DDoS Attacks in 2025: How Threats Scale Faster Than Defenses
Distributed denial-of-service attacks used to feel like distant horror stories. You'd see the headline—"Major Bank Hit by Record DDoS"—and think, "Well, that's not happening to us." That comfortable distance evaporated in 2025.
What we've seen over the past year fundamentally reshapes how security teams need to think about infrastructure resilience. The attacks aren't just bigger. They're faster, smarter, and sourced from places traditional defenses were never designed to handle.
This isn't doom-mongering. It's math. And the math is brutal.
TL; DR
- Terabit-scale DDoS is now daily routine: Major telecom providers experience 30+ Tbps attacks regularly, up from rare monthly events in 2024, as noted by Nokia's analysis.
- Attack speed has quadrupled: 78% of attacks complete within 5 minutes, with over a third finishing in under 2 minutes, outpacing human response times, according to recent research.
- Residential proxies became weaponized: An estimated 100-200 million consumer endpoints now serve as latent attack infrastructure, monetized first as legitimate proxies, then as DDoS-for-hire capacity, as reported by Risky Business.
- AI-driven adaptive attacks: Modern campaigns use algorithmic orchestration to cycle through attack vectors and respond to defensive countermeasures in real time, a trend highlighted by Security World.
- Defense requires complete reimagining: Static thresholds, manual runbooks, and centralized scrubbing centers no longer work against distributed, algorithmically-guided threats, as discussed in Nokia's insights.
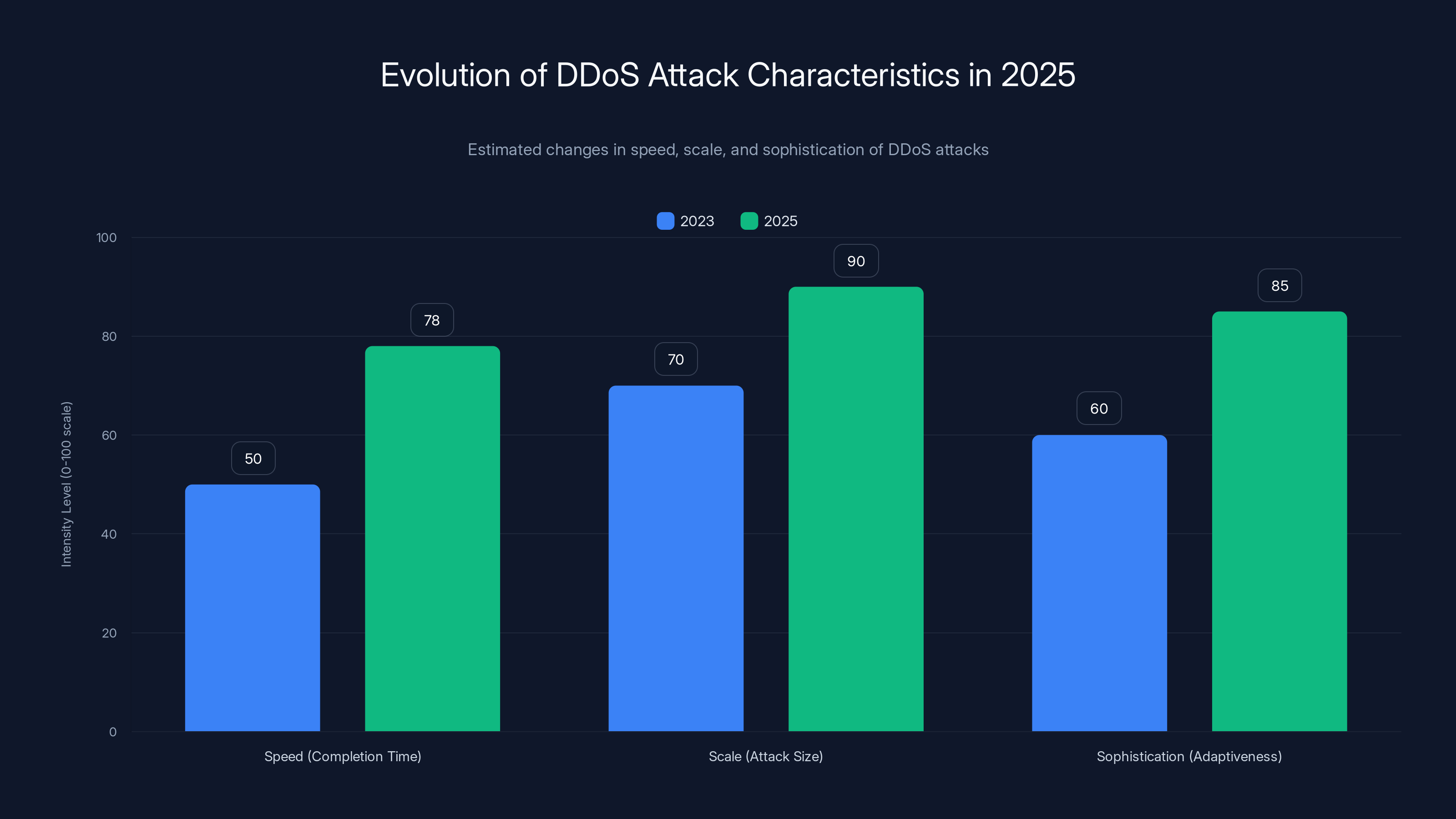
DDoS attacks in 2025 are faster, larger, and more sophisticated compared to 2023, with 78% completing in under 5 minutes and leveraging adaptive algorithms. Estimated data.
What Changed: The 2025 DDoS Landscape
To understand the severity of 2025, you need to know what 2024 looked like. A year ago, terabit-scale attacks were noteworthy anomalies. You'd see them in quarterly threat reports, marked as significant events. Organizations had time to mobilize response teams, activate incident protocols, and gather the internal stakeholders needed to manage the fallout.
That timeline no longer exists.
Today's reality is stark: terabit-level DDoS attacks are a daily occurrence for major telecommunications and cloud infrastructure providers. We're not talking about one every few weeks. We're talking about multiple attacks per day, with some days seeing dozens of distinct incidents.
The first attack exceeding 10 terabits per second arrived in September 2025. By October, incidents tracking past 30 Tbps became routine. The industry consensus has shifted from "if we see a 100 Tbps attack" to "when we see it." Not as fear-mongering. As infrastructure planning, as noted by Nokia.
The scale increase isn't linear. It's exponential, driven by three converging forces: the weaponization of residential proxy networks, AI-driven adaptive attack orchestration, and the raw bandwidth expansion from fiber-to-the-home rollouts in developed markets.
Each of these factors alone would be concerning. Combined, they've created a threat environment that renders yesterday's defensive doctrine obsolete.
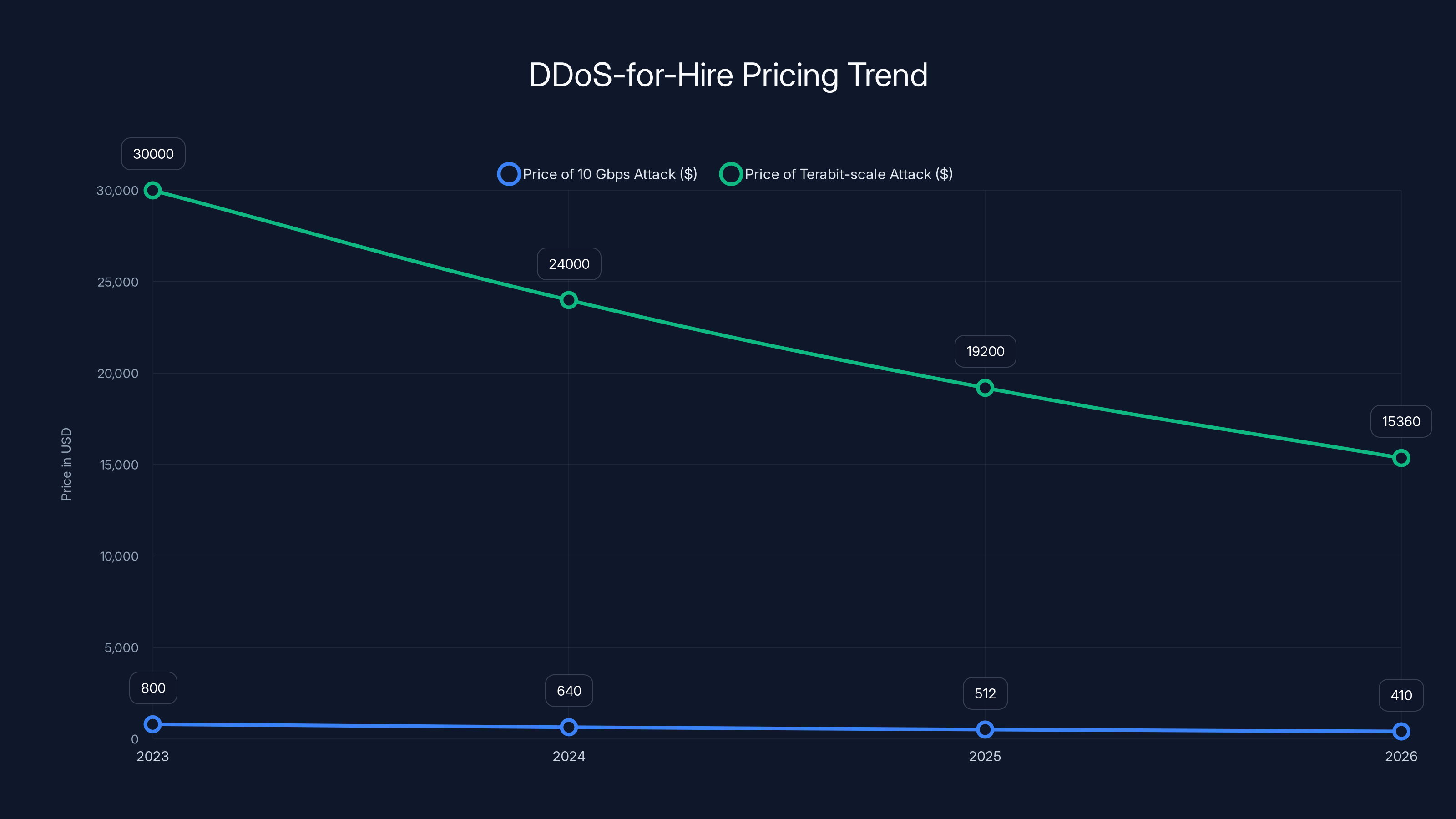
Estimated data shows a 60% price drop for DDoS-for-hire services from 2023 to 2026, making attacks more accessible and frequent.
