Ransomware Groups Hit All-Time High in 2025: Qilin Dominates the Threat Landscape
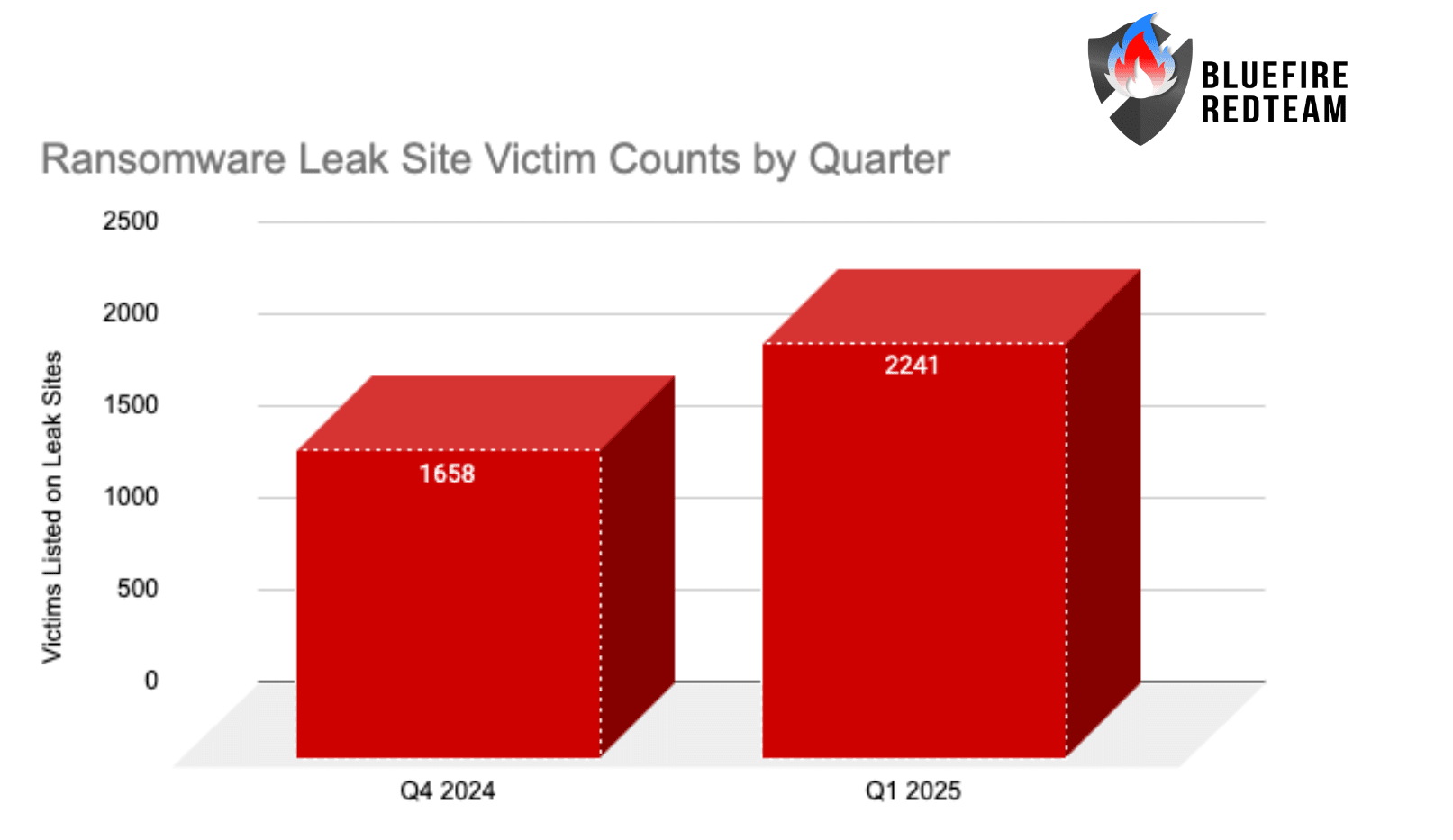
The ransomware crisis just got exponentially worse. We're not talking about incremental increases anymore. In 2025, the number of confirmed ransomware victims hit 7,458 organizations—a record that shatters every previous year. The number of active ransomware groups reached 124, with 73 of those being completely new operations. And if you think law enforcement's crackdown is slowing things down? Think again.
This isn't a niche security problem anymore. It's an existential threat to business continuity, critical infrastructure, and honestly, the stability of entire sectors. What started as opportunistic cybercriminals has evolved into a sophisticated, professionalized ecosystem with specialized roles, venture capital-style funding, and ruthless business practices.
The real shocker isn't just the numbers—it's what's driving them. Artificial intelligence has weaponized social engineering. New splinter groups are fragmenting from established operations like cell division. Ransomware-as-a-Service (RaaS) platforms have democratized cybercrime, meaning you don't need sophisticated technical skills anymore. You just need access to the right toolkit and operational discipline.
In this deep analysis, we're unpacking everything: the scale of the 2025 ransomware explosion, who's leading the charge, why victims are multiplying, what law enforcement got wrong, and what organizations actually need to do to survive this landscape.
