Wi-Fi Security Flaws: How Hackers Crash Your Router [2025]
Your router sits quietly in the corner of your home or office, handling thousands of data packets without complaint. You've probably never given it much thought. And that's exactly the problem.
Last year, security researchers discovered something troubling: a vulnerability so simple, yet so devastating, that an attacker could knock your entire Wi-Fi network offline with literally a single malicious packet. No password needed. No complex exploit chain. Just one frame sent over the air, and boom—your 5G network is down. Your devices lose connection. Ethernet keeps working, but wireless? Gone until you manually power-cycle the router.
This isn't theoretical. The vulnerability has been confirmed in multiple ASUS router models, and researchers believe many other devices using the same Broadcom chipsets are vulnerable too. The scary part? Most people won't even know their router is susceptible until they read an article like this.
Here's what you need to know about this critical security flaw, how attackers could exploit it, and what you can do right now to protect your network.
TL; DR
- The vulnerability exists: A high-severity flaw (8.4/10) in Broadcom chipset software allows attackers to crash 5G Wi-Fi networks with a single malicious frame.
- Confirmed devices: ASUS RT-BE86U is confirmed vulnerable, but other routers using the same chipsets likely are too.
- The impact is real: Your wireless network becomes completely unresponsive, forcing a manual router restart.
- Ethernet isn't affected: Wired connections continue working, but all 5G Wi-Fi clients lose connectivity.
- Patches exist: Broadcom has released fixes, but you need to update your router firmware manually.

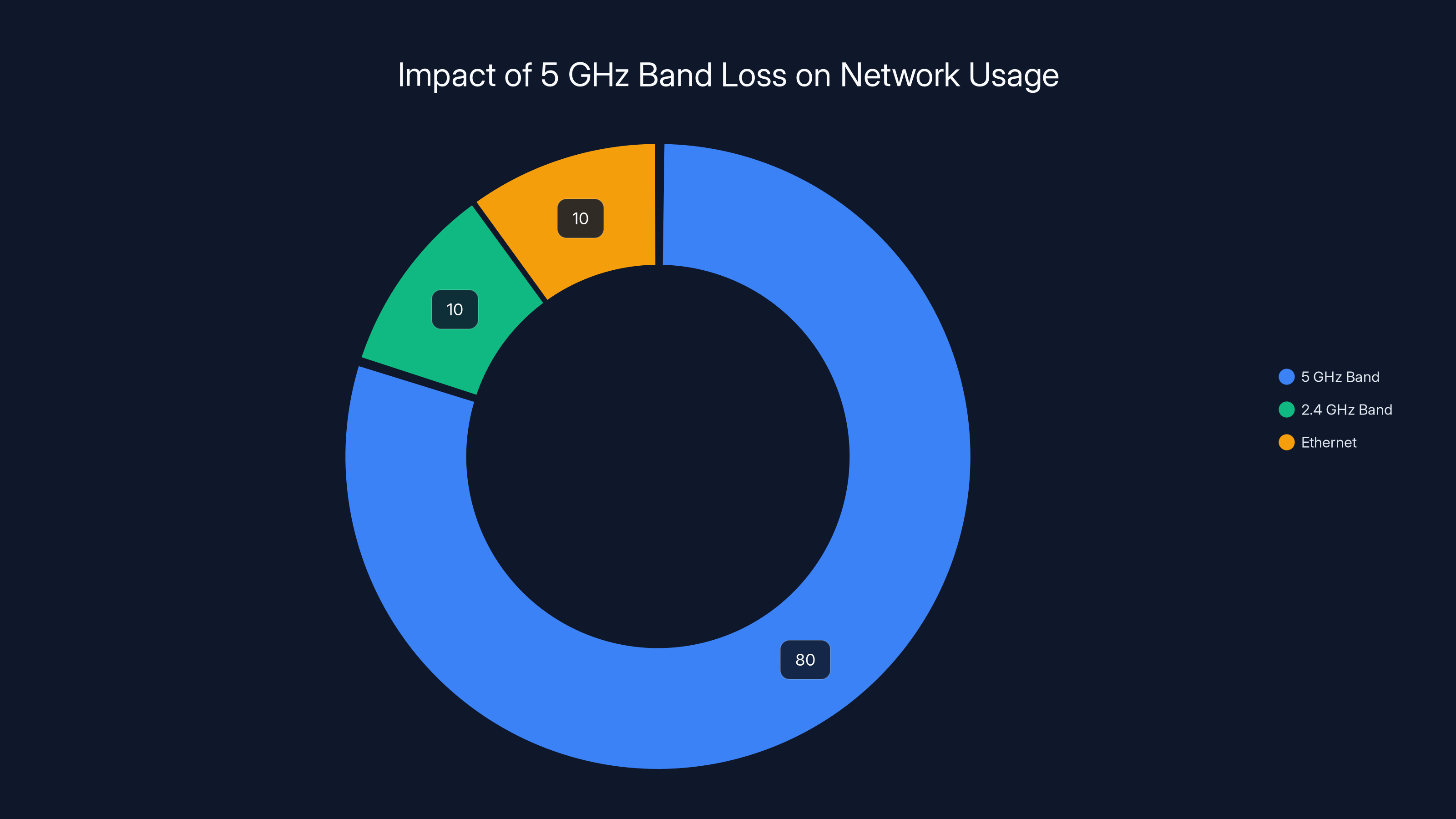
Estimated data shows that losing the 5 GHz band affects 80% of a typical modern network's wireless usage, highlighting its critical role.
What Is This Vulnerability, Actually?
The flaw discovered by researchers at the Black Duck Cybersecurity Research Center isn't a subtle backdoor or an obscure authentication bypass. It's something more fundamental: a denial of service (DoS) vulnerability in how routers handle malformed Wi-Fi protocol traffic.
Denial of service attacks come in many flavors. Some flood servers with millions of requests. Some exploit specific algorithms to consume excessive CPU resources. This one is different. It works by sending specially crafted, malformed 802.11 Wi-Fi protocol frames to the router's wireless chipset.
When the router receives these malicious frames, its software doesn't handle them gracefully. Instead of dropping them or logging a warning, the router essentially crashes. Not completely—the device stays powered on, the CPU isn't dead, the Ethernet ports keep working. But the wireless chipset becomes completely unresponsive. All clients connected to the 5G network lose their signal. They can't reconnect. They can't even detect the network exists anymore.
