkout pages, proving the transaction records were real.
This verification is important because it separates credible breaches from false claims. Someone could fabricate a data list. But when you can independently confirm transactions through a company's own systems, the breach becomes irrefutable.
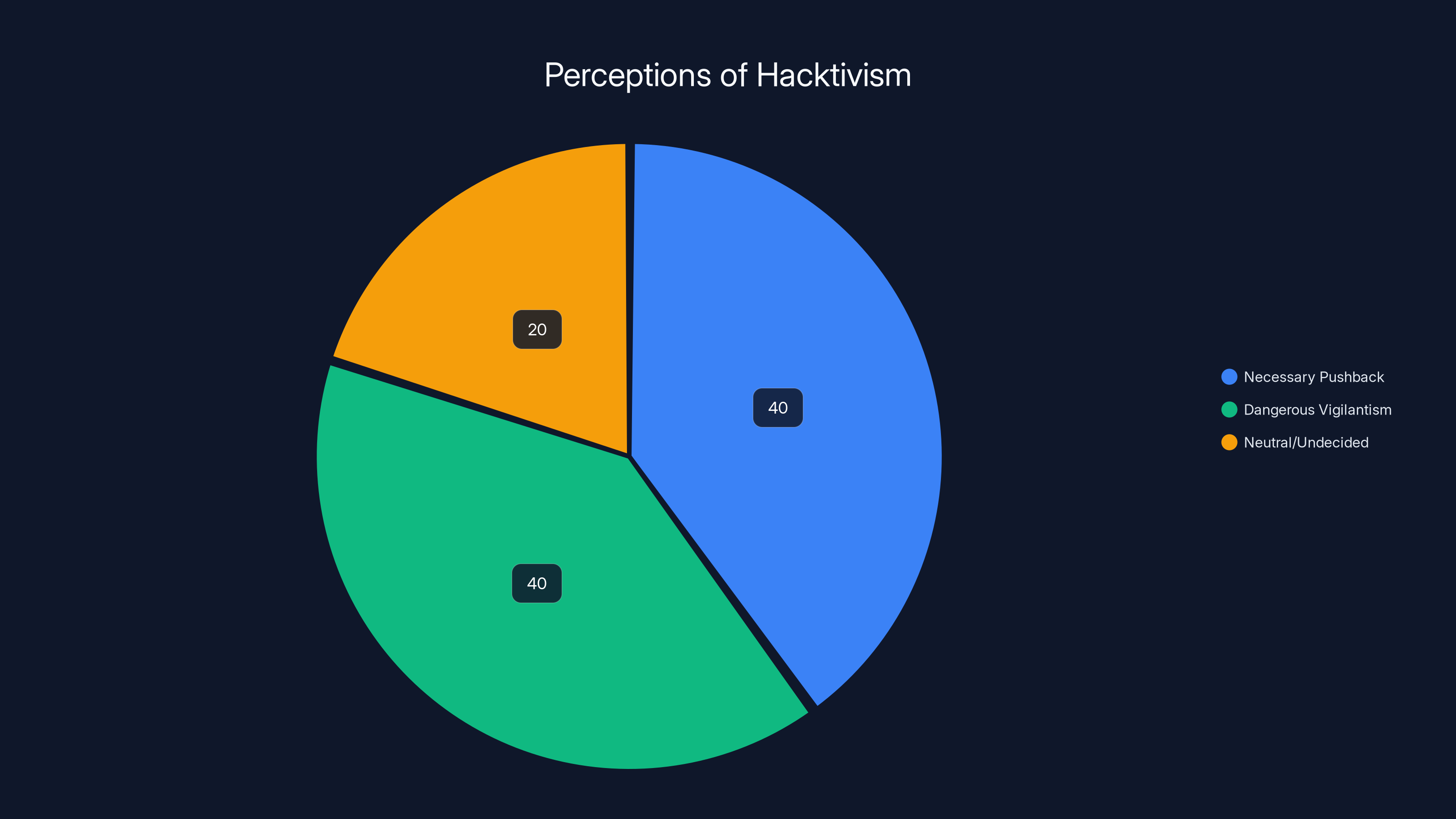
Estimated data shows a split in public perception of hacktivism, with equal views on it being necessary pushback and dangerous vigilantism, while a smaller portion remains neutral or undecided.
Who Is Struktura and What Are These Apps?
Struktura isn't a household name, but the applications it operates are found on hundreds of thousands of devices worldwide. Understanding what these applications do is critical to understanding why someone might justify attacking the company.
Geofinder is marketed as a GPS tracking application. The legitimate use case would be parents tracking their children's location or employers monitoring company vehicles. In practice, it's been used for intimate partner abuse, stalking, and non-consensual surveillance.
u Mobix is more comprehensive. It doesn't just track location. It monitors text messages, social media accounts, call logs, browser history, photos, and videos. It can record phone calls and ambient audio. The advertising material claims it's for parents monitoring children or employers monitoring employees. The reality is that it's frequently purchased by people who want to monitor spouses, partners, or people without their knowledge.
Peekviewer focuses on covert monitoring. Like u Mobix, it captures communications and activity, but it's explicitly designed to remain hidden on the target device.
These applications are part of a category called "consumer spyware" or "spouseware." The industry that produces them is worth hundreds of millions of dollars. Thousands of companies operate in this space, from large developers to small operations run from apartments. The marketing materials consistently use the same cover story: security for children or elderly relatives.
The reality is different. Multiple studies by privacy organizations and journalists have documented that these applications are overwhelmingly used for abuse. A study by the Cyber Civil Rights Initiative found that of reported cases involving spyware, 81% involved intimate partner violence.
So when wikkid targeted Struktura specifically, the hacker framed it as targeting a company that profits from enabling abuse. Whether you agree with the methodology, the moral argument has weight.

