Fake Moltbot AI Assistant Malware Scam: What You Need to Know [2025]
Introduction: When AI Dreams Turn into Nightmares
Last year, something unsettling happened in the developer community. A fake extension showed up on Microsoft's official VSCode marketplace, claiming to be an AI assistant called Claw Bot Agent. The icon looked professional. The description seemed legitimate. The integration list featured real AI providers like OpenAI, Anthropic, and Google. Everything about it screamed trustworthy.
But it wasn't.
Behind the polished interface lurked a fully functioning trojan, quietly waiting to compromise developers' systems. This wasn't just another malware campaign. It was a sophisticated, layered attack that exploited one simple fact: Moltbot, a popular open-source AI assistant, never actually released a VSCode extension. The criminals knew this. They counted on it.
Here's the thing about AI tool proliferation: growth creates opportunity, and not all of it's good. As more developers rush to integrate AI assistants into their workflows, they're becoming increasingly vulnerable to a new breed of supply chain attacks. These aren't random phishing emails. They're meticulously crafted fake tools that exploit your trust in legitimate platforms and your desire to stay productive.
This incident reveals something deeper about how we use AI today. We download extensions, install tools, and run assistants with deep system access without always verifying their authenticity. The attack was eventually detected and stopped, but not before potentially compromising countless users. The real danger isn't just the malware itself. It's the precedent it sets and the vulnerabilities it exposes in how we vet and trust AI tools.
In this comprehensive guide, we'll break down exactly what happened, why it matters, how the attack worked, and most importantly, how you can protect yourself from similar scams targeting AI enthusiasts and developers.

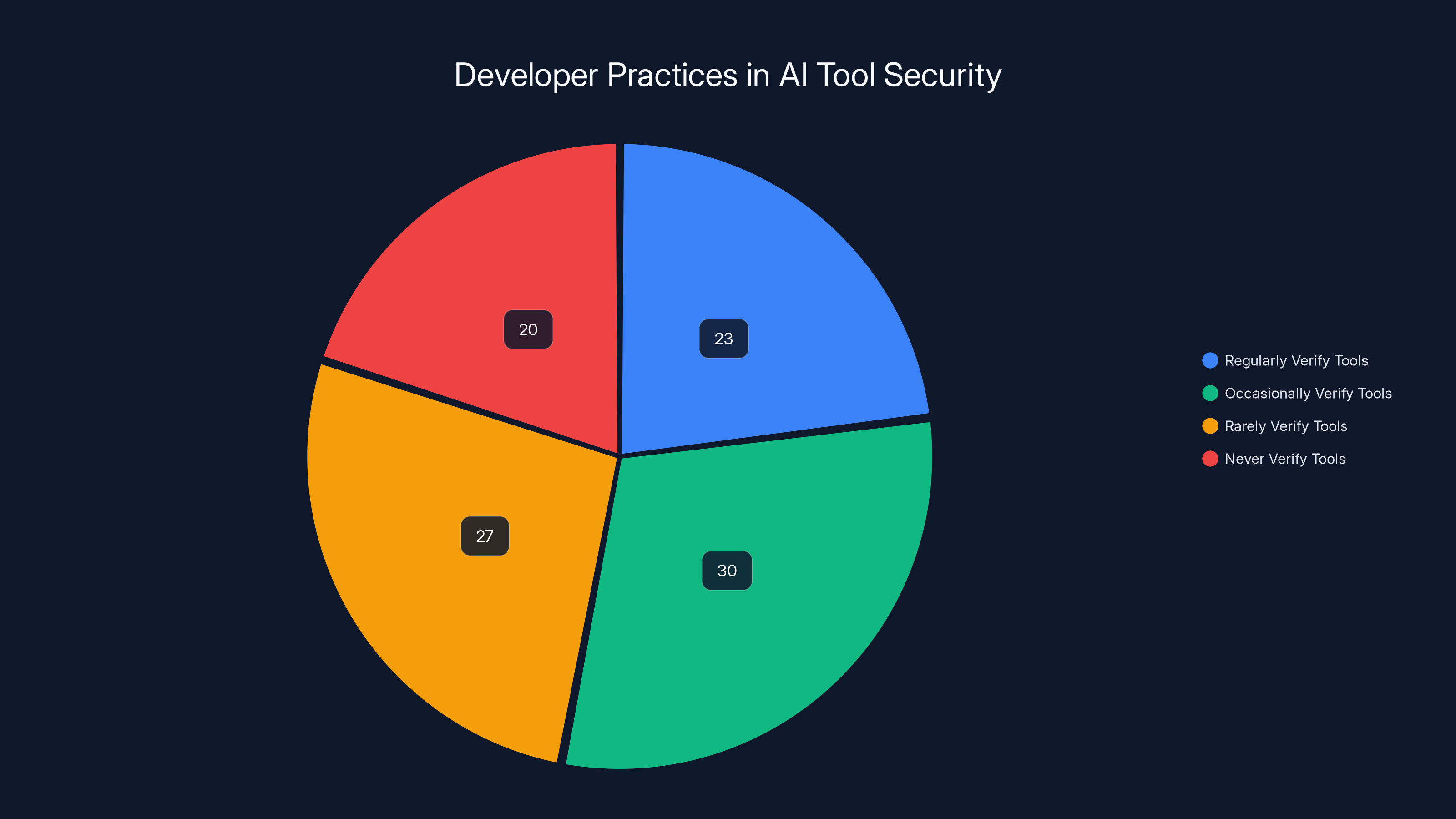
Estimated data suggests that only 23% of developers regularly verify the legitimacy of tools, highlighting a significant security gap. (Estimated data)
TL; DR
- The Attack: Hackers created a fake "Claw Bot Agent" extension on VSCode marketplace impersonating the legitimate Moltbot AI assistant, which never had an official extension
- The Payload: The malware carried a fully functioning trojan using remote desktop software and Rust-based backup loaders, capable of stealing data and controlling systems
- The Sophistication: The attack used multiple layers including fake AI integrations, legitimate-looking UI, and disguised payloads pretending to be Zoom updates
- Why It Happened: Moltbot's popularity (93,000+ GitHub stars) made it an attractive target, and the lack of an official extension created a perfect opportunity for impersonation
- How to Stay Safe: Verify extensions through official channels, check developer credentials, enable security warnings, and research tools before downloading
Understanding Moltbot: The Legitimate AI Assistant
What Is Moltbot and Why Does It Matter
Moltbot is an open-source personal AI assistant that runs locally on your computer or server, rather than relying on cloud-based alternatives. This is a crucial distinction because it means the application has deep system access to function properly. It lets users interact directly with large language models and automate various tasks without sending data to external servers.
The software was originally called Clawdbot but was rebranded to Moltbot to avoid trademark issues. Despite being relatively recent, it's gained significant traction in the developer community. At the time of the malware campaign, Moltbot had accumulated more than 93,000 stars on GitHub, making it one of the more popular open-source AI tools available. This popularity is both a feature and a vulnerability.
