Malicious Browser Extensions: The Hidden Threat Hijacking Your Chrome, Firefox, and Edge Browsers [2025]
Your browser extensions feel harmless. That's the problem.
I'll be honest: most people don't think twice about clicking "install" on a browser extension. It seems low-stakes. A translation tool, an ad blocker, a screenshot utility. Millions of users do this every single day without a second thought.
But here's what security researchers just uncovered: over 840,000 people downloaded malicious browser extensions that are actively stealing their data, hijacking their affiliate purchases, and opening backdoors into their computers.
This isn't some obscure corner of the internet. This is Chrome. Firefox. Edge. The browsers you use right now. Extensions sitting in official repositories that looked legitimate, had decent reviews, and seemed perfectly normal. Yet underneath, they were harvesting your browsing habits, injecting tracking code into every page you visit, and participating in ad fraud schemes.
What's worse? This is the second wave. Security researchers at Layer X discovered this new batch of 17 malicious extensions in January 2025. But it's not new. It's the continuation of Operation Ghost Poster, a campaign that was first discovered just a few weeks earlier in December 2024 with a different set of 17 extensions.
The name alone tells you something. Researchers don't give operations poetic names for minor issues. This is organized, persistent, and sophisticated enough that attackers believed they could run it twice and get away with it.
So what do you need to know? Let me break this down with the kind of detail you won't find in a quick news headline.
TL; DR
- 840,000+ downloads: Malicious extensions spread across Chrome, Firefox, and Edge compromised hundreds of thousands of users
- Operation Ghost Poster returns: This is the second wave of a coordinated campaign first discovered in December 2024
- Multiple attack vectors: Affiliate link hijacking, analytics injection, CAPTCHA bypass, ad fraud, and persistent backdoors
- Manual removal required: All extensions were removed from official stores, but users must uninstall them manually from their browsers
- Years of exposure: Some extensions had been available since 2020, meaning victims were compromised for up to five years
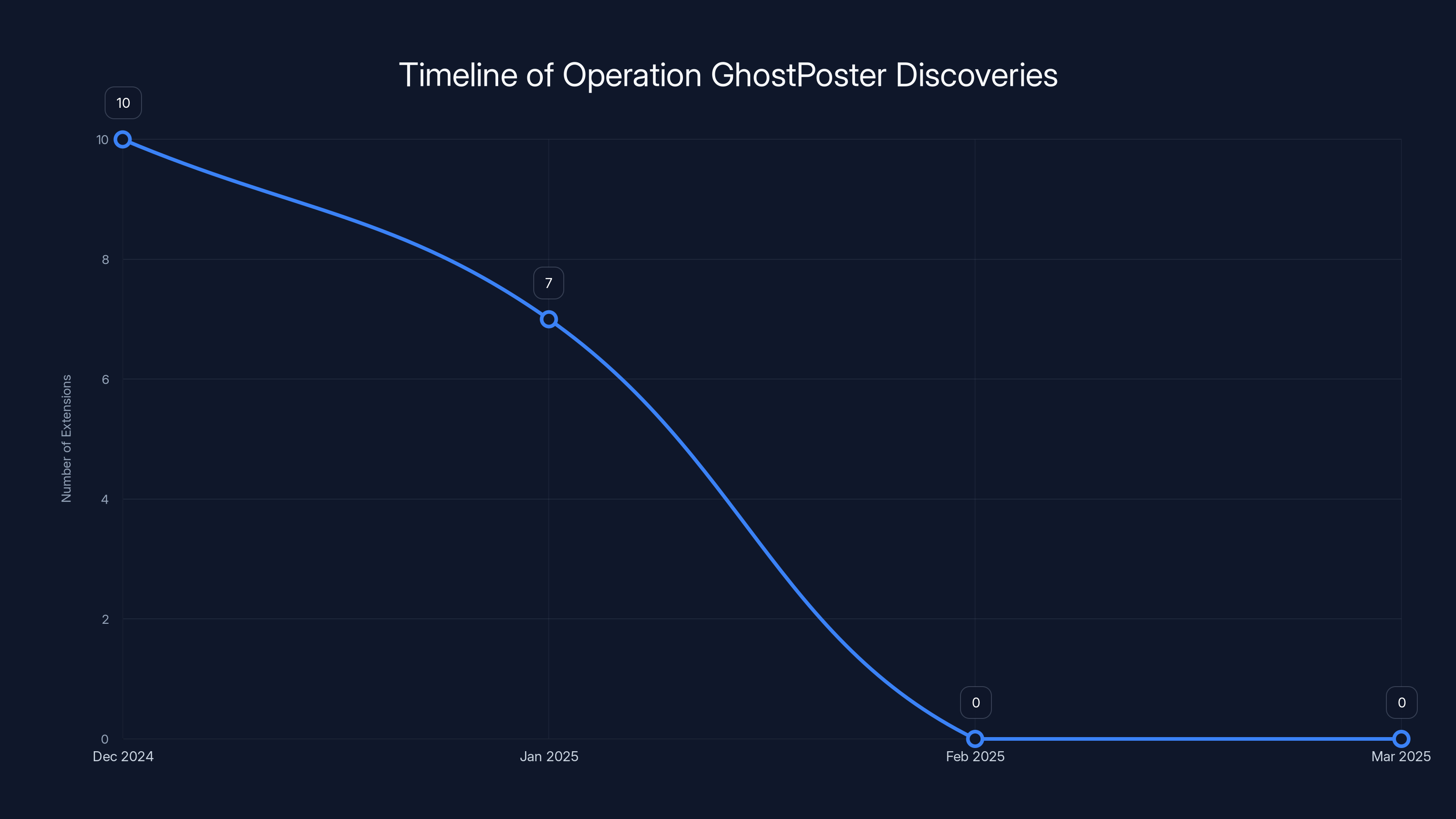
Operation GhostPoster saw two waves of malicious extension discoveries, with a total of 17 extensions found by January 2025. Estimated data based on reported incidents.
What Exactly Are These Malicious Extensions Doing
When you install a browser extension, you're essentially giving it permission to see everything you do online. Every page you visit. Every form you fill. Every purchase you make. Most legitimate extensions need this access for genuine reasons. But malicious ones? They abuse that access completely.
The 17 extensions discovered in this latest batch were doing five specific things that each represent a different kind of threat to your security and privacy.
