Red DVS Phishing Platform Takedown: How Microsoft Stopped a $40M Cybercrime Operation [2025]
Last year, a pharmaceutical company got hit with a Business Email Compromise (BEC) attack that cost them $7.3 million. A residential condo association lost nearly half a million dollars. Thousands of individuals had their credentials compromised. All of it traced back to one platform: Red DVS.
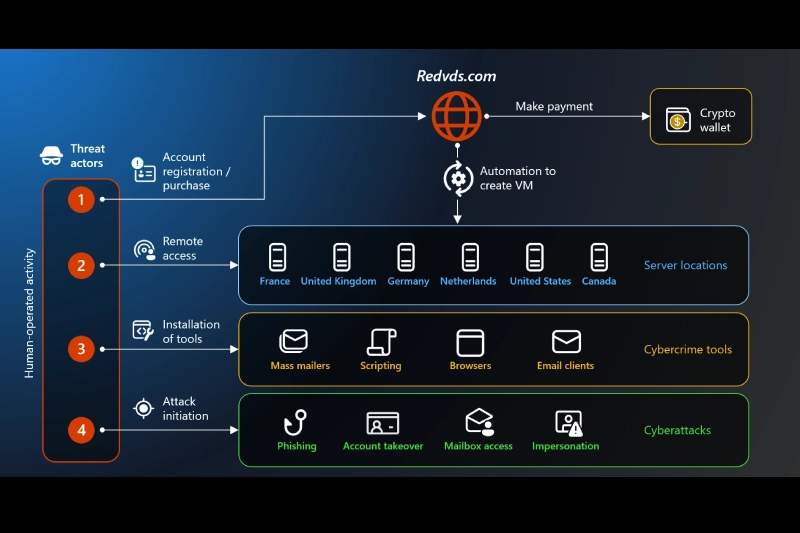
Here's the thing about cybercrime infrastructure—it's usually invisible until it isn't. Red DVS operated quietly for years, renting disposable virtual Windows servers to criminals for as little as $24 per month. That's cheaper than Netflix. For less than the cost of a streaming subscription, bad actors could spin up cloud computers, launch phishing campaigns at scale, and disappear before anyone caught them.
But in a coordinated operation that took months of investigation and cooperation across multiple nations, Microsoft, Europol, and German law enforcement finally shut it down. They seized servers, disrupted the criminal ecosystem, and exposed how modern cybercrime actually works at scale.
What's fascinating—and frankly terrifying—is that Red DVS wasn't some dark web legend. It was operating openly, marketing itself like a legitimate service. Yet for years, it remained one of the most effective tools in the cybercriminal arsenal. Understanding how it worked, why it was so effective, and how it was finally dismantled gives us critical insight into the current threat landscape.
This isn't just a story about one takedown. It's about how cybercriminals have industrialized fraud, how artificial intelligence has made attacks more convincing, and what defenders are actually doing about it.
TL; DR
- Red DVS was a cheap virtual desktop service allowing criminals to rent disposable Windows servers for just $24/month, making phishing and fraud scalable and hard to trace
- **The platform caused at least 7.3M)
- Microsoft, Europol, and German police dismantled the infrastructure by seizing servers across the US and Europe in a coordinated international operation
- Criminals used AI to create phishing emails, deepfakes, and voice cloning to make attacks more convincing and successful
- Red DVS sent over 1 million phishing emails monthly, compromising approximately 200,000 Microsoft customers in less than six months
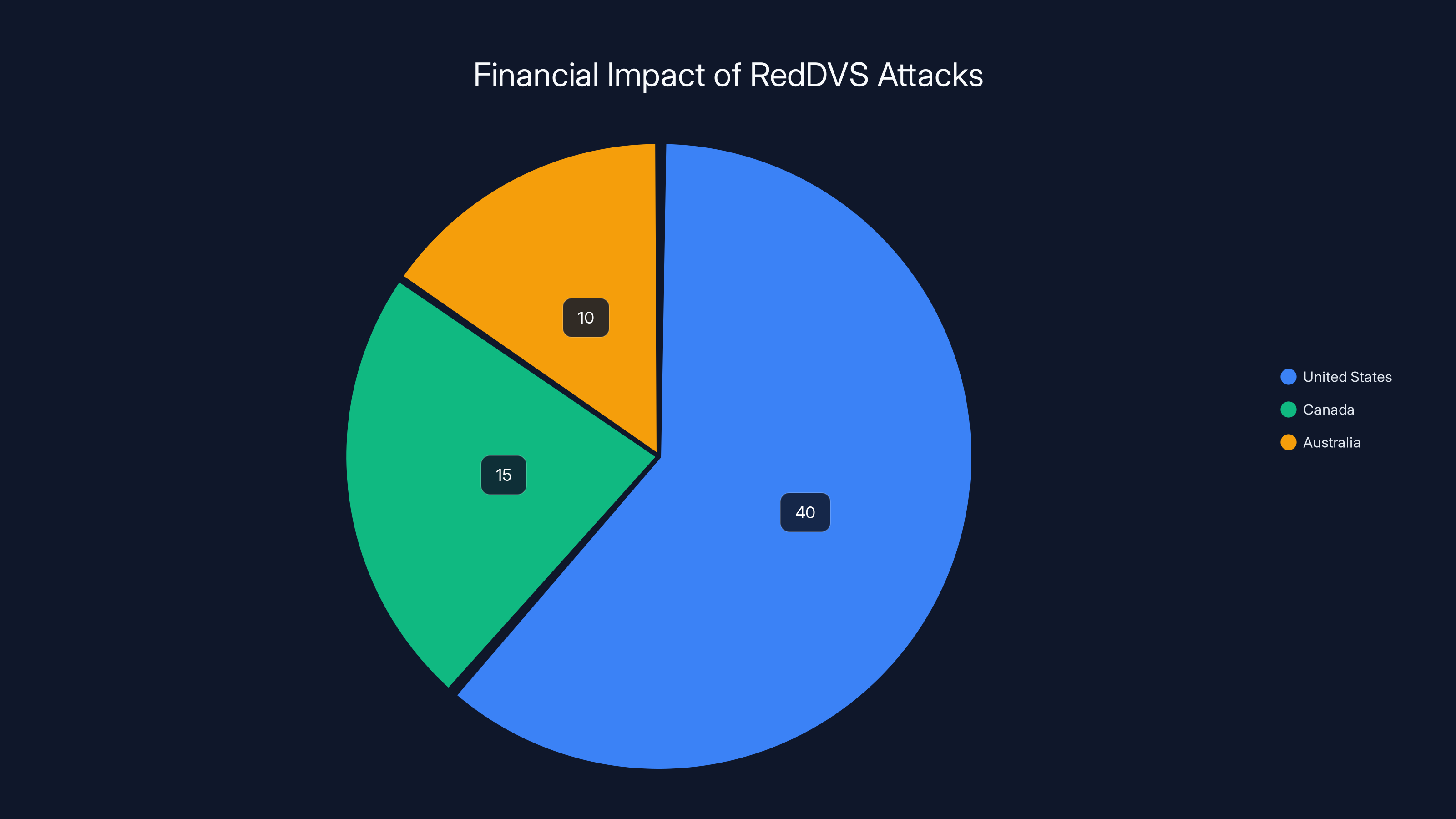
The United States experienced the highest financial impact from RedDVS attacks, with estimated losses of
What Red DVS Actually Was: A Disposable Server Rental Platform for Criminals
Let me paint you a picture of how Red DVS worked, because understanding the mechanics is essential to understanding why it was so dangerous.
Red DVS wasn't a hacking tool. It wasn't sophisticated malware or some zero-day exploit. It was something far simpler and far more effective: a rental service. Think of it like Hertz for criminals—except instead of renting cars, they were renting virtual computers in the cloud.
For $24 a month, a criminal could access a fully functional Windows virtual machine hosted on infrastructure spread across the United States and Europe. These weren't generic VMs. They all came from the same Windows Server 2022 image, which meant they had identical configurations, fingerprints, and characteristics. This standardization was actually a vulnerability that Microsoft researchers would later exploit to track and identify infected machines.
But for the criminals using the service, this setup had enormous advantages. First, it gave them legitimate cloud infrastructure without needing to steal credentials or hack into anything. Second, it provided geographic flexibility—they could rent servers with IP addresses located in the target's home country, making it look like emails were coming from local networks. This bypassed geolocation-based security filters that many organizations had deployed.
Think about what that means for a phishing attack. If your security system flags emails coming from overseas IP addresses, a criminal could just rent a server with a local IP address and send from there. The email would pass authentication checks. It would appear to come from a legitimate location. The target would have no reason to be suspicious.
The platform rented infrastructure from hosting providers across North America and Europe. This meant there was no central point of failure, no single server location that law enforcement could easily shut down. The infrastructure was distributed, resilient, and designed—whether intentionally or accidentally—to be difficult to dismantle.
