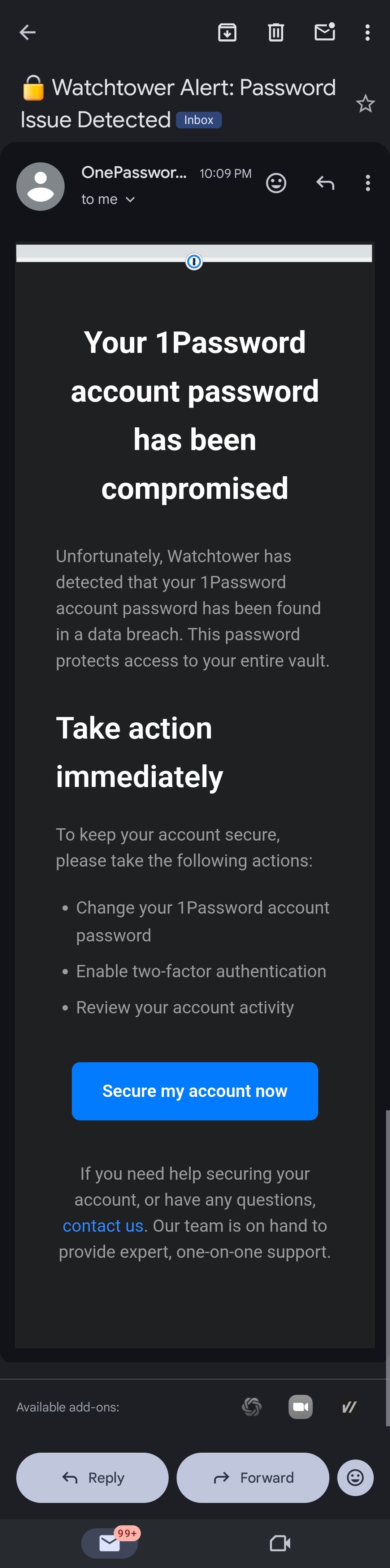
How 1 Password's New Phishing Protection Works: The Complete Guide
Phishing attacks have become one of the most devastating threats to both personal and enterprise security. Every single day, millions of people receive convincing emails or messages that trick them into visiting fake websites designed to steal their passwords. The problem is staggering. According to recent data, roughly 89% of Americans have encountered at least one phishing scam in their lifetime, and 61% have actually fallen victim to one. That's not a small number. That's nearly two-thirds of the population dealing with credential theft, identity fraud, or worse.
The financial impact? Absolutely massive. Businesses lose billions annually to phishing-related incidents. Individual victims face drained bank accounts, ruined credit scores, and months of recovery. So when a major password manager like 1 Password announces a new built-in phishing protection feature, it's worth paying serious attention.
1 Password just rolled out a game-changing tool that addresses one of the most effective phishing techniques: URL spoofing. This isn't just another security feature tacked on as an afterthought. It's a thoughtful, practical solution that catches the tricks hackers use every day.
Here's what makes this announcement significant: phishing has evolved far beyond the obviously fake emails of the early 2000s. Modern phishing attacks are sophisticated. They use nearly perfect replicas of legitimate websites, slight variations in domain names, and social engineering tactics that catch even security-conscious people off guard. 1 Password's new protection addresses this head-on.
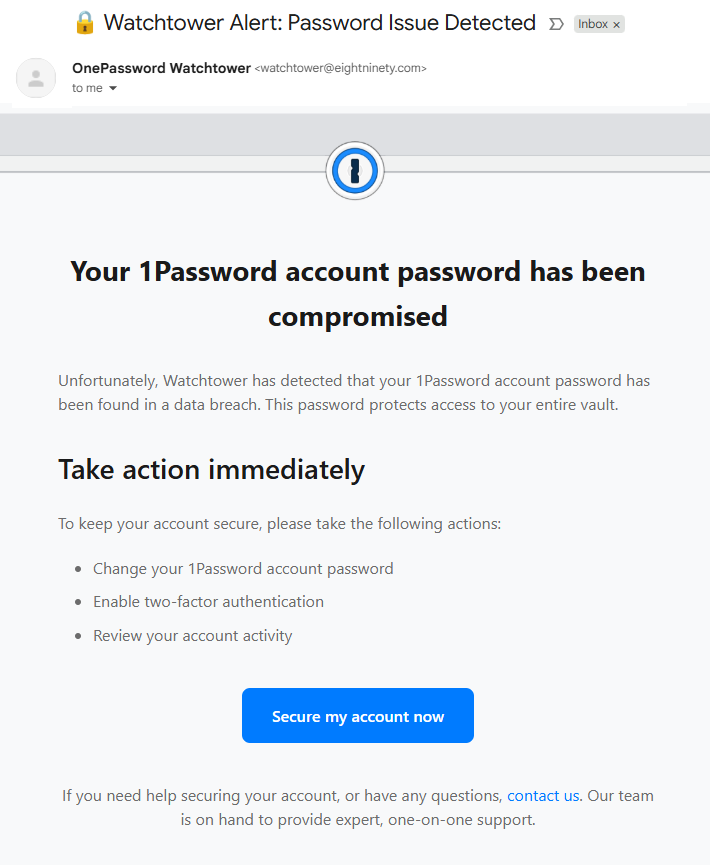
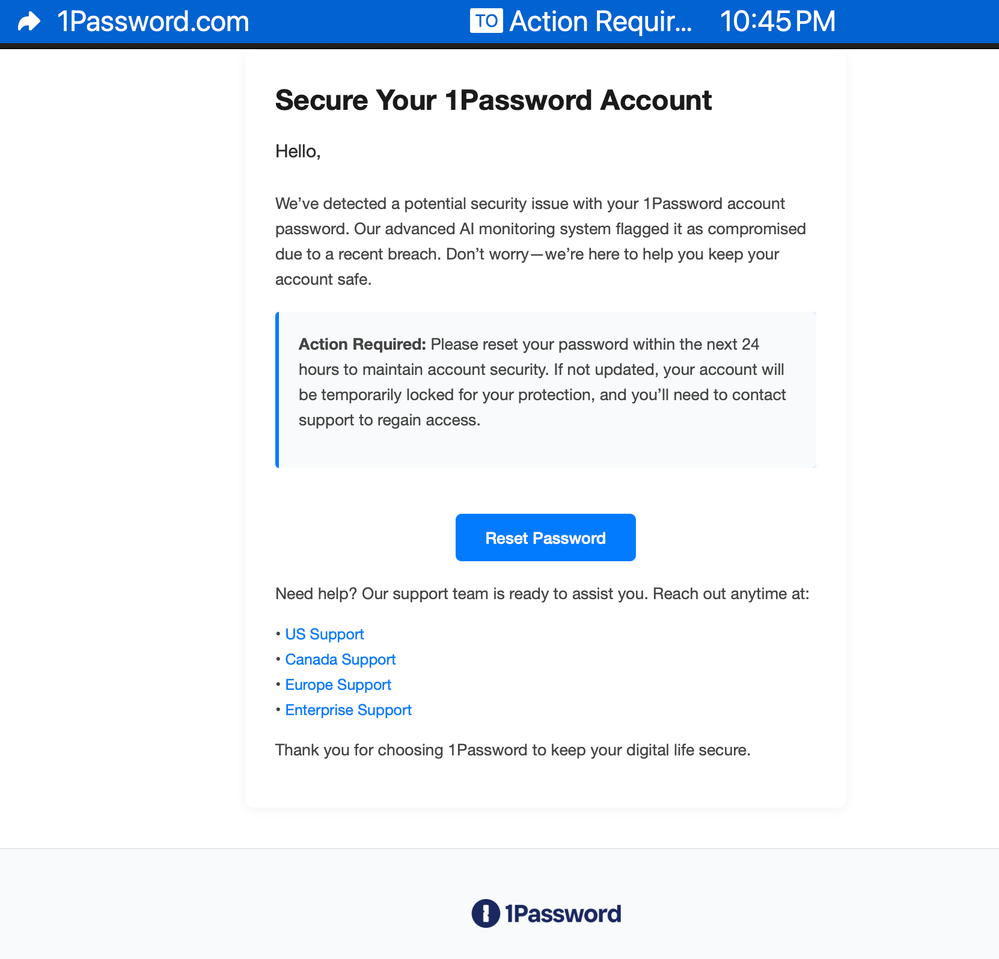
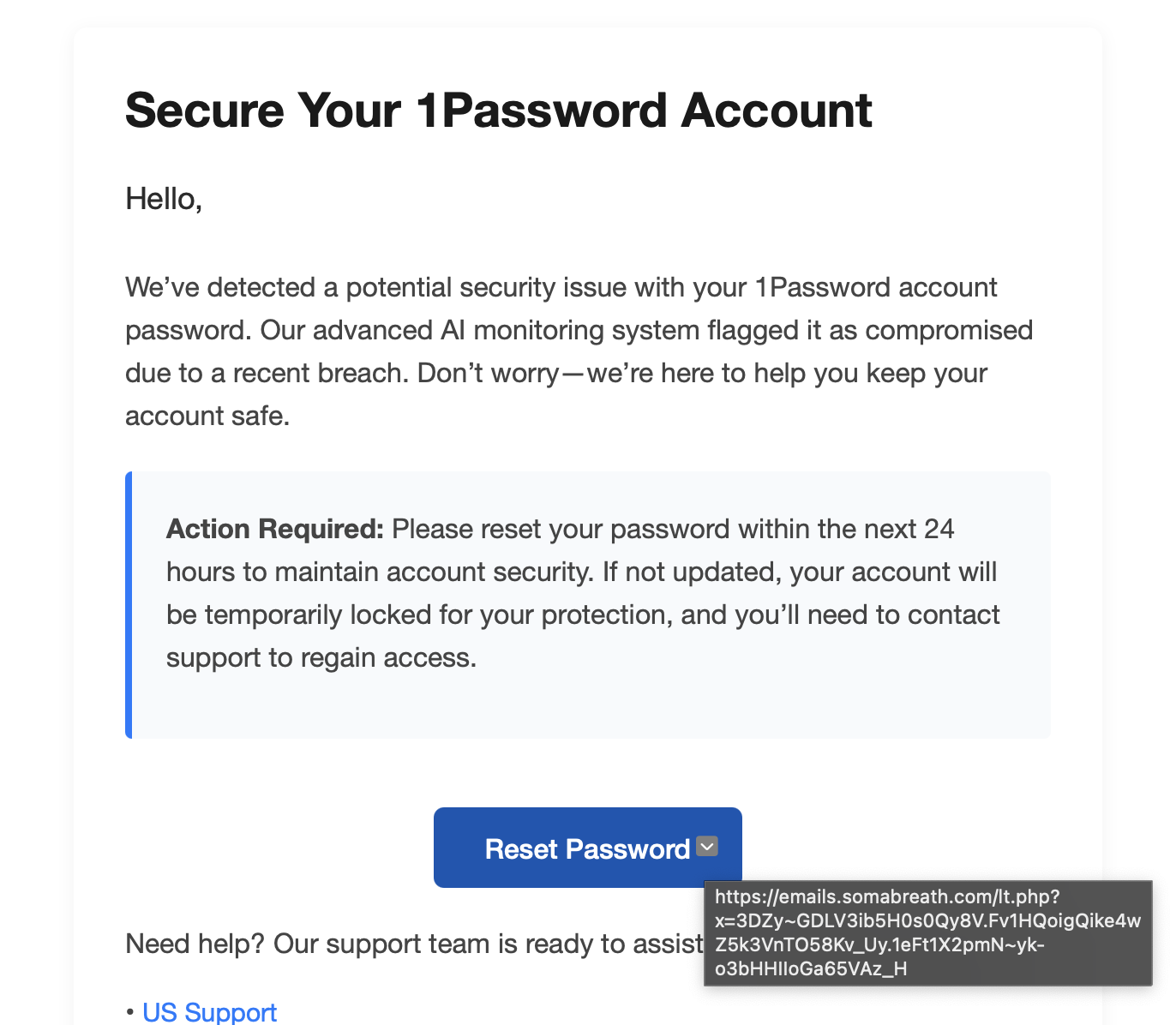
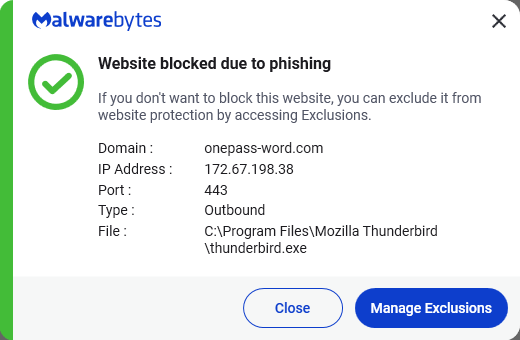
The new feature compares the URL you're currently visiting with the URL stored in your 1 Password vault. If they don't match, the autofill feature simply won't activate. And if you manually try to paste credentials into a suspicious site, 1 Password throws up a warning that tells you something's wrong. Simple. Effective. Potentially worth millions in prevented fraud.
