Zendesk Spam Attack Explained: What's Happening & How to Protect Yourself [2025]
Last month, something strange started happening to email inboxes around the world. People were getting dozens, sometimes hundreds of weird emails from legitimate companies' support systems. The emails had bizarre subject lines, strange content, and absolutely nothing to do with any support tickets these people had actually submitted. No malware. No phishing links. Just... spam flooding inboxes from what looked like real customer service platforms.
This wasn't a typical phishing campaign. It was something weirder, more coordinated, and honestly more frustrating because these emails were coming from legitimate domains that most spam filters trust. The culprit? Zendesk's customer support ticketing system, one of the most widely used support platforms in the world, was being weaponized as a spam delivery mechanism.
Here's what you need to know about this attack, why it's happening, and what you should do about it.
TL; DR
- The Scope: Thousands of email addresses worldwide are receiving spam through legitimate Zendesk support systems, affecting users across the US, UK, Europe, and Asia-Pacific regions.
- The Method: Attackers create fake support tickets using victim email addresses, triggering automated confirmation emails that bypass spam filters because they originate from trusted domains.
- The Impact: While not carrying malware, the volume suggests a possible DoS attack against Zendesk's infrastructure itself, potentially preventing legitimate support tickets from being processed.
- The Response: Zendesk introduced new safety features in January 2025, but the campaign persists, indicating the initial fixes were insufficient.
- Your Protection: Implement email filtering rules, use authentication protocols like SPF/DKIM/DMARC, and monitor your Zendesk account for unauthorized ticket activity.
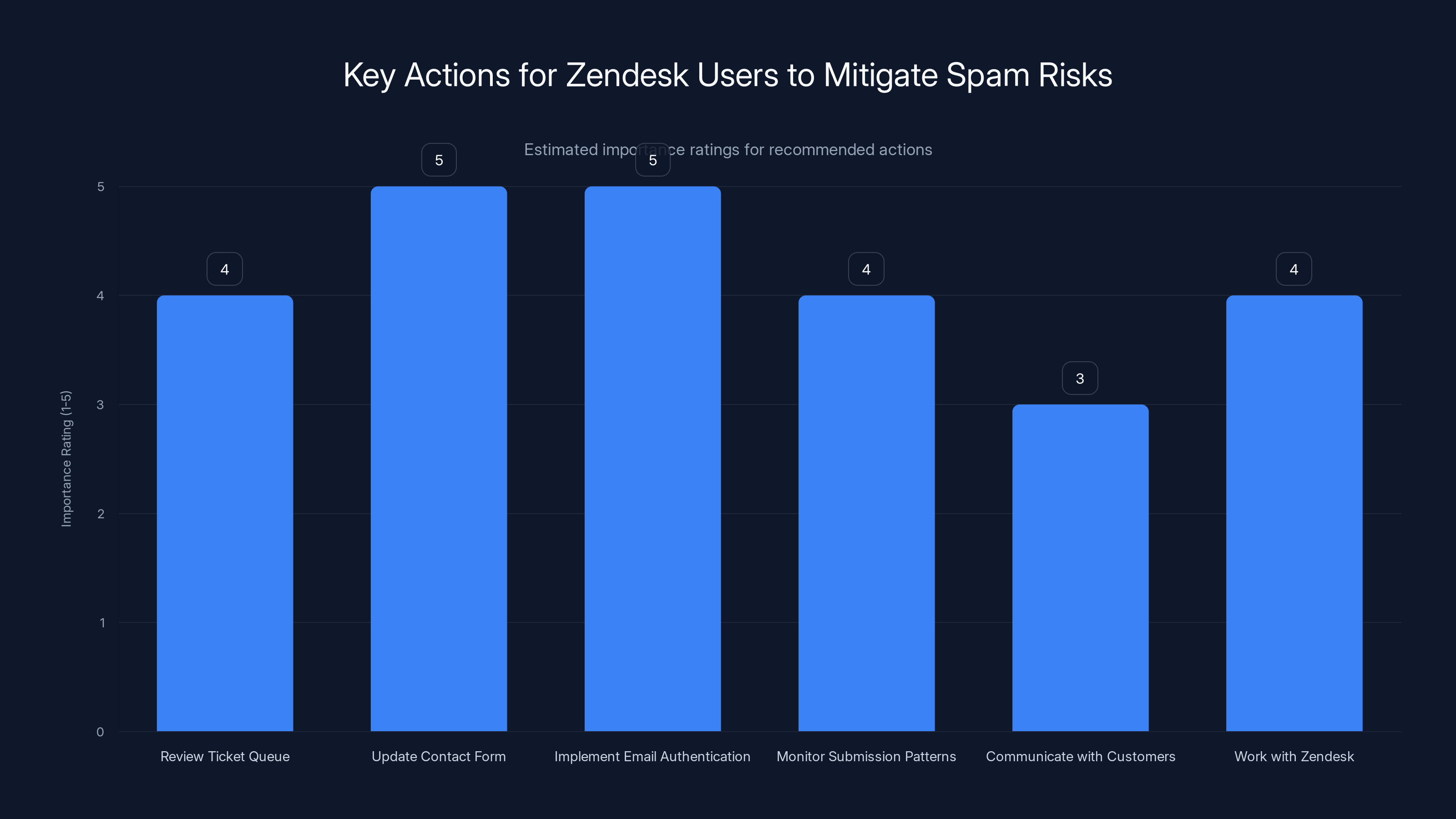
Updating contact forms and implementing strict email authentication are crucial steps for Zendesk users to mitigate spam risks. Estimated data.
What Exactly Is Happening Right Now?
In late January 2025, security researchers started noticing a pattern. Users worldwide were reporting they'd received dozens or even hundreds of automated emails from various companies' Zendesk support systems. The emails weren't personalized. They weren't offering anything. They were just... there. Strange confirmation messages about support tickets the users never created, with subject lines that made no sense.
At first, some people thought it was a coordinated phishing campaign. But there was no phishing link. No "click here to verify your account." No malware attachment. Just spam, pure spam, sent from legitimate corporate email addresses associated with real companies using Zendesk for customer support.
The scale is what makes this unusual. We're talking about thousands of emails hitting individual inboxes. One user on social media described it as a DoS attack against Zendesk support ticketing systems. If attackers can force Zendesk to generate massive volumes of automated emails, the company's email infrastructure gets overwhelmed. Legitimate support tickets? They get lost in the noise. Customer service suffers. The platform becomes unreliable.
This is different from typical spam campaigns that try to compromise users or steal data. This appears to be infrastructure-focused chaos.
What makes this particularly effective is how it bypasses traditional security measures. Because these emails originate from legitimate Zendesk infrastructure used by real companies, they pass through most email authentication checks. SPF records look good. Domain reputation is clean. So these spam emails sail right past Gmail, Outlook, and corporate spam filters and land directly in user inboxes alongside legitimate messages.
The attackers didn't need to compromise Zendesk's servers. They just needed to understand how the platform works: when someone submits a support ticket, an automated confirmation email gets sent to the email address they provided. So the attackers created thousands of fake tickets using email addresses harvested from public sources, data breaches, or just common email patterns.
How Does This Attack Actually Work?
Let's break down the mechanics because understanding the attack is the first step to protecting yourself.