The only fix? Power cycle the router manually.
What makes this particularly nasty is the barrier to entry. An attacker doesn't need to be authenticated to the network. They don't need physical access. They just need to be within Wi-Fi range and have basic tools to craft and send malformed 802.11 frames. That's a skill that's readily available in the security community and increasingly easy to learn.

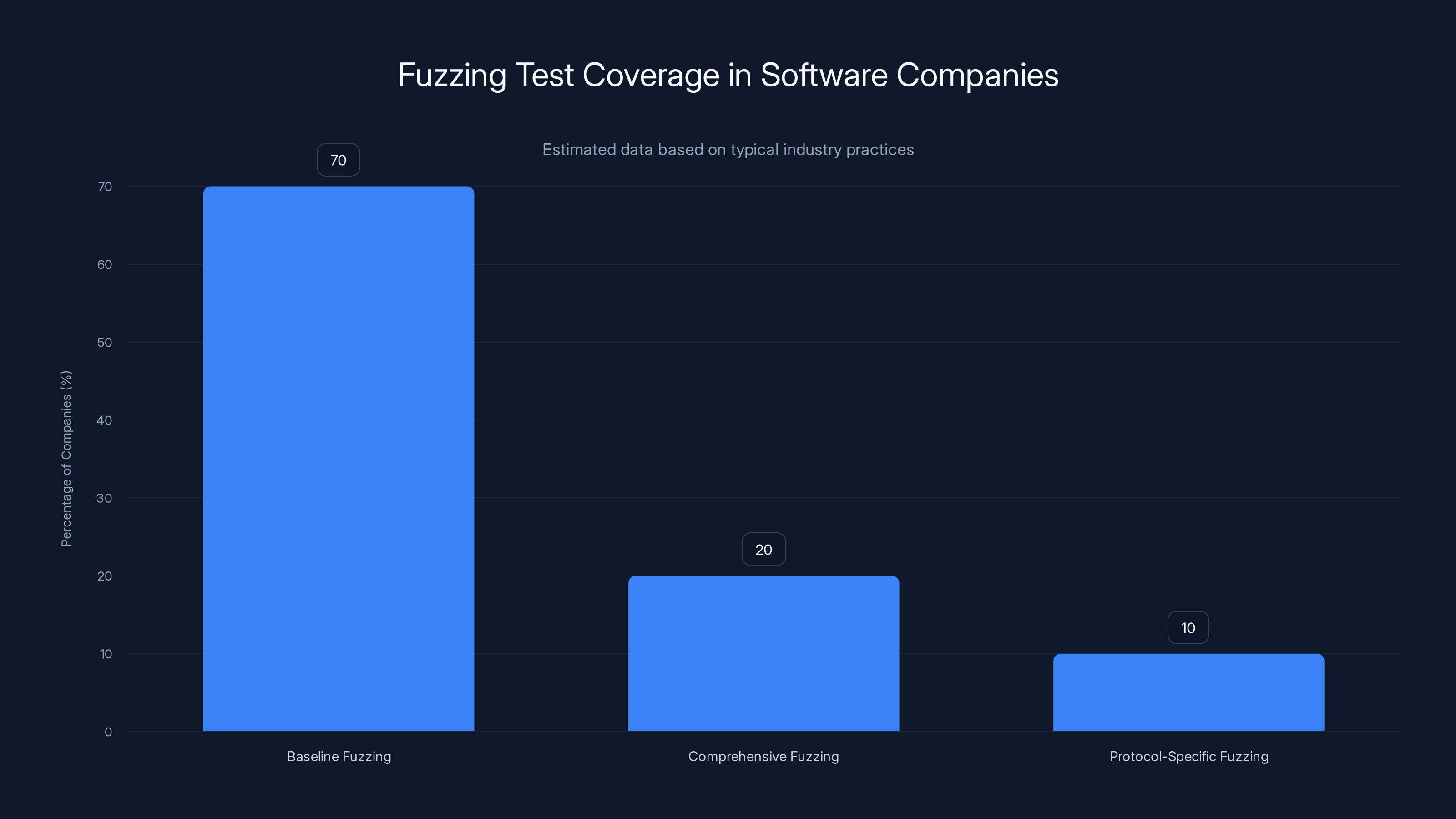
Estimated data suggests that most companies perform baseline fuzzing, while fewer invest in comprehensive or protocol-specific fuzzing, which may lead to missed vulnerabilities.
The Attack Method: How It Actually Works
To understand how this attack works, we need to talk about Defensics Fuzzing, the testing methodology that revealed the vulnerability in the first place.
Fuzzing is a security testing technique where researchers send intentionally malformed, random, or unexpected input to a system and observe how it behaves. The idea is simple: if you can crash a program with random garbage input, there's probably a bug. If that crash has security implications, you've found a vulnerability.
The Black Duck Cy RC team was testing ASUS routers using Defensics with 802.11 protocol test suites. They generated thousands of malformed Wi-Fi frames and sent them to the routers to see what happened.
Most frames were handled fine. The router ignored them or logged them as errors. But certain specific malformed frames caused the router to panic. The researchers documented exactly which test cases crashed the network and reported them to both ASUS and the chipset manufacturer, Broadcom.
Now, here's the critical part: An attacker doesn't need to send thousands of frames. They don't need to run fuzzing suites or have access to sophisticated testing tools. If a security researcher can identify the specific malformed frame that crashes the router, an attacker can replicate it with basic packet-crafting tools. Tools that are freely available online.
So in theory—and this is where it gets scary—an attacker within Wi-Fi range could send a single, specially crafted frame. The router would crash. All 5G clients lose connection. The attack takes seconds and leaves no logs (because the router's wireless chipset crashes before it can log anything).
Why Only 5G? What About 2.4 GHz?