Hijacking Affiliate Links
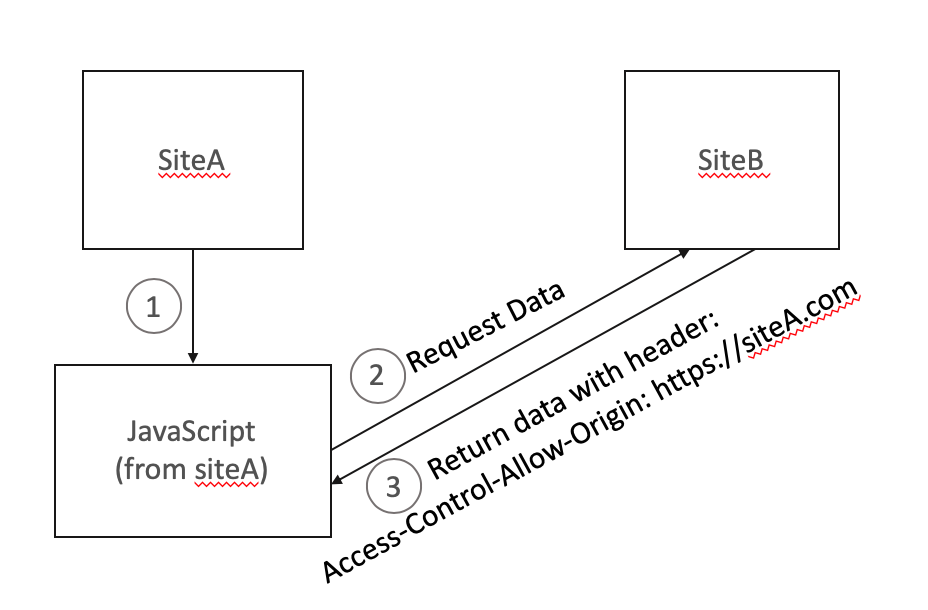
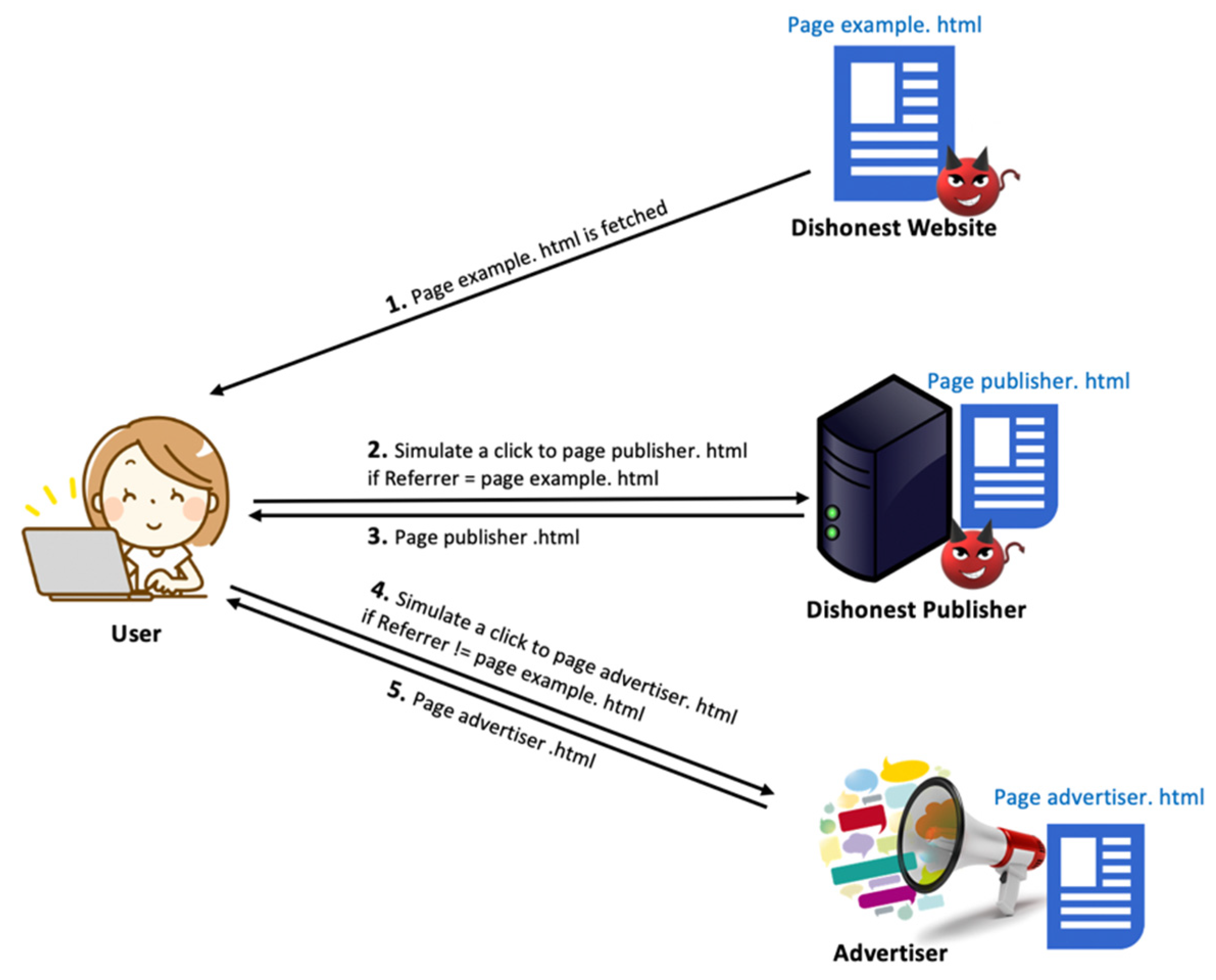
Imagine you visit a tech blog and click on a link to buy a laptop. The content creator gets a commission from that referral. That's how countless creators, YouTubers, and bloggers actually make money. The malicious extensions intercepted those clicks and redirected the affiliate commission to attackers instead. A creator thinks they're getting paid. They're not. The attacker is. This happened at scale across major ecommerce sites like Amazon, eBay, and similar platforms where affiliate commissions matter.
Injecting Tracking and Analytics
Every page you visit after installing one of these extensions got injected with Google Analytics tracking code. Not the tracking code the website owner installed. New tracking code injected by the attackers themselves. That means the attackers saw everything. Your shopping history. Your medical searches. Your financial websites. Your login pages. They built a complete profile of your online behavior.
Stripping Security Headers
Websites send your browser security headers with every response. These headers do things like prevent clickjacking attacks, enforce HTTPS, and protect against other common exploits. The malicious extensions stripped these headers away from every HTTP response. That means the attacker weakened your browser's defenses systematically, making you more vulnerable to man-in-the-middle attacks and other compromise attempts.
Bypassing CAPTCHA with Three Separate Methods
CAPTCHA exists to prove you're human. To prevent automated attacks. These extensions had three different mechanisms to bypass it. That means when the attacker wanted to automate something on your behalf (create accounts, submit forms, make purchases), they could do it without needing you to manually solve CAPTCHA challenges. Automation at scale. Attacks that would normally require human intervention now run fully automated.
Injecting Invisible iframes for Ad Fraud
Most insidious of all: the extensions injected invisible iframes into pages you visited. These iframes showed ads you never saw. Click fraud, where the attacker made it look like you clicked on ads when you didn't. Impression fraud, where ads were charged to advertisers even though nobody real saw them. The iframes self-destructed after about 15 seconds, making them harder to detect. But in those 15 seconds, money changed hands. Advertisers got charged. Attackers profited.
