Bridge Pay Ransomware Attack: What Happened and How to Protect Your Business [2025]
It was late Friday when the call came in. Payment terminals stopped responding. APIs went dark. Suddenly, thousands of merchants across America couldn't process credit cards.
Bridge Pay, one of the nation's major payment gateways, had been hit with a ransomware attack so severe that it forced the entire company to take systems offline. No transactions. No virtual terminals. Nothing. In an economy where brick-and-mortar retail depends entirely on electronic payments, this wasn't just an inconvenience. It was a business disaster.
What makes this attack particularly significant isn't just the scale—it's what it reveals about how fragile our payment infrastructure actually is. When a single company goes down, merchants nationwide are forced to turn customers away or resort to pen-and-paper transactions from the 1990s.
Let me walk you through exactly what happened, why it matters, and what you need to do to protect your business from similar attacks.
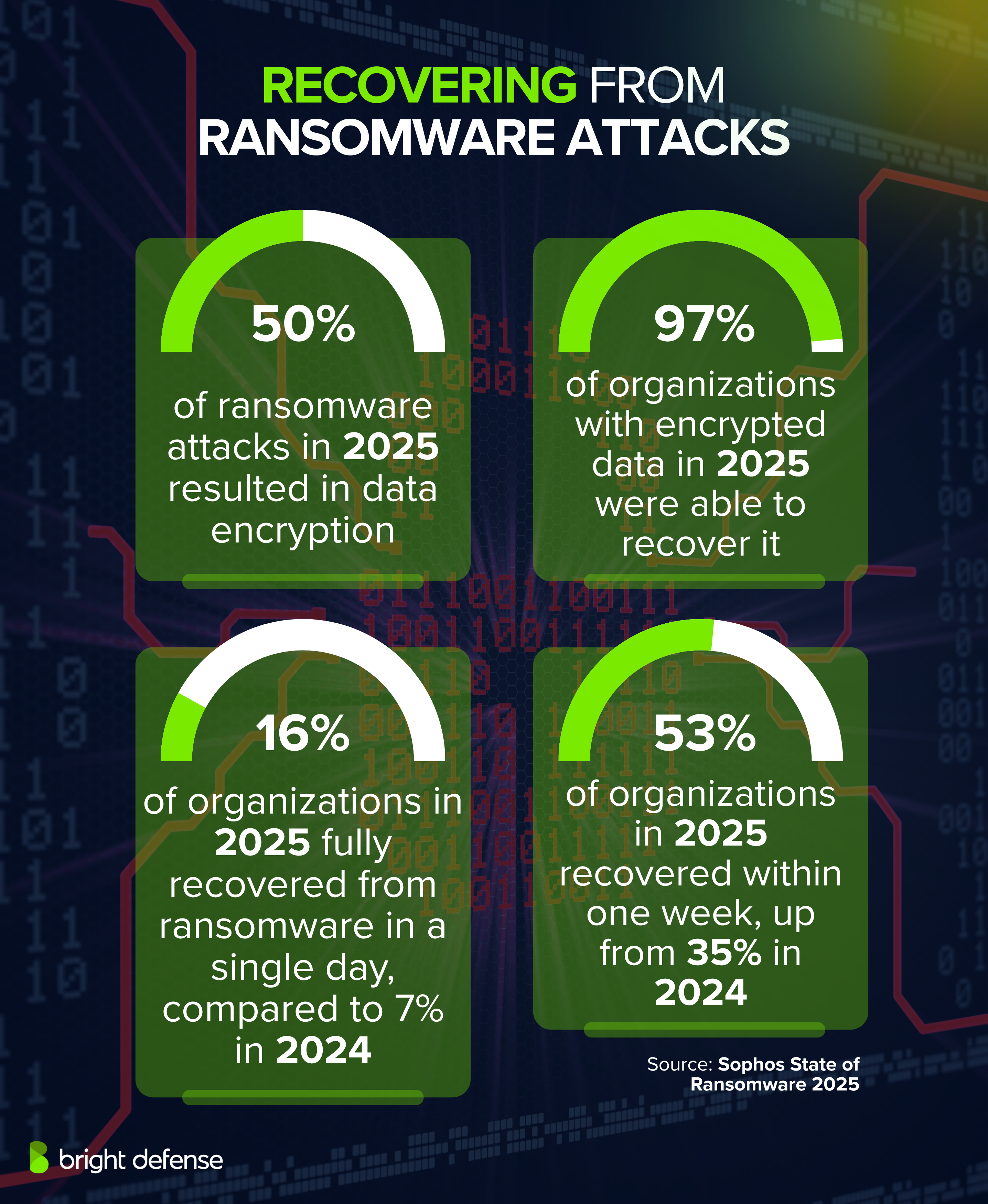
TL; DR
- The Attack: Bridge Pay suffered a ransomware attack that knocked multiple services offline including their payment gateway API, virtual terminals, and reporting systems.
- Who Was Affected: Over 70 US banks and credit unions, plus thousands of merchants nationwide were disrupted.
- The Response: The US Secret Service forensic team was brought in alongside specialized recovery teams to investigate and remediate.
- Data Status: Initial findings indicated no payment card data was compromised, though investigation was ongoing.
- Real Impact: Merchants were forced to accept cash only, and multiple payment processing services went dark simultaneously.
- Bottom Line: This incident demonstrates why payment security redundancy and backup systems are no longer optional for any business accepting cards.
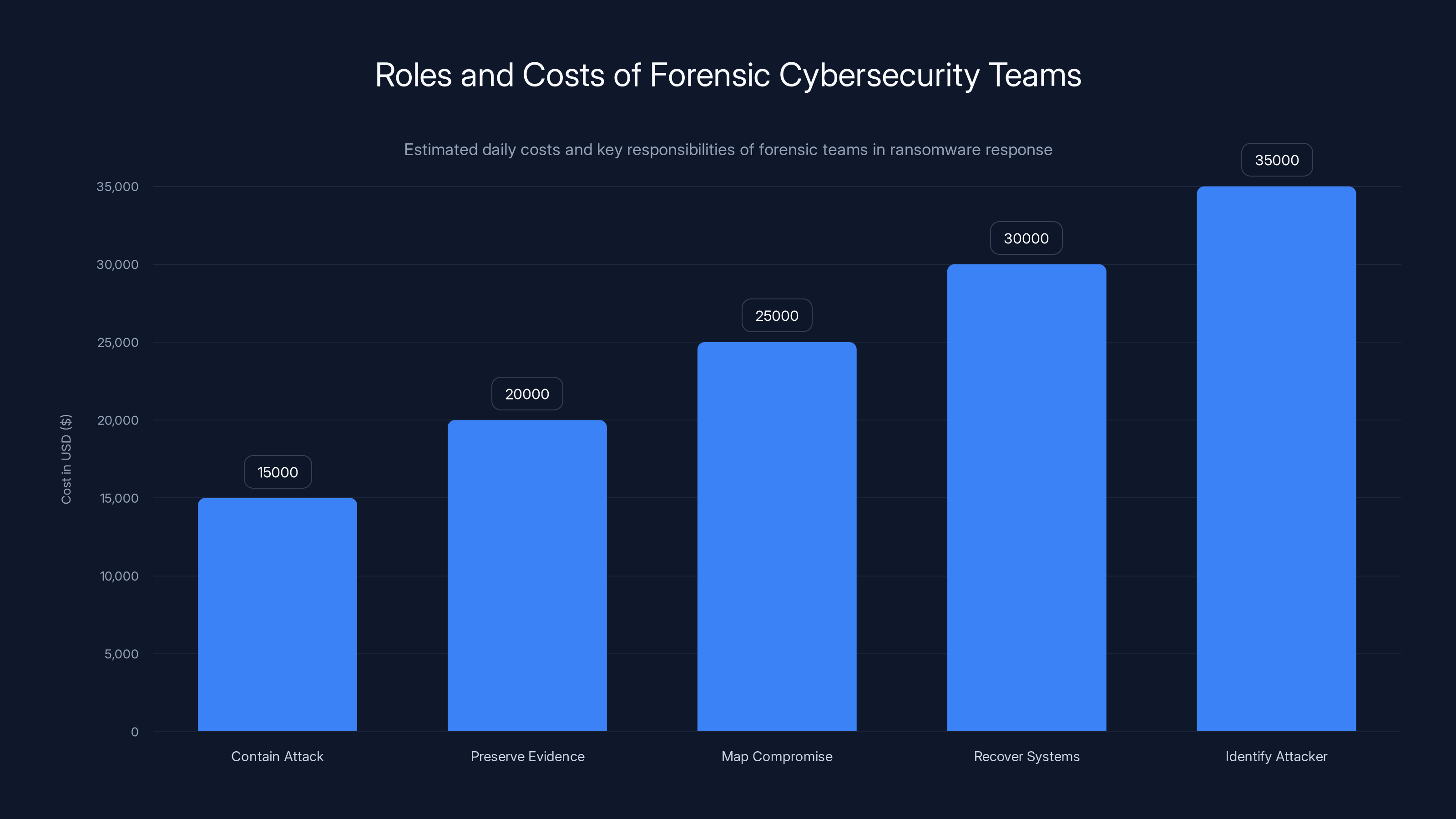
Forensic cybersecurity teams play critical roles in ransomware response, with costs ranging from
What Exactly Is Bridge Pay?