The Five-Minute Problem: When Speed Becomes Your Vulnerability
Let's talk about timing, because timing is everything in this context.
In 2024, attackers operated with what you might call a "human pace." Campaigns would launch, persist for hours, sometimes days. This gave defenders a critical window: detect the anomaly, alert the team, spin up mitigation, and execute countermeasures. Even a slow team might have 20-30 minutes.
In 2025, that window compressed to seconds.
The data is striking: approximately 78% of DDoS campaigns now conclude within five minutes. More than a third wrap up in under two minutes. Some finish in under 60 seconds, as highlighted by Nature.
This isn't attackers getting lazy or impatient. It's the opposite. Campaigns have become algorithmically orchestrated, cycling through attack vectors faster than any human operations team can even formulate a response.
Consider a typical automated attack sequence:
Minute 0:00-0:45: Opens with TCP carpet bombing, overwhelming connection tables
Minute 0:45-1:15: Detects your mitigation activating, pivots to UDP floods targeting different ports
Minute 1:15-1:50: Launches DNS amplification when it sees UDP filtering engage
Minute 1:50-2:00: Executes high-rate SYN flood, calibrated to your updated thresholds
Each wave is calculated. Each pivot is informed by real-time monitoring of your defensive response. The attack literally watches what you do and counters it, all within a two-minute window.
It's like playing chess against an opponent who moves in microseconds and reads your reactions instantly.
This creates a nearly impossible detection problem. Traditional DDoS defense relies on thresholds: "If traffic exceeds X Gbps, trigger mitigation." But with attacks cycling vectors every 30-45 seconds, threshold-based detection becomes reactive, not proactive.
Your system sees the SYN flood spike, activates SYN cookies. By the time that's working, the attack has already shifted to DNS amplification. You filter DNS traffic. The attack pivots to UDP. Each mitigation you enable is one step behind the attack's next move.
The architectural implication is unavoidable: if your detection and mitigation systems can't respond at the network edge in under 60 seconds, you're not defending. You're documenting. Everything after the first minute is forensic analysis of an attack that's already achieved its objective.
This single factor—attack speed—invalidates an entire class of traditional DDoS defense strategies.
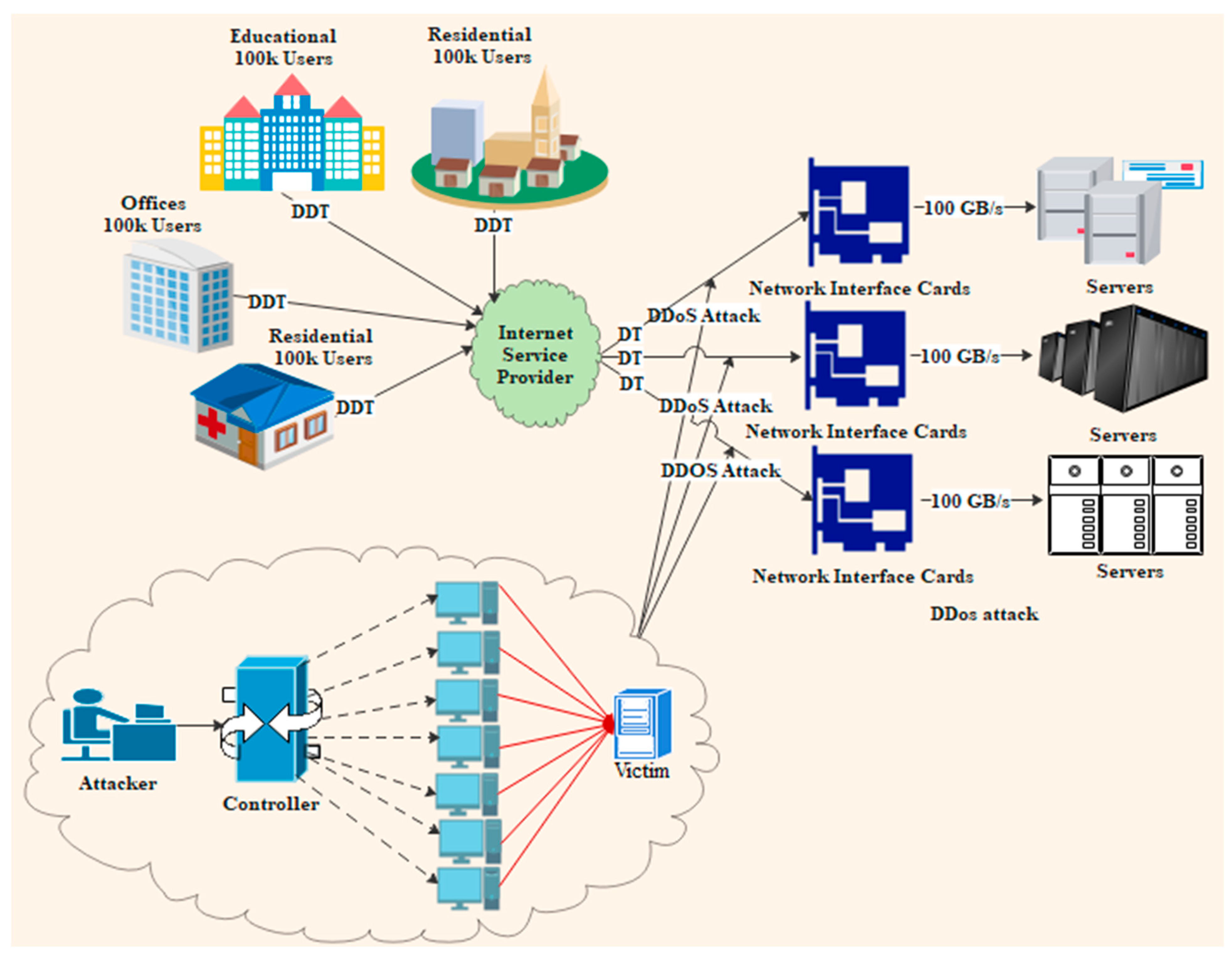
The Proxy Problem: 200 Million Consumer Devices as Attack Infrastructure
Here's where 2025 gets genuinely unsettling. Traditional DDoS botnets had a structural weakness: scale was limited by the number of compromised devices you could actually command.
The largest botnet operations might control a million devices—a significant force, but constrained by the technical challenges of coordinating millions of infected systems. Each device was a discrete unit: someone's router, their security camera, their DVR.
That entire ecosystem is becoming obsolete.
In its place sits something far more dangerous: residential proxy networks have quietly assembled an estimated 100 to 200 million consumer endpoints capable of retransmitting traffic on command. These aren't exposed servers. They're ordinary devices sitting in ordinary homes: cheap Android TV boxes running uncertified firmware, mobile phones with "free" VPN apps, home routers with backdoored versions of open-source software, as described by Infosecurity Magazine.
They're behind NAT. They're invisible to external vulnerability scanning. They look, to the outside world, exactly like a real person browsing the web.
How did this happen? Follow the economics. It's almost elegant in its brutality.
The Gray Market of Residential IP Supply
AI companies—the legitimate ones building large language models—need massive datasets. Training GPT-scale models requires billions of text samples, billions of images, billions of video frames. The most efficient way to gather this data at scale is web scraping, often automated and continuous.
Web scraping at scale creates a detection problem. If you request 10 million pages from a target site using the same IP address, you get blocked. So the industry developed residential proxy services: legitimate services that route your traffic through millions of real consumer devices, making each request appear to come from a different person.
The demand is real. The revenue is substantial. Major ad verification companies, market research firms, and yes, legitimate AI training operations all rely on residential proxies.
This created an enormous business opportunity. Residential proxy services proliferated. Some legitimate, many not. But all of them required one essential resource: millions of consumer devices willing to relay traffic.