Because Moltbot runs locally with deep system access, security researchers have emphasized the importance of careful configuration. Misconfigurations can expose sensitive data, and the tool's privileged access makes it an attractive target for attackers. However, when used correctly, this local-first approach offers privacy benefits that cloud-based alternatives can't match.
Why Developers Trust Moltbot
Developers gravitate toward Moltbot for several practical reasons. First, it doesn't require cloud subscriptions or external API keys for basic functionality. Second, the fact that it's open-source means the entire codebase is publicly auditable, reducing the risk of hidden malicious code. Third, the local-first architecture appeals to privacy-conscious developers who don't want their code or conversations sent to third-party servers.
This trust, however, created a vulnerability. Criminals knew that many developers using Moltbot would welcome a VSCode extension to streamline their workflow. They also knew that the legitimate Moltbot team had never released an official VSCode extension. This gap between user expectations and actual product offerings became the perfect exploit vector.
The Current Status of Moltbot's Website
Interestingly, at the time of the malware discovery, Moltbot's own website was flagged as dangerous by security systems. This created additional confusion in the community. Some users saw warnings when trying to access the legitimate Moltbot website, while simultaneously a malicious extension was freely available on the official VSCode marketplace. The layering of these warnings made it harder for users to distinguish between legitimate concerns and false positives.
This situation highlights a critical problem: when legitimate projects get flagged alongside malicious ones, users often become desensitized to warnings. They might ignore security alerts on real websites because they've encountered too many false alarms.

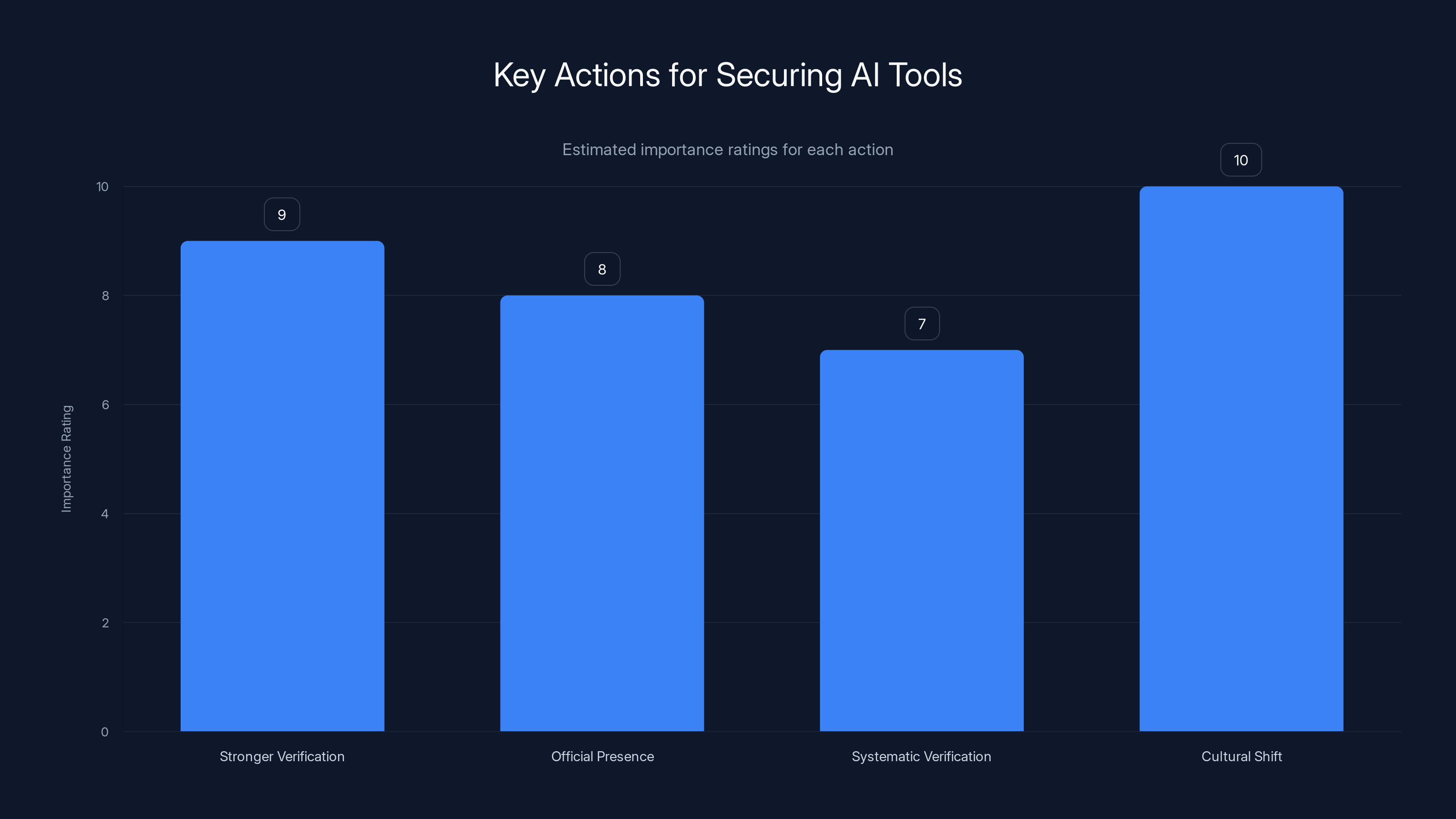
A cultural shift towards security is deemed most crucial, rated at 10, followed by stronger verification processes. Estimated data based on narrative emphasis.
The Malware Campaign: How the Attack Unfolded
The Fake Extension: Claw Bot Agent
The criminals published an extension called "Claw Bot Agent - AI Coding Assistant" on Microsoft's official VSCode marketplace. On the surface, everything appeared legitimate. The extension featured a professional icon, a polished user interface, and claimed integration with seven different AI providers: OpenAI, Anthropic, Google, Ollama, Groq, Mistral, and Open Router.
This diversity of integrations was intentional. By supporting multiple AI providers, the fake extension appeared more feature-rich and realistic than a simple tool targeting just one platform. A developer looking for a versatile AI coding assistant would see exactly what they wanted: flexibility and multiple options.
The extension even functioned as intended for the most part. This is what made it so dangerous. Users could install it, use it for basic tasks, and see it work correctly before the malicious payload activated. This delayed gratification approach is a classic social engineering technique: establish trust first, exploit later.
The Trojan: Multiple Layers of Deception
Beneath the functional interface lurked what security researchers called "a fully functioning trojan." The trojan wasn't deployed through a single vector but through a complex, multi-layered approach that revealed the sophistication of the attackers.
The primary mechanism involved a weaponized instance of legitimate remote desktop software. The attackers didn't build custom malware from scratch. Instead, they took existing, trusted remote desktop tools and configured them to connect to attacker-controlled infrastructure. This approach bypassed many security tools that might flag completely unknown executables.
