Pax 8 Data Breach: How a Simple Email Mistake Exposed 1,800 MSP Partners' Customer Data [2025]
It started with what should've been a routine email.
On January 13, 2026, a Pax 8 employee hit send on a message titled "Potential Business Premium Upgrade Tactic to Save Money." The email went to fewer than 40 UK-based partners. Seems normal, right? Except the attachment wasn't what it should've been. Instead of a simple pricing document, the CSV file contained sensitive information on approximately 1,800 customers, with over 56,000 data entries including organization names, Microsoft SKUs, license counts, and renewal dates.
This wasn't a sophisticated cyberattack. No zero-day exploits. No nation-state hacking group. Just a human error that turned into a significant security incident affecting thousands of managed service providers and their customers worldwide.
The incident raises uncomfortable questions about how cloud commerce platforms handle sensitive partner data, what safeguards exist to prevent these kinds of mistakes, and what comes next for affected MSPs. More importantly, it's a stark reminder that even in an era of advanced cybersecurity tools and AI-powered threat detection, sometimes the biggest vulnerabilities sit between the keyboard and the chair.
Let's break down what happened, why it matters, and what you need to know if you're an MSP, partner, or customer affected by this exposure.
TL; DR
- Data exposed: Over 56,000 entries from approximately 1,800 Pax 8 customers, including organization names, Microsoft SKUs, license counts, and renewal dates
- How it happened: A Pax 8 employee sent an email with the wrong CSV attachment to fewer than 40 UK-based partners on January 13, 2026
- Who was affected: Primarily UK-based MSP partners, with at least one Canadian organization also impacted
- The response: Pax 8 requested deletion of the email and contacted recipients; cybercriminals were reportedly seen trying to purchase the leaked list
- Current status: Data has not appeared on the dark web as of reporting; Pax 8 confirmed the incident did not impact Marketplace availability or security controls
- Bottom line: This incident underscores the critical importance of access controls, data classification, and email security protocols, even at reputable cloud platforms

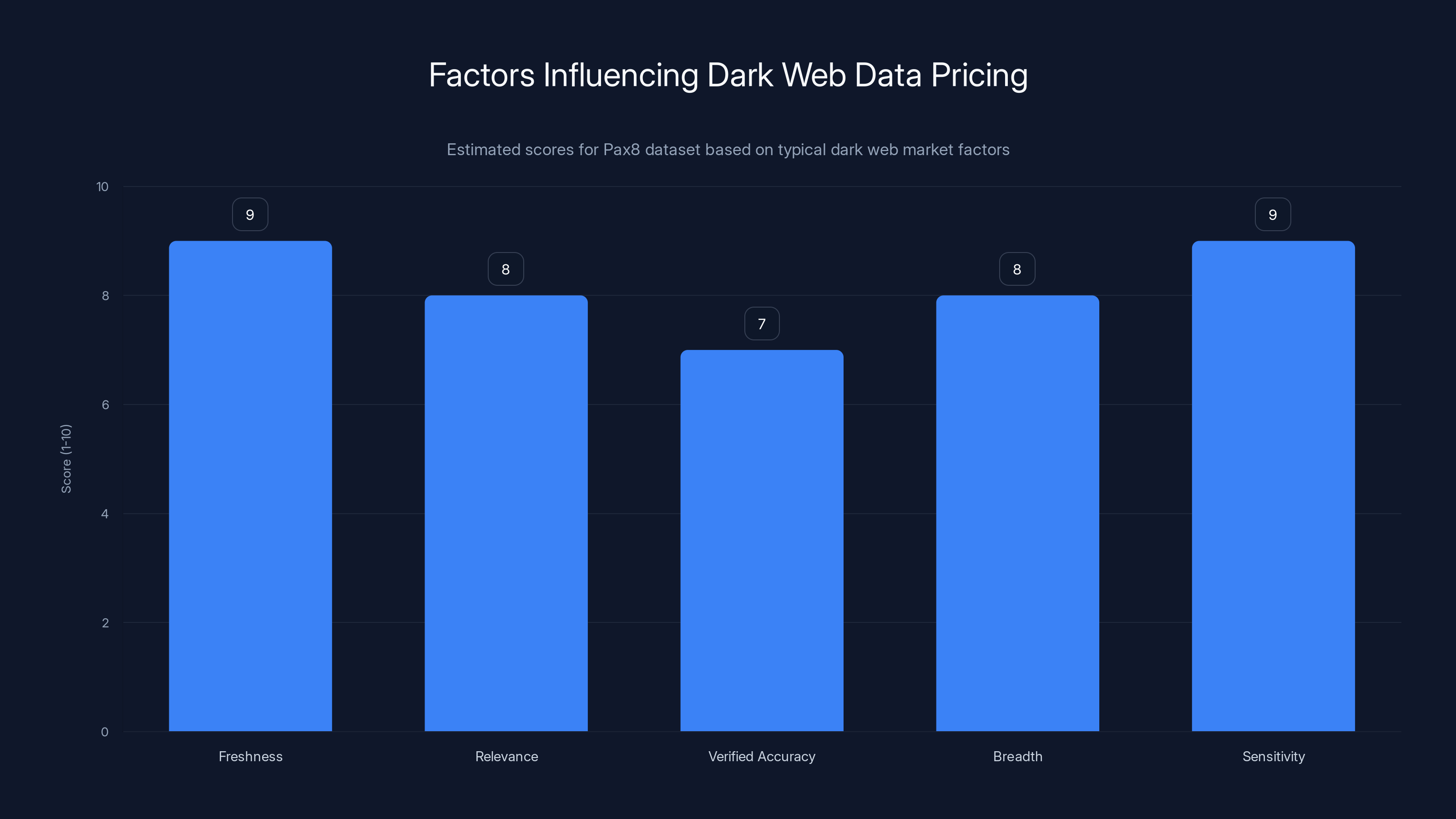
The Pax8 dataset scores high on freshness, relevance, and sensitivity, making it highly valuable on the dark web. Estimated data based on typical market factors.
What Happened: The Timeline of the Pax 8 Data Exposure
Pax 8's January 13 incident wasn't sudden or unexpected in the way cyberattacks typically are. Instead, it unfolded as a cascading series of decisions and oversights that ultimately exposed sensitive business data to unintended recipients.
The incident began when a Pax 8 employee prepared an email intended to discuss pricing optimization opportunities with UK-based partners. The message itself seemed innocuous, carrying a subject line about business premium upgrades. However, when the employee attached the supporting documentation, they grabbed the wrong file from their system.
Instead of attaching a simple pricing guide or promotional document, they included a comprehensive internal CSV spreadsheet containing customer data aggregated across the entire partner network. The file wasn't encrypted, password-protected, or otherwise restricted. It was just a CSV sitting in an inbox, ready to be forwarded, shared, or downloaded by anyone who received the email.