The Exposed Data: What Was Leaked and Why It Matters
The dataset contained 536,000 records with specific categories of information. Let's break down what was actually exposed and the potential harm from each component.
Names and Email Addresses: These are the foundation of identity. Combined with other information, names and emails enable targeted phishing, social engineering, and account takeover attempts. Someone now knows the email address of a person who purchased stalkerware, which creates obvious embarrassment and social risk.
Purchase History: Knowing exactly which surveillance application someone purchased reveals intent. A parent who bought Geofinder for their teenager's safety has a different risk profile than someone who bought u Mobix specifically for monitoring a spouse without consent. This data allows for targeted social engineering based on assumed relationships.
Partial Credit Card Information: The final four digits of a card might seem innocuous. In reality, these digits are often the only variable that differentiates multiple cards on the same account. Someone with this information can identify which specific card was used, cross-reference it with their own financial records, and potentially commit fraud.
Application Purchase Amounts: This reveals spending patterns. Someone who paid $500 for a year of monitoring service reveals different behavior than someone who paid for a month. High spenders might be either committed abusers or security-conscious parents. Either way, the pattern is now exposed.
What's critical to understand is that this data wasn't a random sample. Every single person in this database made a deliberate purchase. They bought something that enabled surveillance. That makes the breach a specific vulnerability for a specific community.
The hacker stated that payment dates weren't included in the extraction. This was a fortunate oversight for potential fraud prevention. Payment dates combined with card numbers and expiration dates would've created a much more serious financial risk. However, the dates' absence doesn't eliminate the threat entirely.
Consider what happens next. Someone now has the email address of 536,000 people who purchased stalkerware. They know which application each person bought. They can now:
- Send targeted phishing emails pretending to be from the company or a competitor
- Contact them claiming to be a victim who discovered their surveillance
- Sell the list to data brokers who create detailed profiles
- Use it for blackmail, claiming they'll publicly identify customers
- Cross-reference these emails with other breached databases to build comprehensive profiles
The data itself is useful for multiple criminal enterprises. The psychological impact is also significant. Many people who purchase surveillance software do so covertly. The knowledge that their identity and purchase are now public creates a major problem.
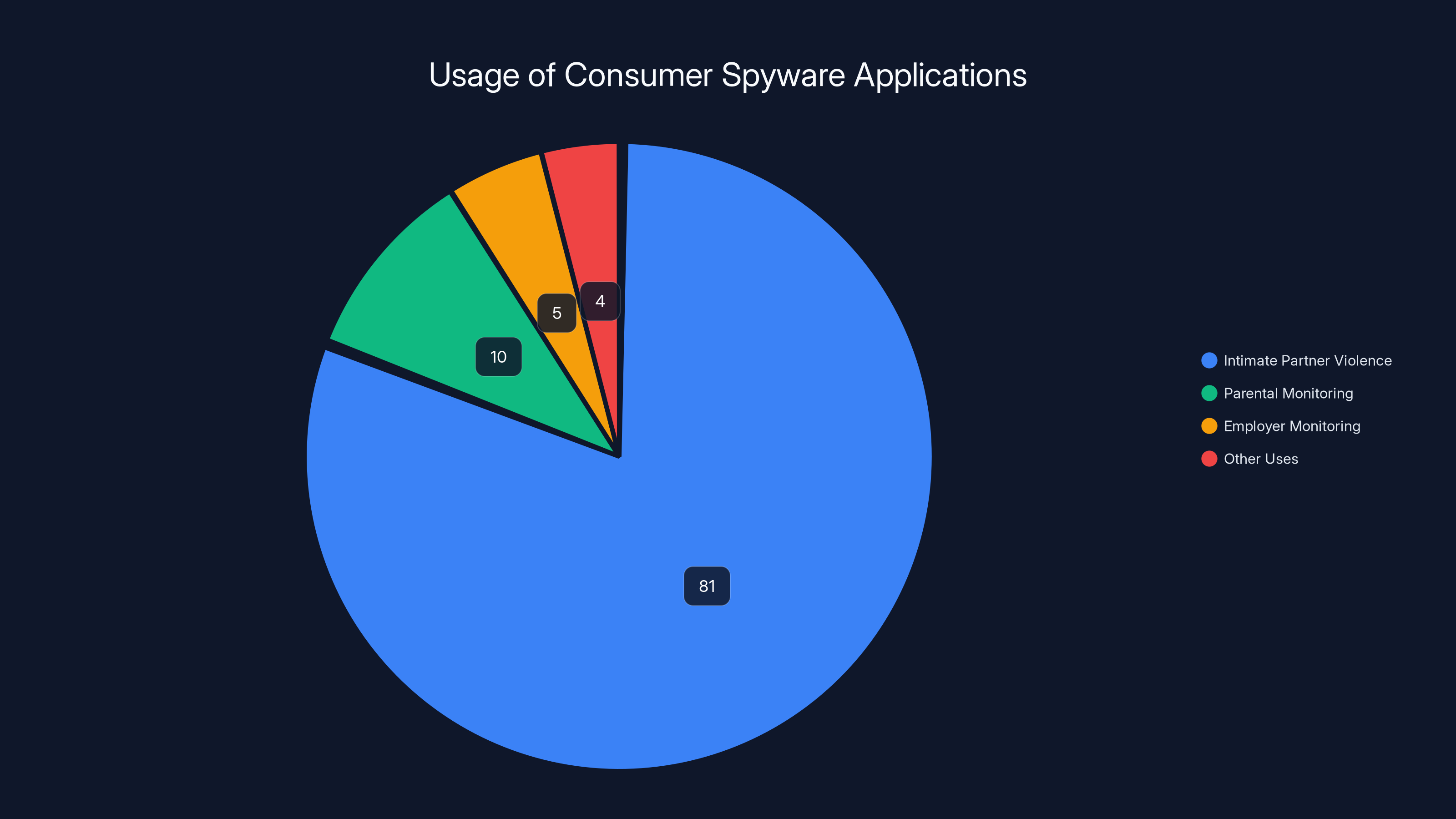
An estimated 81% of consumer spyware applications are used in cases of intimate partner violence, highlighting the potential for abuse. Estimated data based on reported cases.
