Microsoft Teams Phishing Attacks: How Hackers Steal Email Credentials [2025]
Microsoft Teams has become a lifeline for distributed teams. But it's also become a weapon in the hands of attackers who know exactly how to exploit the trust we place in it.
Here's the thing: most phishing still relies on email links that bounce you to sketchy websites. But a new campaign—active across multiple continents—doesn't bother with any of that. Instead, attackers are weaponizing Teams itself. They're creating fake finance-themed teams, using Unicode obfuscation to hide red flags, and sending official-looking Microsoft emails that invite you to join. By the time you realize something's wrong, your email account is compromised.
I'm not talking about some fringe attack hitting a handful of users. Check Point researchers documented this campaign affecting organizations across the United States (nearly 68% of incidents), Europe (15.8%), Asia (6.4%), and smaller pockets in Australia, New Zealand, Canada, and Latin America. The attack vector is ingenious because it weaponizes the exact feature that makes Teams useful: guest access.
Let's walk through what's actually happening, why it works so well, and how to protect your organization before someone on your team falls for it.
TL; DR
- The attack uses Teams' legitimate "Invite a Guest" feature to send official Microsoft emails, bypassing traditional phishing detection
- Obfuscated team names with Unicode characters and visual tricks appear normal to targets but fool automated security systems
- Nearly 68% of documented attacks targeted US organizations, with significant activity in Europe and Asia
- No malware or suspicious links required—social engineering and trust in Microsoft branding do the heavy lifting
- Financial and billing-themed team names create urgency that drives users to click and provide credentials
- Human vigilance and staff training remain your strongest defense against this technique
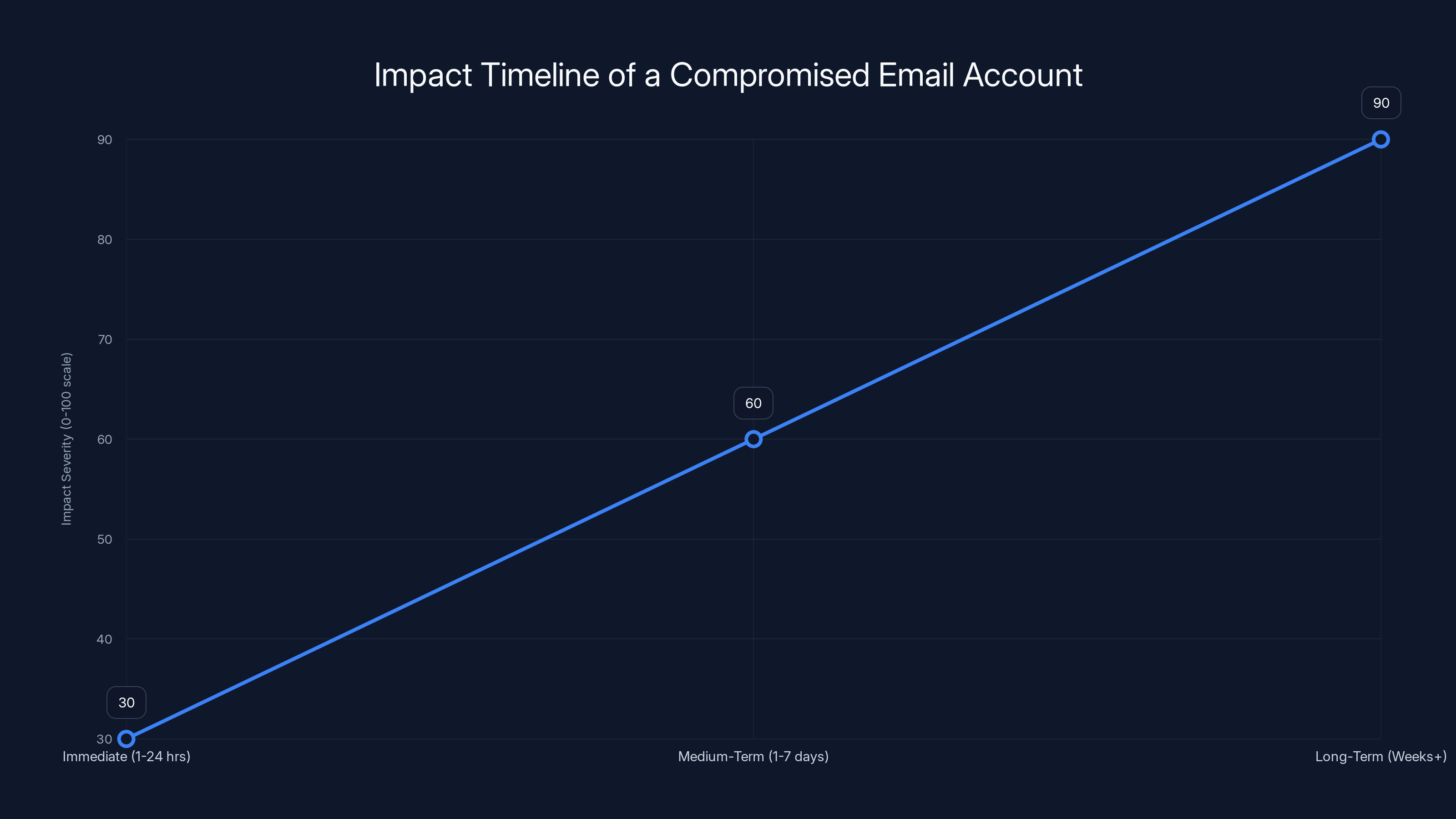
Estimated data shows that the impact severity of a compromised email account increases significantly over time, peaking in the long-term as regulatory fines and reputational damage take effect.
The Fundamentals: Why Teams Is Such an Attractive Target
Teams has exploded in adoption. Microsoft Teams now has hundreds of millions of active users, making it the default collaboration platform for enterprises worldwide. This massive footprint is exactly why attackers have shifted their focus here.
Unlike email, where phishing filters have become reasonably sophisticated over the past decade, Teams security relies heavily on a different assumption: the messages you receive come from people or organizations already in your network. That assumption breaks down fast when attackers can leverage Microsoft's own invitation infrastructure to legitimize their fake teams.
The genius of this approach is that it avoids every traditional phishing email security control. There's no malicious link. There's no file attachment. There's no suspicious sender domain. There's only an official Microsoft email saying someone invited you to join a Teams channel. Most email security systems aren't even looking for the right threat here because, technically, the email is legitimate.
What makes this worse is that Teams adoption in enterprises means the platform feels inherently trustworthy to employees. When someone gets a Teams invite, their guard is down. They're thinking about collaboration, not compromise.
But there's a second psychological factor at play here. The fake teams all use financial or billing language. "Urgent Payment Required." "Invoice Review." "Finance Adjustment." These names trigger the exact emotional response attackers are counting on: urgency mixed with fear. Nobody ignores a Teams invite related to money. That's what makes this approach devastatingly effective.