Zendesk, at its core, is a customer service platform. Companies use it to manage support tickets, track customer issues, and communicate with users. One of Zendesk's key features is that it allows anyone to submit a support ticket without first creating an account. This is intentional design—it lowers friction for customers reaching out with problems. Someone has an issue? They email support at your company, and Zendesk creates a ticket and sends back a confirmation.
The confirmation email includes information about the ticket, how to track it, and sometimes links to access the ticket status. Because this email comes from the legitimate company's Zendesk account, it has all the proper authentication tokens. The email looks real because it is real—it's legitimately generated by the platform.
Now, here's where attackers see opportunity. They don't need to compromise anything. They just need to abuse this legitimate feature at scale.
Step one: Get a list of email addresses. This could come from a data breach, public databases, or just common email patterns (firstname.lastname@gmail.com, etc.). We're talking potentially millions of addresses.
Step two: Use automated tools to submit support tickets to various companies' Zendesk instances using those email addresses. Instead of using their own email, the attacker puts the victim's email in the "submitter" field. The subject line and message content? Anything really. Sometimes gibberish. Sometimes just random text. It doesn't matter.
Step three: Zendesk's automated system does what it's designed to do. It creates the ticket and sends a confirmation email to the address specified. From the victim's perspective, they get a legitimate-looking email from a company's support system about a ticket they never created.
Step four: Repeat this millions of times across different Zendesk instances used by thousands of companies.
The result? Widespread email spam that's almost impossible to filter because it's technically legitimate traffic from trusted sources.
Why Zendesk Confirmation Emails Are Perfect For This
From a technical perspective, this is almost elegant in how well-designed the attack is for exploiting this specific feature.
Zendesk confirmation emails are intentionally trustworthy. They need to be. When a customer submits a support ticket, they need to trust that the confirmation email is legitimate so they can track their issue. This means Zendesk puts real effort into making these emails look official, include proper authentication, and pass security checks.
Companies configure their Zendesk instances to send from their own domains (like support@yourcompany.com or noreply@yourcompany.com). The emails include proper SPF records, DKIM signatures, and sometimes even DMARC policies. To spam filters, these emails look perfect.
The attacker isn't spoofing anything. They're not forging emails. They're just exploiting the legitimate feature in a way it wasn't designed for at scale. It's like finding that a bank's drive-through window works perfectly fine when thousands of people use it simultaneously—eventually it breaks.
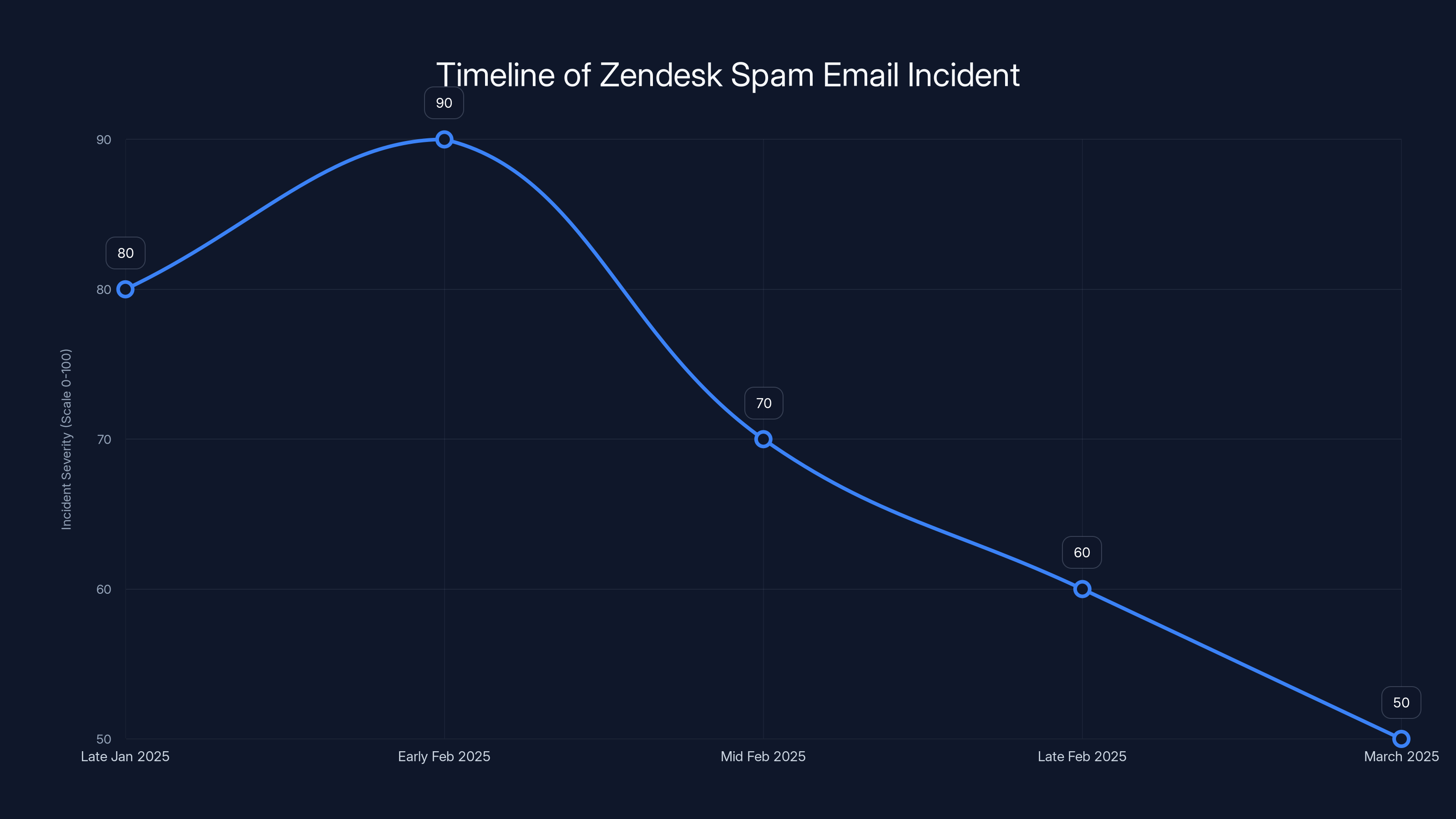
The timeline shows the progression and mitigation efforts of the Zendesk spam email incident from late January to March 2025. Severity decreases as new protections are implemented. Estimated data.
The Evidence Points to a DoS Attack Against Zendesk
Here's the most interesting part of this story: this might not even be about the spam itself. The real attack might be targeting Zendesk's infrastructure.
When security researchers looked at the volume and patterns, several people noted something: if attackers can force Zendesk to send millions of emails, the company's email infrastructure gets overwhelmed. This is called a Denial of Service (DoS) attack, but applied to email rather than web servers.
Imagine Zendesk's email system as a pipeline. It can handle, let's say, 10 million legitimate support confirmations per day. But what if attackers pump in 100 million spam confirmations? The system gets congested. Queues back up. Legitimate support tickets—the real ones that paying customers need—get delayed or lost in the overflow.
This is particularly effective because Zendesk can't just "stop sending emails." These look like legitimate tickets that need legitimate confirmation emails. The company has to distinguish between real customer submissions and attack traffic, and that's not easy when the attack uses real email addresses and legitimate APIs.
One security researcher posted on social media: "Someone is DDoSing Zendesk support ticketing systems and other account creation processes across the internet with my email right now. Anyone know what the attacker is hoping to achieve here?" This captures the confusion perfectly. The attackers aren't trying to compromise individual users. They're trying to break Zendesk itself.