How do you assemble 100 million consumer devices? You distribute software that promises something attractive (a VPN service, better streaming, cheaper internet) but actually serves as a proxy relay. The devices get compromised, but the user doesn't notice degradation because they're not the traffic target—they're the relay.
The economics are what criminals call "double monetization." A freshly compromised residential device first serves as a premium proxy exit. A business buying clean IP addresses for legitimate web scraping pays for access to that endpoint. It generates revenue for the network operator.
Once the IP develops a reputation score—after repeated use, it gets flagged as a proxy exit, known to many defense systems—that same device transitions into DDoS-for-hire operations. The endpoint gets monetized again, now as attack infrastructure.
Every single node gets leveraged twice. First as a revenue source from legitimate customers. Second as attack capacity.
The aggregate numbers are staggering. Brazil alone hosts approximately 25 million proxy nodes. The combined upstream bandwidth capacity of these networks exceeds 100 Tbps. To put that in perspective, most national internet backbones (the tier-1 carriers that form the internet's spine) operate at 50-200 Tbps total capacity. A distributed network of compromised consumer devices now rivals the infrastructure footprint of entire countries' internet systems, as reported by Cryptopolitan.
And the math keeps getting worse. Fiber-to-the-home rollouts in North America increased average upstream bandwidth per compromised endpoint by 75% year-over-year. That single metric—more upload capacity per device—directly translates to more attack traffic capacity with no proportional increase in the number of infected devices.
This changes the fundamental calculus of DDoS defense. You can't block these attacks via IP reputation lists. The IPs are legitimate consumer endpoints. You can't assume they're malicious sources—many requests coming from them are genuine. And the sheer number of potential source addresses (200 million) means any rate-limiting strategy that relies on identifying "bad" IPs becomes mathematically infeasible.
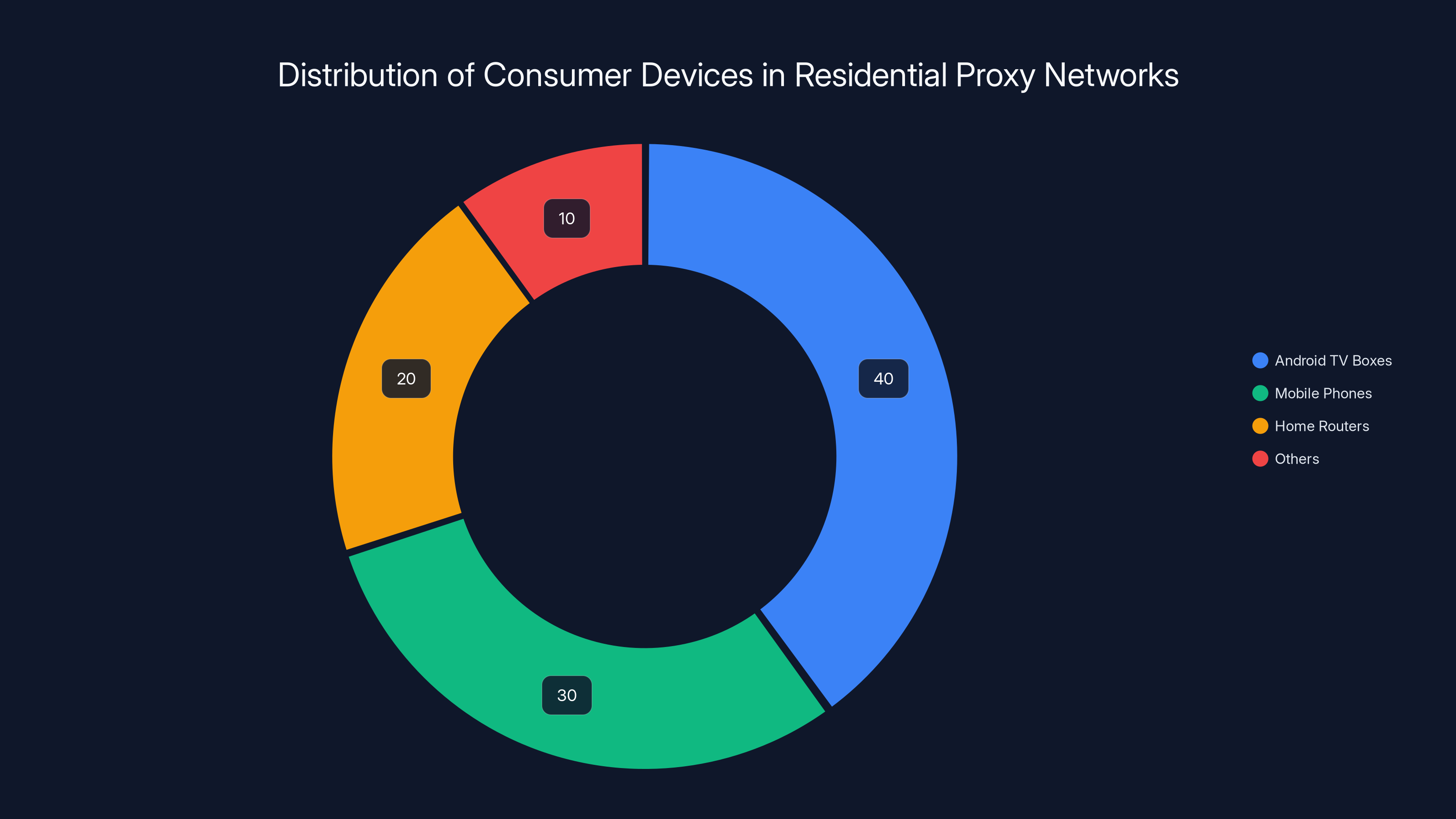
Estimated data shows Android TV boxes and mobile phones dominate the residential proxy networks, making up 70% of the infrastructure.
AI-Driven Adaptive Attacks: When the Attacker Learns as It Attacks
Speed and scale were already dangerous. Add intelligence, and you've created something genuinely novel: attacks that don't follow a predefined script, but instead adapt to your defenses in real time.
This is where we enter territory that traditional DDoS mitigation simply wasn't architected to handle.
Modern DDoS campaigns increasingly incorporate machine learning models that monitor the target's defensive responses and adjust attack parameters accordingly. It's not a human attacker sitting at a keyboard, manually deciding when to switch tactics. It's an algorithm making thousands of microsecond-level decisions.
The attack probes. It measures your response. It calculates the optimal next vector. It executes. It measures again. This cycle repeats dozens of times per minute, as explained by Nokia.
Consider what this means operationally. Your defensive thresholds—"block traffic exceeding 50 Gbps on port 443," for example—are now information the attack uses to optimize its approach. The attack deliberately stays under your thresholds for a period, to understand your actual blocking behavior. Then it calibrates to your revealed response profile.
Earlier in this article, I mentioned attack campaigns cycling through multiple vectors in two minutes. That's not random chaos. That's orchestrated adaptation.
The Mathematics of Algorithmic Attack Orchestration
Think of it like this: in traditional DDoS, the attacker's effectiveness was limited by their knowledge of the target's defenses. They make assumptions about what threshold triggers mitigation, what attack types the target blocks, what response times to expect.
Adaptive attacks eliminate that uncertainty through direct observation. The attack essentially runs a real-time optimization algorithm:
Objective: Maximize impact while evading detection
Variables: Attack vector type, traffic rate, payload characteristics, target range distribution
Feedback: Real-time observation of which traffic gets filtered, which IPs get rate-limited, which ports see responses
Execution: Continuous parameter updates based on feedback
This is optimization under constraint. And modern machine learning is exceptionally good at it.
What makes this particularly difficult to defend against is that it inverts the traditional threat model. You're accustomed to thinking, "I don't know what the attacker will do, so I need defenses that work against anything." Adaptive attacks operate differently: they probe to determine what your defenses actually are, then find the gaps.
They're not attacking your assumed defenses. They're attacking your actual implementation.
The technical literature on this is still sparse—this is genuinely new territory in 2025—but early observations suggest that adaptive DDoS campaigns reduce the effectiveness of traditional mitigation by 30-50%. Not because the traditional techniques are weak, but because the attack learns your specific implementation and routes around it.
Carpet Bombing and Distributed Target Attack Patterns
Traditional DDoS architecture assumed you'd be hit by a concentrated attack aimed at a single target (usually a primary website or critical service). You'd see traffic spike toward one IP, one port, one service, and you'd mobilize defenses against that specific target.
In 2025, that assumption is increasingly wrong.
Over half of documented DDoS campaigns now target multiple hosts simultaneously, spreading attack traffic across entire network ranges rather than focusing on single targets. This is carpet bombing—attackers aren't trying to take down your main website; they're trying to overload your entire network infrastructure, as highlighted by Nokia.
This creates a detection nightmare. Traditional per-host thresholds become meaningless. Your alerting system might be set to trigger if a single host receives more than 100 Gbps of traffic. Distributed carpet bombing sends 10 Gbps to 100 different hosts. Each individual host stays under the alert threshold. But your network is completely saturated.
It's like the difference between one person shouting very loud (concentrated attack) versus 100 people quietly talking in a room designed for 10 people (distributed attack). No individual person exceeds your noise tolerance, but you still can't function.