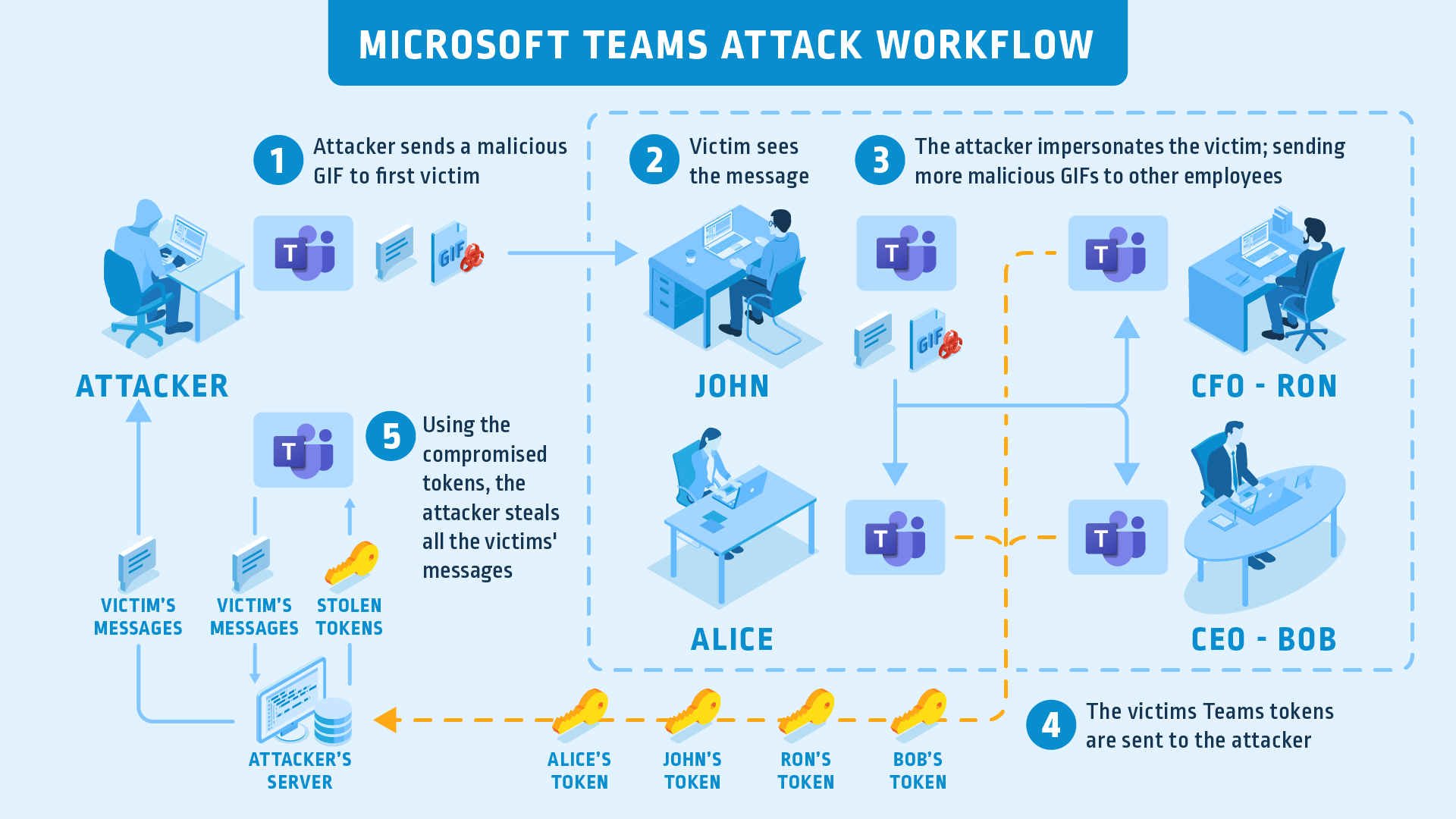
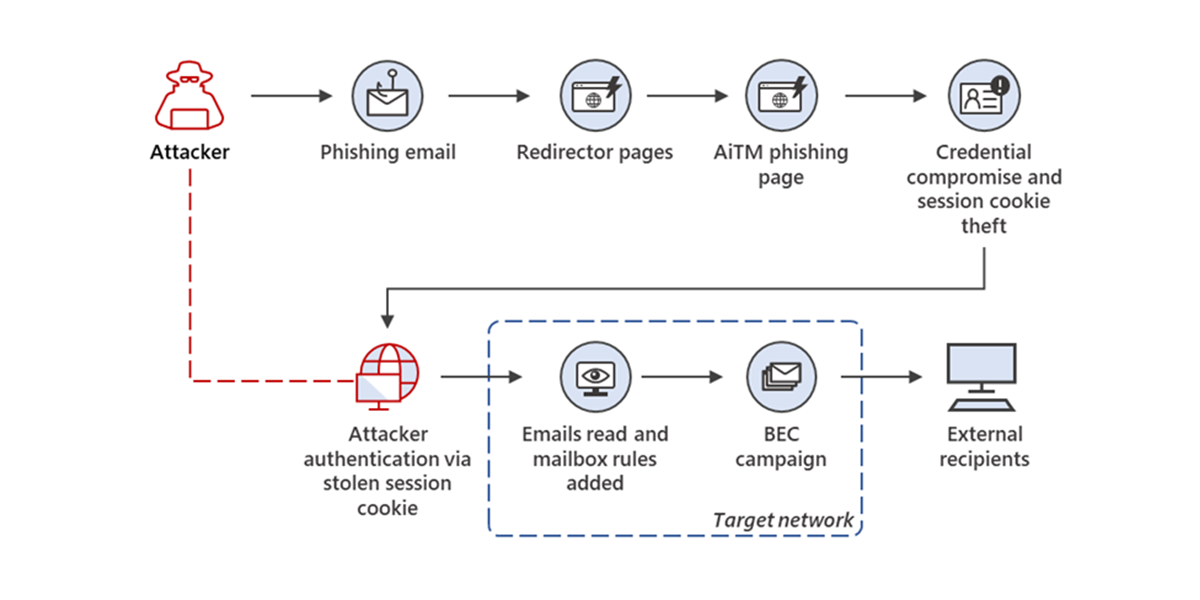
How the Attack Actually Works: Step-by-Step
Let's break down the mechanics of this attack, because understanding the process is how you teach your team to spot it.
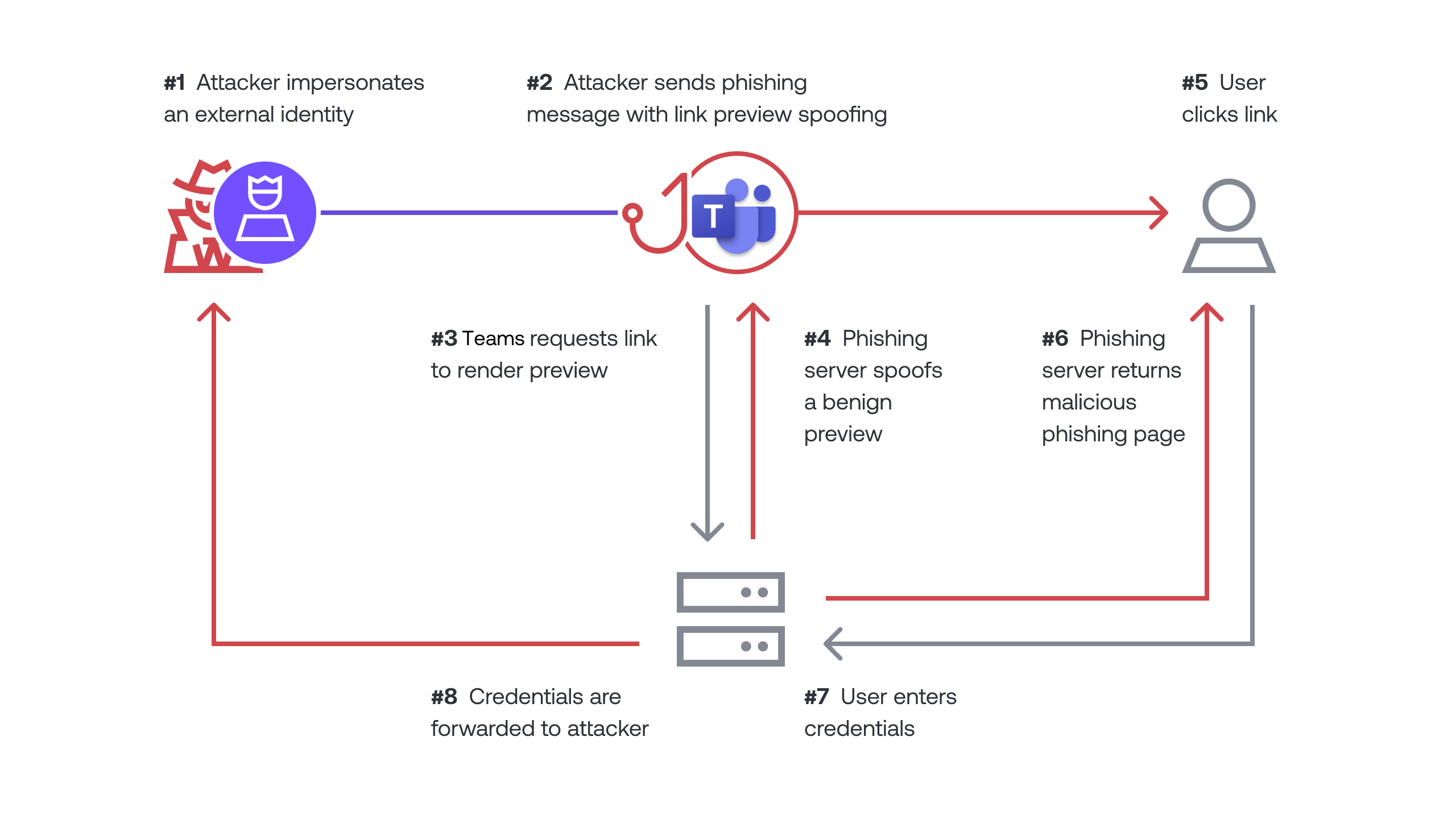
Step 1: Team Creation with Obfuscation
The attacker starts by creating a new Teams workspace. But they don't use a normal name like "Finance Review." Instead, they embed Unicode characters that look identical to standard letters but trick automated security systems. For example, they might use a Cyrillic character that looks visually identical to a Latin letter. To your eye, the team name appears normal. To a security filter looking for keywords like "invoice," the Unicode-laden version slides right through.
Common obfuscation techniques include:
- Mixed Unicode characters (Cyrillic, Greek, or Arabic characters that resemble Latin letters)
- Zero-width characters that don't display but are present in the name
- Homoglyphs (characters that look nearly identical but have different Unicode values)
- Mixed case with unusual spacing to break pattern matching
Step 2: Guest Invitation via Official Microsoft Infrastructure
Once the team exists, the attacker uses Teams' built-in "Invite a Guest" feature. This is the critical moment. When you invite someone as a guest to a Teams channel, Microsoft sends an official email from Microsoft's infrastructure. The email looks like it comes from Microsoft. Because, technically, it does.