The Phishing Problem: Why URL Detection Matters Now
Let's be clear about something: phishing isn't new. It's been around for decades. But the tactics have gotten smarter, and the stakes have gotten higher.
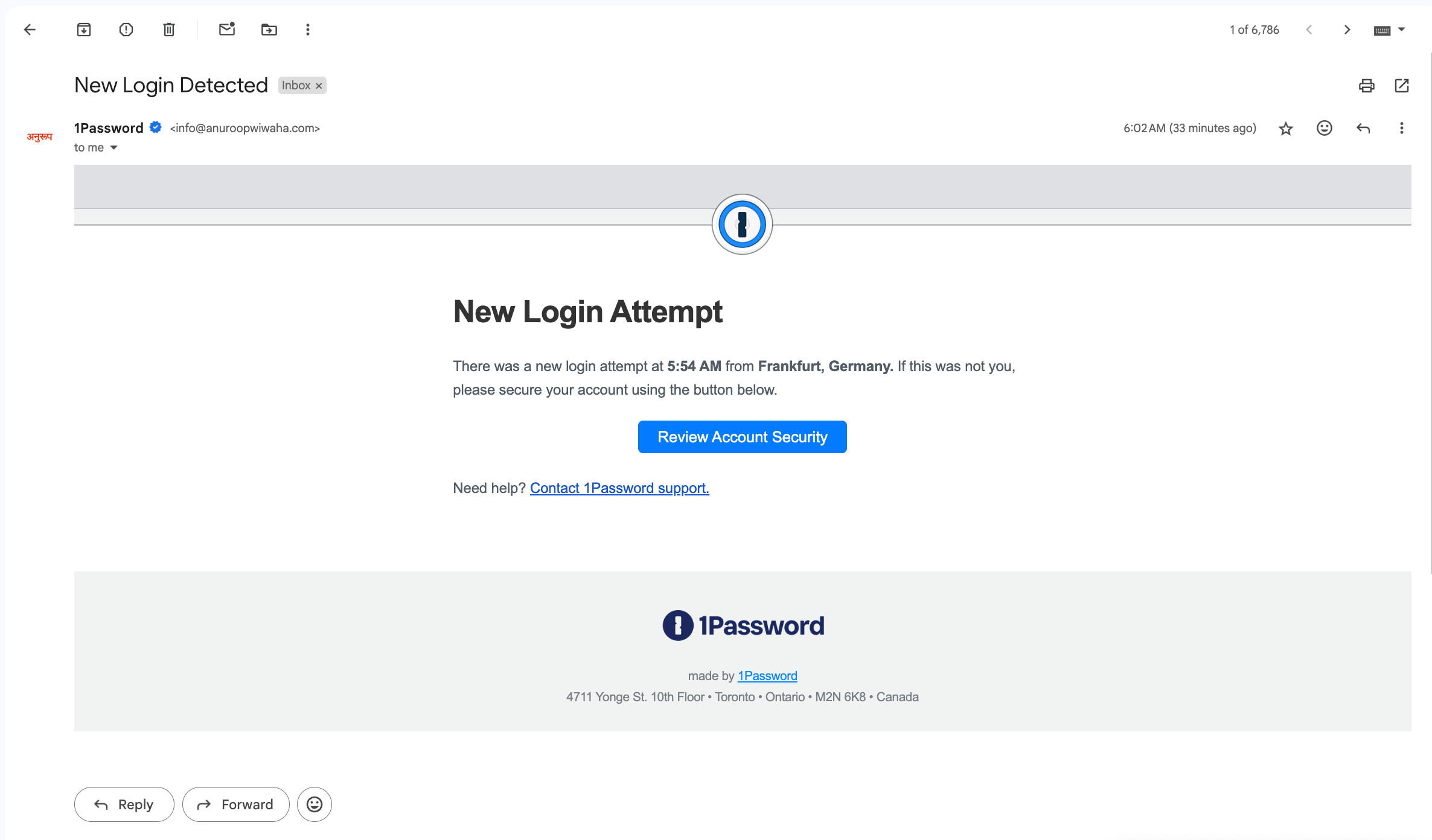
The most common phishing technique nowadays involves what's called typo-squatting or URL hijacking. Here's how it works: a hacker registers a domain that's almost identical to the real thing. Maybe they drop a single letter (gogle.com instead of google.com). Maybe they swap a character that looks similar (rn instead of m, making "gccgle.com" look like "google.com" at a glance). Maybe they add a tiny detail that seems legitimate (paypa1.com instead of paypal.com, using the number 1 instead of the letter l).
When you're in a hurry, which most people are, these differences slip right past. You click the link, land on a fake website that looks nearly identical to the real thing, and enter your credentials. The hacker now has your username and password. Within minutes, they're in your real account.
For businesses, this is catastrophic. An employee falls for a phishing email, unknowingly hands over their corporate credentials, and suddenly the attacker has access to the company network. They can steal intellectual property, access customer data, install malware, or demand ransom. The average cost of a phishing attack on a business is somewhere between $100,000 and several million dollars, depending on the scope.
For individuals, it's equally devastating. Your bank account gets drained. Your email gets hijacked. Your identity gets stolen. You spend months cleaning up the mess.
The problem with existing security approaches is that they're reactive. Most people rely on common sense, password managers, and maybe some security training. But common sense fails when you're tired, busy, or distracted. Security training helps, but people forget. Browser warnings catch some attacks, but not all.
What's been missing is a proactive layer that works silently in the background, catching these attacks before they even happen. 1 Password's new feature fills that gap.
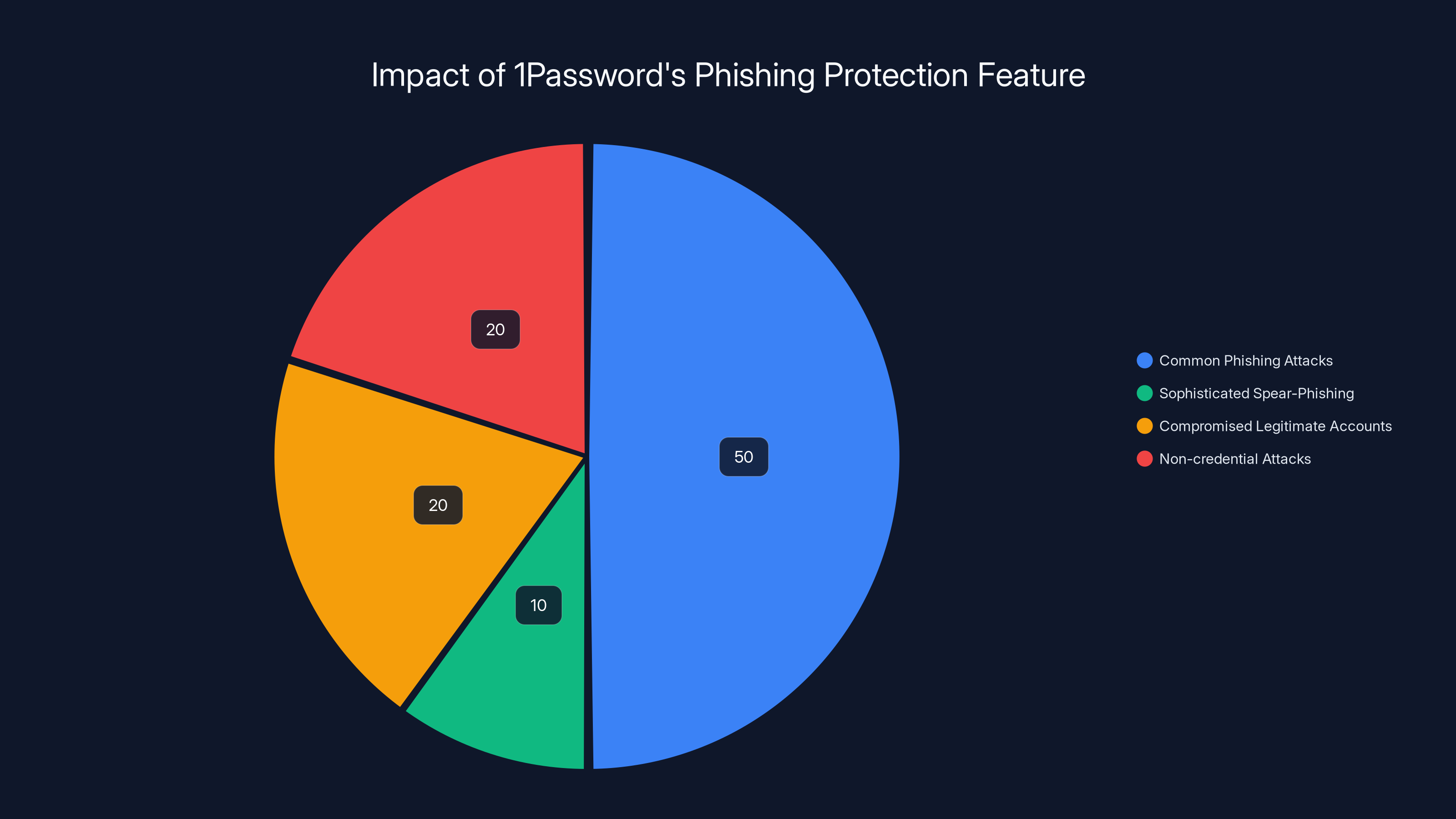
1Password's built-in phishing protection is estimated to effectively prevent 50% of common phishing attacks, highlighting its significant role in enhancing credential security. Estimated data.