Why would someone do this? There are a few possibilities. First, it could be chaos for its own sake—hacktivism or simple disruption. Second, it could be a smokescreen for other attacks happening simultaneously that are harder to notice when everyone's distracted by spam. Third, it could be an extortion attempt where attackers demand payment to stop. Fourth, it could be a proof-of-concept that Zendesk's infrastructure is vulnerable, which becomes valuable information in the hacking community.
What we know is this: Zendesk's initial response in January 2025 didn't work. The company introduced new safety features including enhanced monitoring and rate limits to detect unusual activity. But the spam campaign continued. This suggests the attackers either found a way around the new protections, or the volume is so distributed across so many different companies' Zendesk instances that the protections can't work at the platform level.
Which Companies Are Affected?
The attack has targeted organizations worldwide, affecting users across multiple regions and industries. Documented cases show impact in the United States, United Kingdom, multiple European countries (Germany, France, Italy, Netherlands, Belgium, Spain), Scandinavian countries (Denmark, Finland, Norway, Sweden), and Asia-Pacific regions (Singapore, Australia, New Zealand).
Because the attack works through legitimate Zendesk instances, basically any company using Zendesk for customer support could be affected. This includes tech companies, SaaS platforms, financial services, e-commerce sites, and support-heavy organizations. Smaller companies are potentially more impacted because they're less likely to have sophisticated email security and DoS mitigation strategies.
What's particularly frustrating for these companies is that they're inadvertently participating in the attack. They're not compromised. Their Zendesk instances aren't hacked. They're just being used as unwitting distribution points for spam. From a reputation perspective, this is damaging—customers receive spam appearing to come from legitimate companies, and trust erodes.
Why Zendesk's First Fix Didn't Work
In early 2025, after the initial spam reports, Zendesk's security team announced they were implementing new protections. According to the company's statement: "We've introduced new safety features to address relay spam, including enhanced monitoring and limits designed to detect unusual activity and stop it more quickly."
This sounds comprehensive. Enhanced monitoring? Limits on unusual activity? In theory, this should catch attackers flooding the system with fake tickets.
But the campaign persisted. Why?
There are several technical reasons why stopping this attack is harder than it sounds. First, the attack is distributed. Instead of targeting one company's Zendesk instance, attackers are spreading the load across thousands of different companies' instances. This makes it harder for Zendesk to detect a pattern because each individual instance might not show dramatic spikes—they just each get a modest increase in ticket volume.
Second, the "fake tickets" being created are technically legitimate API calls. Attackers are using Zendesk's public endpoints exactly as designed. They're not exploiting a vulnerability. They're abusing a feature. It's like how you can call a restaurant repeatedly without ever ordering—technically allowed, but obviously bad behavior when done at scale.
Third, distinguishing between a legitimate increase in support tickets and an attack is genuinely difficult. What if your company launches a viral product and gets thousands of legitimate support requests? Zendesk's rate limits can't distinguish between this and attack traffic. Set the limit too low and you block real customers. Set it too high and you let attacks through.
Fourth, there's the authentication problem. These confirmation emails have to get sent to the addresses specified in the ticket submissions. If Zendesk blocks sending to email addresses that aren't verified as real users of the company's product, it solves the spam problem but breaks the legitimate use case of allowing anyone (including non-registered customers) to submit support tickets.
Zendesk acknowledged this by saying "we are actively taking steps and continuously improving"—which is corporate speak for "our first attempt didn't fully solve it." They likely implemented throttling that slowed attacks but didn't stop them, or implemented per-IP limits that attackers simply worked around by distributing the attack across multiple sources.
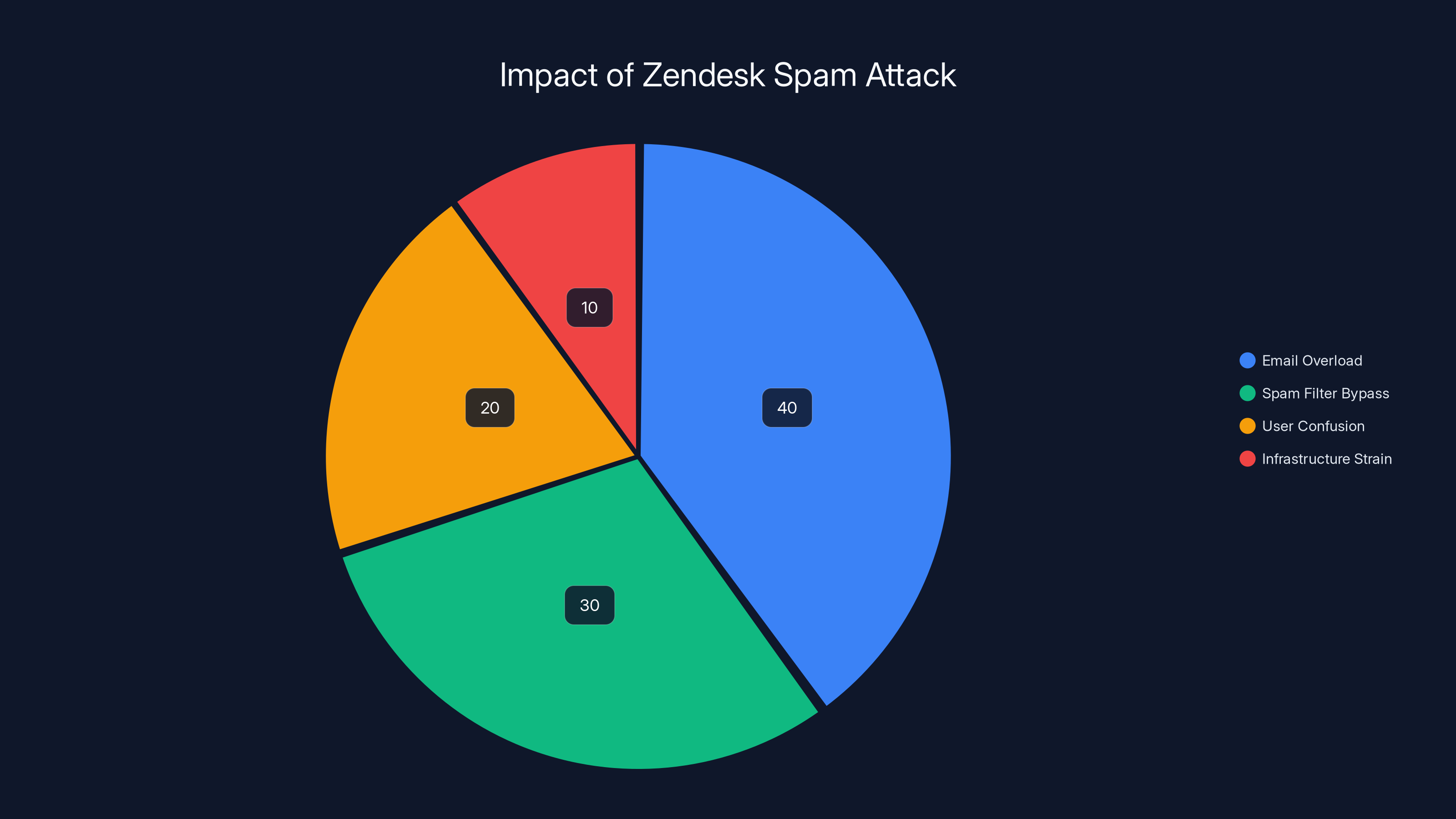
Estimated data shows that the Zendesk spam attack primarily causes email overload and spam filter bypass, with some user confusion and infrastructure strain.