What made Red DVS so effective wasn't complexity. It was simplicity. It solved a specific problem for criminals: how do I get reliable, legitimate-looking infrastructure for less money than I'd spend on a cup of coffee per day?
The Criminal Ecosystem That Built Around Red DVS
Here's what most cybersecurity articles miss: Red DVS wasn't a standalone tool. It was part of an entire criminal ecosystem with specialized roles and services.
Red DVS provided the infrastructure. But criminals needed other tools to make their attacks work. They needed email sending services, credential harvesting kits, social engineering templates, and—increasingly—artificial intelligence tools to make their attacks convincing.
The sophistication of the attacks using Red DVS infrastructure is what really caught security researchers' attention. Criminals weren't just sending generic phishing emails. They were leveraging generative AI to create highly personalized, contextually relevant phishing messages that passed even trained security awareness.
They were using deepfake technology to create fake videos of executives authorizing wire transfers. They were using voice cloning to create synthetic audio that sounded exactly like company leadership. And they were orchestrating all of this using affordable cloud infrastructure rented from Red DVS.
One particularly effective attack pattern involved Business Email Compromise (BEC). Here's how it typically worked:
- Attacker rents a Red DVS server with a local IP address
- Attacker sets up an email that spoofs an executive (or uses a legitimate compromised account)
- Attacker uses AI to generate a convincing message requesting an urgent wire transfer
- Attacker sends the message to finance or accounting staff
- Staff process the transfer without additional verification
- Attacker moves money through multiple accounts and disappears
The H2-Pharma case is instructive here. This wasn't some random phishing email hitting random targets. This was a sophisticated, targeted attack that cost the company $7.3 million. The attackers knew who to target, what kind of requests would seem legitimate, and how to social engineer the right people.
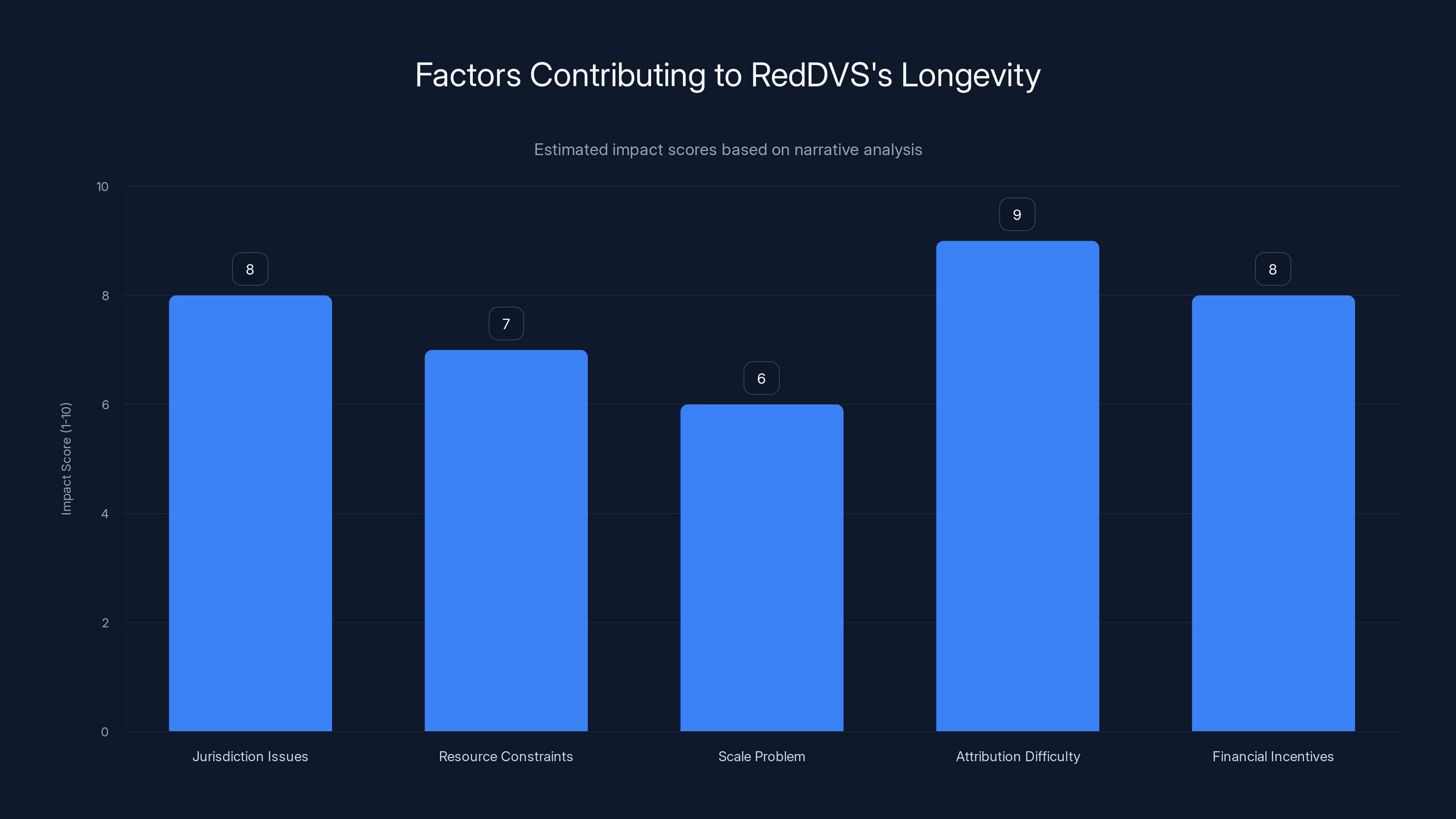
Jurisdiction issues and attribution difficulty were major factors in RedDVS's prolonged operation, each scoring high on impact. Estimated data.
The AI Advantage: How Criminals Made Phishing More Effective
Traditional phishing emails were easy to spot. They had grammar errors. They asked for obviously sensitive information. They looked like they were written by non-native speakers. Any security-aware person could recognize them.
Then AI changed everything.
Criminals using Red DVS infrastructure started leveraging generative AI tools to craft phishing messages that were nearly indistinguishable from legitimate corporate communications. They were grammatically perfect. They referenced specific projects the target was working on. They used the right level of technical terminology. They created urgency in the right way.
The impact on compromise rates was dramatic. When Microsoft researchers analyzed the Red DVS campaigns, they found that AI-generated phishing emails had significantly higher click-through rates and credential harvesting success rates compared to traditionally written phishing.
But it wasn't just email. Criminals were using AI for:
Deepfake video creation: Creating fake videos of executives authorizing transactions, making fraud seem legitimate to suspicious employees.
Voice cloning: Generating synthetic audio that sounded exactly like company executives, allowing criminals to conduct phone-based social engineering attacks.
Social engineering template generation: Using AI to analyze previous successful social engineering campaigns and generate new variations that were even more effective.
Credential harvesting page creation: Automatically generating fake login pages that matched the exact visual design and behavior of legitimate services.
This combination—affordable infrastructure plus AI-powered social engineering—created a perfect storm. Criminals could scale their attacks to thousands of targets simultaneously, with each attack customized and personalized, making them far more effective than generic phishing campaigns.
The numbers prove it. Red DVS customers were sending over 1 million phishing emails monthly just to Microsoft users. They were compromising approximately 200,000 accounts in less than six months. That's not random volume. That's targeting at scale with high success rates.
The Financial Impact: $40 Million and Counting
Let's talk about the actual damage Red DVS caused, because the numbers are staggering.
Microsoft concluded that across the United States alone, Red DVS facilitated losses of at least $40 million in 2025. That's just one year. And that's just the US. In Canada and Australia combined, more than 9,000 customers were scammed.
But the aggregate number doesn't capture the actual human impact. Let's break down some specific cases:
H2-Pharma:
Gatehouse Dock Condominium Association: Almost $500,000 in residential funds compromised. This wasn't a corporation with robust fraud detection. This was a residential community where staff members were social engineered into moving money.
These aren't outliers. These are representative of the scale of damage being done. And Microsoft's $40 million figure is almost certainly conservative. It only includes cases that were:
- Identified and reported
- Traced back to Red DVS infrastructure
- Quantified with specific numbers
Most fraud goes unreported. Many victims don't know they've been compromised until months later. And even when they do report, attributing the attack specifically to Red DVS infrastructure required forensic analysis that most organizations weren't equipped to perform.
The real number is probably two to three times higher. It might be $100 million or more globally.
Let's put this in perspective. The damage caused by Red DVS in one year exceeded the annual budgets of most small to mid-sized security firms. It exceeded what most companies spend on cybersecurity in a decade. And it was all facilitated by a service that charged criminals less than $30 per month.