The invite email contains:
- Microsoft branding and official formatting
- The team name (containing the finance-themed obfuscated text)
- A legitimate Microsoft link to accept the invitation
- Professional language that creates trust
From the recipient's perspective, this is indistinguishable from a legitimate team invitation. Your email security software has no reason to flag it. Your CEO didn't send it, but Microsoft infrastructure did, so all the security checks pass.
Step 3: The Credential Harvest
When the target clicks "Accept" and opens the Teams workspace, they're taken to a login page. This is where the actual phishing happens. The page might be a credential harvester designed to look like Microsoft's login screen, or it might be a malicious site hosting fake Teams infrastructure.
The user enters their email and password, thinking they're logging in to Teams. Instead, they've handed their credentials directly to the attacker. From there, the attacker has access to the victim's email account, calendar, documents, and potentially the entire organizational network if that email account has administrative privileges.
What makes this especially dangerous is the speed. The attacker gets access to email and potentially your entire organization in minutes. By the time your security team realizes something's wrong, the damage is already spreading.
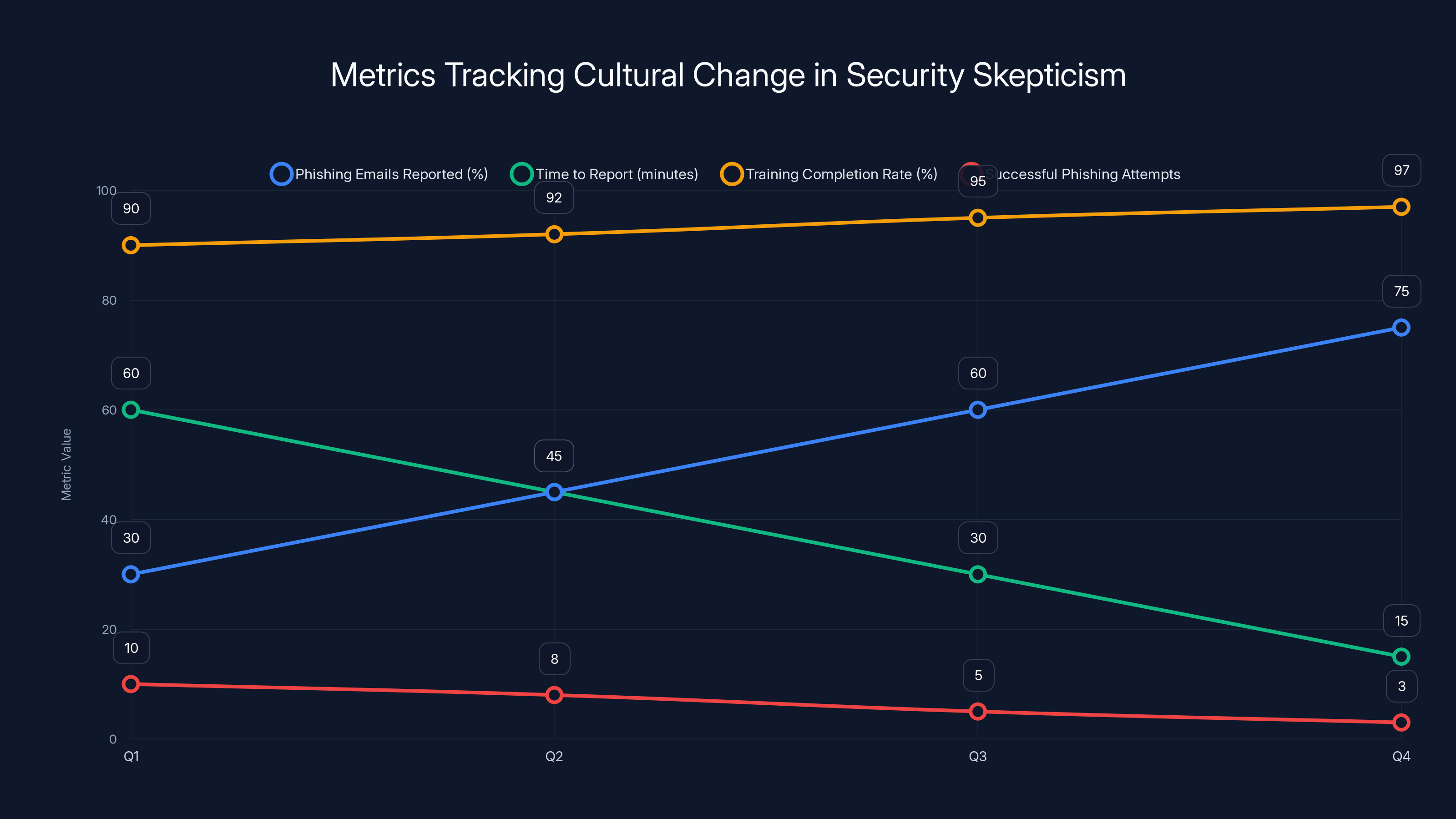
Estimated data shows an increase in phishing emails reported and training completion rates, while time to report and successful phishing attempts decrease, indicating a positive shift in security culture.
The Obfuscation Trick: Why Automated Detection Fails
Automated security systems—firewalls, email filters, threat detection software—rely on pattern matching and keyword recognition. They look for known phishing indicators like malicious domains, suspicious file types, and commonly used phishing keywords.
But Unicode obfuscation breaks that pattern matching in clever ways.
Consider this example: An automated system is looking for team names containing "invoice." A normal attacker might name their team "Invoice Review" and get caught by the filter. But the clever attacker uses Cyrillic characters:
- Standard Latin "i" (U+0069) → Cyrillic "і" (U+0456)
- Standard Latin "c" (U+0063) → Cyrillic "с" (U+0441)
- Standard Latin "o" (U+006F) → Cyrillic "о" (U+043E)
To human eyes, "Іnvоіce Revіew" looks identical to "Invoice Review." But to a regex pattern looking for the exact Unicode sequence of "invoice," the Cyrillic substitution is invisible. It doesn't match. The email sails through.
This technique is so effective because it exploits the gap between human perception and machine logic. We recognize words by shape and context. Machines recognize them by exact character codes. The attacker found the space between those two systems.
Geographic Distribution: Where This Attack Is Hitting Hardest
Check Point's research documented the geographic spread of this campaign with precision. Understanding where the attack is most active helps organizations prioritize their response.
United States Dominance (68% of Incidents)
The majority of attacks concentrated in the United States, which makes sense for several reasons. First, US organizations tend to have larger Teams deployments. Second, the attacker likely speaks English and understands English-language finance terminology well enough to make the fake team names convincing.
Within the US, the attack wasn't random. Certain industries were hit harder than others, though the attacker doesn't appear to target sectors deliberately. Instead, they're running a broad campaign that catches organizations across multiple verticals. Manufacturing, technology, education, and professional services all saw significant activity.
Europe (15.8% of Incidents)
European organizations experienced the second-highest concentration of attacks. Countries like Germany, France, UK, Netherlands, Belgium, Italy, Spain, Denmark, Finland, Norway, and Sweden all reported incidents. This geographic spread suggests the attacker either has multilingual capabilities or is using Teams' internationalization features to craft region-specific team names.
European defenders face the added complexity of GDPR compliance. When a breach occurs, the notification requirements are strict and the fines are severe. This means organizations in Europe need to be especially vigilant about preventing credential compromise in the first place.
Asia (6.4% of Incidents)
While Asia represented a smaller percentage of documented attacks, the absolute number is still significant. Organizations in Singapore, and other regional hubs, reported incidents. The lower percentage might indicate either less Teams penetration in some Asian markets (where local collaboration platforms dominate) or simply less visibility into attacks in that region.
Australia, New Zealand, Canada, and Latin America
These regions experienced smaller shares of documented activity, but the campaign clearly had global reach. Latin America saw interesting regional variation, with Brazil and Mexico experiencing the highest activity (over 75% of the region's incidents).
The Psychology Behind the Scam: Why People Fall for It
Technical defenses matter, but they only go so far. The reason this attack works is pure psychology. Let's break down why humans are vulnerable to this specific manipulation.
Authority and Trust Transfer
Microsoft has spent decades building trust. When you see that Microsoft logo and official formatting on an email, your brain enters a low-vigilance state. You're not thinking "Is this fake?" You're thinking "What does Microsoft want from me?" That shift in mindset is everything.
The attacker exploits this by using Microsoft's actual infrastructure. They're not pretending to be Microsoft. Microsoft is actually sending the email on their behalf. That's why no amount of domain checking or authentication verification helps. The email genuinely comes from Microsoft.
Urgency and Financial Language
Team names like "Urgent Payment Required" or "Invoice Review" trigger a specific emotional response in most people. Money creates urgency. Urgency creates cognitive load. When your brain is in fight-or-flight mode, you're less likely to scrutinize details.