The Broader Security Implications
This attack, while focused on Zendesk, reveals something important about how modern SaaS platforms can be weaponized. Companies rely on these platforms for customer communication. That trust is built into every email filter, every authentication system. When that trust is exploited, even without actual compromise, it can be devastating.
Consider the ripple effects. Companies using Zendesk see their customer support reputation damaged. Users receiving spam from what appear to be legitimate support systems become skeptical of future communications from those companies. Email providers see spam originating from trusted sources and have to adjust filters. The ecosystem gets a little messier.
From an attacker perspective, this is incredibly cost-effective. You need basic scripting skills, a list of email addresses, and patience. No zero-day exploits. No stolen credentials. No sophisticated malware. Just understanding how a common platform works and abusing it at scale.
Zendesk is far from alone in this vulnerability. Any platform that allows unauthenticated submissions of information could potentially be exploited similarly. Contact forms. Survey tools. Ticketing systems. API endpoints that accept user input. If the system automatically sends emails in response to submissions, it becomes a spam delivery mechanism.

How to Spot These Spam Emails
Part of the problem is that these emails look legitimate. They're designed to look legitimate. But there are usually tells if you know what to look for.
Check the sender address carefully. The email comes from a support address for a company you don't use. Look at the domain. Is it noreply@companyname.com? That's usually legitimate for a company that actually sent you support email. But if you've never heard of the company, that's suspicious.
Look for generic content. Real support confirmation emails usually reference something specific—the product you contacted support about, a ticket number, sometimes even details of your submission. These spam emails are often completely generic. The subject line might be random characters. The body might be a copy-paste template that makes no sense in context.
Check for grammatical errors or weird formatting. Legitimate companies usually have someone review support emails before they go out. Spam emails often have formatting issues, strange line breaks, or odd punctuation that suggests they were auto-generated or cobbled together.
Verify the ticket number. Many of these emails include ticket numbers. If you're suspicious, you can often go to the company's support portal and check if a ticket with that number actually exists. Spoiler: it won't.
Watch for the pattern. If you're getting ten of these in a single day from different companies, you're definitely being targeted by the spam campaign, not receiving legitimate support emails.
What Can Individual Users Do?
You might be thinking: "I can't control what attacks happen. What can I actually do about this?" Fair point. Here are practical steps:
First, implement email filtering. Most email providers (Gmail, Outlook, Proton Mail) allow you to create rules based on sender address, subject line, or content. Set up a filter that catches Zendesk confirmation emails from companies you don't recognize and either deletes them or moves them to a folder. Be careful not to filter out legitimate support emails from companies you actually use.
Second, use separate email addresses strategically. Consider using a dedicated email address for support tickets. This keeps your primary email address from being exposed to as much spam. If a company needs customer support, you can provide this secondary address. Real support communications are less likely to go to your main inbox and get lost in spam.
Third, monitor your email address in data breach sites. Services like Have I Been Pwned let you check if your email was in a known data breach. If it was, your address is on attackers' lists. This is common knowledge among security researchers, but many users don't know to check. Knowing your email's exposure level helps you understand the spam risk.
Fourth, be skeptical of unsolicited support emails. This is psychology more than technology. If you get a support email you didn't request, your instinct should be to verify it independently. Go directly to the company's website. Log into your account. Don't click links in unsolicited emails. This is good practice generally, and it helps during campaigns like this.
Fifth, report the spam. Email providers use abuse reports to train their filters. If you see obvious spam originating from Zendesk infrastructure, report it. As more users report it, email providers can improve detection.
Sixth, consider email authentication tools. If you have a personal domain you use for email, implement SPF, DKIM, and DMARC records. This helps email providers verify that messages claiming to be from your domain are actually from you. While this doesn't stop the Zendesk spam campaign directly, it makes it easier for others to trust emails you actually send and reduces confusion.
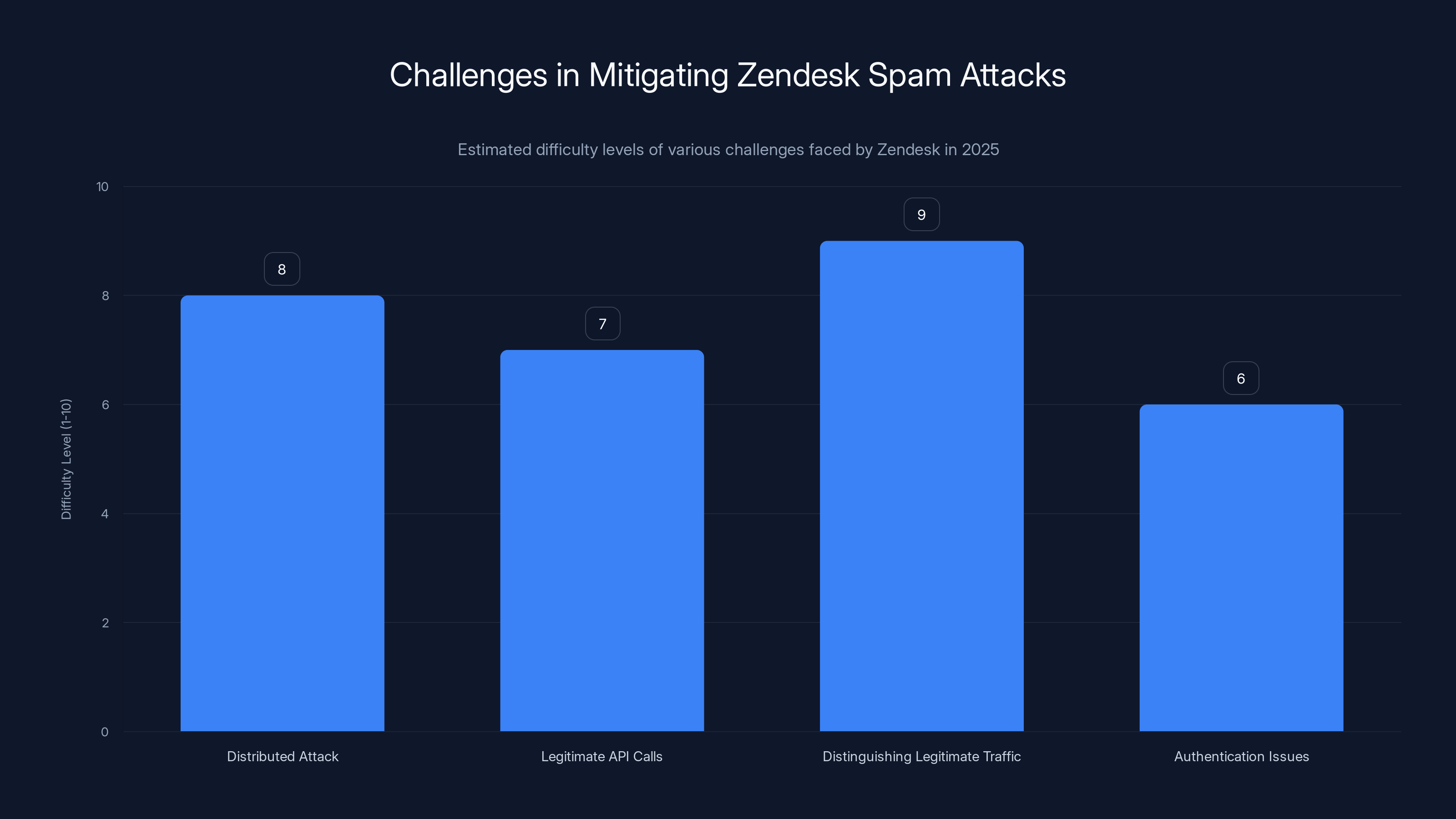
The most challenging aspect for Zendesk in addressing spam attacks was distinguishing legitimate traffic from attack traffic, rated at a difficulty level of 9. (Estimated data)
What Should Companies Using Zendesk Do?