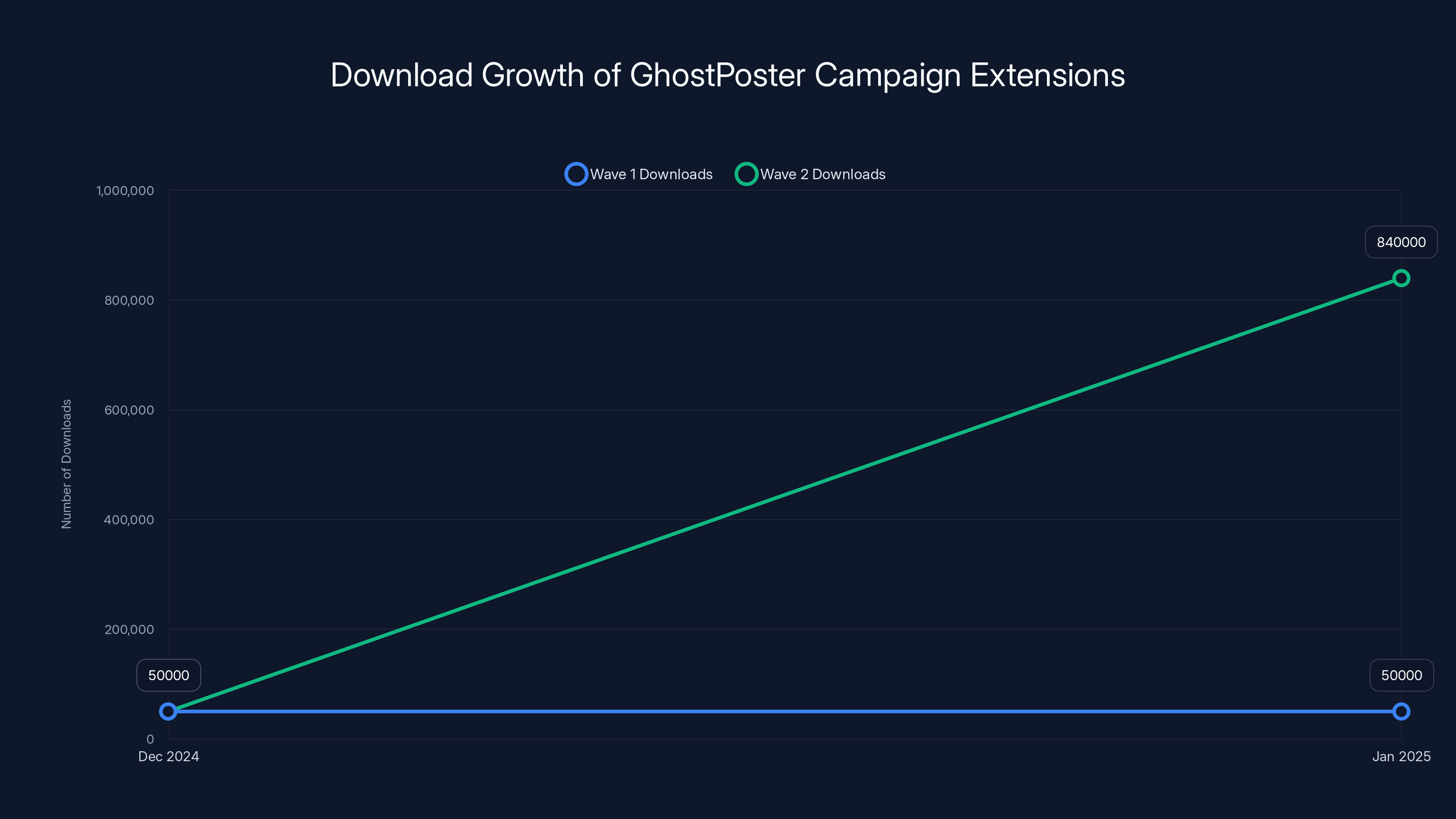
The second wave of the GhostPoster campaign saw a dramatic increase in downloads, rising by 1,580% from 50,000 to 840,000 downloads. Estimated data based on reported figures.
The Technical Sophistication Behind the Attack
When security researchers looked under the hood, they found some genuinely clever tricks. This wasn't an amateurish operation. These people knew what they were doing.
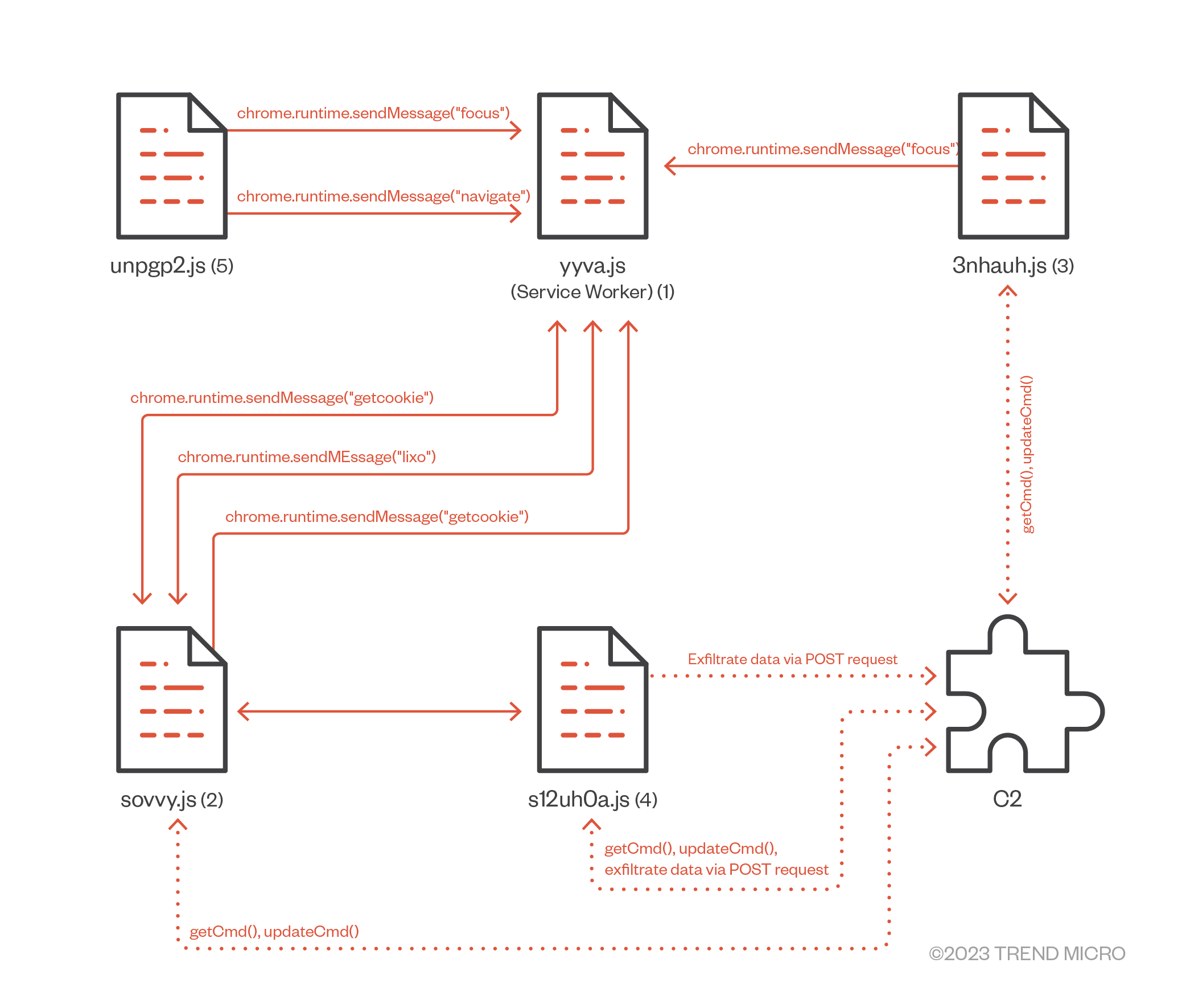
Hidden Payload in PNG Images
The extensions stored malicious JavaScript code inside PNG image files. PNG is an image format. Browsers display images. Security tools scan for malicious code. By hiding the code inside an image file, the attackers created plausible deniability. If a security researcher found the extension, they might not think to extract code from image files. The code served as instructions for downloading the actual malware payload from a remote server.
This technique shows sophistication. It's not common. It requires understanding image file formats, JavaScript, and how extension loading works.
10% Execution Rate
Here's the truly clever part: the malicious payload only executed 10% of the time. Ninety percent of the time, the extension worked fine. It did what it claimed to do. Translate text. Block ads. Download images. Whatever the legitimate function was, it actually performed it. But one out of every ten times you used the extension, the malicious payload triggered instead.
Why? Because it makes the extension harder to detect and analyze. If you install an extension and it works fine, you're not suspicious. If it works fine 90% of the time and occasionally does weird stuff, you might blame network issues or other problems. The attacker gets 90% of the cover of legitimacy and still executes the malicious payload enough times to be profitable.
Multi-Stage Download Architecture
The extension itself wasn't the malware. The extension downloaded the malware from a remote server. This architecture matters because it means if you inspect the extension code, you might not find the malicious payload at all. It's being downloaded dynamically. Security researchers checking the extension store might approve it because the extension as stored appears harmless. The malicious code comes later, from an external source controlled by the attacker.
The Timeline: How Ghost Poster Became a Campaign
Operation Ghost Poster wasn't born in 2024. This needs context.
In early December 2024, security researchers at Koi Security discovered the first wave of this campaign. They found 17 malicious extensions that had been downloaded about 50,000 times combined. The attackers were doing all the things I described above. Hijacking affiliates. Injecting tracking. Building backdoors.
But instead of this being a one-off discovery and removal, researchers found out in January 2025 that the attacker didn't stop. They released a second wave. Not the same extensions. Different ones. But using the same exact playbook. Same techniques. Same goals. Same infrastructure, possibly.