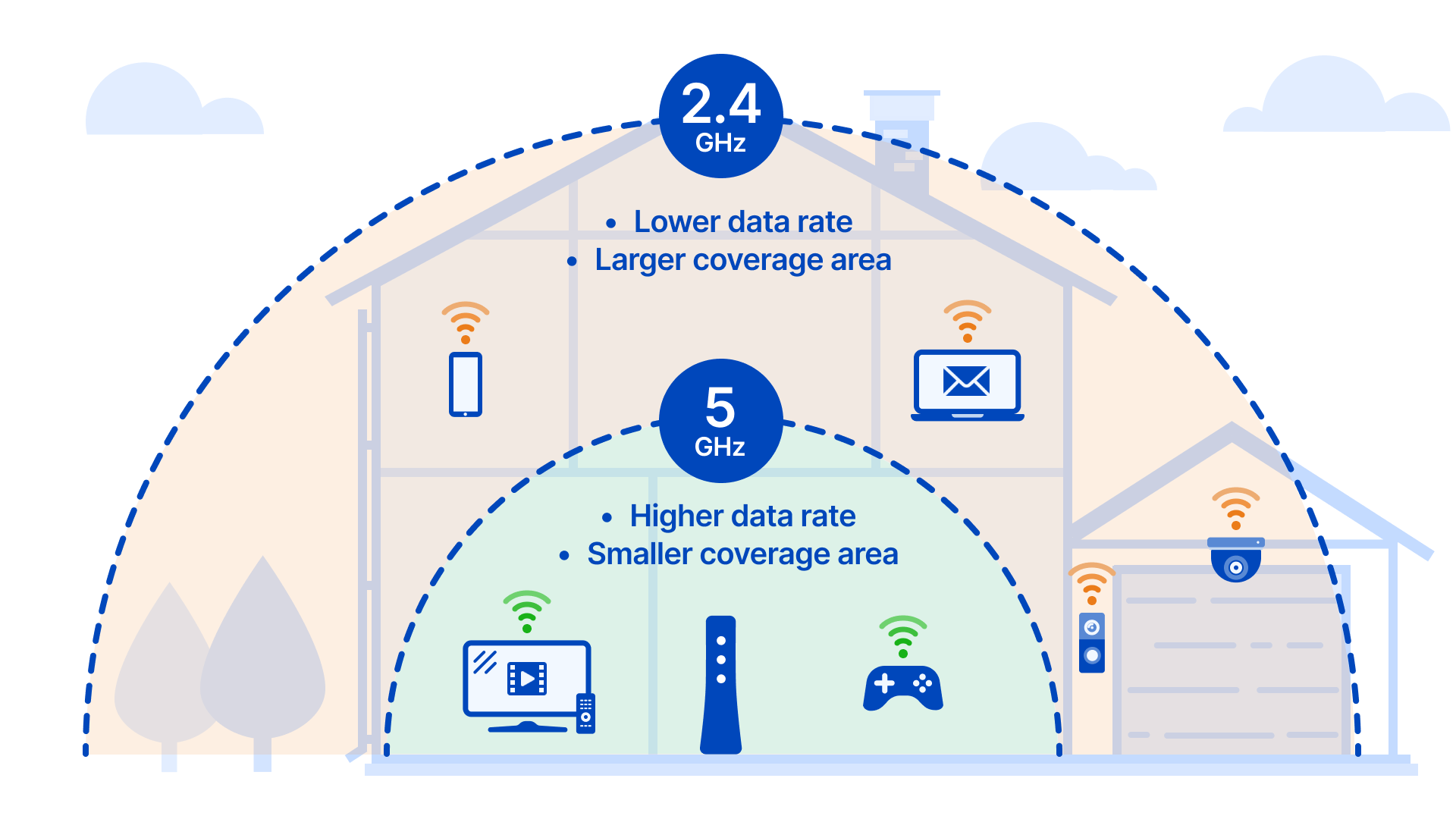
Here's something interesting: the vulnerability only affects the 5 GHz band. The 2.4 GHz band works fine. Ethernet connections are completely unaffected.
This isn't random. It suggests the vulnerability is specific to how Broadcom's 5 GHz chipset handles protocol anomalies. The 2.4 GHz chipset (which may be a different component or firmware variant) handles the same malformed frames without crashing.
For most modern networks, this distinction matters less than you'd think. Many people run dual-band routers with both bands active. A smart home with IoT devices might have cameras and sensors on 5 GHz, phones on 5 GHz, and maybe a legacy device on 2.4 GHz. Losing the 5 GHz band is like losing 80% of your wireless network.
But for critical infrastructure or business networks, the fact that Ethernet keeps working is significant. If you've hardwired your security system, VoIP phone, or monitoring equipment, those continue operating even if Wi-Fi crashes. It's a partial mitigation, but it's something.
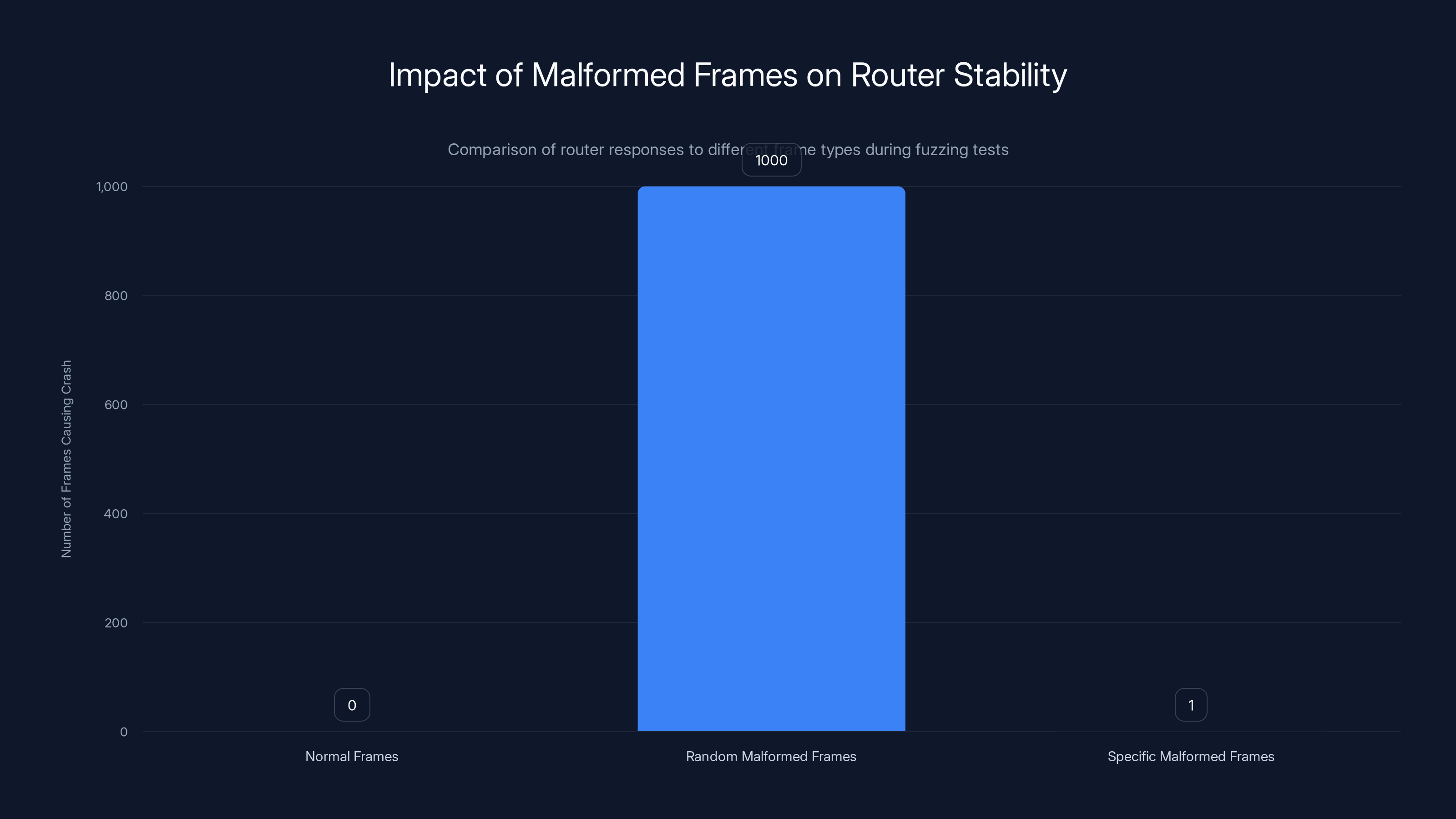
While thousands of random malformed frames were tested, only a single specific malformed frame was needed to crash the router, highlighting the precision required for successful attacks.