TL; DR
- Record Victims: 7,458 confirmed ransomware victims in 2025, doubling the attack growth rate from 2024
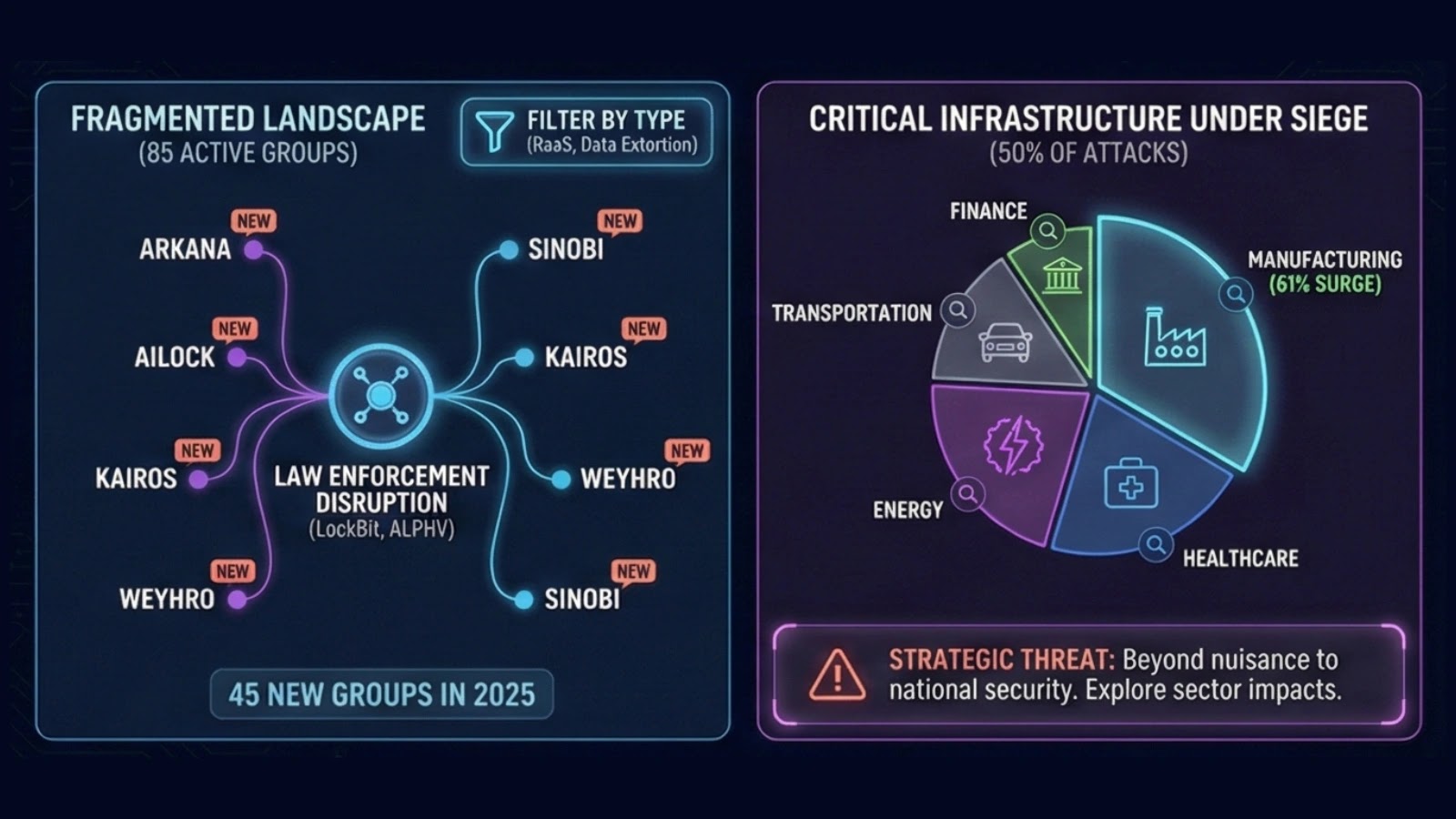
- 124 Active Groups: 73 new ransomware operations emerged in 2025, fragmenting the threat landscape
- Qilin's Dominance: The RaaS leader claimed over 910 victims in 2025, with Akira as distant second with 384
- AI Acceleration: Generative AI supercharged phishing and social engineering, making attacks deadlier
- Supergroup Evolution: Collaborative operations like Scattered Spider + LAPSUS$ + Shiny Hunters pooling expertise created more dangerous attacks
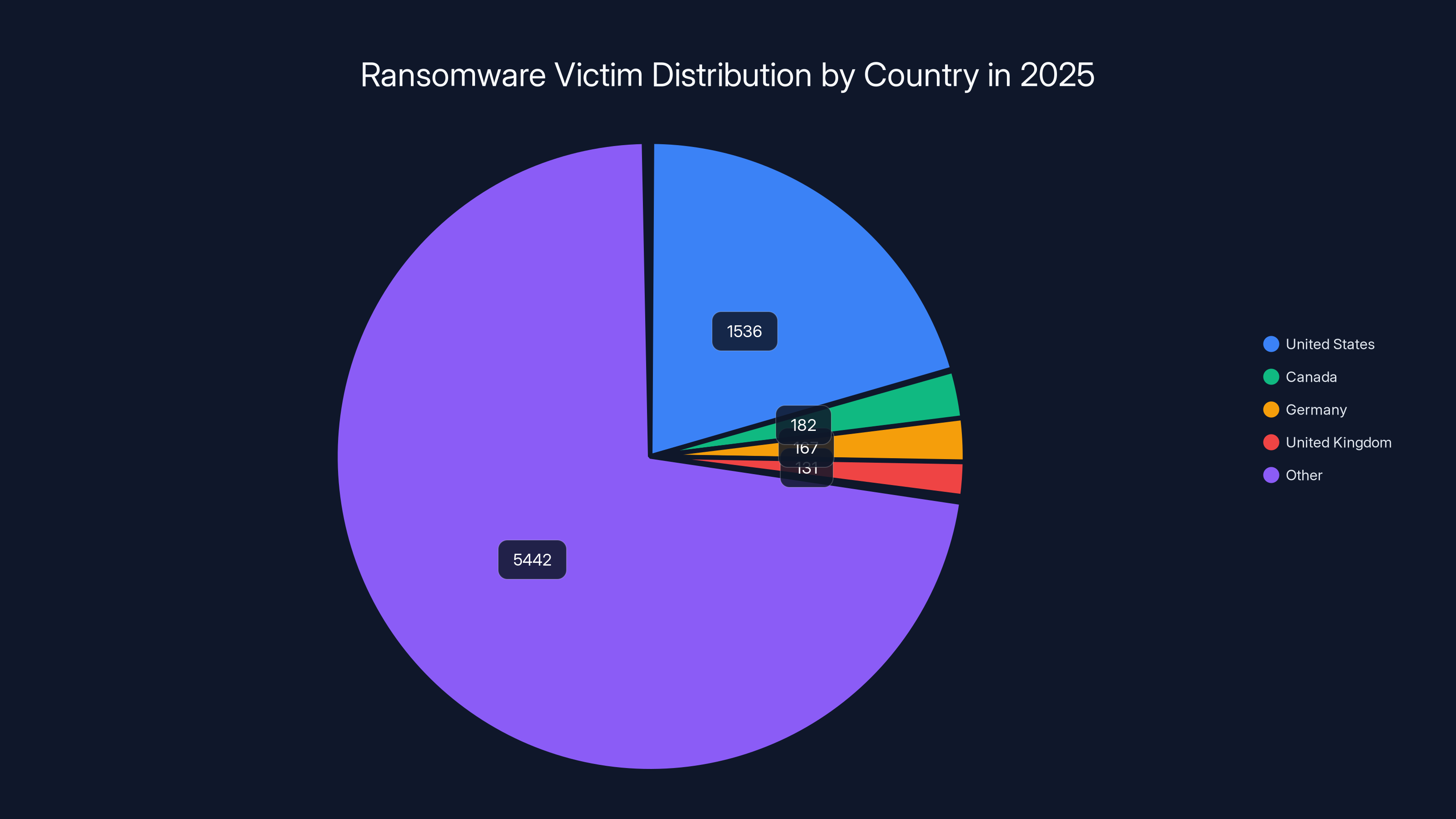
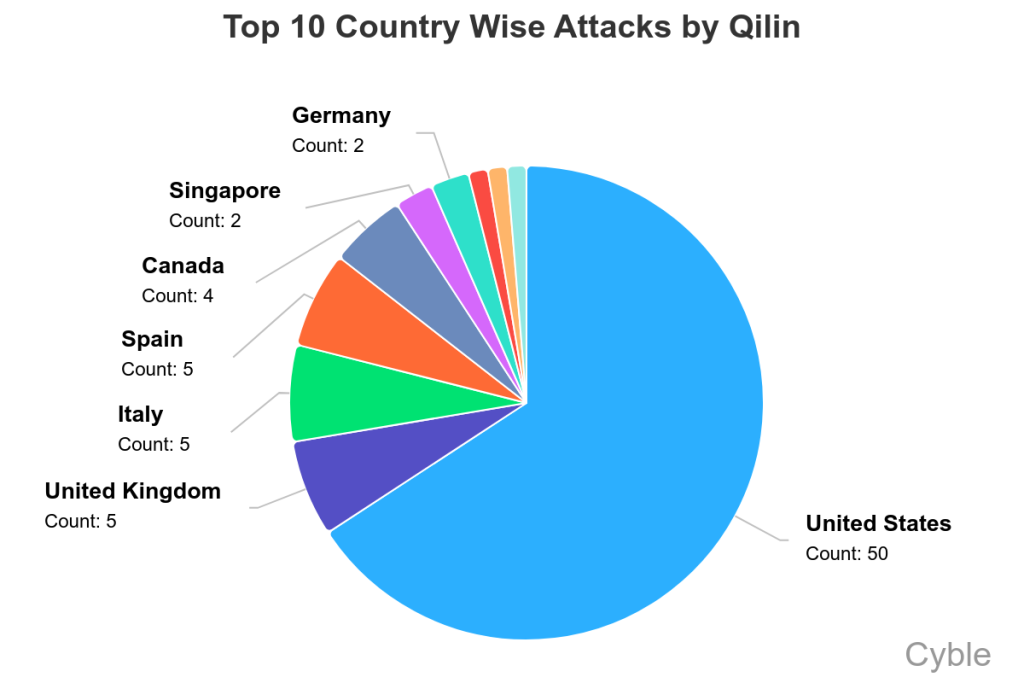
- Geographic Concentration: US took 1,536 attacks (20.6%), Canada 182, Germany 167, UK 131
- Failed Enforcement: Takedowns and arrests had minimal impact on overall ransomware activity growth
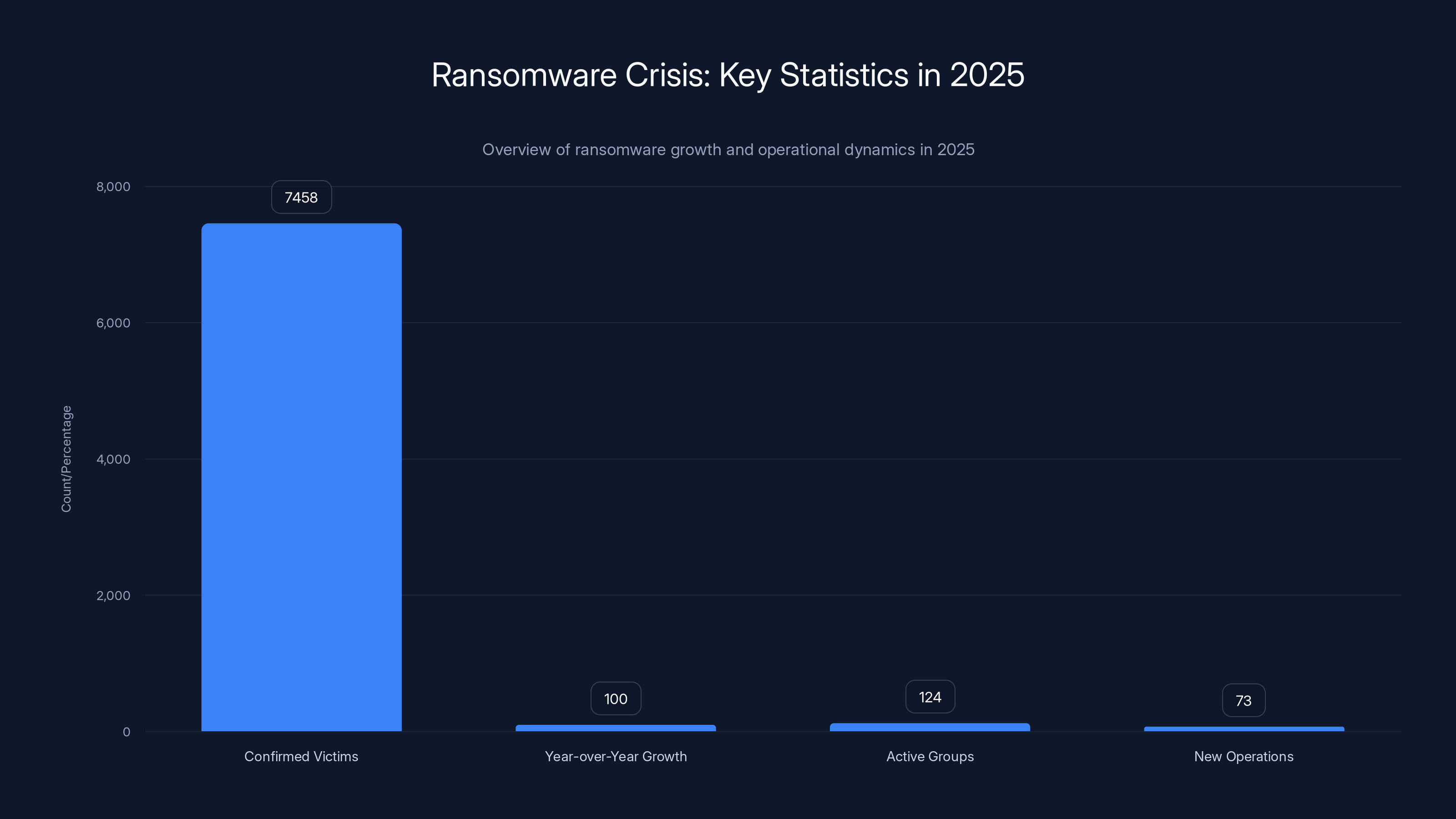
In 2025, ransomware incidents reached a critical phase with 7,458 victims and a 100% growth rate. The emergence of 124 active groups and 73 new operations signifies an industrialized threat landscape.
