Introduction
In 2024, a revelation sent shockwaves through the cybersecurity community. Researchers uncovered that the vast majority of high-profile ransomware attacks weren't powered by custom-built infrastructure at all. Instead, threat actors behind Lock Bit, Conti, Black Cat, and dozens of other notorious groups were renting virtual machines from bulletproof hosting providers for pennies on the dollar.
The discovery changed how we understand ransomware economics. For years, security professionals assumed that launching a sophisticated ransomware campaign required significant technical infrastructure investment. You'd need to set up command-and-control servers, maintain anonymity, handle infrastructure at scale, and manage it all without getting shut down. It seemed expensive. It seemed hard.
Turns out, it's neither.
Here's what happened: Researchers examining multiple ransomware attacks noticed something odd. The compromised Windows servers all had identical hostnames. Not similar hostnames. Identical. The same naming convention appeared across thousands of unrelated attacks, which made no sense unless these weren't actually independent systems. After digging deeper, they found the answer: these were virtual machines created from the same prebuilt Windows templates, all rented from bulletproof hosting providers who don't care about abuse reports or law enforcement takedown requests.
This single finding exposed a massive vulnerability in how the internet's hosting infrastructure works. It revealed that the barrier to entry for cybercrime isn't technical expertise or capital investment. It's just a credit card and a willingness to work with providers who look the other way.
What makes this worse is that it's completely legal in many jurisdictions. The hosting companies aren't technically breaking laws by renting servers. They're just not enforcing terms of service. They're not monitoring for abuse. They're not cooperating with law enforcement. They're providing a service, taking payment, and ignoring everything that happens next.
In this guide, we're going to explore how bulletproof hosting actually works, why so many ransomware groups rely on it, what specific vulnerabilities make these platforms attractive to cybercriminals, and most importantly, how organizations can identify and defend against infrastructure hosted on these networks.
TL; DR
- Bulletproof hosting providers rent cheap VMs to ransomware gangs without enforcing abuse policies or cooperating with law enforcement
- 95% of exposed servers came from just a handful of identical Windows templates, making them trivially easy to identify and correlate
- Major groups including Lock Bit, Conti, Black Cat, and Qilin all relied on the same bulletproof hosting infrastructure
- ISPsystem VMmanager vulnerabilities allow creation of thousands of identical server configurations that never randomize hostnames
- Stark Industries Solutions and First Server Limited, both Russian-linked and EU/UK sanctioned firms, supplied infrastructure to virtually all major ransomware operations
- Organizations must monitor for servers with identical characteristics using tools like Shodan to identify compromised infrastructure before attacks escalate
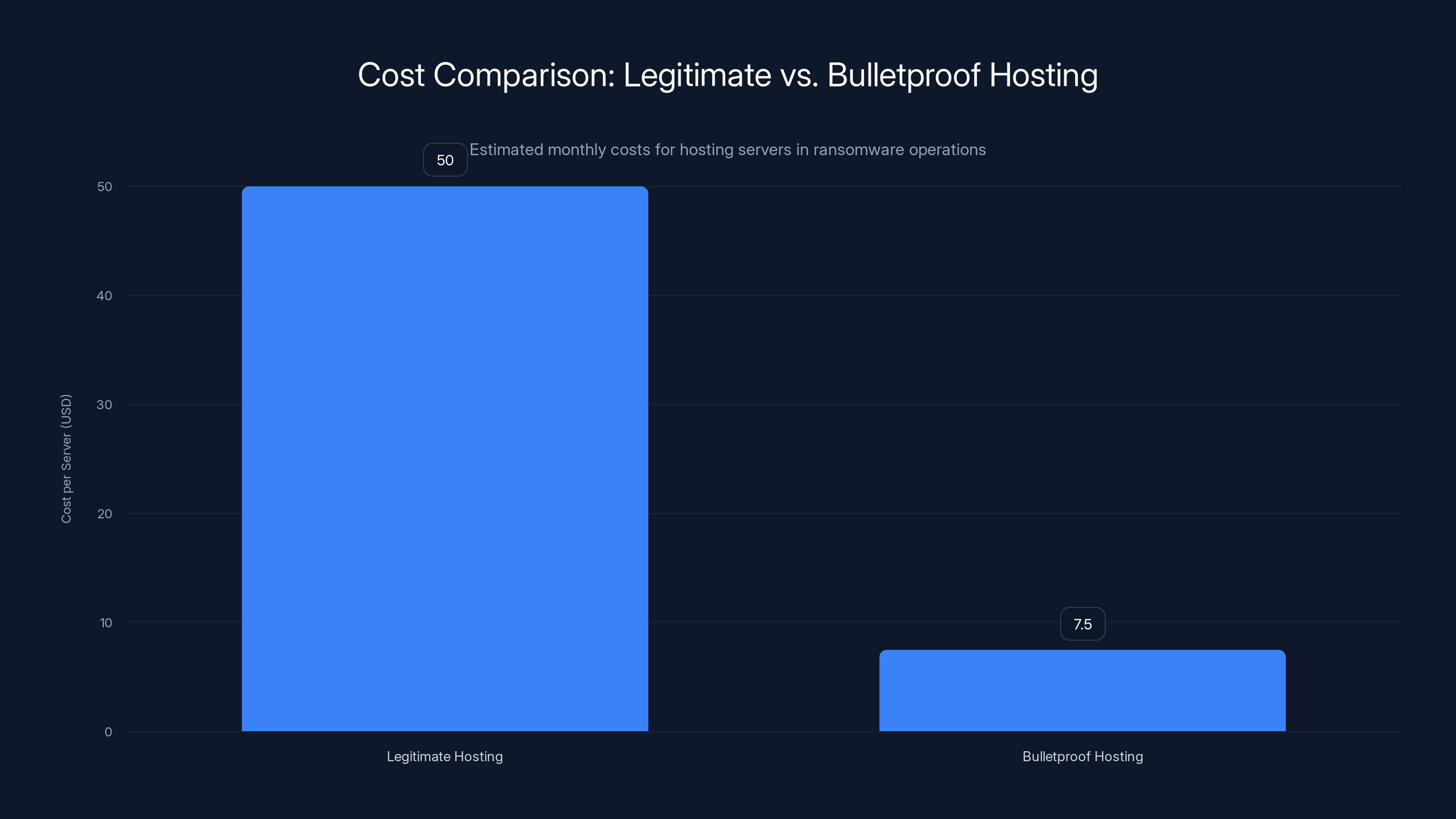
Bulletproof hosting significantly reduces costs for ransomware operations, charging approximately
What Exactly Is Bulletproof Hosting?
Bulletproof hosting sounds like a real technology. It's not. It's a business model.
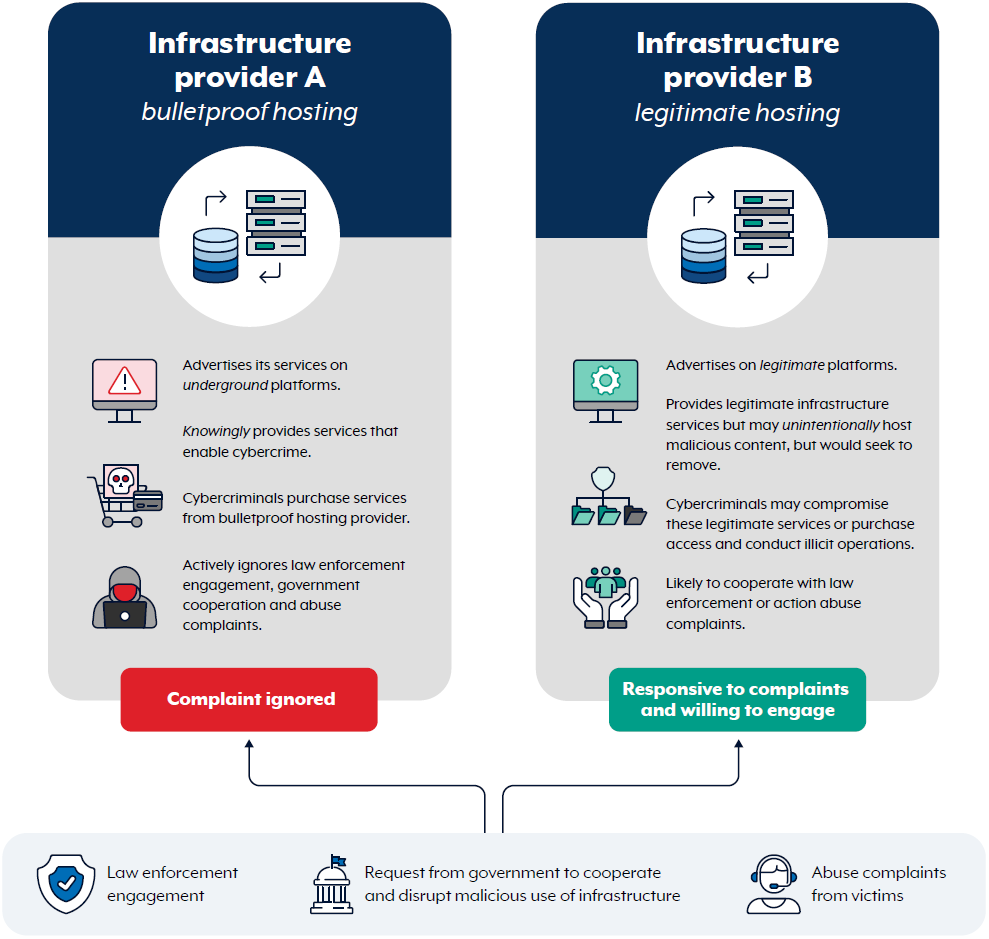
A bulletproof hosting provider is simply a company that rents infrastructure (dedicated servers, virtual machines, IP addresses, bandwidth) but explicitly refuses to cooperate with abuse complaints, law enforcement takedown requests, or terms-of-service enforcement. When your server gets hacked, when it launches attacks, when it hosts malware, when it participates in criminal activity, the hosting company shrugs and takes your money.