Why This Happened: The Technical Vulnerability Explained
The hacker described the vulnerability as "trivial." Let's break down what that likely means in concrete technical terms.
Web applications typically require authentication for accessing customer data. You log in with a username and password, receive a session token, and then can view your own information. Proper security means that even if you're logged in, you can only access your own data, not anyone else's.
A trivial vulnerability in this context probably means one of several things:
Broken Access Control: The application didn't properly verify whether the user requesting data had permission to access it. For example, an API endpoint like "/api/customers/12345" might return that customer's data regardless of who made the request, instead of checking whether the requester was that specific customer.
Parameter Tampering: Customer IDs might be sequential numbers. So if you're customer 5000, and you change the URL to "/api/customers/5001," you'd see the next customer's data. By looping through numbers, you could retrieve all customers.
Information Disclosure: The company might've exposed API documentation, developer notes, or configuration files that explained how to access customer data directly without the normal web interface.
Unprotected Data Export: There might've been a backup or export function that was supposed to be admin-only but was accessible to anyone who knew the right URL.
All of these fall under "trivial" in security terminology. They're not sophisticated. They're not advanced persistent threat tactics. They're basic oversights that any security audit should've caught.
The fact that a surveillance company—a company whose entire business model depends on accessing other people's data covertly—failed to protect its own customer data with basic security controls is darkly ironic.
This happens more often than you'd expect. Companies focused on their core business (in this case, surveillance software) sometimes deprioritize information security. They assume they're too small to be targeted, or they cut corners on security implementation to ship products faster.
The Hacktivist Angle: Vigilante Justice or Dangerous Precedent?
Wikkid's explicit statement was that they targeted the company because it operates "apps used to spy on people." This framing is important because it separates this breach from typical cybercrime, which is motivated by profit.
Hacktivism—using hacking skills for political or social causes—has a complex history. Some view it as necessary pushback against harmful corporations. Others see it as dangerous vigilantism that violates laws and creates risks for innocent people.
In this case, the hacker arguably had a point worth considering. Struktura's applications genuinely enable abuse. They're used to monitor people without consent. They're used in intimate partner violence situations. The company markets them under false pretenses (parental monitoring) while knowing they'll be used for stalking.
At the same time, this breach affected all customers, not just abusers. Some people bought these applications for legitimate purposes: a parent genuinely monitoring their child's safety, an employer tracking company vehicles, a small business owner monitoring operations. These people's information is now compromised too.
There's also the question of proportionality and authority. If the applications are genuinely illegal, the proper response is law enforcement investigation and prosecution. If they're legal but unethical, the response should be regulation and advocacy. Taking matters into your own hands as a hacker, regardless of the moral justification, sets a precedent.
What happens when someone uses this same logic against an organization they disagree with for different reasons? If it's acceptable to breach a surveillance company because the products are harmful, what about a dating app that you think enables predatory behavior? A weapons manufacturer? A tobacco company? A cryptocurrency exchange?
The hacker's motivation was activist, but the mechanism—accessing and publishing customer data—is a tactic used in every data breach, regardless of motivation. The people whose data gets exposed don't care whether the attacker had a good cause. They're exposed either way.
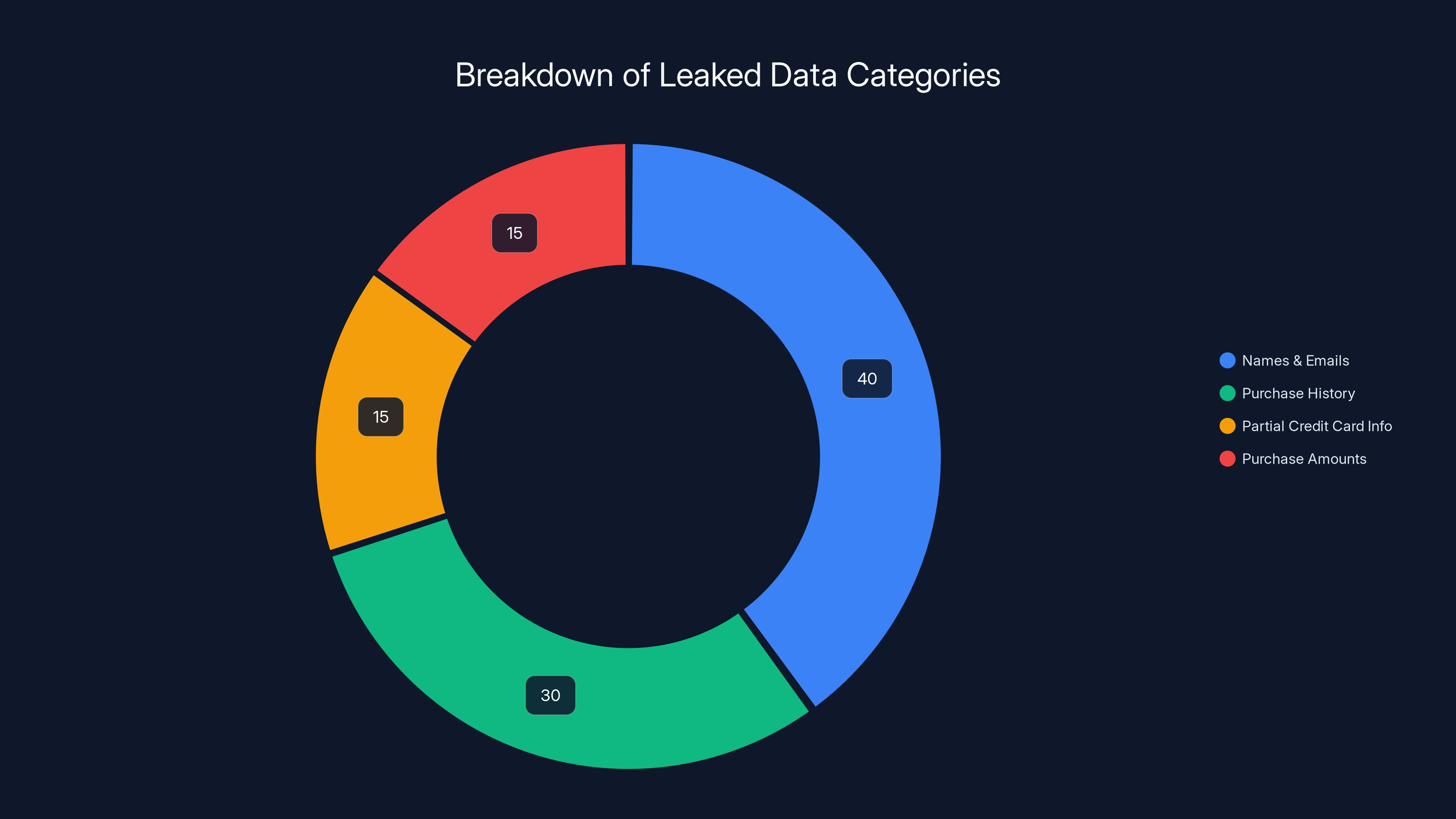
Estimated data distribution shows that names and emails are the most exposed, comprising 40% of the leaked dataset, followed by purchase history at 30%.