If your organization uses Zendesk, this is more serious for you than for individual users. Your company's reputation is on the line if your support email is being used to send spam.
Review your ticket queue. Check Zendesk for tickets created around late January 2025 that look suspicious. Specifically look for tickets with random subject lines, gibberish content, or patterns suggesting automated submission. Document these. They prove your system was targeted, which is helpful if customers report spam and you need to explain what happened.
Update your contact form. If you use Zendesk forms or have public submission endpoints, add CAPTCHA challenges. This dramatically increases the cost for automated attacks because now they need to solve challenges at scale. It's not impossible, but it makes the attack much harder.
Implement email authentication strictly. Work with your email and Zendesk teams to ensure SPF, DKIM, and DMARC are properly configured. Have a DMARC policy set to reject unauthenticated mail in your domain's name. This makes it harder for attackers to spoof your address, though it doesn't prevent Zendesk from legitimately sending on your behalf.
Monitor submission patterns. Set up alerts in Zendesk (or your monitoring system) for unusual spike in ticket volume, especially from new email addresses. If you normally get 100 tickets per day and suddenly get 10,000, something is wrong.
Communicate with customers. If customers report your support system is sending spam, acknowledge it publicly if appropriate. "We're aware that Zendesk-based support systems are being targeted by a spam campaign. These emails are legitimate Zendesk confirmations for submissions, not phishing. Here's how to verify if something is real." Transparency is trust.
Work with Zendesk on the issue. If the campaign is still active by the time you read this, escalate to Zendesk's security team. Provide specific examples. Details about volume, timing, patterns. The more feedback they get, the more they can improve protections.
Consider rate limiting. Talk to Zendesk about ticket submission rate limits for your instance. If you normally get X tickets per hour, set a limit to reject submissions significantly above that rate. This won't stop all attack traffic but will prevent the worst-case scenario where your system is completely overwhelmed.
How Zendesk Should Respond (Going Forward)
Zendesk's security team is clearly aware of the issue and has already begun implementing fixes. But the initial response—rate limiting and monitoring—wasn't sufficient. Here's what should probably come next:
Email verification requirements. Zendesk could require that an email address is verified before a confirmation email is sent. Instead of immediately confirming a ticket to an unverified address, the system could first send a verification email asking the person to confirm they actually submitted this ticket. This adds friction but defeats the spam campaign's primary mechanism.
Progressive enforcement. If an IP address or account is submitting thousands of tickets within a time window that exceeds normal business patterns, escalate the requirements. Maybe require CAPTCHA. Maybe require email verification. The system learns and adapts.
Better analytics for customers. Companies using Zendesk need visibility into whether they're being targeted. Zendesk could surface this in the admin dashboard: "Unusual submission volume detected. X% above normal baseline. This may indicate an attack." This helps customers understand what's happening and respond appropriately.
API changes for future versions. In the next major version of Zendesk, the platform could require additional parameters or authentication for ticket submission. Make it slightly more complex to programmatically create tickets, and suddenly the attack becomes harder.
Cross-customer intelligence sharing. Zendesk sees all the attack traffic across all its customers. They could analyze patterns across the platform and identify attack sources more effectively than any individual customer could. This data could be shared (anonymously) to help industry-wide defenses.
The reality is that Zendesk is in a tough position. They need to maintain the openness that makes their platform valuable—allowing anyone to submit support tickets without friction. But they also need to prevent abuse. This balance is genuinely hard.
Why This Attack Matters Beyond Zendesk
Zendesk spam is the symptom. The disease is a broader problem in how cloud platforms are architected.
Most SaaS platforms inherit a fundamental assumption: the people using the platform are not adversaries. The person submitting a support ticket is a real person with a real problem. The person signing up for an account is a genuine user. These platforms are designed for openness, for low friction, for trust.
But at scale, some of those users aren't users at all. They're attackers, or bots, or malicious automation. And the more powerful and widely-used the platform, the more attractive a target it becomes.
This attack shows how a widely-trusted platform can be weaponized. Zendesk's email infrastructure is trusted. Companies trust it. Email providers trust it. So when spam originates from Zendesk, it goes everywhere. The spam doesn't need to be sophisticated or convincing. It just needs to be voluminous. The platform does the distribution.
Other platforms should pay attention. Any service that allows unauthenticated submissions and sends automated responses is potentially vulnerable to the same attack. Survey tools. Form builders. Webhook services. CMS platforms with comment systems. Anywhere trust is extended to unauthenticated input could become a spam delivery mechanism.
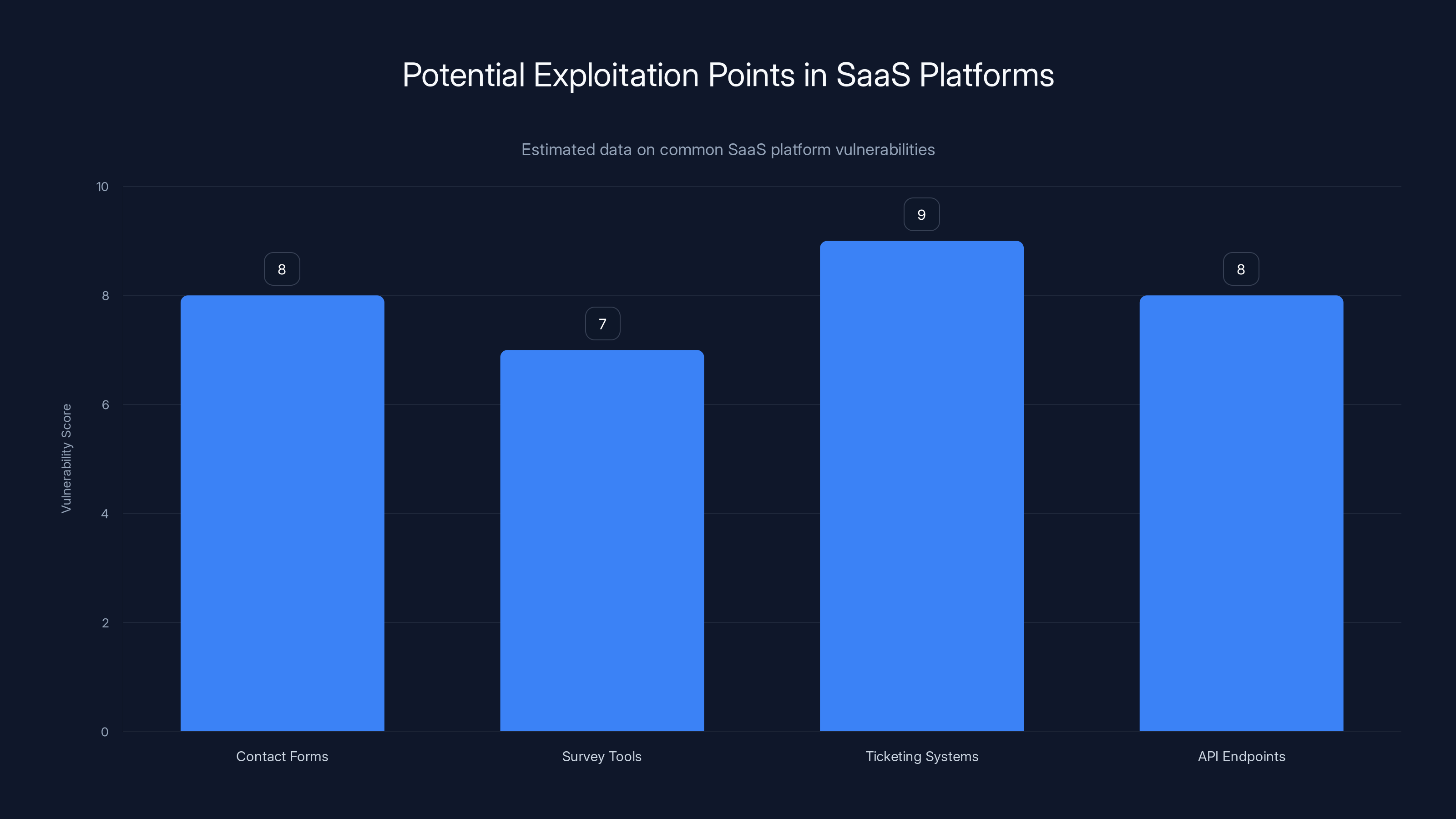
Estimated data suggests that ticketing systems and API endpoints are most vulnerable to exploitation due to their automated response capabilities.