Layer X discovered this second batch with 840,000 downloads. That's a massive jump. The first wave got 50,000 downloads across 17 extensions. The second wave, also 17 extensions, got 840,000 downloads. That's a 1,580% increase in adoption.
Why did the second wave do so much better? We don't know for certain. Maybe the first wave taught the attackers which extension names and categories worked best. Maybe they got better at marketing them. Maybe the discovery and removal of the first wave actually helped because it didn't scare the public enough.
But the important point is this: attackers found a method that worked, got caught, and immediately tried again with a different set of extensions using the same infrastructure and techniques.
Some Extensions Have Been Running Since 2020
This is perhaps the most alarming detail. Among the newly discovered extensions, some were first uploaded to browser repositories in 2020. That's five years ago. Five years of potential compromise for users who installed those extensions.
Think about what changed in your life between 2020 and 2025. Your finances. Your health. Your relationships. Your job. If an extension was backdoored the entire time, attackers saw all of it.
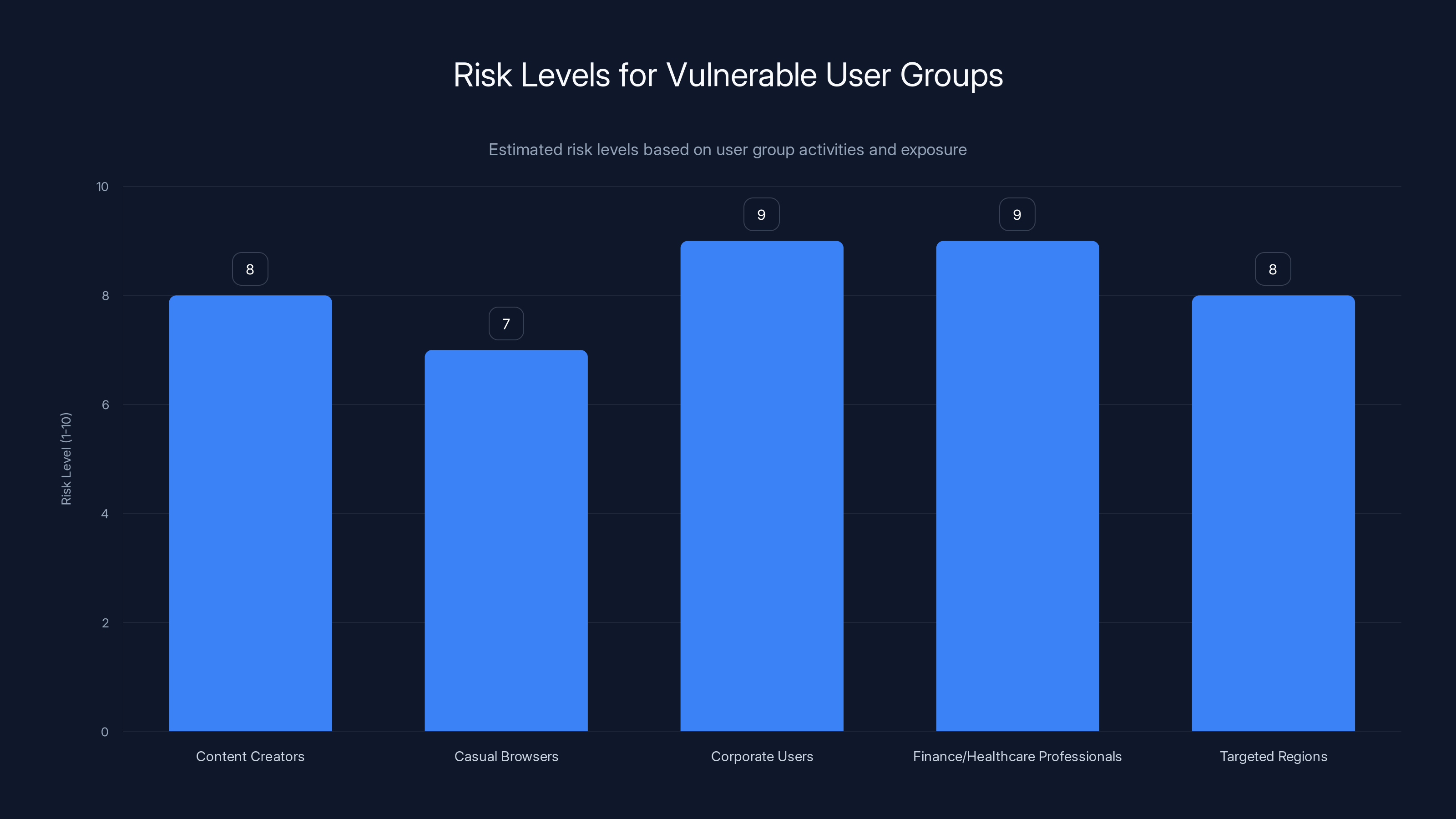
Corporate users and financial/healthcare professionals face the highest risk due to potential data sensitivity and network exposure. Estimated data based on user activities.
Why Browser Repositories Let This Happen
This is the question everyone asks: how did these extensions get into Chrome, Firefox, and Edge official stores?
The answer is that automated approval processes aren't perfect. Not even close.
The Approval Process Problem
Browser vendors like Google, Mozilla, and Microsoft receive thousands of extension submissions every day. Manually reviewing every line of code in every extension is impossible at scale. So they use automation. Static code analysis. Sandboxed execution. Reputation checks.
But the attackers knew this. They built extensions that would pass automated checks. The PNG hiding technique bypassed some code scanning. The 10% execution rate meant the malicious payload wasn't present in static analysis. Dynamic behavior might not trigger until the remote payload was downloaded, which happens after approval.
It's a cat-and-mouse game, and right now, the mouse is winning.
Edge Got Hit First
Interestingly, Microsoft Edge seems to have been the initial target. Multiple malicious extensions appeared in Edge's store before spreading to Chrome and Firefox. This suggests attackers might view Edge as having weaker approval processes, or that the Edge install base made it an attractive testing ground for new techniques.
Once the extensions had been validated in Edge and were gaining downloads, the attackers repackaged them for Chrome and Firefox with minor modifications. The stores had less reason to scrutinize them because similar extensions already existed elsewhere.
No Real-Time Monitoring
Browser repositories have monitoring systems, but they're mostly retroactive. Extensions stay in the store until someone reports them, a security researcher finds them, or they trigger monitoring alerts. But real-time monitoring for the kind of behavior these extensions exhibited (hijacking affiliate links, injecting iframes, downloading payloads) is computationally expensive and often bypassed by the techniques described above.
The Complete List of Malicious Extensions
If you installed any of these, you need to uninstall them immediately. Here's the full inventory from the January 2025 discovery:
- Google Translate in Right Click
- Translate Selected Text with Google
- Ads Block Ultimate
- Floating Player (PiP Mode)
- Convert Everything
- Youtube Download
- One Key Translate
- Ad Blocker
- Save Image to Pinterest on Right Click
- Instagram Downloader
- RSS Feed
- Cool Cursor
- Full Page Screenshot
- Amazon Price History
- Color Enhancer
- Translate Selected Text with Right Click
- Page Screenshot Clipper
Look familiar? They look legitimate because they are designed to be. A download tool, a translator, an ad blocker, a screenshot utility. These are the kinds of extensions millions of people use every day. That's exactly why the attackers picked these categories and names.
The previous wave in December had a different set of 17 extensions with similarly legitimate-sounding names and functions.