Impact on Customers: Risks and Ramifications
The people whose data was exposed face several concrete risks, depending on context.
Identity Theft: With a name and email address, attackers can attempt account takeover at various services. Email is often the recovery method for password resets, making it a valuable asset for attackers.
Targeted Phishing: Attackers now know exactly what you bought. They can craft convincing phishing emails pretending to be from Struktura, a competitor, or someone claiming to be a victim you've been monitored by. "We discovered someone has been monitoring you with u Mobix. Click here to remove the monitoring." This is extremely persuasive to someone who bought that specific product.
Reputation Risk: If your identity is connected to a stalkerware purchase, this creates obvious social and relationship problems. If someone's spouse discovers they bought surveillance software, it destroys trust. If an employer discovers it, it creates liability issues.
Financial Fraud: Even with only partial card information, the exposure is concerning. Someone with your last 4 digits, email, and name can attempt fraud with other financial institutions, especially those with weaker verification.
Insurance and Lending Risk: If your information is used for fraud, even if you dispute it, the fraud attempt appears on your credit report and insurance history. This can affect lending rates and insurance premiums for years.
Data Broker Sales: Breached data invariably gets purchased by data brokers who build comprehensive profiles. Your information might now appear in thousands of people-search databases, background check services, and marketing lists.
For people who purchased these applications for legitimate purposes (parental monitoring of their own minor children, for example), the breach is primarily an identity and fraud risk. For people who purchased them for abuse purposes, the risk is more severe: evidence of their activity is now in the hands of unknown people who might use it to contact their victims or the authorities.

How This Breach Exposes Industry-Wide Problems
This specific breach is just one incident, but it illuminates broader structural problems in the surveillance software industry.
Lack of Regulation: Unlike financial services or healthcare, there's minimal regulatory oversight of consumer spyware. A company can develop and sell applications designed for surveillance with almost no compliance requirements. This means security is never mandated.
Marketing vs. Reality: These companies universally claim their products are for parental monitoring or employee oversight. Industry studies show they're primarily used for abuse. The disconnect between the claimed use case and actual use case means the companies aren't acknowledging their real customer base.
Security Theater: Companies selling invasive surveillance products often practice terrible security themselves. There's a built-in contradiction: if you're building a product that violates privacy, you probably don't care as much about privacy generally. This attitude extends to protecting customer data.
Minimal Accountability: When a data breach happens, most companies issue a statement and move on. Without regulations requiring specific breach notification timeframes, data protection standards, or penalties for negligence, there's little incentive to invest in security.
Business Model Misalignment: The business model of surveillance software companies is fundamentally about making money from invasion of privacy. Companies built on this model aren't naturally incentivized to prioritize security or ethical considerations.
Structura is extreme because the company apparently stored customer payment data in an accessible database without proper access controls. But the industry-wide pattern shows that security isn't a priority for most surveillance software companies.

