Nike Data Breach: What We Know About the 1.4TB World Leaks Hack [2025]
Nike just got hit with one of the year's most significant corporate data breaches, and honestly, this one's different from most hacks you've heard about. On a random Tuesday, cybercriminals calling themselves World Leaks posted Nike's name on their public data leak site, claiming they'd stolen 1.4TB of internal data. That's not gigabytes we're talking about here, that's terabytes. Enough data to fill thousands of laptops.
The scary part? They weren't subtle about it. The hackers posted samples to prove they actually had the goods, showing directories with names like "Women's Sportswear," "Men's Sportswear," "Training Resource - Factory," and "Garment Making Process." This isn't encrypted ransom-note stuff either. This is straight-up file theft, and it represents a fundamental shift in how modern cybercriminals operate.
Here's what makes this breach noteworthy: Nike has largely avoided the kind of catastrophic, headline-grabbing security incidents that have plagued competitors. While companies like Target, Home Depot, and Equifax suffered through ransomware attacks that made international news, Nike maintained a relatively clean security record. Until now.
But before you panic about your Nike account or worry that your credit card is compromised, here's the reality check. Nike says customer data and employee personal information wasn't stolen. The breach appears focused on internal design files, manufacturing data, and business process documentation. That's actually important context because it means your identity isn't floating around on the dark web waiting to be sold to fraudsters.
That said, this breach opens up some serious questions about corporate cybersecurity practices, threat actors, and what happens when multi-billion dollar companies get caught flat-footed by relatively new hacking groups. We're going to break down everything you need to know: who World Leaks is, what actually got stolen, what Nike's saying about it, and most importantly, what this means for you.
TL; DR
- World Leaks claims 1.4TB theft: Cybercriminals say they stole massive amounts of Nike design and manufacturing data, posting samples as proof
- No customer or employee data exposed: Nike confirms that personal information, passwords, and payment data weren't part of the breach
- World Leaks is successor to Hunters International: The threat actor group focuses on data theft rather than encryption-based ransomware
- File-based theft is the new trend: Hackers increasingly steal files without deploying encryption, making recovery possible but preventing attribution
- Nike investigating but not confirming: The company has launched an internal investigation and is assessing the situation, but hasn't provided detailed timeline or scope

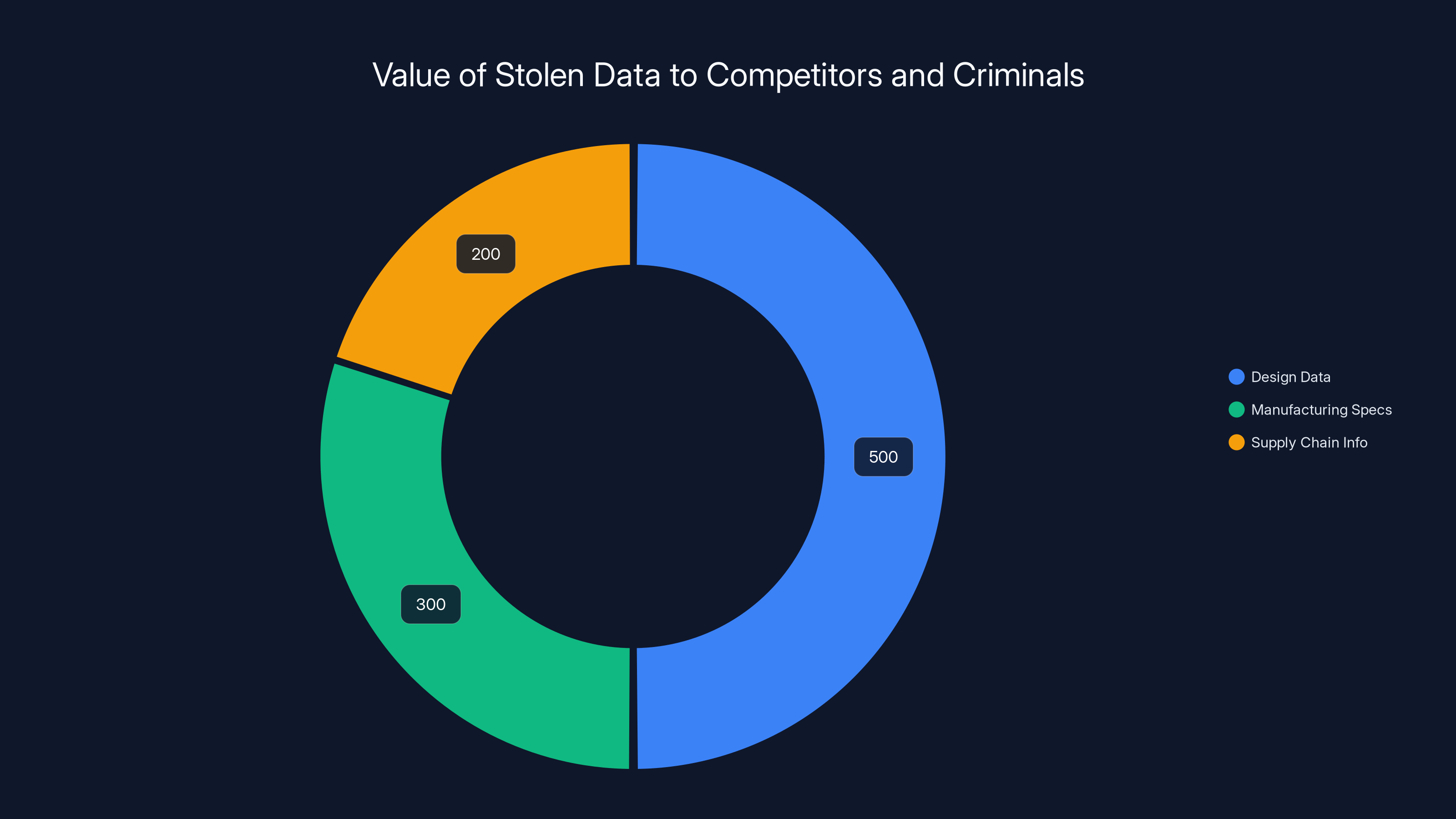
Design data is the most valuable, estimated at
What Exactly Got Stolen in the Nike Breach?
This is where things get interesting, because the data stolen isn't what most people think of when they imagine a corporate hack. We're not talking about customer payment information, Social Security numbers, or email addresses. Instead, World Leaks claims to have accessed internal design documents, manufacturing specifications, supply chain information, and business process documentation.
The sample files shared by the threat actors show a clear focus on Nike's product development and manufacturing operations. Directories with names like "Women's Sportswear" and "Training Resource - Factory" suggest the hackers accessed systems containing sensitive information about how Nike designs shoes, manages production timelines, and coordinates with manufacturing partners. This kind of data is worth millions to competitors or counterfeiters because it reveals proprietary processes and upcoming product lines.
What's particularly concerning is the "Garment Making Process" directory. This suggests access to detailed manufacturing procedures, material specifications, and production workflows that Nike has likely spent decades perfecting and protecting. Counterfeiters would love this information because it lets them produce fake Nike products that are increasingly difficult to distinguish from legitimate merchandise.
The data doesn't appear to include:
- Customer credit card numbers
- Usernames and passwords for Nike.com accounts
- Customer personal identification information
- Employee Social Security numbers or sensitive personal information
- Financial records or banking details
Nike's statement addressing this directly is important: the company confirmed that customer privacy and employee personal identification information were not compromised in this incident. That's not just PR speak either. If customer payment data or personal information had been stolen, Nike would likely be facing mandatory breach notification laws in multiple states and countries, triggering expensive notification requirements and potential regulatory investigations.
What makes this different from typical ransomware attacks is the absence of encryption. World Leaks doesn't lock up files and demand payment for decryption keys. Instead, they steal files and publish them on their data leak site, threatening to release increasingly sensitive information if the company doesn't pay. It's extortion through exposure rather than operational shutdown through encryption.