But the layers didn't stop there. The researchers discovered a Rust-based backup loader that served as a contingency. If the primary remote desktop connection failed, this secondary loader would fetch the same malicious payload from Dropbox, but it disguised the download as a Zoom update. The folder structure even mimicked a screenshot application directory, adding another layer of deception.
Each layer served a purpose. The remote desktop tool gave attackers real-time access to infected systems. The Rust-based loader ensured persistence even if the primary connection was discovered and blocked. The Dropbox distribution method distributed risk and made tracking the attack source more difficult. And the disguised filenames and folders confused automated security analysis tools.
Why This Extension Got on the Official Marketplace
You might be wondering: how did a malicious extension make it past Microsoft's security screening? The answer reveals gaps in how marketplaces validate submissions. The extension functioned correctly as an AI assistant. It didn't immediately crash or behave obviously suspiciously. The remote desktop connection and loader components are small programs that can easily hide among legitimate code.
Microsoft's automated scanning likely flagged some components as suspicious, but the legitimate functionality and professional presentation may have caused reviewers to whitelist it. Additionally, malware authors knew they had a time window before security researchers discovered the threat and reported it. During that window, the extension could compromise thousands of systems.
This reveals an uncomfortable truth: even official marketplaces with security review processes remain vulnerable to sophisticated attacks. The defenders are constantly playing catch-up with attackers who have time to craft increasingly complex exploits.
Why Typosquatting Wasn't Necessary (But Was Expected)
The Typosquatting Alternative
Security researchers noted something interesting: the attackers didn't rely on typosquatting, which is when criminals register similarly-spelled domains or extensions to trick users into installing malware. For example, instead of "Moltbot," they might have registered "Moldbot" or "M0ltbot." This technique is common and often effective.
But the attackers didn't go that route. Instead, they published the fake extension as the sole official offering on the VSCode marketplace, taking advantage of the fact that the legitimate Moltbot never released an extension. This was a more sophisticated approach because it avoided the confusion that typosquatting creates. Users searching for a Moltbot extension would find this one—and because it was the only result, it seemed legitimate.
Why Being First Matters
When a tool doesn't have an official presence in a marketplace, the first high-quality offering becomes the de facto standard. Users searching for "Moltbot VSCode extension" would find "Claw Bot Agent" and assume it was the official solution. The absence of competition from the legitimate project made the malicious extension's job easier.
This highlights a lesson for open-source projects and AI tool creators: leaving marketplace gaps invites malicious actors to fill them. The best defense is a strong official presence in marketplaces where users expect to find you.
The Technical Architecture of the Attack
Component Breakdown
To fully understand the attack's sophistication, let's break down each technical component:
Layer 1: The VSCode Extension
This serves as the user-facing component. It's a legitimate VSCode extension that actually integrates with AI APIs and works correctly. The malicious code is bundled within the extension's dependencies or bundled code, hidden among legitimate functionality. When users install the extension through VSCode's built-in marketplace, no obvious warnings appear.
Layer 2: Remote Desktop Deployment
Once installed, the extension triggers a secondary payload that downloads and installs legitimate remote desktop software, but configured to connect to attacker infrastructure. This tool runs with user privileges (or potentially elevated privileges if the user runs VSCode as administrator). The attackers now have remote access to the developer's system.
Layer 3: Rust-Based Loader
This component acts as a backup mechanism. It's a small, compiled Rust program that's harder to analyze than interpreted code. If the primary remote desktop connection is blocked or discovered, the loader activates and downloads the same payload from Dropbox, disguised as a system update.
Layer 4: Obfuscation and Misdirection
Everything is layered with deceptive naming and folder structures. The Dropbox payload appears to be a Zoom update. The folders are named after legitimate system tools. This misdirection slows down security researchers and helps the malware persist longer on infected systems.
How the Attack Persists
The real danger of this malware isn't the initial infection. It's the persistence mechanisms. Once installed, the trojan ensures it runs every time the user starts their computer. The remote desktop connection allows attackers to maintain ongoing access to steal data, install additional malware, or use the compromised system as part of a botnet.
For a developer's machine, this is catastrophic. Attackers gain access to source code, API keys, credentials stored in environment variables, SSH keys, authentication tokens, and potentially sensitive client information. A single compromised developer account can become the entry point for a broader supply chain attack affecting an entire organization.
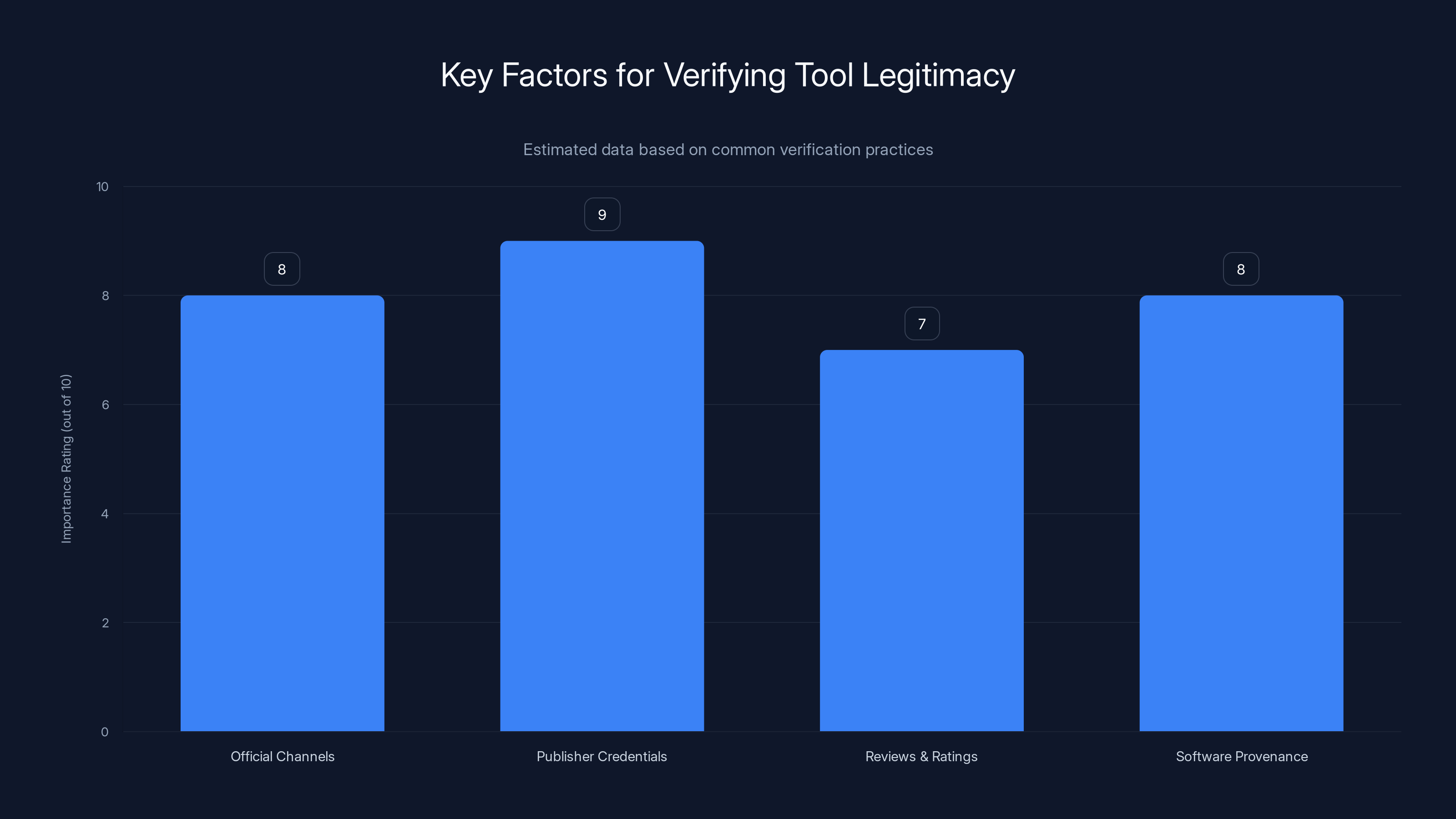
Publisher credentials and official channels are crucial for verifying tool legitimacy, with ratings and provenance also playing significant roles. Estimated data.