The email went to fewer than 40 recipients, all UK-based Pax 8 partners. But in the world of cybersecurity, "fewer than 40" is enough. Once data leaves your organization's control, you've lost the ability to guarantee what happens to it next.
Pax 8 didn't immediately discover the mistake. Instead, the company learned about it only after being contacted by external parties who'd received the email. This is telling. It suggests there wasn't automated monitoring of emails containing sensitive data patterns or real-time alerts when large customer datasets were being shared externally.
Once aware of the situation, Pax 8 moved relatively quickly. The company sent follow-up communications requesting that recipients delete the emails and not distribute them further. All standard incident response procedure, but by then, the data was already in circulation.
Moreover, reports emerged that cybercriminals were actively reaching out to recipients, attempting to purchase the leaked data. This is a common pattern in data breaches. Criminal marketplaces operate quickly, and sellers approach those known to have access to valuable information within hours of exposure.
At the time of reporting, the data had not surfaced on the dark web or criminal forums. However, the absence of public availability doesn't mean the information is secure. It may have been purchased privately, shared among threat actors in closed channels, or stored for future exploitation.
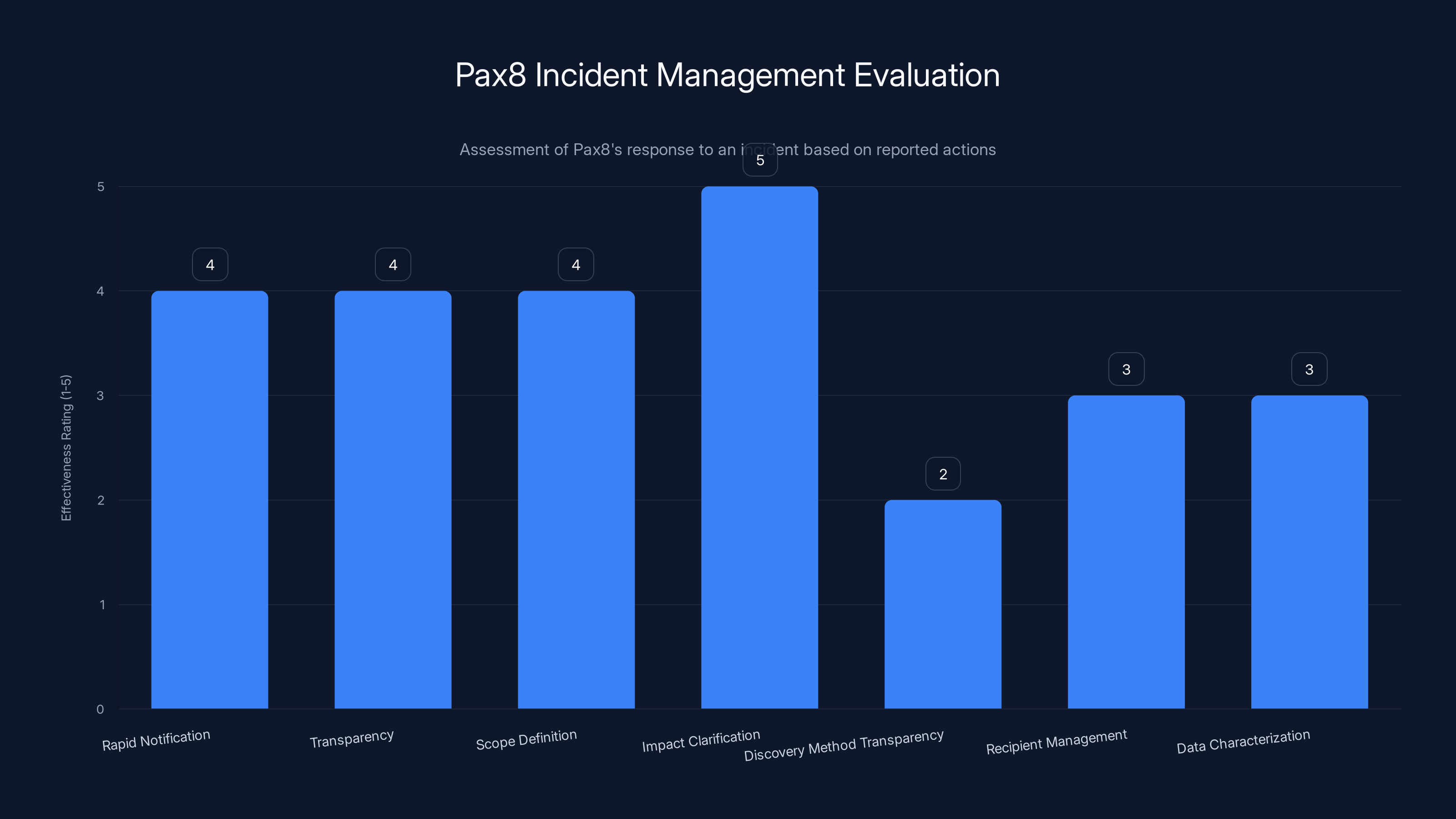
Pax8's incident management shows strong transparency and impact clarification, but lacks in discovery method transparency and recipient management. Estimated data based on narrative.
Understanding Pax 8 and Its Role in the MSP Ecosystem
To understand why this breach matters, you need context on what Pax 8 does and how critical it is to the managed service provider infrastructure.
Pax 8 isn't a household name, but it's absolutely essential to the MSP industry. The company operates as a cloud commerce marketplace, essentially serving as a middleman between software vendors (like Microsoft) and managed service providers who resell cloud services and software licenses to their customers.
Think of it like this: A customer wants Microsoft 365 licenses. They don't buy directly from Microsoft. Instead, they work with an MSP, who procures those licenses through a marketplace like Pax 8. Pax 8 handles the fulfillment, licensing, provisioning, and often provides consolidated billing and support.
This model has exploded over the past decade. Cloud services have become the dominant way companies consume software. Traditional perpetual licensing models have given way to subscription-based cloud offerings. MSPs have evolved from being purely on-premises infrastructure experts to being cloud service brokers and resellers.
Pax 8's position in this ecosystem is powerful. The company sits at an intersection where it has visibility into:
- Which organizations are buying what software and services
- How many licenses each organization has purchased
- When those licenses are up for renewal
- Pricing negotiations and margins across the entire partner network
- Customer details and account information for tens of thousands of organizations
In essence, Pax 8 is a repository of extremely valuable business intelligence. For cybercriminals, a dataset from Pax 8 is like striking gold. The information can be used to:
- Identify high-value targets for ransomware campaigns
- Understand which organizations are underutilizing cloud services (potential upsell opportunities for competitors)
- Track licensing compliance issues (useful for license audits and compliance threats)
- Build customer profiles for social engineering or phishing attacks
- Inform competitive intelligence and pricing strategies
Given this, the exposure of 56,000 entries from 1,800 customers isn't just a data privacy issue. It's a strategic exposure that affects the entire MSP supply chain.