Which Routers Are Actually Vulnerable?
As of now, we know for certain that the ASUS RT-BE86U is vulnerable. This is a high-end Wi-Fi 7 router released in 2024, featuring Broadcom's latest chips.
But the researchers were clear: other devices using the same wireless chipsets and associated software "may be similarly affected."
The problem is that comprehensive list of vulnerable products doesn't exist publicly. Broadcom hasn't released one. ASUS hasn't released one. The researchers suggested that users contact Broadcom directly to find out if their specific model is vulnerable.
That's not helpful for most people.
What we can infer is this: any router using recent Broadcom Wi-Fi 6 or Wi-Fi 7 chipsets from a certain manufacturing window is potentially vulnerable. That's a lot of routers. ASUS, Netgear, D-Link, TP-Link, Linksys, and others use Broadcom chips. If you bought a mid-to-high-end router in the last few years, there's a decent chance it uses one of the affected chipsets.
The ASUS RT-BE86U is just the confirmed case. But researchers and security professionals are treating this as potentially affecting dozens of router models from multiple vendors.
The Real-World Impact: What Happens During an Attack?
Let's paint a realistic scenario. You're working from home, running important video calls, your security cameras are streaming on the 5G network, and your IoT devices are connected. Everything's running smoothly.
An attacker nearby sends a single malicious Wi-Fi frame.
Within milliseconds, your router's wireless chipset crashes. Here's exactly what happens next:
Your laptop loses Wi-Fi connection. The connection just dies. Your video call drops—not gradually, but immediately. The person on the other end sees you disconnect. Your security cameras go offline. Your phone, tablet, and any other wireless devices on the 5G band lose connectivity simultaneously.
You look at your router. It's still powered on. The lights are blinking normally. But Wi-Fi is completely gone. You try to reconnect. The network doesn't even appear. It's as if your Wi-Fi hardware just vanished.
So you do what we all do: you power-cycle the router. You unplug it, wait 30 seconds, plug it back in, and wait another 2-3 minutes for it to boot up and reconnect to your ISP. During that 3-5 minute window, you've got no internet on Wi-Fi at all.
When it comes back online, everything works again. You don't realize you were attacked. There's no notification, no log entry, no indication that anything malicious happened. The crash looks like a normal router glitch.
Now scale that up. Imagine this happens in an office with 50 employees. Or a coffee shop with 200 customers. Or a hospital with connected medical devices. The attacker doesn't need to steal data or access anything—they just need to create chaos and downtime.
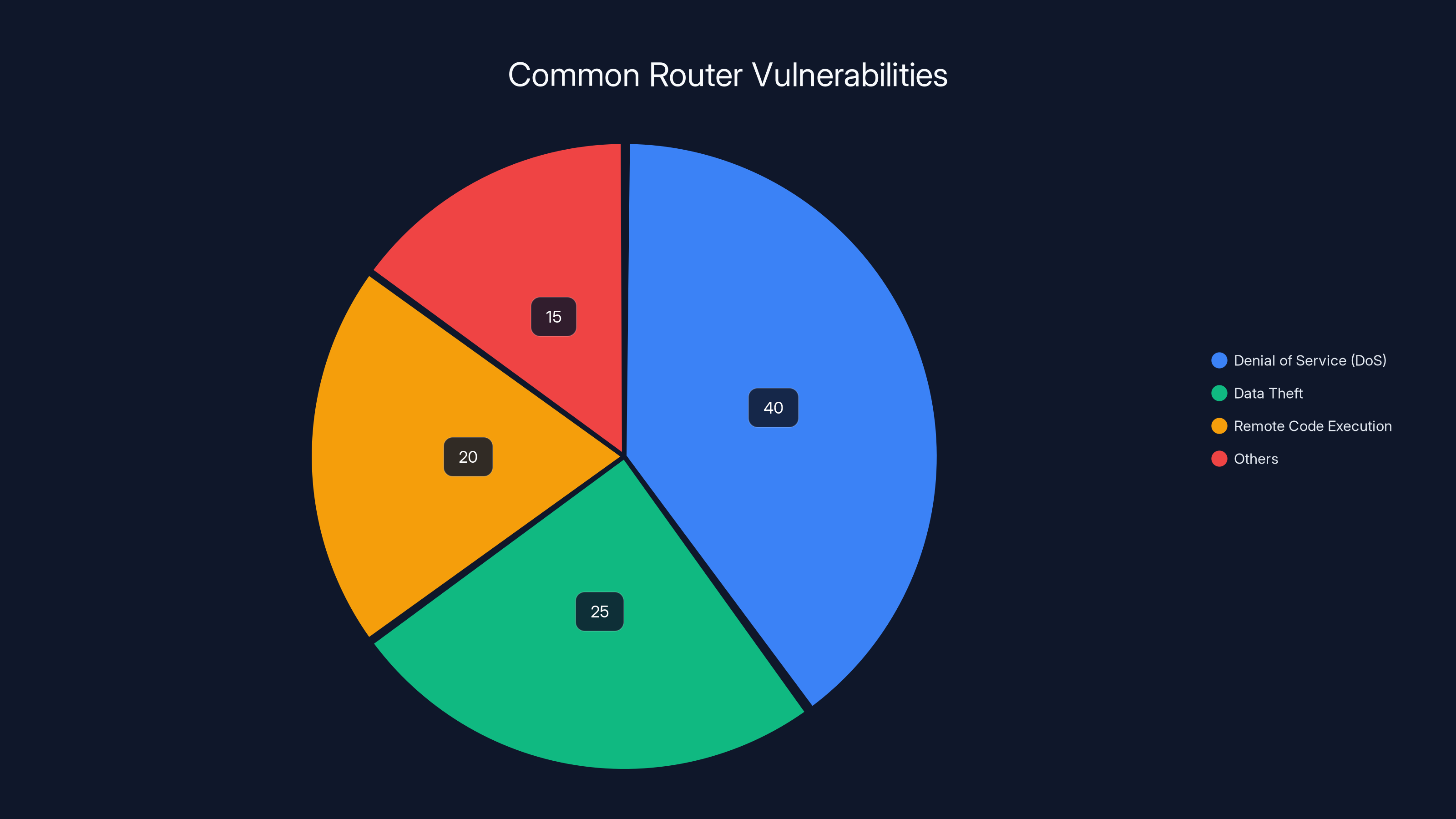
Denial of Service (DoS) attacks make up the largest portion of common router vulnerabilities, estimated at 40%. Estimated data.