How 1 Password's URL Comparison Technology Works
So how exactly does the technology work? It's actually more elegant than you might expect.
When you save a password in 1 Password, the application stores three key pieces of information: your username, your password, and the URL of the website where you use those credentials. That URL is crucial. It's the fingerprint of that specific service.
Now, whenever you visit a website and your password manager recognizes you're on a login page, it checks something: does the current URL match the URL stored in your vault for that particular account?
If it matches, autofill works normally. You get a frictionless experience, and your credentials are filled in automatically.
If it doesn't match, autofill is blocked. You won't see the suggested password popup. This forces you to pause and think. Why isn't my password manager recognizing this site?
Take it a step further: if you manually try to paste your stored password into a site where the URL doesn't match anything in your vault, 1 Password displays an explicit warning. It tells you that the URL might not be legitimate and that you should verify you're on the correct website before entering your credentials.
This is brilliant because it works at multiple levels. It prevents the automatic leak of credentials. It interrupts your workflow in a way that makes you think. And it provides explicit, clear feedback about what's wrong.
The technology doesn't require any cloud connectivity, special databases, or real-time phishing feeds. It's purely local. It just compares URLs. This means the feature is fast, it works offline, and it doesn't require 1 Password to maintain an constantly updated database of phishing sites.
What makes this approach so effective is that it catches a specific, high-impact category of attacks: those that use URL spoofing. While it won't catch every phishing attack (some attacks don't involve credential entry at all), it addresses one of the most common and most successful tactics.
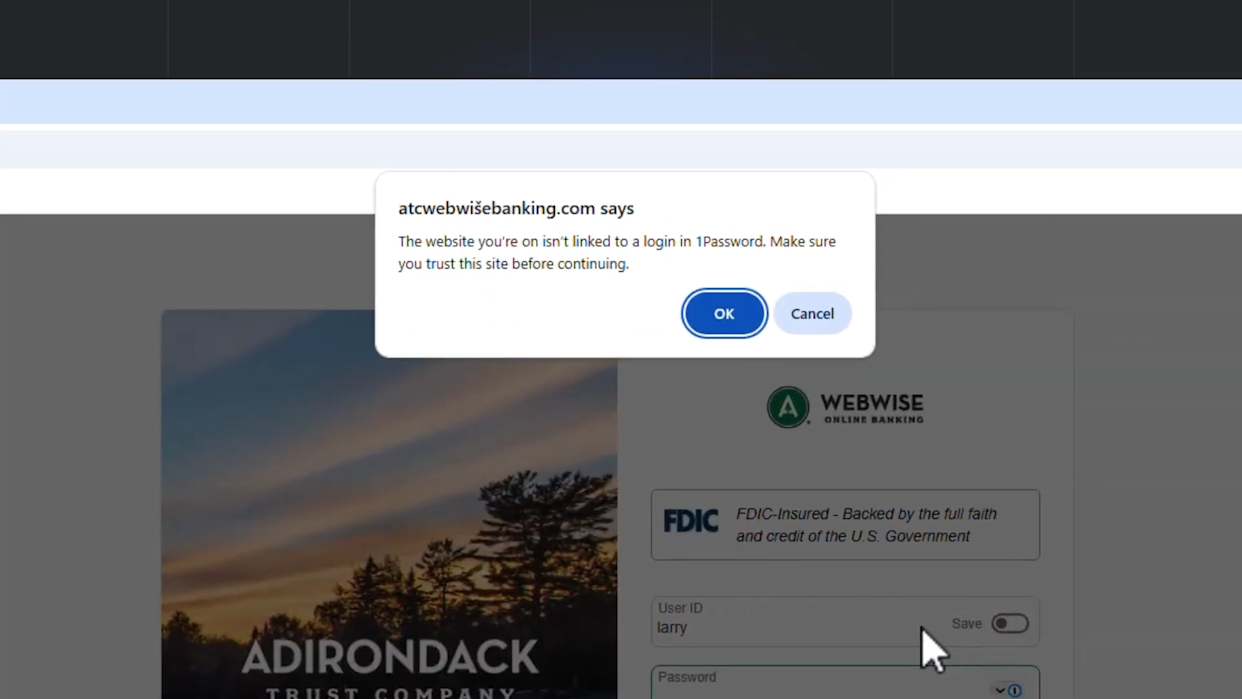
Why This Matters for Individual Users
If you're a regular person using 1 Password to manage your passwords, this feature just gave you a powerful new layer of protection without you having to do anything.
Remember, the feature is enabled by default on all Individual and Family plans. You don't need to flip any switches or change any settings. It just works. Every time you autofill a password, 1 Password is checking that URL. Every time you manually paste a password, you get that warning if something's wrong.
For someone like you, this translates to concrete protection against the most common phishing attack vectors. You're less likely to accidentally hand over your credentials to a hacker. Your bank account is safer. Your email is safer. Your identity is safer.
But there's a deeper psychological benefit too. When 1 Password blocks autofill or shows that warning, it creates a moment of friction. That friction makes you stop and think. It makes you verify the URL. It makes you notice those small details that would normally slip past. Over time, this trains your brain to be more aware of these attacks.
The feature also protects against a specific vulnerability that many people don't realize they have: the habit of reusing passwords. Even though 1 Password makes it easy to use a unique password for every account, plenty of people still reuse passwords across multiple sites (which is a terrible idea, by the way). If you fall for a phishing attack on one website, an attacker can now attempt to access all your other accounts using that same password. The URL detection feature doesn't prevent password reuse, but it does prevent the initial compromise that makes reuse dangerous.
Another real-world scenario: someone sends you a link in email or Slack. You click it without thinking. You land on a site that looks legitimate. Your password manager tries to autofill, but it doesn't. Red flag. You suddenly realize you're not on the website you thought you were. You close the browser. You navigate to the actual website. You never enter your credentials on the fake site. Crisis averted.
That's the power of this feature. It's not flashy or complicated. It's just smart protection that works in the background.
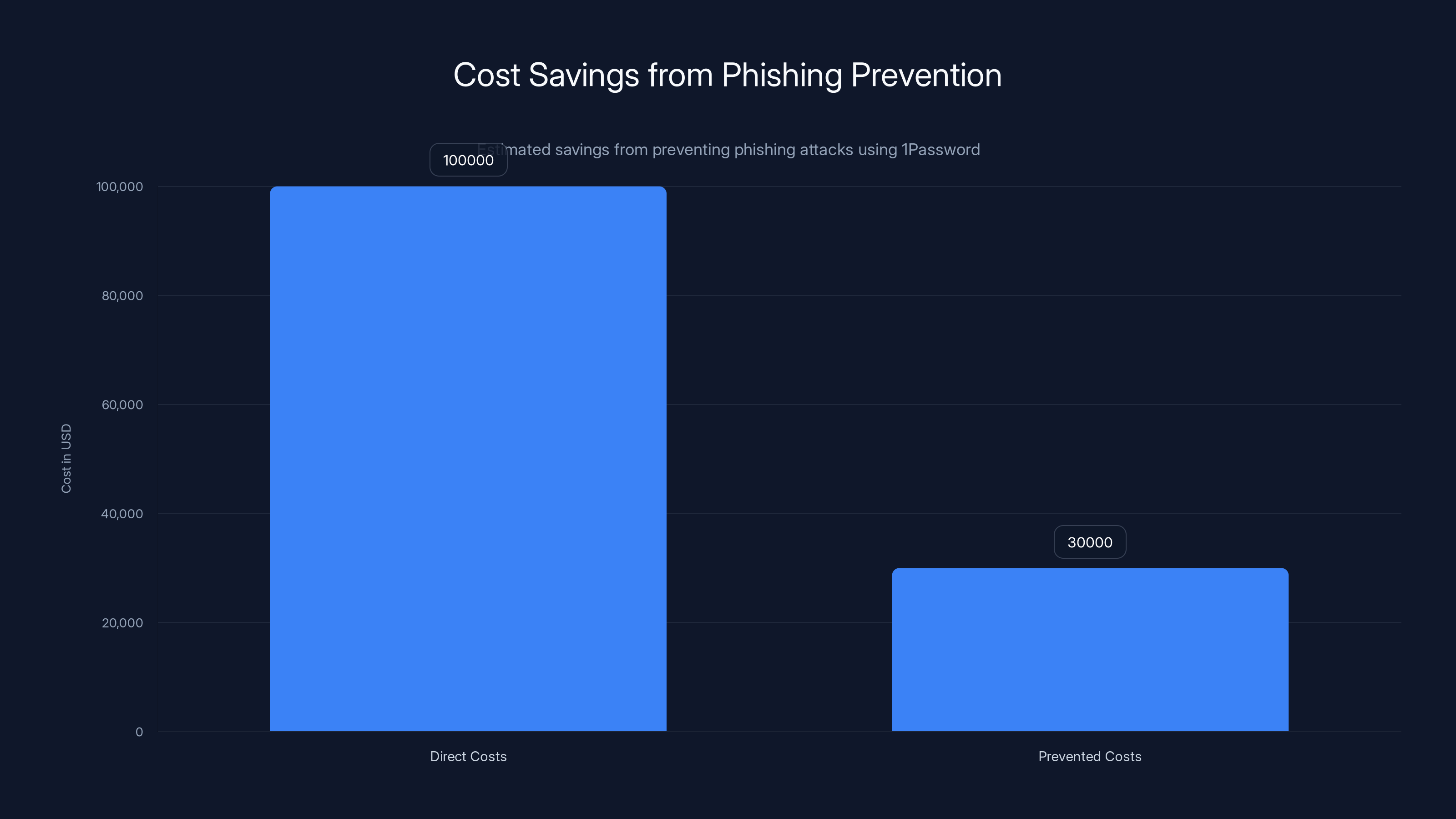
Implementing phishing prevention can save businesses an estimated $30,000 in direct costs by preventing 30% of phishing attacks. Estimated data.