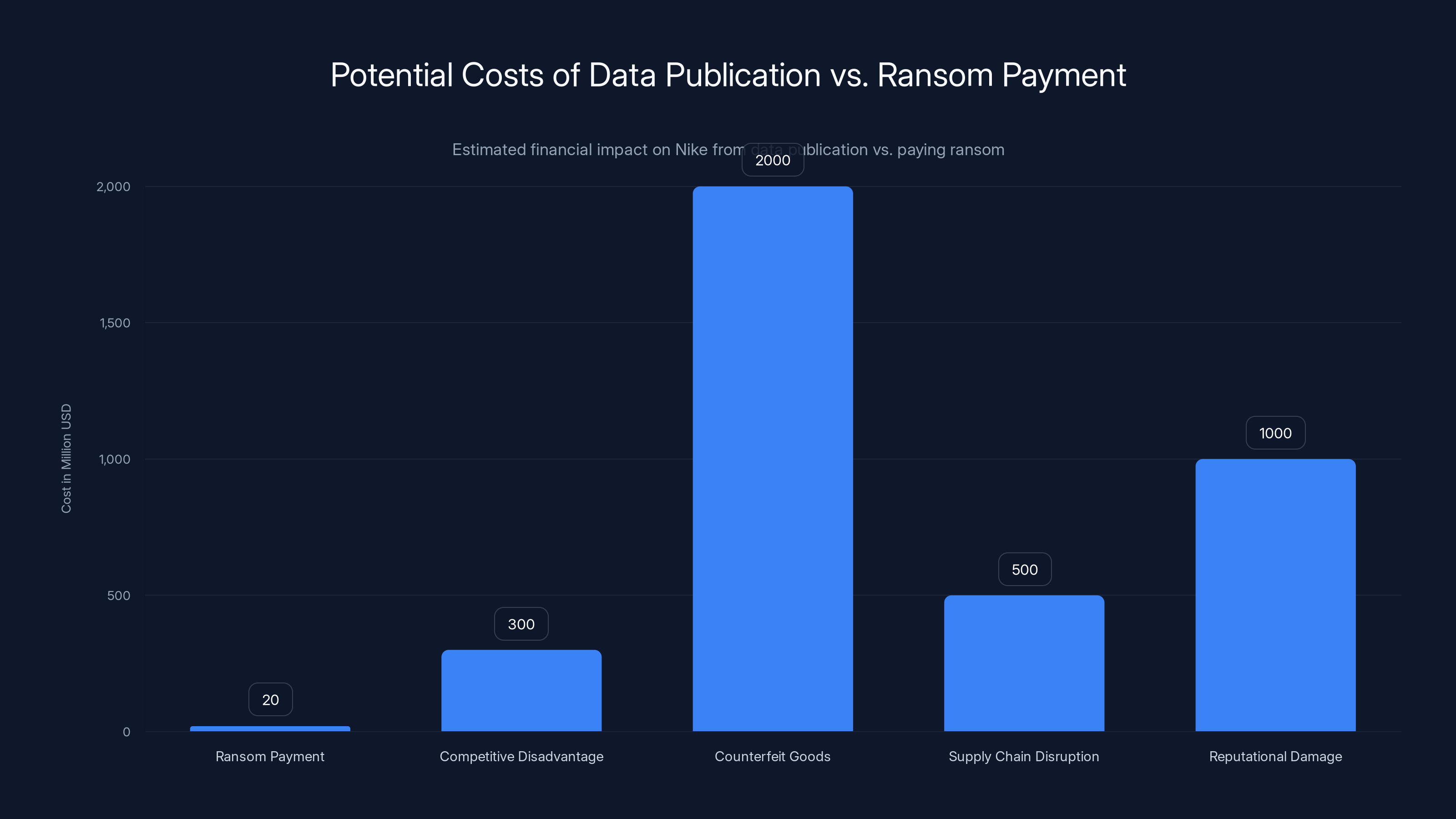
Estimated data suggests that the potential costs of data publication for Nike could far exceed the ransom payment, with counterfeit goods and competitive disadvantage posing significant financial threats.
Who Is World Leaks and Why Should You Care?
World Leaks isn't some random group of script kiddies operating out of a basement in Eastern Europe. This is a sophisticated, well-organized threat actor group that's been making headlines across corporate America for months. They maintain an active data leak site, publish regular "press releases" about their activities, and operate with a level of professionalism that honestly feels more like a business than a criminal enterprise.
What's particularly notable is that World Leaks is widely believed to be the successor organization to another notorious hacking group called Hunters International. Hunters International made waves in the cybersecurity world by emerging after the collapse of the Hive ransomware gang, a group that had been stealing data from Fortune 500 companies for years. When Hive finally got shut down by international law enforcement operations, its leadership and members scattered. Some analysts believe key members regrouped under the World Leaks banner.
The transition from Hunters International to World Leaks happened in mid-2025. Hunters International announced it was shutting down operations and claiming it would release free decryption tools for victims who hadn't paid ransom. On the surface, this looks like a group winding down operations and trying to rehabilitate its image. But many cybersecurity researchers think this was a deliberate move to throw law enforcement off the scent while the group reorganized under a new name.
World Leaks operates differently from traditional ransomware gangs in a meaningful way. Instead of deploying encryption tools that lock up entire networks and force companies to choose between paying ransom or losing access to critical systems, World Leaks focuses purely on data theft. They break into networks, copy sensitive files, and threaten to publish them unless the target pays. No encryption, no system downtime, just the threat of public exposure.
This shift represents a broader trend in the cybercrime world. Encryption-based ransomware is expensive to deploy, complicated to manage, and leaves a massive technical footprint. File theft is simpler, harder to defend against comprehensively, and often just as profitable. Why spend resources on encryption when you can just steal files and threaten their release? It's more efficient, and it's working.
World Leaks' victim list is genuinely impressive:
- Dell: Computer giant Dell had internal information stolen and posted on the World Leaks site
- Chain IQ: Supply chain management company breached with significant operational data exposed
- Multiple other enterprises: The group claims dozens of victims, though not all have been publicly confirmed
The group operates with a level of sophistication that suggests they have serious technical expertise. They maintain infrastructure, manage data securely, publish regular updates, and operate with operational security that makes them difficult to track. They're not using default passwords and obvious vulnerabilities. These are skilled attackers who understand network security and know how to move laterally through corporate systems without getting caught.

The Shift from Ransomware to File Theft: Why It Matters
Here's something that cybersecurity professionals have been discussing for months: the evolution of ransomware into pure data theft represents a fundamental change in how attackers approach corporate breaches. Understanding this shift is crucial to understanding why Nike got hit and why your company might be next.
Traditional ransomware worked like this: attackers get into a network, deploy encryption tools that lock up critical files and databases, then demand payment in cryptocurrency for decryption keys. The business model is straightforward. Company can't operate without their data, so they pay. Law enforcement can't easily trace cryptocurrency transactions, so attackers escape consequences. It worked for years, which is why we saw ransomware attacks dominate headlines from 2018 through 2023.
But ransomware has problems. Encryption requires significant computational resources. Deploying encryption across large networks creates massive technical signatures that security teams can detect. Decryption keys need to be managed and secured, adding complexity. Recovery is often possible through backups, insurance, or even decryption tools from international law enforcement agencies. And most importantly, encryption creates immediate operational crisis that forces companies to involve law enforcement, regulatory agencies, and incident response teams.
File theft avoids all these problems. An attacker breaks into a network, copies sensitive files to external servers they control, and quietly exits. The company has no idea anything happened until they see their files published on a criminal website. There's no immediate operational impact, no system downtime, no obvious forensic evidence of the breach until attackers want there to be. It's stealthy, efficient, and extremely difficult to defend against because you can't encrypt your way out of a theft.
The economics are compelling too. A sophisticated data theft operation requires maybe 2-3 skilled attackers and some rented infrastructure. A full ransomware operation requires technical expertise with encryption, key management, payment processing, customer service for ransom negotiations, and legal infrastructure to launder cryptocurrency. Why build all that complexity when you can just steal files and let the threat of publication do the negotiating?
This shift has profound implications for corporate security. Companies have spent the last five years focusing on detecting and stopping encryption deployment. They've invested in endpoint detection and response tools, backup systems, and recovery procedures specifically designed to counter ransomware. But file theft is invisible until the attacker decides to make it visible. You can't detect what's being stolen if attackers move slowly and carefully. You can't stop file exfiltration if they're using legitimate cloud services or hiding data in normal network traffic.
Nike's breach appears to follow this file-theft model perfectly. Hackers got in, found interesting data, copied it, got out, and then surfaced publicly only after they'd secured the files. There was no encryption deployed, no demand for ransom through encrypted notes on the network, no immediate crisis. Nike probably didn't even know they'd been breached until World Leaks announced it publicly.