The Data That Was Exposed: What's in the Spreadsheet?
The CSV file that leaked contained specific, actionable business information. Let's break down exactly what was exposed and why each data point matters.
Organizational Identifiers
The spreadsheet included partner names and IDs, along with customer names and IDs. This seems straightforward, but it's critical. These identifiers allow threat actors to build comprehensive maps of the MSP ecosystem, understanding which partners work with which customers.
When combined with other data sources, these identifiers can be cross-referenced to build detailed organizational profiles. A threat actor might match a customer ID to public information about that organization, learning everything from its industry and size to its revenue and recent announcements.
Product and License Information
The exposed data included Microsoft SKUs (Stock Keeping Units), which are specific product codes identifying exactly what software products each customer had purchased. This goes beyond just knowing "a company uses Microsoft products." SKUs reveal specific details like whether an organization uses Microsoft 365 Business Standard vs. Enterprise, or which add-ons and premium features they've licensed.
License counts revealed how many seats each organization had purchased. This is particularly valuable to threat actors because it indicates organization size and whether that organization's IT footprint is being properly leveraged and secured.
Renewal Dates and Financial Information
Perhaps most sensitive were the New Commerce Experience (NCE) renewal dates. These dates indicate when each customer's licenses expire and when they'll be making renewal purchasing decisions. For threat actors, this information is gold. It allows them to time attacks strategically.
Imagine being a ransomware gang. You know an organization is about to renew its Microsoft licenses. You encrypt their systems shortly before renewal. Now they're forced to negotiate with you while simultaneously managing license renewal with their MSP. The organization is vulnerable and distracted.
The spreadsheet also included gross and net bookings, which indicate revenue and profitability information. This reveals how much money MSPs are making from customers, which customers are most valuable, and where profitability gaps exist.
Account and Territory Information
The data included account owner information (the specific salesperson or account manager at Pax 8 responsible for each partner relationship) and territory information indicating geographic markets and regions.
This information is useful for social engineering. A threat actor can now identify the specific Pax 8 employee responsible for an MSP account and potentially impersonate them to establish false relationships or extract additional information.

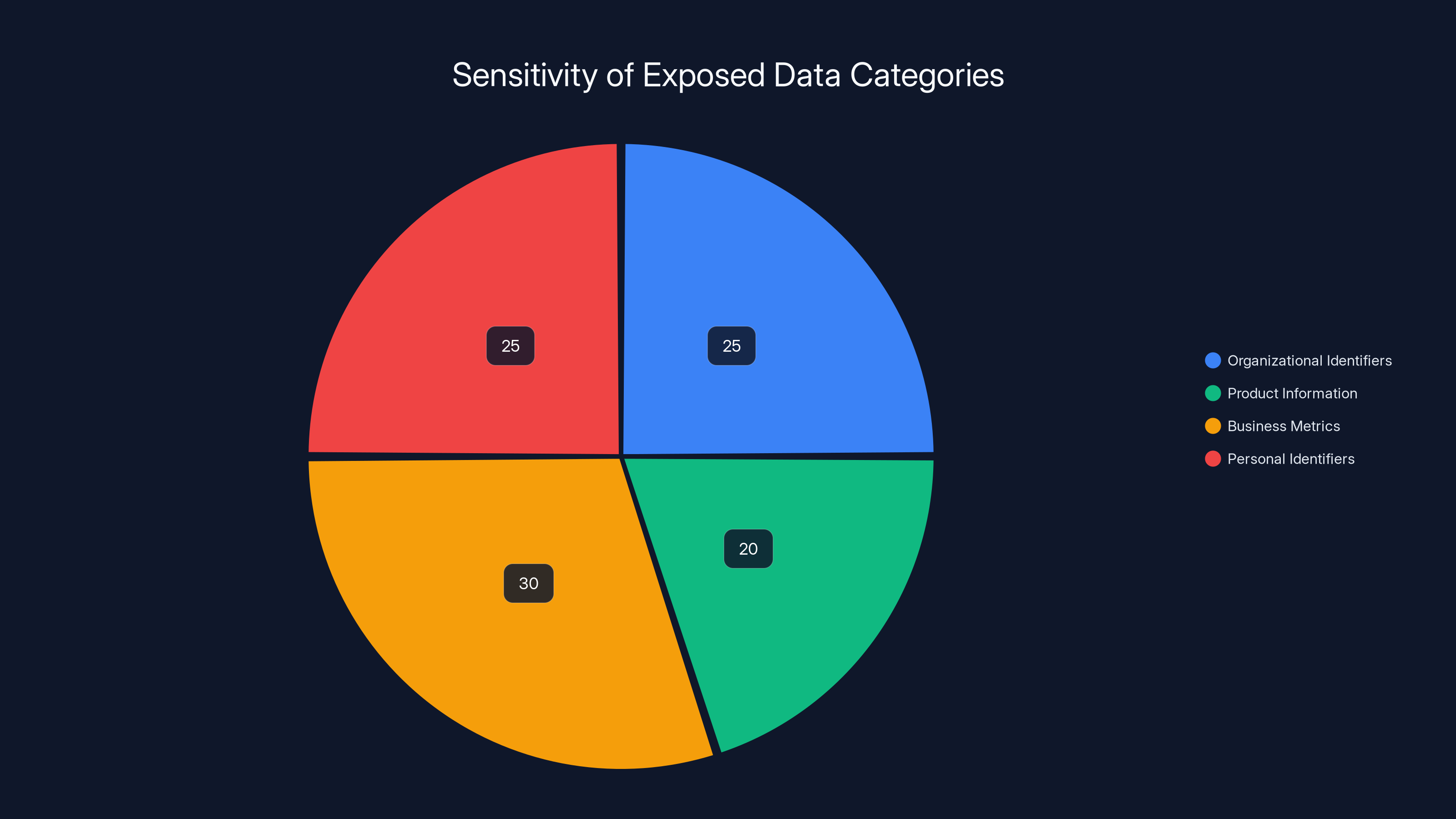
Business metrics are the most sensitive due to their impact on competitive advantage and potential regulatory scrutiny. Estimated data.
Why This Matters: The Ripple Effect Across the MSP Industry
On the surface, this looks like a simple data exposure. One file, fewer than 40 recipients. But the reality is more complex. The impact extends far beyond the initial exposure.
For MSP Partners
MSPs now know their customer data, pricing strategies, and renewal information are potentially in the hands of competitors and cybercriminals. This creates immediate business risks.
Competitors could use the information to target MSPs' most valuable customers with undercutting offers. Cybercriminals can use the information to conduct targeted attacks. More insidiously, MSPs must now assume that threat actors have visibility into their customer base and can strategically plan attacks that cause maximum business disruption.