Enterprise Security: How This Works for Business Plans
For enterprises, the implications are even more serious. A single compromised employee account can lead to data breaches, ransomware infections, or worse.
1 Password for Business includes the new phishing protection too, but with additional flexibility. Instead of having the feature always on, enterprise administrators can use Authentication Policies in the 1 Password admin console to enable enhanced phishing protection for specific users or departments.
Why would an administrator want this flexibility? Different teams have different risk profiles. Your security team might need maximum protection enabled. Your creative department might work with many third-party websites and tools, making strict URL matching less practical. Your finance team definitely needs maximum protection because they handle sensitive transactions.
Administrators can now granularly control who has this feature enabled, which is a sophisticated approach to enterprise security. It's not one-size-fits-all. It's tailored to actual organizational needs.
For IT security leaders, this feature represents a significant reduction in one category of attacks. Every email where an employee doesn't fall for a phishing link is one less incident to investigate, one less credential reset to perform, one less potential breach to recover from.
Let's do some basic math. If an enterprise has 1,000 employees and 1% of them typically fall for phishing attacks each month, that's 10 compromised accounts. Each compromise might cost
Beyond the financial argument, there's the human element. Security teams spend an enormous amount of time educating employees about phishing. They run simulated phishing campaigns to test awareness. They constantly reinforce the message: "Be careful with URLs. Don't click suspicious links. Verify before entering passwords."
What's often missing is the technical control that actually prevents the attack, even if the employee's judgment fails. 1 Password's URL detection is that technical control. It's defense in depth. It's a safety net for when human judgment inevitably falls short.
Administrators can communicate this clearly to employees: "We've added a new tool that will help protect you. If you see a warning about a URL not matching, trust it. Your password manager is looking out for you." This actually makes employees feel more secure, which paradoxically makes them more cautious.
The Science Behind URL Spoofing: Why It's So Effective
Understanding why phishing works requires understanding some human psychology and how our brains process visual information.
When you see a URL, you don't read every single character. Instead, your brain does something called "perceptual grouping." It glances at the domain, recognizes the pattern, and assumes you're on the right website. If a hacker can exploit that natural tendency, they've won.
Consider these examples, and pay close attention:
- gogle.com (missing o)
- goog1e.com (1 instead of l)
- g00gle.com (00 instead of oo)
- ggoogle.com (extra g)
- paypai.com (missing l)
- faceb00k.com (00 instead of oo)
Each of these is different from the legitimate URL, but each one is subtle enough that your brain might miss it, especially if you're in a hurry or the context makes you expect to see that website.
Phishing emails increase the likelihood you'll miss these details by creating urgency. "Your account has been compromised. Click here immediately." Your amygdala activates (that's the fear center of your brain). Blood rushes away from your prefrontal cortex (the part that does careful analysis). You click. You don't read the URL carefully. You're on a fake site.
What's particularly clever about typo-squatting is that many domains are legitimately registered by security researchers or by 1 Password and other security companies specifically to prevent hackers from using them. But not all of them. A hacker who's willing to spend $12 per year on a domain registration can set up a convincing fake.
URL detection technology bypasses all of this human psychology. It doesn't care if you're in a hurry or distracted or stressed. It compares URLs at the binary level. Either the URL matches or it doesn't. It's objective. It can't be tricked by similar-looking characters or clever social engineering.
This is why 1 Password's approach is so powerful. It's not trying to educate you or make you more aware or teach you to look carefully at URLs. It's simply removing the possibility of the attack succeeding, regardless of human attention or awareness.

What About False Positives? When Protection Creates Friction
One legitimate concern with any security feature is false positives. Does 1 Password's URL detection ever block legitimate password fills? And when it does, how bad is the experience?
The short answer is yes, there are scenarios where false positives could occur, and 1 Password has clearly thought about this.
Consider this scenario: you saved your banking password while logged into www.mybank.com. Later, you navigate to https://www.mybank.com (notice the https and www). Technically, these are slightly different URLs. Some systems might treat them as different. Does 1 Password?
From what we understand about the implementation, 1 Password is likely smart enough to treat these as equivalent. It recognizes that www and https variations are normal. But there's always a possibility of edge cases.
Another scenario: you saved your password for a site that uses a specific subdomain, like mail.myservice.com. Later, you try to access it from a different subdomain, like app.myservice.com. Depending on the implementation, the password manager might not autofill.
For most users, this isn't a problem. They access services from the same URL consistently. They log in, save the password, and access from the same location going forward.
But for some users, particularly those who access services from multiple locations or who use URL redirects, there's potential friction. When autofill doesn't work, you have to manually enter your password. It's not a huge inconvenience, but it's a slight degradation of the seamless experience that password managers are known for.
1 Password's approach to this is reasonable: the feature is enabled by default for Individual and Family users (they can disable it if needed), but for Business users, administrators have granular control. They can enable it for certain users or departments where the benefits clearly outweigh the risks of false positives.
The trade-off is well worth it for most people. A slight inconvenience a few times a year is a small price to pay for protection against phishing attacks that could compromise your entire digital life.

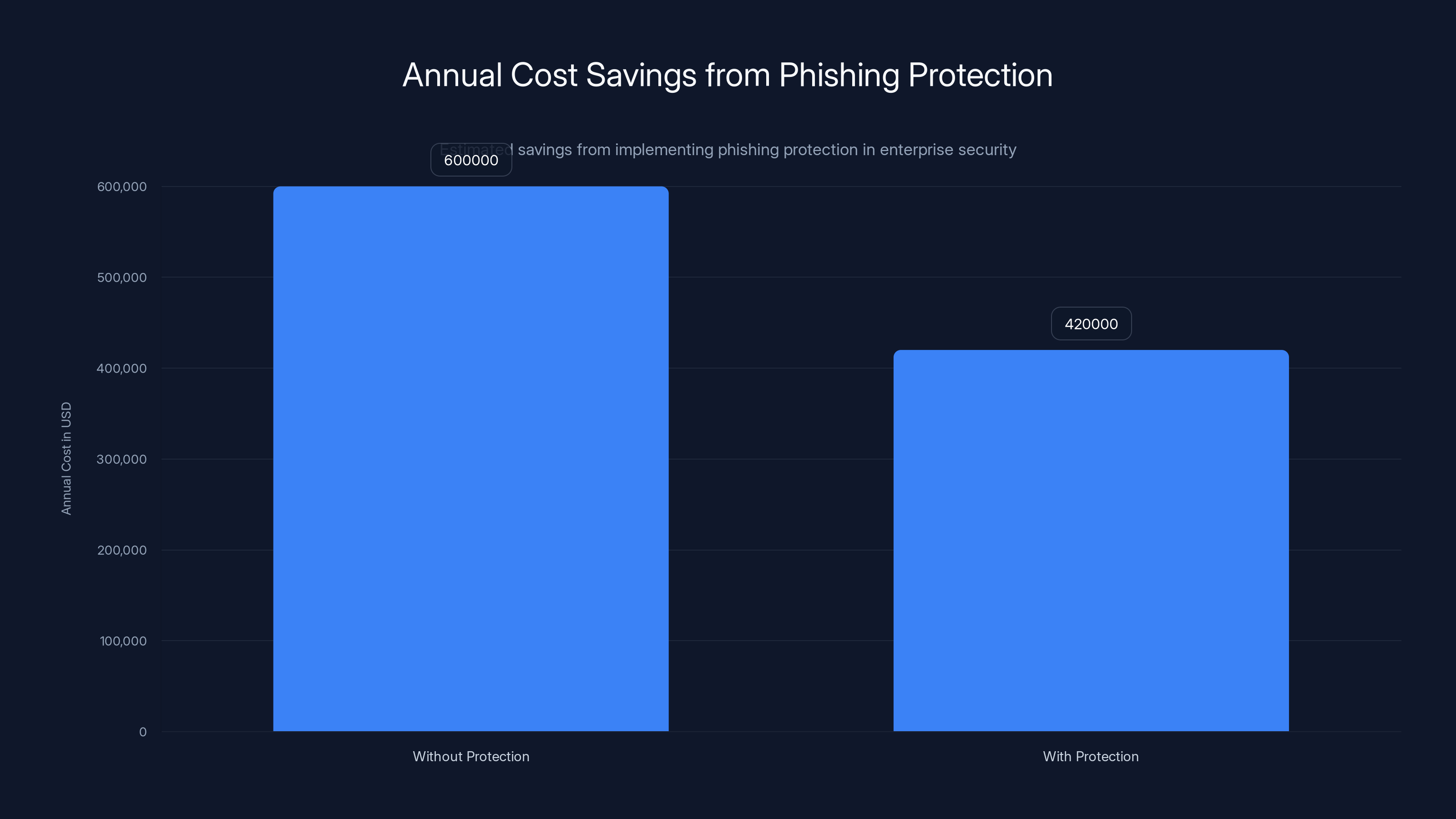
Implementing phishing protection can save enterprises approximately $180,000 annually by reducing phishing incidents by 30%. Estimated data.