The implications:
File theft is fundamentally harder to defend against because:
- Data exfiltration can occur slowly without triggering alerts
- Legitimate cloud services mask malicious data transfer
- Attackers don't need to maintain presence after theft completes
- Detection requires behavioral analysis, not signature-based detection
- Volume-based thresholds miss careful, deliberate copying
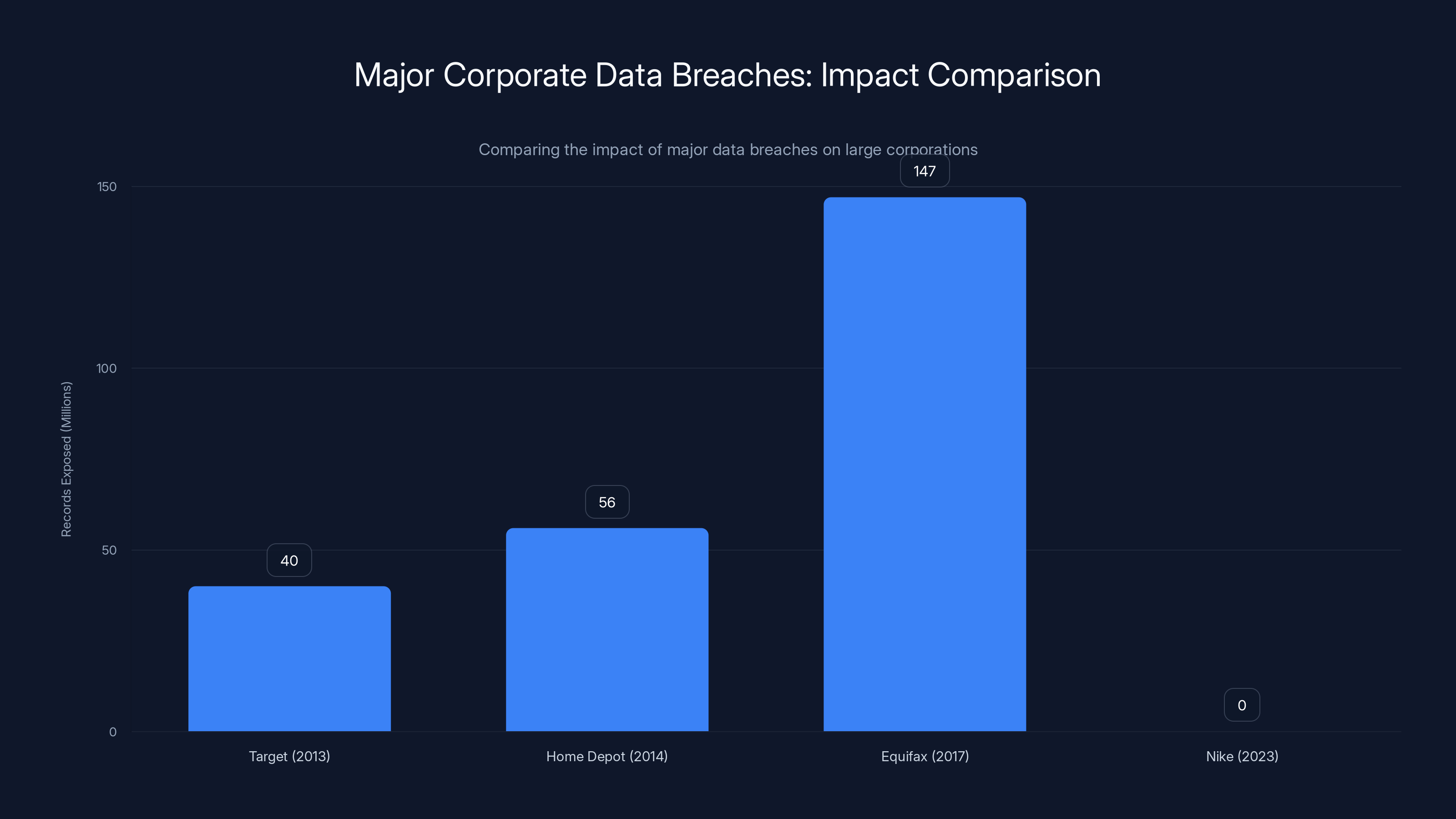
Nike's breach is unusual as it's the first major incident for the company, contrasting with significant breaches at Target, Home Depot, and Equifax. Estimated data for Nike as no records exposed are confirmed.
Nike's Official Response: What the Company Is Saying
Nike's official statement on the breach was carefully crafted corporate language designed to acknowledge the problem without confirming specific details. Here's what the company said, and more importantly, what it actually means.
The official Nike statement, shared with multiple tech media outlets, reads: "We always take consumer privacy and data security very seriously. We are investigating a potential cybersecurity incident and are actively assessing the situation."
Notice what Nike didn't say. They didn't confirm the breach happened. They didn't specify what data was stolen. They didn't provide a timeline for when the breach occurred or when they discovered it. They didn't announce any notification procedures for affected parties. They're using legally careful language that keeps maximum flexibility while acknowledging enough to prevent being accused of cover-ups later.
This is actually pretty standard corporate crisis communication in the security space. Nike's legal team almost certainly advised against making any specific confirmations until they've completed a full investigation. Why? Because specific confirmations can create legal liability. If Nike says "only design data was stolen" and it turns out employee records were also compromised, suddenly the company faces lawsuits. If they say "we discovered the breach on this date" and forensics later show it happened months earlier, they look incompetent. Better to stay vague until you're certain.
That said, Nike's lack of transparency here is frustrating but not unusual. Most companies handle breaches this way because they're dealing with competing pressures: legal teams demanding caution, PR teams demanding reassurance, security teams demanding honesty, and executives demanding that everything stays quiet. The result is usually bland corporate statements that satisfy nobody.
What's notable is what Nike is doing: they're investigating. That suggests they're bringing in external forensics specialists, potentially law enforcement, and definitely their cybersecurity team. They're probably reconstructing network logs, identifying which systems were accessed, determining the scope of the theft, and building a timeline of events. That investigation will take weeks or months.
Nike's statement also doesn't mention whether they're negotiating with World Leaks. Companies often work through intermediaries when dealing with data theft threats. Cybersecurity insurance companies, threat intelligence firms, and negotiation specialists sometimes engage with threat actors to understand the scope of the breach and potentially negotiate payment. Nike might be doing this quietly while maintaining public silence.
The investigation process Nike is undertaking typically follows these steps:
- Immediate containment: Isolate compromised systems, change credentials, review access logs
- Scope assessment: Determine which systems were accessed and what data was copied
- Timeline reconstruction: Figure out when the breach started, how long attackers had access, when exfiltration occurred
- Evidence preservation: Document everything for potential law enforcement involvement
- Notification preparation: Prepare legal and PR responses for regulatory agencies and the public
- Remediation: Patch vulnerabilities, update security controls, monitor for ongoing access
- Public disclosure: Release carefully worded statements once the investigation is sufficiently complete
Nike is probably somewhere in the middle of this process right now. The company has likely already contained the immediate issue, assessed scope, and started working on remediation. The public statement we've seen is probably step five: notification preparation.

Historical Context: Why Nike's Breach Is Unusual
Here's something worth understanding about Nike's cybersecurity history: the company has largely avoided major, publicly reported cybersecurity incidents until now. That's actually remarkable given Nike's size, profile, and the relentless pressure that major corporations face from sophisticated threat actors every single day.
Compare Nike to other major corporations that have experienced significant breaches. Target's 2013 breach exposed the credit card information of 40 million customers and led to massive lawsuits, settlements, and a complete overhaul of the company's security infrastructure. Home Depot's 2014 breach exposed 56 million payment card details and cost the company hundreds of millions in settlements and remediation. Equifax's 2017 breach exposed Social Security numbers and personal information for 147 million people and resulted in a $700 million settlement.
Nike's historical record has been clean. The company hasn't publicly confirmed any major cyberattack on core systems since it became a digital powerhouse. This isn't luck, and it isn't because Nike is inherently more secure than every other company. It's likely a combination of significant security investment, relatively competent incident response, and the fact that attackers have plenty of easier targets.
That dynamic is changing. World Leaks appears to be systematically targeting large, well-known companies because the publicity increases the likelihood of payment. Nike's size, global profile, and valuable internal data make it an attractive target. The company probably thought its security was good enough. But "good enough" in 2023 is increasingly "not good enough" in 2025.
This breach also stands out because it's the first major public Nike security incident in the cloud era. The company has massive cloud infrastructure, thousands of distributed employees, complex supply chains, and digital systems that touch every part of the business. That expanded attack surface is probably why Nike finally got breached. It's not that security got worse. It's that the complexity of modern corporate infrastructure means more places for attackers to find vulnerabilities.
The timing is also interesting. World Leaks announced the Nike breach in 2025, relatively early in the group's operations. This suggests the hacking group is moving quickly to breach major targets and build its reputation. Publishing major corporations on their data leak site creates publicity that helps attract potential customers and establish credibility in the criminal underground. Nike's name recognition works in World Leaks' favor because it proves they have serious capabilities.