For End Customers
End customers are affected even though they never directly received the leaked email. Their organizations' names, software purchases, renewal dates, and licensing volumes are now potentially known to threat actors. This increases their risk profile significantly.
Organizations with valuable licenses or mission-critical software now know they're on threat actors' radar. Ransomware groups, in particular, use this kind of data to identify high-value targets. If your organization's IT infrastructure is completely built on Microsoft services, and threat actors know this, you become a target.
For Pax 8 and the Platform
Pax 8 has a credibility problem now. Partners are questioning how a file like this could be so easily accessible and shareable. Where were the access controls? Why wasn't the data encrypted? Why didn't automated systems flag an internal employee sending a 56,000-row customer database to external partners?
These questions are legitimate, and they reflect real governance gaps.

Root Cause Analysis: How Did This Happen?
Let's dig deeper into why this incident occurred and what systemic failures allowed it to happen.
Insufficient Access Controls
The fundamental issue is that a Pax 8 employee had access to a spreadsheet containing aggregated customer data for 1,800 organizations and 56,000 entries. This is a lot of data for an individual contributor to have in their local system.
Best practice data governance would segregate access significantly. Not every employee needs access to the complete customer database. Access should be restricted based on job function. A person preparing a marketing email about pricing optimization shouldn't have access to a spreadsheet containing license counts and renewal dates for thousands of customers.
The fact that this data was so readily accessible suggests inadequate role-based access control (RBAC) systems.
File Selection and Attachment Mechanisms
The employee sent the wrong file. This points to inadequate safeguards in the email attachment process itself. Modern email security systems can implement policies that:
- Require confirmation before sending emails to external recipients
- Scan attachments for sensitive data patterns
- Flag emails containing large CSV files with customer information
- Require approval from a manager before sending files containing sensitive data patterns
If Pax 8 had implemented these controls, the employee would've been prompted to confirm they intended to send a file with 56,000 rows of customer data to external partners.
Lack of Data Classification
For this to happen, the file either wasn't classified as sensitive, or the classification system didn't prevent its transmission. Data classification typically follows these tiers:
- Public: Can be shared freely
- Internal: Can be shared with employees but not external parties
- Confidential: Restricted to specific employees with legitimate business need
- Restricted/Secret: Extreme restrictions on access and transmission
A spreadsheet containing customer names, license counts, and renewal dates should be classified as Confidential at minimum, if not Restricted. Once classified, Data Loss Prevention (DLP) systems should prevent it from being transmitted to external recipients via email.
No Compensating Controls
Even if access controls were loose, compensating controls could've caught this. Audit logs of file access should've alerted security teams when a large customer database was being prepared for transmission. Outbound email monitoring should've flagged a 56,000-row CSV being sent externally.
The absence of these alerts suggests either insufficient monitoring infrastructure or insufficient security team resources to act on alerts.
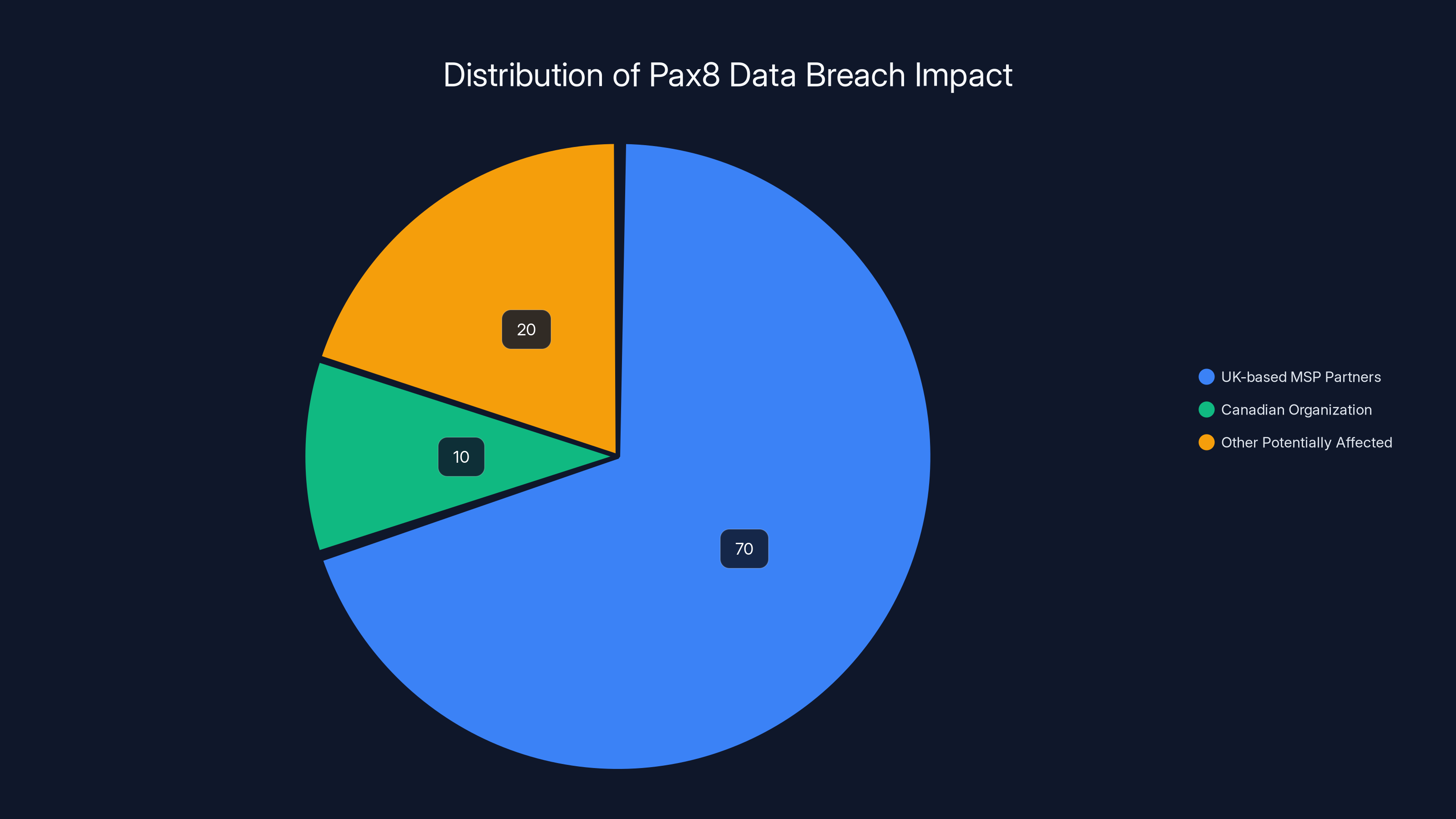
Estimated data shows that UK-based MSP partners were most affected by the Pax8 data breach, with a smaller impact on a Canadian organization and other potentially affected parties.