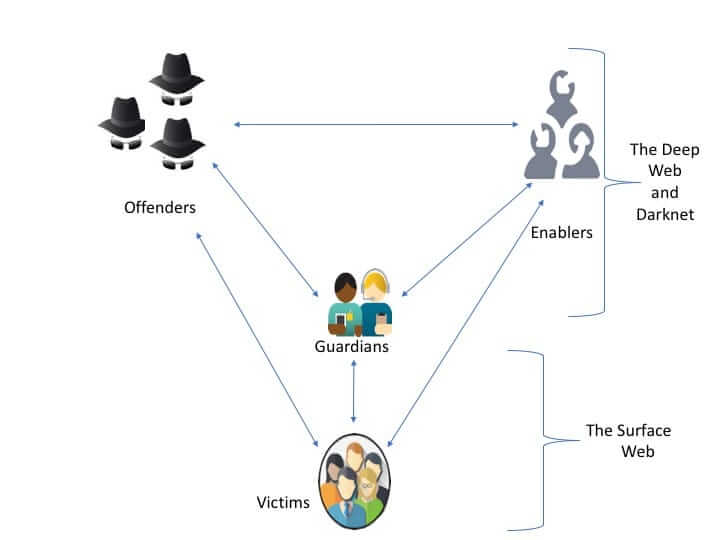
How the Investigation Worked: Tracking a Distributed Infrastructure
Here's where the story gets interesting from a technical perspective. How do you take down a distributed infrastructure that's designed to be resilient and anonymous?
Microsoft researchers started with a curious observation: all Red DVS virtual machines came from the same Windows Server 2022 image. This meant they had identical fingerprints—the same system files, same registry entries, same configuration details. In a way, this standardization was a flaw. It created a unique signature that could be tracked across the internet.
Researchers began identifying machines running Red DVS software by looking for that distinctive fingerprint. They tracked which hosting providers were hosting these servers. They identified IP address ranges. They documented the relationships between different hosting providers.
This is painstaking forensic work. Imagine trying to identify every counterfeit phone in the world just by looking at the serial numbers. That's roughly what Microsoft researchers were doing, except with virtual machines spread across hundreds of hosting providers.
But they had another advantage: they could see where the attacks were coming from. Every phishing email, every credential harvesting attempt, every malware distribution campaign using Red DVS infrastructure left digital breadcrumbs. Researchers could trace those breadcrumbs back to specific servers, specific IP addresses, and specific hosting providers.
They partnered with Europol, the European law enforcement agency coordinating international police operations. They worked with German police, who had jurisdiction over some of the hosting providers. They coordinated with law enforcement in the United States.
The operation—apparently codenamed as part of a larger initiative called "Operation Endgame"—involved simultaneous actions across multiple countries. Servers were seized. Infrastructure was shut down. Data was collected.
What's remarkable is that this wasn't a secret dark web operation. Red DVS was operating relatively openly, marketing its services to criminals. It had websites. It had pricing pages. It had customer support. The criminal ecosystem was industrialized and professional.
Yet it still took months of investigation and international coordination to shut down. That tells you something about the complexity of cybercrime operations and the resources required to actually dismantle them.
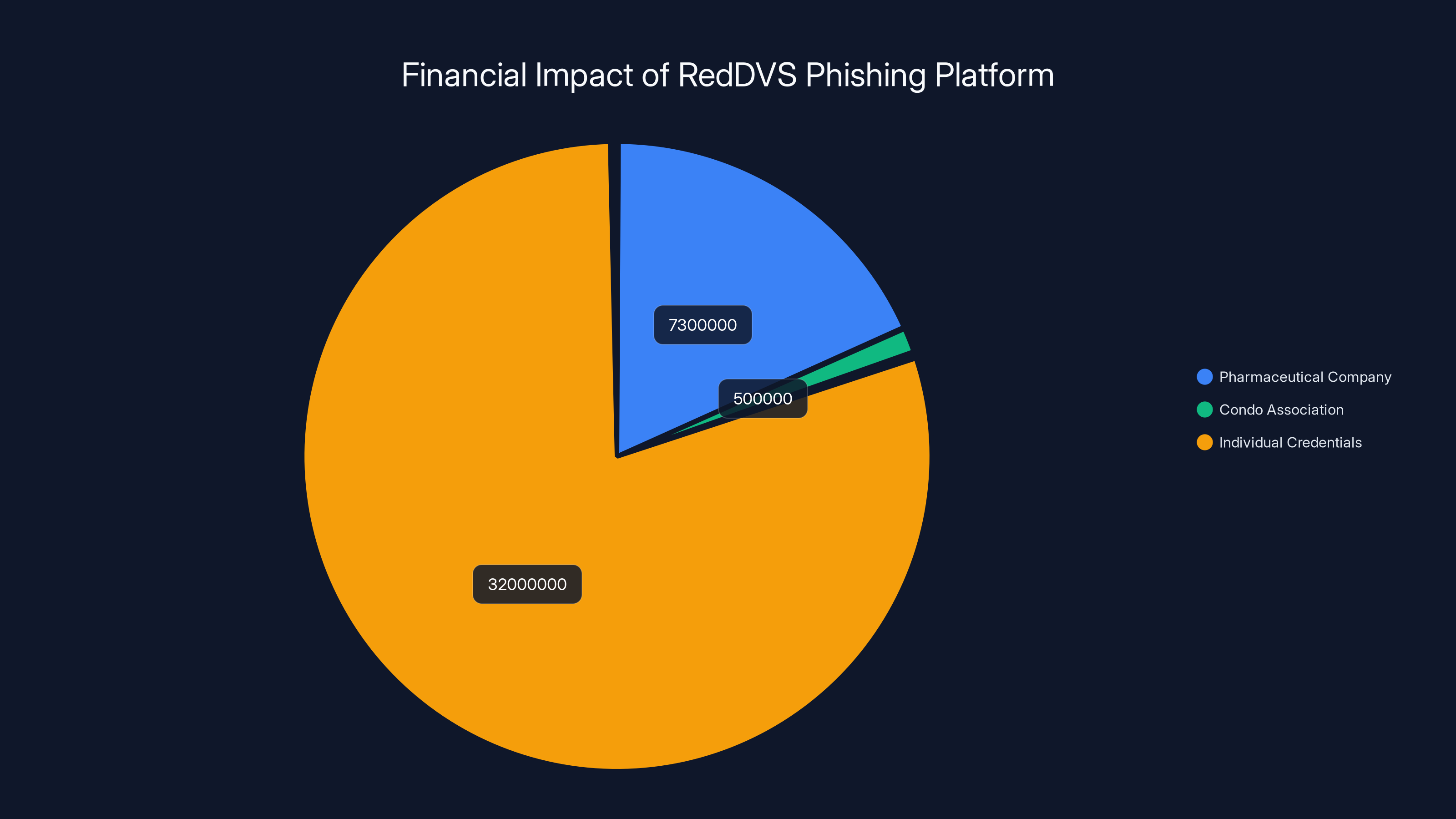
The RedDVS platform caused significant financial damage, with the largest impact on individual credential theft, estimated at $32 million. Estimated data.
The Role of Microsoft and Private Sector Intelligence
Microsoft wasn't conducting this investigation alone. They were working with law enforcement, but they were also acting as an independent investigator using their own technical capabilities and threat intelligence.
This is a crucial point that doesn't get enough attention: private companies are now essential to cybersecurity in ways that government agencies simply cannot match. Microsoft has access to telemetry from billions of devices worldwide. They see phishing emails, malware, credential attacks, and network reconnaissance attempts at a scale that no government agency can match.
Microsoft researchers could analyze Red DVS attack patterns, identify victims, track infrastructure changes, and document the evolution of the criminal operation. They had visibility that law enforcement would never have without corporate assistance.
But here's where it gets complicated. Private companies investigating cybercrime raises questions about oversight, jurisdiction, and the appropriateness of corporate entities acting as investigators. Who holds Microsoft accountable if they make a mistake? What if they accidentally implicate innocent parties in their investigation?
The fact that Microsoft brought in law enforcement—Europol and German police—suggests they understood these concerns. They didn't take action unilaterally. They coordinated with governments that had legitimate authority to seize infrastructure and conduct arrests.
But the reality is that without Microsoft's investigation and intelligence gathering, law enforcement probably wouldn't have had the information they needed to act. This public-private partnership is becoming the norm in cybersecurity, and it's worth thinking carefully about how it should work and what safeguards should be in place.

Business Email Compromise (BEC): The Attack That Made Red DVS Valuable
Business Email Compromise attacks are probably the most damaging attack type we face today, and Red DVS became the infrastructure of choice for scaling BEC operations.
Here's how BEC actually works, because it's important to understand why the traditional security model doesn't prevent it:
Most security tools are designed to stop malware. They scan for malicious code. They block known bad addresses. They look for suspicious behaviors. But BEC doesn't rely on malware. It relies on social engineering.