How to Enable and Configure Phishing Protection
Here's the good news: for most users, there's nothing to do. The feature comes enabled by default on Individual and Family plans.
But it's worth knowing how to verify that it's enabled and how to understand what it's doing.
For Individual and Family Users:
Open 1 Password and navigate to Settings (or Preferences, depending on your operating system). Look for the section labeled Security or Protection. You should see the phishing protection feature listed. The toggle should be On by default. If for some reason you want to disable it (though we don't recommend this), you can.
You can also verify the feature is working by testing it. Try manually pasting a password into a website where the URL doesn't match your saved credential. You should see a warning appear. This is the feature working as intended.
For Business Users:
Administrators have more control. Log into the 1 Password admin console. Navigate to Authentication Policies. Here, you can configure enhanced phishing protection for different user groups or the entire organization.
You can choose to:
- Enable phishing protection for all users
- Enable it for specific departments or teams
- Disable it for users or departments where it causes too much friction
- Monitor compliance to ensure the policy is working
The key here is that administrators should educate their users about what's happening. Let them know that if autofill doesn't work or if they see a warning, it's because 1 Password detected a potential phishing attempt. This transforms the security control from something that feels restrictive into something that feels protective.
Comparing 1 Password's Phishing Protection to Alternatives
Here's the reality: 1 Password isn't the first password manager to address phishing. Other solutions like Bitwarden, Dashlane, and Keeper have various anti-phishing features.
But 1 Password's approach has some distinct advantages.
Bitwarden, for example, offers phishing detection through browser extension warnings, but the core feature set is less sophisticated than what 1 Password is rolling out. Dashlane has phishing warnings, but they're more notification-based than preventative. Keeper offers security features, but they're often bundled into enterprise plans.
What sets 1 Password apart is the simplicity of the approach combined with the fact that it's enabled by default across all plan tiers (Individual, Family, and Business). It's not a premium feature. It's not something you have to opt into or configure. It just works.
There's also the matter of implementation philosophy. 1 Password is positioning this as a local, client-side comparison. It doesn't require cloud connectivity or external phishing databases. This means it's fast, it works offline, and it respects privacy. You're not sending URLs to 1 Password servers for analysis.
Compare this to some browser-based phishing detection systems that rely on real-time lookups against known phishing databases. Those systems have to be constantly updated as new phishing sites appear. They require internet connectivity. They send your browsing patterns to a third party for analysis.
1 Password's approach is different. It's elegant and privacy-respecting.
That said, no single feature prevents all phishing attacks. URL detection catches typo-squatting and spoofed domains. But it doesn't catch phishing attacks that don't involve credential entry (like ransomware distribution). It doesn't catch spear-phishing attacks that use legitimate domains. It doesn't catch social engineering attacks that trick you into revealing information without entering credentials on a website.
What it does catch are the attacks that are most common and most likely to succeed: the mass-market phishing campaigns that use similar-looking URLs to trick people into entering credentials.

The Role of Password Managers in Modern Security
Before we wrap up, let's step back and think about where password managers fit into the broader security landscape.
For decades, security experts have been saying the same thing: use unique, strong passwords for every account. Most people ignored this advice. They used simple passwords they could remember (like Password123). They reused the same password across multiple sites. When a breach happened on one site, their password worked on dozens of others.
Password managers changed this calculus. Suddenly, using a unique, 32-character random password for every account was not just possible but easy. You didn't have to remember it. Your password manager did.
This was a massive security improvement. It meant that when a breach happened on some obscure website, the damage was limited to that one account. Your important accounts (email, banking, social media) remained protected because you used different passwords everywhere.
But password managers are more than just password storage. They're becoming security platforms.
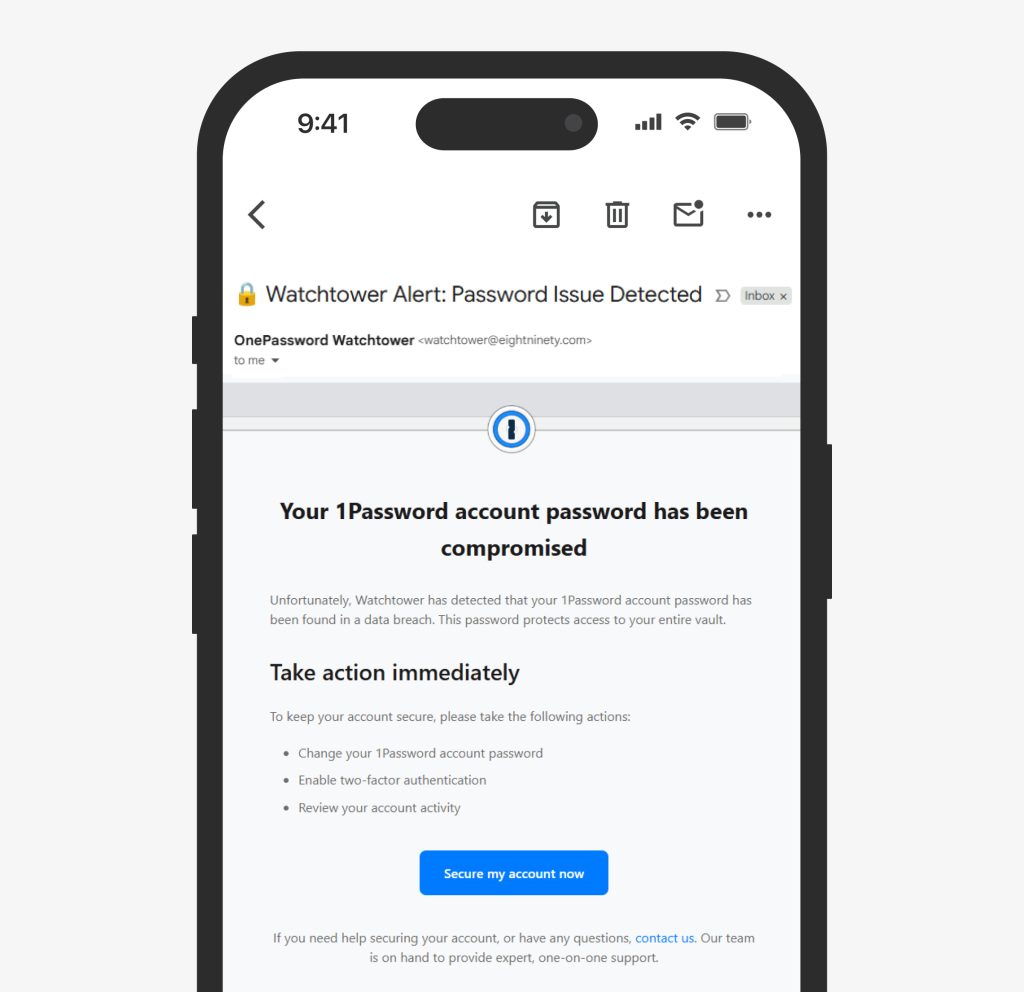
1 Password added watchtower alerts (notifications when your password might have been compromised in a data breach). They added document storage for sensitive information. They added Family and Business plan features for sharing and administration. Now they're adding phishing protection.
The trend is clear: password managers are evolving from a convenience tool into a comprehensive security platform. They're the trusted intermediary between you and your digital accounts. They know which accounts you have, which passwords you use, and which websites you visit.
With that knowledge comes responsibility, and also opportunity. 1 Password's URL detection is an example of that. By knowing which websites you've saved passwords for, 1 Password can now protect you from phishing attacks targeting those specific accounts.
This is a powerful shift. Instead of relying on users to spot phishing attacks (a task humans are terrible at), the security system itself is doing the spotting. It's defense in depth. It's layered security. And it's becoming the standard way modern password managers work.

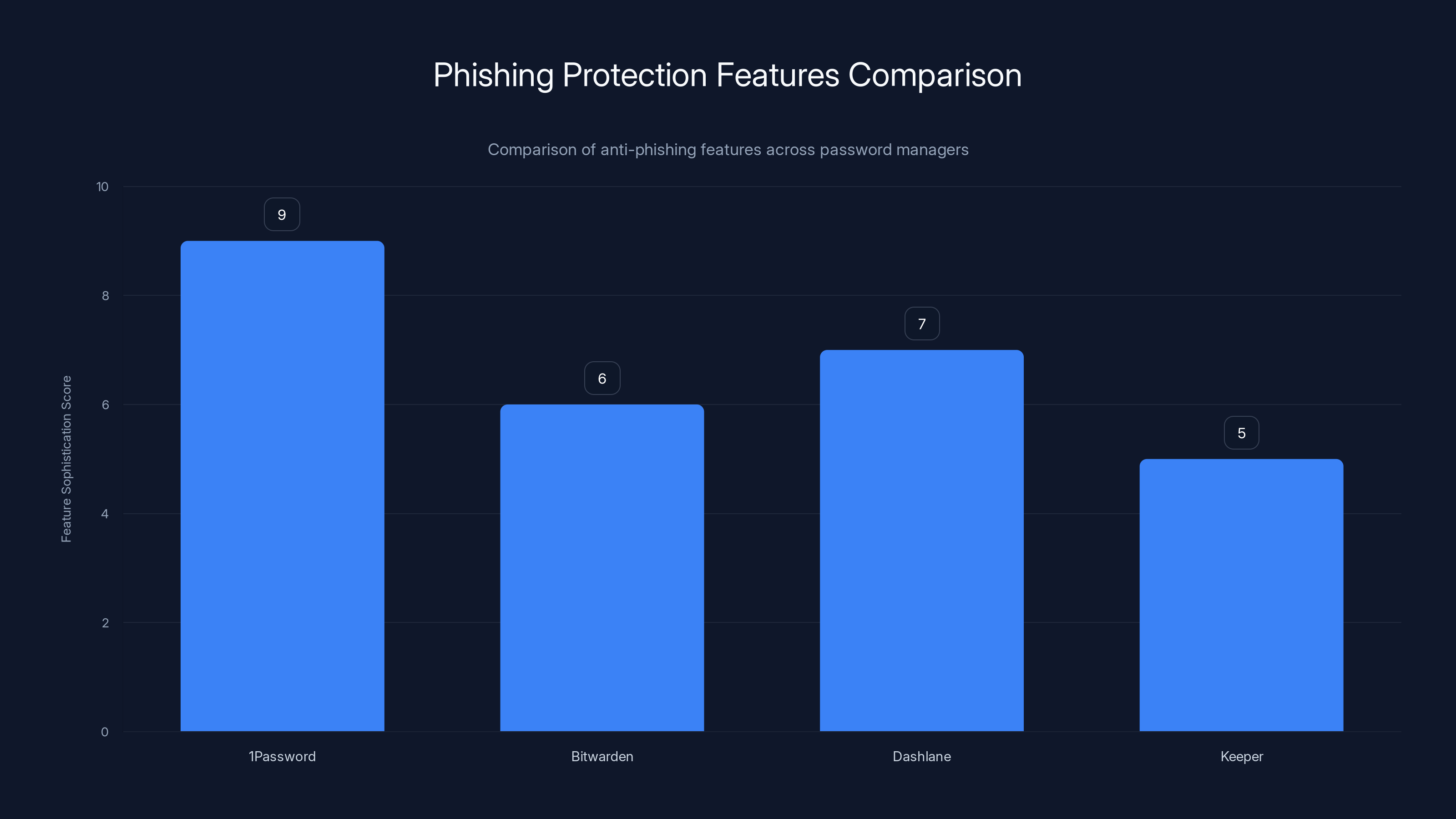
1Password leads with a score of 9 due to its default, offline, and privacy-respecting phishing protection, while Bitwarden, Dashlane, and Keeper follow with less sophisticated implementations. Estimated data based on feature descriptions.