The Longer View: Email Trust and Future Attacks
This attack touches on something fundamental about email security that hasn't been solved: how do you know an email is legitimate?
Traditional spam filtering looks at sender reputation, content analysis, and pattern matching. But this attack gets through those filters because it uses legitimate infrastructure. The sender domain is real. The origin IP is legitimate. The content doesn't contain typical spam markers.
Modern email authentication (SPF, DKIM, DMARC) helps prove that an email came from where it claims to come from. But these are optional. Many organizations don't implement them fully. And even when they do, they don't solve the fundamental problem: legitimate infrastructure being abused for illegitimate purposes.
The industry is slowly moving toward better solutions. BIMI (Brand Indicators for Message Identification) shows company logos in supported email clients, giving users another way to verify legitimacy. Machine learning filters are getting better at detecting spam that doesn't look like traditional spam. Rate limiting and behavioral analysis can catch attacks based on patterns rather than content.
But these are incremental improvements. The fundamental architecture of email—a decentralized system where anyone can send to anyone—makes it vulnerable to abuse. This attack is just one manifestation of a larger problem.
For Zendesk specifically, this incident reveals that even well-designed platforms with good security practices can be exploited when attackers think creatively. The fix isn't just technical. It's also about understanding your users, anticipating abuse patterns, and building resilience into your infrastructure.
Lessons for Platform Builders
If you're building a SaaS platform that accepts user submissions and sends automated responses, this attack offers several lessons:
One: Assume your platform will be abused at scale. Design for it from the start. Implement rate limiting, verification requirements, and behavioral analysis before you need them.
Two: Separate authenticated users from anonymous users. Make it easy for real users to prove they are who they claim. Make it expensive for attackers to impersonate real users at scale.
Three: Monitor aggregate patterns. Individual attacks are hard to spot. But when you look at all submissions across all customers, patterns emerge. If you see a 500% spike in form submissions overnight from previously unused email addresses, something's probably wrong.
Four: Build transparency and alerting for customers. When attacks happen, customers need to know. Not in a way that's scary, but in a way that helps them understand what's happening and respond appropriately.
Five: Plan for resilience, not just prevention. You probably can't stop all abuse. But you can design your system to gracefully degrade under attack. If ticket volume spikes, legitimate tickets still get processed. Email still gets delivered. The system doesn't collapse.
Six: Stay humble about security. Zendesk has smart security people. They implemented what they thought would work. It didn't fully work. Security is an ongoing arms race. Build in flexibility to adapt.
What This Means for Email Providers
Gmail, Outlook, Proton Mail, and other email providers are in the interesting position of seeing this attack from the inside. They can see which sources are sending spam. They can analyze patterns. They can adjust filters.
The challenge is that they also can't just block all mail from Zendesk because Zendesk sends legitimate email for legitimate companies. The granularity is difficult. Blocking at the Zendesk level would break legitimate customers. Blocking at the individual company level requires per-instance analysis.
Email providers are likely already improving their filters based on this campaign. They're probably looking at Zendesk-sourced mail more carefully, checking for patterns. They might be implementing additional verification steps for mail from popular SaaS platforms during attack periods.
Longer-term, email providers need better tools to help users themselves filter this type of spam. Better rule-building interfaces. Better pattern detection. Better ways to verify legitimacy without relying purely on authentication tokens.
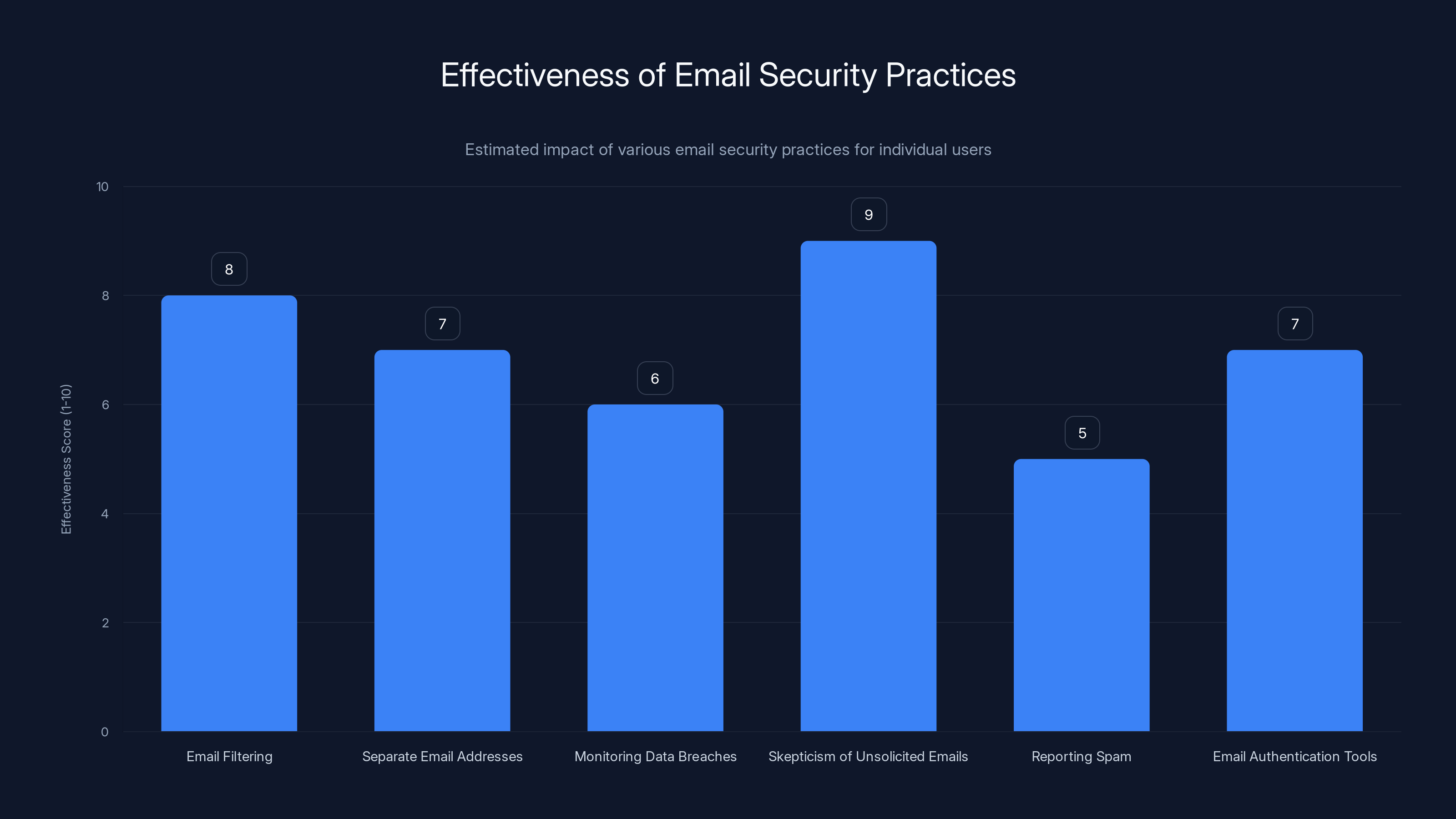
Email filtering and skepticism of unsolicited emails are highly effective practices for enhancing email security. Estimated data.