Think of it like a storage unit company that promises never to look inside your unit, never to cooperate with police, and never to ask questions about what you're storing. Technically, they're just renting space. The fact that you're using it to stage a heist isn't their problem, according to their business model.
These providers typically operate from jurisdictions with weak cybercrime enforcement, limited international law enforcement cooperation, or explicit protection from their host governments. Russia, Eastern Europe, and parts of Southeast Asia have historically been hubs for this activity, though bulletproof providers pop up anywhere enforcement is lax.
The hosting market is divided into three tiers. At the top, you have legitimate providers like AWS, Azure, and Google Cloud, who actively monitor for abuse, respond quickly to law enforcement, and maintain strict acceptable-use policies. In the middle, you have providers who maintain policies but often have slow response times or weaker enforcement. At the bottom, you have bulletproof providers who advertise their unwillingness to cooperate as a selling point.
What makes bulletproof hosting particularly dangerous is that it's not expensive. A virtual machine that might cost
The business model depends on scale and anonymity. Individual customers paying for individual servers would be too traceable. Instead, bulletproof providers rent to resellers, who rent to criminal groups, who then use the infrastructure. By the time law enforcement traces an attack back, they hit layers of shell companies, false identities, and cryptocurrency payments that intentionally obscure the actual customer.
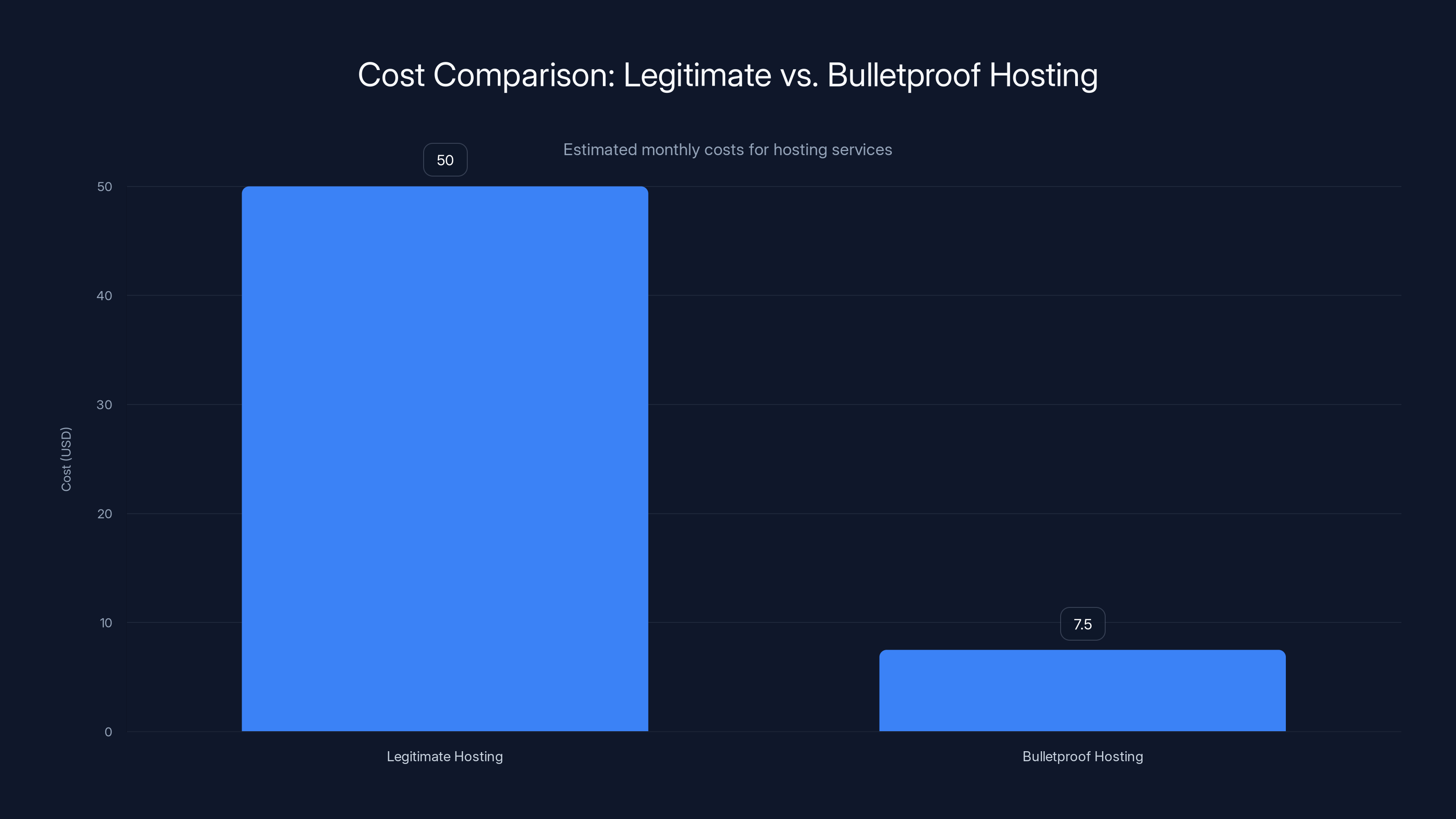
Bulletproof hosting significantly reduces costs for cybercriminals, with monthly expenses dropping from
The Ransomware Infrastructure Problem
Ransomware attacks have three distinct infrastructure requirements. First, you need servers to communicate with victims and send ransom demands. Second, you need staging infrastructure to exfiltrate data before encryption. Third, you need backup servers in case the primary infrastructure gets taken down mid-campaign.
Large ransomware groups like Lock Bit operate networks of dozens or hundreds of servers worldwide. They maintain backup infrastructure, redundancy, load balancing, and contingency plans. Building all of this requires significant upfront investment if you use legitimate providers. A small mistake, a traced transaction, or a single law enforcement alert can cascade into infrastructure seizures across multiple providers.
Bulletproof hosting solves both problems simultaneously. The provider won't shut you down, so you don't need backups. The provider won't share logs or cooperate with law enforcement, so tracking becomes exponentially harder. The provider won't monitor your traffic, so you can do whatever you want without detection.
More importantly, bulletproof hosting is distributed. You might rent servers from dozens of bulletproof providers scattered across multiple countries, each one legally independent, each one uncooperative. To shut down a single ransomware operation requires coordinated law enforcement action across multiple jurisdictions, each with different legal frameworks, different priorities, and different capabilities.
For a threat actor, that's acceptable risk. For a victim, it's a nightmare.
The infrastructure itself isn't sophisticated. Modern ransomware doesn't require cutting-edge technology. It requires reliability. Bulletproof providers offer exactly that. They guarantee uptime, they guarantee no interruptions, they guarantee that your infrastructure will keep running regardless of what you're using it for.
The economic equation is brutal. A single ransomware hit on a mid-size organization can generate

ISPsystem VMmanager: The Vulnerability at Scale
Here's where the story gets interesting. The researchers investigating these attacks didn't find thousands of different hosting providers. They found a pattern. Almost all of the compromised infrastructure shared common characteristics. They all ran the same virtualization platform. They all had identical Windows templates. They all used the same default naming conventions.
The culprit was ISPsystem VMmanager, a legitimate virtualization platform used by thousands of hosting providers worldwide to manage their virtual machine infrastructure. When a hosting provider needs to quickly spin up new VMs, they use templates. A template is essentially a pre-configured Windows installation with all the basic software, drivers, and configurations already in place. New VMs are created from these templates, which should theoretically be faster and more consistent than building each one from scratch.
Here's the critical vulnerability: when VMmanager creates a new VM from a template, it doesn't randomize the hostname. The hostname is the name assigned to each device on a network, used for identification and communication. If a template has a hostname like "WIN-7F3Q4K" or "SERVER-001", every new VM created from that template initially has the same hostname.
Administrators are supposed to change these hostnames manually. But they don't. They don't because it's tedious, they don't because they forget, and they don't because they don't realize it matters. So thousands of independent virtual machines, spread across dozens of bulletproof hosting providers, end up with identical hostnames.
From a defensive perspective, this is stupidly easy to exploit. Using Shodan (a search engine for internet-connected devices), researchers simply searched for servers with these distinctive hostnames. They found tens of thousands of results. Most of them were from the same bulletproof hosting providers.
The implications are staggering. If 95% of your infrastructure all comes from the same handful of templates, then your entire operation is correlated. An attacker compromising one server has a roadmap to all the others. Law enforcement tracing one attack can follow the thread directly to the others. The very infrastructure that's supposed to provide anonymity and reliability actually concentrates risk.
This isn't a flaw unique to ISPsystem. It's a systemic problem across virtualization platforms. Hypervisors like VMware, Hyper-V, and KVM all use templates. Hosting providers worldwide rely on similar shortcuts. The difference is that legitimate hosting providers either randomize hostnames automatically, require administrators to change them, or have compliance processes that catch these issues. Bulletproof providers have no such quality control.