The Threat Actor Angle: Why Cybercriminals Are Interested
Reports indicate that cybercriminals immediately began reaching out to recipients, attempting to purchase the leaked data. This response is telling and reveals how threat actors operate in practice.
The Dark Web Data Market
A thriving market exists for stolen datasets. Threat actors buy and sell information on dark web marketplaces, forum sections, and encrypted chat channels. The value of a dataset depends on several factors:
- Freshness: How recent is the data?
- Relevance: How useful is it for attacks?
- Verified accuracy: Has someone confirmed the data is legitimate?
- Breadth: How many records does it contain?
- Sensitivity: How valuable is each record?
The Pax 8 dataset scores well on most of these dimensions. It's current, it's extremely relevant for targeting MSPs and their customers, and it contains 56,000 records with actionable intelligence.
Typical pricing for such a dataset might range from
Intended Uses
Threat actors interested in purchasing this data likely have specific uses in mind:
Ransomware targeting: Organizations that use extensive Microsoft cloud services are often well-connected to internet infrastructure. They may lack on-premises infrastructure that can be more easily isolated and protected. The data reveals which organizations are most vulnerable to cloud-centric attacks.
Competitive intelligence: Business competitors could use the data to understand which organizations are investing heavily in cloud transformation and which may be vulnerable to switching.
Supply chain attacks: Threat actors could target MSPs with access to thousands of customer environments. If they can compromise an MSP, they gain access to all downstream customers.
Compliance and audit threats: Organizations with specific licensing patterns might be targeted with fake license audit notices, leading to extortion or malware installation.
Why It Hasn't Leaked Yet
At the time of reporting, the data hadn't appeared on public dark web forums or criminal marketplaces. This doesn't mean it's secure. Several scenarios could explain the absence:
- Someone purchased the data privately and is keeping it exclusive
- The data is being hoarded for future exploitation at a critical moment
- Criminal groups are still verifying the data's accuracy and usefulness
- The breach hasn't been fully monetized yet because Pax 8's incident response may have disrupted the sale
Historically, sensitive datasets like this eventually surface. Organizations should assume the data is compromised and plan defenses accordingly.

Pax 8's Response and Incident Management
How Pax 8 responded to the incident reveals both strengths and weaknesses in their incident management processes.
Positive Response Elements
Pax 8 did several things right:
Rapid notification: The company moved quickly to identify affected parties and request deletion of the compromised email. This speed limits the window during which threat actors can distribute or monetize the data.
Transparency with affected parties: Pax 8 sent a follow-up email confirming the incident and explaining what happened. Transparency in breach communication helps maintain trust, even when the news is bad.
Clear scope definition: The company was specific about what was exposed (limited internal business information) and what wasn't (no personally identifiable information, though this is debatable given organization names are included).
Clarification on impact: Pax 8 explicitly stated that the incident didn't impact Marketplace availability or core security controls. This reassures customers that the breach was isolated and not indicative of broader system compromises.
Questionable Aspects
Several aspects of Pax 8's response raise questions:
How was the breach discovered?: Pax 8 doesn't explain how it learned about the breach. Did a partner report it? Did an employee notice? Did a security firm contact them? Transparency on discovery methods builds confidence in breach detection capabilities.
Why were there so many recipients?: While fewer than 40 recipients is relatively small, why were 40 people on an email discussing pricing optimization? This suggests broadcast practices that increase risk.
Characterization of exposed data: Pax 8 said the attachment "did not contain personally identifiable information," but included organization names, partner names, and account owner information. This is debatable. Many privacy laws would consider organization names and account information as sensitive personal data.
No mention of credit monitoring or support: Typical breach notifications offer affected parties credit monitoring or identity theft protection. Pax 8's notification doesn't mention these services.

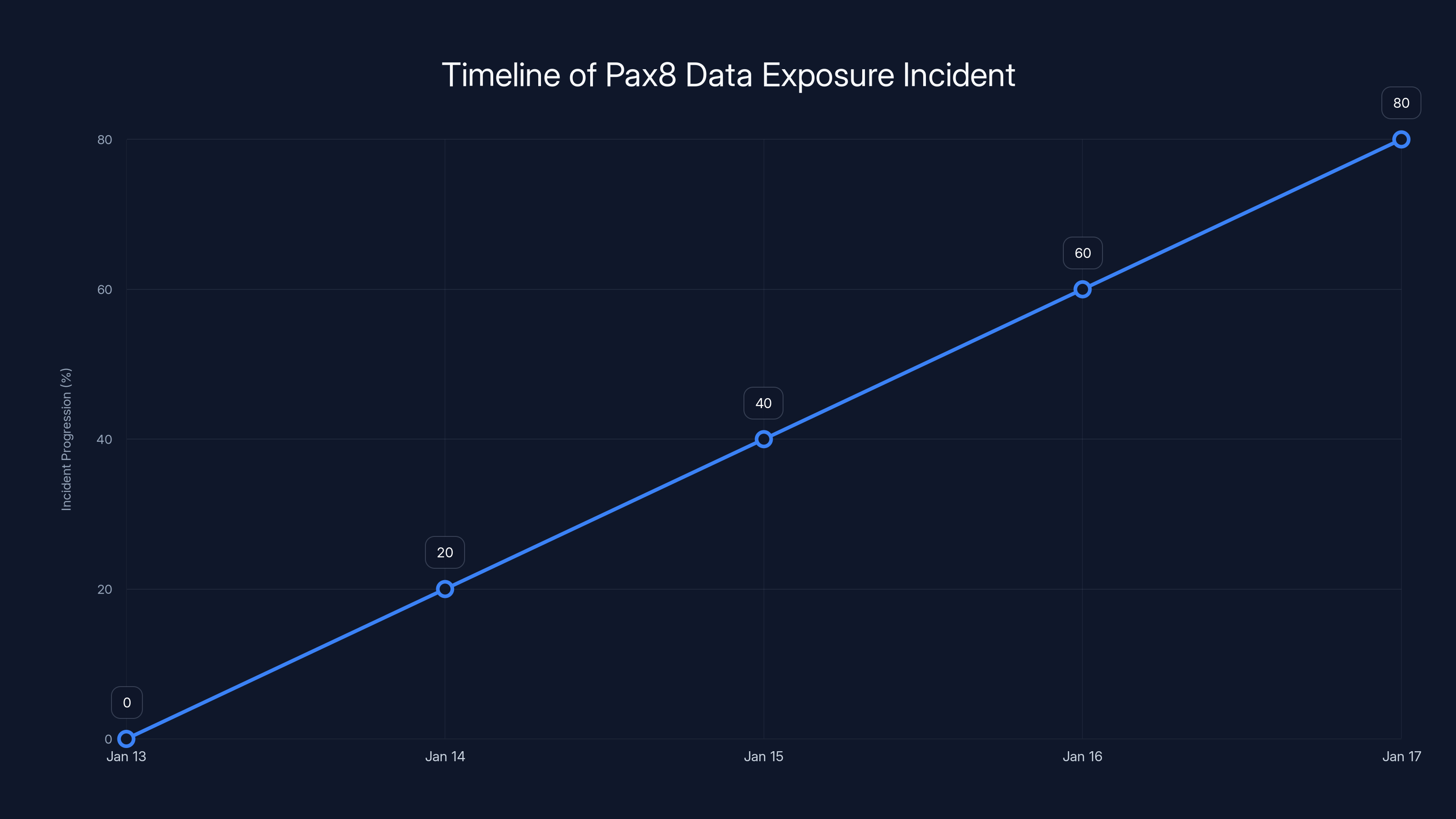
The timeline illustrates the progression of the Pax8 data exposure incident, highlighting the delay in detection and response. Estimated data.