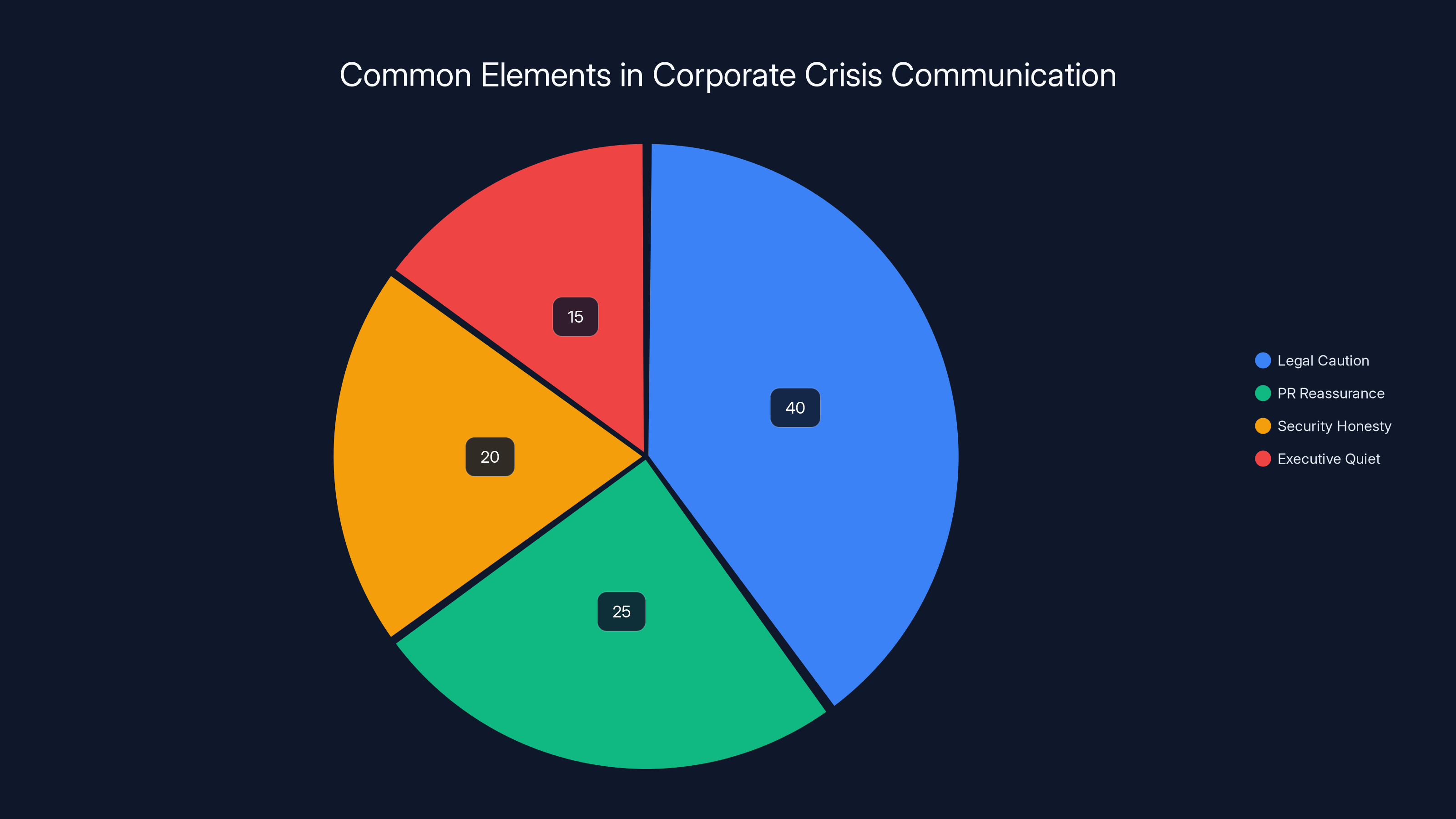
Estimated data shows that legal caution often dominates corporate crisis communication, followed by PR reassurance, security honesty, and executive quiet demands.
What Data Could Be Worth to Competitors and Criminals
When cybercriminals steal 1.4TB of Nike's design and manufacturing data, they're not stealing random files. They're stealing intellectual property worth hundreds of millions of dollars. Understanding what makes this data valuable helps explain why hackers targeted Nike and why the company is taking this seriously.
Design data is the crown jewel of athletic footwear companies. Nike spends billions annually on product research and development. Teams of designers, engineers, and product managers spend months or years creating new shoe designs. They test materials, iterate on prototypes, analyze biomechanics, and fine-tune aesthetics. A successful new shoe line can generate billions in revenue. A failed design wastes hundreds of millions. The intellectual property embedded in design files represents the accumulated knowledge, creativity, and capital investment of hundreds of people.
Manufacturing specifications are equally valuable. Nike doesn't actually manufacture most of its shoes in-house. The company contracts with manufacturing partners in Vietnam, China, Indonesia, and other countries. Those manufacturers need detailed specifications: material specifications, construction techniques, quality standards, testing procedures, timelines, and cost targets. Detailed manufacturing documentation allows a competitor or counterfeiter to produce functionally identical products.
Supply chain information reveals Nike's network of suppliers, manufacturers, and logistics partners. This data shows who makes Nike's shoes, where they're made, how many units are produced, what materials are sourced from where, and how products flow through distribution networks. Competitors could use this information to court Nike's manufacturers or disrupt supply chains. Counterfeiters could identify the exact factories where Nike products are made and potentially insert counterfeit products into legitimate supply chains.
Processes and procedures documentation shows how Nike operates internally. How does the company manage product development timelines? What's the approval process for new designs? How does Nike test products before market release? How does quality assurance work? This operational intelligence helps competitors understand Nike's decision-making, timeline, and strategic priorities.
The criminal value proposition:
-
Direct sale to competitors: Adidas, Puma, or other athletic companies would pay millions for Nike's design and manufacturing specifications. They could accelerate their own product development or copy successful Nike innovations.
-
Counterfeit production: Criminal organizations could manufacture counterfeit Nike products that are nearly identical to legitimate merchandise. Detailed manufacturing specs make counterfeits much more convincing and harder to detect.
-
Extortion through publication: World Leaks threatens to publish stolen data, which forces Nike to choose between paying ransom or having proprietary information publicly available. Once published, the data loses value, so the threat is most potent before publication.
-
Information aggregation: Criminal organizations could combine Nike data with stolen data from suppliers, manufacturers, and logistics partners to build a complete picture of Nike's operations. This comprehensive view is worth significant money in criminal and competitive circles.
The monetary value of this data in criminal markets could easily exceed
Nike's decision whether to pay is complicated. Paying ransom rewards criminals and guarantees they'll target more companies. Not paying means the data gets published, competitors and counterfeiters get access, and the company faces the operational and reputational damage of a major public breach. There's no good choice, just varying degrees of bad.
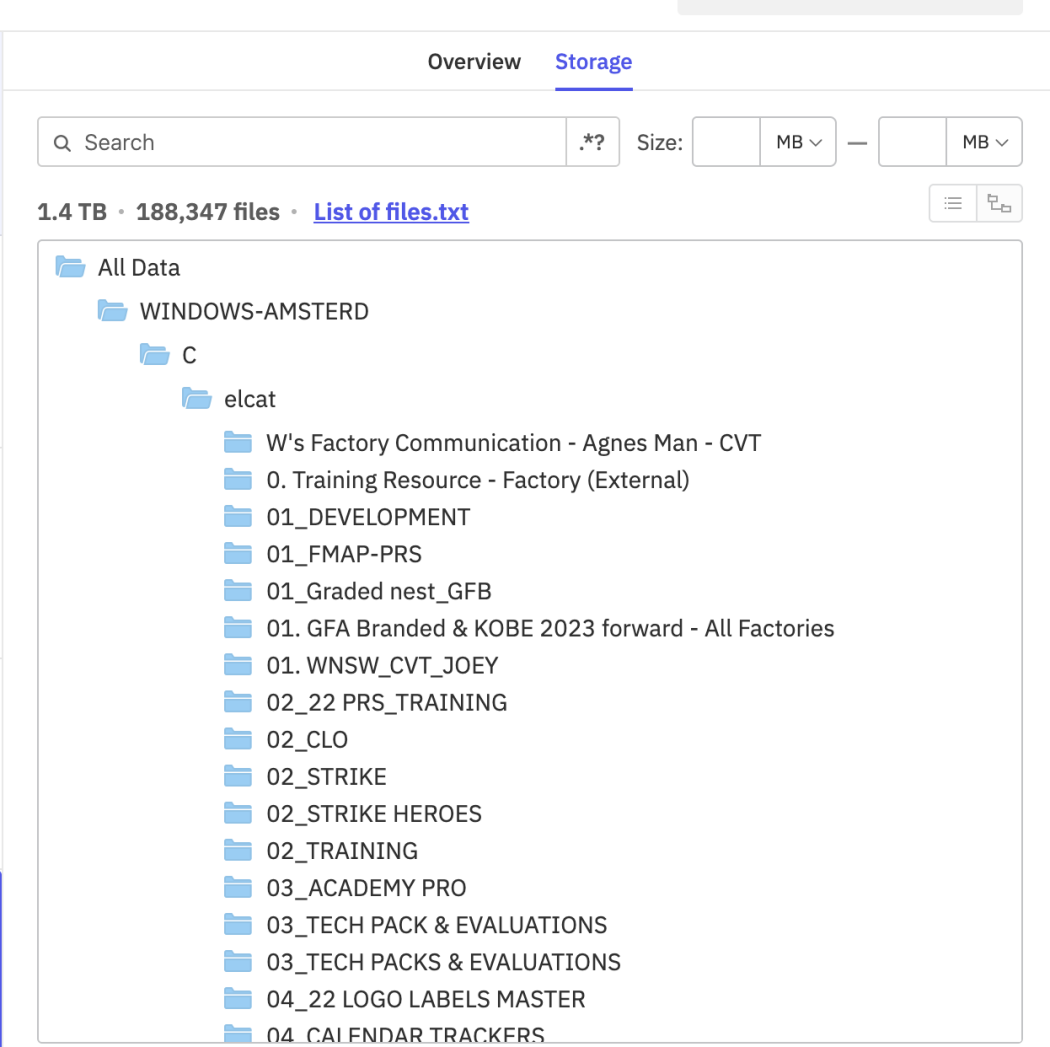
How Nike's Systems Probably Got Breached
We don't know exactly how attackers got into Nike's systems, but we can make educated guesses based on how World Leaks operates and common attack patterns. Understanding the likely attack vector helps explain why even companies with good security still get breached.