Why Broadcom Didn't Catch This in Testing
This is the part that's interesting from a software engineering perspective. Broadcom is a massive company. They have extensive quality assurance, security testing, and code review processes. Yet this vulnerability made it into production code that's now running in millions of routers worldwide.
How?
The answer is that fuzzing wasn't part of their standard security testing process—or at least, not comprehensive enough. Fuzzing is computationally expensive. You're generating thousands or millions of test cases and running them against your software. For a company with tight deadlines and release schedules, that's a significant investment.
Many companies do baseline fuzzing. They'll run fuzzing tools for a certain time period, fix the obvious crashes, and call it done. They don't do comprehensive, exhaustive fuzzing against every possible malformed input.
Broadcom likely did some fuzzing, but the Black Duck Cy RC team had specialized 802.11 protocol fuzzing suites—tools specifically designed to generate malformed Wi-Fi frames. Those are more targeted and more likely to find protocol-specific bugs than generic fuzzing.
So Broadcom's testing probably didn't include comprehensive 802.11 fuzzing. Or if it did, it didn't include the specific test cases that trigger this vulnerability. That's not an excuse, it's just how software security works: testing is never 100% complete.
The Patch Situation: What's Fixed and What Isn't
Broadcom released a patch. According to the advisory, they "came back with a patch" after being notified of the vulnerability.
But here's where it gets murky: We don't have a comprehensive list of which products the patch applies to, and we don't have confirmation that all vulnerable routers have been patched yet.
For ASUS specifically, the RT-BE86U presumably has a patched firmware version available. You'd need to:
- Go to the ASUS support page for your router model
- Check the firmware version available
- Verify that it's newer than the vulnerable version
- Download and install it (this requires you to manually access your router's admin panel)
That's a manual process. There's no automatic rollout to millions of routers. There's no security notification most people will see. If you're not actively checking for firmware updates, you might still be vulnerable right now.
For other router brands using the same Broadcom chipsets, the situation is even more unclear. Some manufacturers may have released patches. Others might not have. It all depends on whether Broadcom notified them, whether they tested the patch, and whether they've pushed it out.
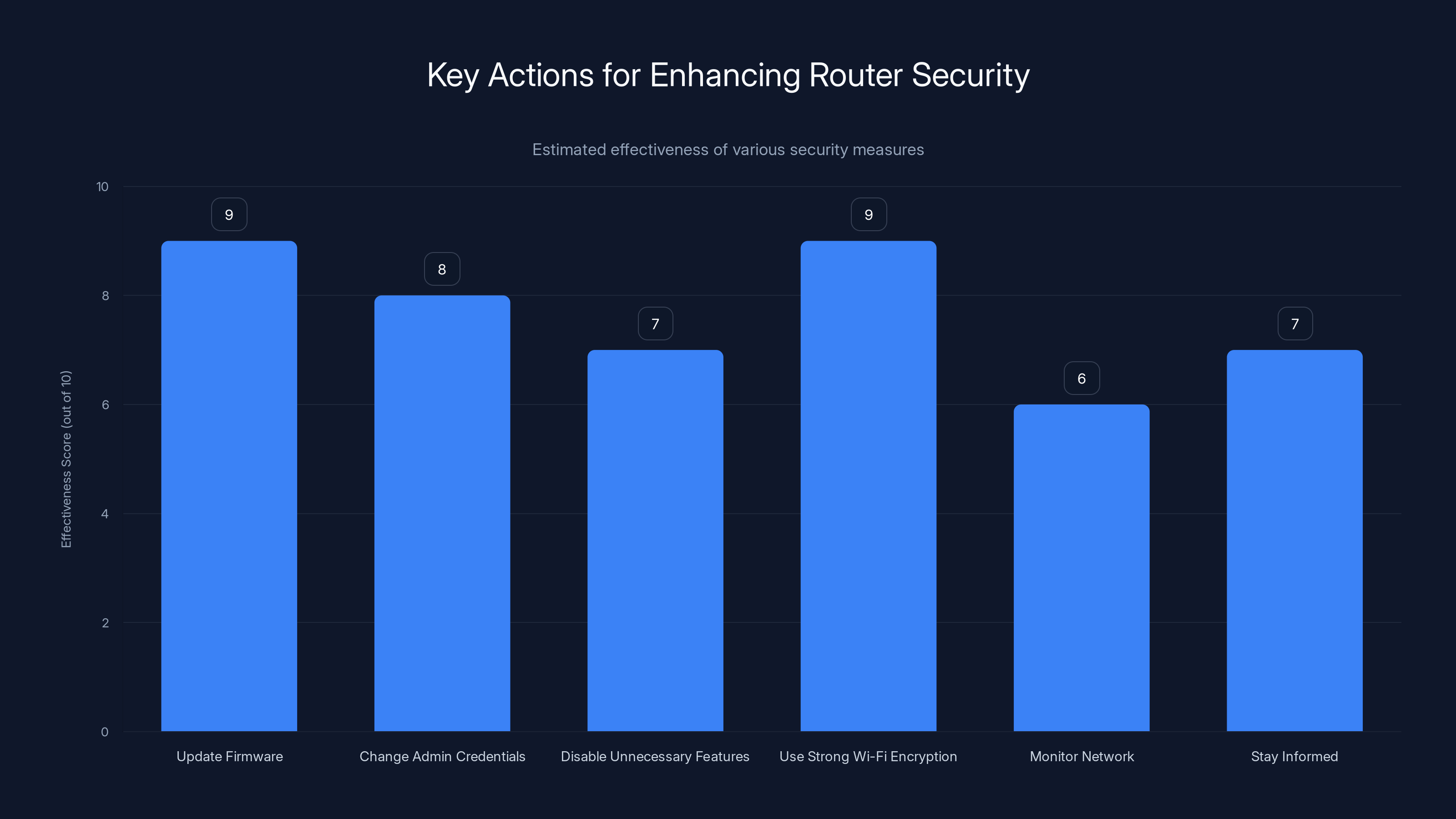
Updating firmware and using strong Wi-Fi encryption are the most effective steps to enhance router security. Estimated data.