The attackers were benefiting from laziness, not sophistication. The infrastructure was exposed not because it was advanced, but because it was generic.

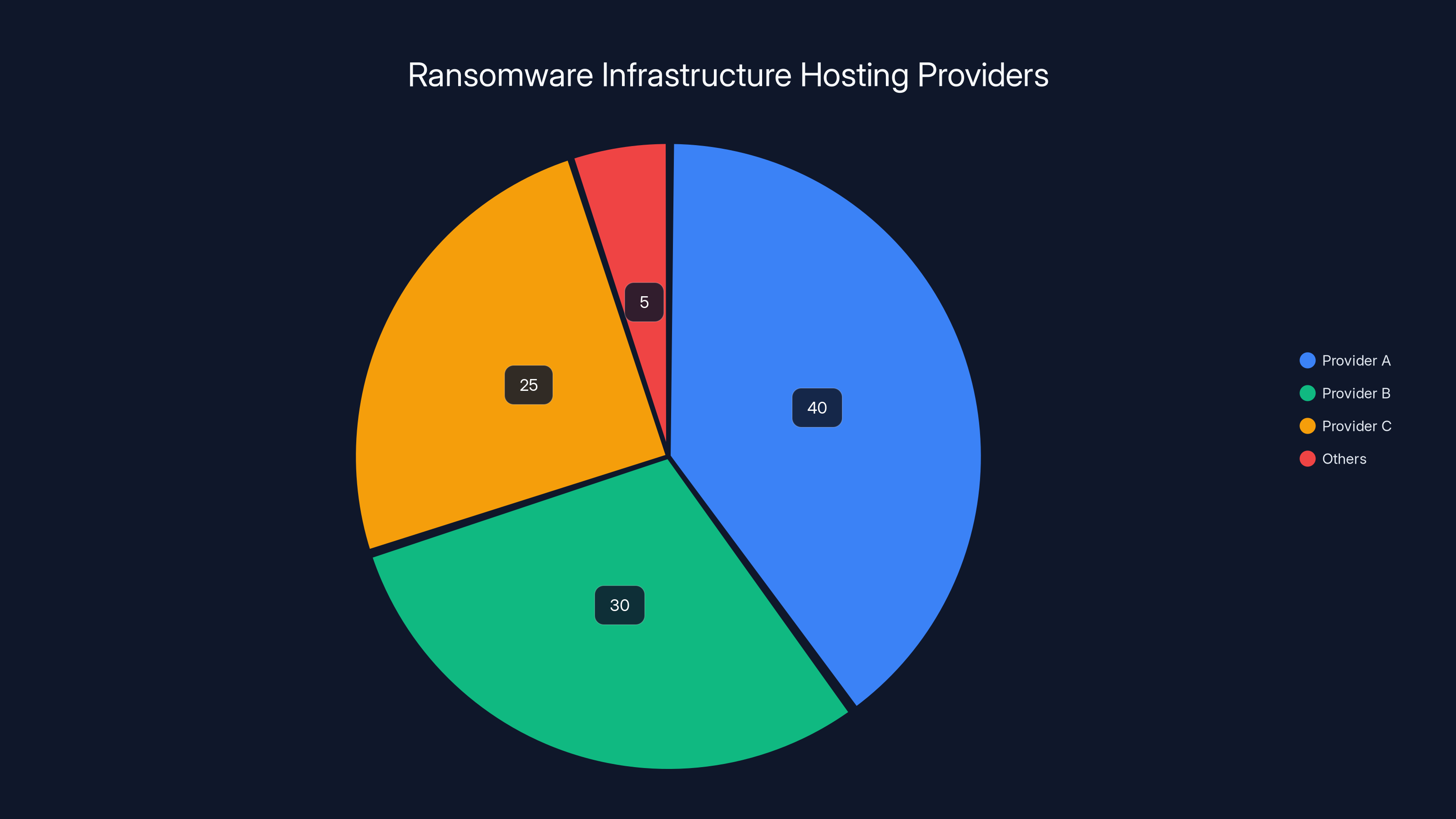
Estimated data shows that 95% of ransomware infrastructure relies on a few key hosting providers, highlighting a critical vulnerability in cybercrime operations.
The Ransomware Groups Relying on Bulletproof Infrastructure
The research identified infrastructure connections linking multiple major ransomware-as-a-service (RaaS) operations to bulletproof hosting providers. These weren't isolated incidents. These were systematic supply chains.
Lock Bit dominated the 2023-2024 ransomware landscape, conducting hundreds of attacks and demanding hundreds of millions in ransom. The group operated multiple backup infrastructure nodes across different bulletproof providers. When law enforcement disrupted one set of servers, Lock Bit simply shifted to another set using different bulletproof providers. The infrastructure diversity was geographic but not operational. All of it traced back to the same template characteristics.
Conti, once the most prolific ransomware operation before its ostensible shutdown, relied on similar infrastructure patterns. Researchers found servers across multiple bulletproof providers using identical configuration patterns. When Conti supposedly dissolved, members split into smaller groups that continued using variations of the same infrastructure model.
Black Cat (ALPHV) emerged as the most sophisticated ransomware group, featuring custom tools, multi-ransom strategies, and professional operation procedures. Despite that sophistication, the group still rented its backup infrastructure from the same bulletproof providers serving other gangs. This suggests that even the most advanced threat actors find cost-effective infrastructure essential enough to risk the exposure.
Qilin, a newer group that rose to prominence in 2023, specialized in attacking large enterprises. The group's rapid scaling and global presence would have been impossible without access to cheap, reliable, unmonitored infrastructure. Researchers traced Qilin's activity to bulletproof providers serving dozens of other criminal operations.
Trick Bot and Ursnif started as banking malware operations before pivoting to ransomware. Both groups maintained extensive command-and-control infrastructure across bulletproof providers. The persistence and scale of their operations depended on not worrying about infrastructure disruptions.
Net Support, Red Line, and other malware families all followed the same pattern. The researchers traced hundreds of individual malware campaigns to just a handful of bulletproof hosting providers, all with infrastructure that shared these telltale template characteristics.
The consolidation was stunning. Most major ransomware operations of 2023-2024 relied on essentially the same supply chain. They weren't using different providers to diversify risk. They were using the same providers because those were the providers that worked reliably, didn't get shut down, and offered the right combination of cheap cost and zero accountability.

Stark Industries Solutions and First Server Limited: Infrastructure Hub Operators
The research specifically called out two companies as major suppliers of infrastructure to ransomware operations: Stark Industries Solutions and First Server Limited. Both companies share critical characteristics. Both are registered in jurisdictions with weak cybercrime enforcement. Both have been sanctioned by the EU and UK for supporting state-sponsored activities. Both operate hosting operations that explicitly reject abuse reports and law enforcement requests.
Stark Industries Solutions operated as a reseller and provider of bulletproof hosting, operating data centers and renting infrastructure under various brand names and subsidiary companies. The group used complex shell company structures to obscure the actual operators. When one brand got disrupted, Stark would simply rebrand and continue operations under a new name.
What made Stark Industries particularly significant is the volume and diversity of its customer base. The company didn't just serve one or two ransomware groups. It served dozens. This wasn't accident or coincidence. It was the business model. Stark Industries provided infrastructure-as-a-service specifically designed for criminal operations that needed reliability without accountability.
First Server Limited operated similarly, though with slightly different operational patterns. First Server marketed itself as offering unmonitored, unfiltered hosting with explicit guarantees of not cooperating with law enforcement. The company's terms of service (where they existed) included clauses promising not to review traffic, monitor activity, or respond to abuse complaints except under direct court order from Russian courts, which effectively meant never.
Both companies maintained extensive server farms with thousands of virtual machines. Both companies used aggressive anonymization techniques including shell companies, cryptocurrency-only payments, and complex international transaction chains to obscure the flow of money. Both companies explicitly recruited customers from criminal forums and dark web marketplaces.
The connection to Russian state-sponsored activity is significant. While both companies claimed independence, their sanctioning by Western governments suggests deeper connections to Russian intelligence or Russian-backed criminal enterprises. The companies continued operating despite sanctions, suggesting they had either state protection or significant resources to maintain operations underground.
From a law enforcement perspective, identifying these specific companies was valuable. Shutting down a few major infrastructure providers is technically simpler than hunting hundreds of individual threat actors. It's theoretically possible to negotiate with a hosting provider. It's nearly impossible to negotiate with decentralized criminal groups.
From a ransomware gang perspective, the consolidation was risky. Having most of your infrastructure supplied by two major providers created a single point of failure. But the cost and reliability benefits apparently outweighed the concentration risk.