The Incident Timeline and Discovery
How Security Researchers Found It
The attack was discovered relatively quickly by security researchers at Aikido, a security-focused organization focused on emerging threats. They likely identified the extension through threat intelligence feeds, user reports, or routine marketplace scanning. Once flagged, they analyzed the extension's code and behavior, discovering the trojan components.
The fact that it was discovered at all speaks to the increasing sophistication of security analysis tools. Malware that would have gone undetected years ago can now be identified by automated threat detection systems. However, there's always a lag between when malware is published and when it's detected. During that window, real damage occurs.
The Speed of Remediation
Once identified, the extension was removed from the VSCode marketplace relatively quickly. However, anyone who installed it during the active period has a compromised system. Removing the extension doesn't remove the remote desktop software already installed or the persistence mechanisms already established.
This is why detection speed matters so much. Every day a malicious extension remains available, more users download and install it. For this particular attack, we don't know exactly how many systems were compromised, but security researchers later noted the campaign targeted "countless unsuspecting users".
Public Disclosure and Community Response
After discovery, the security community quickly informed developers of the threat. Tech publications covered the story, security advisories were published, and Moltbot's developers released statements clarifying that they had no official VSCode extension. However, not every developer sees these warnings. Many continue working with outdated information, unaware that their system might be compromised.
Why Developers Are Prime Targets
High-Value Targets
Criminals specifically target developers and development teams because of what they have access to. A compromised developer's machine provides attackers with:
- Source code for proprietary projects
- API keys and credentials for production systems
- SSH keys that grant access to servers and repositories
- Authentication tokens for cloud services
- Encryption keys for sensitive systems
- Client information and confidential project details
A single compromised developer can become an entry point for attacking an entire organization. This makes developers worth far more to attackers than typical users.
Trust in the Developer Ecosystem
Developers rely on open-source tools and marketplace extensions as essential parts of their workflow. Unlike average users who might be skeptical of unknown software, developers often trust tools recommended by their peers or published on official marketplaces. This trust is usually warranted, but it creates an exploitable blindspot.
When criminals can publish code on official marketplaces, they inherit the legitimacy of those platforms. A developer installing from the VSCode marketplace assumes Microsoft has vetted the extension, making them more likely to grant permissions without scrutiny.
The Speed of Tool Adoption
Developers move fast. When a useful new tool appears, they download and integrate it immediately, sometimes without thoroughly reviewing the code or publisher information. This speed is a strength in development culture but becomes a weakness when security is involved. Attackers count on this impatience.
The faster a malicious tool spreads through the developer community, the more systems get compromised before it's detected and removed. By the time the threat is public knowledge, thousands of machines might already be infected.
How to Verify Tool Legitimacy
Check Official Project Channels
Before installing any extension or tool, verify its legitimacy through official channels. Visit the project's GitHub repository, official website, or documentation. Legitimate projects clearly state which marketplaces they officially publish to and provide links directly to those listings.
For Moltbot specifically, checking GitHub would have revealed no official VSCode extension announcement. This should have been a red flag for the fake extension.
Analyze Publisher Credentials
On marketplaces like VSCode, examine the publisher's account. Legitimate publishers usually have:
- Multiple published extensions or tools
- Consistent publishing history spanning months or years
- Other recognizable projects in their portfolio
- Clear contact information and communication
- Active community engagement and support
A brand-new account with a single high-quality extension should always raise suspicion. Attackers are willing to create fake publisher accounts, but they typically can't fake a years-long track record.
Read Reviews and Ratings Carefully
Marketplace ratings provide signals about extensions' legitimacy. However, attackers sometimes buy fake reviews or inflate ratings artificially. Read individual reviews, particularly negative ones. Users who noticed something suspicious often leave warnings in the comments. Look for reviews mentioning unexpected behavior, battery drain, network connections, or system performance issues.
For the fake Claw Bot Agent extension, detailed reviews that examined its network behavior would have revealed the suspicious remote desktop connections.
Request and Review Source Code
For open-source extensions, you can download and examine the source code before installing. Look for suspicious network connections, file system access requests, or permission requirements that seem excessive for the tool's stated functionality.
If the published extension's code doesn't match what you can review on GitHub, that's a serious warning sign. Some attackers publish legitimate-looking code on GitHub while distributing a different, malicious binary through marketplaces.
Check for Code Signing and Verification
Many tools use cryptographic signatures to verify that code hasn't been tampered with. Check whether your extensions and tools are signed by their publishers. Tools that lack proper code signing might have been compromised or modified without the publisher's knowledge.
VSCode extensions can be signed and verified, providing an additional layer of assurance that what you're installing matches what the publisher released.

Reviewing permissions and verifying publishers are crucial steps, rated highest in importance for preventing attacks. Estimated data.
Security Warnings and How They Fail
The Problem with Flag-Based Security
When Moltbot's official website was flagged as dangerous, it created a problematic situation. Users trying to verify the legitimacy of the fake extension by visiting the official site would see security warnings. This didn't necessarily deter them from using the fake extension though, because:
- The warnings were false positives (the real site isn't dangerous)
- Users became desensitized to security warnings
- They already had the fake extension installed and working
- Trusting the marketplace felt safer than visiting flagged websites
This demonstrates a crucial security failure: when legitimate sites get incorrectly flagged, users lose faith in warning systems. They start ignoring warnings even when they're accurate.
Marketplace Review Limitations
Microsoft's VSCode marketplace, like all software distribution platforms, has limitations in its security review process. Reviewers can't execute all code paths, can't predict all possible behaviors, and can't catch every sophisticated attack. They rely on automated scanning and manual inspection, both of which have gaps.