A BEC attack typically involves:
-
Reconnaissance: Attacker researches the target company, identifying key decision makers, organizational structure, financial processes, and ongoing projects
-
Email spoofing or compromise: Attacker either spoofs a legitimate email address or compromises a real account with valid credentials
-
Social engineering: Attacker sends an email that appears to come from a trusted source (usually an executive or someone in finance) requesting an urgent wire transfer
-
Urgency and legitimacy: The request references real projects or operations the target is aware of, creating a sense of legitimacy
-
Action: Target processes the wire transfer without additional verification
-
Money movement: Attacker moves funds through multiple accounts in different countries, making recovery nearly impossible
Red DVS infrastructure was perfect for this because:
- Local IP addresses: Criminals could rent servers with IP addresses in the target's country, bypassing geolocation filters
- Low cost: The minimal monthly fee meant attackers could run many parallel campaigns without significant expense
- Scalability: With hundreds of servers available, attackers could target hundreds of companies simultaneously
- Anonymity: The distributed nature of the infrastructure made it difficult to trace attacks back to the attacker's actual location
- Flexibility: Attackers could quickly pivot to new hosting providers if one was discovered
The H2-Pharma case exemplifies this. Attackers targeted a pharmaceutical company, identified key finance personnel, and sent an email that appeared to come from company leadership. The email requested an urgent wire transfer, probably referencing a real acquisition, partnership, or supplier relationship. The finance staff, seeing what appeared to be a legitimate request from trusted company leadership, processed the transfer.
Only later did the company realize the request never came from actual leadership. By then, $7.3 million was gone.
BEC attacks are incredibly difficult to prevent because they don't exploit technical vulnerabilities. They exploit human nature—our tendency to trust authority, respond to urgency, and assume messages from familiar addresses are legitimate.
Malware Distribution Through Red DVS Infrastructure
Phishing and BEC attacks were only part of what Red DVS enabled. The infrastructure was also used for distributing malware at scale.
Malware distribution requires infrastructure that can:
- Host payloads: Store the malicious code files
- Serve downloads: Deliver files to infected machines
- Evade detection: Avoid being blocked by firewalls, proxies, and security appliances
- Provide anonymity: Hide the operator's actual location and identity
Red DVS provided all of these capabilities. A criminal could rent a server, upload malware, and distribute it through email links, drive-by downloads, or trojanized documents.
The distributed nature of Red DVS infrastructure was particularly valuable for malware distribution because it meant defenders couldn't simply block a single server. If one server got shut down, the attacker still had hundreds of others. If one IP address got blacklisted, the attacker could move to a different hosting provider.
Common malware families distributed through Red DVS infrastructure likely included:
- Infostealer malware: Software that steals passwords, browser history, and stored credentials
- Ransomware: Software that encrypts files and demands payment for decryption
- Remote access trojans (RATs): Software that gives attackers remote control of infected machines
- Banking trojans: Software specifically designed to steal banking credentials and intercept transactions
Each of these malware families requires distribution infrastructure. The traditional approach was to host malware on bulletproof hosting providers—hosting companies specifically designed to resist takedown attempts and ignore abuse complaints. These hosting providers were expensive and difficult to access.
Red DVS offered a cheaper alternative for attackers who didn't need the bulletproof hosting guarantee. For $24 a month, they could get legitimate infrastructure and distribute malware before the infrastructure was identified and shut down.

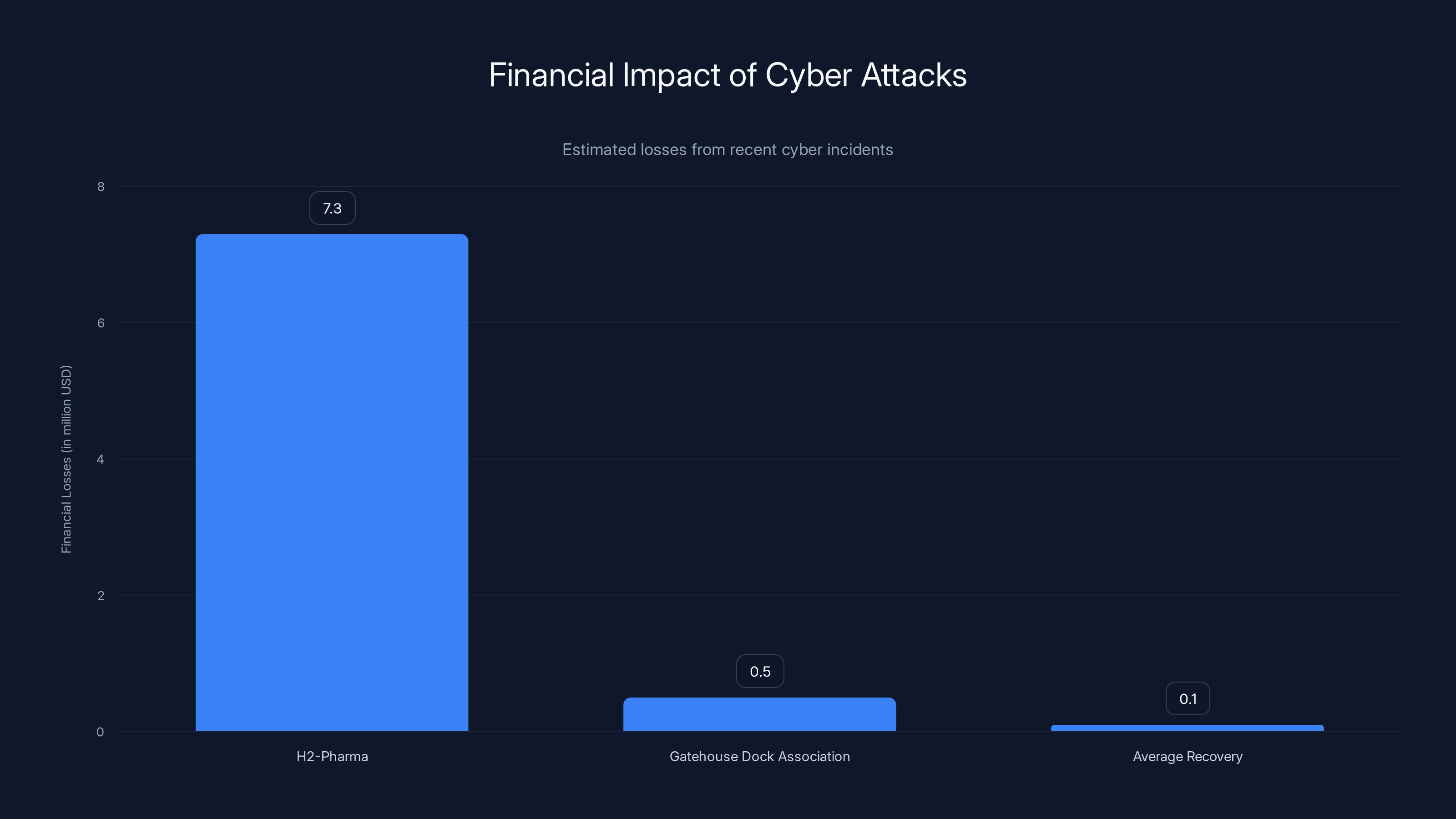
H2-Pharma and Gatehouse Dock Association suffered significant financial losses due to cyber attacks, with minimal recovery. Estimated data.
The Gatehouse Dock Case: How Fraud Reaches Residential Communities
When we think about cybercrime victims, we typically imagine large corporations or wealthy individuals. The Gatehouse Dock Condominium Association case is a reminder that fraud impacts communities and institutions we might not expect.
The attack cost the condo association almost $500,000 in resident funds. That's not a number a residential association can easily recover from. That money was probably earmarked for maintenance, repairs, community services. Now it's gone.
How does a cybercriminal compromise a condo association? The answer probably involves the same techniques: spear-phishing emails targeting property management staff, social engineering calls, compromised credentials. But once inside, the attacker has access to financial systems that might not have the same level of fraud detection as corporate systems.
Small to medium-sized organizations often don't have:
- Fraud detection software: Monitoring for unusual wire transfer patterns
- Multiple approval layers: Requiring multiple people to verify large transactions
- Anomaly detection: Flagging transfers to new vendors or unusual amounts
- Employee training: Security awareness programs that teach people to recognize social engineering
Residential associations, apartment complexes, HOAs—these organizations often operate on tight budgets with limited IT staff. They might use off-the-shelf accounting software without advanced fraud prevention. They might not have the security infrastructure that large corporations have.
Yet they hold resident funds. Thousands of people have money in association accounts, trusting that it will be used for community maintenance and improvements.
A $500,000 loss to a condo association might affect hundreds of residents who now face unexpected assessment increases or delayed maintenance projects. The impact cascades far beyond the direct victim.
This is an often-overlooked consequence of cybercrime: it doesn't just hurt the organizations that are directly attacked. It impacts everyone connected to those organizations—residents, customers, employees, families.