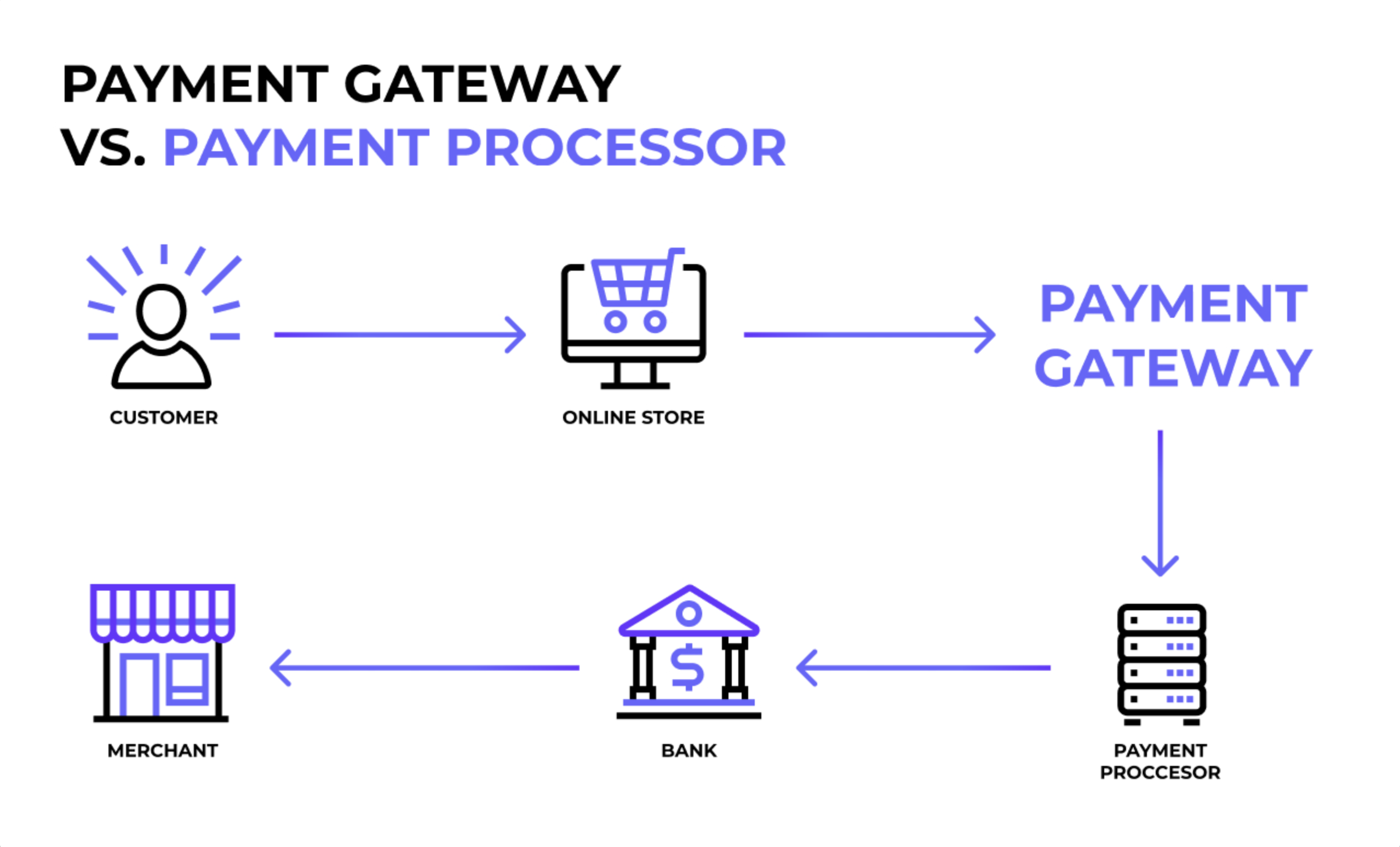
Before you can understand why this attack was so destructive, you need to know what Bridge Pay actually does. It's not a bank. It's not a credit card company. Bridge Pay is a payment processor and gateway that sits in the middle between merchants and their customers' banks.
Think of it like this. When you swipe your card at a coffee shop, that transaction doesn't go directly to your bank. It flows through multiple systems. Bridge Pay handles the technical infrastructure that makes that possible. They provide the APIs (application programming interfaces) that let point-of-sale systems talk to the banking network. They run the virtual terminals that let online businesses process payments. They manage the reporting dashboards that show merchants what they've sold.
If Bridge Pay goes down, transactions can't flow. It's like cutting a major artery in the payment system.
The company serves small businesses, mid-market enterprises, and financial institutions. They're not a household name like Stripe or Square, but they're significant enough that when they go dark, it affects millions of dollars in daily transactions.
Timeline of the Attack: When Everything Fell Apart
Ransomware attacks don't happen overnight. They typically follow a pattern, and the Bridge Pay incident is no exception.
The Initial Compromise (Unknown Date)
Ransomware actors typically spend weeks or months inside a victim's network before they actually deploy the encryption that makes the attack visible. During this "dwell time," they're mapping the network, identifying valuable data, and planning the most damaging approach. With Bridge Pay, this phase likely happened without anyone knowing.
Friday Afternoon: The Encryption Begins
Late Friday, Bridge Pay's systems started going dark. The ransomware hit multiple services simultaneously, which suggests the attackers had deep access to critical infrastructure. Within hours, payment gateway APIs were unreachable. Virtual terminals locked up. The reporting systems that merchants use to track sales went offline. This wasn't a partial outage—it was a comprehensive takedown.
The Notification
Bridge Pay posted to their incident response page that the outage was the result of a ransomware attack. They didn't minimize it or call it a "technical issue." They were direct about what happened. This transparency actually matters—it tells customers that leadership knows exactly what hit them.
Saturday: Forensic Teams Deployed
Within 24 hours, Bridge Pay had engaged specialized forensic recovery teams. More importantly, they brought in the US Secret Service. When federal law enforcement is involved, you know you're not dealing with run-of-the-mill cybercriminals. The Secret Service has a dedicated electronic crimes task force that handles major financial crimes, and their involvement signals that this attack had serious implications for the financial system.
Sunday Update: Investigation Ongoing
On Sunday afternoon, Bridge Pay posted an update saying the investigation was still ongoing. Remediation efforts were in progress. They hadn't fully recovered yet, but they were making progress.