World Leaks and similar groups typically use one of several approaches to gain initial access to target networks:
Phishing and Social Engineering: The most common attack vector is still phishing emails targeting employees with access to critical systems. An attacker sends a convincing email that appears to come from Nike IT or another trusted source, tricking an employee into clicking a malicious link or downloading a trojanized file. Once the employee clicks, malware gets installed on their machine, giving attackers a foothold in the network.
Phishing is devastatingly effective because it targets human behavior rather than software vulnerabilities. You can patch every software vulnerability on the planet, but you can't eliminate the possibility that a tired employee might click the wrong link at 6 PM on a Friday. World Leaks probably conducted targeted phishing campaigns against Nike employees, focusing on people with access to sensitive systems.
Exploited Vulnerabilities: The second most likely vector is exploitation of unpatched vulnerabilities in exposed systems. Nike probably runs thousands of internet-facing applications: employee portals, customer websites, API endpoints, remote access systems, etc. Any of these systems might have vulnerabilities that haven't been discovered or patched yet. An attacker could scan for these vulnerabilities, find one that works, and exploit it to get initial access.
Common vulnerable systems include:
- VPN appliances that allow remote access
- Web applications with SQL injection or other injection flaws
- API endpoints with broken authentication
- Collaboration tools with remote code execution bugs
- Email systems with known exploits
Compromised Credentials: Another likely vector is stolen or compromised credentials. Maybe an employee's password was compromised in a previous breach of another company. Maybe an employee used the same password across multiple sites. Maybe a contractor or third-party vendor had weak credentials that got discovered. Once attackers have valid credentials, they can often just log into systems like legitimate employees, making detection extremely difficult.
Supply Chain Compromise: Nike works with thousands of vendors, suppliers, contractors, and partners. Any of those relationships could be the attack vector. An attacker might compromise a vendor's systems, get access to vendor credentials, or plant malware that propagates through vendor software. Once inside through the vendor relationship, attackers can move to Nike's critical systems.
Once attackers have initial access through any of these vectors, they execute a multi-stage attack:
- Establish persistence: Install malware or backdoors that survive reboots and system changes, ensuring continued access
- Escalate privileges: Use techniques to gain higher-level access that allows interaction with more systems
- Move laterally: Discover other systems on the network and compromise them to reach sensitive data
- Find valuable data: Locate design files, manufacturing specs, business data, and other high-value information
- Exfiltrate data: Copy the identified data to attacker-controlled infrastructure
- Cover tracks: Delete logs, disable monitoring, and remove evidence of the compromise
- Maintain access: Keep backdoors open so the attacker can return later if needed
The entire process from initial access to successful data exfiltration probably took weeks or months. World Leaks isn't in a hurry. They want to get out with as much valuable data as possible. The slower they move, the less likely detection systems catch them. Once they have the data, they go quiet for a while before threatening to publish it.
Nike probably didn't detect the breach until World Leaks announced it publicly. That's the current state of affairs in cybersecurity. Many sophisticated attackers exfiltrate data without being detected, then surface publicly to extort the target. The victim finds out they've been breached from a press release on a criminal website, not from their own security monitoring.
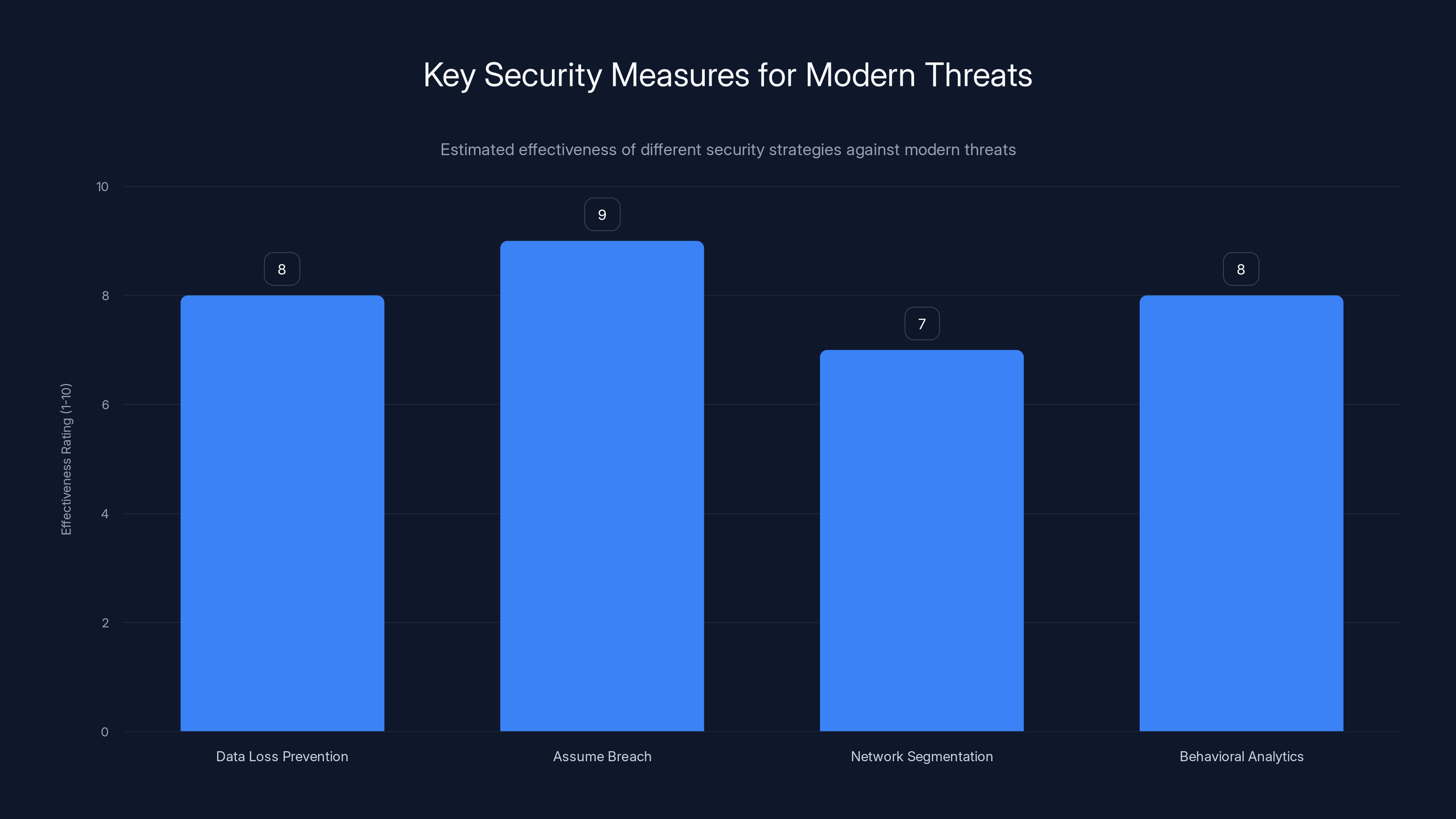
Assuming breaches and implementing robust data loss prevention are rated highly effective strategies against modern threats. Estimated data.
The Extortion Economics: Why Companies Sometimes Pay Ransom
When a threat actor like World Leaks steals your data and threatens to publish it, the economics of ransom payment become surprisingly complex. Understanding why some companies pay can illuminate the systemic issues that keep data theft profitable and recurring.