The fake Claw Bot Agent extension passed review because:
- It had legitimate functionality
- The malicious components were well-hidden
- The remote desktop tool itself is legitimate software
- The overall size and complexity made complete analysis time-consuming
User Permission Warnings
When you install an extension that requests elevated permissions, VSCode displays warnings. However, many AI coding assistants legitimately need broad system access to work effectively. Users often grant these permissions without fully considering the implications. An extension that accesses your file system, runs terminal commands, and makes network connections could justify those permissions for a legitimate tool, but the same permissions are perfect for malware.
Supply Chain Attacks and Broader Implications
This Wasn't An Isolated Incident
The fake Moltbot extension represents part of a broader pattern. Security researchers have documented multiple campaigns using similar techniques:
- Typosquatting attacks on NPM and PyPI registries, compromising millions of developers
- Malicious GitHub repositories posing as legitimate projects, stealing credentials from developers who clone them
- Compromised maintainer accounts on open-source projects, allowing attackers to inject malware into widely-used libraries
- Fake documentation sites that look like legitimate project docs but host malicious downloaders
These aren't rare exceptions. They're increasingly common tactics in the cybercriminal playbook. Attackers have realized that targeting developers provides better ROI than targeting end users, because developers have access to infrastructure, secrets, and source code.
The Cascading Risk
When a developer's machine is compromised through a VSCode extension, the damage extends far beyond that individual. Consider the cascading risks:
- Repository compromises: If the developer has access to GitHub, GitLab, or other repositories, attackers can inject malware into source code
- Credential theft: API keys, database passwords, and deployment credentials become available to attackers
- Build pipeline infiltration: Development tools can be modified to inject malicious code into compiled binaries
- End-user impact: If the developer works on projects used by thousands or millions of people, those users inherit the compromised code
A single compromised developer can become the entry point for compromising an entire software supply chain.
Lessons for Open-Source Projects
The Moltbot incident highlights important lessons for open-source maintainers:
- Maintain marketplace presence: If users expect to find your project on a marketplace, be there first with the official version
- Communicate clearly: Use GitHub descriptions and official documentation to explicitly state which marketplaces you officially publish to
- Provide verification guidance: Help users understand how to verify they're installing the legitimate version
- Monitor for impersonation: Regularly search marketplaces for fake versions of your project
- Establish code signing: Use cryptographic signatures so users can verify downloaded code
How To Protect Yourself From Similar Attacks
Best Practices for Extension Installation
Develop a systematic approach to evaluating extensions before installation:
- Search for official announcements in the project's GitHub repository, documentation, or official website
- Verify the publisher account by reviewing their complete portfolio and publication history
- Check marketplace reviews for specific mentions of suspicious behavior
- Review permission requests and consider whether they're necessary for the tool's functionality
- Download and scan the extension's code with security tools before installing
- Test in isolation by installing in a fresh environment and monitoring system behavior
- Keep track of what you install so you can audit your setup if a threat is later discovered
Monitor Extension Behavior
Even after installation, remain vigilant about how extensions behave:
- Watch for network connections that seem unusual or unrelated to the extension's stated purpose
- Monitor CPU and memory usage for unexpected spikes
- Check file system access to see what directories the extension accesses
- Review process creation to understand what additional programs get launched
Tools like Process Monitor on Windows or Activity Monitor on macOS can help you understand what your extensions are actually doing.
Keep Your System Updated
Security patches in VSCode, Node.js, and the operating system itself often close vulnerabilities that malware exploits. Regular updates significantly reduce your attack surface.
Use Endpoint Protection
While not foolproof, reputable endpoint protection software catches many malware samples, including variants of known malware. It won't catch every sophisticated attack, but it adds a valuable layer of defense.
Principle of Least Privilege
Avoid running VSCode as administrator or with elevated privileges. The fake Claw Bot Agent extension would have been more dangerous with admin privileges, allowing it to make system-wide changes and persist more effectively. Running applications with standard user privileges limits what compromised tools can do.
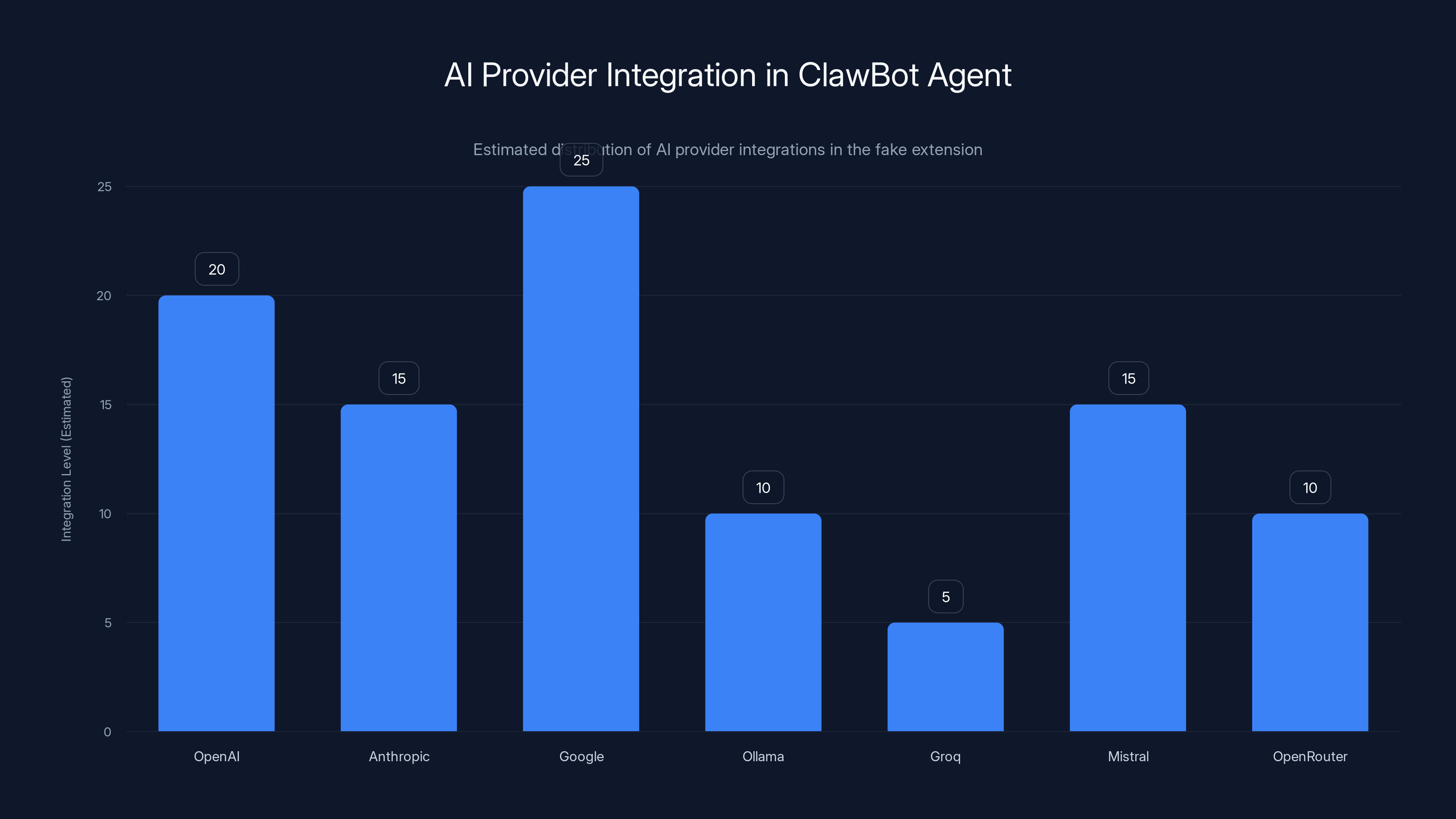
The fake extension 'ClawBot Agent' claimed integration with seven AI providers, with Google and OpenAI having the highest estimated integration levels. Estimated data.