This technique dilutes detection effectiveness and requires defenders to think differently about thresholds. Instead of watching individual targets, you need to monitor aggregate network segment behavior, looking for patterns of distributed load that aren't explainable by legitimate traffic variations.
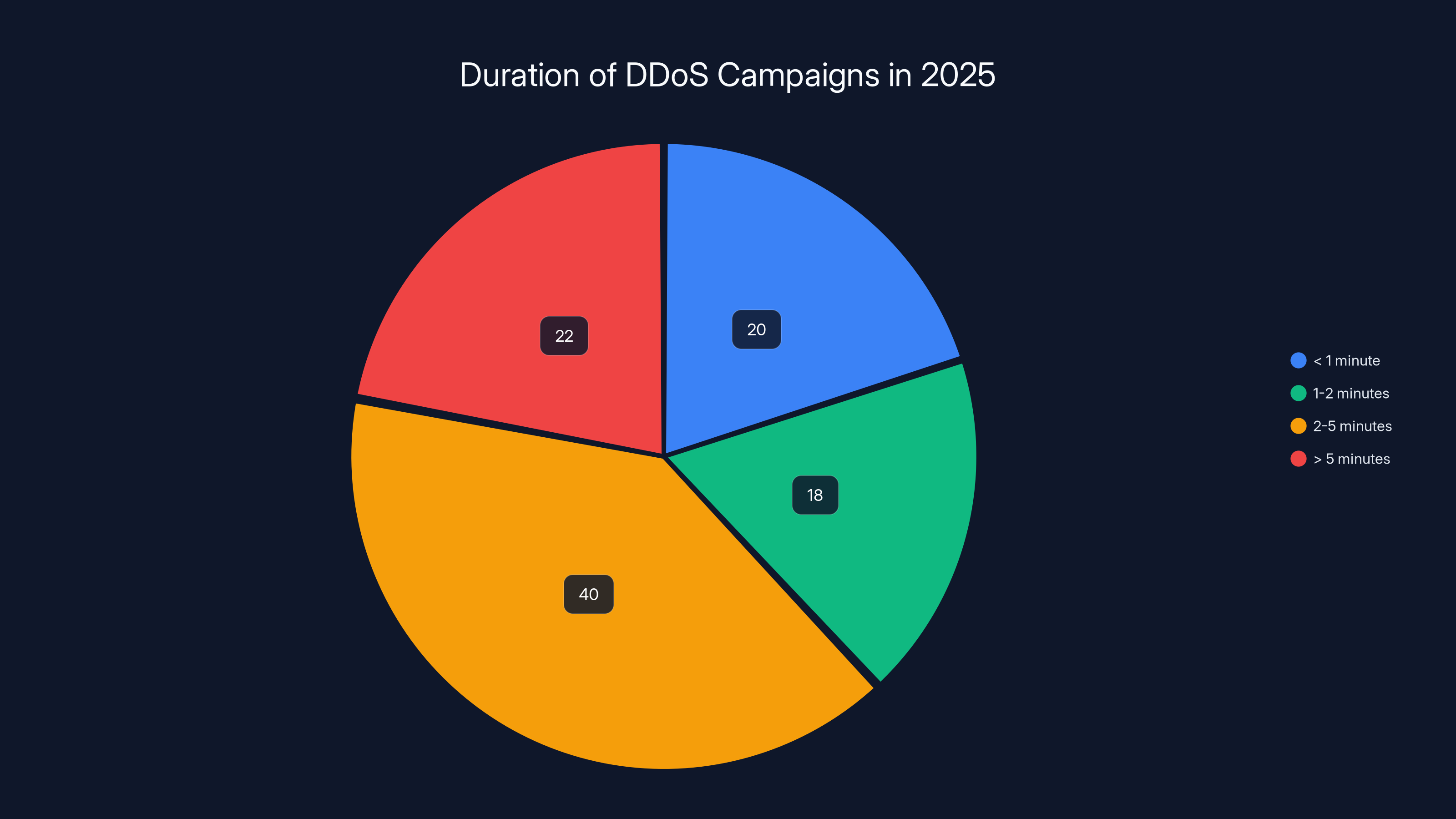
Estimated data shows that 78% of DDoS campaigns conclude within five minutes, with a significant portion ending in under two minutes. This rapid execution poses a challenge for traditional defense mechanisms.
The Architectural Reckoning: What Traditional Defense Can't Do
Let's be direct: infrastructure designed for 2024's threat model doesn't effectively defend against 2025's attacks. This isn't a matter of tuning configurations or purchasing larger pipes. It's a fundamental architectural mismatch.
Yesterday's DDoS defense assumed:
Assumption 1: Humans detect and respond. Alert systems would identify the attack, oncall teams would mobilize, and defenses would activate.
Reality: Attacks complete before humans can acknowledge the alert.
Assumption 2: Centralized scrubbing works. Route traffic through a cleaning center, filter bad traffic, pass good traffic back.
Reality: With 200 million legitimate-looking source IPs participating in distributed attacks, "filter" becomes mathematically impossible. You'd need to examine every packet's behavioral characteristics in real time, which requires processing terabits of data per second.
Assumption 3: Attack signatures are identifiable. SYN floods have certain packet characteristics. DNS amplification looks distinctive. UDP floods are recognizable.
Reality: Adaptive attacks deliberately vary their signatures to avoid pattern matching. The attack knows what your IDS looks for and explicitly doesn't match it.
Assumption 4: Blocking sources is effective. If your attack comes from Brazil, block Brazilian IPs.
Reality: The attack comes from 200 million IPs globally, many of them legitimate consumer ISP addresses. Blocking them blocks real users.
Each of these assumptions was reasonable in 2024. In 2025, they're architectural liabilities.
The uncomfortable reality, which some of the largest infrastructure providers have now publicly acknowledged, is that traditional DDoS defense as an architecture is approaching obsolescence. Not as a complete solution. But as a primary defense.
What Actually Works in 2025: Edge Automation and Behavioral Analytics
If traditional architecture doesn't work, what does?
The organizations successfully defending against 2025's DDoS environment have adopted three core principles: edge-based decision making, continuous algorithmic adaptation, and behavioral traffic analysis.
Edge-Based Decision Making
Defense can't happen in a centralized location anymore. By the time malicious traffic reaches your scrubbing center, it's already consumed network capacity between the attacker and that center. At terabit scales, every millisecond of delay means wasted bandwidth.
Defenders now operate at the network edge—at ISP peering points, at content delivery network boundaries, as close to the source of traffic as possible. Decision-making about what to block happens in microseconds, at distributed points across the network.
This requires pre-positioning defensive infrastructure at geographic and topological distance from centralized data centers. It's expensive. But it's increasingly non-negotiable.
Continuous Algorithmic Adaptation
Static thresholds and fixed rules lose to adaptive attacks. Your defensive parameters need to change continuously, not in response to a detected attack, but proactively, to avoid developing patterns that attackers can learn.
This sounds theoretically abstract. In practice, it means systems that:
- Randomly vary rate-limiting thresholds
- Swap blocking signatures minute-to-minute
- Change traffic analysis parameters based on historical effectiveness
- Deliberately introduce variability in response patterns to prevent learning
Defense becomes unpredictable, not to humans (who are informed of policy changes), but to algorithmic attackers trying to learn your actual implementation.
Behavioral Traffic Analysis
With 200 million legitimate-looking source IPs potentially participating in attacks, you can't distinguish attackers from users via IP reputation alone. You need to identify attack traffic via behavioral characteristics: traffic patterns, payload characteristics, timing distributions.
This is computationally expensive. Analyzing every packet's behavior in real time at terabit scales pushes the limits of current hardware. But it's becoming necessary.
Behavioral analysis can identify attack traffic even when it comes from legitimate consumer ISP addresses, because the pattern of traffic differs from normal user behavior. A residential device under attack control will send traffic in distinctive patterns that differ from a person browsing the web.
This isn't perfect—false positives exist—but it's the most effective technique available for distinguishing attack from legitimate traffic in distributed attack scenarios.