Other Wi-Fi Vulnerabilities You Should Know About
This Broadcom vulnerability isn't an isolated incident. It's part of a broader pattern of Wi-Fi security issues discovered in recent years.
ASUS Ai Cloud Security Flaw
ASUS has been hit with multiple security vulnerabilities in recent years. The Ai Cloud flaw affected routers' ability to securely manage remote access. The vulnerability could allow attackers to compromise your router remotely if you had Ai Cloud enabled.
The lesson here: features like "remote management" and "cloud access" are convenient, but they're also security risks. Unless you absolutely need them, disable them.
D-Link Gateway Remote Code Execution
D-Link DSL gateway devices (a different product category, but still Wi-Fi infrastructure) had a critical vulnerability allowing remote code execution. An attacker could execute arbitrary commands on the device and potentially pivot to your entire network.
RCE is worse than DoS. A DoS attack crashes your network. An RCE attack gives the attacker full control.
Sonic Wall Firewall Crashes
Sonic Wall, a vendor of enterprise firewalls and network security appliances, had to patch a flaw that allowed attackers to crash their devices remotely. Again, a DoS vulnerability affecting critical network infrastructure.
The pattern is clear: network infrastructure vendors (Broadcom, ASUS, D-Link, Sonic Wall) are regularly discovering vulnerabilities in their products that affect availability or security.

Why Wi-Fi Routers Are Such Attractive Targets
Routers are like the skeleton key of your network. They sit at the boundary between your internal devices and the internet. Compromise them, and you potentially compromise everything connected to them.
Attackers care about routers for several reasons:
1. Scale: A single router patch could affect millions of devices worldwide. Broadcom makes chipsets for routers from dozens of vendors. One vulnerability multiplies across an enormous install base.
2. Trust: Most home networks don't protect against router-level attacks. Your firewall and antivirus protect the devices inside, but the router itself is often trusted implicitly. If the router is compromised, those protections are bypassed.
3. Persistence: Malware on a router can survive a reboot of your computer or phone. It persists because the router itself is running malicious code.
4. Invisibility: Most people never interact with their router after initial setup. An attacker could have malware running on your router for months without you noticing.
5. Accessibility: Routers are left on 24/7, constantly connected to the internet, often with default passwords or no authentication at all.
From an attacker's perspective, a router is the perfect target.

How to Check If Your Router Is Vulnerable
There's no simple web tool where you can plug in your router model and get a "yes, you're vulnerable" answer. But you can take steps to find out.
Step 1: Identify Your Router Model
Look at your router physically or check your network settings. The model number should be printed on the device or visible in your router's admin panel.
Step 2: Note Your Current Firmware Version
Access your router's admin panel (usually 192.168.1.1 or 192.168.0.1, check your router's manual). Log in with your admin credentials. Navigate to the Settings or System section and find the firmware version.
Step 3: Check the Manufacturer's Website
Go to your router manufacturer's support page and search for your model. Look for firmware release notes or security advisories. If there's a newer firmware version available, check the release notes to see if it addresses "802.11 DoS" or "denial of service" issues.
Step 4: Contact the Manufacturer or Broadcom
If you can't find clear information, contact the manufacturer's support team or Broadcom directly and ask if your router model is vulnerable to the recent 802.11 DoS flaw and if a patch is available.