Security Implications: What This Means for Defenders
The Red DVS takedown offers several important lessons for anyone responsible for cybersecurity.
First, infrastructure matters more than you might think. Cybercriminals need legitimate infrastructure to operate at scale. They can't operate from their basements anymore. They need cloud servers, email sending capabilities, hosting providers. This creates chokepoints where they can be disrupted.
The question is: how much responsibility do hosting providers have for the criminal use of their infrastructure? Red DVS rented servers from legitimate hosting providers. Did those providers know they were renting to criminals? Probably not—but they also probably didn't ask hard questions.
There's a tension here between privacy (hosting providers shouldn't monitor every customer) and security (hosting providers shouldn't knowingly enable crime). Finding the right balance is an ongoing debate.
Second, AI is changing the threat landscape in ways we don't fully understand yet. Criminals are using generative AI to make social engineering more effective. They're using deepfakes to create convincing videos. They're using voice cloning to impersonate executives.
Defenders are still figuring out how to detect AI-generated content at scale. We don't have good tools for identifying synthetic audio or video. Our security awareness training is built around traditional phishing, not AI-generated social engineering.
This is a gap we need to close quickly, because the attackers are moving faster than we are.
Third, the incident response and recovery process is broken. H2-Pharma lost
Once money is transferred through multiple accounts in different countries, recovery is nearly impossible. Law enforcement can investigate and arrest the perpetrators, but the money is gone. Victims are left holding the bag.
This suggests we need to focus more on prevention and less on prosecution. If we can't recover stolen money, we need to make sure it doesn't get stolen in the first place.
Fourth, the need for international cooperation is non-negotiable. Red DVS infrastructure spanned the US and Europe. Taking it down required coordination between American companies, American law enforcement, German police, and Europol.
Not all countries prioritize cybercrime investigation. Not all law enforcement agencies have the technical expertise. Building the relationships and institutional capacity to respond to international cyber incidents takes time and resources. But without it, criminals will continue operating across borders with impunity.

Preventative Measures: How Organizations Can Protect Themselves
Assuming organizations actually want to prevent Red DVS-style attacks, what should they do?
Email authentication is non-negotiable. SPF (Sender Policy Framework), DKIM (Domain Keys Identified Mail), and DMARC (Domain-based Message Authentication, Reporting, and Conformance) are technical standards that make email spoofing much more difficult. They're not perfect, but they're vastly better than nothing.
Here's the problem: most organizations have these tools available but don't properly configure them. They set SPF records but don't enforce them. They don't monitor DMARC reports. They treat email authentication as a "nice to have" rather than essential security infrastructure.
This is probably the single most effective thing an organization can do to prevent Red DVS-style phishing attacks. Full stop.
Multi-factor authentication (MFA) on email and financial systems. If an attacker compromises a credential, MFA prevents them from actually accessing the account. This slows them down and gives the organization time to detect the compromise.
MFA isn't perfect—attackers can intercept MFA codes or use MFA bombing to overwhelm users—but it's significantly better than passwords alone.
Wire transfer controls. Organizations should require multiple approvals for wire transfers above a certain threshold. Different approvers should verify the request through separate channels (phone call, in-person, video call). New payees should require additional scrutiny.
These seem like obvious controls, but many organizations don't have them. Smaller organizations especially tend to operate on trust and assume fraud won't happen to them.
Employee training. Not security awareness training where employees watch a 10-minute video and then get tested. Real training that teaches people to recognize social engineering, understand urgency-based decision-making, and verify high-stakes requests through independent channels.
Good training takes time and needs to be reinforced regularly. Most organizations don't invest in it sufficiently.
Threat intelligence and incident response planning. Organizations need to know what attacks are happening in their industry. They need to have an incident response plan that's actually tested and rehearsed. They need to know who to contact if they suspect a compromise.
When an attack happens, the first 24 hours are critical. Organizations that have prepared in advance can respond quickly and minimize damage. Organizations caught off-guard often don't even realize they've been compromised until it's too late.
Monitoring and anomaly detection. Organizations should monitor financial transactions, email patterns, and user behavior for anomalies. When something unusual happens—a large wire transfer to a new payee, an executive sending emails at 3 AM from a new location, someone accessing the network from a new country—these should trigger investigation.
Anomaly detection is imperfect and requires tuning to avoid false positives. But it's better than assuming that your security controls will catch everything.
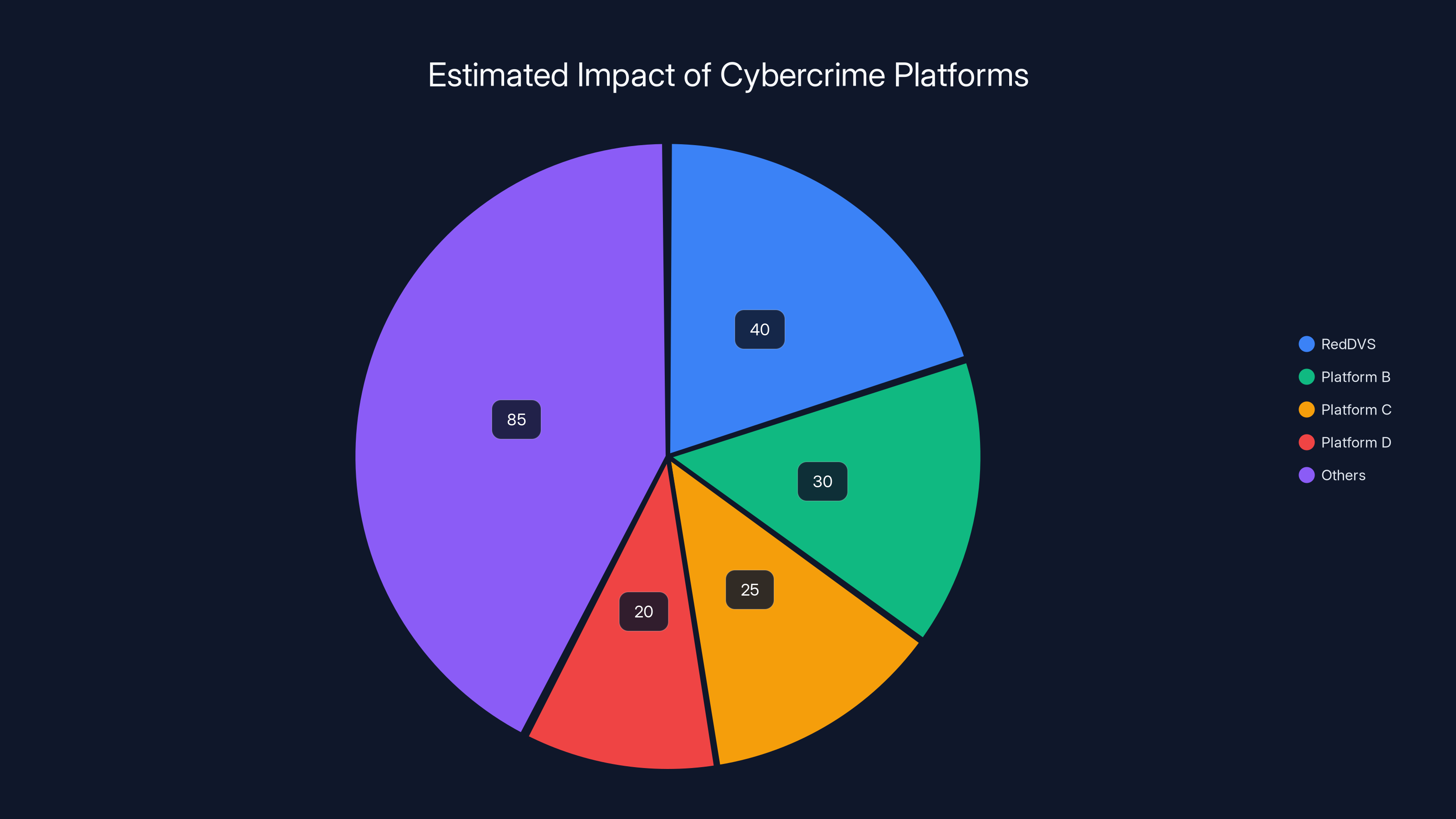
Estimated data shows RedDVS caused $40 million in damage, highlighting the broader impact of similar platforms, which collectively contribute to a significant portion of cybercrime damage.
The Broader Context: Why Red DVS Succeeded for So Long
One question worth asking: why did it take so long to dismantle Red DVS? It was operating openly, causing documented damage, using identifiable infrastructure. Why didn't law enforcement shut it down sooner?
The answer probably involves several factors:
Jurisdiction issues: Red DVS had infrastructure in multiple countries. Taking action requires coordination across different legal systems, which is slow and complicated.