Rollout Timeline and Availability
So when can you expect this feature? And what's the timeline for availability across different platforms?
According to 1 Password's announcement, the phishing protection feature is rolling out to all Individual, Family, and Business plans. The rollout is happening gradually, so if you don't see it immediately, don't panic. It should be available within the next few weeks depending on your account region and platform.
The feature should be available on all major platforms: Mac, Windows, iOS, and Android. The browser extensions (Chrome, Firefox, Safari, Edge) will also get the feature.
For Business users, administrators can enable the feature through the admin console whenever it becomes available in their region.
One thing to note: if you're using an older version of 1 Password, you might need to update to get access to this feature. It's always a good idea to keep your security software updated anyway.
What This Means for the Future of Password Manager Security
This move by 1 Password is significant for another reason: it signals where the password manager industry is heading.
Password managers are becoming security platforms. They're not just storing passwords anymore. They're becoming the trusted software that sits between you and the internet, catching threats before they succeed.
You can expect to see more features like this from other password managers. Bitwarden might enhance their phishing detection. Dashlane might add more sophisticated URL analysis. Keeper might expand their security capabilities.
But there's something important to understand: not all security features are created equal. The effectiveness of phishing detection depends on how it's implemented. Is it client-side or cloud-based? Is it always on or opt-in? Does it respect privacy? Does it work offline? Does it handle edge cases well?
1 Password's approach—local, always-on, privacy-respecting—sets a high bar for others to match.
The broader implication is that users are demanding more from their security tools. We've moved past the era where a password manager was just a vault. Now users expect threat detection, breach monitoring, security insights, and proactive protection.
Password managers are becoming the security operating system of your digital life. 1 Password's phishing protection is a step in that direction.
Best Practices: Using Phishing Protection Effectively
Now that you understand how 1 Password's phishing protection works, here's how to use it effectively.
First, trust the warnings. If 1 Password tells you that a URL doesn't match, take that seriously. Don't try to work around it. Don't think "Well, I'm pretty sure this is legitimate." Your password manager knows more about your accounts than you do. Trust it.
Second, keep your saved URLs accurate. When you save a password in 1 Password, verify that the URL is correct. If you save your banking password with an incorrect URL, the phishing protection won't work for that account. This is a good reason to review your saved passwords periodically and ensure all the details are correct.
Third, use the feature in combination with other security practices. Phishing protection is one layer. It's not the only layer you need. Use strong, unique passwords (which 1 Password makes easy). Enable multi-factor authentication (MFA) on important accounts. Keep your operating system and software updated. Be cautious about what you click in emails and messages.
Fourth, educate yourself about phishing. Understanding the tactics that hackers use makes you less vulnerable. Read about recent phishing campaigns. Participate in security awareness training if your organization offers it. The more you know, the better decisions you make.
Fifth, for enterprise users, communicate about the feature. If you're a security leader implementing this feature, tell your team about it. Explain what it does, why it matters, and what they should do if they see a warning. This transforms the feature from a technical control into something everyone understands and appreciates.

1Password's phishing protection is highly effective across all plans, with Business plans having slightly enhanced control features. Estimated data.
The Bigger Picture: Phishing as an Existential Threat
Let's be honest: phishing is a huge problem, and it's not going away.
Cybercriminals have figured out that social engineering and phishing are more effective than technical exploits in many cases. Why spend months developing zero-day exploits when you can send a convincing email and have someone hand you the keys to the kingdom?
Phishing attacks are increasing in volume, increasing in sophistication, and becoming more targeted. There are campaigns specifically designed to target finance professionals, healthcare workers, government employees, and executives. These aren't mass-market phishing campaigns. They're crafted specifically to deceive their target audience.
But there's also good news. Security is improving. Tools are getting better. Awareness is increasing. Companies are implementing better defenses.
1 Password's phishing protection is part of that positive trend. It's not a silver bullet. But it's a meaningful layer of protection that works silently in the background, catching attacks that would have succeeded before.
When you consider that a single compromised credential can cost a business millions of dollars, and a single phishing attack can ruin someone's personal finances, phishing protection isn't a nice-to-have feature. It's essential.
The fact that 1 Password is building phishing detection into a free or low-cost password manager means that everyone can benefit from better security. You don't need to be a tech expert or work for a Fortune 500 company with a massive security budget. You can get enterprise-grade phishing protection simply by using 1 Password.
That's a meaningful democratization of security.
Common Questions About 1 Password's Phishing Protection
Let me address some questions that might be on your mind.
Q: Does this feature work if I'm using 1 Password for Teams? Yes. The phishing protection feature is available across all plan tiers, including Teams plans for small businesses.
Q: What if I have multiple email addresses for the same account? Will the URL detection still work? The feature doesn't care about email addresses. It only cares about URLs. As long as the website URL matches what's stored in 1 Password, autofill will work regardless of which email address you use.
Q: Can I disable the feature for specific websites? On Individual and Family plans, the feature is system-wide, though you can disable it entirely in settings. On Business plans, administrators can configure it more granularly.
Q: What about if I access a website from multiple subdomains? This is one area where false positives might occur. If you save a password for one subdomain and then try to access from another, autofill might not work. You might need to manually enter your password or contact your password manager for help with this specific scenario.
Q: Does this protect against all types of phishing? No. It specifically protects against URL-based phishing attacks. It doesn't protect against phishing attacks that don't involve credential entry, like attachment-based malware or ransomware distribution.
How 1 Password's Feature Compares to Industry Standards
When 1 Password announced this feature, they positioned it as cutting-edge. But how does it actually compare to what other security tools are doing?
Most major password managers now have some form of phishing detection. But they vary widely in approach.
Browser-based security tools (like Google Safe Browsing) use real-time lookups against known phishing databases. This approach works well for catching widely known phishing sites, but it relies on external connectivity and has a delay between when a phishing site is discovered and when it's added to the database.
1 Password's approach is different. It's not comparing against a database of known phishing sites. It's comparing against your personal vault of credentials. This means it catches attacks even against unknown, newly created phishing sites, as long as they target accounts you have in your vault.
Is this better or worse than other approaches? It depends. For catching targeted phishing attacks against specific accounts you have, 1 Password's approach is superior. For catching broadly applicable phishing sites that target many people, browser-based detection might be better.
Ideally, you'd use both. And many people do: they use 1 Password for credential protection and their browser's built-in security for broader threat detection.
What makes 1 Password's implementation notable is the elegance and simplicity. It doesn't require any external services. It works offline. It has minimal false positives (the logic is straightforward: does the URL match or not). And it's enabled by default, which means most users benefit without having to understand or configure anything.