Let's work through the financial calculation from Nike's perspective. The company needs to assess the cost of paying ransom versus the cost of data publication. On the payment side, World Leaks will probably demand somewhere between
On the publication side, the costs are harder to quantify but potentially much higher. If Nike's design and manufacturing data gets published:
-
Competitive disadvantage: Competitors gain access to Nike's product roadmap, manufacturing techniques, and supplier network. This could cost Nike hundreds of millions in lost market share over coming years as competitors accelerate product launches and improve manufacturing efficiency.
-
Counterfeit goods: Criminal organizations could produce higher-quality counterfeit Nike products, potentially costing the company 5-10% of revenue through lost sales and brand damage.
-
Supply chain disruption: Competitors might recruit Nike's manufacturers or suppliers once they understand Nike's operations. This could disrupt production and increase manufacturing costs.
-
Reputational damage: Public knowledge of a major security breach could damage Nike's brand, especially if customers worry about data security.
-
Regulatory fines: Depending on which data was accessed and which countries' regulations apply, Nike could face regulatory fines. Though since Nike says no customer PII was stolen, regulatory fines are probably minimal.
When you stack up these costs, paying $20 million to prevent publication starts looking economically rational. The company pays a small percentage of annual revenue to avoid hundreds of millions in potential losses. From a purely financial perspective, it makes sense.
But here's the systemic problem with that logic: when companies pay, it validates the business model for threat actors. If Nike pays $20 million, World Leaks proves to its investors and partners that they can make serious money from data theft extortion. The group becomes more active, targets more companies, and other criminal groups copy the model. Every ransom payment funds future attacks against more companies.
Insurance companies have complicated this calculus. Cyber insurance now covers ransom payments in some cases, making it easier for companies to justify payment. But insurance also creates perverse incentives: if the insurance company is paying, the victim company has less incentive to invest in strong security. Why spend money on security when insurance will cover the ransom?
Law enforcement discourages ransom payment, arguing it funds criminal organizations and makes future attacks more likely. But from an individual company's perspective, paying is often the rational choice. This creates a classic prisoner's dilemma: everyone would be better off if nobody paid ransom, but each individual company is better off paying than not paying.
The ransom negotiation process (if Nike chooses to engage):
- Initial demand: World Leaks demands a specific amount, usually high, leaving room for negotiation
- Negotiation: Nike's security team (or hired negotiators) contacts the threat actor through secure channels to discuss payment
- Proof of data: Threat actors provide samples proving they have valuable data
- Price agreement: Through back-and-forth negotiation, a price is agreed upon
- Payment setup: Details for payment transfer are arranged, usually through cryptocurrency
- Payment transfer: Money is transferred to attacker-controlled cryptocurrency wallets
- Data confirmation: Threat actors claim the data will be deleted (no guarantee they actually delete it)
The entire process usually takes 2-4 weeks if the company decides to negotiate.

Security Lessons: How Companies Should Respond to Modern Threats
The Nike breach should serve as a wake-up call for every large organization: your current security approach is probably inadequate for 2025's threat landscape. Sophisticated attackers like World Leaks are moving faster, targeting bigger companies, and proving that traditional security controls don't catch everything. Here's what companies should actually be doing differently.
First, implement robust data loss prevention: Companies need systems that can detect when large amounts of sensitive data are being copied or transferred. If World Leaks had attempted to exfiltrate 1.4TB from Nike, detection systems should have caught it. But many companies don't have proper data loss prevention in place, either because it's expensive or because it's not properly configured.
Data loss prevention means:
- Monitoring all data transfers leaving the network
- Alerting when suspicious volumes of data move to external storage
- Blocking transfers of known sensitive files without proper authorization
- Tracking cloud uploads that might hide data exfiltration
Second, assume breach is inevitable: The old security model was about preventing breaches. The new model is about detecting breaches faster and limiting damage once they happen. Companies should operate under the assumption that attackers WILL get into the network at some point. The question isn't if, but when and how quickly you detect them.
This means:
- Implementing aggressive logging and monitoring of all network activity
- Using behavioral analytics to detect unusual access patterns
- Maintaining detailed forensic records so you can reconstruct attacks
- Planning incident response procedures before incidents happen
- Regularly testing incident response procedures
Third, segment networks and control lateral movement: Once attackers get into a network, they typically move laterally through systems to find valuable data. If Nike had properly segmented its network, attackers might have been limited to a small portion of systems. Instead, they apparently had enough access to find and copy massive amounts of data.
Network segmentation means:
- Separating critical data systems from general-use systems
- Requiring strong authentication to move between network segments
- Monitoring traffic between segments for suspicious patterns
- Limiting what each system can access to only what's necessary
Fourth, implement zero-trust architecture: Traditional security assumes that anything on your internal network is trustworthy. Zero-trust architecture assumes nothing is trustworthy unless it can prove otherwise. Every access request requires authentication and authorization, regardless of whether it comes from inside or outside the network.
Fifth, invest heavily in threat intelligence: Companies need to understand what attackers are targeting them. World Leaks isn't randomly selecting targets. They're probably researching Nike, understanding valuable data, and planning attacks specifically designed to access that information. Nike should have known it was being targeted.
Threat intelligence means:
- Monitoring underground forums where attackers discuss targets
- Tracking indicators of compromise from previous attacks on similar companies
- Understanding which threat actors are interested in your industry
- Predicting which of your systems are most likely to be targeted
Sixth, demand security from vendors and partners: Nike works with thousands of suppliers and partners. Any of them could be the weak link that allows attackers into Nike's systems. Nike should require security standards from vendors, audit their security practices, and monitor their systems for breaches that could compromise Nike.
Seventh, conduct regular penetration testing: Nike should hire security firms to attempt to break into the company's systems regularly. This kind of controlled testing helps identify vulnerabilities before attackers find them. If Nike had conducted thorough penetration testing, they might have discovered the vulnerabilities that World Leaks exploited.
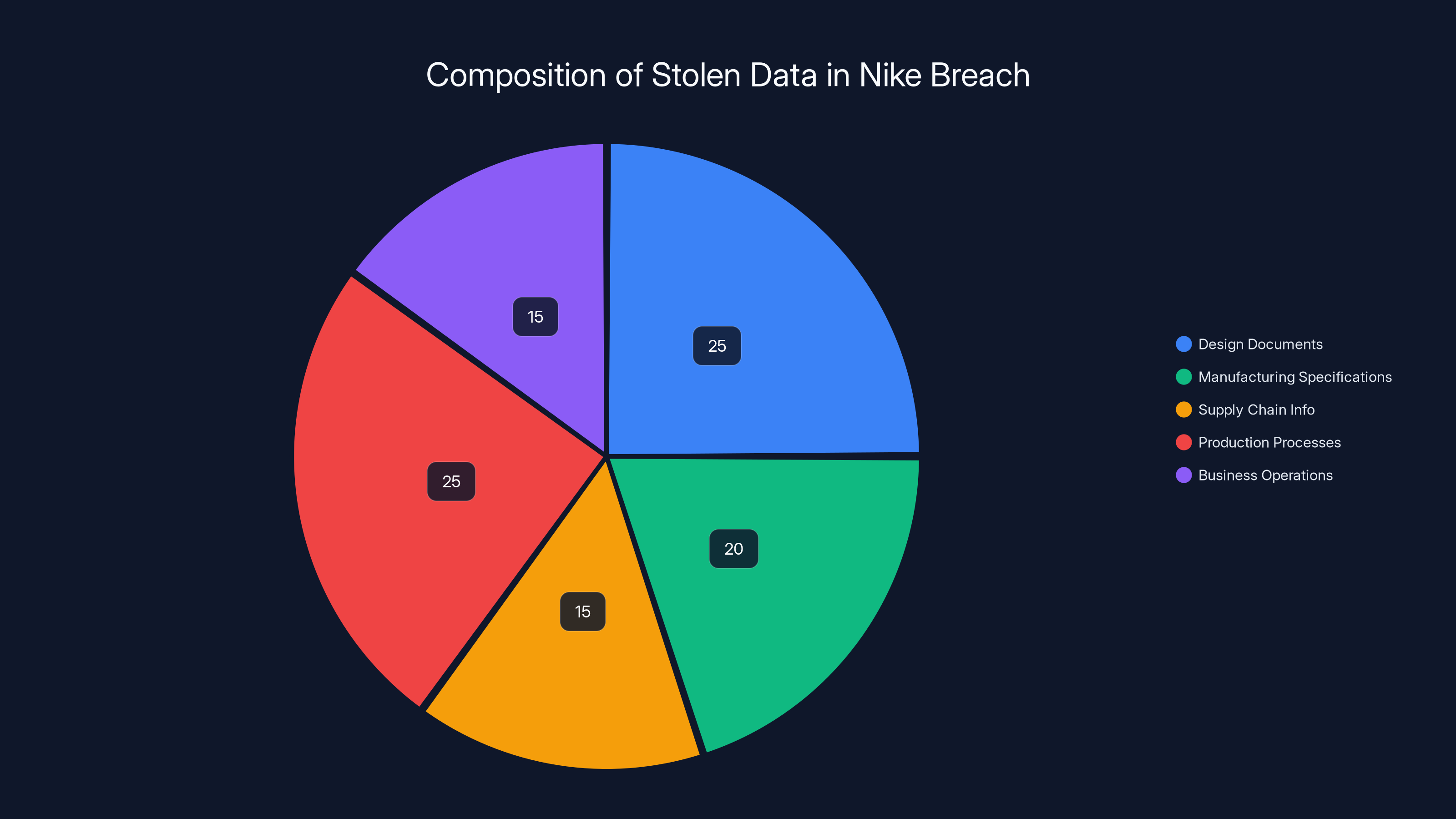
The stolen data from the Nike breach is estimated to be composed of design documents (25%), manufacturing specifications (20%), supply chain information (15%), production processes (25%), and business operations data (15%). Estimated data.