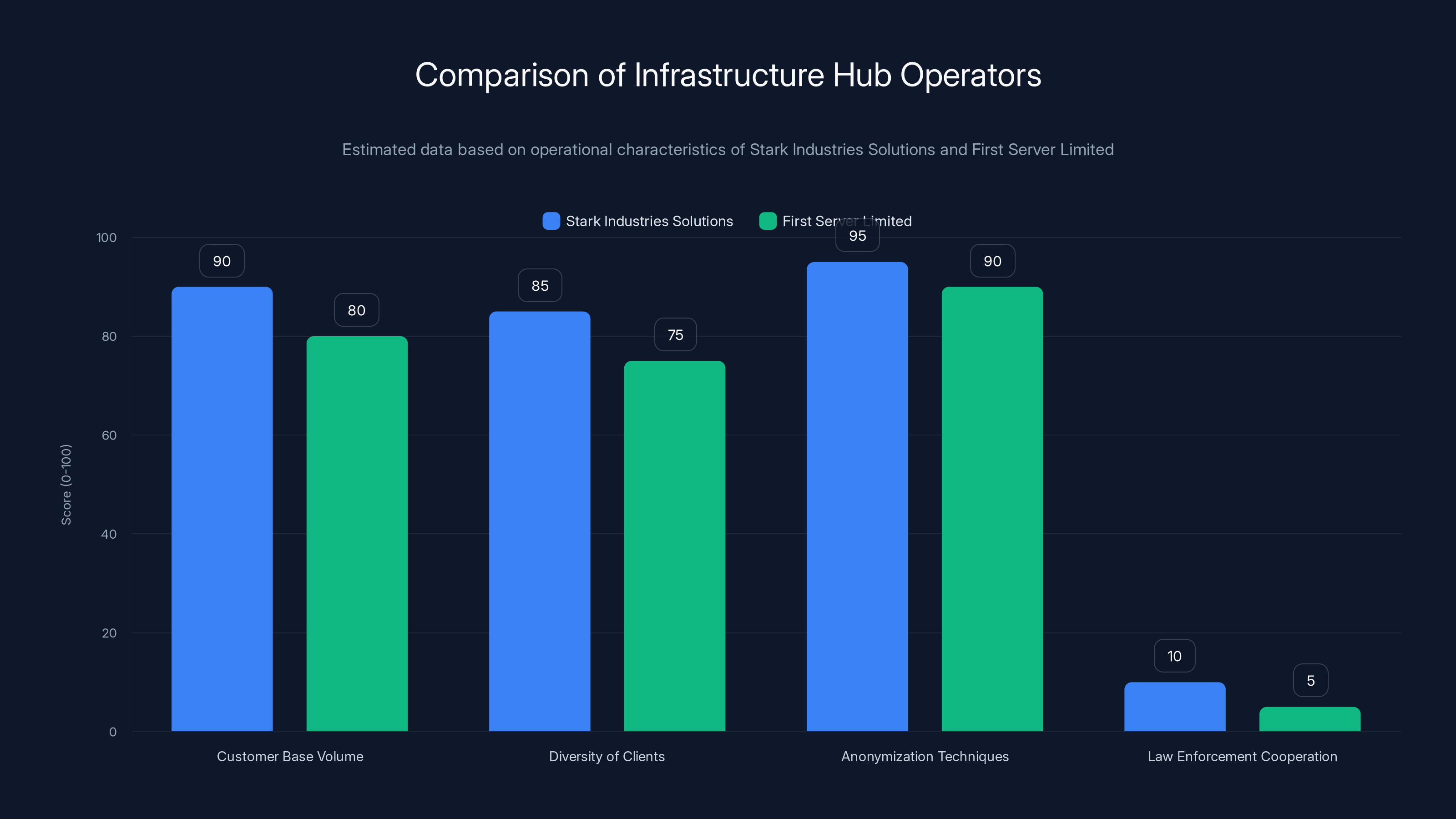
Stark Industries Solutions and First Server Limited are major infrastructure providers for ransomware operations, with Stark having a slightly larger and more diverse customer base. Both companies employ strong anonymization techniques and minimal cooperation with law enforcement. (Estimated data)
How Bulletproof Infrastructure Enables Attack Scaling
Ransomware attacks follow a consistent operational pattern. Reconnaissance, initial compromise, lateral movement, data exfiltration, encryption, and ransom demand. Each stage requires reliable command-and-control communication between attacker systems and compromised victim infrastructure.
In a traditional ransomware operation, the attacker needs to maintain operational security throughout this process. If the C2 server gets detected, the entire operation collapses. If law enforcement traces the server, they might trace the attacker. If the server goes down, the attacker loses communication with every compromised system.
Bulletproof hosting solves these problems at every stage. The C2 server stays online because the hosting provider doesn't care about abuse reports. The server remains unmonitored because the provider explicitly doesn't monitor traffic. The operational costs remain low because the provider doesn't charge premium rates for guaranteed uptime.
More critically, bulletproof hosting enables operational scaling that would otherwise be prohibitively expensive. A ransomware gang that can spin up new infrastructure in minutes and at negligible cost can afford to run multiple simultaneous campaigns. They can maintain backup infrastructure for every primary server. They can geographically distribute their operations. They can continuously retire old servers and provision new ones to stay ahead of law enforcement.
The economics change everything. A legitimate hosting provider might charge
For a ransomware gang operating dozens or hundreds of servers, the cost difference is the difference between a sustainable operation and a struggling one. At
This infrastructure enables certain attack patterns that wouldn't otherwise make sense. Some ransomware gangs maintain dedicated infrastructure for specific victim organizations. If they're targeting a Fortune 500 company, they'll provision backup servers in different geographic regions with different network providers, creating redundancy that ensures the operation continues even if one server gets disrupted.
Other gangs maintain distributed exfiltration infrastructure. They don't want to copy all of a victim's data through a single server. So they provision multiple servers in different regions, each handling pieces of the exfiltration simultaneously. This distributes the bandwidth load, avoids overwhelming any single connection, and makes the exfiltration harder to trace because the data flows through multiple independent nodes.
The most sophisticated operations maintain dark web infrastructure for ransom negotiations. Multiple independent servers running Tor or other anonymization networks, each configured to be a backup if others get shut down. These operations can afford that redundancy specifically because bulletproof hosting is cheap enough to support it.
Without bulletproof hosting, these operational patterns would require either significant capital investment or acceptance of substantial operational risk. With bulletproof hosting, they're simply business-as-usual economics.
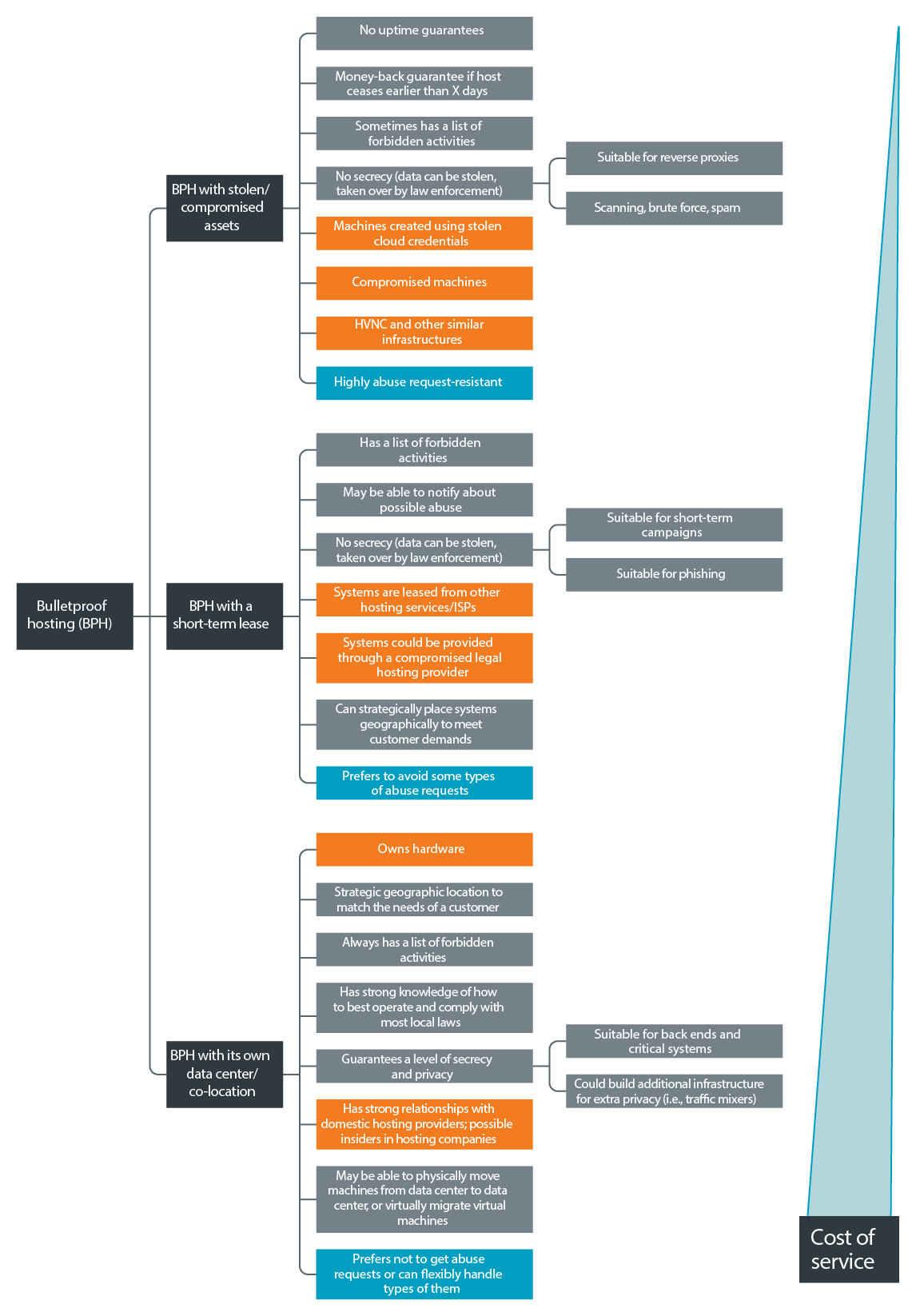
Windows Template Weaknesses and Identical Configurations
The discovery that 95% of these servers came from identical or near-identical Windows templates reveals a fundamental weakness in how hosting providers manage their infrastructure. It's not malicious. It's not unusual. It's just standard hosting operations optimized for efficiency without considering security implications.