Research in behavioral economics shows that humans make worse decisions under time pressure. The attacker knows this. They're betting that the speed of your response ("I need to click this NOW") will override your natural skepticism ("Wait, does this look right?").
Normalization of the Unexpected
Teams is where legitimate business happens. You receive invitations to channels multiple times per week. Your brain has normalized the experience. When another invitation arrives in your inbox, you don't think "Is this suspicious?" You think "Oh, someone added me to another channel."
The attacker is hiding in plain sight, using the normal flow of business communication to mask abnormal intent.
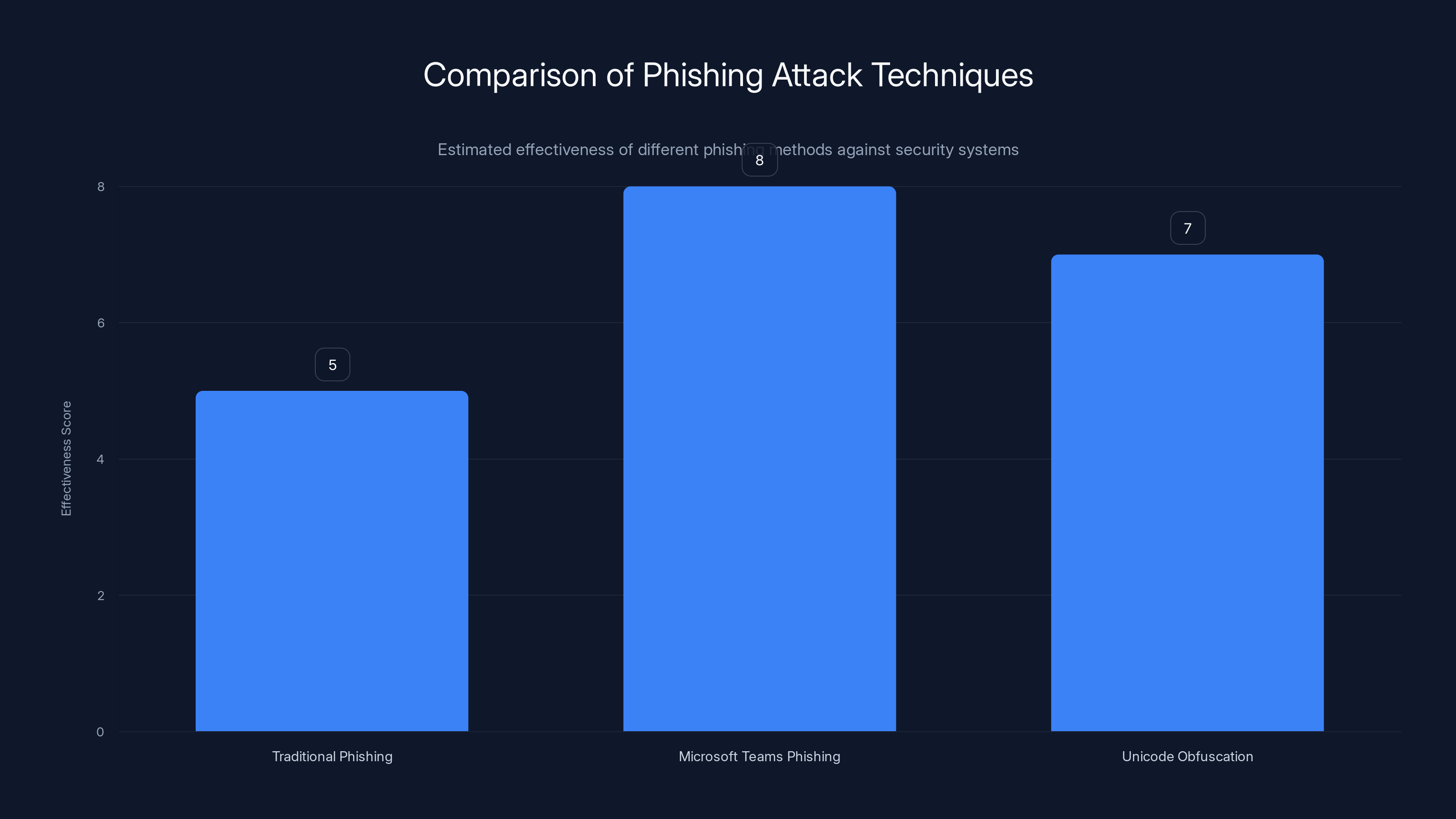
Microsoft Teams phishing attacks are estimated to be more effective than traditional phishing due to their use of legitimate infrastructure. Estimated data.
Targeted Industries and Why They Matter
While the campaign doesn't deliberately target specific sectors, certain industries are experiencing higher impact because they rely more heavily on Teams and handle more sensitive financial data.
Manufacturing
Manufacturing organizations use Teams extensively for supply chain coordination, production scheduling, and vendor management. These teams often contain people with access to financial systems, procurement databases, and supplier information. When an attacker compromises an email account in manufacturing, they gain visibility into critical business operations and financial transactions.
Technology
Tech companies are obvious targets because they employ security-conscious people who should know better (but often don't when they're in a hurry) and because they maintain the most valuable intellectual property. A compromised email in a tech organization might expose source code, customer lists, or strategic plans.
Education
Universities and educational institutions have complex organizational structures with thousands of email accounts. Many staff members have weak security hygiene because they're focused on teaching and research, not security. Educational institutions also manage sensitive student data, making them attractive targets for data theft.
Professional Services
Law firms, accounting firms, and consulting companies handle highly sensitive client information. A compromised email account in a professional services firm could expose attorney-client privileged communications, financial records, or strategic business information. The downstream impact extends to the firm's clients as well.
Red Flags That Should Trigger Immediate Suspicion
Now that you understand how the attack works, let's focus on what to actually look for. These red flags should prompt an immediate "Do not click. Report to security."
Unusual Team Names with Visual Oddities
Legitimate team invitations use clear, professional naming conventions. If a team name contains:
- Unusual spacing or mixed case ("In Vo Ice REview")
- Characters that look almost right but slightly off (especially Cyrillic mixed with Latin)
- Payment amounts or phone numbers embedded in the name
- Excessive exclamation marks or unusual punctuation
- Repeated characters ("INVOICE!!!!" or "Urgent... Urgent... Urgent")
Then someone is probably trying to trigger your attention while evading filters.
Invitations from Unknown or Vague Senders
Legitimate team invitations usually come from people you know or organizations you recognize. If the invite comes from "Microsoft on behalf of [organization]," but you can't identify who specifically invited you, that's suspicious.
Always ask: "Do I know who this person is? Did they specifically ask me to join this team? Would this team logically exist in our organization?"
Timing That Doesn't Make Sense
If you receive a Teams invite for a "payment review" or "billing adjustment" at 2 AM on a Sunday, that's unusual. Legitimate financial processes happen during business hours with clear context. Attackers often target off-hours because people are less vigilant.
The Credential Request
This is the final red flag. Legitimate Microsoft services never ask you to re-enter your credentials when you click an invite link. Your browser automatically handles authentication. If you're directed to a login page after clicking a Teams invite, that's a phishing page. Close it. Report it. Don't enter anything.
How Email Accounts Become the Keys to Your Organization
Understanding the damage from email compromise helps explain why this attack is so dangerous. When an attacker gains access to someone's email, they don't just read emails. They gain a foothold inside your entire organizational network.
Email as Identity
Your email account is tied to everything. Password resets for other services go to email. Two-factor authentication codes arrive via email. Recovery codes for critical services are stored in email. An attacker with email access can reset passwords on Slack, GitHub, cloud storage, VPN systems, and administrative consoles.
Lateral Movement
Once inside email, the attacker can read your calendar and see when important meetings happen. They can see who you communicate with and what projects you're working on. They can impersonate you in messages to other employees, asking for access to systems or credentials.
This is called lateral movement, and it's how a single compromised account turns into a complete organizational breach. The attacker uses your trust relationships to gain access to other systems and accounts.
Data Exfiltration
Your email contains years of communication. Business strategies, customer information, financial data, intellectual property, personal employee information, client contracts. An attacker with email access can copy this entire history in seconds and sell it or use it for competitive advantage.
Regulatory and Compliance Violations
When an email account containing regulated data is compromised, your organization faces notification requirements, potential fines, and legal liability. In healthcare, HIPAA violations can result in fines up to $1.5 million per incident category. In finance, similar penalties apply. The cost of remediating email compromise extends far beyond the immediate damage.