What This Means for Nike Customers and Employees
If you're a Nike customer, employee, or partner, the key question is probably: does this breach affect me? The answer is probably no, but it depends on what you're worried about.
For Nike customers: The breach almost certainly doesn't expose your payment information or personal data. Nike explicitly stated that customer personal information wasn't compromised. Your credit card data is (probably) safe. Your order history is (probably) safe. Your address and phone number are (probably) safe. What was stolen was internal design and manufacturing data, not customer data.
That said, it's not a bad idea to take basic precautions. Monitor your Nike account for suspicious activity. If you notice purchases you didn't make or login activity from unfamiliar locations, change your password immediately. Enable two-factor authentication if available. But there's no need to panic or assume your identity has been stolen.
For Nike employees: The situation is slightly different. If you're a Nike employee in design, manufacturing, supply chain, or any role with access to sensitive business data, this breach represents a risk. Your work could be accessed by competitors. Trade secrets you've worked on could be published. But again, personal employment information doesn't appear to have been stolen, so your Social Security number and financial information are probably safe.
Nike employees should expect increased security scrutiny going forward. The company will probably implement more aggressive authentication requirements, more monitoring of data access, and more restrictions on what employees can copy or transfer. These security measures are inconvenient but necessary.
For Nike business partners and suppliers: If you supply materials or services to Nike, this breach potentially affects you too. Attackers now have visibility into Nike's supply chain relationships. Competitors know which suppliers Nike uses. This could lead to direct recruitment of suppliers or targeted attacks against your company if attackers want to understand Nike's supply chain more deeply.
Suppliers should expect Nike to implement stronger security requirements going forward. The company will probably require partners to meet specific security standards, undergo security audits, and maintain detailed logs of interactions with Nike systems.
For competitors and the industry: This breach is a wake-up call for the entire athletic apparel industry. If World Leaks can steal Nike's design data, they can probably steal Adidas's, Puma's, or any other major company's data. Expect accelerated investment in security across the industry. Expect more companies to get breached as threat actors expand their targeting. Expect more public breaches announced on data leak sites.

How to Protect Yourself in an Era of Corporate Data Breaches
You can't control whether Nike or any other company gets breached. But you can control how much damage a breach causes to your personal life. Here are practical steps to protect yourself in an era where major corporate breaches happen regularly.
Step 1: Use unique passwords for every account Don't use the same password across multiple websites. If one company gets breached and your password is exposed, attackers have access to all your accounts. Use a password manager to generate and store unique passwords for each site. This is the single most important thing you can do.
Step 2: Enable two-factor authentication everywhere Two-factor authentication (2FA) adds a second verification step beyond just your password. Even if attackers have your password, they can't access your account without also having your phone or authentication app. Enable 2FA on email, banking, shopping accounts, and any site that offers it.
Step 3: Monitor your credit Set up free credit monitoring through Equifax, Experian, or Trans Union. These services alert you if someone tries to open new accounts in your name. Even if your personal information was stolen in a breach, thieves can't do much without accessing your credit to open new accounts.
Step 4: Use a VPN for sensitive transactions When conducting sensitive activities like banking or shopping, use a VPN to encrypt your internet traffic. This prevents potential eavesdropping on public Wi Fi networks. VPNs add a layer of privacy and security to your online activities.
Step 5: Keep software updated Software updates include security patches that fix vulnerabilities. Keep your operating system, browser, applications, and firmware all updated to the latest versions. Attackers exploit unpatched vulnerabilities, so staying current reduces risk.
Step 6: Be skeptical of emails and links Don't click links in unsolicited emails, even if they appear to come from trusted sources. Phishing attacks are the most common way attackers get into corporate networks. If you get a suspicious email, navigate to the website directly rather than clicking the email link. Verify the sender's email address carefully.
Step 7: Use privacy-focused services When possible, use email providers, messaging apps, and web services that prioritize privacy and encryption. Companies like Proton Mail or Signal offer stronger privacy guarantees than mainstream providers. This limits the personal information available if a company gets breached.
Step 8: Limit data you share online The less data you share online, the less can be stolen. Don't provide unnecessary information during account creation. Don't include sensitive details in public profiles. Be cautious about what you share on social media. Every piece of information you withhold is information that can't be stolen.
The Role of Law Enforcement and International Response
When a breach of this magnitude occurs at a major corporation, the response involves more than just the company. Law enforcement agencies, government bodies, and international organizations all get involved. Understanding this landscape helps explain why breaches take time to resolve and why companies sometimes seem slow to respond.
In the United States, the FBI and Secret Service investigate major cybercrimes. Nike probably contacted or was contacted by the FBI immediately after detecting the breach. The FBI's Cyber Division maintains relationships with major corporations and uses breach investigations to gather intelligence on threat actors. If the FBI can identify members of World Leaks, they can potentially pursue prosecution or coordinate international law enforcement response.
International coordination is complex because cybercriminals often operate from countries that don't extradite to the United States. If World Leaks operates from Russia, China, Iran, or other countries with difficult diplomatic relationships, prosecution might be impossible. This dynamic has created a situation where major cybercriminals essentially operate with impunity from within safe havens.
The Department of Justice occasionally secures indictments against international cybercriminals, though conviction and imprisonment is rare. Sanctions against countries that harbor cybercriminals are becoming more common, but they're not particularly effective at stopping criminal activity. The United States and allies have imposed sanctions on Russian hacking groups, Iranian threat actors, and North Korean attackers, but these sanctions mostly just make financial transactions slightly more difficult rather than stopping attacks entirely.
Interpol and Europol coordinate internationally, but they're hampered by limited authority and resources. Investigating international cybercrime requires cooperation from law enforcement in countries where the criminals operate, and not all countries prioritize cybercrime investigation. Russia, China, and other authoritarian governments often protect their own cybercriminals if the group operates against rival countries.
This creates a fundamental asymmetry: companies are expected to defend against nation-state-level threat actors and sophisticated criminal groups that operate with impunity from countries the company can't reach. It's an impossible situation that explains why major breaches continue to happen despite enormous security investments.
Law enforcement does provide some value though. Investigators can help companies understand attack methods, identify threat actors, coordinate response, and potentially pursue prosecution if they can identify and locate perpetrators. But realistically, companies need to assume law enforcement won't solve the problem. Companies need to solve it themselves through better security.
What's Next: Future of Corporate Cybersecurity
The Nike breach is probably just the beginning of a wave of major corporate breaches targeting high-profile companies. World Leaks and similar groups have proven the business model works, and other groups will almost certainly adopt the same approach. Here's what security experts expect in the coming months and years.
Increased targeting of high-profile companies: World Leaks benefits from publicity when major companies get breached. Expect the group to target Fortune 500 companies, government contractors, major healthcare systems, and other high-visibility targets. The publicity increases pressure on companies to pay.
Expansion into critical infrastructure: As file theft becomes more profitable, criminal groups will expand into power grids, water systems, hospitals, and other critical infrastructure. The stakes get much higher when attackers threaten to shut down life-critical systems or publish patient data from hospitals.
Deepening of supply chain compromises: Attackers will increasingly target smaller companies in supply chains leading to major corporations. A breach of a mid-size supplier might provide access to multiple major companies simultaneously. Supply chain security will become paramount.
Evolution of extortion tactics: Threat actors are getting creative beyond just threatening publication. They're threatening to contact customers, threaten to corrupt data, or threaten to contact regulators. The extortion tactics will become increasingly sophisticated and difficult to defend against.
Emergence of data brokers for stolen data: Criminal markets are developing where threat actors sell stolen data to competitors, fraudsters, and other malicious actors. Rather than direct extortion, some groups might sell data to the highest bidder.