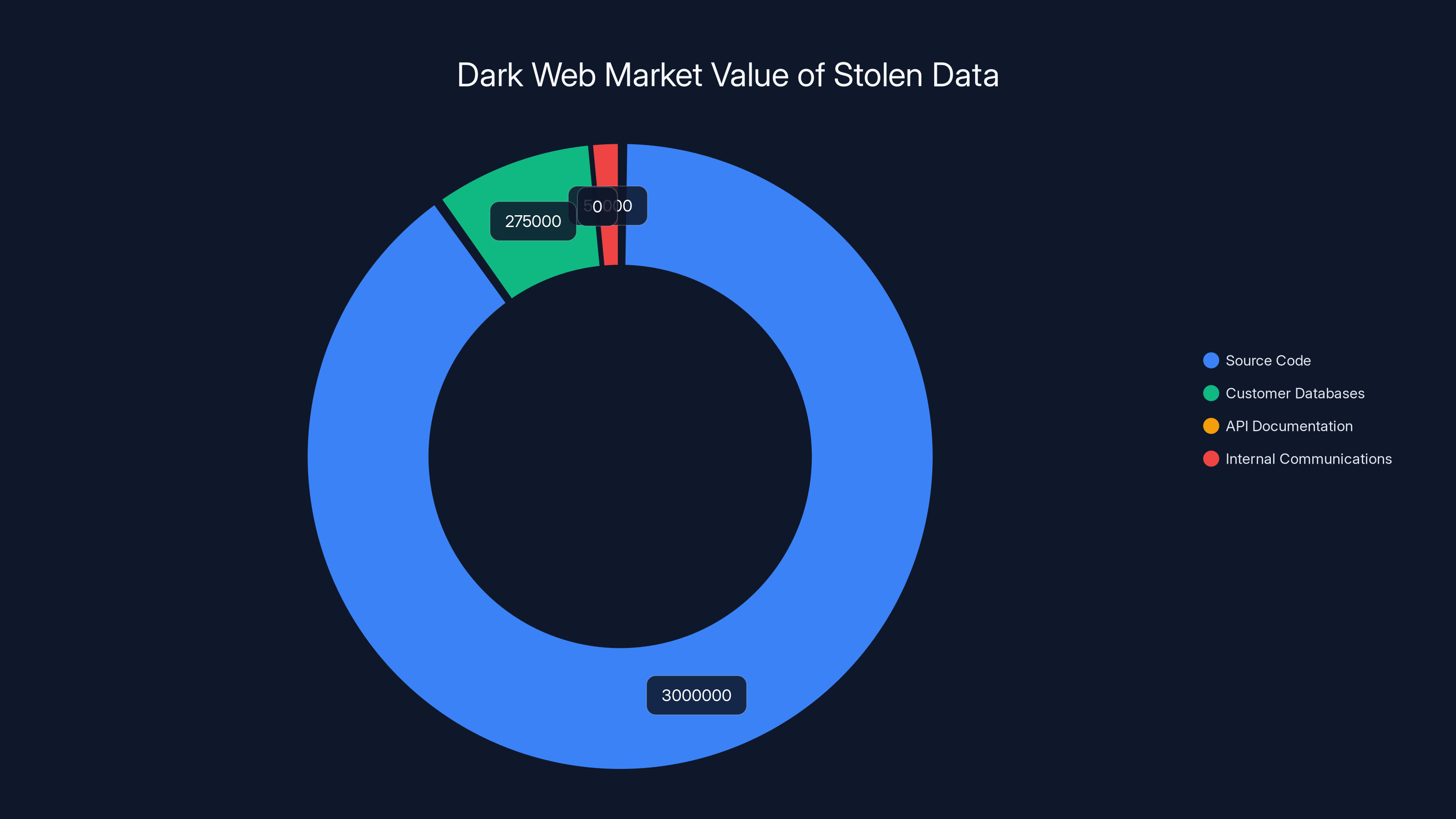
Source code is the most valuable on the dark web, potentially fetching up to $5 million. Customer databases also hold significant value, while API documentation is often used internally rather than sold. Estimated data based on typical dark web pricing.
The Ransomware Mechanics: How These Attacks Actually Work
Understanding how ransomware operates helps you grasp why Bridge Pay's situation was so serious.
Ransomware is fundamentally a two-part extortion scheme. The first part is encryption. Attackers gain access to your systems (often through phishing emails, unpatched vulnerabilities, or compromised credentials), then they deploy encryption malware that scrambles all your data. Your files become unreadable. Your systems lock up. Without the decryption key, everything is inaccessible.
The second part is the threat. Attackers tell you: "Pay us in Bitcoin, and we'll give you the key to decrypt your files." Usually, they demand six figures or more.
But here's where it gets worse. Modern ransomware gangs also exfiltrate data before they encrypt it. They copy sensitive information—customer data, financial records, source code, employee information—to their own servers. Then they threaten to sell it on the dark web or release it publicly if you don't pay. This creates two reasons to pay: recover your systems, and keep your data private.
With Bridge Pay, the attackers had potential access to payment processing information. Even though Bridge Pay said no payment card data was compromised, the threat of exposure was real. Attackers could potentially access merchant account information, API keys, transaction logs, or other sensitive infrastructure data.
The Bitcoin Demand
Ransomware gangs typically demand payment in Bitcoin because it's pseudonymous. A Bitcoin transaction leaves a record on the blockchain, but it doesn't inherently identify who made the transaction. Attackers can move the Bitcoin through mixing services or cryptocurrency exchanges to obscure its origin. Law enforcement can sometimes trace it, but it's harder than tracing a wire transfer.
The Negotiation
Most organizations don't pay the full ransom. They negotiate. The criminals know this. They typically demand an amount that sounds outrageous (sometimes $20 million or more), fully expecting the victim to counter with a lower offer. It's like a twisted haggling session, except both parties know that federal law enforcement is investigating and that payment might trigger sanctions.
The Attacker: Who's Behind the Bridge Pay Attack?
Here's the frustrating part: at the time of the incident, Bridge Pay and law enforcement hadn't publicly identified who was responsible.
Ransomware attacks are typically attributed based on several factors. First, the specific ransomware variant used. Some gangs have signatures—they use particular code patterns, negotiate in specific ways, or leave custom ransom notes. Second, the timing and targeting of the attack. Some gangs focus on specific industries. Third, the ransom amount demanded and the negotiation tactics used.
Without a confirmed attribution, we're left with educated guesses. Major US payment processing companies are prime targets for international cybercriminal gangs, particularly those based in Russia, Eastern Europe, and parts of Asia where law enforcement is less aggressive about pursuing cybercrime.
What we do know: the attackers had sophisticated access. They didn't just get into a single merchant account. They compromised Bridge Pay's internal infrastructure deeply enough to take down multiple services simultaneously. This requires either:
- Excellent reconnaissance and planning
- Stolen credentials from a privileged employee or contractor
- Exploitation of a critical unpatched vulnerability
- Supply chain compromise (attackers getting in through a vendor or partner)
Attacks of this sophistication usually come from organized gangs, not random script kiddies. These are professionals.
Impact on Merchants: The Ripple Effect
Let's talk about what actually happened to the people trying to run businesses.
When Bridge Pay went down, it didn't just affect Bridge Pay's direct customers. It cascaded. The company provides services to over 70 banks and credit unions across the US. Those institutions then serve thousands of merchants. When you do the math, we're talking about hundreds of thousands of points of sale that suddenly couldn't process cards.
The Services That Went Dark
Multiple critical payment services became unavailable:
- Bridge Comm Gateway API: This is what e-commerce platforms and point-of-sale systems use to actually process transactions. No API, no online sales.
- Pay Guardian Cloud API: Another critical processing interface. Down as well.
- My Bridge Pay Virtual Terminal: Small businesses use this to process card payments through a web browser. Restaurants, retail shops, service providers. All unable to accept cards.
- Reporting and Analytics: Merchants couldn't see transaction history, reconcile payments, or track their daily sales.
When a payment processor goes down, merchants have two options: they can try to use a backup processor (if they have one set up), or they can fall back to cash and check. Most don't have a backup.
The Real-World Consequences
Reports from Bleeping Computer indicated that merchants nationwide were forced to accept cash only. Think about what that means:
- A restaurant can't process credit cards, so customers walk out or leave bad reviews about the cash-only inconvenience.
- An online retailer's sales go to zero for days.
- A beauty salon can't process appointments because their POS system is dead.
- A gas station can only serve customers who have cash in their wallet.
For a modern business, this is catastrophic. The average small business operates on thin margins. A 48-hour or 72-hour outage could mean tens of thousands in lost revenue. Some businesses never recover from incidents like this.