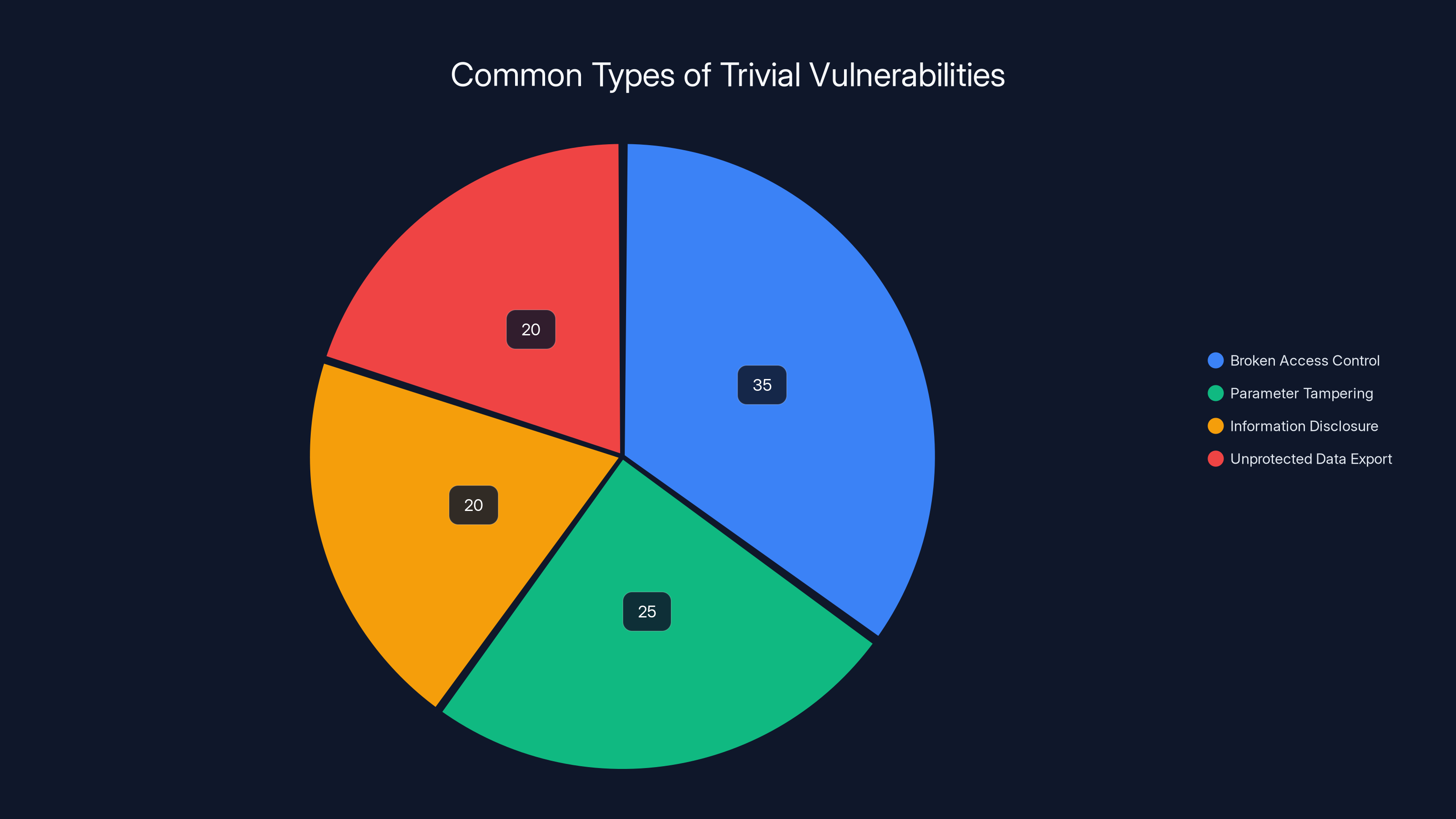
Estimated data shows that broken access control and parameter tampering are the most common trivial vulnerabilities, each accounting for a significant portion of security oversights.
Broader Implications: What This Means for Privacy
This breach exists at the intersection of several major privacy and security issues.
The Surveillance Industry is Growing: The market for consumer surveillance software is estimated in the hundreds of millions of dollars. Thousands of companies operate in this space. Law enforcement uses surveillance software. Abusive partners use it. Employers use it. The market is expanding because demand is strong.
Regulatory Gaps: Several countries (including the EU) have been working on restrictions for stalkerware, but enforcement is inconsistent. The United States has almost no federal restrictions on surveillance software. This means companies can operate in regulatory gray areas.
The Encryption Paradox: Many surveillance software companies oppose strong encryption, arguing that encrypted communications prevent them from monitoring activity. They lobby against end-to-end encryption. Meanwhile, their own customer data sits unencrypted in databases.
Activist vs. Criminal: The distinction between hacktivism and cybercrime becomes murky in cases like this. If a hacker's motivation is righteous, does that make the crime acceptable? Law enforcement would say no. Society increasingly tolerates hacktivism when directed at targets they dislike. This creates incentive for more breaches under the guise of activism.
Customer Vulnerability: People who buy surveillance software represent an easy target for attackers. They're known to be engaged in potentially unethical activity. They're easily embarrassed and unlikely to be sympathetic figures. This makes them perfect victims for extortion or public shaming.
The broader implication is that surveillance software customers—whether guilty of abuse or legitimately monitoring family—are now in a database that hackers have demonstrated how to access. Future attackers might use the same "trivial" vulnerability to extract updated customer lists.

How to Protect Yourself: Practical Security Steps
Whether you're concerned about being a surveillance software customer, or you're worried about being targeted by someone using these applications, there are concrete steps you can take.
Change Your Passwords: If you purchased from Struktura or any surveillance software company, change those passwords immediately. Use a completely different password that you haven't used elsewhere.
Monitor Your Credit: Set up fraud alerts with the three major credit bureaus (Equifax, Experian, Trans Union). Consider credit freezes if you're seriously concerned. These prevent new accounts from being opened in your name.
Check Your Email: If you believe you might be in the leaked database, check your email address on Have I Been Pwned. Sign up for breach notifications so you're alerted if your email appears in future breaches.
Review Financial Statements: Check your credit card and bank statements for unauthorized charges. Fraudsters often test stolen card information with small charges first. Identify these quickly.
Use Unique Email Addresses: For sensitive purchases, use a dedicated email address that you use nowhere else. This compartmentalization limits damage if that email gets breached. Services like Simple Login or Proton Mail's aliases make this easy.
Enable Two-Factor Authentication: On important accounts (email, banking, social media), enable 2FA. This prevents account takeover even if your password is compromised.
Be Wary of Phishing: Someone now has enough information about you to craft convincing phishing emails. Be skeptical of emails claiming to be from any company you've used, especially financial services or email providers.
Protect Yourself from Surveillance: If you're concerned about being monitored, the technical controls are limited once an app is installed. At the user level, security experts recommend using separate devices (a monitored device for known monitoring, a separate device for private activity). At a higher level, leaving situations where you're monitored without consent is the most effective protection.