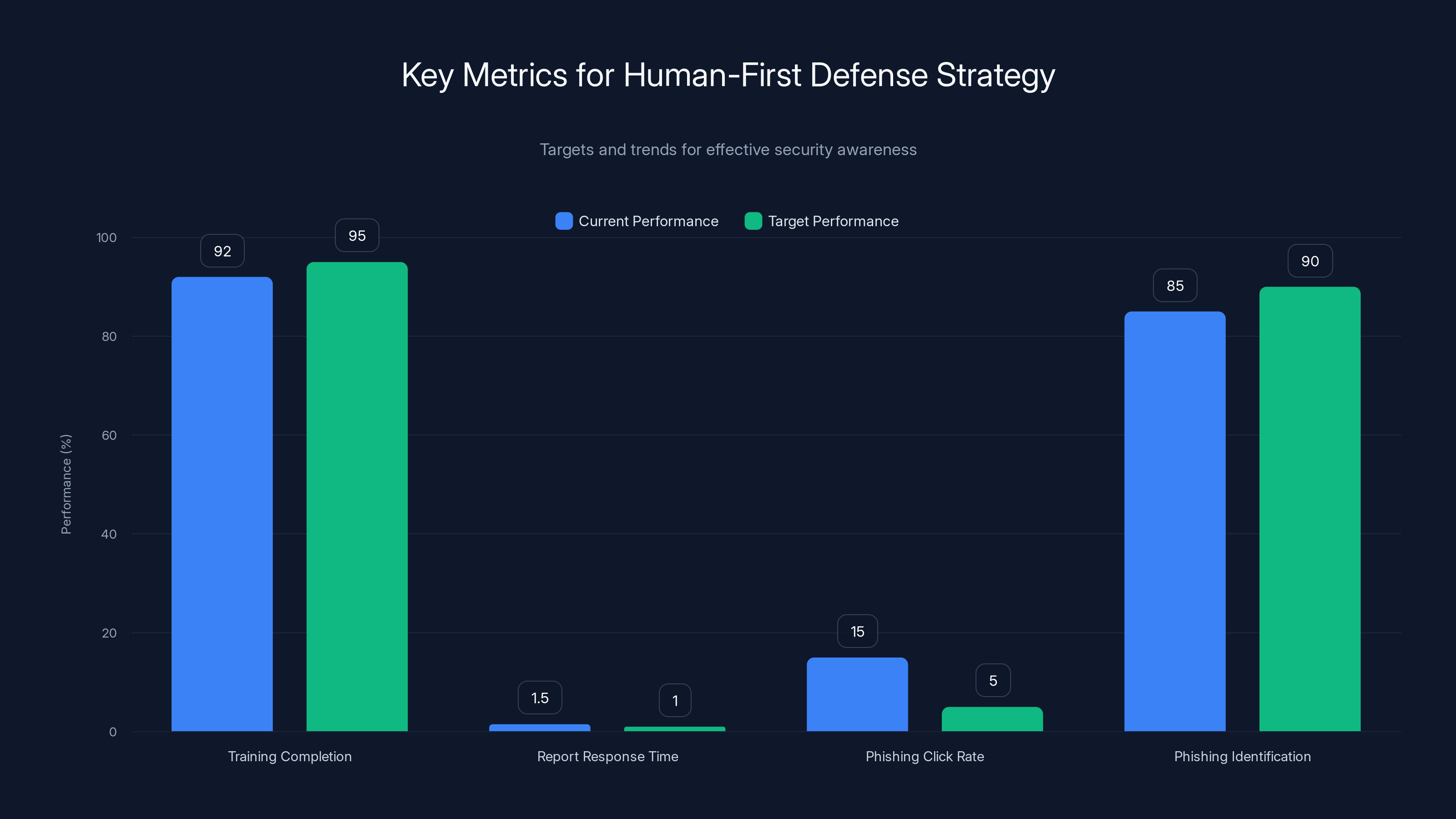
The chart compares current performance against target metrics for a human-first defense strategy. Training completion and phishing identification are close to targets, while response time and click rates need improvement. Estimated data.
The Failure of Traditional Email Security
Most organizations rely on email security systems to catch phishing. But this attack exposes a fundamental limitation of those systems: they can't distinguish between legitimate use of a platform and malicious use.
Why Standard Email Filters Miss This
Email security systems typically look for:
- Malicious domains or sender addresses
- Known phishing keywords and patterns
- Suspicious file attachments or scripts
- Links to known malicious sites
- Spoofed domains impersonating legitimate organizations
This attack has none of those indicators. The email comes from Microsoft's legitimate servers. The sender is technically the organization itself (inviting someone to Teams). The links are legitimate Microsoft links. The text contains no typical phishing language.
The Sandbox Problem
Some advanced email security systems use sandboxing—they open attachments and click links in isolated environments to see if anything malicious happens. But this attack doesn't execute malware. It doesn't trigger malicious behavior in a sandbox. It simply delivers a credential harvester page after the user authenticates, which happens outside the email security perimeter.
The User Education Gap
Email security training traditionally focuses on spotting phishing emails: suspicious senders, unusual requests, malicious links. But this attack flips the script. The email is legitimate. The sender is legitimate. The link is legitimate. The threat is the action the user takes after clicking.
This requires a different type of training: teaching users to be suspicious of unexpected Teams invitations regardless of how legitimate they appear, and understanding that Microsoft would never ask them to re-enter credentials.
Establishing a Human-First Defense Strategy
Since technical controls can't catch this attack, your defense rests on the people in your organization. That's not a weakness—it's actually where your strongest protection lies.
Comprehensive Security Awareness Training
Training isn't a checkbox you complete once. It needs to be ongoing and specific to actual threats your organization faces. This particular attack should be featured in training because:
- It uses a platform employees use daily
- It avoids traditional phishing indicators
- It's currently active and hitting organizations like yours
- It requires new defensive thinking, not old habits
Effective training shows real examples. Share screenshots of what an obfuscated team name looks like. Explain that legitimate Microsoft will never ask them to log in again. Have employees practice identifying red flags in simulated scenarios.
Creating a Safe Reporting Culture
The biggest barrier to reporting suspicious activity is fear of being wrong or looking foolish. "I don't want to bother security with a false alarm." This hesitation leaves attacks undetected.
Create a culture where reporting is rewarded. Implement a "suspicious email" button in email clients. Make sure employees know they can forward weird Teams invites to security without fear of consequences. Celebrate the people who report suspicious activity—they're the ones who catch real attacks before damage happens.
Metrics That Matter
Track these metrics to measure your human defense program:
- Percentage of employees completing security training: Target 95%+
- Average time from suspicious report to security investigation: Target under 1 hour
- Number of simulated phishing emails clicked: Track trends over time (should decrease)
- Percentage of employees correctly identifying phishing in assessments: Target 90%+
Executive Sponsorship
Security awareness only works when leadership models it and reinforces it. If your CEO ignores security training, employees notice. If executives report suspicious activity and talk about their own security practices, the culture shifts.
Implementing Technical Controls That Actually Help
While human vigilance is your primary defense, certain technical controls can reduce your exposure.
Teams Guest Access Policies
Microsoft Teams allows administrators to control who can invite guests and what guests can do. Review your policies:
- Restrict guest invitations to specific teams or channels
- Disable guest access if you don't need it
- Implement conditional access policies that require additional verification for guest invitations
- Log all guest invitations and review them periodically
Email Authentication and Verification
Implement DMARC, SPF, and DKIM to make it harder for attackers to spoof legitimate domains. While this doesn't prevent the attack (since it comes from legitimate Microsoft infrastructure), it provides defense-in-depth.
Conditional Access for Email
Implement policies that require additional verification for email access, especially for sensitive accounts:
- Require multi-factor authentication for all email access
- Implement location-based access controls (block unusual geographic access)
- Require device compliance (endpoints must have security software)
- Implement anomalous activity detection (unusual login patterns trigger additional verification)
Monitor for Credential Compromise
Implement tools that detect when employee credentials appear in phishing sites or breach databases. Services like Microsoft Defender can detect compromised credentials early.