Resource constraints: Law enforcement agencies investigating cybercrime are under-resourced. They have limited personnel with specialized technical expertise. They have to prioritize which cases to investigate.
The scale problem: There are thousands of criminal services operating at any given time. Red DVS was one of many. Without a specific victim with resources to pressure law enforcement, it might never have risen to the top of the priority list.
Attribution difficulty: Identifying who actually operates Red DVS is hard. The service itself is an infrastructure platform. The actual criminals using it are different people. Attributing specific crimes to specific operators requires investigation.
Financial incentives: Red DVS was profitable. It probably had hundreds of paying customers. The people operating the service had motivation to stay operational and were probably skilled at avoiding detection.
What probably changed is that enough victims complained, enough damage was documented, and enough pressure was applied that law enforcement and tech companies decided to act. The H2-Pharma case with its $7.3 million loss probably helped create the urgency needed to launch an investigation.
This is a frustrating reality of cybercrime: the victim sometimes has to make enough noise to get law enforcement's attention. If victims are quiet, if losses aren't reported, if companies don't pressure authorities, then criminals continue operating.
This creates a perverse incentive system where large, organized crime operations go unchecked while flashy attacks make headlines.
The Endgame Operation: Part of a Larger Takedown Campaign
The Red DVS takedown was apparently part of "Operation Endgame," a larger international effort to dismantle cybercriminal infrastructure. This operation has targeted multiple criminal services and platforms, including infostealer malware networks and bulletproof hosting providers.
What's interesting about Operation Endgame is that it represents a shift in how law enforcement approaches cybercrime. Rather than focusing on individual criminals, they're focusing on the infrastructure that enables crime.
This makes sense. Individual cybercriminals are sometimes hard to identify and prosecute. But the services they use—hosting providers, email services, credential markets—these are more discrete targets. Take down the infrastructure and you disrupt hundreds of criminals simultaneously.
But there's a challenge: criminal infrastructure is resilient. Take down one bulletproof hosting provider, and another one comes online. Dismantle one platform, and criminals move to another.
The question is whether Operation Endgame can stay ahead of the threat. Can law enforcement and tech companies identify criminal infrastructure faster than new infrastructure comes online? Or is this a whack-a-mole game that we'll be playing indefinitely?
The answer probably involves both attacking existing infrastructure and making it harder for new infrastructure to come online. That might mean:
- Better abuse reporting mechanisms: Making it easier for legitimate organizations to report abuse
- Hosting provider accountability: Holding hosting companies responsible for criminal use of their infrastructure
- Financial tracking: Following money flows to identify criminal operations
- International coordination: Better agreements between countries on how to handle cybercrime
- Technology improvements: Developing tools that make it harder for criminals to operate anonymously
All of these are being pursued to varying degrees. None of them are perfect solutions. But together they might be able to raise the difficulty level enough that it becomes harder for criminal services to operate.
The Future of Cybercrime Infrastructure: What Comes After Red DVS
The Red DVS takedown doesn't eliminate the problem it was solving. There's still demand for affordable, anonymous cloud infrastructure among criminals. New services will emerge to meet that demand.
But the takedown might shift how those services operate. Criminals might:
- Use even more distributed infrastructure: Multiple hosting providers, multiple countries, constantly rotating IP addresses
- Develop better obfuscation: Making it harder to identify criminal usage through forensic analysis
- Build custom infrastructure: Rather than relying on existing cloud providers, developing their own hosting capabilities
- Use legitimate services more carefully: Being more cautious about leaving forensic signatures that could be tracked
Defenders will need to evolve in response. This is an ongoing arms race with no definitive end state.
What seems likely is that cybercrime will become more expensive and more technically sophisticated. The days of cheap, disposable infrastructure might be ending. But the most organized criminals—those with the most resources and motivation—will find ways to continue operating.
The real issue is the gap between what it costs to conduct a cyber attack and what it costs to defend against it. Right now, offense is cheaper than defense. Criminals can rent infrastructure for $24 a month and cause millions in damage. Defenders have to invest in complex, expensive security solutions just to stay ahead.
Until that equation changes, cybercrime will remain a profitable activity, and new platforms like Red DVS will continue to emerge.

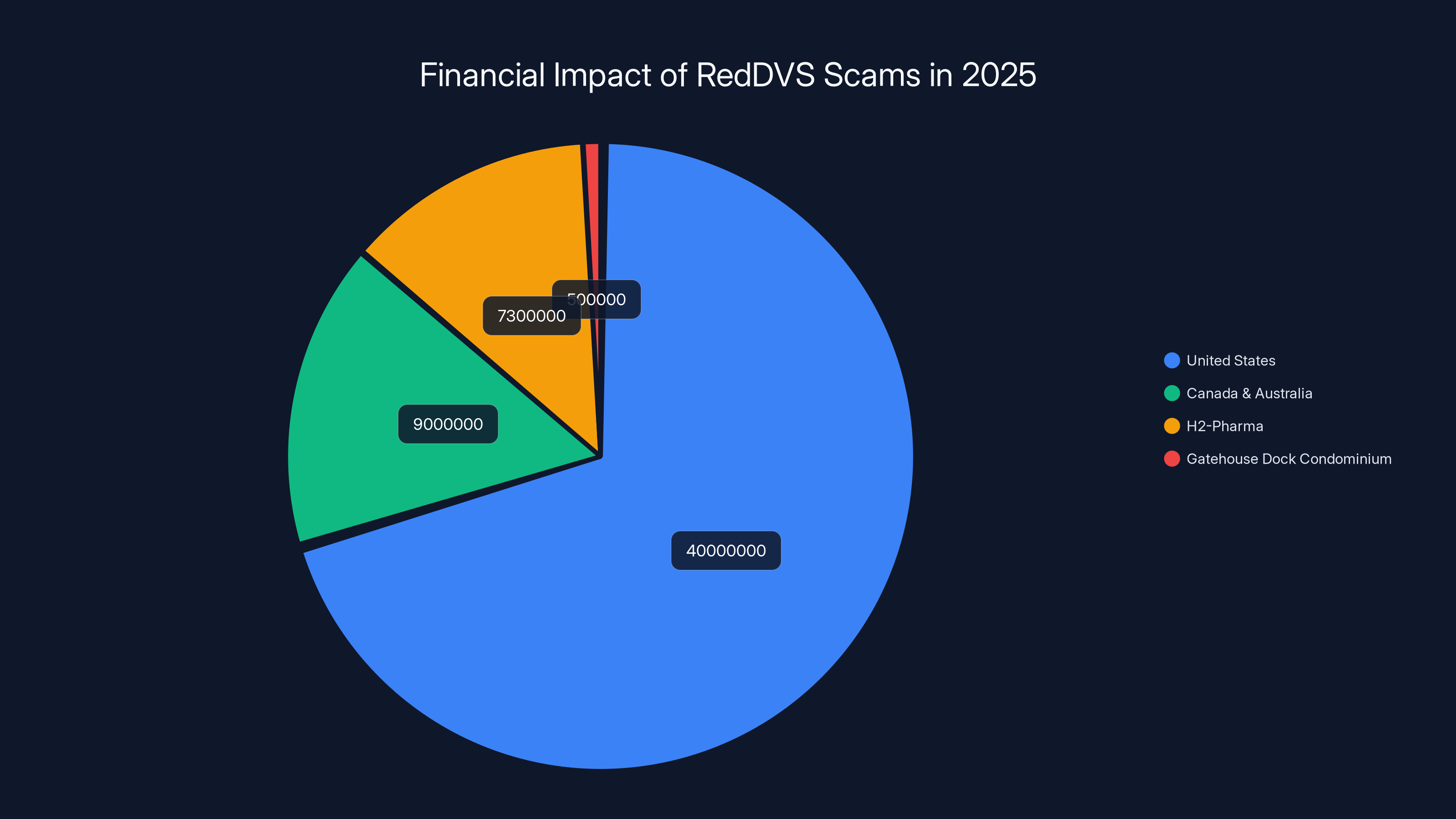
The pie chart illustrates the estimated financial impact of RedDVS scams in 2025, with the United States experiencing the highest losses at $40 million. Estimated data.
International Coordination and Law Enforcement Response
What's remarkable about the Red DVS takedown is how it required coordination across multiple countries and agencies. This operation involved:
- Microsoft's threat intelligence teams conducting forensic analysis
- Europol coordinating international law enforcement
- German police with jurisdiction over hosting providers
- US law enforcement investigating domestic impacts
- Private companies that were victims of Red DVS-facilitated attacks
This kind of coordination doesn't happen automatically. It requires:
Established relationships: Different agencies need to have worked together before and have existing protocols for information sharing.
Technical expertise: Law enforcement needs personnel who understand cybercrime infrastructure and can work with tech companies on complex investigations.
Legal frameworks: Different countries have different laws regarding data access, surveillance, and prosecution. Finding legal pathways to coordinate action requires careful legal work.