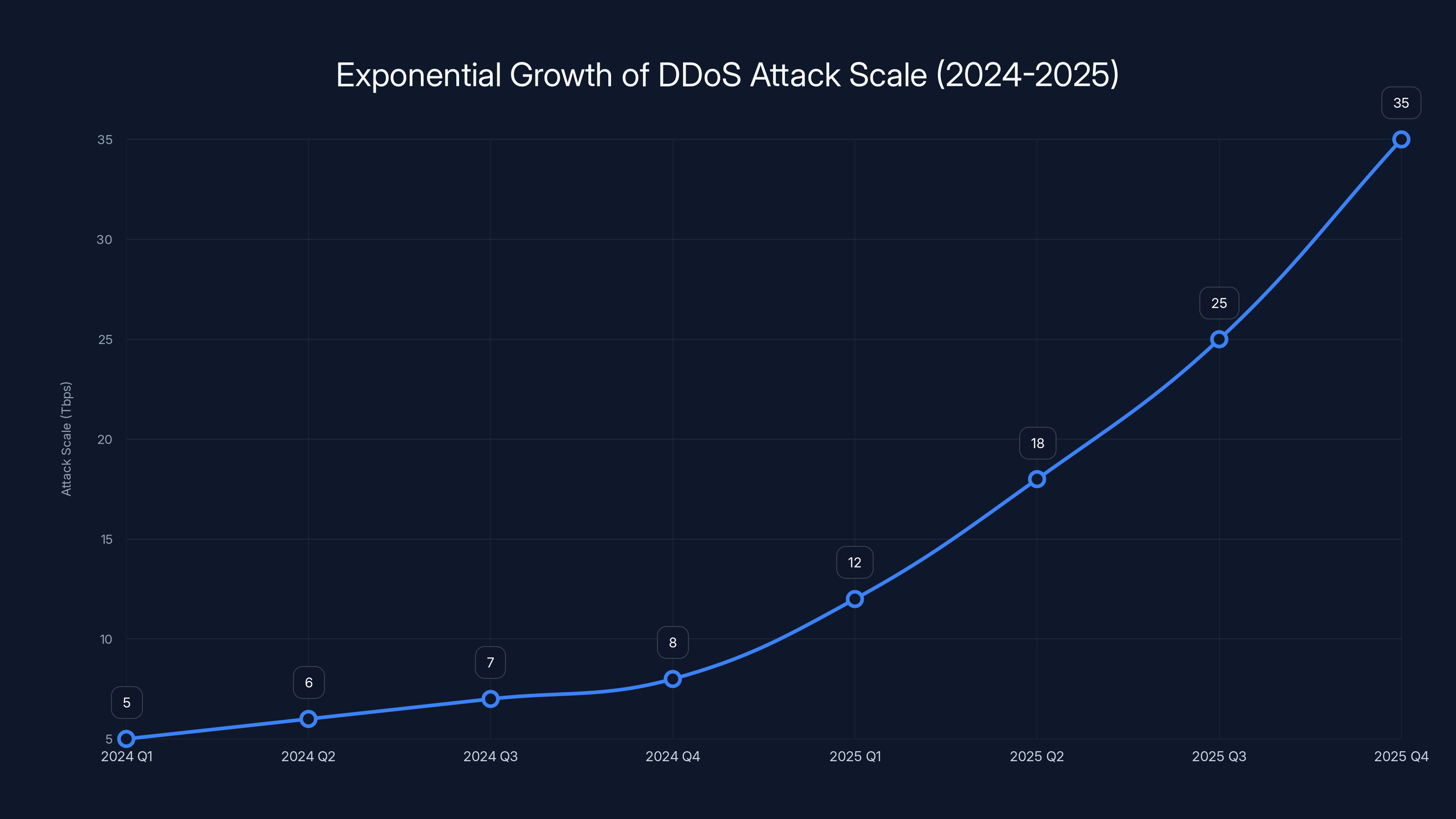
The scale of DDoS attacks has grown exponentially from 2024 to 2025, with incidents surpassing 30 Tbps becoming routine by late 2025. (Estimated data)
The Supply Chain of DDoS-for-Hire: Economics of Attacks as a Service
Why are attacks becoming more sophisticated and more frequent? Follow the money.
DDoS-for-hire services have matured into a robust marketplace. You can purchase DDoS attack capacity like you'd purchase server bandwidth, with tiered pricing based on attack duration, scale, and vector sophistication.
A 10 Gbps attack lasting an hour might cost
This democratizes attacks. You no longer need advanced technical skills to launch a devastating attack. You need a credit card and a DDoS-for-hire provider. The services often operate through cryptocurrency payments to maintain anonymity, further reducing friction.
The supply chain is brutal in its efficiency:
- Malware developers create software that compromises consumer devices
- Distribution networks (often bundled with seemingly legitimate apps) infect hundreds of millions of devices
- Residential proxy networks monetize the bandwidth first via legitimate proxy services
- DDoS-for-hire operations monetize the same infrastructure as attack capacity
- Service becomes accessible to anyone willing to pay
Each participant in this supply chain is economically incentivized to expand capacity. More devices mean more revenue from both legitimate proxy operations and DDoS-for-hire services.
The market is functioning efficiently. The outcomes, from a defensive perspective, are catastrophic.
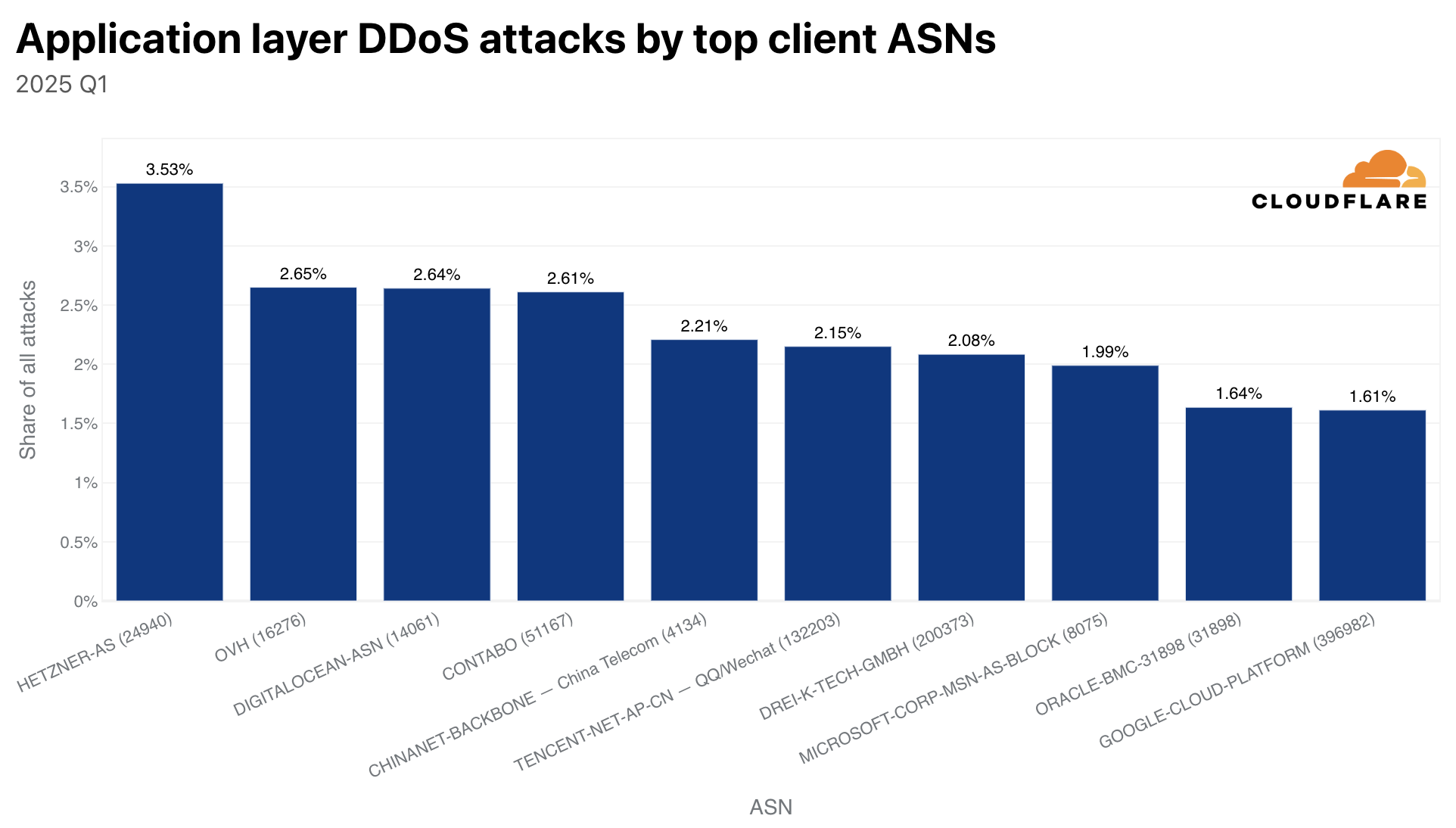
Sectoral Impact: Who's Most Vulnerable in 2025
DDoS doesn't affect all organizations equally. Certain sectors face compounded risk.
Financial Services
Banks and financial platforms are perennial targets. A 2-hour DDoS that prevents trading, prevents transactions, or denies access to customer accounts creates immediate reputational damage and potential financial liability.
Financial services organizations are upgrading defenses rapidly, but they're competing against attackers who can now deploy terabit-scale attacks within minutes.
Telecommunications
Telecom carriers sit at the internet's core. They're the infrastructure. When a telecom faces a terabit-scale attack, the impact isn't limited to that carrier's customers—it can degrade internet performance across entire regions.
Major telecom providers now publish weekly reports of their DDoS experiences, documenting attacks that would have made industry headlines five years ago but now barely merit a footnote.
E-commerce and Digital Retail
Retailers' highest-revenue days (holiday shopping, major sales events) coincide with peaks in overall internet traffic. Adding a terabit-scale DDoS to that legitimate traffic spike creates exponential impact.
A retailer that could weather a DDoS attack for 4 hours when it's a normal traffic day might collapse under combined load on Black Friday.
SaaS and Cloud Providers
Cloud platforms host thousands of customers. A DDoS that affects the platform affects all hosted applications, potentially creating cascading impact across hundreds of independent services.