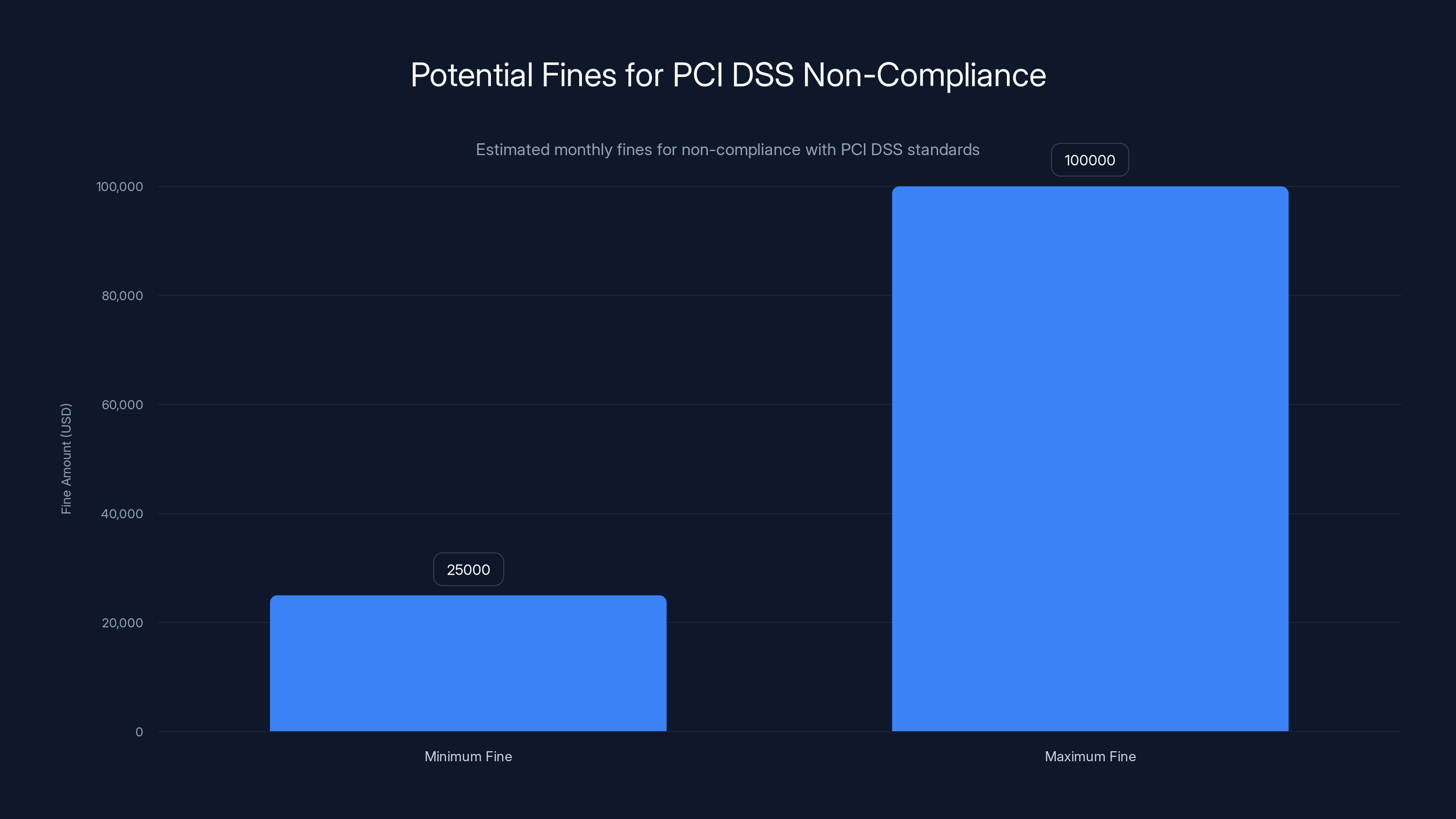
Payment processors face fines ranging from
Initial Investigation: The Forensic Response
When the ransomware hit, Bridge Pay immediately brought in specialized teams. This tells you something about how seriously they took the situation.
The Forensic Teams
Forensic cybersecurity teams are specialized incident responders. They're not the company's regular IT staff. They're external experts who know how to:
- Contain an active attack (stop the bleeding)
- Preserve evidence (don't destroy clues about how attackers got in)
- Map the scope of compromise (understand how far the attackers got)
- Recover systems safely (rebuild without re-infecting)
- Identify the attacker (gather data for law enforcement)
These teams typically cost
The US Secret Service Involvement
The US Secret Service has a division called the Financial Crimes Division. They investigate financial crime, counterfeiting, and electronic crimes. Their presence in the Bridge Pay investigation tells you that federal law enforcement considered this a significant threat to the financial system.
What the Secret Service brings:
- Law enforcement authority to compel cooperation from witnesses and other companies
- Access to intelligence databases about known threat actors
- Coordination with international law enforcement agencies (Interpol, etc.)
- Authority to trace Bitcoin transactions and cryptocurrencies
- Expertise in negotiating with ransomware gangs (if that becomes necessary)
The Initial Findings
Bridge Pay's initial forensic findings were encouraging in one way: no evidence of payment card data compromise. This is crucial because if customer payment card data had been stolen, the regulatory and liability implications would be catastrophic.
However, the investigation was ongoing. Forensics take time. Attackers are sophisticated at covering their tracks. It took weeks or months of analysis to understand the full scope of what was accessed.
Data Exfiltration: The Hidden Threat
Even though Bridge Pay said payment card data wasn't compromised, there's a darker possibility that usually gets glossed over in these announcements.
Modern ransomware gangs operate what's called a "double extortion" model. They don't just encrypt your data. They also copy sensitive information to their own servers. Then they threaten to:
- Sell it to other criminals
- Release it to competitors
- Post it on the dark web
- Sell it to journalists to embarrass the company
For Bridge Pay, the potential data exfiltration could include:
- Merchant account information: Details about which banks and businesses use Bridge Pay's services
- API keys and credentials: The actual authentication tokens that developers use to integrate with Bridge Pay's systems
- Transaction metadata: While not the actual card numbers, transaction data could reveal patterns about which merchants are most valuable
- Internal communications: Emails that might reveal business relationships, negotiations, or vulnerabilities in other systems
- Source code: The actual software that runs Bridge Pay's systems (extremely valuable to competitors or attackers)
- Customer databases: Contact information for merchants and bank officials
Any of these could be catastrophic if released. Source code is particularly sensitive because it might reveal security weaknesses that other payment processors could exploit.
The threat of data release is often what actually forces companies to consider paying the ransom. Encryption is recoverable through backups or paying for decryption. But if your proprietary information and customer data are on the dark web permanently, that damage is irreversible.
The Broader Ecosystem Impact: Banks and Credit Unions
Here's what makes this attack significant beyond just Bridge Pay: it revealed how interconnected the payment system is, and how that interconnection creates systemic risk.
Over 70 banks and credit unions were affected. That's not a coincidence. Bridge Pay provides backend processing infrastructure for financial institutions. When Bridge Pay goes down, those banks lose the ability to process certain types of transactions.
How Banks Depend on Payment Processors
Most banks don't actually run their own payment processing infrastructure for all transaction types. It's too expensive and too specialized. Instead, they contract with payment processors like Bridge Pay to handle:
- Card processing
- ACH transfers (bank-to-bank transfers)
- Wire transfer routing
- Merchant settlement
- Reporting and compliance
When a processor goes down, banks have limited options. They can potentially reroute traffic to backup processors, but that takes time and requires pre-existing agreements.
Systemic Risk
This creates what economists call "systemic risk." If one critical piece of infrastructure fails, it cascades throughout the system. The 2008 financial crisis happened partly because financial institutions were interconnected in ways that nobody fully understood. When Lehman Brothers failed, it triggered failures throughout the financial system.
Payment processing isn't quite at that level of systemic importance, but it's getting there. We've become entirely dependent on electronic payments. If enough payment processors went down simultaneously, it would create a real economic crisis.