When a hosting provider sets up operations, they create a master Windows installation. They include all the necessary drivers, security patches, and basic software. They configure system settings, create local user accounts, and install monitoring agents. This master becomes the template.
Creating each new VM from this template is faster and more consistent than building from scratch. A provider might provision 1,000 new VMs in a week using this approach. All of them will be identical, all will have the same software versions, all will have the same configurations.
For legitimate hosting operations, this is fine. The provider will have processes to change hostnames, create unique security credentials, configure unique network settings, and ensure that each VM is genuinely independent despite sharing a common base. Administrators see this as good infrastructure-as-code. You build once, deploy many times, all consistently configured.
For bulletproof hosting operations, it becomes a vulnerability. The provider doesn't care about these hardening steps. The customer doesn't ask for them. So thousands of VMs end up with identical hostnames, identical system configurations, identical user accounts, sometimes even identical SSH keys or RDP credentials.
This creates what security researchers call "fingerprinting." Each set of identical systems has a unique fingerprint that makes them instantly recognizable and correlated. It's like having unique serial numbers on each server in a way that proves they came from the same manufacturer.
From an attacker's perspective, this is actually somewhat helpful. Compromising one server from a bulletproof hosting provider gives you insights into the architecture of all other servers from the same provider. You understand the network topology, the filesystem structure, the installed software, the user accounts. This intelligence is valuable if you're conducting operations across multiple servers from the same provider, or if you're trying to laterally move within a network that includes multiple servers from the same provider.
From a defensive perspective, it's catastrophic. Security analysts looking at attack infrastructure can instantly identify which servers are related. They can see that these aren't independent compromises. They're all part of the same infrastructure pattern. They can trace from one attack to the next, building a complete picture of the operational infrastructure supporting multiple ransomware operations.
The KSM (Key Management Server) issue compounds this problem. Windows allows free usage for 180 days without a license, after which it requires activation. Some bulletproof hosting providers would rather not deal with licensing costs or activation servers, so they let the systems run in an unlicensed state. Every single server from these providers would have this characteristic, creating another fingerprint.
Some providers configure all systems with identical RDP settings, identical firewall rules, or identical network configurations. Each of these shared characteristics becomes another data point that correlates the infrastructure.
Security researchers can search Shodan for these distinctive characteristics and instantly identify large clusters of related systems. It's like finding all the cars from the same factory that year, with the same paint job, the same interior, and the same engine. You can't hide when your systems are all identical to each other.
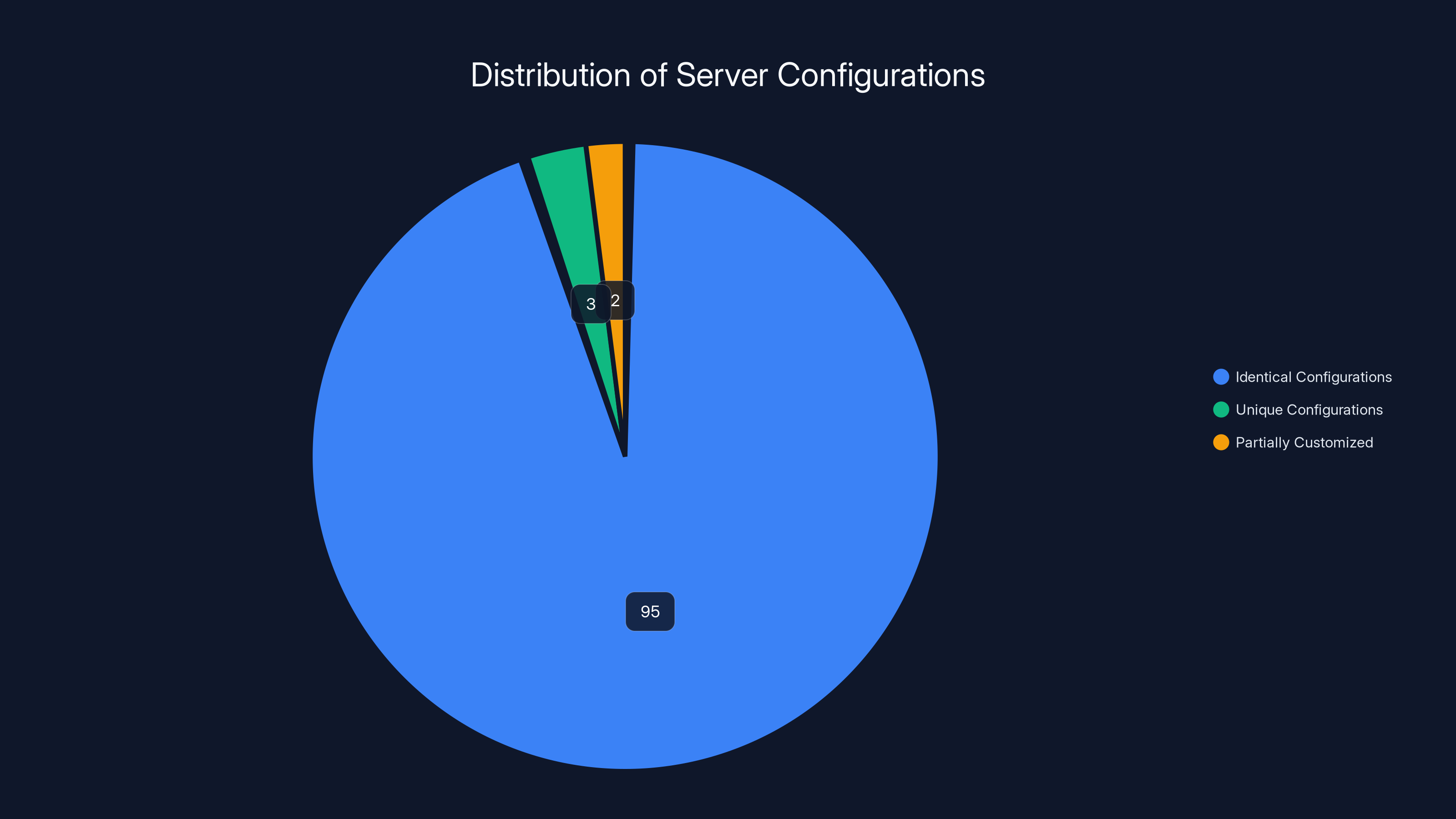
Estimated data shows that 95% of servers are created from identical Windows templates, highlighting a potential security vulnerability due to lack of customization.
The Role of Resellers in the Supply Chain
Bulletproof hosting doesn't operate as a direct-to-criminal market. You don't just Google "bulletproof hosting provider" and sign up. The supply chain is more complex.
At the top level, you have physical infrastructure operators. These are companies that own or lease data centers, maintain power systems, provide network connectivity, and manage physical security. These companies are mostly legitimate, though some deliberately locate in regions with lax cybercrime enforcement.
Below that, you have hosting providers who lease infrastructure from data centers and resell it to customers. This is where bulletproof hosting emerges. Some providers decide to specialize in serving customers who need infrastructure without accountability.
Below that, you have resellers. These are smaller companies or individuals who buy infrastructure from bulletproof hosting providers and resell it further down the chain. Resellers provide a layer of anonymity between the actual criminal end-users and the original hosting provider.
Below that, you have criminal customers who actually use the infrastructure for ransomware operations, malware hosting, botnet C2 servers, and other illegal activity.
The genius of this structure is that each layer can plausibly claim it doesn't know what's happening below it. The data center owner claims they don't monitor the hosting provider's activities. The hosting provider claims they don't monitor reseller activity. The reseller claims they don't know what customers use the infrastructure for. Each layer provides legal plausible deniability.
In practice, everyone knows. The hosting providers explicitly market themselves as bulletproof. The resellers recruit from criminal forums. The customers are obviously conducting illegal activity. But the layering makes enforcement harder. You can't just shut down the hosting provider and stop all ransomware. You have to trace through multiple legal entities, multiple jurisdictions, and multiple business relationships.
More importantly, the layering makes attribution harder. If an attacker uses a server that was purchased by a reseller from a hosting provider from a data center, the chain of responsibility is unclear. Which entity is actually providing the infrastructure? Which entity can be held liable?
This supply chain structure is why Stark Industries Solutions and First Server Limited were significant enough to name in the research. They weren't the end-users. They were chokepoints in the supply chain. If you could shut down those two companies, you'd cut off a significant portion of ransomware infrastructure.
But you can't shut them down because they operate internationally, because they rebrand constantly, because they have financial backing to continue operations despite sanctions, and because their customers are dispersed across multiple criminal organizations that would immediately find alternative suppliers.
How Organizations Can Detect Bulletproof-Hosted Infrastructure
The good news is that bulletproof hosting creates detectable patterns. The bad news is that detection requires proactive monitoring and specific threat intelligence.
Shodan searching is the most accessible method. Organizations can search Shodan for servers with characteristics associated with known bulletproof providers. This includes distinctive hostnames, specific server configurations, particular network ranges, or combinations of software versions that indicate template-based deployments.