The Attribution Problem: Who's Actually Doing This?
As of early 2025, there's no definitive attribution. It's not publicly known which hacking group is responsible, or if it's even an organized group at all. This is intentional—the attack doesn't need sophisticated attackers. It just needs someone with basic scripting skills and patience.
Some security researchers have speculated that the attackers might be affiliates of larger cybercriminal groups testing new techniques. Others think it could be hacktivists making a point about platform security. Some wonder if it's competitive attack—a rival company or disgruntled employee trying to damage Zendesk's reputation.
Without definitive evidence, attribution is speculation. But it doesn't really matter for defense purposes. Whether this is one person with a script or an organized group, the defensive measures are the same. Regardless of who's attacking, the platform needs to be more resilient.
What matters is this: if someone can do it to Zendesk, they can do it to other platforms. If this goes unaddressed, expect similar campaigns against other widely-used customer service platforms. If you see success with Zendesk, why not try the same technique against Intercom? Or Freshdesk? Or any support platform?
Practical Timeline: What Happened When
Understanding the timeline helps you know whether you might be affected and what to look for.
Late January 2025: Initial reports of unusual Zendesk-sourced spam emails. Security researchers start investigating. Users report receiving dozens or hundreds of emails from support systems for companies they don't interact with.
Early February 2025: Zendesk acknowledges the issue. The company confirms that legitimate support ticketing systems are being abused. Initial investigation suggests possible DoS attack targeting Zendesk infrastructure.
Mid-February 2025: Zendesk announces deployment of new safety features including enhanced monitoring and rate limiting. The company states the issue is being addressed and users shouldn't expect immediate resolution.
Late February 2025: Security researchers observe that the attack continues despite new protections. Some companies report marginally reduced spam, but the campaign is ongoing. Speculation increases that attackers have found workarounds or are distributing the attack across multiple methods.
March 2025 and beyond: The campaign persists in some form. Zendesk continues developing additional protections. Individual companies and email providers deploy their own mitigations. The issue becomes a "known situation" that security teams manage rather than an active crisis.
This timeline is important because it suggests that full resolution might take months, not weeks. Security fixes at this scale rarely happen quickly. Organizations need to plan for ongoing mitigation rather than expecting a magic bullet.
Email Security Best Practices in Light of This Attack
This attack is a useful reminder of email security fundamentals that still matter, even in the age of sophisticated security tools.
Implement comprehensive email authentication. If your organization sends email, implement SPF, DKIM, and DMARC. These don't solve the Zendesk spam problem directly, but they establish baseline trust and make your legitimate email harder to spoof.
Use organizational email authentication records. Beyond just DMARC alignment, consider implementing stricter policies that align with your organization's actual needs. If legitimate third parties send email on your behalf (like Zendesk), explicitly allow them in your SPF records. Make the policy clear: everything not authorized gets rejected.
Monitor your infrastructure's reputation. If your domain or IP address is being used to send spam (even legitimate spam being abused by attackers), your reputation tanks. Use reputation monitoring tools to catch this early. Services like Return Path, Validity, or Google's Postmaster Tools can help.
Train users on email security. Teach your team to recognize suspicious emails, verify sender addresses, and report potential attacks. This is especially important for support teams who might receive higher volumes of suspicious email.
Implement defense-in-depth. Don't rely on any single security measure. Use multiple layers: authentication, filtering, user training, monitoring, incident response. When one layer fails, others catch problems.
Have an incident response plan for email. If your email infrastructure is compromised or abused, what's the response? Who do you notify? What do you communicate publicly? Having a plan in advance makes the response faster and more professional when something actually happens.
When the Attacker Is the Platform Itself
Here's an unsettling thought: what if the attacker isn't an external threat actor, but someone with access inside Zendesk or at one of the companies using it?
Inside jobs are rare but possible. An employee with access to bulk operations could theoretically create thousands of tickets programmatically. An administrator at a major Zendesk customer could abuse the platform's own infrastructure.
However, several factors make this less likely. First, modern SaaS platforms log access extensively. Bulk operations leave traces. If someone inside Zendesk was creating fake tickets, there would be audit logs. Second, the attack is widespread across too many different Zendesk instances. It would require coordination across multiple companies, which is harder to hide. Third, no credible evidence of insider access has emerged.
But it's worth considering. Not all security threats are external. Sometimes the most effective attacks come from people who already have access to systems. This attack—while likely external—should prompt organizations to audit their own access controls, logging, and who has the ability to perform bulk operations.
Looking Forward: Will This Happen Again?
Absolutely. Even if Zendesk completely solves this attack, the technique will be used against other platforms. Once an attack method proves effective, it becomes part of the attacker toolkit.
We'll probably see similar campaigns against:
- Freshdesk, Intercom, and other support platforms using the same ticket submission abuse technique
- Form builders and contact forms on websites, exploited to spam the site owners
- Survey platforms where anonymous responses trigger automated emails
- Webhook services where attackers trigger notifications at scale
- API platforms that send automatic confirmations for user actions
The pattern is always the same: find a legitimate feature that sends automated email, abuse it at scale. The platform becomes a spam distribution network for attackers.
The good news is that each platform that gets attacked becomes better defended. Zendesk's experience will inform Freshdesk's defense. Email providers improve filtering. Incident response becomes smoother. The ecosystem gradually becomes more resilient.
But it's an arms race. New platforms will emerge with the same architectural vulnerabilities. New attackers will discover new techniques. Security is never finished.
FAQ
What is the Zendesk spam attack?
The Zendesk spam attack is a campaign where attackers exploit Zendesk's legitimate support ticketing system to send spam emails to thousands of users worldwide. Attackers create fake support tickets using stolen or harvested email addresses, triggering automated confirmation emails that bypass spam filters because they originate from trusted corporate domains. The emails contain no malware or phishing links—they're just spam, but the volume suggests it could be a DoS attack targeting Zendesk's email infrastructure.