Data Classification and Sensitivity Assessment
Let's objectively assess how sensitive the exposed data actually is, despite Pax 8's characterization.
What Makes This Data Sensitive?
The exposed information includes:
- Organizational identifiers: Names and IDs of 1,800 organizations
- Product information: Specific Microsoft services and features each organization uses
- Business metrics: License counts, renewal dates, and financial information
- Personal identifiers: Account owner names (Pax 8 employees responsible for specific partners)
Under many privacy frameworks, this information is clearly sensitive:
- GDPR: Account owner names and organization contact information could be considered personal data under GDPR, even if not in traditional personal data format
- CCPA: Organization names and purchase history could fall under consumer data protections in California
- HIPAA: If any exposed organizations were healthcare providers, information about their licensing could be regulated
- SEC regulations: For public companies, material business information about software spending could affect stock valuations
Business Sensitivity
Beyond legal classifications, the information is highly sensitive from a business perspective:
MSPs consider their customer lists confidential. The relationships they maintain with customers, the services they provide, and the value they derive are proprietary information. Exposing this allows competitors to target customers and threat actors to identify valuable targets.
License and renewal information is particularly sensitive because it reveals:
- Which customers are about to make purchasing decisions (high-value target window)
- Which customers are expanding IT infrastructure (growth indicators)
- Which customers might be vulnerable to ransomware (mission-critical systems identified)
Pax 8's Characterization Issues
When Pax 8 says the data "did not contain personally identifiable information," this is a narrow interpretation. The data certainly contains business-sensitive information and information that can be traced to specific individuals (account owners).
This characterization matters for regulatory and legal purposes, but it understates the actual sensitivity and value of the leaked data.

Recommendations for MSPs and Affected Organizations
If your organization was affected by this breach, here are concrete steps to take.
Immediate Actions (Within 24-48 Hours)
1. Verify impact scope: Confirm whether your organization's data was in the exposed spreadsheet. Contact Pax 8 directly for clarity on which customers were affected.
2. Alert your security team: Brief your internal security team and executives. This data is now potentially in the hands of threat actors, and your organization should be prepared for targeted attacks.
3. Monitor for suspicious activity: Increase monitoring of your network and endpoints for any indicators of compromise. Threat actors may attempt to exploit the information immediately.
4. Prepare communications: Draft communications to your own customers explaining that their information may be exposed. Transparency reduces reputational damage.
5. Review renewal dates: If your renewal dates were exposed, accelerate or postpone renewal dates where possible to avoid the predictable window when you're vulnerable.
Medium-Term Actions (1-2 Weeks)
1. Threat modeling: Conduct threat modeling specific to the data exposed about your organization. What attacks become more effective now that threat actors know your software stack and license counts?
2. Email security audit: Conduct a full audit of your email security posture. Can you send large customer databases to external recipients without approval? Do you have adequate DLP policies?
3. Access controls review: Review who in your organization has access to sensitive data like customer information and pricing. Implement least-privilege access.
4. Incident response plan: Test or develop an incident response plan. This breach may not be the last. Be prepared to respond quickly to any security incidents.
5. Vendor risk assessment: Re-evaluate your risk tolerance for using Pax 8. Are there alternative marketplace platforms? How has this incident affected your confidence in Pax 8's security practices?
Long-Term Actions (1-3 Months)
1. Security culture: Implement training for employees on data handling, secure email practices, and attachment verification. Most breaches involve human error.
2. Data governance: Implement formal data classification policies. Not all employees need access to complete customer databases.
3. DLP implementation: If you haven't already, implement Data Loss Prevention systems that prevent accidental transmission of sensitive data.
4. Encryption adoption: Encrypt sensitive data at rest. Even if a file is exfiltrated, encryption provides an additional protection layer.
5. Threat intelligence integration: Subscribe to threat intelligence services that monitor dark web activity related to data breaches. Early warning if your data surfaces can enable faster response.

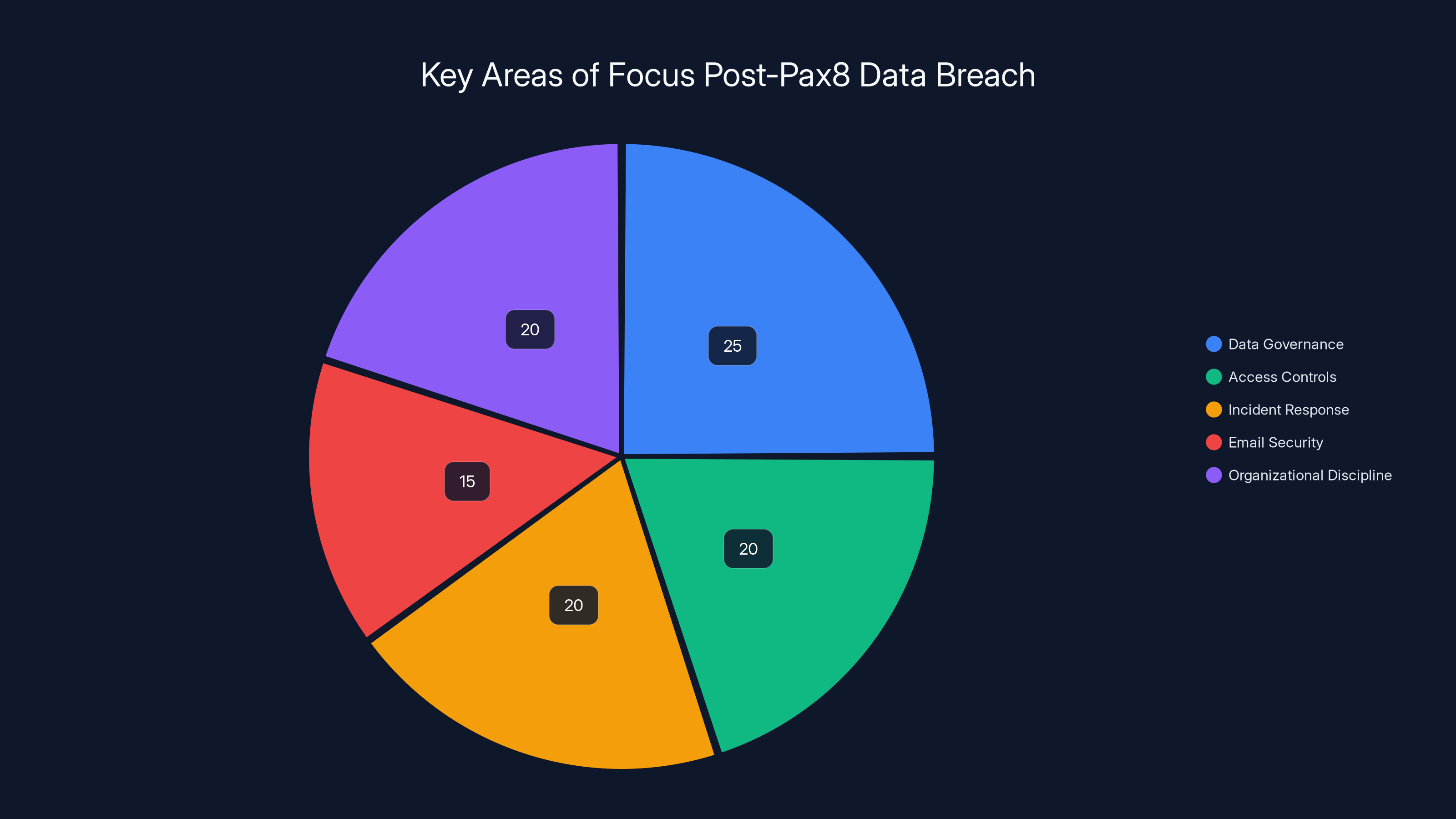
Estimated data shows that data governance and access controls are top priorities post-breach, highlighting the need for comprehensive security measures.