For example, searching Shodan for systems with hostname patterns like "WIN-" followed by specific character sequences, if those patterns are known to indicate Stark Industries infrastructure, will reveal all systems from that infrastructure. Organizations can then cross-reference whether any of those IP addresses have been observed in their network logs.
Network telemetry analysis looks for connections to known bulletproof hosting IP ranges. If an organization maintains detailed network logs showing all outbound and inbound connections, they can check whether any of those connections go to IP ranges known to be operated by bulletproof providers.
The challenge is obtaining and maintaining current information about bulletproof hosting IP ranges. These providers actively rotate IP addresses and use sophisticated techniques to obscure their ownership. But threat intelligence companies track these ranges continuously. Organizations can subscribe to threat feeds that provide updated lists.
DNS analysis examines which domains resolve to bulletproof-hosted infrastructure. If a domain resolves to an IP address operated by a bulletproof provider, that's suspicious. Legitimate organizations rarely use bulletproof hosting. The presence of a domain pointing to bulletproof infrastructure suggests either a compromised system or an intentionally malicious domain.
Historical attack correlation traces attacks that have been publicly analyzed or reported to determine which infrastructure they used. If you find attack infrastructure from a known ransomware operation, and that infrastructure shows the same characteristics as systems identified in the research (identical hostnames, specific template patterns), then you can infer that your organization may be targeted by the same threat actor.
Threat intelligence sharing allows organizations to benefit from research conducted by other companies and security firms. When researchers identify bulletproof infrastructure associated with specific attacks, that information gets published in threat intelligence reports. Organizations can subscribe to these reports and learn about infrastructure they should monitor for.
File hash correlation examines malware samples and infrastructure artifacts used in attacks. If a ransomware sample connects to a specific infrastructure set, researchers might extract that information and share it. Organizations can check whether they've observed similar patterns in their own network.
External vulnerability scanning checks for systems that might be vulnerable to the same exploitation methods used to compromise bulletproof infrastructure. If attackers are using specific exploitation techniques against shared infrastructure, organizations can check whether they're vulnerable to similar techniques.
Incident response log analysis reviews past breaches or detected intrusion attempts to see whether attackers used bulletproof infrastructure. If an organization detected an intrusion but wasn't able to fully scope the damage, examining what infrastructure the attackers used might reveal that they were leveraging bulletproof hosting, which provides intelligence about the threat actor's profile and capabilities.
The challenge with all of these detection methods is that they're reactive. You're looking for infrastructure that's already been identified and publicly disclosed. By the time infrastructure becomes well-known enough to track, the threat actors may have already moved to new infrastructure.
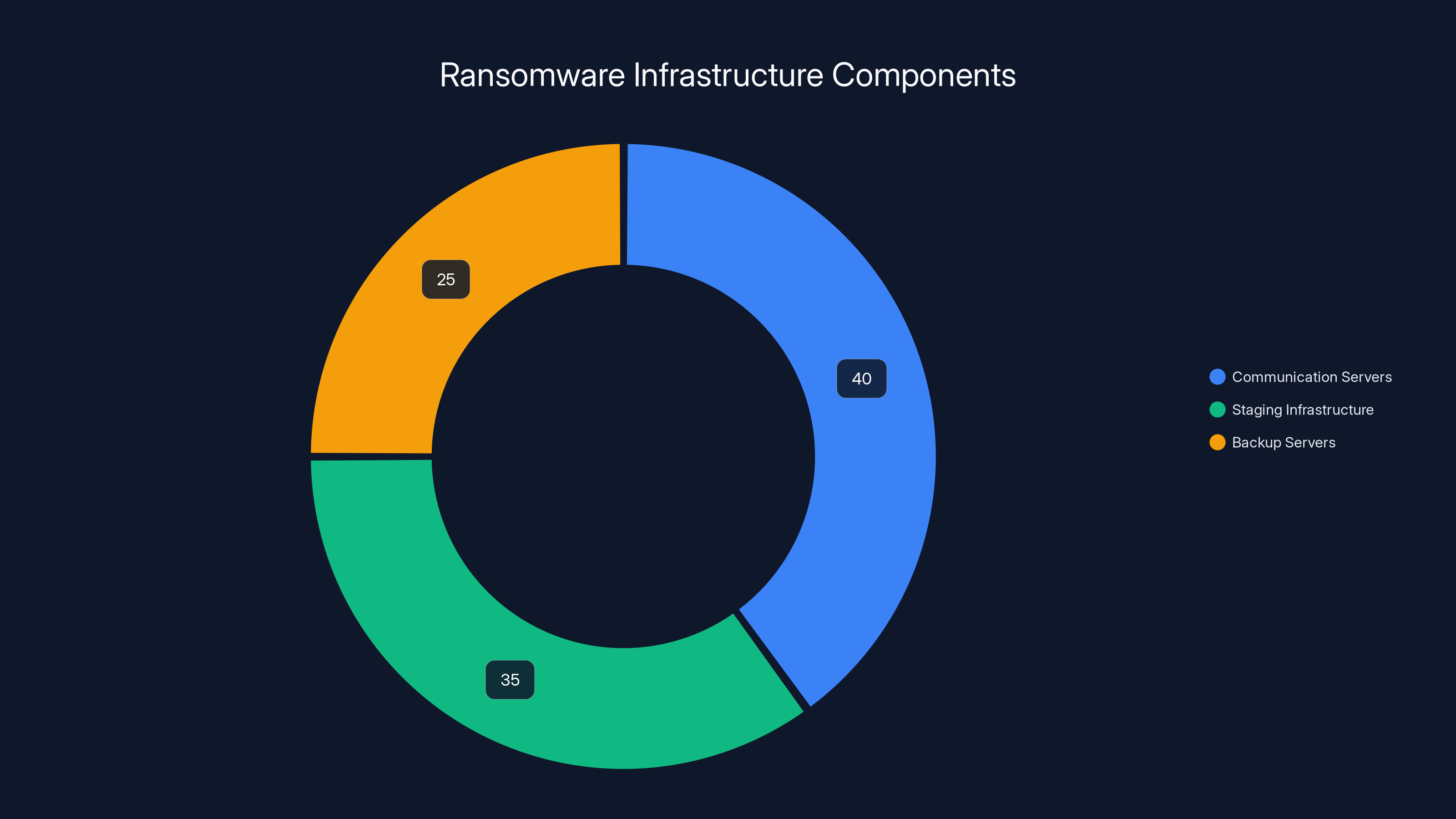
Estimated data shows that communication servers make up the largest portion of ransomware infrastructure, followed by staging infrastructure and backup servers.
Defensive Strategies Against Bulletproof-Hosted Threats
Detection is helpful but incomplete. Organizations need defensive strategies that work regardless of where attackers host their infrastructure.
Network segmentation limits an attacker's ability to move laterally after establishing initial access. If an organization segments its network into isolated zones, an attacker compromising a system in one zone can't automatically move to the others. This doesn't prevent the initial compromise, but it prevents the escalation that makes ransomware attacks profitable.
Credential hygiene prevents attackers from using stolen credentials to maintain access. If an organization regularly rotates credentials, uses multi-factor authentication, implements conditional access policies, and monitors for abnormal credential usage, then even if an attacker compromises one account, they can't sustain long-term access.
Endpoint detection and response (EDR) tools monitor systems for malicious behavior regardless of where the command-and-control infrastructure is located. The attacker's infrastructure might be bulletproof, but the malware running on your systems still has to do something malicious. EDR tools watch for that activity.
Data exfiltration prevention limits the damage even if an attack succeeds. If an organization implements strict controls on data movement, monitors for unusual data access patterns, and requires approval for large data transfers, then even if ransomware operators gain access, they might not be able to steal data, which eliminates the double-extortion component of their attack model.
Backup redundancy ensures that even if ransomware encrypts primary systems, recovery is possible without paying ransom. The most critical defensive measure against ransomware is ensuring that backups exist, are regularly tested, and are isolated from primary systems so they can't be encrypted alongside production data.
Threat intelligence integration means that when the latest bulletproof hosting research is published, the organization can incorporate that intelligence into their detection tools. If your EDR platform knows that certain infrastructure sets are associated with ransomware, it can flag any connections to those sets as high-priority.
Email filtering and URL rewriting prevents the initial compromise that would give attackers access in the first place. Since most ransomware campaigns start with phishing emails, preventing those emails from reaching users, sandboxing suspicious links, and monitoring for malicious attachments stops the chain before it begins.
Security awareness training is underrated but critical. Many ransomware campaigns rely on social engineering to get users to click malicious links, download files, or open documents with embedded macros. Training users to be skeptical of unexpected emails, to verify sender identities, and to report suspicious messages reduces the attack surface significantly.
The theme connecting all of these strategies is that they're infrastructure-agnostic. They work whether attackers use bulletproof hosting, legitimate hosting providers, or their own data centers. The specific infrastructure doesn't matter. The defensive principles remain consistent.

The Broader Implications for Cybercrime Economics
The bulletproof hosting revelation shows that modern cybercrime follows predictable economic patterns. Threat actors optimize for cost, reliability, and operational security. Bulletproof hosting providers offer an economical solution that hits all three factors.
But the research also shows that this economic efficiency creates vulnerabilities. The optimization that makes bulletproof hosting cost-effective (using identical templates, centralizing infrastructure, operating at scale) simultaneously creates the fingerprints that make infrastructure detectable and correlatable.