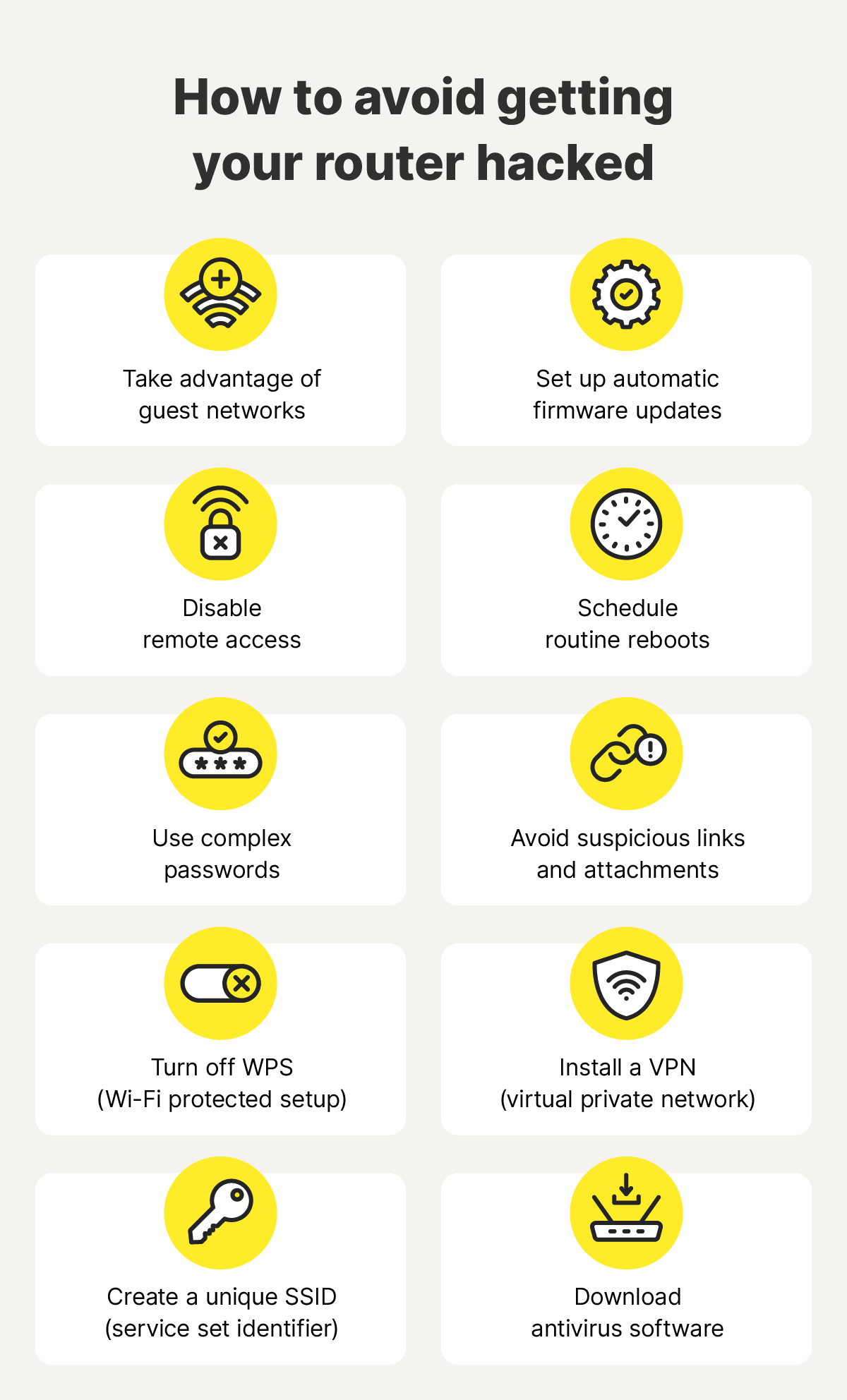
Immediate Actions: Protecting Your Network Right Now
Even if you're not sure whether your router is vulnerable, there are steps you can take right now to improve your Wi-Fi security and reduce your attack surface.
1. Update Your Firmware
If there's a firmware update available for your router, apply it immediately. Firmware updates often include security fixes for vulnerabilities that have been discovered since your router was manufactured.
How to update firmware varies by manufacturer, but generally:
- Access your router's admin panel
- Look for "System", "Administration", or "Tools"
- Find "Firmware Update" or "Software Update"
- Check for available updates
- If available, download and install
- The router will reboot automatically
2. Change Your Admin Credentials
If you're still using the default admin username and password (usually "admin" / "admin"), change it immediately. Use a strong, unique password.
Why? Because if someone gets access to your router's admin panel, they can reconfigure it, disable logging, or install malware. Default credentials make this trivial.
3. Disable Unnecessary Features
Features like:
- Remote management / cloud access
- UPnP (Universal Plug and Play)
- WPS (Wi-Fi Protected Setup)
- Guest networks (if you don't use them)
These features add complexity and potential attack surface. Unless you specifically use them, disable them.
4. Use WPA3 If Supported
If your router supports it, enable WPA3 for Wi-Fi encryption. WPA3 is the latest standard and is significantly more secure than WPA2 (the previous standard).
Not all routers support WPA3 yet (it's relatively new), but if yours does, use it. Your compatible devices will connect with stronger encryption.
5. Regularly Check Firmware for Updates
Most routers don't automatically update firmware (unlike phones or computers). You need to manually check for updates periodically.
Make it a habit: once a month, spend 5 minutes logging into your router and checking if a firmware update is available. It's the single most effective way to patch vulnerabilities.
6. Keep Network Logs (If Possible)
Some advanced routers let you enable logging of network activity. If your router supports this, enable it. It won't prevent attacks, but it can help you detect anomalies.
If your router crashes unexpectedly, you might see suspicious traffic in the logs before the crash.
Why This Matters: The Bigger Picture
This Broadcom vulnerability isn't just about losing Wi-Fi for a few minutes. It's symptomatic of a larger problem in the IoT and network infrastructure space.
Routers are complex pieces of software. They typically run a Linux kernel, manage networking stacks, handle encryption, coordinate with multiple hardware components, and stay connected 24/7/365. The attack surface is enormous.
Yet most routers aren't treated with the same rigor as enterprise infrastructure. They don't have the same security testing, patch management, or update distribution mechanisms as, say, a Microsoft Windows OS.
And users often don't care. A router that works is a router that's ignored. People don't update router firmware the way they update their phones. They don't read security advisories. They don't even think about their router until it stops working.
From an attacker's perspective, this is gold. A vulnerability that affects millions of devices, most of which will never be patched, and most users will never know they're vulnerable.
Looking Forward: What Needs to Change
To meaningfully improve Wi-Fi security, several things need to happen:
1. Automatic Security Updates
Routers should automatically download and install security patches, similar to how phones and computers do. The current model—where users manually check for updates—is broken.
2. Mandatory Security Testing
Before shipping firmware, manufacturers should be required to run comprehensive fuzzing and security testing. Not baseline testing, but exhaustive testing specifically designed to find edge cases and protocol anomalies.
3. Responsible Disclosure
When vulnerabilities are discovered, manufacturers should be given a reasonable time to patch before public disclosure. Currently, the timeline is often unclear, leading to confusion about which devices are actually affected.
4. Transparency
Manufacturers should publish clear lists of which devices are vulnerable to each CVE and which firmware versions patch it. Currently, this information is scattered across multiple vendor websites or not publicly available at all.
5. User Education
People need to understand that routers are critical infrastructure and require the same care as other security-critical devices.

FAQ
What exactly is a denial of service (DoS) attack?
A denial of service attack is when an attacker makes a service (in this case, your Wi-Fi network) unavailable to legitimate users. Instead of stealing data or gaining unauthorized access, the attacker simply crashes the system. In the case of this vulnerability, the attacker sends malformed Wi-Fi frames that crash your router's wireless chipset, making Wi-Fi completely unavailable until you manually restart the router.