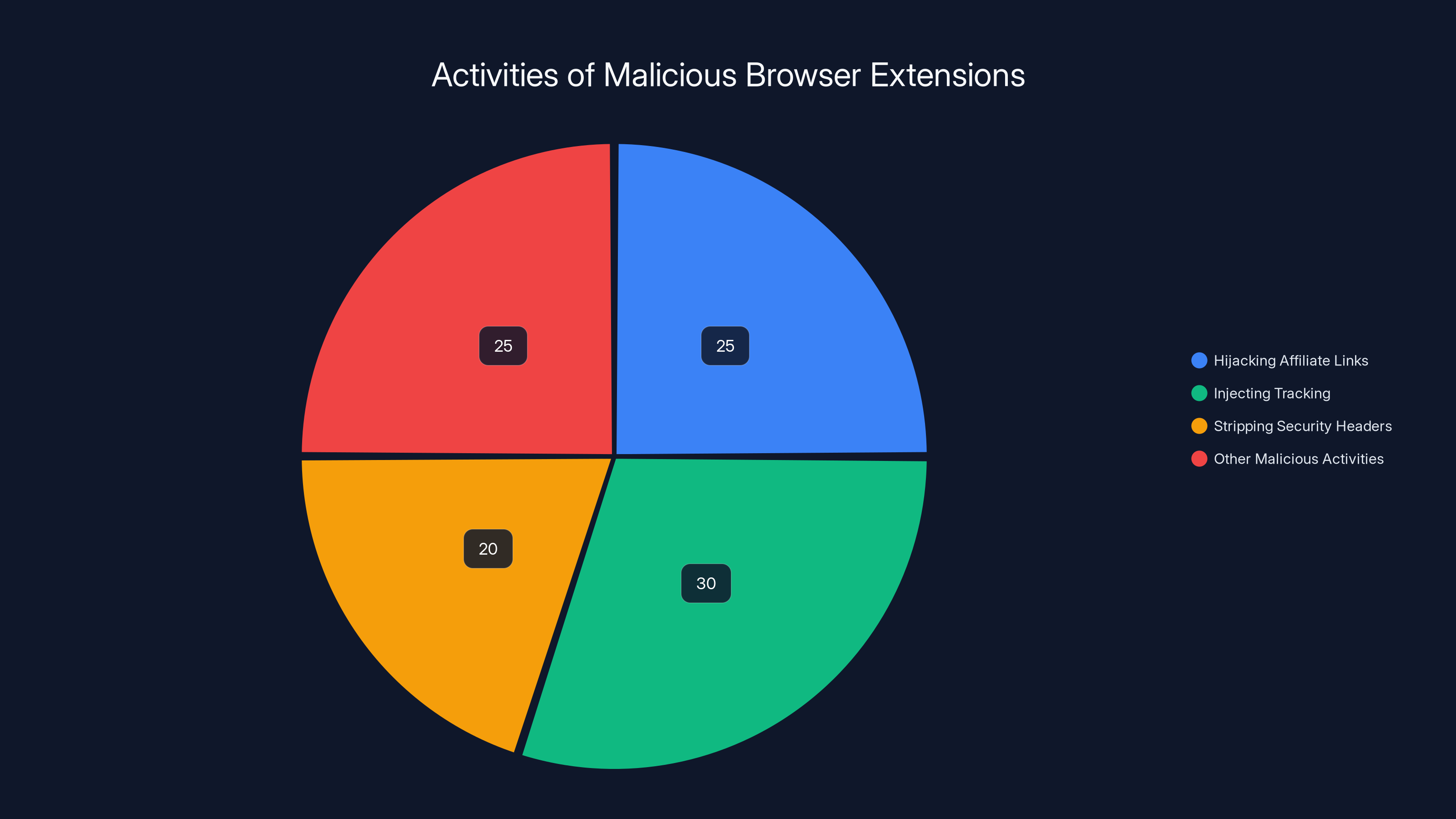
Estimated data shows that injecting tracking code is the most common activity by malicious extensions, followed by hijacking affiliate links and stripping security headers.
How to Detect If You're Compromised
You might have installed one of these extensions. Statistically, if you've used Chrome, Firefox, or Edge regularly and you like the convenience of browser extensions, there's a chance you grabbed one. Here's how to figure out if you're actually compromised.
Check Your Extensions List
Start by opening your browser's extensions manager. In Chrome, go to chrome://extensions. In Firefox, go to about:addons. In Edge, go to edge://extensions. Look for any of the 17 extensions in the list above. If you find one, uninstall it immediately. Don't wait. Do it now.
But here's the thing: just because you don't see them doesn't mean you're safe. The extensions might have been removed from the store already. Google, Mozilla, and Microsoft all removed them. But if you had it installed before removal, you need to manually uninstall it from your browser. The store removal doesn't auto-uninstall from existing user installations.
Check Your Password History
If you were compromised, the attackers saw everything you did online, including forms you filled out and passwords you entered. Check the password managers or browser password sync history. Look for accounts you don't recognize creating. If you see accounts created at times when you weren't using your computer, that's a red flag.
Monitor Your Email and Financial Accounts
If an extension was backdoored the whole time, attackers potentially had enough access to reset your email password or make changes to financial accounts. Check your email recovery options. Make sure the recovery phone number and backup email are yours. Check your bank account for unauthorized transactions. Check your credit card statements. Look for small fraudulent charges that you might have missed.
Run a Full System Scan
While the malicious extensions themselves don't install persistent malware directly, some users might have been vulnerable to exploitation. Run a full system scan with your antivirus software. If you don't have antivirus software, download one. Windows Defender is built into Windows and is actually pretty good. For Mac, run a Malwarebytes scan.
Check Browser History for Anomalies
Browser history might show visits to pages you don't remember visiting. The malicious extensions injected iframes, which might or might not show up in history depending on the browser and how the iframes were loaded. But you might see visits to ad networks or click fraud destinations.
Immediate Steps to Protect Yourself
Even if you don't think you installed one of these extensions, the threat is real enough that you should take precautions.
Step 1: Audit Your Extensions Right Now
Open your extensions manager. Go through every single one. Ask yourself for each extension: Do I use this? Is it from a trusted developer? When did I install it? If you haven't used it in months, uninstall it. Every extension is a potential attack surface.
Step 2: Use Your Browser's Store Only
Only install extensions from official browser repositories. Chrome Web Store. Firefox Add-ons. Microsoft Edge Add-ons. Don't install extensions from random websites. Yes, there are legitimate extensions hosted elsewhere, but it's not worth the risk.
Step 3: Check Extension Permissions
When you install an extension, it asks for permissions. Read them. An ad blocker shouldn't need permission to access your email. A screenshot tool shouldn't need permission to modify webpages. If the permissions seem excessive, don't install it.
Step 4: Keep Your Browser Updated
Browser vendors push security updates constantly. Install them as soon as they're available. Automatic updates are enabled by default in most browsers, but check to make sure.
Step 5: Change Critical Passwords
Especially for email, banking, and online shopping. Change them from a different device that you're confident is clean. Use a unique password for each account. Use a password manager so you don't have to remember them.
Step 6: Enable Two-Factor Authentication
Especially on email, banking, and shopping accounts. Two-factor authentication means that even if an attacker has your password, they can't get into your account without a second factor (your phone, a security key, or an authenticator app).