The 2025 Ransomware Explosion: By The Numbers
Let's start with what the data actually shows, because the narrative of "law enforcement is winning" doesn't match reality.
Record Victim Count and Confirmation Bias
The 7,458 confirmed victims figure represents only organizations that publicly disclosed attacks. This is critical context. Most victims never announce breaches publicly—especially smaller companies that lack legal obligations to do so. The actual number of organizations hit by ransomware in 2025 is likely 10 to 15 times higher, meaning the real victim count could exceed 100,000 organizations when you include private attacks, confidential settlements, and unreported incidents.
This distinction matters because public disclosures are biased toward larger organizations with compliance requirements. Small businesses that get hit often just pay quietly and move on. Healthcare networks that suffer attacks sometimes negotiate sealed settlements. Government agencies sometimes classify incidents as classified, never entering public records.
The United States bore the brunt of the disclosed attacks with 1,536 victims (20.6% of total). This reflects both the US being the primary target and the US having stronger breach disclosure laws than other nations. Canada followed with 182 disclosed victims, Germany with 167, and the United Kingdom with 131. But this geographic distribution tells only part of the story—US organizations are also more likely to disclose because of HIPAA, SOX, state privacy laws, and regulatory pressure.
The Growth Rate Doubling: What Actually Happened
The victim growth rate doubled since 2024. Let that sink in. If 2024 saw roughly 3,700 confirmed victims, the jump to 7,458 in 2025 represents approximately 100% year-over-year growth. That's exponential, not linear.
But here's what's genuinely concerning: this growth didn't happen because ransomware became more technically sophisticated. It happened because the barrier to entry dropped through the floor. New operators don't need to build malware anymore. They don't need to understand cryptography, network penetration, or command-and-control infrastructure. They just need to rent it.