Can an attacker steal my data with this vulnerability?
This specific vulnerability only causes denial of service (crashing your Wi-Fi). It doesn't allow the attacker to steal data, intercept communications, or access your devices. However, it's still serious because it can disrupt your entire network and cause significant downtime. Other router vulnerabilities (like the Sonic Wall and D-Link flaws) do allow data theft and remote code execution, which are more severe.
How do I know if my router is vulnerable?
You can check by identifying your router model, logging into its admin panel, noting your current firmware version, and then checking your manufacturer's website or contacting them to ask if your model is affected by the recent 802.11 DoS vulnerability. As of now, the ASUS RT-BE86U is confirmed vulnerable, and other routers using Broadcom chipsets may be affected, but no comprehensive list exists publicly.
If I'm on Ethernet, am I safe from this attack?
Yes and no. If you're connected to your router via Ethernet cable, your own connection won't be disrupted by this DoS attack. However, your Wi-Fi network will still crash, affecting all wireless devices on the network. Additionally, if your router crashes completely (due to a different vulnerability), even Ethernet connections might be affected.
Should I buy a new router if mine is vulnerable?
Not necessarily. The first step is to update your firmware if a patched version is available. If a patch exists and you install it, the vulnerability is fixed. Only consider buying a new router if your manufacturer hasn't released a patch and your router is old enough that they're unlikely to do so. Before buying a new one, check what router models are currently safe or consider waiting for models with better security track records.
How does this vulnerability compare to other recent router security issues?
This DoS vulnerability (8.4/10 severity) is serious but less critical than remote code execution vulnerabilities like the D-Link gateway flaw, which allows attackers full control of the device. However, DoS attacks can still cause significant business disruption and are easier for attackers to execute than RCE attacks. The Sonic Wall firewall vulnerability was also a DoS attack, showing this is a common pattern in network infrastructure vulnerabilities.
What's the difference between WPA2 and WPA3 in terms of protecting against this vulnerability?
Neither WPA2 nor WPA3 (which are Wi-Fi encryption standards) protect against this vulnerability, because the vulnerability exists at the hardware chipset level, not the encryption layer. An attacker doesn't need to be authenticated to send the malicious frame that crashes the router. However, using WPA3 is still a good security practice because it protects against other attacks, like password cracking and man-in-the-middle attacks.
Can I disable 5 GHz and just use 2.4 GHz as a workaround?
Yes, technically this would make you immune to this specific attack since only the 5 GHz band is vulnerable. However, this is a poor long-term solution because 5 GHz is faster and more efficient. Instead, you should update your firmware as soon as a patch is available, and only consider disabling 5 GHz if you're running an old router that will never receive a patch and you can't replace it.
Why didn't Broadcom's internal testing catch this bug?
Broadcom likely didn't run comprehensive 802.11-specific fuzzing (the testing methodology that found the bug) during development. Fuzzing is computationally expensive and time-consuming. Most manufacturers do some baseline fuzzing but not exhaustive protocol-specific fuzzing. The Black Duck Cy RC team used specialized 802.11 protocol fuzzing tools, which are more likely to find protocol-specific bugs than generic testing tools.
Should I be worried about my router being attacked right now?
The risk depends on whether your router is vulnerable and your threat model. If you're a regular person in a residential area, the risk is relatively low (attackers aren't randomly targeting home networks with this attack). If you're a business or in a high-security environment, the risk is higher. Regardless, updating your firmware is the appropriate response and should be done as soon as a patch is available.

Conclusion: Taking Control of Your Network Security
Your router doesn't get much respect. It sits in a corner, plugged into the wall, connecting your devices to the internet, and we rarely think about it. Until it breaks, of course. Then suddenly it's the most important device in your home.
But routers deserve security attention. They're powerful computers running complex software, connected to the internet 24/7, sitting at the boundary between your private network and the outside world. A compromised router is worse than a compromised phone because it can attack all your devices simultaneously.
The Broadcom vulnerability discovered by Black Duck Cy RC is a good reminder that these devices aren't infallible. They're made by humans, they contain bugs, and those bugs sometimes have security implications.
The good news is that you have agency here. You're not helpless. You can:
- Update your router firmware regularly (this is the most important thing you can do)
- Change your default admin credentials
- Disable unnecessary features that increase attack surface
- Use strong Wi-Fi encryption (WPA3 if supported)
- Monitor your network for unusual activity
- Stay informed about new vulnerabilities affecting your specific router model
Wi-Fi security won't be perfect—no security ever is. But these basic steps significantly reduce your risk and make you a harder target for attackers.
The next time your router seems to randomly crash or lose connectivity, you might wonder: was that a bug, a glitch, or an attack? Thanks to vulnerabilities like this one, it's harder to know for sure. But by staying on top of firmware updates and basic network security hygiene, you're giving yourself the best chance of staying protected.
Your router may not be exciting, but it's worth your attention. Give it the care it deserves.

Key Takeaways
- A critical 8.4/10 severity vulnerability in Broadcom chipsets allows attackers to crash 5G Wi-Fi networks with a single malformed frame sent over the air.
- The ASUS RT-BE86U is confirmed vulnerable, but the flaw likely affects dozens of other router models using the same Broadcom chipsets.
- The attack is a denial of service that requires manual router restart to recover, affecting all 5G wireless clients while Ethernet and 2.4 GHz bands remain functional.
- Most routers were never tested against 802.11-specific fuzzing, which is how security researchers discovered this vulnerability in the first place.
- Immediate protection requires updating router firmware, changing default credentials, disabling unnecessary features, and monitoring for security advisories monthly.
Related Articles
- DDoS Attacks in 2025: How Threats Scale Faster Than Defenses [2025]
- Malicious Browser Extensions Across Chrome, Firefox, Edge [2025]
- Massive Phishing Campaign Targets Middle East Officials, Activists, Journalists [2025]
- Fast Pair Bluetooth Vulnerability: Why 300M Devices Need Patching [2025]
- VoidLink: The Advanced Linux Malware Reshaping Cloud Security [2025]
- Taiwan's 2.5M Daily Cyberattacks: China's Hybrid War Strategy [2025]
![Wi-Fi Security Flaws: How Hackers Crash Your Router [2025]](https://tryrunable.com/blog/wi-fi-security-flaws-how-hackers-crash-your-router-2025/image-1-1768842369397.jpg)