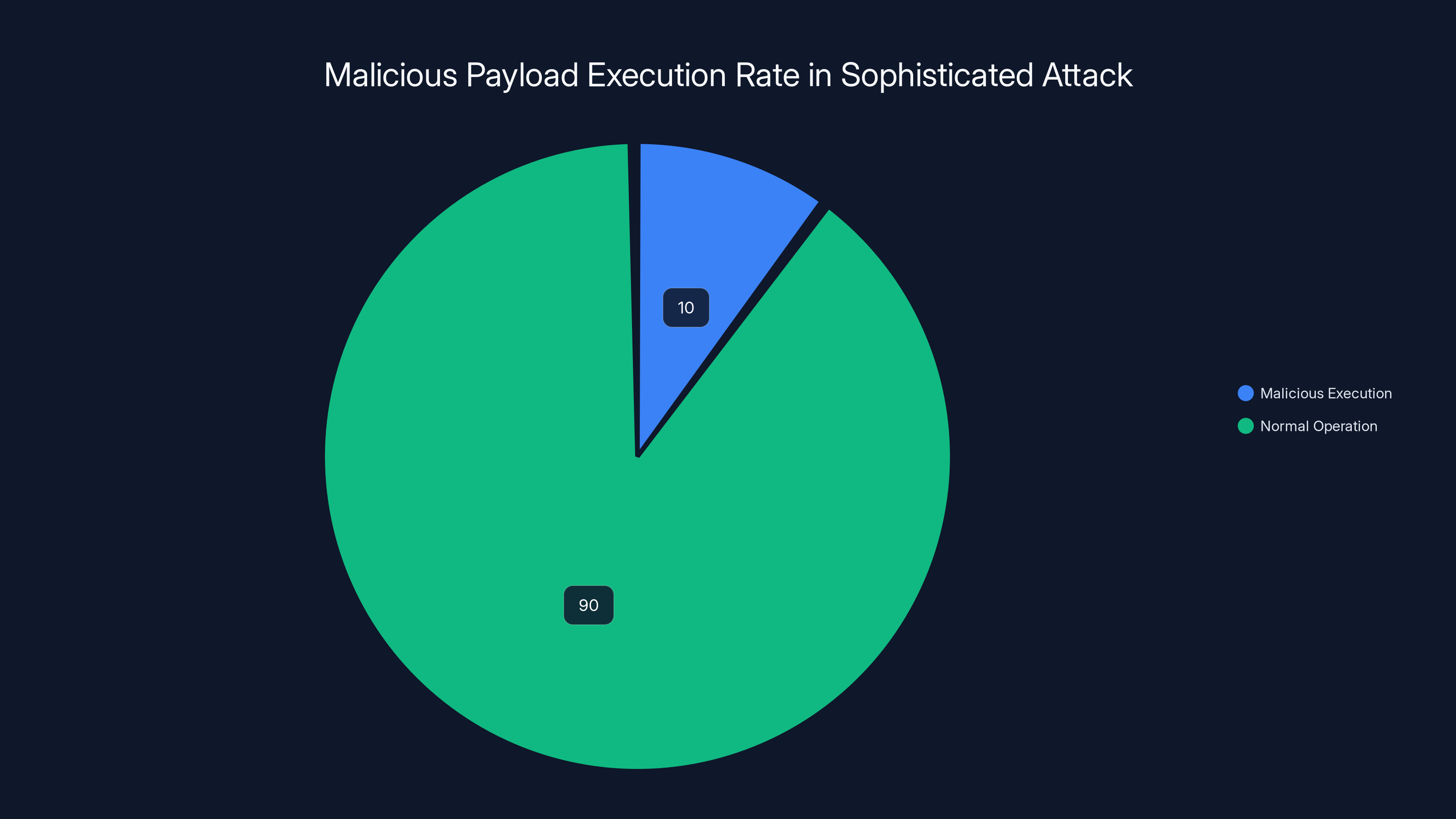
The attack's sophistication is highlighted by its 10% malicious execution rate, allowing it to operate under the guise of legitimacy 90% of the time.
The Bigger Picture: Why This Keeps Happening
Malicious extensions have been a problem for years. This isn't new. So why does it keep happening? Why don't browser vendors stop it completely?
The answer is about scale and economics.
Browser Extension Ecosystem at Scale
There are millions of extensions. Chrome Web Store alone has over 200,000 extensions. Firefox has over 20,000. Microsoft Edge has tens of thousands. Manual review of every single one is impossible. Automated detection is good but not perfect. Attackers are constantly finding new ways to bypass detection.
Meanwhile, malicious extensions are economically attractive to attackers. The affiliate hijacking alone can generate thousands of dollars per day if the extension has enough users. Ad fraud is similarly profitable. There's economic incentive to keep trying.
The Approval Process Trade-Off
Browser vendors have to balance security with developer experience. Make the approval process too strict and legitimate developers leave. Make it too lenient and malicious actors get through. Right now, the vendors are clearly on the lenient side, probably because they benefit from extension ecosystem growth and developer satisfaction.
User Apathy
Most users don't audit their extensions. Most users don't know extensions can be malicious. Most users don't think about the security implications of installing software that has access to everything they do online. That user apathy makes it easy for attackers to hide malicious extensions in plain sight.
Previous Disclosure Fatigue
There have been other major extension security issues. Millions of Chrome users installed an extension called "Web Developer" that turned out to be compromised. Millions installed "Copyfish" which was problematic. Millions installed countless other extensions with security issues. When you have that many incidents, people stop paying attention. It becomes background noise.

How Attackers Distribute Malicious Extensions
Understanding how the attack actually reaches users is important.
Direct Installation from Store
The simplest method. Users search for "screenshot tool" or "translator" and install what looks legitimate. The extension has reviews. The description looks normal. The developer profile might show previous extensions. Everything looks fine until the malicious payload activates.
Social Engineering and Marketing
Attackers might post about the extension on social media. Recommend it in forums. Create tutorial videos showing how to use it. "Download this screenshot extension, it's way better than the built-in tool." Someone sees the recommendation, installs it, and now they're compromised.
Bundling with Other Software
In some cases, legitimate software might recommend installing additional extensions. If those recommendations are compromised, the attacker reaches the user base of legitimate software. It's a channel for distribution that seems trustworthy.
Update Attacks
Once an extension is popular and installed by many users, the attacker might update it to include malicious code. Legitimate extension that got compromised. Users have auto-update enabled, so the malicious version installs automatically without their knowledge.
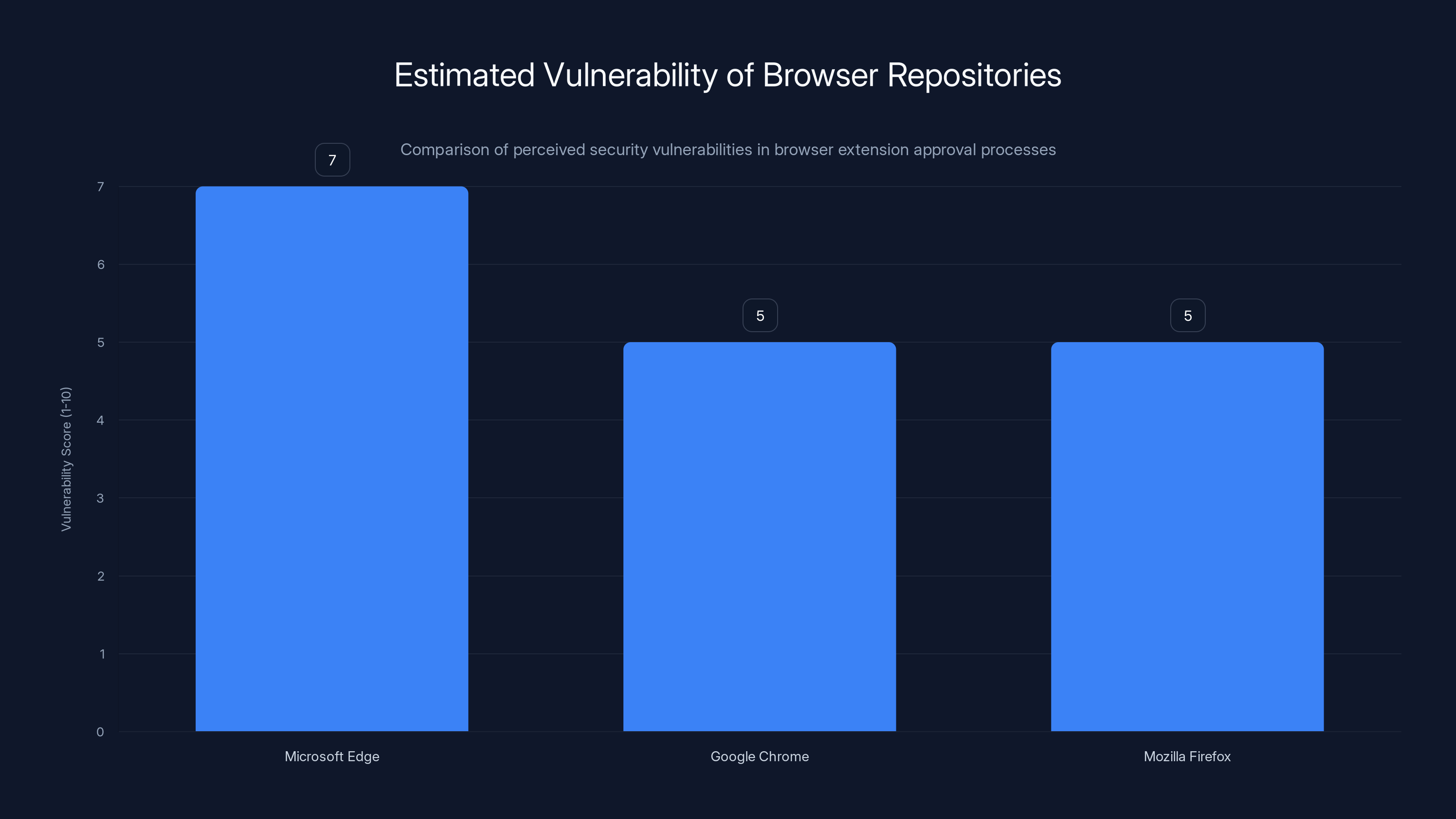
Estimated data suggests Microsoft Edge may have a higher perceived vulnerability in its extension approval process compared to Chrome and Firefox, making it an initial target for malicious extensions.