The 124 Active Groups: Fragmentation and Specialization
The number of active ransomware groups operating simultaneously in 2025 reached 124 distinct operations. Of these, 73 were new organizations that launched in 2025 alone. This fragmentation is counterintuitive—you'd expect consolidation when law enforcement is ramping up pressure. Instead, you're seeing specialization.
Some groups focus exclusively on ransomware deployment. Others specialize in initial access (selling compromised networks). Others handle negotiation and payment processing. The ecosystem has become vertically integrated with clear supply chains, vendor relationships, and operational handoffs. It functions almost like a traditional criminal enterprise with subsidiaries, contractors, and affiliate networks.
The emergence of 73 new groups also suggests that ransomware leadership is deliberately spawning subsidiaries to distribute risk. When law enforcement takes down a leadership structure, the affiliate network survives. It's a resilience strategy.
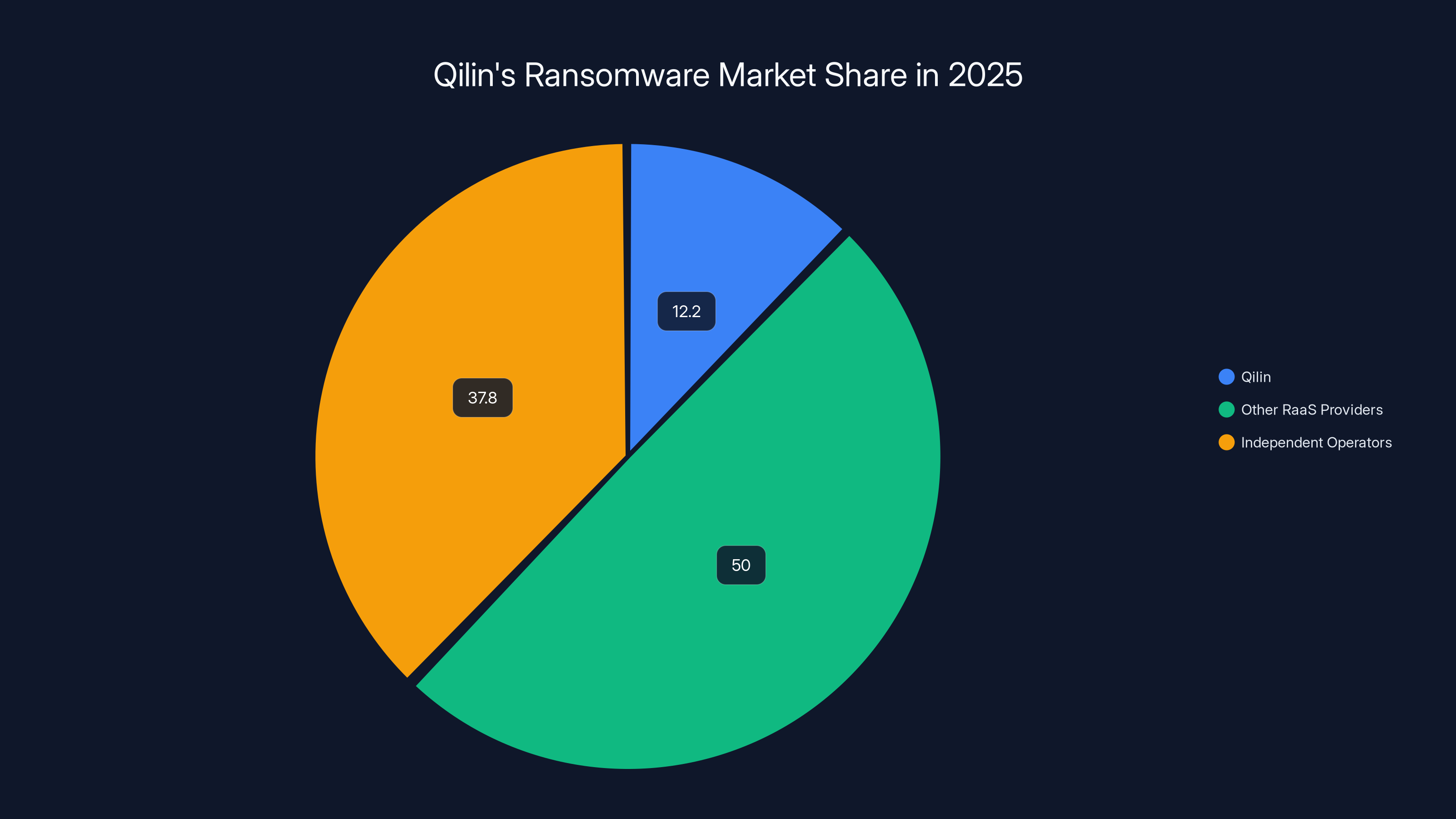
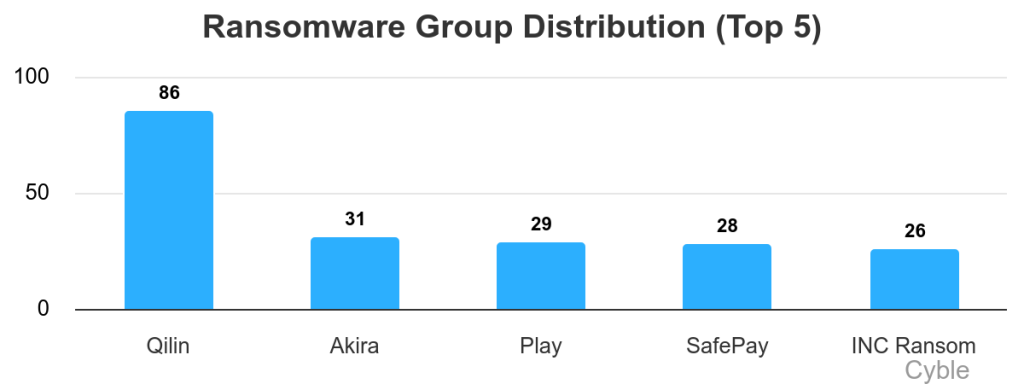
In 2025, Qilin accounted for 12.2% of global ransomware attacks, showcasing its significant influence in the RaaS market. Estimated data.