Broader Implications for Cloud Commerce Platforms
This incident has implications beyond Pax 8. It raises important questions about how cloud commerce platforms generally handle sensitive partner and customer data.
The Problem of Data Aggregation
Cloud commerce platforms like Pax 8 necessarily accumulate vast amounts of data:
- Customer lists from thousands of organizations
- Usage and licensing information
- Financial information and pricing
- Renewal schedules and contract terms
This data aggregation is essential for the platform's operation. But it creates enormous risk. A single breach can expose thousands of organizations simultaneously.
Compare this to traditional software vendors, where each customer relationship is isolated. If a vendor's system is breached, one customer's information is exposed. With cloud commerce platforms, a single incident affects the entire partner network.
Regulatory Scrutiny Ahead
This incident will likely prompt regulatory scrutiny. Regulators in the EU, UK, and other jurisdictions are increasingly focused on vendor risk and data handling practices.
Expect to see:
- Requests for evidence of Pax 8's data governance practices
- Audits of other cloud commerce platforms for similar vulnerabilities
- Potential fines or enforcement actions if regulators determine practices were inadequate
- Increased contractual requirements for customers and partners demanding stronger security commitments
Industry-Wide Best Practices
Cloud commerce platforms should be implementing:
Data minimization: Don't aggregate unnecessary data. If you don't need to store 56,000-row customer databases on employee systems, don't.
Encryption everything: Encrypt sensitive data at rest and in transit. This won't prevent accidental transmission, but it provides defense in depth.
Automated controls: Implement DLP, email security, and endpoint controls that prevent accidental transmission of sensitive data.
Regular audits: Conduct regular audits of who has access to what data and why. Remove access for employees who no longer need it.
Incident response: Have a tested, documented incident response plan. Speed matters in breach response.

Industry Precedents: Similar Incidents in the MSP Ecosystem
This incident isn't unprecedented. The MSP and cloud services industry has experienced several similar breaches and exposure incidents.
Connect Wise Supply Chain Attack (2022)
Connect Wise, a major MSP management platform provider, suffered a significant breach affecting thousands of MSPs. The breach included customer data and system access credentials. This incident demonstrated that even established MSP infrastructure providers can be vulnerable.
Kaseya VSA Ransomware Attack (2021)
Kaseya VSA, remote management software used by thousands of MSPs, was compromised by the REvil ransomware gang. The attack cascaded through the MSP supply chain, affecting hundreds of downstream customers. This incident showed how vulnerabilities in central platforms can have exponential impact when MSPs are involved.
Solar Winds Supply Chain Attack (2020)
Solar Winds software updates were compromised to distribute malware to thousands of customers. The attack affected not just businesses but U. S. government agencies. This demonstrated that even trusted vendors can be compromised in supply chain attacks.
Lessons from Past Incidents
These precedents suggest patterns:
- Supply chain vulnerabilities are critical: Attacks on platforms serving MSPs have disproportionate impact
- Trust is earned hard and lost easily: One breach damages vendor relationships for years
- Incident response speed matters: Fast, transparent communication reduces damage
- Technical controls can't replace process controls: Many incidents involve human error or process failures, not just technical vulnerabilities

The Role of Email Security in Preventing Similar Incidents
This incident happened via email. Understanding how modern email security should prevent such incidents is important.
Email Security Best Practices
Data Loss Prevention (DLP): Modern DLP systems scan email attachments for patterns suggesting sensitive data. A spreadsheet with 56,000 entries containing customer names, license counts, and financial information would trigger DLP policies at well-configured organizations.
Recipient verification: Some email security systems require approval before sending emails to external recipients or groups. This creates a speed bump that catches mistakes before they become breaches.
Encryption: Sensitive attachments should be encrypted or sent through secure file transfer mechanisms that require authentication to access.
Audit logging: Every email containing sensitive data should be logged and auditable. This enables forensic investigation when breaches occur.
User training: Email is the #1 attack vector for data exfiltration. Organizations that invest in email security training significantly reduce accidental data exposure.
Email-Specific Threats
Emails are particularly dangerous for data exposure because:
- Permanence: Once sent, email exists in multiple places (sender's sent folder, recipient's inbox, email provider's backup systems)
- Forwarding: Recipients can easily forward emails to others, amplifying exposure
- Recovery difficulty: Recalls and deletions in email aren't reliable
- External systems: Email passes through multiple external systems (ISPs, email providers), any of which might retain copies
Given these characteristics, organizations handling sensitive data should have robust email security controls.

Looking Forward: What This Means for the MSP Industry
This incident has several implications for how MSPs, vendors, and platforms will evolve.
Increased Due Diligence
MSPs will likely increase due diligence on platforms and vendors they depend on. Questions about security practices, incident response, and data governance will become standard in vendor evaluation.
Pax 8 and similar platforms will face more scrutiny during sales cycles. Sales teams will need to address security questions more thoroughly.