Network Segmentation
Limiting what an attacker can do after compromising an email account requires proper network segmentation. Ensure that:
- Administrative accounts are separate from standard user accounts
- Critical systems are isolated from user networks
- Service accounts have minimal necessary permissions
- Lateral movement requires additional authentication
Incident Response Plan
Despite your best efforts, someone will eventually click a phishing link. When that happens, you need a plan:
- Identify and isolate the compromised account
- Reset credentials and notify the user
- Review what the attacker accessed
- Check for lateral movement and privilege escalation
- Investigate downstream impact
- Notify affected parties if data was exposed
- Document lessons learned
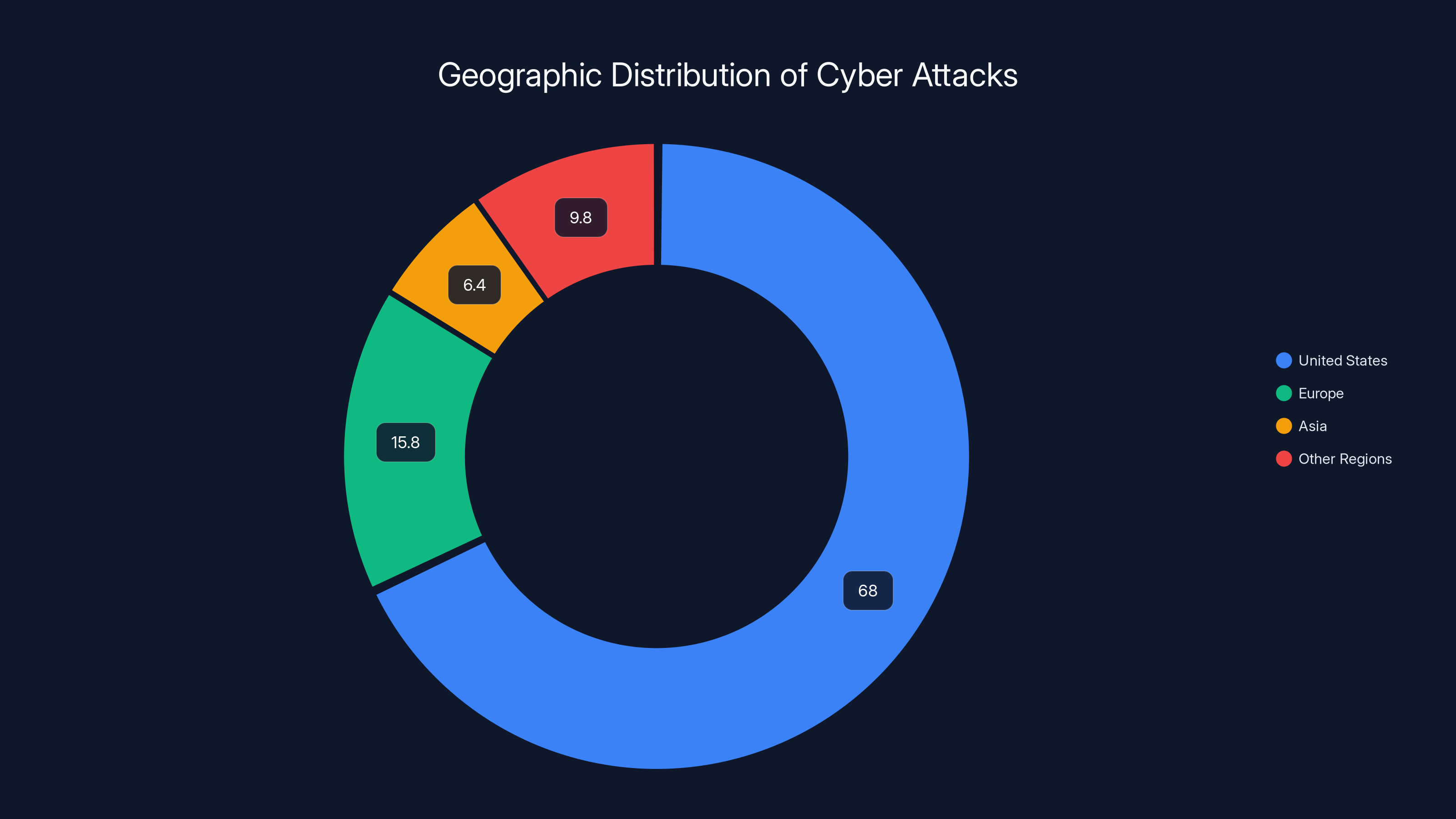
The United States experienced the highest concentration of attacks at 68%, followed by Europe at 15.8% and Asia at 6.4%. Other regions accounted for 9.8% of incidents. Estimated data.
The Broader Pattern: Why Attackers Shift Tactics
This Teams-based attack didn't appear out of nowhere. It's part of a predictable pattern in attacker behavior: as defenders improve at catching one attack type, attackers migrate to vectors defenders aren't watching.
The Evolution of Phishing
A decade ago, most phishing happened through email with obvious red flags: poor grammar, suspicious domains, urgent requests. Defenders got better. Email security improved. So attackers adapted.
They started using legitimate platforms—cloud storage services, document sharing, video conferencing—as delivery mechanisms. Why try to spoof Microsoft when you can use Microsoft's own infrastructure?
This pattern repeats because it's effective. Teams is trusted. Email from Teams invitations isn't flagged. Users don't question Teams activity. So the attacker uses Teams.
The Next Evolution
As organizations improve Teams security awareness, attackers will shift again. They might start using other collaboration platforms, VoIP systems, or emerging communication tools that employees trust but haven't heard warnings about.
The fundamental principle remains constant: attackers target the intersection of trust and low awareness. They find communication platforms that:
- Organizations use heavily
- Employees trust implicitly
- Security teams haven't focused training on
- Technical controls don't monitor closely

What Happens After a Compromise: The Damage Assessment
If someone in your organization has been compromised through this attack, here's what you're dealing with.
Immediate Impact (Hours 1-24)
Once an attacker has an email account, they typically:
- Change the password to lock out the legitimate user
- Enable email forwarding to capture ongoing communications
- Export the mailbox to an external storage service
- Check for cloud file access and copy sensitive documents
- Review the calendar for insights into business operations
- Look at contact lists to identify targets for follow-up attacks
All of this happens before you even notice the account is compromised. By the time you discover the breach (often when the user reports they can't access their email), the attacker already has your data.
Medium-Term Impact (Days 1-7)
The attacker uses the stolen information to plan secondary attacks:
- Sending phishing emails impersonating the compromised user to other employees
- Requesting sensitive information from vendors or customers
- Resetting passwords on cloud services
- Attempting to access administrative systems
- Selling or distributing the stolen data
Long-Term Impact (Weeks and Beyond)
Some of the damage from a single compromised email account extends for months or years:
- Loss of intellectual property or trade secrets
- Regulatory fines for data breach notification requirements
- Reputational damage when customers learn their data was exposed
- Remediation costs for cleaning up the damage
- Loss of trust from business partners and customers
The financial cost of email compromise is substantial. Studies show the average cost of a data breach in 2024 exceeded $4.9 million, with email as the initial attack vector in over 60% of cases.
Building a Detection and Response Infrastructure
Since prevention will eventually fail (no security measure is 100% effective), you need rapid detection and response capabilities.
Signals That Something's Wrong
Implement monitoring for these behaviors:
- Email forwarding rules created (especially to external domains)
- Large bulk email sends from a single account
- Unusual login locations or times for an account
- Mass file downloads from cloud storage
- Password changes without user request
- Admin privilege escalation from a standard user account
- Unusual API activity or automation execution
Alerting and Automation
Don't wait for humans to notice these behaviors. Implement automated alerts:
- Alert security team immediately when email forwarding is created
- Trigger account lock-out if unusual login patterns detected
- Notify user if devices are added to their account
- Pause business-critical workflows if suspicious activity detected
- Automatically disable API tokens if misuse is detected
Investigation Playbooks
When an alert triggers, security teams need a clear playbook:
- Verify the alert isn't a false positive (check if the user requested the action)
- Immediately change the account password
- Review account activity for the past 90 days
- Check for mailbox forwarding rules
- Identify what files or systems were accessed
- Determine what data was exposed
- Check if the attacker attempted lateral movement
- Notify affected parties if required by regulation
Retention and Forensics
Maintain email logs and access records for at least 90 days. When a compromise occurs, this history is critical for determining what happened and preventing future attacks.