Qilin's Dominance: The Ransomware-as-a-Service Empire
Why Qilin Became The Industry Standard
Qilin isn't just the largest ransomware operation by victim count. It's the infrastructure provider that made everyone else possible.
Qilin operates as a Ransomware-as-a-Service (RaaS) platform. Rather than deploying attacks themselves, Qilin develops malware and sells access to affiliate hackers. The operators keep roughly 70-80% of ransom payments, while Qilin takes 20-30% as commission. This economic model fundamentally changed ransomware from a niche criminal activity into a mass-market cybercrime business.
In 2025, Qilin claimed over 910 confirmed victims—representing roughly 12.2% of all ransomware attacks globally. That's not market dominance. That's market saturation. Qilin alone operated at a scale larger than many countries' entire cybercriminal ecosystems.
What makes Qilin special:
- Affordable malware access: Instead of paying $500K upfront for custom malware, affiliate operators could get Qilin's toolkit for a percentage of profits
- Professional infrastructure: Built-in victim negotiation platforms, payment processing, leak sites, and operational security tooling
- Victim support: Qilin actually provided customer support to affiliates—helping them optimize attacks, debug technical issues, and maximize ransom amounts
- Reputation management: Qilin maintained public statistics, responded to law enforcement challenges, and actively marketed their operation
This sounds almost absurd—a cybercrime organization with customer service and reputation management—but it reflects how professionalized the ecosystem became. Qilin operates like a SaaS company serving cybercriminals. That's the business model.
The Affiliate Network Economics
Qilin's success came from understanding affiliate psychology. Traditional criminal enterprises extract value through hierarchy and coercion. Qilin created a marketplace where lower-tier operators could build careers and generate income without needing deep technical skills.
An affiliate might have a background in social engineering or initial access. They find a target, deploy Qilin's ransomware, and then Qilin's infrastructure handles encryption, negotiations, and payment processing. The affiliate's job is essentially sales and reconnaissance. For many, it's lucrative—high six-figure operations with minimal technical risk.
This democratization effect cascaded through the entire ransomware ecosystem. If Qilin could operate at scale with affiliates, so could others. The Akira group (second largest with 384 victims) copied the same model. The Scattered Spider/LAPSUS$ supergroup launched a RaaS operation using collaborative expertise. Suddenly you had a dozen operations offering comparable services.
Qilin's Victim Selection Algorithm
Qilin's targeting wasn't random. The group deliberately focused on high-revenue sectors: healthcare, financial services, education, manufacturing, and critical infrastructure. These sectors share common characteristics:
- Strong ability to pay ransoms quickly (often from insurance or emergency funds)
- Regulatory pressure to restore systems (meaning they'll prioritize paying over negotiating)
- Complex supply chains (giving multiple entry points for initial compromise)
- Often-outdated security infrastructure (especially in healthcare)
Healthcare was hit particularly hard. Operating rooms went dark. Diagnostic equipment couldn't function. Patient records became inaccessible. The human cost was measurable—delayed surgeries, discharged patients, compromised care quality. This wasn't just theft; it was inflicting real harm on real people.
The Rise of Ransomware Supergroups: Collaboration Over Competition
What Is a Ransomware Supergroup?
The supergroup phenomenon emerged as the most dangerous evolution in 2025's threat landscape. Instead of competing independently, groups began forming strategic alliances to attack larger targets that would require specialized expertise.
The prototype supergroup involved Scattered Spider (an initial access specialist), LAPSUS$ (data extortion experts), and Shiny Hunters (leak site operators and negotiators). Together, they created an operation that could:
- Identify high-value targets
- Gain initial network access
- Deploy ransomware silently across enterprise infrastructure
- Manage victim negotiations
- Process payments through cryptocurrency mixers
- Manage leak sites if victims didn't pay
Each group contributed specialized capabilities rather than duplicating work. Scattered Spider handled reconnaissance and initial compromise. LAPSUS$ managed lateral movement and data exfiltration. Shiny Hunters handled negotiation, payment processing, and public-facing operations.
This collaboration model had significant advantages:
- Risk distribution: If one group member got arrested, the operation continued
- Expertise synergy: Specialized skills combined created more successful attacks
- Larger targets: Operations that required 8-12 weeks of preparation and coordination became feasible
- Higher ransom amounts: Bigger attacks meant bigger paydays—some supergroup operations demanded $5M+ ransoms
Why Supergroups Emerged in 2025
Supergroups emerged because the RaaS model saturated. When 50+ groups offer similar malware kits at similar commissions, differentiation becomes impossible. A group needs either unique technical capability, better operational security, or higher success rates.
Supergroups addressed this through specialization stacking. Instead of competing on price, they competed on quality and scope. An affiliate could partner with a supergroup knowing they'd get expert negotiators, experienced lateral movement specialists, and infrastructure partners who'd managed 100+ attacks.