Market Opportunity
This incident creates opportunities for security vendors:
- DLP vendors can market the need for email security in the MSP context
- Cloud access security brokers (CASBs) can position themselves as solutions for controlling cloud platform access
- Incident response firms can grow their MSP-focused practices
- Risk management consulting focused on supply chain risk will become more valuable
Regulatory Evolution
Expect regulators to focus increasingly on supply chain security. Questions like "Who has access to customer data at your vendors?" will become standard compliance questions.
Data processing agreements and vendor security questionnaires will become more demanding and specific.
Industry Consolidation Pressure
This incident might accelerate consolidation in the cloud commerce space. Smaller, under-resourced platforms might struggle to invest in security infrastructure. Larger, well-funded platforms like Pax 8 will likely emerge stronger as customers consolidate around vendors they trust more.
FAQ
What exactly was exposed in the Pax 8 data breach?
The Pax 8 breach exposed a CSV spreadsheet containing over 56,000 entries from approximately 1,800 customers. The exposed data included organization names, Microsoft SKUs (product codes), license counts, renewal dates, financial information (gross and net bookings), territory information, and Pax 8 account owner details. While Pax 8 claimed no personally identifiable information was exposed, the data includes organizational identifiers and personal names of Pax 8 employees, making it sensitive from both privacy and business perspectives.
How did the data exposure happen?
A Pax 8 employee sent an email to fewer than 40 UK-based partners with the incorrect CSV attachment. Instead of attaching a simple pricing document as intended, the employee attached a comprehensive internal spreadsheet containing aggregated customer data. The error wasn't discovered immediately and only became apparent when external parties contacted Pax 8 about the exposure. The incident highlights failures in email security controls, data access management, and file selection safeguards.
Who was affected by the data breach?
Approximately 1,800 Pax 8 customers were affected, with data exposure primarily impacting UK-based MSP partners and at least one Canadian organization. The initial email was sent to fewer than 40 recipients, but because email is easily forwarded and shared, the actual number of people with access to the data may be higher. MSPs, their customers, and end-users of cloud services managed through Pax 8 partners are all potentially affected.
What did cybercriminals do with the exposed data?
Reports indicate that cybercriminals quickly reached out to email recipients attempting to purchase the leaked data. This is standard practice in the data breach marketplace, where stolen datasets are bought and sold on dark web forums and encrypted channels. At the time of reporting, the data had not appeared on public dark web marketplaces, though private sales or exclusive access arrangements may have occurred. The data could be used for ransomware targeting, competitive intelligence, supply chain attacks, or compliance-based extortion.
How did Pax 8 respond to the breach?
Pax 8 responded with relatively swift incident management, sending follow-up communications to recipients requesting deletion of the compromised emails and confirmation that the information wouldn't be further distributed. The company confirmed the breach in an official email, explained what was exposed, and clarified that core Marketplace systems and security controls were not impacted. However, some aspects of the response remained opaque, including how the breach was discovered and whether additional support services were offered to affected parties.
What should MSPs and affected organizations do about this breach?
Affected organizations should immediately verify whether their data was exposed by contacting Pax 8 directly. They should alert security teams, increase network monitoring for suspicious activity, and prepare communications for their own customers. Medium-term actions include conducting threat modeling specific to the exposed information, auditing email security and access controls, reviewing incident response plans, and reassessing vendor security practices. Long-term, organizations should implement formal data governance, deploy DLP systems, adopt encryption for sensitive data, and integrate threat intelligence monitoring.
Could this incident have been prevented?
Yes, this incident could have been prevented with stronger technical and process controls. Data Loss Prevention (DLP) systems scanning email attachments should have flagged a 56,000-row customer database being sent to external recipients. Role-based access control (RBAC) should have restricted such a file to employees with legitimate business need. Email security policies requiring approval before sending to external recipients could have caught the error before transmission. Data classification and encryption could have provided additional protection. The incident represents failures in data governance, access controls, and email security best practices.
Conclusion: Learning from Pax 8's Misstep
The Pax 8 data breach is a high-profile reminder that even well-established, trusted platforms serving critical infrastructure can suffer from operational failures. This wasn't a sophisticated cyberattack or a novel vulnerability. It was a human error amplified by insufficient safeguards.
For MSPs, this incident underscores the reality that your vendors' security practices directly impact your security posture. When Pax 8's employee sent that email, they didn't just expose Pax 8's customer data. They exposed the MSP partners' customer lists and business information. They cascaded risk through an entire supply chain.
For cloud commerce platforms and Saa S providers more broadly, the lesson is stark: data aggregation creates risk concentration. The more customer data you accumulate in central systems, the more impact a single security incident can have. Mitigation requires investment in data governance, access controls, and incident response capabilities.
For the broader cybersecurity industry, this incident demonstrates that technical controls matter, but so do process controls. The fanciest intrusion detection system doesn't prevent an employee from sending the wrong file via email. Preventing that requires email security controls, data classification, and organizational discipline.
The good news is that the data hasn't surfaced on public dark web marketplaces as of reporting. The bad news is that absence doesn't mean security. It's more likely that threat actors are either verifying the data, using it for private operations, or waiting for the right moment to exploit it.
MSPs and customers affected by this breach should act quickly to mitigate risk, knowing that the threat landscape has permanently shifted in their disfavor. The organizations impacted now exist in threat actors' targeting databases, and their software infrastructure is documented in criminal repositories.
Long-term, this incident should prompt organizations across the industry to elevate expectations for vendor security practices, strengthen their own incident response capabilities, and implement layered defenses that assume vendors will eventually experience breaches. In cybersecurity, not if but when is the operative principle.
The Pax 8 incident is a wake-up call that even in an age of advanced cybersecurity tools, the simplest mistakes can have the most significant consequences. That lesson deserves our collective attention.
Key Takeaways
- Pax8 exposed data on 1,800 customers through a misdirected email containing a CSV file with 56,000+ sensitive entries including organization names, Microsoft SKUs, license counts, and renewal dates
- The breach resulted from multiple security failures: inadequate access controls, insufficient email safeguards, and lack of data classification preventing the file from being transmitted externally
- Cybercriminals immediately attempted to purchase the leaked data, though it has not yet surfaced on public dark web marketplaces, suggesting either private sales or data hoarding for future exploitation
- MSPs and customers affected should immediately verify exposure, increase security monitoring, audit vendor practices, and implement data governance controls to prevent similar incidents
- This incident reflects broader supply chain security risks in cloud commerce platforms that aggregate sensitive customer data, with implications for regulatory scrutiny and industry consolidation
Related Articles
- Illinois Health Department Data Breach: 700K+ Exposed [2026]
- FCC Cyber Trust Mark Program: UL Solutions Withdrawal & National Security Impact [2025]
- Best Photo Recovery Software for Deleted Images [2025]
- GenAI Data Policy Violations: The Shadow AI Crisis Costing Organizations Millions [2025]
- Critical Infrastructure Breach: Engineering Firm Hack Exposes US Utilities [2025]
- NordVPN Salesforce Breach Claim: What Really Happened [2025]