How does the Zendesk spam attack work technically?
Attackers compile lists of email addresses and use automated scripts to submit fake support tickets to various companies' Zendesk instances, placing victim email addresses in the "submitter" field rather than their own. Zendesk's automated system legitimately creates these tickets and sends confirmation emails to the specified addresses. Since these confirmations originate from real, trusted corporate domains with proper authentication tokens, they pass through most spam filters. Repeating this across thousands of companies' Zendesk instances at scale creates massive spam volume that's difficult to filter and potentially overwhelms Zendesk's email infrastructure.
Why can't spam filters block these emails?
These emails originate from legitimate corporate domains that companies have reputations for sending real email. They have proper SPF records, DKIM signatures, and pass authentication checks. Email filters are designed to trust legitimate business infrastructure, and these emails exploit that trust. Additionally, the emails are distributed across thousands of different company domains, so blocking one sender domain doesn't solve the problem. Creating rules that catch suspicious content is difficult when the emails are often just generic confirmation messages.
Is this actually a DoS attack against Zendesk?
That's the leading theory. The volume and coordination suggest attackers might be trying to overwhelm Zendesk's email infrastructure rather than target individual users. If millions of fake tickets are created, Zendesk must send millions of confirmation emails. This congests the company's email pipeline, potentially causing legitimate support confirmations to be delayed or lost. It's an infrastructure attack using the platform against itself, which is more sophisticated than simple user-directed spam.
What should I do if I receive these spam emails?
First, don't panic—these emails contain no malware or phishing links. Create email filter rules to catch confirmation emails from companies you don't recognize and move them to a folder. Verify suspicious emails by going directly to the company's website rather than clicking links in the email. Consider using separate email addresses for support tickets. Monitor your address on breach notification sites like Have I Been Pwned to understand your exposure. Most importantly, report the spam to your email provider to help improve collective filtering.
Is my company vulnerable if we use Zendesk?
Yes, any company using Zendesk could have its support system abused as a spam distribution point. The good news is you're not "hacked"—your Zendesk instance isn't compromised. The bad news is your company's domain reputation might suffer if customers receive spam appearing to come from your support system. Implement CAPTCHA challenges on your support forms, monitor ticket submission patterns, verify email addresses before sending confirmations, and communicate with customers about the campaign. Zendesk's latest protections should reduce but not eliminate the risk.
Will Zendesk fix this completely?
Probably not completely, but the situation will improve. The company's initial fixes (rate limiting and monitoring) weren't sufficient, so they'll likely implement additional protections like email verification, progressive enforcement, and better analytics. However, completely solving this attack requires balancing security with Zendesk's core feature of allowing unauthenticated ticket submissions. Some spam will likely continue, but at lower volume and with better detection over time.
Could this attack happen to other platforms?
Absolutely. Any SaaS platform that allows unauthenticated submissions and sends automated email responses is vulnerable. Contact forms, survey tools, form builders, webhook services, and other platforms could face similar attacks. Once this technique proved effective against Zendesk, attackers will try it elsewhere. Each targeted platform will need to implement similar defenses.
What makes this attack different from regular spam?
Traditional spam comes from attacker-controlled infrastructure or compromised systems. This attack abuses legitimate, trusted infrastructure to distribute spam. Attackers don't need to compromise anything or control email servers. They just exploit a legitimate feature at scale. This makes the attack much harder to block because it uses real, trusted sources. It also reveals how architecture designed for openness can be weaponized.
How long will this attack campaign continue?
There's no definitive answer, but typically campaigns like this last months rather than weeks. Attackers will continue if it's effective or if they achieve their goal (whatever that is). Zendesk will continue releasing protections. Email providers will improve filters. Eventually the attack becomes less effective, attackers move on, and the campaign quiets down. However, the technique remains in the attacker toolkit and will be used against other platforms.

Conclusion: The Real Security Lesson Here
The Zendesk spam campaign matters, but not primarily because of the spam itself. Most users will be annoyed. Most companies will implement a filter. Life goes on.
What matters is what this attack reveals about how modern security works in the cloud era. Trust is the foundation of internet infrastructure. Email providers trust that mail from Zendesk is legitimate. Companies trust that their Zendesk instances are secure. Users trust that emails from company support systems are real.
When that trust is exploited—not through hacking, but through understanding how systems work and abusing features at scale—it exposes vulnerabilities throughout the ecosystem. It shows that security isn't just about protecting against attacks we expect. It's about defending against creative abuse of legitimate functionality.
Zendesk will fix this. Email providers will improve. The industry will become incrementally more resilient. But new platforms will emerge with similar vulnerabilities. New attackers will discover new techniques. The cycle continues.
For you, personally, this attack is a reminder that email remains less secure than we'd like. That legitimate-looking emails can be suspicious. That security requires both technical protections and human skepticism.
For companies, it's a reminder that you're not isolated from platform security decisions. When a major service you depend on gets attacked, you feel the effects. Building resilience means monitoring your infrastructure, understanding platform limitations, and having plans for when things go wrong.
For platform builders, it's a reminder that security is architectural. It can't be bolted on after launch. Features that seem innocent—"let anyone submit a support ticket"—become attack surfaces at scale. The best platforms are designed with adversaries in mind from day one.
The Zendesk spam campaign will fade from headlines eventually. But the security lessons it teaches will remain relevant as long as platforms are used at scale and attackers remain creative. That's probably indefinitely.
The good news? Understanding attacks like this makes you better equipped to recognize them, respond to them, and prevent similar attacks on systems you build or depend on. Security is often about staying one step ahead of the creative ways people find to break things. This attack, while annoying, is an excellent teacher.
Stay alert. Keep your filters updated. Verify suspicious emails independently. And remember: when something seems too weird to be spam, it might actually be an infrastructure attack disguised as ordinary spam. The Zendesk campaign is proof that security threats aren't always what they seem.
Key Takeaways
- Attackers are exploiting Zendesk's legitimate support ticketing system to send spam at scale by creating fake tickets using harvested email addresses.
- The attack bypasses email spam filters because confirmation emails originate from trusted corporate domains with proper authentication tokens.
- This appears to be a DoS attack targeting Zendesk's email infrastructure itself, potentially overwhelming legitimate support ticket processing.
- Zendesk's initial security fixes (rate limiting and monitoring) were insufficient, with the campaign continuing despite company efforts to mitigate.
- Individual users can implement email filters, verify suspicious emails, and monitor breach databases; companies should add CAPTCHA and email verification to submission forms.
Related Articles
- ExpressMailGuard: AI-Powered Email Aliases & Spam Protection [2025]
- Substack Data Breach Exposed Millions: What You Need to Know [2025]
- Microsoft's Example.com Routing Anomaly: What Went Wrong [2025]
- Substack Data Breach [2025]: What Happened & How to Protect Yourself
- Coinbase Insider Breach Exposed 30 Customers' Data [2025]
- Moltbook Security Disaster: How AI Agents Exposed 1.5M Credentials [2025]
![Zendesk Spam Attack Explained: What's Happening & How to Protect Yourself [2025]](https://tryrunable.com/blog/zendesk-spam-attack-explained-what-s-happening-how-to-protec/image-1-1770381488508.jpg)