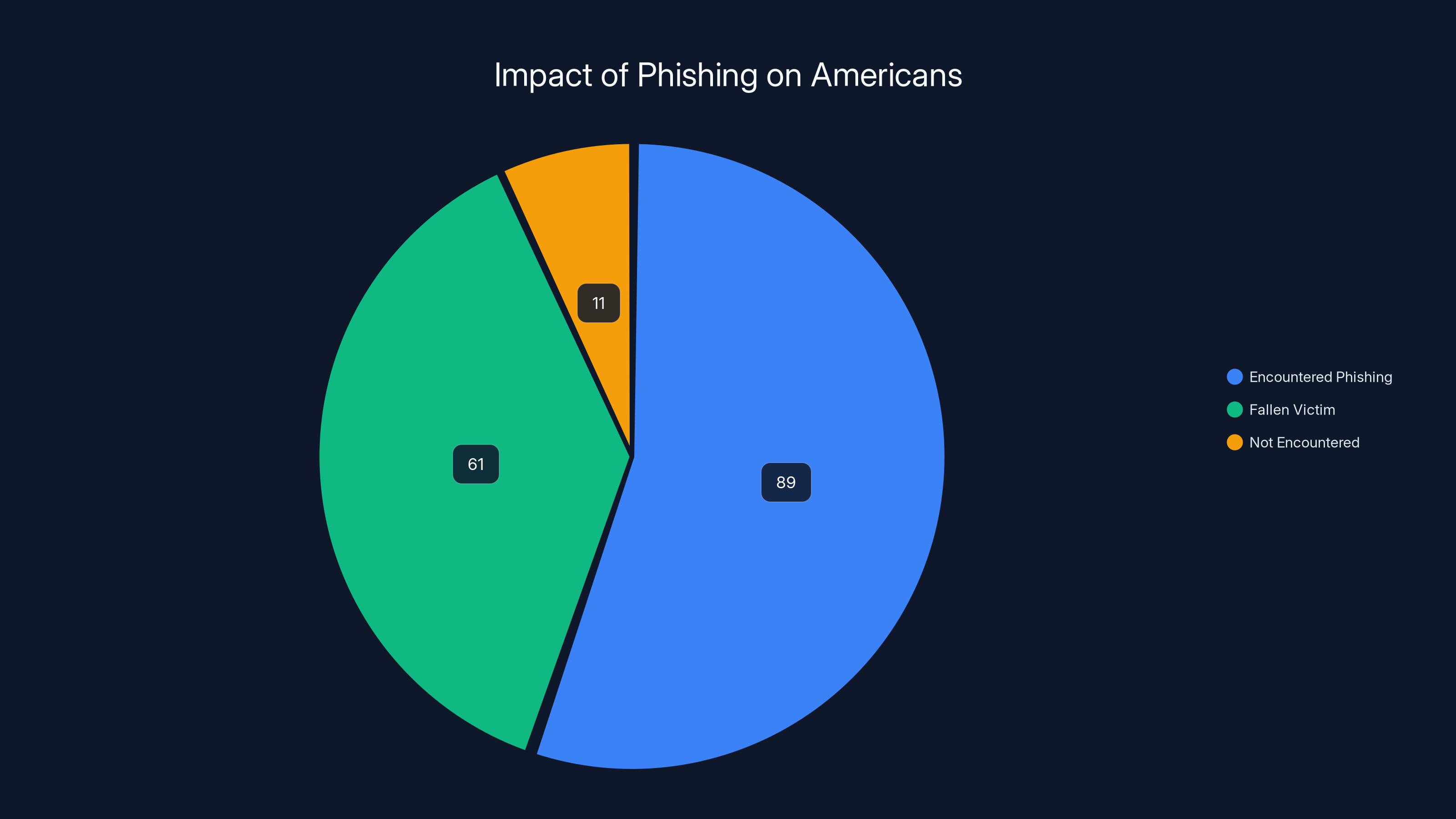
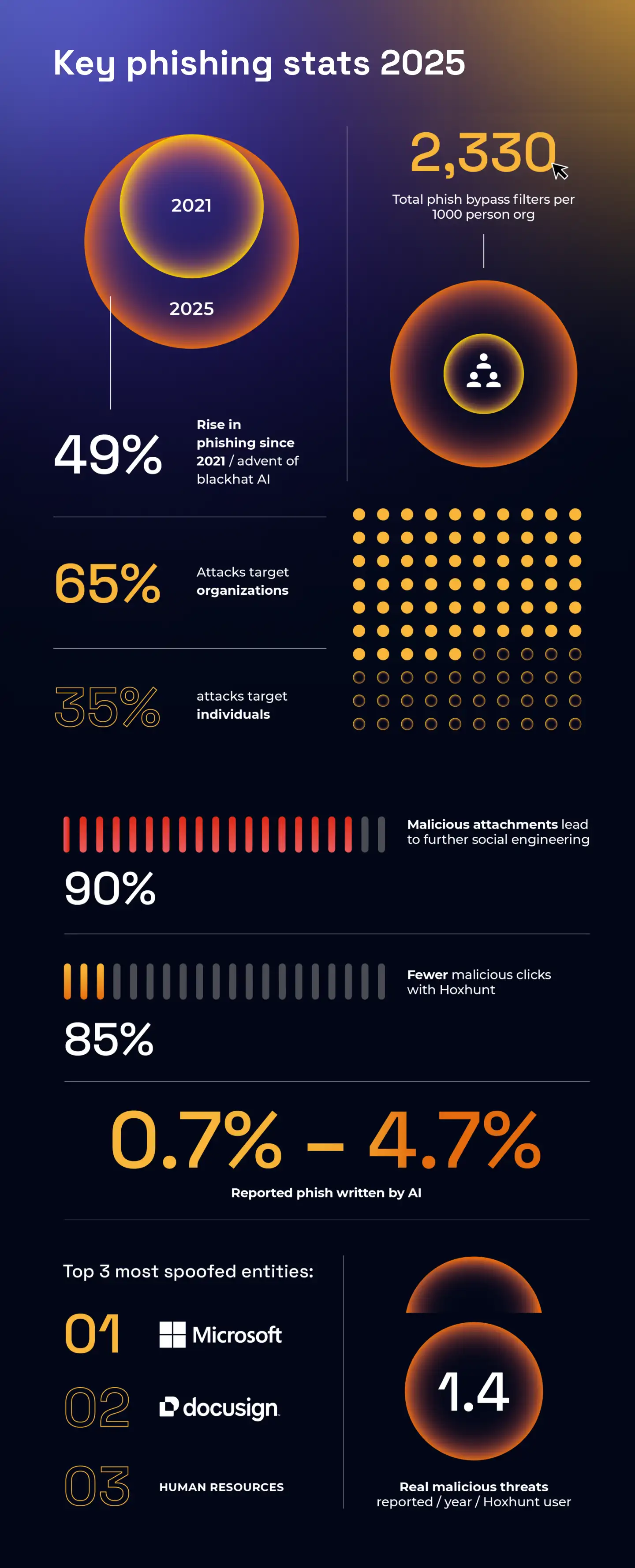
Estimated data shows that 89% of Americans have encountered phishing, with 61% falling victim. This highlights the critical need for effective phishing protection solutions.
The Economics of Phishing Prevention
Let's do some simple math to understand the economic impact of phishing protection.
Suppose you're a business with 1,000 employees. Based on industry statistics, roughly 1-3% of employees fall for phishing attacks each year. Let's say 2%, or 20 employees.
Each successful phishing attack costs your business money:
- Initial investigation and response: $2,000-5,000 per incident (IT time, forensics, etc.)
- Password resets and account recovery: $500-1,000 per incident
- Potential data exposure or ransomware: Could be tens of thousands to millions
- Regulatory fines (depending on industry): Could be substantial
- Reputation damage: Hard to quantify but significant
Let's use conservative numbers: $5,000 per incident for investigation and remediation.
20 incidents ×
Now, suppose 1 Password's phishing protection prevents 30% of these attacks (which is a conservative estimate; for URL-based phishing, the prevention rate could be much higher).
6 prevented incidents ×
But here's the thing: preventing a breach that could have exposed customer data or installed ransomware is worth far more than $30,000. You're not just preventing the direct costs of response. You're preventing the indirect costs of business disruption, potential lawsuits, and regulatory action.
For enterprises using 1 Password for Business, the ROI on phishing protection is substantial.
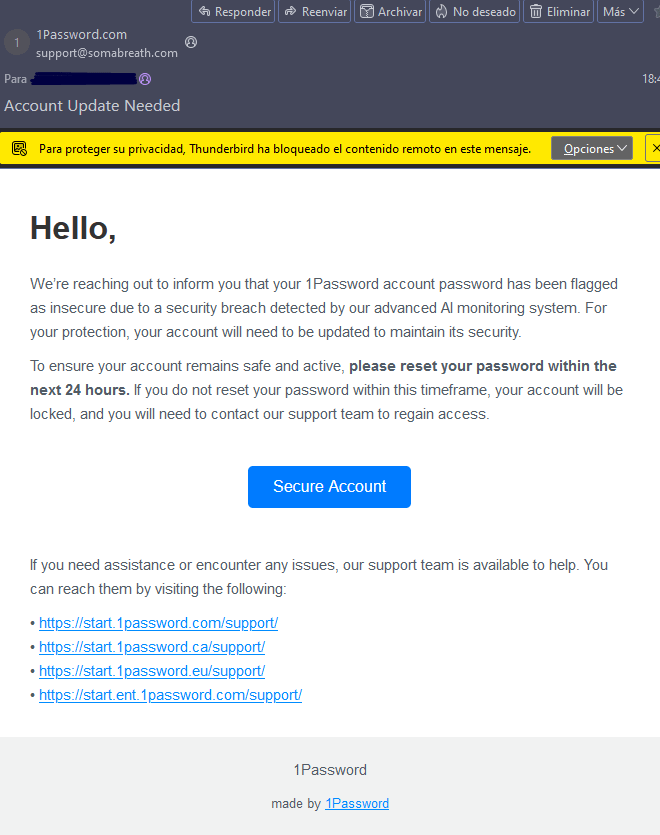
The Human Element: Why Technology Alone Isn't Enough
Here's something important: technology can prevent many phishing attacks, but it can't prevent all of them. And it certainly can't replace human judgment and awareness.
Consider a sophisticated spear-phishing attack. A hacker has researched their target extensively. They know the names of colleagues, projects they're working on, communication styles. They craft an email that seems to come from a trusted person (CEO, trusted partner, etc.). They include details that make it seem legitimate.
You click the link. But 1 Password's phishing protection won't help here, because either:
- The attacker used the legitimate website domain (in some attacks, they compromise a real account and send messages from it)
- The attack doesn't involve credential entry at all (it's a malware download or a scam)
- The URL looks legitimate enough that you've actually visited that website before, so the URL matches your vault
In these scenarios, you're left relying on human judgment. You need to notice something off about the message. You need to verify the sender. You need to be cautious about clicking links you weren't expecting.
This is why security awareness training is still important. It's why companies invest in employee education. It's why security leaders spend time teaching people to recognize phishing attacks.
The best security is layered. Technical controls like 1 Password's phishing protection catch many attacks. But human awareness catches the ones that slip through the cracks.
For organizations, this means combining:
- Technical controls (phishing protection, email filtering, browser security, etc.)
- Security awareness training (teaching employees to recognize attacks)
- Incident response procedures (knowing what to do if someone is compromised)
- Regular security assessments (testing your defenses with simulated attacks)
When all these elements work together, you get defense in depth. You're not relying on any single layer. You're resilient to attacks even when some layers fail.
Looking Ahead: The Future of Phishing Protection
Where is this heading? What should we expect from password managers and phishing protection in the next few years?
There are a few trends worth watching.
First, machine learning and behavioral analysis will likely become more prevalent. Instead of just comparing URLs, password managers might analyze the entire context of a login attempt: the time of day you usually log in, the location, the device you're using, even the typing speed and patterns. Unusual patterns could trigger warnings.
Second, integration with email and messaging apps. Password managers have traditionally worked at the browser level. But increasingly, they might integrate with email clients to warn you about phishing emails before you even click them. Imagine 1 Password analyzing your incoming emails and flagging suspicious ones.
Third, federated learning and anonymous threat sharing. Your password manager could learn from threats detected on other users' accounts (while preserving privacy) and use that knowledge to protect your accounts. If millions of 1 Password users are being targeted by a specific phishing attack, everyone could benefit from collective knowledge.
Fourth, stronger authentication. Phishing works because passwords are the currency of authentication. As multi-factor authentication, passkeys, and biometric authentication become more widespread, phishing attacks will become less effective. Password managers will evolve to handle these new authentication methods.