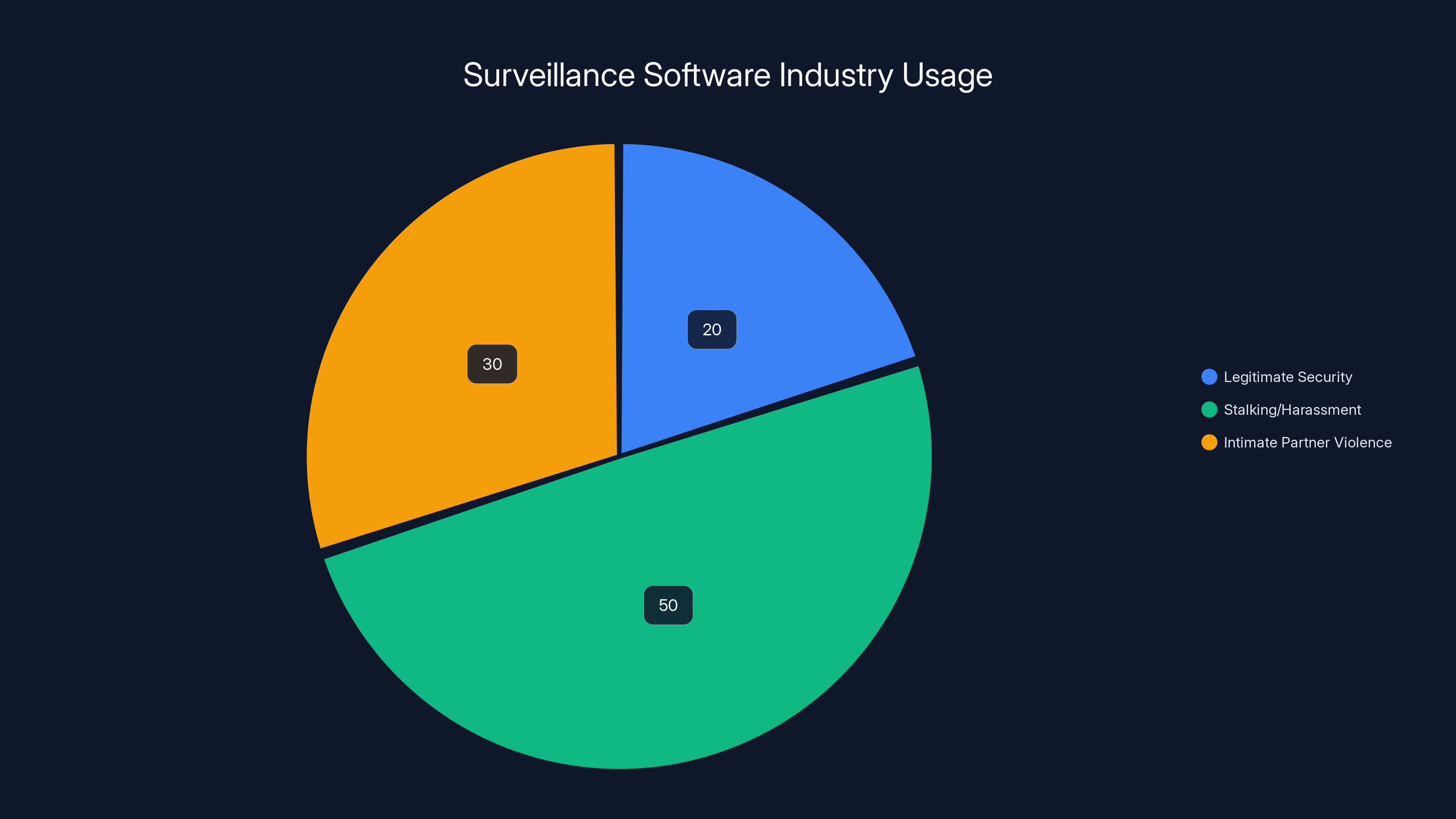
Estimated data shows that a significant portion of surveillance software is used for stalking and harassment, overshadowing legitimate security purposes.
Company Response and Accountability
At the time this breach became public, Struktura issued no official statement. This silence is noteworthy for several reasons.
Delayed Response: Responsible disclosure practices suggest that once a company becomes aware of a breach, they should notify affected customers within a reasonable timeframe. Struktura's apparent silence suggests either they didn't know about the breach for an extended period, or they chose not to disclose it.
Legal Liability: Without an official response, the company avoids confirming details that might be used against them in lawsuits. Silence is a strategy to minimize legal exposure, even if it leaves customers uninformed.
Reputation Management: The company might be consulting with lawyers about damage control. An honest response would probably make the situation worse, so silence is presented as the better option.
Business Continuation: Notably, Struktura continued operating its applications despite the breach. There was no shutdown of services, no security review, no apparent changes to how the company operated.
This response—or lack thereof—reflects how many companies handle breaches. Unless they're forced to disclose by law, they minimize communication. They don't acknowledge negligence. They don't explain how they'll prevent future breaches. They wait for the story to die.
This strategy works because media attention to data breaches is short-lived. After a few weeks, the story disappears from headlines, and most people move on. The company returns to normal operations.
For customers, this means your best source of information is often journalists and security researchers, not the company itself.

The Larger Ecosystem: Other Surveillance Software Companies
While Struktura is the specific target of this breach, it's not an outlier. Hundreds of surveillance software companies operate globally, and many have similar security and operational patterns.
Global Scale: Surveillance software companies operate across multiple countries. Geofinder, u Mobix, and Peekviewer were marketed globally, with customers in dozens of countries. This makes jurisdiction and enforcement complicated.
Interconnected Networks: Many of these companies share common payment processors, hosting providers, or development teams. A vulnerability in one might affect others. Data sold by one company might be purchased by another.