Red Flags That Should Trigger Suspicion
Technical Red Flags
Certain characteristics should immediately trigger skepticism:
- Extension requests administrator privileges when the functionality doesn't seem to require them
- Network connections to unknown destinations without legitimate reason
- Executable files bundled in the extension when the tool shouldn't need pre-compiled binaries
- Obfuscated or minified code that can't be easily audited
- Large file sizes for what should be simple extensions
- Unsigned executables or missing cryptographic signatures
Behavioral Red Flags
Some warning signs emerge through behavior rather than technical analysis:
- New extension with immediate popularity or high ratings that seem unearned
- Marketing that emphasizes speed and convenience without discussing security
- Poorly written documentation or communication that's inconsistent with the tool's quality
- Missing or evasive responses to security-related questions in reviews or issues
- Frequent version updates with vague changelog entries
Community Red Flags
Pay attention to what the broader community is saying:
- Lack of discussion about the extension in developer communities despite its claimed popularity
- No presence on the project's official channels or from the claimed developers
- Negative comments that mention suspicious behavior, even if drowned out by positive reviews
- Absence of technical blog posts or documentation from the developers about how the extension works

What To Do If You're Already Compromised
Immediate Steps
If you installed the fake Claw Bot Agent extension or suspect your system was compromised:
- Disconnect from the network to prevent attackers from exfiltrating data or establishing persistence on other systems
- Force a shutdown rather than a normal shutdown, to prevent malware from cleaning up logs
- Boot into a clean environment like Linux from a USB drive to safely analyze your system
- Document everything before taking actions, preserving evidence of the compromise for analysis
Analysis and Cleanup
- Use forensic tools to identify all malware components and understand what was accessed
- Review system logs to understand when the compromise occurred and what actions were taken
- Check for persistence mechanisms like scheduled tasks, startup entries, or system modifications
- Search for installed remote desktop tools that you don't remember installing
- Review network connection history to identify attacker infrastructure
Recovery Steps
- Change all credentials from a different, uncompromised machine (passwords, API keys, tokens)
- Revoke SSH keys that were stored on the compromised system
- Review code repositories for unauthorized changes
- Consider full system reinstall for critical development machines
- Notify affected parties including your organization, clients, and users of potentially compromised projects
When to Seek Professional Help
For critical systems, consider engaging incident response professionals who can:
- Perform sophisticated forensic analysis
- Identify all evidence of the compromise
- Understand attacker objectives and scope
- Ensure complete remediation
- Provide documentation for legal purposes if needed
The cost of professional help is usually far less than the damage from an incomplete cleanup or missed persistence mechanisms.
The Future of AI Tool Security
Increasing Sophistication of Attacks
As AI tools become more essential to development workflows, we should expect attacks to become more sophisticated. Attackers will:
- Invest more time in making fake tools look legitimate
- Study real projects more carefully to understand user expectations
- Develop patience releasing malicious tools that stay undetected for longer
- Create ecosystem attacks that compromise multiple tools in a developer's workflow simultaneously
- Target maintainer accounts specifically because they control what gets published
Marketplace Evolution
Secure marketplaces will likely implement:
- Stricter publisher verification requiring identity confirmation and historical credentials
- Code analysis automation using advanced security scanning during review
- Cryptographic code signing that users can verify independently
- Behavioral sandboxing that allows extensions to run in limited environments before full approval
- Community reporting mechanisms that quickly flag suspicious extensions
However, these defenses create an arms race. As marketplace security improves, attackers will find new approaches.
Developer Education
The most important defense is developer education. Developers who understand:
- How to verify tool legitimacy
- What permissions are actually necessary
- What warning signs indicate malicious code
- How to monitor system behavior
- When to seek help
These developers will be significantly harder targets for sophisticated malware campaigns.

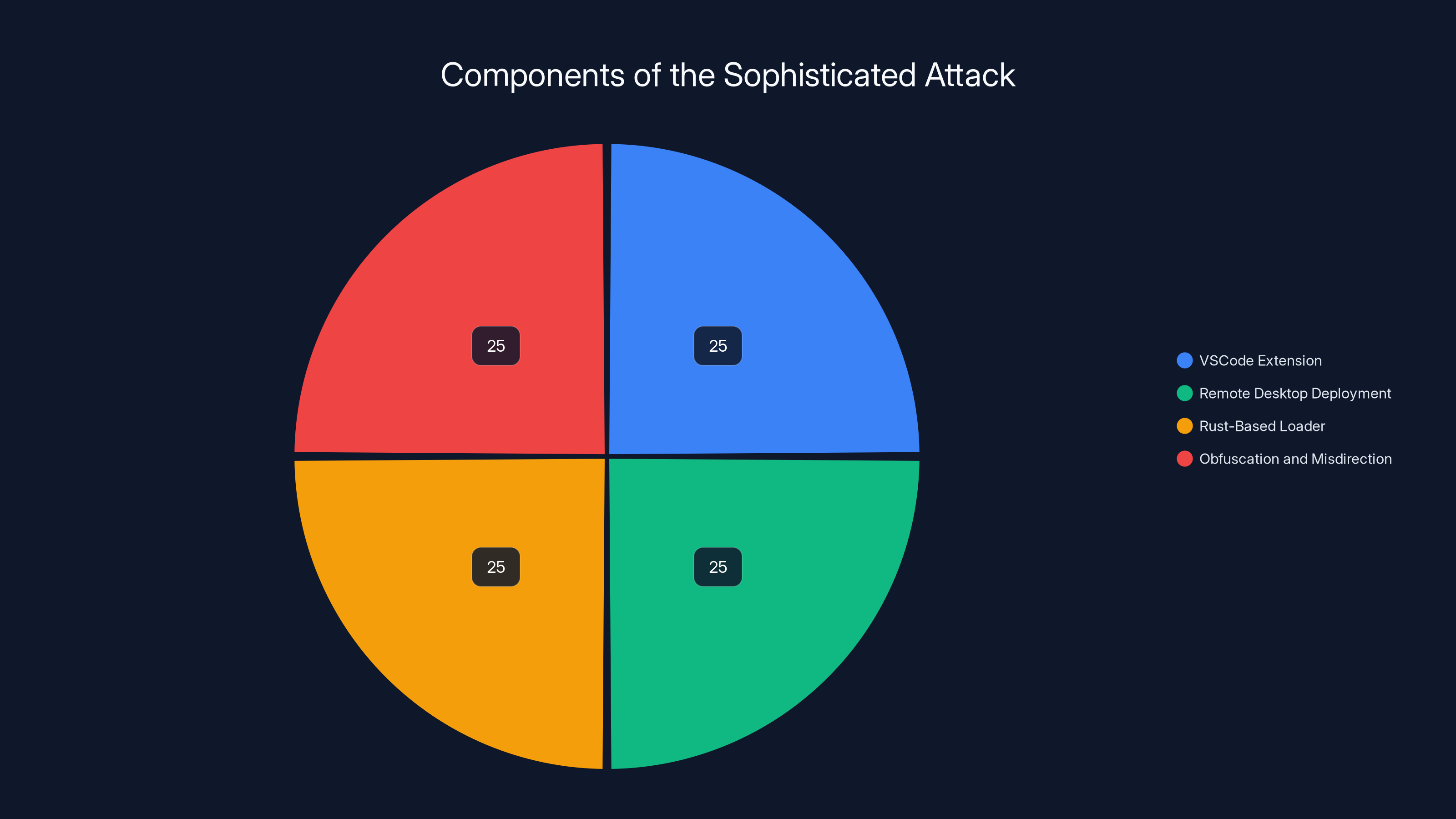
The attack is evenly distributed across four main components, each playing a crucial role in its execution and persistence. Estimated data.