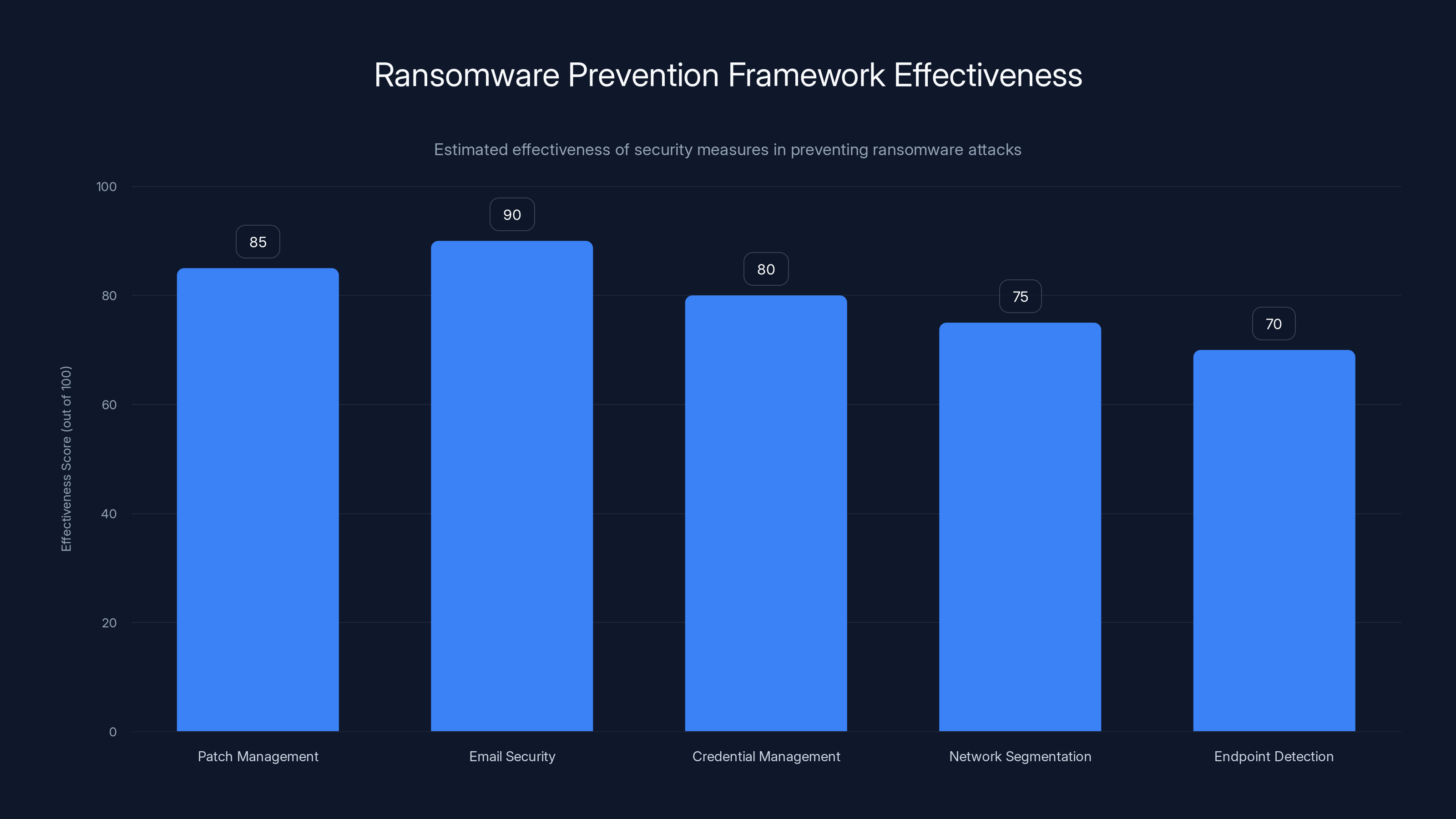
Email security is the most effective measure, with an estimated 90% effectiveness in preventing ransomware attacks, highlighting the importance of filtering and training. Estimated data.
Why Payment Processors Are Prime Targets
Understanding why attackers targeted Bridge Pay in the first place helps you understand your own vulnerability.
Payment processors are ideal targets for ransomware attacks for several reasons:
1. They're Worth a Lot of Money
When you hold the keys to payments, you're holding leverage. A payment processor outage costs merchants thousands or millions of dollars per hour. Companies will pay significant ransoms to restore service quickly. A typical ransomware demand for a payment processor might be
2. They Have Valuable Data
Payment processors see transaction metadata for thousands of merchants. They have API keys, internal credentials, and access patterns. They have details about which financial institutions use their services. All of this is extremely valuable to criminals.
3. They're Under Pressure to Recover Quickly
Unlike a software company that might spend weeks rebuilding after a ransomware attack, a payment processor faces intense pressure to restore service within hours or days. Regulators expect it. Customers demand it. This pressure sometimes leads to rushing recovery and paying ransoms that might not be necessary.
4. They Have Limited Redundancy
While major payment processors have backup systems, a sophisticated attack that compromises core infrastructure can take down multiple redundancies simultaneously. Attackers who spend months inside a network can identify and disable backup systems.
5. They're Internet-Facing
Payment processors need to be accessible to thousands of merchants and banks. This large attack surface makes them vulnerable to initial compromise through phishing, credential theft, or vulnerability exploitation.
Regulatory Response and Compliance Implications
When a payment processor suffers a ransomware attack, it doesn't just face business consequences. It faces regulatory consequences.
PCI DSS Compliance
The Payment Card Industry has strict data security standards called PCI DSS (Payment Card Industry Data Security Standard). These standards require:
- Encryption of payment data
- Network segmentation
- Regular security testing
- Incident response procedures
- Staff training
When a payment processor suffers a breach, regulators investigate whether they met PCI DSS requirements. If not, they face fines of
The Secret Service Investigation
The fact that the US Secret Service was involved means this wasn't just a financial crime. It was potentially a federal crime. Ransomware attacks that involve extortion and potentially cross state lines fall under federal jurisdiction.
The Secret Service investigation would look at:
- How attackers got in (was it due to negligence?)
- What systems were compromised
- Whether the company had reasonable security in place
- Whether they met regulatory requirements
- Evidence for law enforcement prosecution
Banking Regulators
The Office of the Comptroller of the Currency (OCC) and the Federal Reserve also oversee payment processors and the banks that use them. They would want assurance that:
- The outage won't recur
- The company has improved security
- Customer data is truly protected
- Business continuity is ensured
Bridge Pay would likely face regulatory audits, mandatory security improvements, and possibly fines depending on findings.

Recovery Efforts: Getting Systems Back Online
Restoring a payment processor after a ransomware attack is extraordinarily complex. It's not like restoring a regular business system. Payment systems handle real money, so mistakes have immediate consequences.
The Recovery Challenge
When you suffer ransomware, your first instinct might be to restore from backups. That's logical—you have a backup, you restore it, you're back in business. But with payment processors, it's more complicated.
First, you have to ensure the backups themselves weren't infected. Ransomware often sits dormant in backup systems, waiting for you to restore so it can encrypt everything again. Forensic teams have to examine backups to ensure they're clean.
Second, you have to rebuild in a way that maintains data integrity. Payment systems are transactional. If you restore from a backup that's 48 hours old, what happened to the transactions in between? Merchants are owed money for transactions processed during the outage. That money has to be accounted for.
Third, you have to maintain regulatory compliance during recovery. You can't just spin up servers and hope for the best. Every system has to meet PCI DSS requirements, which means encryption, monitoring, logging, and access controls from the moment they come online.
Parallel Processing
Some payment processors use a technique called "parallel processing" during recovery. They bring systems back online in a safe mode where transactions are processed but not fully settled. This allows merchants to accept payments while the company completes full recovery. Then, once systems are fully recovered, all the parallel transactions are reconciled.