Rebranding and Shell Companies: The same software is often rebranded under different names and operated through different corporate entities. Someone buying "Family Tracker" might be buying the same application as someone buying "Phone Guard," just with a different interface.
Minimal Oversight: Unlike financial services or telecommunications companies, surveillance software companies face minimal regulatory oversight. There's no required security auditing, no licensing, no professional standards.
Growing Market: The market for surveillance software is expanding. Demand comes from employers wanting to monitor remote workers, governments wanting to conduct surveillance, law enforcement wanting investigative tools, and individuals wanting to monitor others. This growth attracts more companies and capital.
The implication is that Struktura's vulnerability is probably not unique. Similar "trivial" vulnerabilities likely exist at other surveillance software companies. Future breaches are probable, not just possible.
Regulatory Response and Future Solutions
Governments and regulators are slowly responding to the surveillance software problem, though progress is incremental.
European Union Approach: The EU has been developing regulations explicitly targeting stalkerware. Some member states have criminalized surveillance software distribution. The GDPR also applies additional compliance requirements that make customer data storage more restrictive.
United States: The U. S. has limited federal restrictions on stalkerware. Some states have introduced legislation (notably New York's STOP Act), but federal oversight is minimal. Congress has discussed surveillance software but taken limited action.
App Store Restrictions: Apple and Google have both attempted to restrict stalkerware from their app stores. However, developers use workarounds, rebranding, and alternative distribution methods.
Law Enforcement: Some law enforcement agencies are beginning to investigate and prosecute stalkerware distribution. The FBI has highlighted stalkerware as a serious problem related to intimate partner violence.
Private Sector: Some payment processors and financial institutions are starting to refuse service to surveillance software companies. This is effective because it makes it harder for these companies to accept customer payments.
The challenge with all these approaches is that surveillance software companies are often small, distributed operations that can easily relocate or rebrand. Enforcement is difficult across international boundaries.
Future solutions likely involve a combination of:
- Stricter criminal penalties for unauthorized surveillance
- Mandatory security standards for software companies storing customer data
- Payment processor and hosting provider restrictions on surveillance software
- International cooperation on law enforcement
- Device-level protections making it harder to install surveillance software without detection

Lessons for Cybersecurity Professionals
This breach offers several important lessons for security practitioners.
Security Through Obscurity Fails: Struktura likely assumed that because they were operating in a morally gray area, they wouldn't be targeted. This is a classic security assumption error. Security professionals should base protections on actual threat models, not assumptions about who will attack.
Basics Matter More Than Complexity: The vulnerability was described as "trivial." This suggests the company failed at basic security: access control, input validation, authentication. Complex security measures matter, but not when the basics are broken.
Risk Multiplies: A surveillance software company handling customer payment data faces multiple risks: hacktivists targeting them for ethical reasons, criminals targeting them for profit, law enforcement investigating them, and victims trying to recover information. The business model creates risk.
Disclosure Timing: Companies that respond quickly to breaches and disclose transparently tend to recover better than companies that stay silent. Transparency costs short-term reputation damage but prevents long-term erosion of trust.
Customer Communication: The lack of official communication from Struktura left a vacuum filled by journalists and the hacktivists themselves. Companies should control this narrative through rapid, honest disclosure.
FAQ
What exactly is stalkerware and how does it work?
Stalkerware, also called spouseware or consumer spyware, is software designed to covertly monitor another person's digital activity. These applications typically track location via GPS, intercept text messages and emails, record phone calls, capture browser history, and monitor social media activity. They're installed on the target device and designed to remain hidden while continuously transmitting data to the person who installed the software. While companies market them as parental monitoring or employee oversight tools, research shows they're predominantly used for intimate partner abuse and non-consensual surveillance.
Who was affected by the Struktura breach?
The breach exposed 536,000 customer records from Struktura, a Ukrainian software company operating surveillance applications including Geofinder, u Mobix, and Peekviewer. Customers spanned multiple countries, representing anyone who had purchased one of these surveillance applications at any point. The leaked data included their names, email addresses, which specific surveillance app they purchased, transaction amounts, and the last four digits of their payment cards. People who purchased for legitimate purposes (like parents monitoring their children) were affected alongside those who purchased for abusive purposes.
What specific information was exposed in the leaked database?
The leaked database contained 536,000 records, each including a customer's full name, email address, the specific surveillance application they purchased, the amount they paid, and the last four digits of their payment card (along with card type: Visa or Mastercard). Notably absent were payment dates and full credit card numbers, which limited some fraud potential. However, the combination of name, email, and partial card information is still valuable for identity theft, phishing, and social engineering attacks.
How was the vulnerability exploited to access the data?
The hacker described the vulnerability as "trivial," suggesting a basic flaw in the website's access controls or authentication system. Common scenarios for such vulnerabilities include broken access control (the site returning customer data to anyone requesting it without verifying authorization), sequential parameter tampering (changing customer IDs in URLs to access other customers' data), or unprotected API endpoints that return sensitive information without proper authentication. The specific technique wasn't publicly detailed, but the fact that it required no sophisticated hacking tools suggests poor fundamental security practices at Struktura.
Who is the hacker and what was their motivation?
The hacker goes by the alias "wikkid" and identified their motivation as targeting applications used to spy on people. Rather than attempting to monetize the data through sale or extortion, the hacker posted it on a public hacking forum, suggesting activism rather than profit motive. Wikkid explicitly stated they wanted to expose a company profiting from invasive surveillance applications. This framing raises ongoing debates about hacktivism, vigilante justice, and whether moral justification legitimizes illegal data breach tactics.
What are the security risks for people whose data was exposed?
Exposed customers face multiple risks including identity theft using their name and email address, targeted phishing emails crafted with knowledge of their specific surveillance app purchase, credit fraud using partial card information, reputation damage if their surveillance purchase becomes known, and data broker sales of their information to people-search databases. Someone whose data is leaked also has evidence of their surveillance activity available to hackers, journalists, or law enforcement—creating legal and social risk depending on how the surveillance was used. The exposure creates years of vulnerability to account takeover, fraudulent account opening, and identity-based attacks.