Gaming
Online gaming communities are frequent DDoS targets, both as deliberate attacks for extortion and as attacks motivated by rivalry or disputes. The attack sophistication hitting gaming platforms now mirrors attacks against financial infrastructure—terabit-scale campaigns that can take down entire gaming networks.
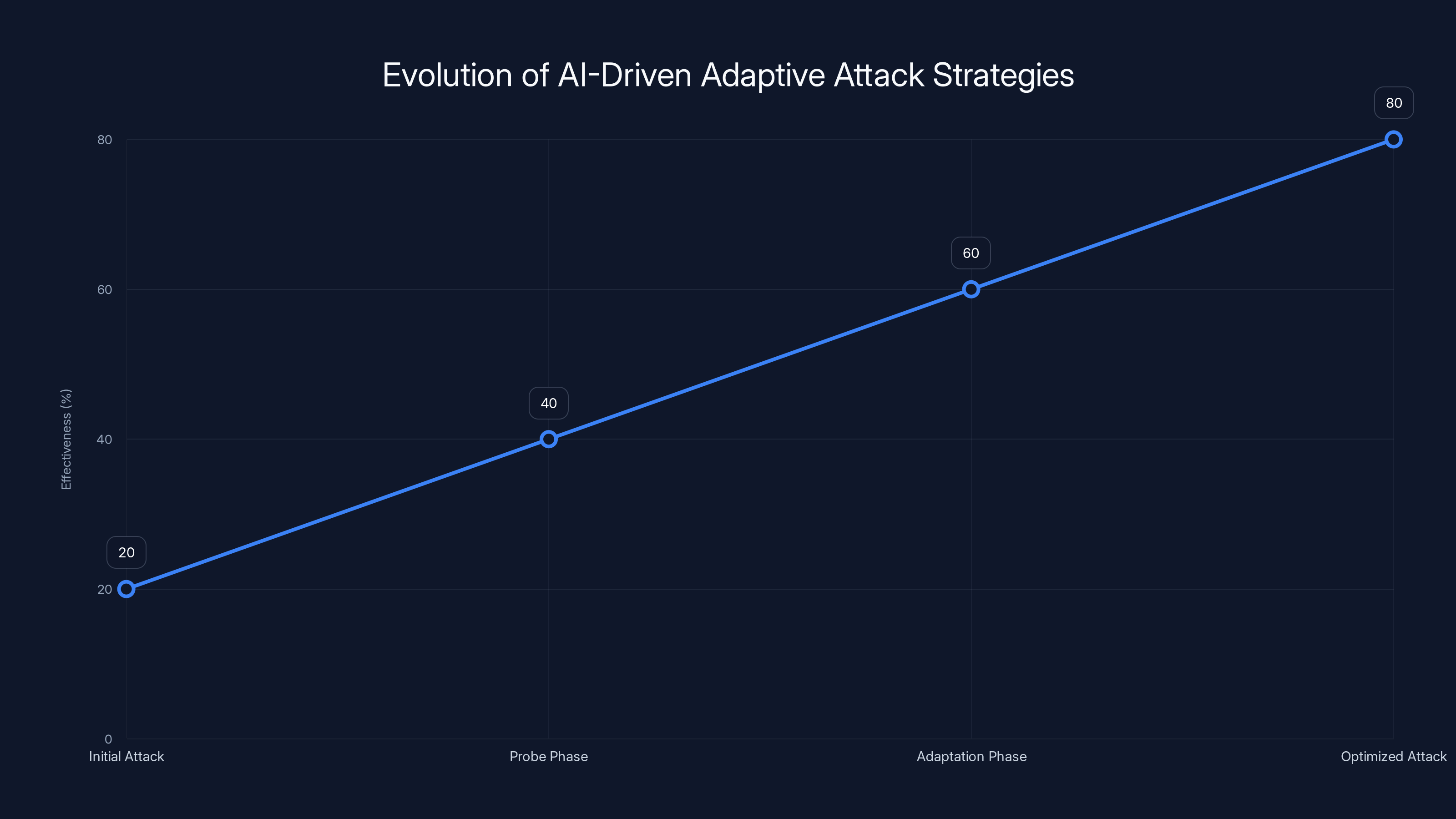
AI-driven adaptive attacks increase in effectiveness as they learn and adapt to defenses in real-time. Estimated data illustrates the progression from initial attack to optimized strategy.
Detection Evolution: Moving Beyond Signatures
Detection has historically relied on signature matching: "This traffic pattern looks like a SYN flood, so it's an attack." With adaptive attacks that deliberately vary signatures to avoid detection, signature-based systems lose effectiveness.
2025 is forcing the security industry toward behavioral detection: identifying attack traffic based on statistical anomalies and pattern deviations, rather than matching known attack signatures.
This is harder. Behavioral detection systems need baseline models of legitimate traffic for your specific environment. They need to detect attacks that might only differ from legitimate traffic by subtle statistical measures. False positives become more likely (legitimate traffic spikes get flagged as attacks).
But it's the direction necessity is forcing.
Organizations with mature behavioral detection systems are reporting:
- Earlier detection of adaptive attacks (30-60 seconds earlier than signature-based systems)
- Better accuracy at distinguishing attack from legitimate traffic in distributed campaign scenarios
- Reduced false positive rates once the behavioral model matures (after 2-4 weeks of learning normal traffic patterns)
The tradeoff is significant: behavioral detection requires more computational resources, more time to train effective models, and higher technical sophistication to implement and tune properly.
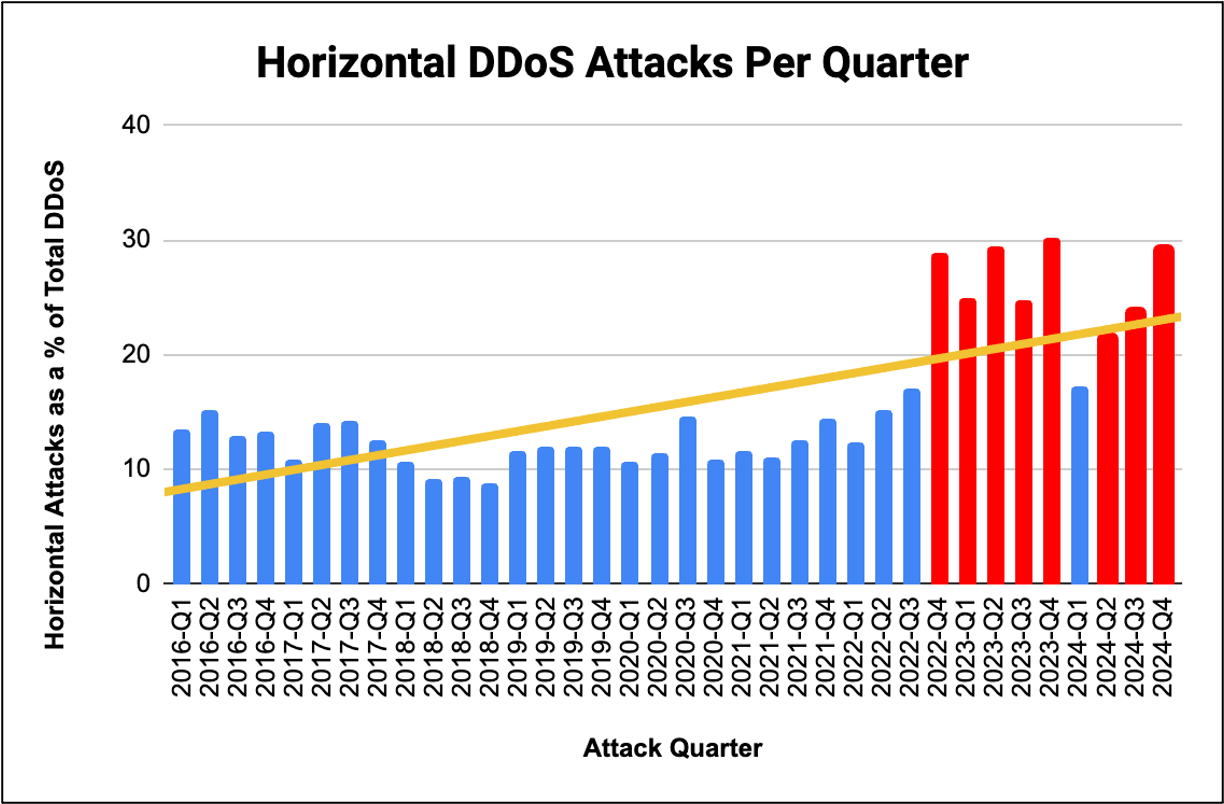
Regulatory Response and Compliance Implications
Governments and regulatory bodies are beginning to react to 2025's DDoS reality.
The EU's NIS2 Directive, which took effect in 2024, now explicitly requires organizations to maintain DDoS defenses appropriate to threat scale. "Appropriate" is being interpreted to mean defenses that can handle terabit-scale attacks—a significant compliance bar that most mid-market organizations have not yet met.
US critical infrastructure regulations are similarly tightening, with CISA (Cybersecurity and Infrastructure Security Agency) publishing updated guidance that assumes adversaries can deploy 30+ Tbps attacks against targets of interest.