What Browser Vendors Are Doing About This
After the discovery of Operation Ghost Poster, browser vendors did take action. But the response is reactive, not proactive.
Google Chrome Response
Google removed the extensions from Chrome Web Store. Google also likely updated their detection systems to catch similar patterns. But there's no indication they're changing the fundamental approval process.
Mozilla Firefox Response
Mozilla did the same. Removed extensions from Firefox Add-ons. Updated detection. But no major changes to how extensions are reviewed or monitored.
Microsoft Edge Response
Edge removed the extensions. Made statements about enhanced monitoring. But like Google and Mozilla, the response was to remove what was found rather than prevent similar things in the future.
The Real Issue
All three vendors are reacting after the fact. They're waiting for researchers to discover malicious extensions, then removing them. This is damage control, not prevention. There's no indication of fundamental changes to how extensions are approved or monitored in real-time.

Long-Term Solutions and Best Practices
What should actually happen to prevent this? Here are some ideas that security researchers and experts have proposed.
Code Signing and Verification
Browser vendors could require that all extension code be signed by the developer and cryptographically verified before execution. This would mean that even if an extension is modified after approval, the browser would refuse to run the modified code. It's not perfect, but it would prevent compromise through updates.
Behavioral Analysis in the Store
Instead of just static code analysis, vendors could run extensions in a sandbox before approval. Actually execute them. See what they do. Make sure they're doing what the description claims and nothing else. This is computationally expensive, but it would catch many attacks.
User Consent for Sensitive Operations
Instead of giving extensions blanket permission to access everything, browsers could require user consent for sensitive operations. A popup when an extension wants to hijack affiliate links. A prompt when it wants to inject iframes. This wouldn't stop determined attackers, but it would make casual attacks harder.
Real-Time Monitoring
Browser vendors could monitor extension behavior in real-time after installation. Look for patterns consistent with the attacks described above. If an extension starts hijacking links or injecting iframes, the browser disables it and alerts the user.
Coordinated Vulnerability Reporting
There should be a system where security researchers can report malicious extensions to all browser vendors simultaneously, rather than discovering them separately. This would reduce the window of vulnerability.
Developer Review Process
Browser vendors could add additional review for extensions that request access to sensitive APIs. Not every extension needs to monitor every page you visit. If an extension is requesting extensive permissions, it should get extra scrutiny.
The Affiliate Hijacking Angle: Impact on Content Creators
One of the underreported aspects of Operation Ghost Poster is the impact on content creators.
Most creators, from bloggers to YouTubers to podcast hosts, rely on affiliate commissions. They create content, they link to products, and when someone clicks the link and buys, they get a percentage of the sale. For many creators, affiliate income is the difference between being able to afford a setup and having to quit.
When an extension hijacks those affiliate links, the creator loses the commission entirely. But here's the insidious part: the creator might not even know it's happening. They see the click tracked in their analytics. They see the person made a purchase. But the affiliate network doesn't track it as their referral because the link was intercepted.
Some creators might think their audience isn't as engaged as it seems. They might reduce content about certain products or retailers. They might blame the retailer. They might think the affiliate program is broken. Meanwhile, the attackers are actually getting the commission for sales driven by the creator's content.
This affects the creator economy at scale. YouTube creators. Twitch streamers. Blog writers. Anyone who relies on affiliate revenue got hit by this.
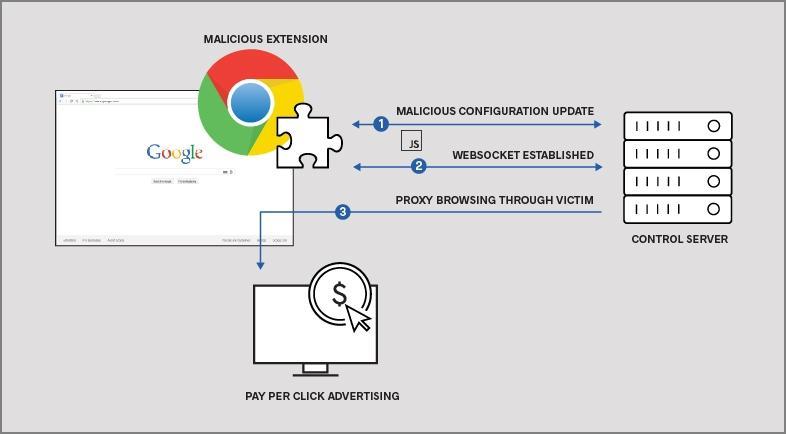
Is This Going to Happen Again
Yes. Absolutely yes.
Operation Ghost Poster happened twice already. There will be a third wave, or a different operation using similar techniques, or a variant using new techniques entirely. Here's why.
The Economic Incentive Remains
Affiliate hijacking, ad fraud, and account compromise are still profitable. Maybe less profitable than they were before this disclosure, because people are now aware. But still profitable enough for motivated attackers.
The Defense Is Reactive
Browser vendors are still reacting after discovery rather than preventing attacks proactively. Until that changes, attackers will keep finding new ways to get extensions into the store and use them maliciously.
The User Base Is Large
Millions of people use browser extensions and don't think about security. As long as the pool of potential victims is that large, attackers will keep trying.
The Approval Process Has Fundamental Limits
You cannot perfectly distinguish between a legitimate extension and a malicious one just by reviewing code and running automated checks. Some level of malicious activity will always get through.
What you can do is stay vigilant. Audit your extensions regularly. Keep your passwords unique and strong. Enable two-factor authentication. Keep your browser updated. These practices won't protect you from every attack, but they significantly reduce your risk.

Specific Vulnerable User Groups
Some users are at higher risk from this attack than others.
Content Creators and Affiliate Marketers
They're using many different retail sites. They're clicking affiliate links constantly. They're also likely to install extensions that help with content creation like screenshot tools and downloaders. That makes them prime targets.
Casual Browsers with Many Extensions
Users who install every useful-looking extension without thinking about security are obviously at higher risk. The more extensions you have, the higher the probability one of them is malicious.
Users on Corporate Networks
If you install malicious extensions on a corporate machine, you're potentially compromising the entire corporate network. Corporate security teams should absolutely be blocking known-malicious extensions and regularly auditing user installations.
Financial and Healthcare Professionals
If you work in finance or healthcare and your browser got compromised, the data exposed could be particularly sensitive. Regulations like HIPAA and others might apply. Breaches become reportable incidents.