Industry Response and Best Practices
What Security Companies Are Recommending
Following the Moltbot incident, security organizations issued recommendations including:
- Institute software bill of materials (SBOM) requirements for all development tools
- Implement runtime behavior monitoring for development environments
- Require code review for any changes to development infrastructure
- Establish zero-trust policies for tool installation, verifying authenticity regardless of source
- Create developer security training programs focused on social engineering and tool verification
Organizational Policies
Development organizations are implementing:
- Approved tools lists: Only officially approved extensions and tools can be installed
- Installation requests: Developers request new tools, which are verified before approval
- Centralized management: Tools installed through organizational accounts with accountability
- Security scanning: All tools undergo security analysis before approval
- Regular audits: Periodic review of installed tools to identify unauthorized or compromised software
Open-Source Community Response
Open-source projects are adopting defensive measures:
- Official marketplace announcements clearly stating where projects can be legitimately found
- Security policy documentation explaining how users can verify releases
- Contributor verification ensuring that code changes come from legitimate maintainers
- Release signatures cryptographically signing all releases so users can verify authenticity
- Incident response plans for when projects are impersonated or compromised
Understanding the Economics of Malware Distribution
Why This Attack Made Sense Economically
From the attackers' perspective, the Claw Bot Agent campaign made perfect sense economically. The cost was low:
- Creating a functional VSCode extension: minimal effort (could be copied from open-source projects)
- Bundling legitimate remote desktop software: just configuration, no development needed
- Publishing to marketplace: free
- Supporting the malware: minimal ongoing effort
The revenue potential was enormous:
- Developer accounts are valuable: Each compromised developer has access to sensitive systems worth thousands or millions
- Rapid scaling: Once deployed, the malware reaches thousands of systems with no additional effort
- Multiple monetization approaches: Sell access to infected systems, ransom stolen credentials, inject backdoors into projects for future exploitation
From a pure ROI perspective, targeting developers through marketplace extensions is incredibly efficient.
Monetization of Compromised Developer Accounts
Once an attacker controls a developer's machine, they can monetize it in multiple ways:
- Credential theft and sale: API keys, SSH keys, and cloud credentials sold on dark markets
- Ransomware deployment: Encrypt sensitive files and demand payment
- Backdoor installation: Create persistent access sold to other cybercriminals
- Supply chain poisoning: Inject malware into software the developer is building
- Espionage: Access to proprietary source code and business information
- Cryptomining: Use the system's computational resources for cryptocurrency mining
Each compromised developer represents multiple revenue streams, making the attack economically rational from the attacker's perspective.

Comparing This Attack to Other Marketplace Compromises
Similar Historical Incidents
The Moltbot case follows a pattern we've seen before:
The NPM left-pad incident (2016): A developer unpublished a simple 11-line module that thousands of projects depended on. Attackers could have taken over the namespace and published malicious code to millions of systems.
The PyPI "bitcoin" package: Attackers registered the name of a popular Bitcoin library and published a malicious version. Developers installing it expecting functionality from the legitimate library instead got a data stealer.
The Xcode Ghost attack (2015): Attackers compromised the Xcode IDE distribution, injecting malware into thousands of iOS apps built with the tool. The malware persisted in user devices for years.
The Solar Winds supply chain attack (2020): Attackers compromised build systems of a network management tool, injecting malware into updates that reached thousands of organizations including government agencies.
Each incident follows the same pattern: trust is exploited, the attack is sophisticated but not detected immediately, and the damage scales widely before discovery.
What Made the Moltbot Attack Different
The Moltbot campaign had some distinguishing characteristics:
- It impersonated a specific legitimate project rather than creating a typosquat or generic name
- It filled a gap that the legitimate project hadn't addressed (VSCode extension)
- It was sophisticated with multiple layers and backup mechanisms
- It was caught relatively quickly compared to some other attacks
What didn't make it different: the fundamental vulnerability it exploited, which is the trust developers place in marketplaces and the difficulty of verifying tool legitimacy at scale.
Practical Tool: Building Your Verification Checklist
Creating a Personal Verification System
Develop a reusable checklist for evaluating any new extension or tool:
Pre-Installation
- Official project documentation mentions this tool or confirms its absence
- Publisher account has history spanning multiple years
- Multiple other tools or extensions in publisher's portfolio
- Clear contact information and support channels available
- Recent release date (not abandoned project)
- Marketplace reviews mention specific use cases and benefits
- No comments mentioning suspicious behavior or network activity
- Code is publicly available and reviewable
- Source code matches the published version
- Cryptographic signatures available for verification
Installation
- Review all permission requests before confirming
- Understand why each permission is necessary
- Consider installing in separate environment first
- Document baseline system behavior before installation
- Create restore point or snapshot
Post-Installation
- Monitor network connections for unexpected activity
- Check CPU and memory usage patterns
- Review filesystem access in real-time
- Watch for new processes spawned by the extension
- Regularly verify nothing has changed in system configuration
Using this checklist consistently significantly reduces your risk of installing malicious tools, though it requires more time and attention than simply installing whatever looks useful.

FAQ
What is the Claw Bot Agent extension and why is it dangerous?
Claw Bot Agent was a fake VSCode extension published on Microsoft's official marketplace that impersonated Moltbot, a legitimate open-source AI assistant. It appeared functional and well-designed but contained a fully operating trojan malware that gave attackers remote access to infected systems. The danger comes from its sophisticated layering, which used remote desktop software configured to connect to attacker infrastructure, backup loaders disguised as legitimate software, and persistence mechanisms that survive system restarts.