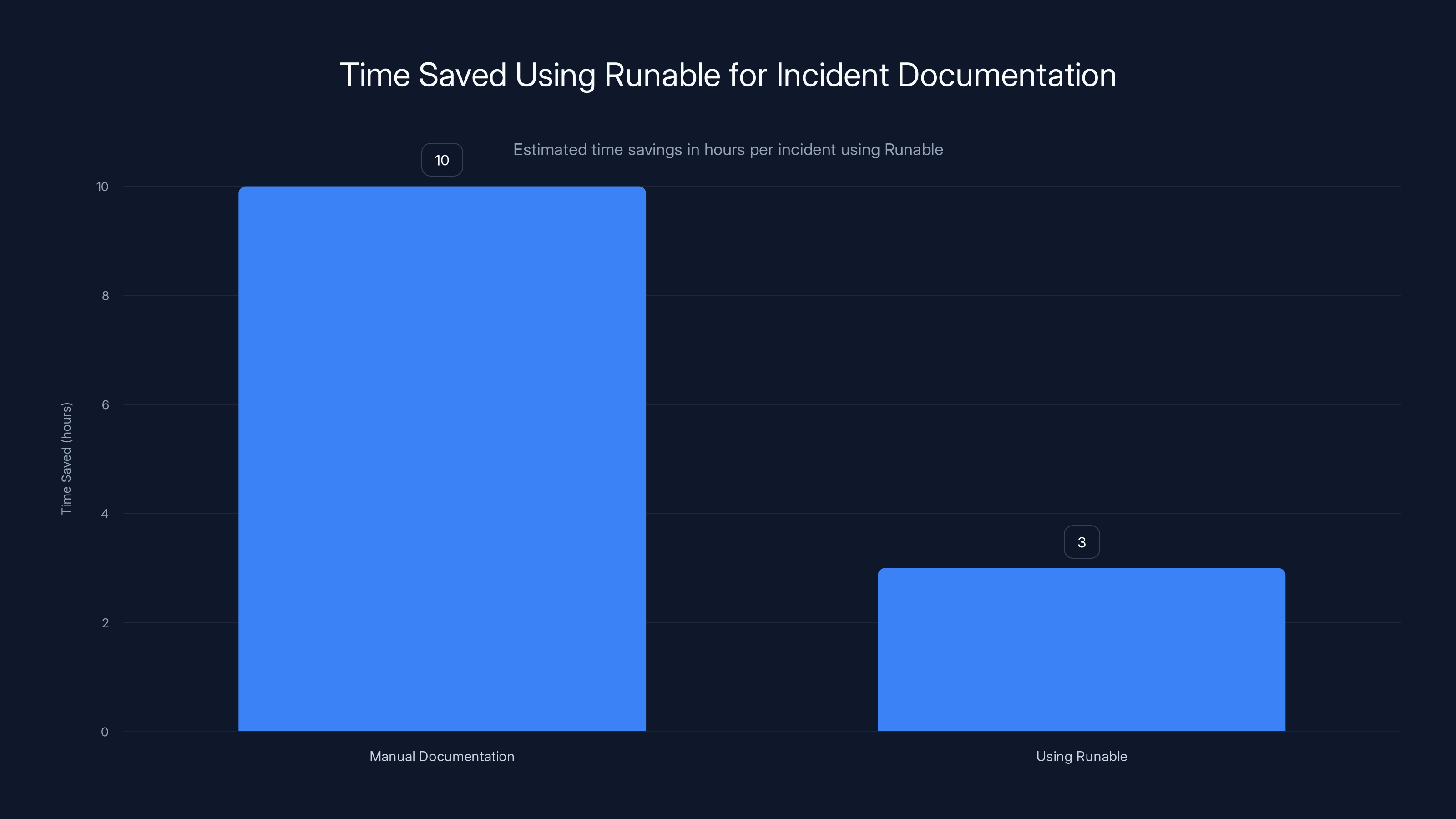
Using Runable can save an estimated 7 hours per incident by automating documentation tasks, significantly accelerating response times. (Estimated data)
Protecting Sensitive Accounts: Layered Defense for High-Value Targets
Not all accounts are created equal. Your CEO's email is worth significantly more to an attacker than a new hire's email. Your approach to protecting high-value accounts should be different.
Identifying High-Value Accounts
Focus enhanced protection on accounts belonging to:
- Executives (CEO, CFO, CTO)
- Finance department (access to payment systems)
- HR department (access to employee records and payroll)
- IT administrators (access to critical systems)
- Sales leaders (access to customer and deal information)
- Legal department (access to confidential communications)
Enhanced Protections for High-Value Accounts
For these accounts, implement stricter controls:
- Require hardware security keys for authentication (not just software MFA)
- Implement step-up authentication for sensitive actions (forwarding rules, admin access)
- Restrict email forwarding (disable for sensitive accounts)
- Implement conditional access that requires specific devices
- Monitor activity in real-time with alerting
- Restrict email delegation and shared mailbox access
- Require approval for cloud file sharing
Dedicated Devices for Sensitive Access
For the highest-risk accounts, consider dedicated devices that access only email and critical systems. These devices:
- Don't access the internet or download files from untrusted sources
- Maintain minimal software to reduce attack surface
- Use enterprise security configurations
- Allow monitoring of all activity
This sounds extreme, but for a CEO's account, the ROI is substantial.
Incident Response: The First 24 Hours
When you discover a compromised email account, your response in the first 24 hours determines the scope of damage.
Hour 1: Containment
Immediate actions:
- Reset the compromised account password
- Force sign-out of all active sessions
- Disable the account if it can't be immediately re-secured
- Notify the account owner
- Preserve evidence (don't delete anything the attacker touched)
- Check if MFA can still be used (attacker may have registered new devices)
Hours 2-6: Investigation
Determine scope:
- Review email forwarding rules (delete any suspicious ones)
- Check mailbox delegation permissions
- Review recent email activity and sent items
- Identify all files accessed or modified
- Check admin account activity (attackers often escalate privileges)
- Review Teams and other collaboration platform activity
- Search email for sensitive data that was exposed
Hours 6-24: Remediation
Clean up and prepare communication:
- Change passwords for any accounts accessed from this email
- Revoke API tokens and authentication sessions
- Remove suspicious email forwarding and delegation
- Notify customers if their data was exposed
- Prepare breach notification if required by regulation
- Document timeline and findings for post-incident analysis
After 24 Hours: Extended Investigation
Continue investigation for days or weeks:
- Determine if attacker moved laterally to other systems
- Check if persistence mechanisms were installed
- Conduct forensics on the compromised account
- Interview the account owner for context
- Check third-party systems that this account has access to
- Monitor for further activity from the attacker
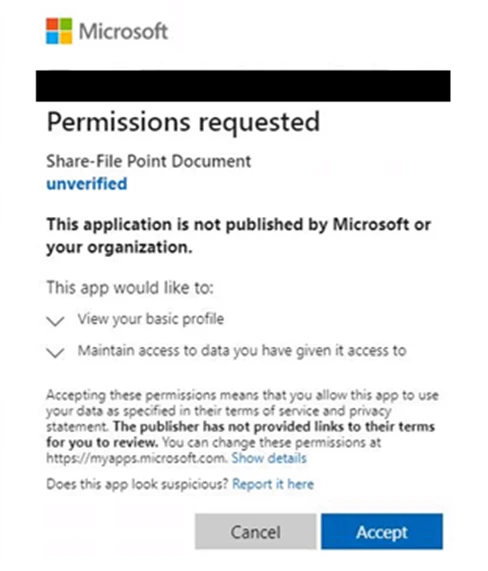
Real-World Impact: Why This Matters Beyond Theory
Let's ground this in reality. What does email compromise actually cost an organization?
The Vendor Impersonation Scam
An attacker compromises an account in accounting. They spend a week reviewing invoices and communications with major vendors. Then they send an email from the compromised account to a vendor saying "Please update our payment information for future invoices. Use this new banking detail." They attach a PDF invoice with legitimate company letterhead.
The vendor processes the fraudulent payment instruction. For the next month, $200,000+ in payments go to the attacker's account before anyone notices. Even when discovered, recovering the money from international bank accounts can be impossible.
The Internal Breach Cascade
An attacker compromises an HR manager's email. They review the employee directory and see that three finance employees have admin access to the company's accounting system. They send emails impersonating the HR manager: "Can you verify the password requirements for our new accounting system? We're doing a security audit. What's your current password?"
One employee responds with their password, thinking it's a legitimate internal request. The attacker now has accounting system access and transfers funds to themselves. It takes weeks to discover because the transaction logs show activity from the employee's legitimate account (used by the attacker).
The Customer Data Theft
An attacker compromises a sales director's email. The sales team uses the director's account to share customer information, contract terms, and pricing details. The attacker copies this data. Weeks later, a competitor mysteriously knows your pricing strategy for every customer. You lose major deals because competitors are undercutting you by exactly the right amount.
These scenarios aren't hypothetical. They happen constantly because email compromise is the easiest way for attackers to cause damage once they're inside your organization.
Advanced Defense: Zero Trust Architecture for Teams
Long-term security requires moving beyond perimeter defense (checking if traffic comes from a trusted network) to zero trust (verify every access attempt, every time).
Zero Trust Principles Applied to Teams
Zero trust means:
- Never trust, always verify: Every Teams invitation is treated as potentially suspicious until verified
- Least privilege: Users only get access they strictly need
- Continuous monitoring: All Teams activity is monitored for anomalies
- Assume breach: Design systems assuming some accounts will be compromised
Implementation Steps
Moving to zero trust for Teams requires:
- Identity verification: Implement strong identity verification before allowing Teams access (multi-factor authentication at minimum)
- Device trust: Verify devices meet security standards before allowing access (antivirus, encryption, updates)
- Continuous compliance: Monitor for policy violations and remediate immediately
- Activity monitoring: Alert on unusual Teams activity (bulk invitations, unusual access times, data exfiltration)
- Privilege management: Manage Teams admin access carefully, require elevated access for sensitive operations
Defense in Depth
Implement multiple layers:
- Email authentication (DMARC, SPF, DKIM)
- Conditional access policies
- Device compliance requirements
- Multi-factor authentication
- Anomaly detection
- User behavior analytics
- Content scanning
- Secure email gateways
No single layer stops determined attackers, but multiple layers force them to work harder and risk detection.
Emerging Threats: What Comes Next
Attackers are constantly evolving. Here's what security researchers expect in the coming months.
AI-Enhanced Impersonation
Large language models make it easier to craft convincing phishing messages. Instead of obviously broken English, attackers can generate grammatically perfect impersonations that match the writing style of real team members.
Deepfake Video in Teams
As video deepfake technology improves, attackers might create fake video messages from executives requesting credential transfers or wire fraud. Imagine receiving a video message from your CEO asking you to transfer funds to a new account. Detecting the deepfake becomes critical.