Users in Geographic Regions Targeted by Attackers
Layer X noted that the extensions appeared in Edge's store first, suggesting geographic targeting. Users in regions where the extensions were particularly well-distributed faced higher risk.
The Detection Methods Researchers Used
How did Layer X actually discover these extensions?
Behavioral Analysis
Researchers ran the extensions in controlled environments and observed their behavior. What network requests did they make? What websites did they communicate with? What data did they exfiltrate? By comparing the behavior to the supposed function of the extension, researchers identified inconsistencies.
Code Inspection
They extracted the extension code and analyzed it line by line. They found the PNG images with hidden JavaScript. They traced the code back to see where payloads were being downloaded from.
Telemetry Correlation
Researchers looked at network traffic patterns and compared them to known ad fraud and affiliate hijacking techniques. When they saw extensions making network requests consistent with these attacks, they flagged them for deeper investigation.
Comparative Analysis
They compared the first wave of Operation Ghost Poster extensions to the second wave. Found similarities in techniques, infrastructure, and payload behavior. This connection is what established that this was a campaign by the same attacker, not a coincidence.
User Feedback
Sometimes users or website operators notice weird behavior. Extra clicks. Traffic from unexpected sources. Forms being filled automatically. When security researchers see multiple reports of similar strange behavior, it points them toward investigating specific extensions.
How to Report Suspicious Extensions
If you find an extension you think is malicious, reporting it to the proper authorities is important.
Report to the Browser Vendor
Every browser has a way to report abusive extensions. In Chrome, go to the extension's store page and click "Report abuse." In Firefox, click the flag icon on the add-on page. In Edge, there's a similar reporting mechanism. Be specific about what makes you think the extension is malicious. Share evidence if you have it.
Report to Security Researchers
If you're confident in your finding, you can report directly to security research organizations like Bleeping Computer, Security Affairs, or direct to vendors via responsible disclosure. These organizations take technical reports seriously and have channels to get information to vendors quickly.
Report to Law Enforcement
If you've suffered financial loss due to a malicious extension, you can report to your local law enforcement's cybercrime division or to the FBI's Internet Crime Complaint Center (IC3) if you're in the US. While they might not be able to help with a single incident, reports aggregate data that helps law enforcement understand threats.
Share on Security Websites
Web platforms like VirusTotal allow researchers to upload suspicious files and get community analysis. If you find malicious code, uploading it there can help security researchers understand the threat.
FAQ
What is Operation Ghost Poster?
Operation Ghost Poster is a coordinated campaign to distribute malicious browser extensions through Chrome, Firefox, and Edge official repositories. It was first discovered in December 2024 and continued with a second wave in January 2025, totaling over 17 extensions across two separate discovery incidents.
How did the malicious extensions avoid detection in browser stores?
The extensions used several evasion techniques including hiding malicious code inside PNG image files, executing payloads only 10% of the time to avoid consistent detection, and using multi-stage architecture where the actual malicious payload was downloaded after initial approval. These techniques combined allowed them to pass automated security checks.
What should I do if I installed one of the 17 malicious extensions?
First, immediately uninstall the extension from your browser. Then change your passwords on critical accounts like email, banking, and shopping sites from a different device. Run a full antivirus scan. Monitor your financial accounts and email for unauthorized access or account changes. Enable two-factor authentication on important accounts if you haven't already.
Can the extensions install persistent malware on my computer?
The extensions themselves don't directly install traditional persistent malware, but they do install backdoors for persistent access and they expose you to other exploitation vectors. The attackers can download additional payloads through the backdoor connection, potentially leading to persistent malware installation. You should assume any system that had one of these extensions installed for an extended period needs security review.
Why do browser vendors keep letting malicious extensions through?
Browser approval processes rely heavily on automation due to the sheer volume of extension submissions. Attackers have learned to build extensions that pass automated checks through code obfuscation, delayed execution, and multi-stage architectures. Additionally, browser vendors balance security with developer experience. Making approval too strict discourages legitimate extension development.
How can I prevent installing malicious extensions in the future?
Only install extensions you genuinely need from official browser stores. Check extension permissions carefully before installation. Audit your existing extensions regularly and uninstall anything you don't actively use. Keep your browser updated. Use antivirus software. Enable two-factor authentication on important accounts. These practices significantly reduce your risk even if a malicious extension slips through store reviews.
Will there be more malicious extension campaigns after Operation Ghost Poster?
Yes, almost certainly. The economic incentive for affiliate hijacking, ad fraud, and account compromise remains strong. As long as browser extensions have broad access to user activity and approval processes remain reactive rather than proactive, attackers will continue trying new campaigns. Staying aware and following security best practices is your best defense.
How do I know if my extension had malicious code running?
You likely won't know for certain without forensic analysis, but you can look for signs including unauthorized transactions on shopping sites, affiliate revenue that's lower than expected, unusual browser activity in your history, new accounts created in services you use, or alerts from your bank or email provider about suspicious activity.
Should I stop using browser extensions entirely?
Not necessarily, but you should be selective. Browser extensions provide genuine value when chosen carefully. The key is limiting the number you install, only using ones you actively need, checking permissions, and regularly auditing your installation. A few carefully chosen extensions are fine. Dozens of extensions with unknown purposes is risky.
What's the difference between the first and second waves of Operation Ghost Poster?
The first wave (December 2024) consisted of 17 different extensions with about 50,000 total downloads. The second wave (January 2025) was 17 different extensions (not the same ones) with 840,000 total downloads. Both used similar malicious techniques but different extension names and identities. This second wave shows the attacker either improved their marketing strategy or found that the technique works well enough to retry quickly.

Conclusion: Making Smart Choices About Browser Extensions
Browser extensions are useful. They save you time. They make your browsing experience better. But they're also a security risk if you're not careful.
The discovery of Operation Ghost Poster's two waves should serve as a wake-up call. Not because it means the internet is suddenly more dangerous than you thought, but because it confirms that even major browser vendors can't perfectly protect you. You have to be part of your own security.
Start today. Audit your extensions right now. Uninstall anything you don't recognize or don't actively use. Check the permissions. Be skeptical. When you need a new extension, read reviews and check the developer's other work. If something seems off, don't install it.
Change your passwords on important accounts. Use a password manager so you're not reusing passwords. Enable two-factor authentication. Keep your browser updated. These steps take maybe an hour total, and they significantly reduce your risk.
Is this foolproof? No. Perfect security doesn't exist. But it's the practical middle ground between paranoia and apathy. It's what actual security professionals do.
Your browser is the gateway to your entire online life. Protect it accordingly.

Key Takeaways
- Operation GhostPoster returned with 840,000+ downloads across 17 new malicious extensions in January 2025, following an initial 50,000-download wave in December 2024
- Malicious extensions use sophisticated techniques including hidden code in PNG files, 10% execution rates, and multi-stage payload downloads to evade detection
- These extensions hijack affiliate links costing creators revenue, inject tracking across all pages, bypass CAPTCHAs, and participate in ad fraud
- Users must manually uninstall these extensions from their browsers as store removal doesn't auto-uninstall from existing installations
- Protect yourself immediately by auditing extensions, changing critical passwords, enabling two-factor authentication, and monitoring financial accounts for unauthorized activity
Related Articles
- How to Disable Chrome's On-Device AI Scam Detection [2025]
- Massive Phishing Campaign Targets Middle East Officials, Activists, Journalists [2025]
- Fast Pair Bluetooth Vulnerability: Why 300M Devices Need Patching [2025]
- VoidLink: The Advanced Linux Malware Reshaping Cloud Security [2025]
- DDoS Attacks in 2025: How Threats Scale Faster Than Defenses [2025]
- Taiwan's 2.5M Daily Cyberattacks: China's Hybrid War Strategy [2025]
![Malicious Browser Extensions Across Chrome, Firefox, Edge [2025]](https://tryrunable.com/blog/malicious-browser-extensions-across-chrome-firefox-edge-2025/image-1-1768840727310.jpg)