The Cost
Recovery from a major ransomware attack can cost tens of millions of dollars. You're paying forensic teams (
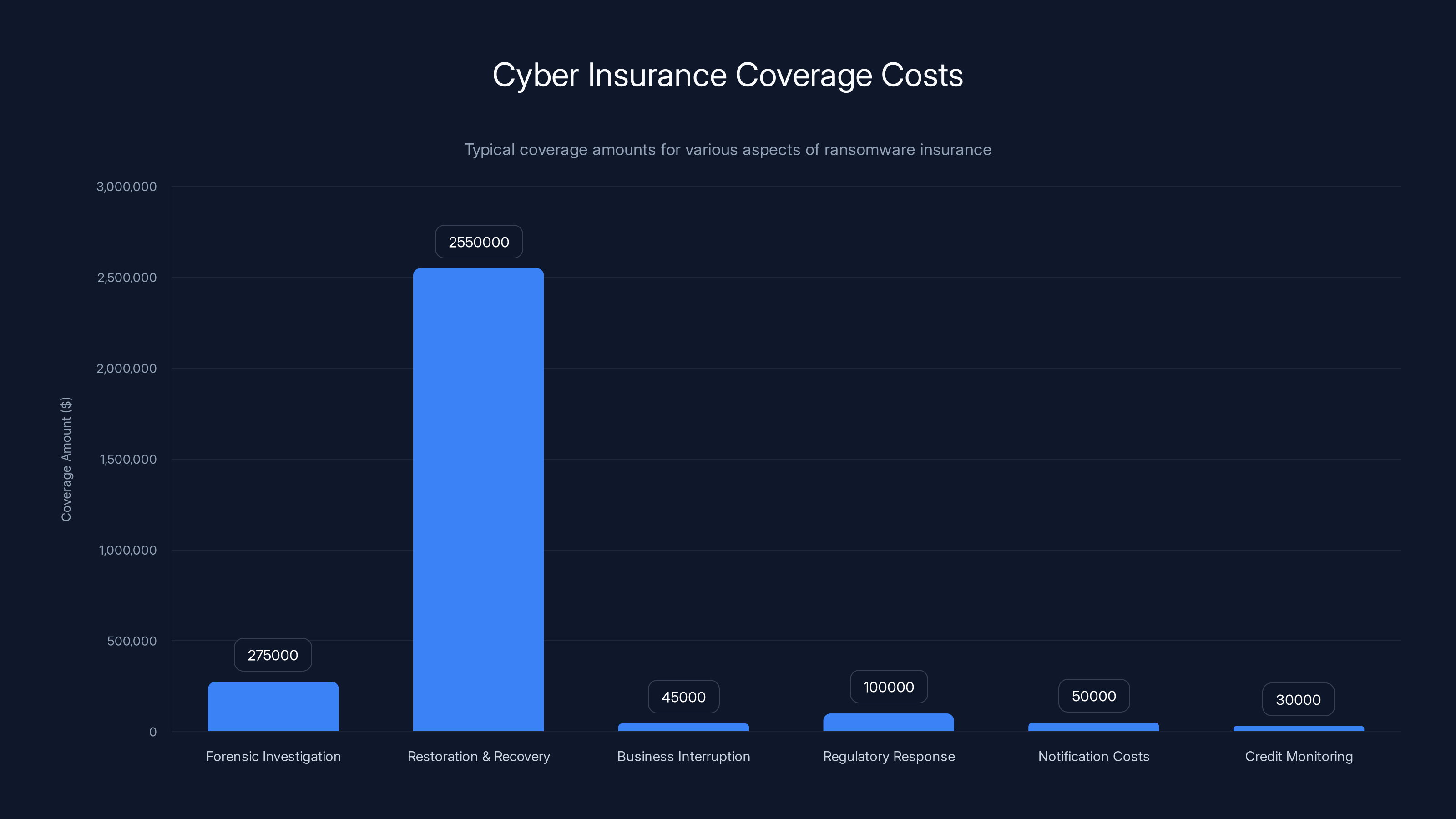
Cyber insurance policies cover various aspects, with restoration and recovery costs being the most significant, ranging from
What Businesses Should Learn From This
The Bridge Pay attack is a masterclass in why you need to take payment security seriously.
Principle 1: Assume Your Processor Will Fail
You cannot depend on any single payment processor to be available 100% of the time. Outages happen. Ransomware happens. Data breaches happen. If your business is solely dependent on one payment gateway, you're gambling with your revenue.
The fix: Have a backup processor configured and tested. You don't need to use it daily, but it needs to be ready to switch to in minutes, not hours. Services like Stripe, Square, or Pay Pal can serve as backups for many businesses. The cost of maintaining a backup processor is trivial compared to the cost of an outage.
Principle 2: Diversify Your Payment Methods
Don't rely entirely on credit card processing. Offer:
- ACH transfers (bank-to-bank payments)
- Pay Pal or digital wallet processing
- Cryptocurrency payments (if appropriate for your business)
- Bank transfers or wire transfers
- Check payments for high-value transactions
When card processing goes down, you still have alternatives.
Principle 3: Understand Your Processor's Security Posture
Before you contract with a payment processor, investigate:
- Are they PCI DSS Level 1 compliant? (Highest level)
- Do they publish a security white paper?
- Have they undergone third-party security audits?
- What's their incident response plan?
- How do they handle data retention?
- What's their backup and disaster recovery strategy?
Don't just assume they're secure. Ask for proof.
Principle 4: Have an Offline Fallback Plan
If all digital payment systems fail, you need a way to continue serving customers. For retail:
- Maintain some cash for making change
- Have a manual payment terminal that doesn't require internet (many still exist)
- Establish procedures for customers to pay later
- Keep detailed records of offline transactions for later processing
For service businesses, you might offer to invoice customers who can't pay immediately.
Principle 5: Monitor Your Processor's Status
Subscribe to your payment processor's status page. Follow their social media. When there's an outage, you want to know immediately, not from customer complaints. Some processors offer webhooks that alert you programmatically when services degrade.
If Bridge Pay had better status communication, merchants might have switched to backup processors faster.

Industry Response and Standards Evolution
The Bridge Pay attack is driving changes in how the payment industry thinks about security and resilience.
Increased Scrutiny of Payment Processors
Regulatory bodies are paying closer attention to payment processor security. The banking regulators' guidance now emphasizes that banks should evaluate their payment processors' security posture regularly. Some regulators are recommending that large financial institutions maintain relationships with multiple payment processors so they have redundancy.
Third-Party Risk Management
The Bridge Pay incident highlighted a critical vulnerability: when you depend on a third party, you're dependent on their security practices. Banks that use Bridge Pay couldn't control Bridge Pay's security decisions. They were victims of someone else's security failure.
This is driving evolution in third-party risk management. Companies now conduct regular security assessments of their vendors, require cyber insurance, and sometimes build in contractual penalties for security failures.
Zero Trust Architecture
Major payment processors are moving toward zero trust architecture, which means:
- Every user and device must be authenticated, even internal employees
- Every transaction is verified, even between internal systems
- Network access is granular and restricted
- Everything is logged and monitored
- There's no "trusted internal network"
Zero trust doesn't prevent ransomware, but it slows attackers down and makes lateral movement harder. It requires constant authentication instead of one-time login and then full access.
Increased Investment in Detection
Payment processors are investing heavily in detection and response capabilities:
- Advanced threat detection that identifies unusual behavior patterns
- Automated response systems that can isolate compromised systems instantly
- Behavioral analytics that detect attackers hiding in the network
- Threat hunting teams that actively search for intruders
The Dark Web and Extortion: What Happened to Stolen Data?
One of the most important questions after a ransomware attack is: what happens to the data?
Ransomware gangs maintain leak sites on the dark web where they advertise stolen data. If Bridge Pay's attackers exfiltrated sensitive information, that data was cataloged, priced, and potentially sold.
The Dark Web Market for Stolen Data
On these leak sites, data is categorized by value:
- Source code: Extremely valuable. Payment processor source code might fetch 5 million depending on sophistication.
- Customer databases: Credit unions' customer lists are valuable to identity thieves. A database of 100,000 names, addresses, and financial account information might sell for 500,000.
- API documentation and credentials: Invaluable to other attackers. These might not be sold but used internally.
- Internal communications: Sometimes less directly valuable but potentially embarrassing if released publicly.
If Bridge Pay paid a ransom and the attackers agreed to delete the data, there's no guarantee the data was actually deleted. Ransomware gangs are criminals. They have no incentive to honor agreements. Many victims pay ransom only to find their data released anyway.
The FBI's Stance on Ransom Payments
The FBI and other law enforcement agencies actively discourage paying ransoms because:
- It funds criminal operations
- It doesn't guarantee data deletion
- It incentivizes more attacks
- It may violate sanctions if the attackers are based in sanctioned countries
However, the FBI also understands that some organizations feel compelled to pay to restore service. The official guidance is: don't pay, but if you do, report it to law enforcement immediately so they can track the Bitcoin and try to recover it.