Supply Chain Attacks via Integrations
Teams integrates with hundreds of applications. If an attacker compromises a bot or integration that many organizations use, they can push malicious content to thousands of Teams channels at once. The impact could be massive.
Mobile-First Attacks
Mobile Teams adoption is increasing. Attackers will focus on mobile phishing since mobile devices have smaller screens (harder to spot obfuscation), less sophisticated security, and users are more likely to be distracted.
Creating an Organizational Culture of Security Skepticism
The most powerful defense is cultural. Organizations that survive attacks are the ones where:
- Employees feel empowered to question unusual requests
- Reporting suspicious activity is celebrated
- Security training is continuous and relevant
- Leadership models good security practices
- Skepticism is the default posture, not naivety
Building This Culture
It requires sustained effort:
- Make security visible: Post security reminders regularly, celebrate security wins, share lessons from near-misses
- Make reporting easy: Implement simple "Report Phishing" buttons, one-click forwarding to security
- Make consequences clear: Explain in real terms what happens when compromise occurs (this helps people understand why their action matters)
- Make training relevant: Use actual threats your organization faces, not generic examples
- Make leadership involved: Executives should talk about security in town halls and 1:1s
Metrics That Show Cultural Change
Track:
- Percentage of phishing emails reported before clicking: Should increase over time
- Average time to report suspicious activity: Should decrease
- Percentage of employees completing training: Should stay above 95%
- Reduction in successful phishing attempts: Should decrease as awareness improves
Leveraging Runable for Security Incident Response Documentation
When incidents occur, your team needs to generate comprehensive response reports, timelines, and communications quickly. Runable helps streamline this process by automating the creation of incident response documents, status reports, and stakeholder communications.
Instead of manually compiling investigation findings into formatted documents, Runable can generate professional incident reports, timeline documents, and remediation plans from your raw data. This saves hours during critical response periods when every minute counts.
Use Case: Generating incident response reports and stakeholder communications automatically during security incidents to accelerate containment and remediation
Try Runable For FreeFor organizations under attack, Runable's $9/month plan includes AI-powered document generation that can help compile evidence, create remediation timelines, and prepare breach notifications without slowing down your response team.
FAQ
What makes the Microsoft Teams phishing attack different from traditional phishing?
Traditional phishing relies on fake domains, malicious links, or suspicious attachments that security systems can detect. This Teams-based attack leverages Microsoft's legitimate infrastructure to send official-looking invitations through the actual "Invite a Guest" feature. The email genuinely comes from Microsoft, the link is genuine, and there's no malware involved. The threat only materializes after the user clicks and encounters a credential harvester, which happens outside the email security perimeter.
How do obfuscated Unicode characters fool automated security systems?
Automated security systems use pattern matching and keyword detection that look for exact character sequences. When attackers use Unicode homoglyphs (characters that look identical to standard letters but have different Unicode values), the attack bypasses these filters. For example, a Cyrillic "і" looks identical to a Latin "i" but registers as a completely different character. To humans, "Іnvoіce" looks like "Invoice." To security regex patterns, it's invisible and doesn't match.
What should I do if I receive an unexpected Teams invitation with suspicious characteristics?
Don't click the link. Instead, report the invitation to your security team immediately using your organization's phishing report mechanism. If you accidentally clicked and were directed to a login page, close the page without entering credentials and notify security. Contact the person or department that supposedly invited you through a verified communication channel (not Teams) to confirm whether the invitation was legitimate. Your security team can then investigate and block the malicious team.
How can I protect sensitive email accounts in my organization?
Implement layered protection for high-value accounts (executives, finance, IT admins) including hardware security key requirements, conditional access policies restricting unusual logins, disabled email forwarding, real-time activity monitoring, and dedicated devices for accessing critical systems. Use multi-factor authentication for all accounts, but require stronger forms (hardware keys instead of software apps) for sensitive roles. Enable step-up authentication for sensitive actions like creating email forwarding rules.
What's the average impact of a compromised email account?
The average cost of email-based data breaches exceeds $4.9 million, including detection time (average 206 days), remediation, regulatory fines, notification costs, and lost business. Compromised email accounts are the entry point for 60% of all data breaches. The impact extends beyond immediate financial loss to include reputational damage, loss of customer trust, and ongoing liability if personal data was exposed. Some organizations face GDPR fines of 4% of annual revenue for data breaches involving email compromise.
How can we improve detection of compromised email accounts?
Implement continuous monitoring for signals like email forwarding rule creation, unusual login patterns from new geographic locations, mass file downloads, password changes, and rapid privilege escalation. Use user behavior analytics to establish baselines and alert on anomalies. Implement conditional access policies that require additional verification for risky sign-ins. Maintain email logs for at least 90 days to enable forensic investigation. Implement credential breach monitoring to detect when employee credentials appear on phishing sites or breach databases.
What's the difference between traditional security awareness training and training for this specific attack?
Traditional training teaches people to spot obvious phishing: suspicious sender addresses, poor grammar, urgent requests, malicious links. This attack subverts that training because the email is legitimate, comes from Microsoft, and contains no traditional red flags. Effective training for this attack focuses on new principles: being skeptical of unexpected Teams invitations regardless of apparent legitimacy, never re-entering credentials after clicking an invite link, and treating finance-themed team names with extra caution. Training should show actual examples of obfuscated team names so employees can recognize the visual oddities.
How long does an attacker have access before detection?
The average time to detect a compromised email account is 206 days (over 6 months). During this time, an attacker with email access can completely infiltrate your organization, exfiltrate massive amounts of data, and establish persistent backdoors. The longer the attacker remains undetected, the more thorough their access becomes. This is why rapid detection infrastructure is critical—every day of undetected access multiplies the damage.
What's the role of leadership in preventing this type of attack?
Leadership sets the tone for organizational security culture. When executives model good security practices (using strong authentication, reporting suspicious activity, treating security seriously), employees follow. When leaders dismiss security concerns as inconvenient, employees cut corners. Leadership should regularly discuss security in town halls, reward employees who report suspicious activity, and ensure security awareness training is mandatory and relevant. Executives should also be held to the same security standards as employees—high-value accounts face the highest risk.
Are there regulations I need to follow when a Teams-based compromise occurs?
Yes. If personal data was exposed, you must comply with notification requirements. GDPR requires notification within 72 hours, CCPA requires notification without unreasonable delay, HIPAA requires notification of healthcare data breaches, and other regulations apply based on the type of data and your jurisdiction. You should also notify affected customers and any business partners whose data was compromised. Legal counsel should be involved immediately to ensure compliance with all applicable regulations.
The Bottom Line: This Attack Will Continue
The Teams-based credential harvesting campaign documented by Check Point represents a broader shift in attacker strategy. As defenders improve traditional email security, attackers migrate to vectors that are harder to defend: legitimate business platforms used by millions of people daily.
This attack will continue and evolve because it works. It requires minimal technical sophistication. It avoids traditional security controls. It exploits genuine trust in Microsoft infrastructure. And most importantly, it gets results. Some percentage of people will always click, and that's enough.
Your defense rests on three pillars: awareness (training people to spot red flags), prevention (implementing technical controls), and detection (finding compromises quickly when they occur). None of these alone is sufficient. All three together create an environment hostile enough to compromise that attackers move to easier targets.
The organizations that survive attacks intact are the ones that treat security as a continuous process, not a checklist. They invest in people, processes, and technology. They assume breaches will happen and plan for rapid detection and response. They create a culture where reporting suspicious activity is celebrated.
Start there. Your organization's security depends on it.
Key Takeaways
- Teams phishing attacks use Microsoft's legitimate infrastructure to bypass traditional email security controls
- Unicode homoglyphs in team names fool automated detection while appearing normal to human eyes
- 68% of documented attacks targeted US organizations, but the campaign is truly global
- Email credentials are the keys to organizational compromise, enabling lateral movement and data theft
- The average detection time of 206 days means attackers have months to infiltrate your systems
- Human awareness and rapid incident response are more effective than technical controls alone
- High-value accounts need enhanced protection including hardware security keys and conditional access policies
Related Articles
- OpenAI Scam Emails & Vishing Attacks: How to Protect Your Business [2025]
- Mustang Panda's CoolClient Backdoor Evolution: What Security Teams Need to Know [2025]
- Enterprise AI Security Vulnerabilities: How Hackers Breach Systems in 90 Minutes [2025]
- Okta SSO Under Attack: Scattered LAPSUS$ Hunters Target 100+ Firms [2025]
- TikTok US Outage Recovery: What Happened and What's Next [2025]
- 800,000 Telnet Servers Exposed: Complete Security Guide [2025]
![Microsoft Teams Phishing Attacks: How Hackers Steal Email Credentials [2025]](https://tryrunable.com/blog/microsoft-teams-phishing-attacks-how-hackers-steal-email-cre/image-1-1769638467858.jpg)