Political will: Cybercrime investigation takes resources away from other priorities. Both governments and tech companies need to prioritize it.
Victim cooperation: Often the initial evidence comes from victims who are willing to cooperate with investigators and allow their systems to be analyzed.
The Red DVS operation probably took months of preparation. Investigators had to:
- Identify that Red DVS infrastructure was involved in attacks
- Collect evidence linking Red DVS to specific crimes
- Identify the hosting providers and server locations
- Coordinate with those hosting providers and with law enforcement in relevant countries
- Prepare simultaneous takedown actions across multiple jurisdictions
- Execute the takedown operations while preserving evidence
- Transition seized infrastructure to law enforcement or shut it down completely
Every step has legal implications and requires coordination. It's not surprising that it took months or years to plan and execute.
The question going forward is whether this level of coordination can be sustained and scaled. If law enforcement can coordinate this effectively against multiple criminal platforms, it could significantly raise the cost of cybercrime operations. If coordination breaks down, criminals will continue operating with relative impunity.
Trust and Verification in Cybersecurity
One theme running through the Red DVS story is the importance of verification. Criminals use phishing emails that appear to come from trusted sources. They use spoofed IP addresses that appear to come from legitimate locations. They use AI-generated content that appears to be authentic.
Defenders need to verify more carefully.
The email authentication standards (SPF, DKIM, DMARC) are essentially verification mechanisms. They verify that an email actually came from the domain that claims to send it. They're not perfect, but they're vastly better than blindly trusting sender addresses.
Multi-factor authentication is another verification mechanism. It verifies that the person accessing an account is actually authorized to access it. Again, not perfect, but better than relying on passwords alone.
Wire transfer verification—calling someone on a known phone number to verify a transfer request—is a human-level verification. It's slow, but it works.
The pattern is clear: the more you verify, the harder you make it for attackers. The challenge is doing this in a way that doesn't create so much friction that legitimate operations become impossible.
This is the eternal tension in security: security versus usability. The most secure system is one that's disconnected from the network and requires multiple layers of verification for every action. But nobody can work efficiently in that environment.
Organizations need to find the right balance for their risk profile. High-value transactions need more verification. Routine operations can have less. But the default should be verification, not trust.
Lessons for Cloud Infrastructure Users
One overlooked lesson from the Red DVS case is what it means for legitimate users of cloud infrastructure.
Red DVS rented servers from legitimate hosting providers. Those hosting providers probably didn't know (or didn't actively confirm) that their servers were being used for criminal activity. But the infrastructure itself was standard, legitimate cloud infrastructure.
This raises questions:
Should hosting providers be more vigilant about criminal use of their infrastructure? Probably yes, but how? You can't realistically inspect every customer's activity. You have to balance customer privacy with abuse prevention.
Should legitimate cloud users be concerned about being compromised by criminal activity on shared infrastructure? Not much. Cloud providers use various isolation mechanisms to prevent one customer's activity from affecting another customer's security. But the existence of criminal operations on the same infrastructure is still troubling.
What responsibility do hosting providers have? This is genuinely unclear legally and ethically. Most hosting providers have terms of service that prohibit illegal activity. But enforcement is inconsistent.
For legitimate users, the lesson is probably to:
- Choose reputable hosting providers with strong abuse policies
- Monitor your own infrastructure for unauthorized activity
- Use authentication and authorization controls to ensure only authorized people can access your systems
- Monitor outbound traffic to ensure you're not unknowingly participating in attacks
- Cooperate with law enforcement if your infrastructure is compromised
The broader point is that infrastructure security is shared responsibility. Hosting providers, users, and law enforcement all have roles to play. None of them can solve the problem alone.
The Role of Ransomware and Extortion
While the Red DVS case focuses on phishing, BEC, and malware distribution, it's worth noting that ransomware is probably also a significant use case for Red DVS infrastructure.
Modern ransomware operations typically involve:
- Initial compromise (often through phishing)
- Lateral movement and persistence (establishing long-term access)
- Exfiltration (stealing data before encryption)
- Encryption (making data unusable)
- Extortion (demanding payment for decryption)
- Money movement (converting cryptocurrency to usable currency)
Red DVS infrastructure could be used at multiple stages of this process:
- Hosting phishing pages for initial compromise
- Hosting command-and-control servers for lateral movement
- Hosting ransom pages where victims pay for decryption
- Facilitating payment processing
The monetary damage from ransomware operations dwarfs the damage from traditional fraud. A single ransomware operation can cost organizations tens of millions of dollars. Multiple operations per year means that ransomware is responsible for more financial damage than BEC, phishing, and other attacks combined.
Taking down infrastructure that supports ransomware operations is just as important as taking down infrastructure supporting phishing or BEC. The Red DVS takedown probably disrupted ransomware operations even if that wasn't the primary focus of the investigation.

Attribution and Enforcement Challenges
One question that probably isn't addressed in public statements about the Red DVS takedown is: who was actually operating Red DVS? Were they arrested? Are charges being filed?
Attributing cybercrime to specific individuals is notoriously difficult. Red DVS was a platform—infrastructure that different criminals could use. The people operating the platform are different from the people using it for phishing, BEC, and other attacks.
Law enforcement would have to prove:
- Who created and owned Red DVS
- That they knew it was being used for criminal activity
- That they didn't attempt to prevent that criminal activity
- That they profited from the criminal activity
Proving all of this requires forensic analysis, financial records, and potentially cooperating witnesses. It's not trivial.
Further complicating things: Red DVS operators might be located in countries that don't have extradition treaties with the US or Europe. They might be protected by their home government. Even if arrested, prosecution might be slow or ineffective.
The fact that the operation focused on seizing infrastructure might indicate that law enforcement chose to disrupt the service rather than attempt to arrest and prosecute the operators. This is pragmatic but represents a partial success at best.
Compare this to the traditional criminal justice system, where prosecution is the goal. In cybercrime, disruption—shutting down the operation and seizing infrastructure—is often the most achievable outcome.
This has implications for deterrence. If criminals believe they can operate a service that causes millions in damage and the worst outcome is that their servers get seized and the service shuts down, the risk-reward calculation might still favor operating the service. They can rebuild, move to new infrastructure, and continue.
For law enforcement response to be truly effective, it would need to include successful prosecution of the operators. Without that, disruption is temporary.
Systemic Issues and Market-Level Problems
The Red DVS case highlights some systemic problems that go beyond any single law enforcement action:
The too-cheap-to-meter problem: Cloud infrastructure is so inexpensive that criminals can rent it in bulk. The $24/month price point means that a criminal organization can afford to rent hundreds of servers simultaneously. Even if some get shut down, they have many others.
Increasing prices would limit the problem, but it would also make legitimate cloud infrastructure more expensive for everyone.
The anonymity problem: Criminals can rent hosting using stolen identity information, cryptocurrency payments, or other anonymous methods. Knowing who actually rents a server is difficult, especially across different countries with different documentation requirements.
The globalization problem: Hosting infrastructure is distributed globally. A criminal in Russia can rent servers in the US. A criminal in the US can rent servers in Europe. Enforcement is difficult because it requires international coordination.
The too-big-to-dismantle problem: There's so much criminal activity happening simultaneously that law enforcement can't possibly address all of it. They have to choose which operations to investigate and prioritize. Criminals can operate under the radar unless they become high-profile.
The evolving-tactics problem: Criminals continuously adapt and evolve their techniques. By the time law enforcement has dismantled one platform, criminals have already moved to new approaches. It's a constantly-moving target.
These systemic problems don't have easy solutions. They're not something that can be solved by a single law enforcement operation or a single piece of technology. They require sustained effort, coordination, and continuous adaptation.

Looking Forward: Predictions for the Cybercrime Landscape
Based on the Red DVS case and broader cybercrime trends, what should we expect in the near term?
More sophisticated use of AI: Criminals will increasingly use AI for social engineering, deepfakes, and content creation. This will make attacks more convincing and harder to detect. Defenders will need better tools for identifying synthetic content.
Higher barriers to entry for amateur criminals: As defenses improve and law enforcement becomes more active, it will become harder for amateur criminals to operate. This might reduce the volume of attacks but increase the sophistication of remaining attackers.
Consolidation of criminal operations: Rather than thousands of independent criminals, we might see consolidation around a smaller number of sophisticated criminal organizations with the resources to survive law enforcement attention.
More focus on insider threats: As perimeter defenses improve, criminals might focus more on compromising insiders who can legitimately access systems and bypass controls.
Ransomware continuing to evolve: Ransomware will continue to be the most profitable attack vector. Criminals will experiment with new extortion approaches (targeting executives directly, targeting customers rather than the organization, etc.).
Geopolitical tensions influencing cybercrime: Nation-state actors and state-sponsored criminals will become harder to distinguish from regular criminals. Attribution will become even more difficult.