For many organizations, compliance with updated regulations now requires infrastructure upgrades that cost hundreds of thousands of dollars or more. This is creating a compliance-driven arms race where organizations must upgrade DDoS defenses not because they necessarily believe they're targeted, but because regulations now require it.
The Economics of Modern Defense: Infrastructure Costs
Let's talk budget. Defending against 2025's DDoS environment is expensive in ways that 2024's environment wasn't.
Traditional DDoS defense (hardware-based mitigation appliances plus centralized scrubbing services) might cost a mid-market organization $50,000-150,000 per year.
Modern defense—edge-based detection and mitigation, behavioral analytics, continuous adaptation—typically costs 3-5x that amount. For large organizations, we're talking $500,000 to several million dollars annually, depending on traffic scale and required capability.
This is creating a divergence: well-funded organizations (enterprise companies, major financial institutions) are deploying capable defenses. Smaller organizations and less-funded government agencies are falling behind, creating vulnerability tiers.
An attacker with terabit-scale capacity can take down a small municipality's public services, a regional bank's online platform, or a mid-market SaaS company's infrastructure. They simply can't yet reliably take down the largest financial institutions or cloud platforms, which have invested heavily in edge-based, behavior-analyzed defenses.
This creates uncomfortable security posture inequality.
Predictions: Where This Heads
Assuming current trends continue (and there's no reason to believe they'll reverse), expect the following in the next 18-24 months:
100 Tbps will become routine. Not exceptional. Not noteworthy. Routine. Major ISPs will publish monthly reports documenting their 100+ Tbps attacks the way they currently report terabit-scale incidents.
Smaller targets will become untenable to defend. Mid-market organizations and local government agencies will face DDoS attacks they simply cannot defend against with available budgets and technical capacity. Some will develop creative defensive approaches (geographic redundancy, deliberate isolation, migration to different networks). Most will accept risk.
AI-powered offense will outpace AI-powered defense. Offensive tools are cheaper and easier to deploy than defensive systems. The equation favors attackers.
Regulatory pressure will increase. Compliance requirements for DDoS defense will become more stringent, creating a compliance-driven upgrade cycle. This will paradoxically put smaller organizations further behind as they struggle to afford increasingly expensive required defenses.
Residential proxy networks will continue consolidating. The 100-200 million currently compromised endpoints will grow. Upstream bandwidth capacity will expand. Attack capacity will scale.
ISP-level defenses will become critical. Individual organizations won't be able to defend against terabit-scale attacks alone. Increasingly, defense will require ISP-level cooperation, with carriers filtering attack traffic at upstream points in the network.
This last point is crucial and often understated: individual organization DDoS defense is approaching its limits. You can't defend against 100 Tbps at your network edge if the ISP is delivering all 100 Tbps to your door. You need your ISP to do some filtering upstream.
This creates dependencies organizations haven't historically had to manage, and it shifts some defensive responsibility to infrastructure providers.
Best Practices for 2025: What Organizations Should Actually Do
Given this landscape, what should an organization actually do?
1. Inventory Your Current Defense
Understand what you actually have. Not what your documentation says you have—what's actually deployed and working. Most organizations discover their DDoS defense is more theoretical than operational when tested at scale.
Test it. If you haven't run a simulated terabit-scale attack against your infrastructure, you don't actually know if your defenses work. Many organizations discover, during testing, that their "protected" infrastructure collapses under attack traffic that's a fraction of what 2025 attackers can deploy.
2. Adopt Edge-Based Detection
Work with your ISP or CDN provider to implement edge-level DDoS detection. This should operate before traffic reaches your network boundary.
This is increasingly non-negotiable. Defending purely at your data center boundary isn't sufficient anymore.
3. Implement Behavioral Analytics
Add systems that can identify attack traffic based on behavioral characteristics, not just signatures or IP reputation.
This is computationally expensive but increasingly necessary for defending against distributed, adaptive attacks.
4. Plan for Graceful Degradation
You might not be able to completely stop a terabit-scale attack. Design your critical services to function in a degraded mode, prioritizing the most essential functionality.
Some organizations are implementing:
- Essential-only service modes that disable non-critical features during attacks
- Geographic failover that shifts traffic to unaffected regions
- Rate limiting for authenticated users to preserve service for actual customers during attacks
- Deliberate IP filtering that blocks entire geographic regions (if business model permits)
5. Build ISP Relationships
Major internet providers (Comcast, Verizon, AS9, etc.) increasingly offer DDoS mitigation at the carrier level. This isn't your ISP's retail DDoS protection service—it's coordinated, carrier-grade defense deployed at upstream points.
These services are expensive but increasingly necessary for organizations handling sensitive traffic or facing determined attackers.
6. Monitor Residential Proxy Network Activity
If you know how to identify traffic originating from residential proxy networks (which have statistical signatures even though individual IPs look legitimate), you can correlate attack traffic back to specific proxy providers.
This doesn't stop attacks but enables you to notify law enforcement and proxy providers of weaponized infrastructure.
7. Maintain Compliance Posture
Regulations are tightening. Document your DDoS defenses and regularly test them against required threat models. Regulatory compliance will become a primary driver of DDoS defense investments.
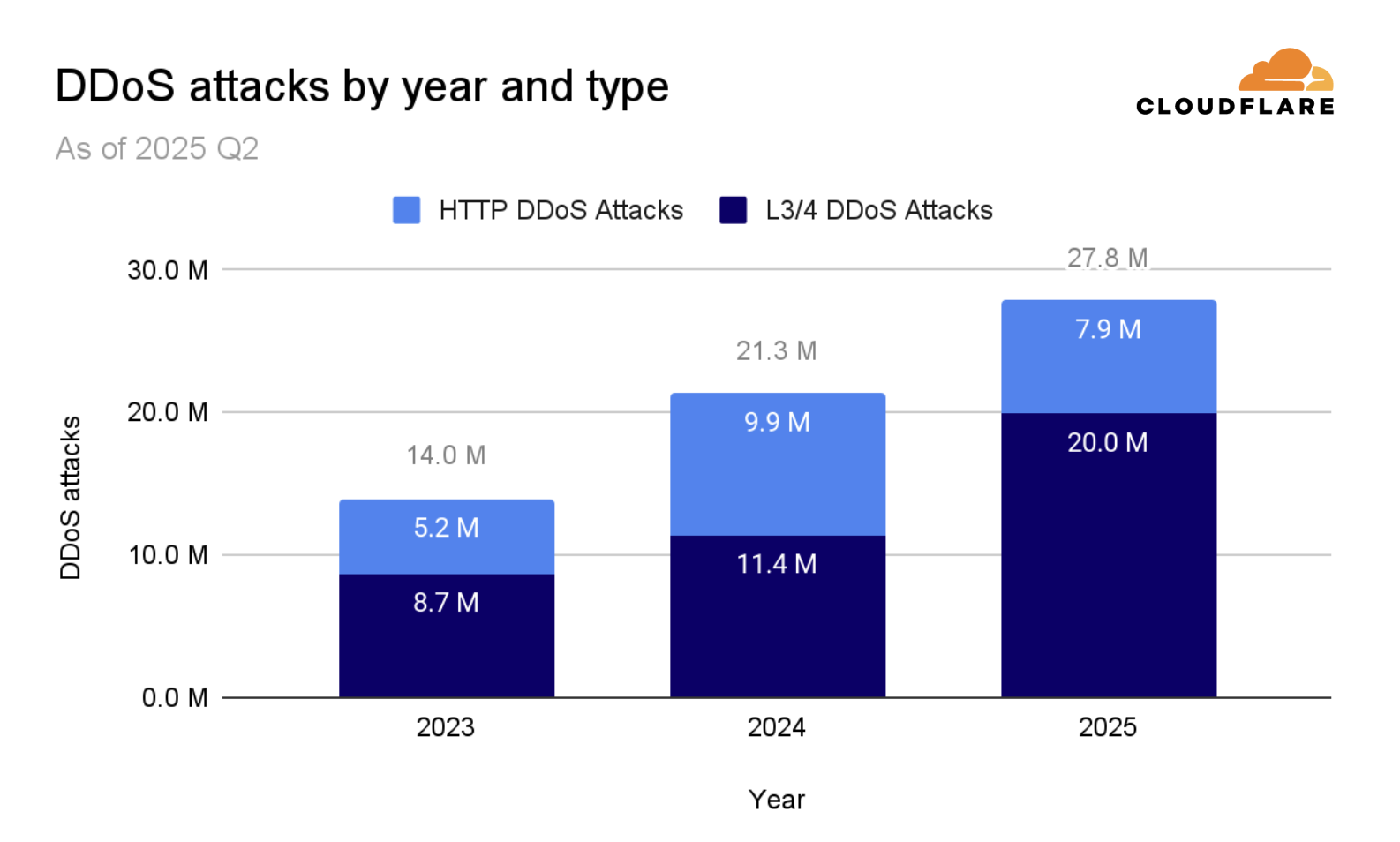
The Organizational and Team Challenge
Beyond technical defenses, there's an organizational challenge that security leaders rarely discuss.