How do I know if I installed the malicious Claw Bot Agent extension?
If you installed any VSCode extension called "Claw Bot Agent" or "Claw Bot Agent - AI Coding Assistant," particularly before the attack was publicly disclosed, your system may be compromised. Check your VSCode extension list for this specific name. Also review your VSCode version history and installation dates. If you installed it before the attack was discovered, immediately disconnect from the network and consider the remediation steps outlined in this guide. Check your system for unexpected remote desktop software installations and monitor network connections for suspicious outbound traffic.
What makes the Moltbot attack different from other malware campaigns?
The Moltbot attack stands out because it impersonated a specific legitimate project and filled a gap that the real project hadn't addressed (no official VSCode extension existed). This gave the fake extension legitimacy without requiring typosquatting or confusing similar names. The attack also demonstrated sophisticated multi-layered deception with backup loaders, persistence mechanisms, and disguised file structures. Most importantly, it targeted developers through an official marketplace, exploiting the trust placed in platform security reviews.
How can developers verify that extensions are legitimate?
Developers can verify extension legitimacy by checking multiple signals: examining the publisher's account history and portfolio of other tools, reviewing the project's official GitHub repository for marketplace links, reading specific reviews mentioning actual behavior, analyzing the extension's code for suspicious components, verifying cryptographic signatures if available, and checking whether the official project actually releases tools on that marketplace. No single indicator is definitive, but combining these checks significantly reduces risk.
Should I stop using VSCode extensions entirely?
No, stopping extension use entirely would severely limit development productivity. Instead, adopt a systematic verification process for any extension before installation. Only install extensions from publishers with established track records, focus on minimal, single-purpose extensions rather than comprehensive tools when possible, and regularly audit your installed extensions to remove those no longer in use. The risk is manageable with appropriate due diligence; the key is being intentional rather than careless about what you install.
What should I do if my VSCode extension installs unexpected software?
If you notice an extension installing software you didn't explicitly authorize, immediately uninstall the extension and any programs it installed. Disconnect from the network to prevent attackers from establishing persistence on other systems. Boot into a clean environment to analyze what was installed and whether remote access was established. Check running processes for unexpected applications, review network connections to identify attacker infrastructure, and if this occurred on a work machine, notify your organization's security team immediately. Consider professional forensic analysis if the extension was installed on a critical system.
Why do remote desktop tools in VSCode extensions represent a security concern?
Remote desktop tools allow attackers to control your system as if they were sitting at your keyboard. An extension that installs remote desktop software configured to connect to attacker-controlled servers creates a backdoor for complete system compromise. The attacker gains access to everything on your machine: source code, credentials, cryptographic keys, project files, and anything else. This is more dangerous than typical malware that only steals specific data types, because it provides persistent, ongoing access that survives security patches and tool updates.
How can organizations protect their developers from these attacks?
Organizations can implement several defenses: establish an approved tools and extensions list that undergoes security review before approval, require developers to request new tools rather than installing arbitrary software, implement centralized management where tools are installed through organizational accounts with auditing, perform regular security scans of development machines, provide training to developers about verification and social engineering, and establish policies requiring code review for any infrastructure changes. Additionally, monitor network activity from development machines to detect suspicious outbound connections and implement endpoint protection that catches known malware families.
Conclusion: Trust, But Verify
The Moltbot malware campaign represents a critical lesson for the developer community: as AI tools become more essential to our workflows, attackers will increasingly target them. The bad actors understand that developers trust the tools they use, often implicitly, and that marketplace platforms carry inherited legitimacy that extends to all published content.
What happened with Claw Bot Agent wasn't inevitable. The attack succeeded because of a chain of vulnerabilities: Moltbot's popularity without marketplace presence, developers' natural desire for convenient tools, the marketplace's limitation in security screening, and the general assumption that official platforms have vetted their content.
Breaking this chain requires action at multiple levels. Marketplace platforms need stronger verification processes and better tools for detecting sophisticated attacks. Open-source projects need to establish clear official presences in marketplaces where users expect to find them. Developers need to adopt systematic verification practices and remain skeptical even of seemingly legitimate tools. Organizations need to implement policies that slow down tool adoption enough to allow for verification.
Most importantly, we need a cultural shift. The speed and convenience that make developer tools appealing shouldn't come at the cost of security. It's perfectly reasonable to spend five or ten minutes verifying a tool before installing it on a system that contains access to critical infrastructure. That's not paranoia. That's responsibility.
The legitimate Moltbot team did nothing wrong. They built a useful tool and shared it with the community. The problem emerged at the intersection of their success and the marketplace infrastructure that users trusted. This same problem will emerge repeatedly as more AI tools proliferate. The question isn't whether we'll face similar attacks again. The question is whether we'll learn from this incident and change our behavior accordingly.
Next time you install an extension, take the time to verify it. Check the publisher. Review the code. Understand the permissions. Ask yourself whether it really needs everything it's requesting. These small steps, multiplied across the developer community, make the ecosystem safer for everyone. Because in the world of software supply chains, there's no such thing as a small compromise. Every system matters. Every compromise has consequences. Every developer is a potential target.
Stay skeptical. Stay secure.
Use Case: Secure your development workflow with automated security analysis and validation tools that help you vet extensions and dependencies before they reach your systems.
Try Runable For Free
Key Takeaways
- Moltbot malware campaign used a fake ClawBot Agent VSCode extension with sophisticated trojans targeting developers through official marketplace trust.
- The attack exploited a gap (no legitimate VSCode extension) combined with developers' trust in marketplaces, achieving high-quality impersonation without typosquatting.
- Multi-layered malware used legitimate remote desktop software, Rust-based backup loaders, and disguised payloads for persistence and obfuscation.
- Developers are prime targets because compromised accounts provide access to source code, credentials, API keys, and infrastructure affecting entire supply chains.
- Systematic verification practices including publisher account history review, permission analysis, code examination, and behavioral monitoring significantly reduce installation risk.
- Organizational defense requires approved tools policies, centralized management, regular security audits, and employee training on tool verification procedures.
- Similar attacks will continue escalating as AI tools become more essential; industry response includes stricter marketplace verification and cryptographic code signing.
Related Articles
- Browser-Based Attacks Hit 95% of Enterprises [2025]
- VSCode Malicious Extensions: How 1.5M Developers Got Compromised [2025]
- Upwind Security's $250M Series B: Runtime Cloud Security's Defining Moment [2025]
- Okta SSO Under Attack: Scattered LAPSUS$ Hunters Target 100+ Firms [2025]
- Vishing Kits Targeting SSO: Google, Microsoft, Okta at Risk [2025]
- WinRAR Security Flaw CVE-2025-8088: Complete Defense Guide [2025]
![Fake Moltbot AI Assistant Malware Scam: What You Need to Know [2025]](https://tryrunable.com/blog/fake-moltbot-ai-assistant-malware-scam-what-you-need-to-know/image-1-1769708396299.jpg)