It's a fundamental tension. You can't build cost-effective large-scale infrastructure without introducing patterns. You can't introduce patterns without creating signature characteristics. You can't create signature characteristics without enabling detection.
This suggests that while bulletproof hosting will continue to be used, the economics of ransomware will gradually shift. As infrastructure becomes more difficult to hide, threat actors will either need to invest in more sophisticated operational security (which increases costs) or accept higher operational risk (which reduces profitability).
Law enforcement has also learned that focusing on major infrastructure providers is more effective than hunting individual attackers. Shutting down or disrupting a major bulletproof hosting provider cuts off multiple threat actors simultaneously. This creates incentive for law enforcement agencies to cooperate internationally and target infrastructure chokepoints.
The sanctions on Stark Industries and First Server Limited suggest this approach is already happening. By sanctioning major infrastructure suppliers, Western governments make it harder for their customers to do business, even if enforcement against individual criminals remains limited.
Sanctions and International Law Enforcement Response
The EU and UK sanctions against Stark Industries Solutions and First Server Limited represent a strategic shift in how Western governments approach cybercrime. Rather than pursuing individual ransomware groups, they're targeting the infrastructure enablers.
Sanctions work by restricting access to financial systems, preventing legitimate businesses from dealing with sanctioned entities, and creating legal liability for anyone who helps a sanctioned company. In theory, this makes it impossible for a company to operate if it's sanctioned by major economic powers.
In practice, a company explicitly operating to support cybercriminals can circumvent sanctions. They don't rely on legitimate business relationships, so financial restrictions have limited impact. They don't need legitimate banking relationships, so they can operate through cryptocurrency, which doesn't respect sanctions. They operate from countries that protect them, so diplomatic pressure is limited.
Nevertheless, sanctions create friction. They make it harder to expand operations, they increase operational costs, they complicate supply chains, and they create legal liability for legitimate companies that might consider doing business with sanctioned entities.
More importantly, sanctions represent official acknowledgment that these companies are state-adjacent or state-supported. The research suggested that both companies had connections to Russian state-sponsored activity. Sanctions publicly confirm those connections, making it clear to everyone that these aren't rogue private companies, but extensions of state power.
This has broader implications for cybercrime enforcement. If bulletproof hosting providers are effectively state actors or state-sponsored entities, then attacks using that infrastructure might be attributable to specific nations. A ransomware attack using Stark Industries infrastructure could be framed as an attack by the entity that operates or protects Stark Industries, rather than as a purely criminal matter.
International law enforcement has also increased cooperation. The research that identified bulletproof infrastructure connections was collaborative, involving multiple countries and multiple organizations. When the FBI, CISA, Europol, and national law enforcement agencies coordinate on ransomware investigations, they can share intelligence about infrastructure, enabling faster identification and disruption of attacks.
The challenge is that international law enforcement still can't directly disrupt infrastructure operated from protected jurisdictions. But they can disrupt it at the edges. They can prosecute individual affiliates who use bulletproof hosting. They can seize cryptocurrency payments. They can pursue civil litigation against infrastructure customers. They can work with legitimate companies to monitor connections to known bulletproof infrastructure.
Future Evolution of Bulletproof Hosting Infrastructure
As detection methods improve and law enforcement increases pressure, bulletproof hosting infrastructure will evolve. The specific providers identified in the research might be disrupted, but the business model will persist because it's fundamentally economical.
We'll likely see three major trends. First, increased decentralization. Rather than relying on two major providers, ransomware gangs will split infrastructure across dozens of smaller providers, accepting higher operational complexity in exchange for reduced single points of failure.
Second, improved operational security. Bulletproof providers will stop using identical templates, will randomize hostnames, will rotate infrastructure more frequently, and will generally implement better practices to avoid the fingerprinting that made their current infrastructure so detectable.
Third, geographic diversification. Infrastructure will be distributed across more jurisdictions, making international law enforcement coordination harder. Rather than concentrating infrastructure in a few major data centers, providers will use smaller operations scattered globally.
The common thread is that threat actors will continue to demand cheap, reliable, unmonitored infrastructure. They'll get it, because the economics of providing it are too favorable. A bulletproof hosting provider can generate significant income from small monthly fees across thousands of customers, with minimal operational overhead.
But each defensive evolution by bulletproof providers increases the costs they pass to customers, which reduces profitability for threat actors. The result is a gradual escalation where ransomware becomes more expensive to conduct, even as the fundamental infrastructure remains available.
Organizations should view bulletproof hosting not as a crisis point but as a persistent threat landscape feature. The infrastructure will exist. Threat actors will use it. Detection and defense must adapt accordingly.
Case Study: Attribution Through Infrastructure Analysis
Let's examine a real example of how bulletproof infrastructure analysis helped attribute attacks. When researchers identified that a specific ransomware campaign was using infrastructure from Stark Industries Solutions, they could trace multiple attacks to the same threat actor group.
The key insight was that while the attacker changed the actual server IP addresses regularly (rotating infrastructure to avoid detection), the underlying characteristics remained consistent. All of the servers used identical Windows templates. All had the same hostname patterns. All were located in bulletproof hosting networks with minimal security controls.
When a second attack emerged weeks later in a completely different geographic region and targeting an entirely different industry, security analysts could check whether the infrastructure characteristics matched the earlier attack. If they did, they could conclusively attribute the attacks to the same group, even though the surface details were completely different.
This infrastructure-based attribution is more reliable than behavioral attribution, which looks at attack patterns and tactics. Two different groups might use similar tools and techniques. Two different groups are unlikely to accidentally use infrastructure from the exact same bulletproof hosting provider with identical template characteristics.
The analysis revealed that the group was more active, more prolific, and more diverse in its targeting than previously understood. Once researchers recognized the infrastructure pattern, they could identify dozens of attacks that had previously been analyzed as separate incidents. This allowed the security community to develop more comprehensive threat profiles, identify vulnerabilities in common victim infrastructure, and issue targeted warnings to at-risk organizations.
For the organizations being attacked, this meant that when they received threat intelligence linking their incident to known bulletproof infrastructure, they could understand that they weren't random victims. They were part of a systematic campaign by a group that was actively developing and improving its attack methodology. That understanding should inform their response and recovery efforts.

Key Defensive Metrics and Monitoring
Organizations serious about defending against bulletproof-hosted threats should establish specific metrics and monitoring targets.
Outbound connection monitoring should track any connections to known bulletproof hosting IP ranges. This can be automated through firewall and proxy logging, with alerts triggered whenever a system attempts to communicate with suspicious infrastructure.
C2 detection should look for patterns of regular communication between internal systems and external infrastructure at odd hours or in large volumes, which would indicate command-and-control communication.
Data exfiltration monitoring should track unusual data movement patterns, particularly large transfers to external IP addresses, unusual geographic locations, or suspicious protocols.
Credential attack detection should flag multiple failed login attempts, unusual access times, access from impossible geographic locations, or attempts to enumerate user accounts.
Encryption activity monitoring should watch for processes attempting to access and modify large numbers of files in rapid succession, which would indicate ransomware activity.
Network persistence mechanisms should be monitored for signs of backdoors, scheduled tasks, startup entries, or other persistence methods that would allow attackers to maintain access across reboots.
The goal isn't to catch ransomware in the moment of encryption (by then it's often too late), but to identify the compromise as early as possible, preferably during reconnaissance or initial compromise phases when response is most effective.
The Role of Threat Intelligence Platforms
Despite the focus on technical detection, much of the protection against bulletproof-hosted threats comes from threat intelligence. Understanding which infrastructure is currently bulletproof, which companies are operating it, which threat actors are using it, and which organizations are at risk requires continuous intelligence gathering.
Commercial threat intelligence platforms like those offered by major cybersecurity companies now include specific data about known bulletproof hosting infrastructure. This data includes IP ranges, hosting providers, associated domains, and historical attack campaigns that used the infrastructure.
For organizations that can't hire dedicated threat intelligence analysts, subscribing to these platforms might be more cost-effective than trying to develop this intelligence internally. The feeds are continuously updated, the analysis is conducted by specialists, and the data is integrated with detection tools automatically.
Open-source intelligence gathering is also possible. Security researchers publish their findings regularly. Threat intelligence sharing communities like MISP (Malware Information Sharing Platform) allow organizations to share and access compromise indicators. Tools like Shodan and Alien Vault OTX provide accessible ways to query for infrastructure characteristics.
The key is integrating threat intelligence into operational processes. Intelligence that isn't used to inform detection, response, or recovery efforts is academic exercise. Intelligence that drives specific changes to firewall rules, monitoring thresholds, detection logic, and incident response procedures provides actual security value.
Organizational Risk Assessment Framework
Not all organizations face equal risk from bulletproof-hosted ransomware. A framework for assessing organizational risk can prioritize defensive investments.
Criticality assessment evaluates whether the organization is a likely target. Critical infrastructure operators, healthcare organizations, major financial institutions, and large enterprises are higher-value targets. Small businesses and non-critical operations are lower-value targets.
Financial assessment determines whether the organization is likely to pay ransom. Organizations with strong liquidity, cyber insurance, and low tolerance for operational downtime are more likely to pay, making them more attractive targets. Organizations with limited funds, self-insured risk models, and operational flexibility are less attractive.
Security posture assessment evaluates current defensive capabilities. Organizations with strong backup and recovery capabilities, network segmentation, EDR tools, and security monitoring are harder targets, which makes them less attractive despite potentially higher payoff.