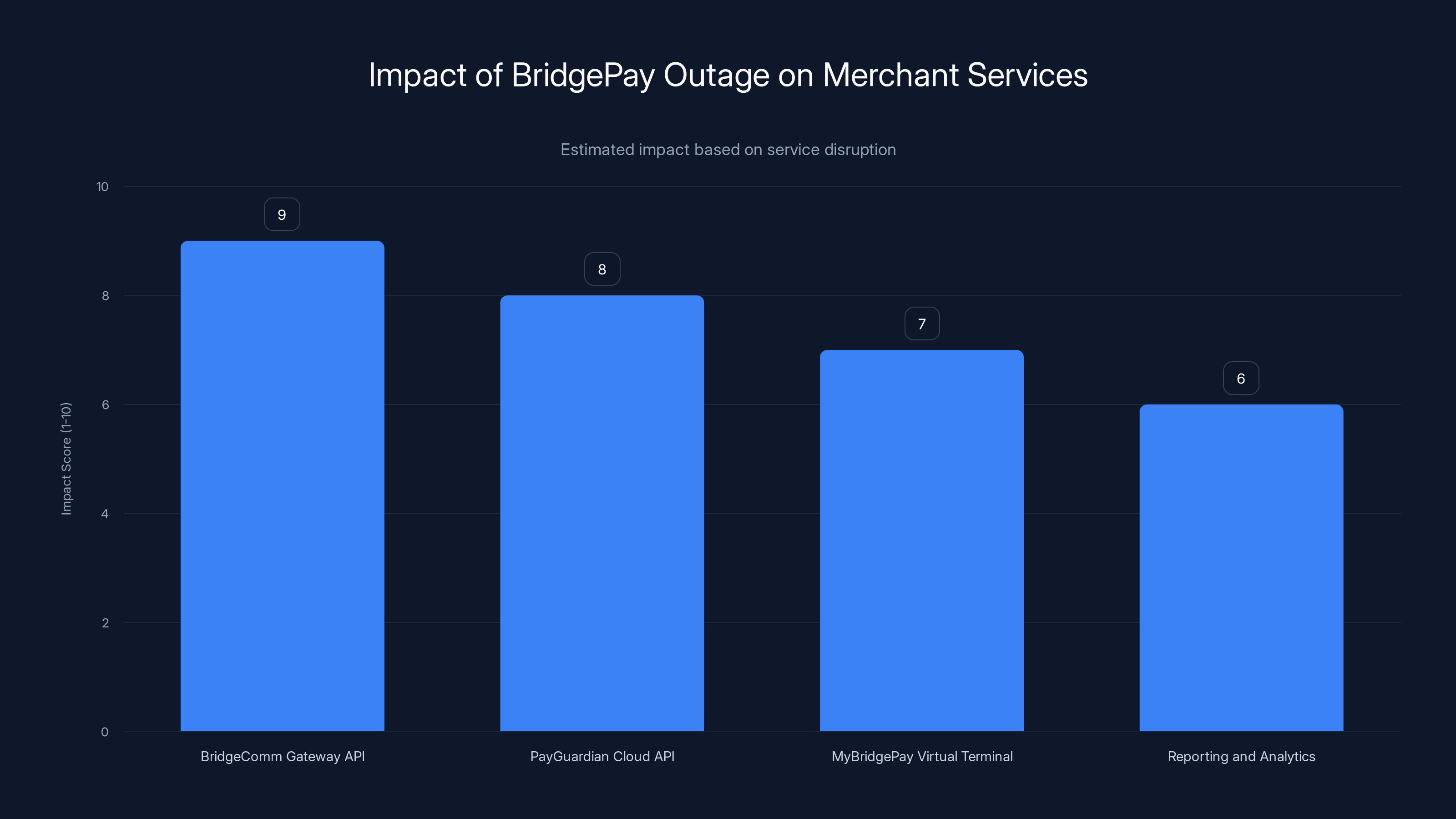
The BridgePay outage severely impacted merchant services, with the BridgeComm Gateway API experiencing the highest disruption. Estimated data.
Preventing Similar Attacks: A Security Framework
While you can't completely prevent ransomware attacks, you can make yourself a difficult target. Here's a framework for improving your resilience:
Tier 1: Prevention
Focus on not getting compromised in the first place:
- Patch management: Keep all systems updated. Most attacks exploit known vulnerabilities that have patches available.
- Email security: 80-90% of ransomware enters through phishing. Implement email filtering, URL rewriting, and security awareness training.
- Credential management: Use multi-factor authentication everywhere. Require strong passwords. Implement single sign-on. Use password managers.
- Network segmentation: Divide your network into zones. Even if attackers get into one zone, they can't instantly move to critical systems.
- Endpoint detection: Install endpoint detection and response (EDR) tools that identify suspicious behavior on computers and servers.
Tier 2: Detection
Assuming prevention fails, detect the attack as early as possible:
- Log aggregation: Collect logs from all systems into a central location. Search for suspicious activity patterns.
- Security information and event management (SIEM): Use SIEM tools to correlate logs and identify attacks.
- Threat hunting: Hire security professionals to actively search your network for intruders.
- User and entity behavior analytics (UEBA): Monitor for unusual behavior that might indicate compromise.
Tier 3: Response
When an attack is detected, respond immediately:
- Incident response plan: Have a documented plan that outlines roles, communication procedures, and escalation paths.
- Isolated backup systems: Keep backups offline and encrypted so they can't be compromised alongside production systems.
- Disaster recovery testing: Actually test recovery from backups. Many organizations discover their backups are corrupted only when they need them.
- Communication procedures: Know who to contact (law enforcement, cyber insurance, forensic teams, customers, regulators).
Tier 4: Recovery
When you're hit, recover faster than attackers can demand payment:
- Cybersecurity insurance: Coverage for ransomware can cover recovery costs, business interruption, and ransom (though paying is discouraged).
- Incident response team: Pre-identify the forensic firm, lawyers, and consultants you'll hire in case of attack.
- Backup and recovery procedures: Know exactly how to restore from backups safely.
- Communication templates: Pre-write communications to customers, employees, and regulators so you respond correctly under stress.
Insurance and Financial Protection
Cybersecurity insurance has become critical for businesses that process payments.
What Ransomware Insurance Covers
A good cyber insurance policy typically covers:
- Forensic investigation: 500,000 for hiring forensic teams
- Restoration and recovery: 5,000,000+ depending on policy
- Business interruption: Coverage for lost revenue during outages (usually 30-60 days of lost profit)
- Regulatory response: Coverage for legal consultants helping with regulatory inquiries
- Notification costs: If customer data is breached, insurance covers the cost of notifying affected individuals
- Credit monitoring: Offer affected customers credit monitoring services
Important Exclusions
Read the fine print carefully. Most policies exclude:
- Failure to implement basic security: If you weren't running updates or had weak passwords, they might deny claims
- Ransom payments: Many policies now exclude or limit ransom coverage (due to sanctions concerns)
- Failure to detect intrusions: If you knew about suspicious activity but didn't respond, they might deny claims
- Insider threats: If an employee caused the damage, coverage might not apply
Cost-Benefit Analysis
A cyber insurance policy might cost
- A single ransomware attack costs $1.24 million on average
- A payment processor outage costs businesses thousands to millions per hour
- Regulatory fines for security failures can exceed $100,000
- Reputational damage and lost customers can persist for years
Insurance is relatively cheap compared to the risk.

What Bridge Pay Users Should Do Now
If you use Bridge Pay, here are concrete steps:
Immediate Actions
- Verify incident status: Check Bridge Pay's official incident response page for updates on recovery status.
- Change API keys: If your integration uses API keys, request new ones from Bridge Pay and update your systems.
- Review transaction logs: Look for any unauthorized activity in your merchant account during the outage window.
- Check for data breaches: Monitor your email for breach notifications about your merchant account data.
- Review backups: If you maintain local transaction logs or customer data, verify they haven't been compromised.
Short-term Actions
- Implement a backup processor: Set up Stripe, Square, or another processor as a fallback.
- Test failover procedures: Simulate a Bridge Pay outage and verify you can switch to your backup.
- Update incident response plan: Document specific procedures for payment processor outages.
- Review insurance: Check that your cyber insurance includes business interruption coverage.
- Strengthen credentials: Implement multi-factor authentication on your Bridge Pay merchant account.
Long-term Actions
- Vendor assessment: Evaluate Bridge Pay's long-term commitment to security improvements.
- Diversification: Don't put 100% of transaction volume through one processor.
- Monitoring: Subscribe to Bridge Pay's status page and security alerts.
- Relationship review: Periodically assess whether Bridge Pay continues to meet your needs.
Future of Payment Security: What Comes Next
The payment industry is evolving rapidly in response to threats like the Bridge Pay attack.
Decentralization and Blockchain
Some forward-thinking companies are exploring blockchain-based payment processing. The idea: instead of depending on one company's infrastructure, use a distributed network. No single point of failure. No ransomware to encrypt. This is still experimental for mainstream payments, but it's coming.
API-First Architecture
Payment processors are moving toward API-first architectures with better isolation. Instead of one big system that processes everything, you have specialized microservices that handle specific functions. If one service is compromised, others keep running.
Zero-Knowledge Proofs
New cryptographic techniques like zero-knowledge proofs might allow payment processing without exposing sensitive data. Merchants could prove transactions occurred without revealing card details or customer information. This wouldn't prevent ransomware, but it would reduce the value of stolen data.