Cloud security becoming increasingly important: As more organizations move to cloud infrastructure, cloud-specific attacks will become more common. The focus on securing traditional on-premises infrastructure will shift to cloud-native security.
None of these predictions are radical or surprising. They're natural evolutions of existing trends. The important point is that cybercrime will continue to be a significant problem with no definitive solution in sight.
Recommendations for Organizations
If you've read this far, you're probably either in a security role or concerned about your organization's security. Here are concrete recommendations:
Do email authentication properly: Implement SPF, DKIM, and DMARC. Configure them correctly. Monitor DMARC reports. This is the single highest-ROI security control for preventing phishing.
Implement MFA broadly: Not just on email, but on every system that holds sensitive data or controls important processes. Make it mandatory, not optional.
Create real incident response capabilities: Not documentation that sits on a shelf, but actual capabilities that are regularly tested and practiced. Know who to call, what to do, and how to respond quickly.
Invest in security awareness training: Real training, not checkbox compliance. Teach people to recognize social engineering, understand urgency-based attacks, and verify important requests.
Implement financial controls: Multiple approvers for large transactions. Verification through separate channels. New payees get extra scrutiny. These are simple controls that catch a surprising amount of fraud.
Monitor for anomalies: Implement tools that flag unusual behavior—large transactions, new vendors, unusual access patterns, login attempts from new locations. Investigate these anomalies promptly.
Have a threat intelligence program: Know what attacks are happening in your industry. Subscribe to threat intelligence feeds. Participate in information sharing communities. Use this information to improve your defenses.
Backup everything regularly: Assume you'll be compromised at some point. Make sure you can recover from ransomware or data loss without paying ransom or suffering permanent data loss.
Establish a security culture: Make security everyone's responsibility, not just the security team's job. Leaders need to prioritize security, employees need to understand why it matters, and processes need to reflect security principles.
None of these are novel recommendations. They're fundamentals that most security frameworks include. Yet many organizations still don't implement them effectively. That's where the opportunity lies. Better execution of fundamentals prevents more attacks than searching for the next cutting-edge technology.

Conclusion: The Bigger Picture
The Red DVS takedown is important, not because it solved cybercrime or because it represents law enforcement's technical prowess, but because it illustrates the current state of the cybercrime-cybersecurity arms race.
Criminals have industrialized and professionalized. They operate like businesses, renting infrastructure, specializing in specific attack vectors, using AI to improve their success rates. They're organized, coordinated, and profitable.
Defenders are also improving, but they're playing catch-up. The cost asymmetry still favors attackers. The complexity of modern systems still creates exploitable vulnerabilities. The human element—social engineering, trust—remains a fundamental weakness.
The Red DVS operation shows that law enforcement and tech companies can work together to disrupt criminal infrastructure. But it also shows the limitations of this approach. Even with successful disruption, the underlying problems remain. Criminals will find new platforms. New services will emerge to fill the market gap.
What's needed is sustained pressure: continuous investigation of criminal infrastructure, international coordination between law enforcement agencies, technical innovations that make attacks harder, better defenses in organizations that are targets, and—importantly—better consequences for attackers who are actually caught.
The $40 million in damage from Red DVS in a single year is staggering. But it's just one platform. Multiply this by hundreds of other criminal services, and you get a sense of the scale of the problem.
The Red DVS takedown is a win. But the war is far from over. And the criminals who moved off Red DVS infrastructure have probably already migrated to the next platform.
The important thing is that law enforcement and tech companies keep moving, keep investigating, keep disrupting. Because if they stop, the criminals won't. And the damage will keep accelerating.
For organizations reading this, the message is clear: your defenses matter. They matter because law enforcement can't catch every criminal. They matter because even if a criminal platform is shut down, variants will emerge. Your organization's security—how well you implement email authentication, how thoroughly you monitor for anomalies, how quickly you respond to incidents—that's what actually protects you.
You can't rely on law enforcement to dismantle every criminal platform. You have to be prepared to defend yourself. And most organizations that do the fundamentals well—email authentication, MFA, anomaly detection, rapid response—are significantly harder targets than the easy victims that criminals prefer.
Make yourself a harder target. That's how you actually win this war.
FAQ
What is Red DVS and how did it work?
Red DVS was a cybercriminal platform that rented disposable virtual Windows servers to criminals for as little as $24 per month. It provided criminals with legitimate cloud infrastructure that was distributed across hosting providers in the US and Europe, allowing them to conduct phishing, business email compromise (BEC), and malware distribution attacks while evading detection through location-spoofing and anonymity.
How did Red DVS enable phishing and BEC attacks so effectively?
Red DVS worked by providing criminals with virtual machines that came from a standardized Windows Server 2022 image, allowing them to rent servers with IP addresses located in their targets' countries. This bypassed geolocation-based security filters and made emails appear to come from legitimate local networks. Criminals combined this with AI-generated phishing content to create highly convincing social engineering messages targeting finance and accounting staff with wire transfer requests.
What was the total financial impact of Red DVS?
Microsoft documented at least
How did law enforcement dismantle Red DVS?
Microsoft, Europol, and German police coordinated a complex international investigation that identified the distinctive fingerprints of Red DVS virtual machines, tracked the hosting providers hosting them across multiple countries, collected evidence of crimes facilitated through the platform, and executed simultaneous takedown operations to seize servers and shut down the infrastructure.
What role did artificial intelligence play in Red DVS attacks?
Criminals using Red DVS infrastructure leveraged generative AI to create grammatically perfect, contextually relevant phishing emails that were significantly more effective than traditional phishing. They also used AI for deepfake video creation, voice cloning to impersonate executives, face-swapping technology, and automated generation of social engineering content tailored to specific targets.
What can organizations do to prevent Red DVS-style attacks?
Organizations should implement proper email authentication (SPF, DKIM, DMARC), deploy multi-factor authentication on email and financial systems, establish wire transfer approval controls requiring multiple verifiers, invest in real security awareness training, monitor for anomalous financial transactions and user behavior, maintain regular backups, and develop incident response capabilities that are regularly tested and practiced.
How is the Red DVS takedown part of a larger law enforcement effort?
The Red DVS operation was part of Operation Endgame, a broader international effort targeting criminal infrastructure platforms including infostealer malware networks and bulletproof hosting providers. This represents a strategic shift in law enforcement approach—focusing on infrastructure that enables many criminals simultaneously rather than individual perpetrators.
Why was Red DVS able to operate for so long despite causing documented damage?
Red DVS succeeded because it operated relatively openly as a legitimate-appearing service, its infrastructure was distributed across multiple hosting providers making it difficult to completely dismantle, attribution of the actual operators was complex, law enforcement was resource-constrained and had to prioritize cases, and the service remained operational as long as new victims kept using it and the damage wasn't widely publicized.
What happens to Red DVS users and infrastructure now?
While the takedown seized Red DVS servers and infrastructure, attribution and prosecution of actual operators is unclear from public statements. However, the disruption forces criminals to migrate to new platforms or build their own infrastructure, raising their operating costs and complexity, and making them more likely to leave forensic traces that could lead to detection and prosecution.
What new criminal platforms might emerge to replace Red DVS?
Criminals will likely develop more distributed, harder-to-track infrastructure using even more countries and hosting providers, invest in custom infrastructure rather than relying on legitimate cloud providers, use better operational security to avoid leaving forensic fingerprints, and focus on harder-to-defend markets like smaller organizations and developing countries where security awareness is lower.

Key Takeaways
- RedDVS rented disposable virtual Windows servers to criminals for just $24/month, enabling phishing, BEC, and malware distribution at massive scale
- The platform facilitated at least $40 million in losses in the US alone in 2025, with individual BEC attacks costing companies millions
- Criminals used AI to generate convincing phishing emails, create deepfakes, and conduct voice cloning attacks that bypassed traditional security awareness training
- Microsoft identified RedDVS infrastructure through forensic analysis of identical Windows Server 2022 VM fingerprints and coordinated an international takedown with Europol and German police
- Organizations must prioritize email authentication, multi-factor authentication, wire transfer verification controls, and anomaly detection to prevent similar attacks
Related Articles
- ExpressVPN 78% Discount Deal: Complete Savings & Comparison Guide [2025]
- LinkedIn Comment Phishing: How to Spot and Stop Malware Scams [2025]
- UK Scraps Digital ID Requirement for Workers [2025]
- Iran Internet Blackout: What Happened & Why It Matters [2025]
- Instagram Password Reset Emails: What You Need to Know [2025]
- CISA Retires 10 Emergency Directives: What Changed for Federal Cybersecurity [2025]
![RedDVS Phishing Platform Takedown: How Microsoft Stopped a $40M Cybercrime Operation [2025]](https://tryrunable.com/blog/reddvs-phishing-platform-takedown-how-microsoft-stopped-a-40/image-1-1768473487563.jpg)