Data sensitivity assessment determines whether the organization has data valuable enough to support double-extortion attacks. Organizations with trade secrets, sensitive personal information, or proprietary information are at higher risk than organizations with primarily public information.
The result of this assessment should drive defensive priorities. Organizations that assess as high-risk should invest heavily in detection, response, and recovery capabilities. Organizations that assess as lower-risk might focus on foundational security practices without specializing in ransomware defense.
All organizations, regardless of assessed risk, should maintain basic defensive hygiene: backups, multi-factor authentication, security awareness training, and system patching. The marginal investments beyond those fundamentals should be driven by risk assessment.

FAQ
What is bulletproof hosting?
Bulletproof hosting is a business model where hosting providers explicitly refuse to cooperate with law enforcement, respond to abuse reports, or enforce acceptable-use policies. These providers rent infrastructure (servers, virtual machines, IP addresses) to customers who want to conduct activities without risk of infrastructure shutdown. The hosting providers don't care what customers do with the infrastructure, as long as payment is received. This enables ransomware groups, malware operators, and other cybercriminals to maintain reliable command-and-control infrastructure without worrying about disruption.
How do ransomware groups benefit from bulletproof hosting?
Ransomware groups benefit from bulletproof hosting through three mechanisms. First, the cost is dramatically lower than legitimate hosting, reducing operational expenses from
Why do identical Windows templates create problems?
Identical Windows templates create a fingerprint that makes it trivially easy to identify and correlate related infrastructure. If 95% of a bulletproof hosting provider's virtual machines come from the same template with identical hostnames, system configurations, and security settings, then researchers can search for these distinctive characteristics using tools like Shodan and instantly find thousands of related systems. This correlation reveals that seemingly independent attacks are actually part of the same infrastructure, enabling attribution and threat actor profiling that would be impossible if infrastructure were truly diverse.
How can organizations detect bulletproof-hosted infrastructure in their networks?
Organizations can detect bulletproof-hosted infrastructure through several methods. Shodan searches can identify servers with distinctive bulletproof hosting characteristics. Network telemetry analysis can identify connections to known bulletproof hosting IP ranges. Threat intelligence feeds provide updated lists of bulletproof infrastructure. DNS analysis identifies suspicious domains resolving to bulletproof infrastructure. Historical attack correlation links current compromises to known bulletproof-hosted campaigns. The challenge is that most of these methods are reactive, identifying infrastructure that's already been publicly disclosed rather than catching new infrastructure as it's deployed.
What should my organization do if we detect connections to bulletproof hosting infrastructure?
Detecting connections to bulletproof infrastructure indicates either a compromised system within your organization or a legitimate system misconfigured to connect to suspicious infrastructure. First, immediately isolate the system to prevent further communication with the external infrastructure. Second, analyze the system's logs to determine when the connection started, what data it accessed, and what other systems it communicated with. Third, check whether other systems show similar connections or characteristics. Fourth, engage incident response and law enforcement if a breach is suspected. Finally, conduct network-wide scanning to identify whether the bulletproof infrastructure connection is isolated to a single system or indicates broader compromise.
Why haven't law enforcement agencies shut down bulletproof hosting providers?
Law enforcement can't shut down bulletproof hosting providers because they operate in jurisdictions with weak cybercrime enforcement or active protection from host governments. Stark Industries Solutions and First Server Limited, identified in the research as major infrastructure suppliers, operate with apparent state protection despite EU and UK sanctions. International law enforcement can sanction these companies, pursue their individual customers, and coordinate to disrupt infrastructure at the edges, but they can't directly shut down providers operating from protected jurisdictions. The economic incentive for these providers is also substantial, with potential revenues in the millions annually from relatively minimal operational overhead.
How will bulletproof hosting infrastructure evolve as detection improves?
As detection methods improve, bulletproof hosting infrastructure will likely become more decentralized (distributed across many smaller providers rather than concentrated in a few large ones), more operationally secure (randomizing hostnames, rotating infrastructure more frequently, avoiding distinctive fingerprints), and more geographically distributed (using data centers across more jurisdictions to complicate international law enforcement coordination). These defensive evolutions will increase operational costs for both bulletproof providers and their ransomware customers, potentially making large-scale ransomware campaigns more expensive to conduct. However, the fundamental business model will persist because the demand for cheap, reliable, unmonitored infrastructure remains consistent.
What's the connection between bulletproof hosting and state-sponsored activity?
The research identified that major bulletproof hosting providers like Stark Industries Solutions and First Server Limited have connections to Russian state-sponsored activity and have been sanctioned by the EU and UK accordingly. This suggests that bulletproof hosting operates not as independent criminal enterprise but as state-adjacent infrastructure. The implications are significant: attacks using bulletproof-hosted infrastructure might be attributable to specific nation-states rather than purely criminal groups. International law enforcement can pursue diplomatic pressure and sanctions against these entities more aggressively than they could against purely criminal providers. The state connection also explains why these providers continue operating despite sanctions and law enforcement pressure, they have state resources and protection behind them.
Should my organization subscribe to threat intelligence services to monitor for bulletproof hosting threats?
Yes, subscribing to threat intelligence services that include bulletproof hosting infrastructure data is likely cost-effective for most organizations. The alternative is developing in-house expertise to track bulletproof providers, conduct Shodan searches, analyze network logs, and maintain awareness of the latest infrastructure used by threat actors. For organizations without dedicated security personnel, threat intelligence platforms provide access to this expertise at a reasonable cost. For organizations with mature security programs, threat intelligence platforms provide validation and supplementary data to internal intelligence efforts. Even for large organizations, subscribing to multiple platforms provides defense-in-depth by aggregating data from multiple sources.
Conclusion
The revelation that major ransomware operations rely on infrastructure from just a handful of bulletproof hosting providers represents both a significant vulnerability in cybercrime infrastructure and a critical alert for defensive strategists.
On the offensive side, the consolidation of ransomware infrastructure on bulletproof hosting providers enabled massive scaling of attacks, rapid operational tempo, geographic distribution, and redundancy that would otherwise be prohibitively expensive. The economics are compelling. When infrastructure costs drop from
But the same consolidation created the fingerprints that enable detection and attribution. Because 95% of this infrastructure comes from identical templates with identical hostnames and configurations, researchers can identify and correlate thousands of systems instantly. What was supposed to be hidden becomes visible. What was supposed to be distributed reveals its centralized nature. What was supposed to be anonymous becomes traceable.
On the defensive side, the key insight is that bulletproof hosting infrastructure, while persistent, creates detectable patterns. Organizations shouldn't assume that ransomware actors have perfect operational security. They shouldn't assume that detecting infrastructure connections is impossible. They should implement monitoring, threat intelligence integration, and detection capabilities that specifically watch for connections to known bulletproof hosting providers.
More broadly, the research shows that cybercrime follows economic logic. Threat actors optimize for cost, reliability, and operational security. Understanding those economic drivers helps predict where threats will come from, how infrastructure will evolve, and what defensive investments provide the highest return.
The sanctions on major bulletproof hosting providers represent a strategic shift toward targeting infrastructure rather than individual threat actors. This approach is more effective because disrupting infrastructure affects all downstream customers simultaneously. It also enables attribution to specific nations and state-adjacent entities, which potentially allows for stronger diplomatic and economic responses.
For organizations, the practical implications are clear. Monitor for connections to bulletproof hosting infrastructure. Subscribe to threat intelligence that provides current data on bulletproof providers. Implement detection tools that watch for malicious behavior regardless of infrastructure source. Maintain backups that ensure recovery is possible even if attacks succeed. And understand that while bulletproof hosting will continue to evolve, the fundamental characteristics that enable detection won't disappear, because the same factors that make bulletproof hosting cost-effective (scale, template-based deployment, centralized management) simultaneously create the fingerprints that enable identification.
The game between attackers and defenders continues. The attackers got a cheap, reliable infrastructure supply chain. The defenders got a roadmap to finding them. In the long term, that roadmap might matter more.
Key Takeaways
- Bulletproof hosting provides ransomware gangs cheap, reliable, unmonitored infrastructure at 10x lower cost than legitimate providers
- 95% of bulletproof-hosted infrastructure comes from identical Windows templates with identical hostnames, creating detectable fingerprints
- Major ransomware operations including LockBit, Conti, BlackCat, and Qilin all rely on infrastructure from Stark Industries Solutions and First Server Limited
- The same economic factors that make bulletproof hosting attractive to threat actors simultaneously create vulnerabilities that enable detection and attribution
- Organizations can detect bulletproof infrastructure connections through Shodan searches, network monitoring, threat intelligence feeds, and behavioral analysis
Related Articles
- FBI Seizes RAMP: The Collapse of Ransomware's Last Stronghold [2025]
- Qilin Ransomware Gang Hits Tulsa Airport: What You Need to Know [2025]
- RedDVS Phishing Platform Takedown: How Microsoft Stopped a $40M Cybercrime Operation [2025]
- Major Cybersecurity Threats & Digital Crime This Week [2025]
- FBI Seizes RAMP Cybercrime Forum: What Happened & What It Means [2025]
- Inside Pig Butchering Scam Compounds: How Forced Labor Fuels Cybercrime [2025]
![Bulletproof Hosting & Ransomware: How Cybercriminals Exploit Virtual Machines [2025]](https://tryrunable.com/blog/bulletproof-hosting-ransomware-how-cybercriminals-exploit-vi/image-1-1770318978562.jpg)