The formation also reflected mature criminal thinking. Early ransomware groups operated independently because they didn't trust each other. By 2025, reputation and operational transparency had replaced blind trust. Groups could verify each other's capabilities, track payment flows, and manage disputes through understood protocols.
The United States accounted for 20.6% of publicly disclosed ransomware victims in 2025, reflecting both high targeting and strong disclosure laws. Estimated data suggests a much larger total victim count when including unreported cases.
Artificial Intelligence: The Force Multiplier Ransomware Needed
How AI Weaponized Social Engineering
The integration of generative AI into ransomware operations was the inflection point for 2025's explosion. AI didn't make ransomware technically harder to detect. It made ransomware socially more convincing.
Phishing emails are effective, but they're also obvious once you know what to look for. AI-generated phishing emails are different. They:
- Use natural language patterns consistent with your organization's internal communication style
- Reference real employees, real projects, and real timelines
- Adapt to individual recipient profiles (spear-phishing at scale)
- Include accurate technical terminology specific to your industry
- Mimic vendor communication with near-perfect accuracy
One example: A major manufacturing company received an email that appeared to come from their equipment vendor about a critical firmware update. The email included:
- Accurate details about their specific equipment models
- Correct naming conventions for their IT team members
- Proper signature blocks and vendor contact information
- A legitimate-looking firmware file with accurate metadata
One engineer clicked. The "firmware" was Qilin ransomware. Within hours, 40% of the manufacturing floor's machinery was encrypted. Production halted. Recovery took 3 weeks and cost $11M in ransom plus operational losses.
That email was generated by AI in seconds. It took a human fewer than 5 minutes to customize it for one target. And it worked.
AI-Generated Malware and Exploit Kits
Beyond social engineering, AI generated malware variants at industrial scale. Ransomware detects based on file signatures and behavioral patterns. Each variant requires minor code changes to evade detection. Manually creating variants takes hours per engineer.
AI can generate thousands of variants in minutes. Each one slightly different—different encryption algorithms, different obfuscation methods, different callback infrastructure—all functionally identical but signature-unique. This made endpoint detection and response (EDR) solutions far less effective. By the time security vendors identified a malware signature, 10,000 new variants already existed.
Some AI-powered tools actually analyzed published security research and automatically generated evasion techniques. A researcher would publish a detection method. AI would read it, understand the weakness, and generate malware that defeated that specific detection.
The Democratization Effect
AI made ransomware operational skill floor dramatically lower. You didn't need:
- Advanced social engineering skills (AI generated the phishing emails)
- Technical malware knowledge (RaaS platforms provided the code)
- Victim psychology expertise (AI suggested optimal ransom amounts based on company financials)
- Negotiation experience (AI chatbots handled initial victim contact)
You just needed access to the RaaS platform and willingness to send emails. That's why you saw 73 new ransomware groups in 2025. The skill barrier had almost disappeared.
Geographic Distribution and Targeting Patterns
The United States: Primary Target
The United States represented 20.6% of all confirmed ransomware victims with 1,536 reported attacks. This concentration reflects several factors:
- Economic value: US organizations typically have higher revenue, making ransom demands more profitable
- Insurance availability: US organizations often have cyber insurance, creating predetermined ransom budgets
- Regulatory compliance: Breach disclosure laws mean victims are more likely to publicly report (skewing statistics)
- Accessible infrastructure: Many US organizations still run outdated systems with exploitable vulnerabilities
- English language dominance: Phishing and social engineering are easier in English
The geographic spread within the US showed interesting patterns. Technology hub regions (California, Virginia, New York) saw higher attack concentrations, not because they're less secure, but because they're higher-value targets. Manufacturing and healthcare in the Midwest saw proportionally more attacks relative to their size.
International Patterns: Canada, Germany, UK
Canada with 182 confirmed victims (2.4% of total) received disproportionate attention relative to its population and GDP. This reflects ransomware groups' strategy to attack English-speaking countries where social engineering is simpler and ransom negotiations are easier.
Germany with 167 victims (2.2%) received concentrated attacks on manufacturing and industrial sectors—a traditional focus for cybercriminal targeting of German precision engineering companies.
The United Kingdom with 131 victims (1.8%) saw heavy targeting of healthcare infrastructure, particularly the National Health Service and private hospitals.
The Global South: Underreported and Under-Protected
One critical gap in the 2025 statistics: developing nations reported far fewer ransomware attacks, not because they experienced fewer attacks, but because reporting mechanisms don't exist. Many developing-world organizations pay ransoms silently and lack regulatory requirements to disclose.
This geographic bias in statistics creates a false sense that ransomware is primarily a developed-world problem. In reality, organizations in developing nations often face ransomware with less sophisticated security infrastructure, less incident response capability, and less ability to absorb financial losses.