Quantum-Safe Encryption
As quantum computers become more powerful, current encryption might become breakable. Payment processors are investigating quantum-safe encryption algorithms that will remain secure even against quantum attacks.
Mandatory Multi-Processor Requirements
Regulators might eventually require that critical financial institutions maintain relationships with multiple payment processors, ensuring redundancy at the regulatory level.

The Real Lesson: Fragility of Trust
If there's one thing the Bridge Pay attack teaches, it's this: we've built an incredibly sophisticated financial system that depends entirely on trust. Trust that payment processors are secure. Trust that banks maintain backups. Trust that ransomware won't wipe everything out.
But trust is fragile.
When that trust breaks, the consequences cascade instantly through the entire system. Merchants who've done everything right still lose revenue because they depended on a processor that got hacked. Banks that maintain excellent security still face outages because their processors were compromised. Customers who've never heard of Bridge Pay still can't buy coffee because of an attack they'll never fully understand.
The solution isn't to eliminate trust. Trust is necessary for a functioning economy. The solution is to build systems that work even when trust fails. Redundancy. Diversity. Resilience. These aren't optional features anymore. They're essential infrastructure.
The payment systems that survive the next decade will be those that assume failure is inevitable and design around it. Companies that assume their processors will fail. Banks that assume their systems will be attacked. Merchants who assume they'll need backups.
If you're running a business, assume Bridge Pay or any other critical vendor will fail at the worst possible moment. Build accordingly. Your revenue depends on it.
FAQ
What exactly is a payment gateway?
A payment gateway is the technology that authorizes transactions between merchants and customers. When you swipe a credit card at a store or enter payment information online, the gateway connects that transaction to the banking network, verifies funds, and processes the payment. Bridge Pay operates a payment gateway that thousands of merchants depend on daily. Without it, transactions can't be completed.
How do ransomware attackers get inside systems like Bridge Pay's?
Attackers typically use one of several methods: phishing emails that trick employees into clicking malicious links or attachments, exploitation of unpatched security vulnerabilities in public-facing systems, compromise of credentials from previous breaches, or supply chain attacks (compromising a vendor that the target company trusts). Sophisticated attacks often combine multiple entry points and spend weeks or months inside a network before deploying encryption.
What does "ransomware dwell time" mean?
Dwell time is how long attackers stay inside a network before they actually deploy ransomware encryption. Modern attackers have dwell times averaging 224 days. During this time, they're mapping the network, finding valuable data, disabling backups, and planning the most damaging approach. Longer dwell time means more preparation and usually more effective attacks.
Can paying the ransom guarantee data recovery?
No. Paying a ransom guarantees nothing. Criminals are criminals. Even if attackers provide a decryption key, they have no incentive to actually delete the data they exfiltrated. Many victims pay ransom and discover their data was released anyway. Law enforcement actively discourages ransom payment because it funds criminal operations and incentivizes more attacks.
What is PCI DSS compliance and why does it matter for payment processors?
PCI DSS (Payment Card Industry Data Security Standard) is a set of security requirements that organizations handling payment card data must meet. Compliance includes encryption, network segmentation, regular security testing, access controls, and incident response procedures. Payment processors like Bridge Pay must maintain the highest level of PCI DSS compliance (Level 1). Failure to meet standards results in fines and potential loss of the ability to process cards.
How can merchants protect themselves from payment processor outages?
The best protection is redundancy. Set up a backup payment processor and test it regularly. Maintain multiple payment methods (ACH transfers, digital wallets, checks) so customers have alternatives if card processing fails. Have an offline fallback plan for processing payments when all digital systems are down. Monitor your processor's status page and have a communication plan for notifying customers about outages. Consider cyber insurance that covers business interruption.
What does the US Secret Service have to do with cybercrime?
The US Secret Service's Electronic Crimes Task Force investigates major financial crimes including ransomware, extortion, and cyberattacks on financial institutions. Their involvement in the Bridge Pay investigation signals that law enforcement considered it a serious threat to the financial system. They bring law enforcement authority to investigate, subpoena cooperation, coordinate with international agencies, and trace cryptocurrency payments.
How long does it typically take to recover from a ransomware attack like Bridge Pay's?
Recovery timeframe varies significantly. A well-prepared company with good backups might recover in 24-48 hours. A company without good backups or with deeply compromised systems might take weeks or months. For payment processors, the pressure to recover quickly is intense because every hour of downtime costs merchants thousands or millions of dollars. Bridge Pay's recovery was ongoing for several days at minimum, based on their incident updates.
What happens to data when it's leaked on the dark web?
Once stolen data is posted to dark web leak sites, it can be purchased by anyone with cryptocurrency. Criminals use this data for identity theft, account takeover, phishing, or selling to other criminals. Some data has value forever (like customer lists or source code). Other data has limited value (transaction records). There's no expiration date on dark web exposure. Even years later, criminals might still be using data from old breaches.
Should merchants stop using payment processors altogether?
No. Payment processors provide critical infrastructure that merchants couldn't replicate individually. The issue isn't that processors exist, but that merchants shouldn't depend entirely on one processor. Diversification—using multiple processors, multiple payment methods, and fallback options—reduces risk. The goal is resilience, not elimination of payment processors.
How are payment systems changing to prevent future attacks like this?
The industry is moving toward greater redundancy, decentralization, and detection capabilities. Regulators are encouraging (and in some cases requiring) that financial institutions maintain relationships with multiple processors. Technology improvements include zero trust architecture (assuming no network is trustworthy), better threat detection, faster incident response, and blockchain-based alternatives that eliminate single points of failure. Insurance requirements are also driving security improvements as insurers raise standards for coverage.

The Bottom Line
The Bridge Pay ransomware attack wasn't an anomaly. It was a preview of the risk environment that businesses now operate in. Payment systems, like all critical infrastructure, are targets for sophisticated attackers with significant financial incentives.
What matters now is how you respond. The businesses that survive and thrive will be those that assume failure is inevitable and design redundancy into every critical system. Not just payment processing, but communications, data backups, customer notifications, and recovery procedures.
If you're running any kind of business that accepts payments, this incident should drive concrete action:
- Set up a backup payment processor this week
- Test your failover procedures
- Review your cyber insurance coverage
- Create a written incident response plan
- Schedule regular security assessments
These aren't optional improvements. They're essential business continuity measures. The question isn't whether your systems will fail. It's whether you'll be ready when they do.
Key Takeaways
- BridgePay ransomware attack knocked payment systems offline for thousands of merchants and 70+ banks nationwide, forcing cash-only operations.
- The US Secret Service involvement signals this was a critical threat to financial infrastructure requiring federal law enforcement investigation.
- Payment processors are prime ransomware targets because they control financial transaction flows, hold valuable data, and face pressure to pay quickly.
- Initial forensic findings indicated no payment card data was compromised, but data exfiltration was likely used as additional extortion leverage.
- Merchants and businesses must implement backup payment processors and diverse payment methods to survive processor outages and ransomware attacks.
- Recovery from major ransomware attacks costs millions and takes weeks due to forensic analysis, system rebuilding, and regulatory compliance requirements.
- Modern ransomware uses 'double extortion' strategy: encrypt data AND exfiltrate sensitive information, then threaten both recovery and data release.
- Average ransomware dwell time of 224 days means attackers spend months inside networks before deploying visible encryption, causing extensive damage.
- Cyber insurance with business interruption coverage is critical for payment-dependent businesses, typically costing less than single incident losses.
- Future payment security will require decentralization, API-first architecture, multiple processor redundancy, and zero trust security frameworks.
Related Articles
- SonicWall Breach Hits Marquis Fintech: What Banks Need to Know [2025]
- Flickr Data Breach 2025: What Was Stolen & How to Protect Yourself [2025]
- Windscribe VPN Server Seized by Dutch Authorities: What It Means for Your Privacy [2025]
- Sapienza University Ransomware Attack: Europe's Largest Cyberincident [2025]
- Conduent Data Breach 2025: What Millions of Americans Need to Know [2026]
- Substack Data Breach Exposed Millions: What You Need to Know [2025]
![BridgePay Ransomware Attack: What Happened and How to Protect Your Business [2025]](https://tryrunable.com/blog/bridgepay-ransomware-attack-what-happened-and-how-to-protect/image-1-1770662417939.jpg)