What should people do if they're concerned about being in the breach?
First, check if your email appears in the leaked database using sites like Have I Been Pwned. Then place fraud alerts with the major credit bureaus (Equifax, Experian, Trans Union) and monitor your credit reports regularly. Change passwords for any accounts you used to purchase surveillance software, and ensure those new passwords are completely unique. Enable two-factor authentication on critical accounts like email and banking. Review financial statements for unauthorized charges. Be wary of phishing emails since attackers now know what you purchased. Consider using a separate email and payment method for sensitive purchases in the future.
Why didn't Struktura disclose the breach publicly?
Struktura issued no official statement about the breach. This silence likely reflects legal strategy to minimize liability, timing to avoid confirming details that could be used in lawsuits, and business continuity concerns (acknowledging the breach might damage the business). The company may not have been aware of the breach initially, or they delayed discovering it was public. Without mandatory disclosure requirements beyond some jurisdictions' laws, companies can often minimize communication about breaches, letting media attention fade and moving on without formal accountability.
Are other surveillance software companies vulnerable to similar attacks?
Likely yes. The surveillance software industry as a whole shows patterns of weak security practices. Many companies in this space are small operations with minimal investment in information security. If Struktura had a "trivial" vulnerability allowing database access, it's probable that similar vulnerabilities exist at other surveillance software companies. The business models are similar, regulatory oversight is minimal, and the industry hasn't prioritized security. Future breaches at other surveillance software companies are probable, particularly if hacktivists view exposing these companies as a priority.

Conclusion: What This Breach Reveals About Trust and Surveillance
The Struktura breach is simultaneously a victory for digital privacy advocates and a cautionary tale about the messiness of vigilante justice. A company built on invading privacy got its own privacy violated. A company that failed to protect customer data demonstrated profound hypocrisy. A hacker exploited basic security oversights and exposed half a million people.
What makes this case particularly significant is what it reveals about the surveillance software industry. These companies universally claim to provide security and monitoring solutions for legitimate purposes. In practice, they're primarily used for abuse. The companies market themselves one way while knowing they're enabling stalking, harassment, and intimate partner violence.
Yet at the same time, those customers—guilty and innocent alike—had their data protected with laughably inadequate security. The irony is almost too perfect: a company whose entire business model is surveillance failed at basic data protection.
The hacker's framing of activism rather than profit is interesting but doesn't resolve the ethical complexity. Yes, the targets were a surveillance software company that enables abuse. But 536,000 people's data was exposed, including some who purchased for legitimate purposes and others whose surveillance purchases might've been coercive (forced by an abuser to prove they had nothing to hide).
Moving forward, the takeaways are multiple:
For individuals: Your data is constantly at risk. Companies you trust with payment information often protect it poorly. Assume everything you purchase online will eventually be breached. Use separate email addresses and payment methods for sensitive purchases. Monitor your credit and accounts actively rather than reactively.
For regulators: The surveillance software industry needs actual oversight. Mandated security standards. Breach notification requirements with meaningful penalties. Restrictions on what surveillance software can do and how it can be marketed. Criminalization of usage without consent. Right now, the industry operates in a gray zone where companies profit from enabling abuse while facing minimal consequences.
For companies: Security theater and silence don't work anymore. When breaches happen, companies that respond quickly and transparently recover better than companies that hide. More importantly, companies should align their actions with their values. If you're genuinely providing parental monitoring tools, operate accordingly. If you know your product is being used for abuse, acknowledge it and stop selling to abusers. Hypocrisy is increasingly exposed.
For hackers and activists: The line between justified targeting and collateral damage is blurry. Exposing abuse is important work. Doing it through methods that also expose innocent people comes with consequences. Legal, ethical, and social consequences. Consider whether your action achieves your stated goals or just creates more victims.
The surveillance industry will continue growing. Demand for monitoring technology is strong. Regulation will continue lagging. More breaches will happen. The question is whether we collectively demand accountability from surveillance companies and hackers alike, or whether we accept that invasion of privacy is just normal now.
What happened to Struktura wasn't unique. It was just visible. Thousands of companies are operating with similar vulnerabilities. Thousands of hacktivists are working against targets they view as immoral. The breach itself is a window into a broader reality: nobody's data is truly safe, and the people operating surveillance systems are often worse at protecting data than the people they're trying to stop.

Key Takeaways
- 536,000 customer records from Struktura, a stalkerware developer, were stolen via a basic website vulnerability
- Exposed data included names, emails, purchase history, and partial credit card information but not payment dates
- The hacker justified the breach as targeting apps used to spy on people, raising complex questions about hacktivism
- Customers face identity theft, phishing, fraud, and reputation risks from the exposed data
- The surveillance software industry operates with minimal security standards and regulatory oversight
- Companies should respond to breaches with transparency rather than silence to maintain customer trust
- Future breaches at other surveillance software companies are probable given similar industry vulnerabilities
Related Articles
- Flickr Data Breach 2025: What Was Stolen & How to Protect Yourself [2025]
- Quishing: The QR Code Phishing Scam Taking Over [2025]
- Europe's Sovereign Cloud Revolution: Investment to Triple by 2027 [2025]
- BridgePay Ransomware Attack: What Happened and How to Protect Your Business [2025]
- Stalkerware Apps Hacked: 27 Data Breaches & Why You Should Never Use Them [2025]
- Proton VPN Windows Split Tunneling + Kill Switch: Complete Guide [2025]
![Stalkerware Data Breach: 500,000 Records Leaked by Hacktivists [2025]](https://tryrunable.com/blog/stalkerware-data-breach-500-000-records-leaked-by-hacktivist/image-1-1770727430201.jpg)