Erosion of cyber insurance effectiveness: As claims increase and payouts grow, cyber insurance is becoming more expensive and more restrictive. Eventually, cyber insurance might become unaffordable or unavailable for companies in high-risk industries. This will force companies to self-insure and invest more heavily in actual security.
Regulatory tightening: Governments are imposing stricter data protection and breach notification requirements. The EU's GDPR is just the beginning. Expect more countries to impose similar regulations, forcing companies to invest in security compliance.
Consolidation of security vendors: Companies are realizing they need integrated security solutions rather than piecemeal point products. Expect major acquisitions consolidating the security vendor landscape into a smaller number of comprehensive platforms.
FAQ
What is World Leaks and who operates it?
World Leaks is a cybercriminal group that specializes in stealing corporate data and threatening to publish it unless targets pay ransom. The group is widely believed to be the successor organization to Hunters International, another notorious hacking group that shut down in mid-2025. World Leaks maintains a public data leak site similar to a news website, publishing information about breached companies and stolen data. The group operates with sophisticated technical skills and professional business practices.
How did attackers likely get into Nike's systems?
The exact method is unknown, but most likely vectors include phishing emails targeting employees, exploitation of unpatched software vulnerabilities, compromised credentials from previous breaches, or compromises of vendor or supplier systems. Once attackers gained initial access through any of these vectors, they likely used techniques to escalate privileges, move laterally through the network, and locate valuable data. The entire process probably took weeks or months as attackers moved carefully to avoid detection.
Is my Nike account data exposed in this breach?
No, according to Nike's statement, customer personal information and payment data were not exposed in this breach. The stolen data consisted of internal design and manufacturing information, not customer account data. However, it's still good practice to monitor your Nike account for suspicious activity, enable two-factor authentication, and ensure your password is unique and strong.
What was actually stolen in the Nike data breach?
According to World Leaks and Nike's acknowledgement of the breach, attackers stole approximately 1.4 terabytes of internal data including design documents, manufacturing specifications, supply chain information, production processes, and business operations data. The stolen data includes directories labeled "Women's Sportswear," "Men's Sportswear," "Training Resource - Factory," and "Garment Making Process," indicating comprehensive access to product development and manufacturing infrastructure.
Could this breach affect Nike products or manufacturing?
Not directly. Nike's manufacturing continues uninterrupted because no systems controlling actual manufacturing were encrypted or shut down. However, long-term impact could include competitors using stolen design specifications to accelerate their own products, improved counterfeiting operations using manufacturing details, or supply chain disruptions if competitors recruit Nike's suppliers. The immediate operational impact is minimal, but strategic impact could be significant.
What should companies learn from the Nike breach?
Companies should recognize that data theft is increasingly sophisticated and difficult to detect. The Nike breach demonstrates that even large, well-resourced companies can be compromised by skilled threat actors. Companies should invest in data loss prevention, implement zero-trust security architecture, conduct regular security assessments, segment networks to limit lateral movement, improve threat intelligence capabilities, and assume breach is inevitable rather than trying to prevent all breaches entirely.
Will Nike have to pay ransom to World Leaks?
That's unknown. Nike might negotiate with World Leaks through intermediaries, might work with law enforcement to pursue the group, might pursue litigation, or might simply accept the breach and focus on remediation. Ransom payment is ultimately a business decision based on comparing the cost of payment against the cost of publication. Nike hasn't publicly confirmed whether it's negotiating, and likely won't unless required to by law.
Is my personal information safe if I'm a Nike employee?
Yes, based on Nike's statement, employee personal information was not exposed in this breach. The stolen data consisted of business operational information, not employee personal data. However, employees might see increased security restrictions and monitoring as Nike implements stronger security controls going forward.
How does file theft differ from traditional ransomware?
Traditional ransomware deploys encryption to lock up files and systems, forcing companies to choose between paying ransom or losing access to critical systems. File theft involves simply copying valuable data without deploying encryption, allowing normal business operations to continue. File theft is harder to detect because there's no obvious malicious activity, but it's equally damaging because it compromises intellectual property and sensitive information.
What happens to stolen data after ransom is paid?
There's no guarantee. Threat actors claim they'll delete stolen data after payment, but there's no mechanism to verify deletion actually happened. Even if the primary threat actor deletes data, copies might exist with other criminal groups. Once data is stolen, it's effectively out of the victim's control. This is why many security experts argue ransom payment doesn't actually solve the problem.

Conclusion
The Nike data breach represents a fundamental shift in how modern cybercriminals operate and where corporate security is failing. This isn't a random attack against a vulnerable company. It's a targeted assault against one of the world's most valuable brands by a sophisticated threat actor group that has proven their capabilities across dozens of high-profile breaches. And it demonstrates that even companies with massive resources and dedicated security teams can find themselves on a criminal leak site without realizing they've been breached until they read about it in the news.
What makes this breach significant isn't just the size of the data stolen or the profile of the company targeted. It's what the breach reveals about the current state of corporate cybersecurity. Companies are defending against nation-state threat actors with resources that dwarf their own. Security teams are fighting a losing battle against criminals who operate from countries they can't reach and face minimal consequences for their actions. Traditional security controls are proving inadequate against determined, sophisticated attackers.
The broader trend is clear: file theft has become the preferred attack model because it's more profitable, harder to detect, and more difficult to defend against than traditional ransomware. Ransomware operators are increasingly pivoting to data theft. New threat actor groups like World Leaks are emerging specifically to exploit this model. The security industry is reacting slowly to a threat that's already reshaping the cybercrime landscape.
For Nike specifically, the breach represents a significant strategic setback. Competitors now have access to design specifications, manufacturing processes, and supply chain information that Nike spent decades developing. Counterfeiters will improve their products using stolen manufacturing details. The company's competitive advantage has been compromised. Even if Nike negotiates with World Leaks, even if the immediate crisis passes, the long-term damage is difficult to quantify but potentially enormous.
But the Nike breach is less about Nike and more about what it reveals about corporate security in 2025. It reveals that current approaches are insufficient. It reveals that threat actors are moving faster than companies can defend. It reveals that detection is failing, investigation is slow, and response is reactive rather than proactive. Most importantly, it reveals that this is not a unique incident but rather the new normal. More breaches will follow. More companies will discover they've been compromised. More internal data will end up in criminal hands.
The solution isn't complicated in principle, just expensive and difficult in practice. Companies need to invest heavily in detection and response capabilities rather than assuming prevention will work. Companies need to assume breach is inevitable and focus on limiting damage when it happens. Companies need to segment networks, control data access, monitor for suspicious activity, and maintain detailed forensic evidence. Companies need to partner with law enforcement, coordinate with industry peers, and be transparent with customers.
But most fundamentally, companies need to recognize that the old security model is broken. Building better firewalls and more sophisticated detection won't solve this problem because the problem is that attackers are already inside. The breach happened before Nike detected it. The files were copied before any alarms triggered. By the time Nike realized anything was wrong, the damage was already done.
That's the harsh reality of modern cybersecurity, and the Nike breach is just one more illustration of it. The good news is that companies can improve, invest wisely in security controls that actually work, and significantly reduce risk even if they can't eliminate it entirely. The bad news is that most companies won't invest enough, won't move fast enough, and will continue experiencing breaches like Nike's until the costs of breaches finally exceed the cost of proper security.
For now, the Nike breach serves as a wake-up call, a data point in a growing trend, and a reminder that even mega-corporations with billion-dollar budgets remain vulnerable to determined attackers. It's a sobering lesson in the limits of modern cybersecurity, and unfortunately, it's probably not the last such lesson we'll see in 2025.
Key Takeaways
- WorldLeaks, successor to Hunters International, stole 1.4TB of Nike design and manufacturing data without deploying encryption
- File theft is replacing traditional ransomware because it's more profitable and harder to detect than encryption-based attacks
- Nike customers' payment and personal data were not exposed; breach focused on internal business intelligence and product specifications
- File-based data theft requires comprehensive detection strategies including data loss prevention, behavioral analytics, and network segmentation
- Supply chain compromise represents increasing attack vector as sophisticated threat actors target vendors to access larger enterprise systems
Related Articles
- Under Armour 72M Record Data Breach: What Happened [2025]
- 149 Million Credentials Exposed: The Massive Data Leak Explained [2025]
- VSCode Malicious Extensions: How 1.5M Developers Got Compromised [2025]
- Pegasus Spyware, NSO Group, and State Surveillance: The Landmark £3M Saudi Court Victory [2025]
- AI-Powered Malware Targeting Crypto Developers: KONNI's New Campaign [2025]
- Proton VPN Linux Overhaul 2025: Complete GUI & CLI Guide
![Nike Data Breach: What We Know About the 1.4TB WorldLeaks Hack [2025]](https://tryrunable.com/blog/nike-data-breach-what-we-know-about-the-1-4tb-worldleaks-hac/image-1-1769517468998.jpg)