DDoS defense historically was a specialized domain—a team owned DDoS mitigation, deployed scrubbing centers, managed vendor relationships. During attacks, an incident commander activated the DDoS runbook.
This model doesn't work when attacks complete in two minutes.
Defense now requires real-time, algorithmic decision-making. It requires infrastructure distributed across geographic and topological space. It requires coordination with ISPs, CDN providers, and cloud platforms.
It requires, in many cases, complete automation of defensive responses, with humans informed after the fact ("Here's what our system did during the attack") rather than directing response in real time.
This is a cultural shift. Many security organizations have built identity around managing incidents. Shifting to automated defense removes humans from the incident response loop—which is necessary, but often creates organizational resistance.
Leadership that's successfully defending against 2025's DDoS environment has embraced this shift. They've:
- Structured teams around continuous defense rather than incident response
- Invested in automation and algorithmic systems
- Shifted security culture toward "defense should work without human intervention"
- Empowered engineering teams to modify defensive parameters in real-time
This is harder culturally than technically, but it's essential.
The Asymmetry Problem: Why Offense Wins
Here's an uncomfortable truth: in a purely technical sense, modern DDoS attackers have structural advantages that defenders don't.
Offense is algorithmically simple: generate lots of traffic, observe what the target does, adjust traffic characteristics. Offense is inherently adaptive and learning-based.
Defense is architecturally complex: you need to identify attack traffic without false-positives, maintain functionality for legitimate users, and do all this at terabit scales in microseconds.
The problem isn't solvable via technology alone. You can't outrun an algorithm-vs-algorithm competition if offense has lower latency, lower complexity, and fewer constraints.
Defense requires hybrid approaches:
- Deliberate unpredictability (to prevent learning)
- Multiple independent defensive layers (so no single bypass works everywhere)
- Regular defensive parameter rotation (so the attacker can't optimize against a static target)
- Controlled redundancy (so capacity is distributed across geography and topology)
These work, but they're expensive, complex, and require continuous operational management.
The asymmetry will persist. Offense will continue to have structural advantages. The question for each organization is how much defensive investment makes sense given their risk tolerance.
Conclusion: Adaptation as Survival
2025 marks the moment when DDoS scaled past the point where traditional defense architecture could handle it.
This isn't hyperbole. Major infrastructure providers—the companies running the internet's backbone—are openly discussing how their previous defenses are insufficient. When carriers that have invested billions in network infrastructure acknowledge they need to fundamentally rethink defense, you're witnessing a genuine shift.
The organizations that will successfully navigate this environment are those willing to:
- Abandon yesterday's assumptions about defense architecture
- Invest in edge-based, algorithmic, behavioral-analytic defenses
- Accept that perfect defense against terabit-scale attacks may not be possible, and plan accordingly
- Build dependencies on ISP and cloud provider defensive capabilities
- Restructure teams and processes around continuous, automated defense
It's not comfortable. It requires significant investment. It demands acknowledging that your previous defenses are becoming obsolete.
But the alternative—continuing to deploy 2024 solutions against 2025 threats—guarantees failure.
The year ahead will sort organizations into two categories: those that adapted and those that got overwhelmed. Which will you be?
FAQ
What is a distributed denial-of-service (DDoS) attack?
A DDoS attack floods a target with traffic from many sources simultaneously, overwhelming the target's infrastructure and making services unavailable to legitimate users. Traditional DDoS attacks came from compromised computers (botnets); modern attacks leverage residential proxy networks, compromised IoT devices, and algorithmic orchestration to achieve terabit-scale impact. The goal is disruption rather than data theft—denying service is the entire objective.
How have DDoS attacks changed in 2025?
Attacks have accelerated dramatically in three ways: speed (78% now complete in under 5 minutes), scale (terabit-level attacks are daily routine), and sophistication (adaptive algorithms that change tactics in response to defenses). The primary change is sourcing: attacks now leverage 100-200 million residential proxy nodes that look like legitimate user traffic, making them nearly impossible to distinguish from genuine traffic. This fundamentally breaks traditional defense approaches.
Why are residential proxy networks becoming attack infrastructure?
Residential proxy services were created legitimately to provide clean IP addresses for web scraping, ad verification, and market research. These services distribute software that compromises consumer devices, making them relay points for web traffic. Criminals recognized the opportunity: once an IP's reputation degrades from legitimate proxy use, the same endpoint can be weaponized for DDoS-for-hire operations. Each device gets monetized twice, creating economic incentive for rapid expansion of proxy networks to 100+ million devices.
What makes modern DDoS attacks "adaptive"?
Adaptive attacks use machine learning algorithms that monitor your defensive responses in real-time and adjust attack parameters accordingly. Instead of following a predetermined script, the attack watches what you block, measures how quickly you respond, and pivots to a different attack vector before your countermeasures take effect. It's like playing chess against an algorithm that changes strategies every 30 seconds based on your revealed responses. Traditional defenses with static thresholds and fixed rules lose to this approach because the attack learns your actual implementation and routes around it.
Can traditional DDoS defense still work in 2025?
Traditional DDoS defense—centralized scrubbing centers, IP reputation-based filtering, signature detection—is increasingly inadequate for terabit-scale, adaptive attacks from millions of legitimate-looking sources. These approaches can still work as part of a layered strategy, but cannot serve as primary defense anymore. Modern effective defense requires edge-based detection, behavioral analytics that identify attack traffic via patterns rather than signatures, continuous algorithmic adaptation of defensive parameters, and ISP-level cooperation. Organizations relying purely on traditional approaches are vulnerable to attacks that modern providers deploy routinely.
How long does it take to detect and respond to a modern DDoS attack?
Most documented attacks now complete in under 5 minutes, with over a third finishing in under 2 minutes. Human incident response—alerting teams, escalating through management, activating mitigation procedures—typically takes 4-6 minutes minimum. This means by the time humans recognize an attack and begin responding, the attack has already achieved its objective. Effective modern defense requires automated responses at the network edge that activate in seconds, without waiting for human decision-making. This represents a fundamental shift in how defense must be architected.
What's the cost of defending against modern DDoS attacks?
Traditional DDoS defense cost mid-market organizations
What happens if an organization can't afford modern DDoS defenses?
Organizations with limited budgets face difficult choices: accept significant risk from attacks they cannot defend against, implement graceful degradation where critical services continue at reduced capacity during attacks, build geographic redundancy to failover during attacks, or shift to infrastructure providers (cloud platforms, CDNs) that handle DDoS defense at scale. Some organizations are implementing "essential-only" service modes that disable non-critical features during attacks, or are using IP filtering to intentionally block entire geographic regions if their business model permits. None of these are ideal solutions, but represent pragmatic approaches when full defense is financially infeasible.
Will DDoS attacks continue escalating beyond terabits?
Yes. Current projections suggest 100 Tbps attacks will become routine within 18-24 months. The scale will continue growing as long as upstream bandwidth capacity expands (fiber-to-home rollouts are still accelerating) and residential proxy networks continue expanding. The limiting factor isn't technical capability—it's the total global internet capacity. At some point, attacks will approach or exceed regional internet backbone capacity, creating internet-wide impact rather than just targeting specific organizations. This is the point where even the largest organizations cannot defend independently.
Key Takeaways
For security leaders and organizational decision-makers, remember these critical points from 2025's DDoS landscape:
-
Attack speed is now your primary vulnerability. 78% of attacks complete in under 5 minutes. If your team can't respond in seconds, your defenses fail. Automation is mandatory.
-
Source IP reputation is no longer reliable. With 100-200 million legitimate-looking residential proxy addresses participating in attacks, IP-based blocking loses effectiveness. Behavioral analysis is essential.
-
Traditional defense architecture is becoming obsolete. Centralized scrubbing, static thresholds, and signature detection don't work against adaptive, terabit-scale, distributed attacks. Edge-based, algorithmic, behavioral-analytic defense is non-negotiable.
-
Cost of defense is rising dramatically. Budget for 3-5x your previous DDoS defense spending if you want modern capability. This creates inequality where well-funded organizations are defensible and others are not.
-
Regulatory compliance is tightening. NIS2 and CISA guidance now explicitly require defenses capable of handling terabit-scale attacks. Compliance with regulations will drive investment regardless of perceived threat.
-
ISP cooperation is now critical. Individual organization defense is insufficient at terabit scales. You need ISP-level mitigation upstream. Build these relationships now.
-
Defense requires organizational change. Shift from incident response teams to continuous automated defense. This is culturally difficult but technically necessary.
Related Articles
- CrowdStrike SGNL Acquisition: Identity Security for the AI Era [2025]
- Why Cybercriminals Are Getting Younger: The Crisis of 2025 [2025]
- Taiwan's 2.5M Daily Cyberattacks: China's Hybrid War Strategy [2025]
- Digital Rights 2025: Spyware, AI Wars & EU Regulations [2025]
- Cybersecurity Insiders Plead Guilty to ALPHV Ransomware Attacks [2025]
- Government Spyware Targeted You? Complete Action Plan [2025]
![DDoS Attacks in 2025: How Threats Scale Faster Than Defenses [2025]](https://tryrunable.com/blog/ddos-attacks-in-2025-how-threats-scale-faster-than-defenses-/image-1-1768318660332.jpg)