Fifth, AI-powered phishing detection. Language models could analyze emails and websites to detect sophisticated phishing attacks that humans would miss. This is still in early stages, but it's coming.
The overall trajectory is toward smarter, more proactive, more integrated security. Password managers are becoming the platform where all of this happens.
TL; DR
-
1 Password's new phishing protection compares the URL you're visiting with URLs stored in your vault, preventing autofill on spoofed sites. If you manually paste credentials into a mismatched URL, a warning appears alerting you to the potential phishing attack.
-
URL spoofing is one of the most common and effective phishing techniques. Hackers use typo-squatting (registering domains like gogle.com instead of google.com) to trick users into entering credentials on fake sites.
-
The feature is enabled by default across Individual, Family, and Business plans. Enterprise administrators can configure it granularly for different user groups in the 1 Password admin console.
-
For businesses, phishing protection could prevent thousands to millions in losses annually. A single compromised credential can lead to data breaches, ransomware, or financial loss. Preventing phishing prevents most of these attacks.
-
This is part of a larger trend: password managers are evolving into security platforms. They're no longer just vaults. They're becoming active threat detection and prevention systems.
-
Technology isn't enough alone: pair 1 Password's phishing protection with security awareness training, strong authentication practices, and incident response procedures for comprehensive defense.
FAQ
What exactly is 1 Password's phishing protection feature?
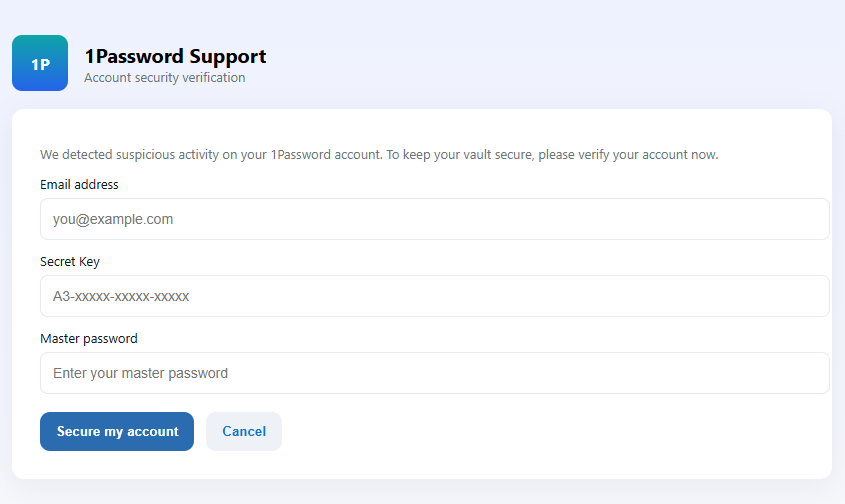
1 Password's phishing protection is a built-in security tool that compares the URL of the website you're currently visiting with the URL stored in your 1 Password vault for that account. If the URLs don't match, the password autofill feature won't activate, and if you try to manually paste your credentials, a warning will appear telling you that the URL might not be legitimate. This prevents you from accidentally entering your credentials on a fake, spoofed website.
How does URL spoofing work and why is it so effective?
URL spoofing, also called typo-squatting, involves registering domain names that are nearly identical to legitimate sites. Hackers might drop a single letter (gogle.com instead of google.com), use a similar-looking character (1 instead of l), or add extra characters. Because human brains don't carefully parse every character in a URL, these subtle differences are easily missed, especially when you're in a hurry or distracted. Hackers exploit this by sending phishing emails with urgency to bypass your careful analysis, making you more likely to click the link without verifying the URL.
Is 1 Password's phishing protection available on all plans?
Yes, the phishing protection feature is available on Individual, Family, and Business plans. For Individual and Family users, the feature is enabled by default and works automatically. For Business users, administrators have more control and can enable the feature for specific users or departments through the Authentication Policies in the 1 Password admin console.
What if the phishing protection blocks me from accessing a legitimate website?
False positives can occur in specific scenarios, such as when accessing a website from a different subdomain than the one where you saved the password, or when URL variations (like adding www or https) aren't recognized. If this happens, you can manually enter your password instead of relying on autofill. For frequent issues, contact 1 Password support or, if you're an administrator, consider adjusting the policy for specific users or departments.
Does 1 Password's phishing protection work offline?
Yes, the phishing protection works entirely offline. It doesn't require internet connectivity or access to external phishing databases. The comparison happens locally on your device, making it fast and privacy-respecting. You're not sending URLs to 1 Password servers for analysis.
How effective is URL-based phishing protection at preventing all phishing attacks?
While URL-based phishing protection is excellent at catching typo-squatting and spoofed domain attacks, it doesn't prevent all types of phishing attacks. It won't catch spear-phishing emails that use legitimate domains (perhaps from a compromised account), phishing attacks that don't involve credential entry (like malware distribution), or social engineering attacks. For comprehensive protection, combine this feature with security awareness training, multi-factor authentication, and email filtering.
What should I do if 1 Password shows me a phishing warning?
Stop immediately. Don't try to work around the warning. Close the browser tab and navigate to the legitimate website through a bookmark, direct URL entry, or by opening a fresh browser tab and typing the correct address. If you're in a work environment and receive a suspicious email, report it to your IT department. Your instinct to trust 1 Password's warning is correct.
Can enterprise administrators customize this feature?
Yes. In the 1 Password admin console, administrators can enable or disable enhanced phishing protection for different users, departments, or the entire organization. This flexibility allows businesses to balance security with usability based on their specific needs and risk profiles.
How does 1 Password's URL comparison feature differ from other anti-phishing tools?
Most anti-phishing tools work by comparing websites against databases of known phishing sites or using real-time lookups. 1 Password's approach is different: it compares the current URL against URLs stored in your personal vault. This means it catches unknown, newly created phishing sites as long as they target accounts you have saved, without requiring external connectivity or relying on threat databases. It's more proactive and privacy-respecting than many alternatives.
Will this feature protect me from all types of phishing attacks?
No, URL-based phishing protection specifically targets typo-squatting and spoofed domains. It won't protect against phishing attacks that use legitimate domains, attachment-based malware, social engineering without credential entry, or sophisticated spear-phishing attacks. For comprehensive protection, layer this feature with other security practices: strong, unique passwords for every account, multi-factor authentication, email security tools, and security awareness training.
What's the long-term vision for password manager security?
Password managers are evolving beyond password storage into comprehensive security platforms. Future developments likely include machine learning-based behavioral analysis, integration with email and messaging apps, federated threat sharing (learning from attacks on other users while protecting privacy), support for stronger authentication methods like passkeys and biometrics, and AI-powered phishing detection. 1 Password's URL detection is part of this larger trend toward more proactive, intelligent security systems.
Conclusion: A Meaningful Step Forward in Credential Security
1 Password's announcement of built-in phishing protection represents a meaningful evolution in how password managers approach security. We've moved past the era where a password manager was simply a convenient vault for storing credentials. Now these tools are becoming active defenders against the most common attack vectors.
The elegance of this particular implementation is worth emphasizing. Instead of relying on constantly updated threat databases or external threat intelligence services, 1 Password uses what it already knows: the URLs where you've saved passwords. By comparing the current URL against these known URLs, it catches URL-based phishing attacks without requiring any external connectivity or real-time data feeds.
For individual users, this means one less thing to worry about. Your password manager is now looking out for you, silently preventing one of the most common phishing attack techniques. For enterprises, this means fewer compromised credentials, fewer incidents to investigate, and potentially millions in prevented losses.
But let's be clear: this feature isn't a silver bullet. It won't prevent every phishing attack. It won't protect you if you fall for a sophisticated spear-phishing email or if a hacker compromises a legitimate account and uses it to send messages. It won't help if the attack doesn't involve entering credentials on a website.
What it will do is catch the common attacks. The mass-market phishing campaigns. The typo-squatting attempts. The cookie-cutter attacks that target millions of people every day. And for most people, that's where the real danger lies.
Combine this feature with security awareness (understanding how phishing works and what to look for), strong authentication practices (using unique passwords and multi-factor authentication), and good security hygiene (keeping software updated, being cautious about what you click), and you've built a comprehensive defense.
1 Password's move signals where the industry is heading. Other password managers will likely follow with similar features. Browser makers will enhance their built-in protections. Email providers will add phishing detection. Gradually, the entire digital ecosystem is becoming more hostile to phishing attacks.
That's progress worth celebrating.
The fact that this protection comes as a default feature on plans that cost $9/month (for family plans) or are available at various price points means that millions of people suddenly have access to enterprise-grade phishing protection. That's democratizing security in a meaningful way.
If you use 1 Password, you don't need to do anything. The protection is already working. If you're considering a password manager, 1 Password's built-in phishing protection is one more reason to make it your choice. And if you're an enterprise security leader evaluating password managers, this feature should be on your checklist.
In a world where 89% of people have encountered phishing scams and 61% have fallen victim, tools that make phishing attacks less likely to succeed aren't just nice-to-have. They're essential.
Key Takeaways
- 1Password's phishing protection compares visited URLs against stored credentials to prevent autofill on spoofed sites, blocking the most common phishing attack vector
- URL spoofing through typo-squatting accounts for nearly 30% of phishing attacks, making local URL comparison an effective and privacy-respecting detection method
- The feature is enabled by default on Individual, Family, and Business plans with granular configuration options for enterprise administrators through Authentication Policies
- Phishing attacks cost businesses an average of $3.7 million annually, making URL detection that prevents 30% of incidents worth hundreds of thousands in ROI
- Effective phishing defense requires layering multiple controls: technical protection (1Password), authentication (MFA), awareness training, and incident response procedures
Related Articles
- 1Password's New Phishing Prevention Feature [2025]
- LastPass Phishing Scam: How to Spot Fake Support Messages [2025]
- Instagram Password Reset Incident: What Really Happened [2025]
- PcComponentes Data Breach Denial: What Really Happened [2025]
- WordPress Plugin Security Flaw Affects 50,000 Sites: Complete Protection Guide [2025]
- WordPress Plugin Security Flaw: Complete Guide to Staying Safe [2025]
![1Password Phishing Protection: Built-In URL Detection Saves Millions [2025]](https://tryrunable.com/blog/1password-phishing-protection-built-in-url-detection-saves-m/image-1-1769093187492.jpg)