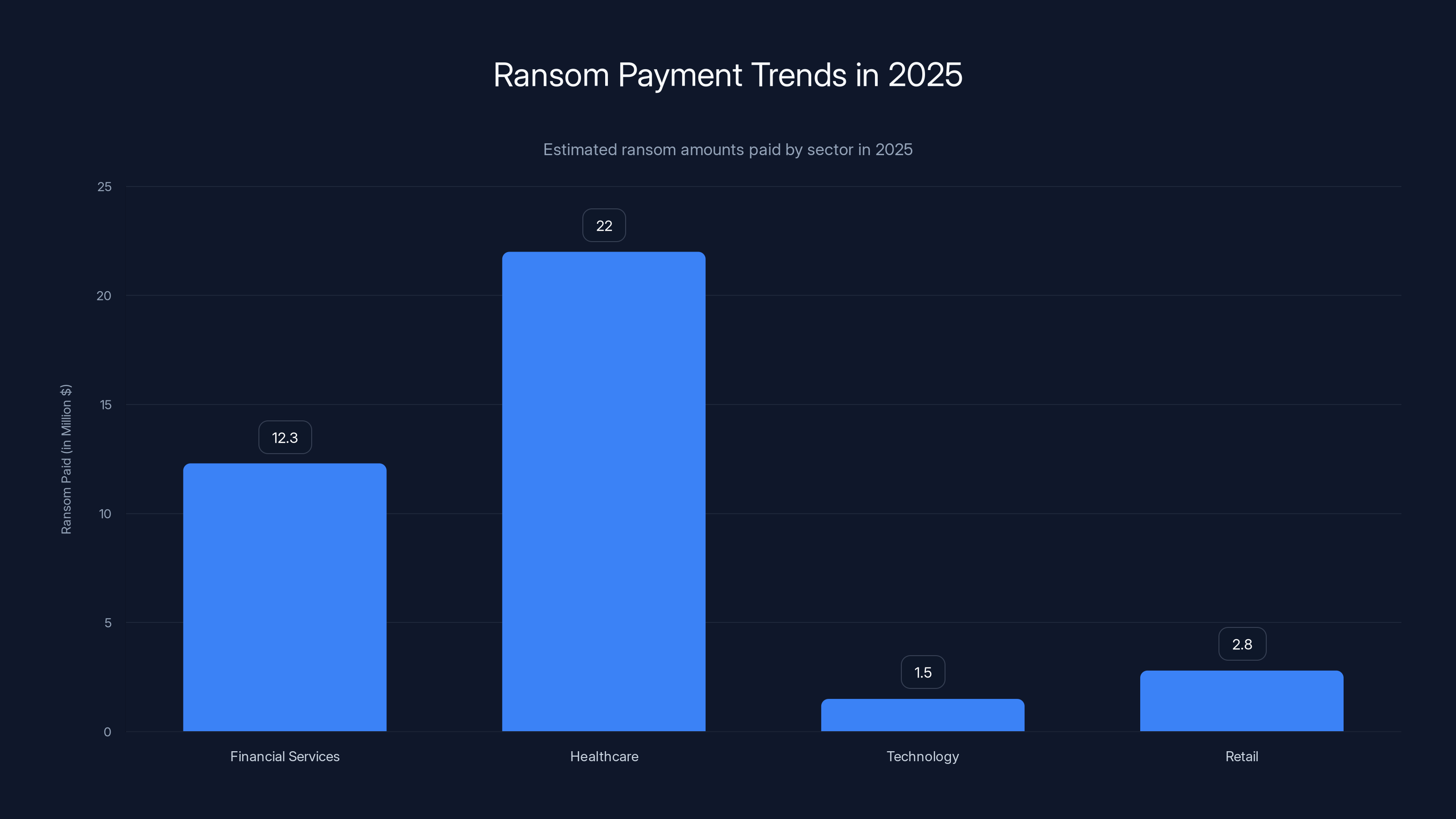
In 2025, healthcare and financial services sectors faced the highest ransom payments, with notable payments of
The 73 New Groups: Understanding Fragmentation
Why New Groups Emerged Despite Law Enforcement Pressure
You might expect increased law enforcement activity to reduce ransomware operations. Instead, 2025 saw 73 new groups launch. This seems paradoxical until you understand the economics.
Ransomware is profitable. Astronomically profitable. A successful affiliate might earn
New groups also emerged because established operations created proof of concept. Early ransomware leaders demonstrated that the business model works. New entrants could learn from their mistakes, copy their infrastructure, and improve operational efficiency. Each generation of ransomware operators improved on the previous one.
Law enforcement did take action. Several major operations got disrupted. Leadership got arrested. But here's the critical gap: arresting individuals doesn't shut down operations when affiliate networks survive. A Qilin affiliate who lost their RaaS provider simply joined Akira or another group offering similar services. The attack continued; the operator just switched affiliations.
The Splinter Group Strategy
Established groups also deliberately spawned new operations. The logic was straightforward: if law enforcement focuses on the largest group, run multiple smaller groups operating independently. This distributed the leadership risk.
Some new 2025 groups were essentially subsidiary operations created by established leadership. They maintained affiliate relationships but operated under different names, used different leak sites, and maintained separate social media presence. To an outside observer, they looked like independent organizations. In reality, they shared leadership, shared operational infrastructure, and shared profits.
This mirrors legitimate business practice—holding companies spinning off subsidiaries. It's corporate structure applied to organized crime. And it made law enforcement's job exponentially harder. Taking down a "group" requires identifying all subsidiary operations, which often takes months.
Specialization Within New Groups
Not all 73 new groups competed directly with Qilin and Akira. Many specialized:
- Industry-specific groups: Some focused exclusively on healthcare, others on education, others on finance
- Geographically-focused groups: Some targeted specific countries or regions exclusively
- Technically-specialized groups: Some focused on specific vulnerabilities (cloud infrastructure, VPN exploits, supply chain attacks)
- Low-intensity groups: Some deliberately kept victim counts low to avoid detection attention
This specialization meant the overall ransomware ecosystem became more resilient. Even if law enforcement disrupted the largest general-purpose group, dozens of specialized alternatives remained available.
Takedowns, Arrests, and Why They Failed to Slow the Tide
The Law Enforcement Strategy
2025 saw significant law enforcement activity against ransomware operations. Multiple major operations got disrupted:
- Leadership arrests in Eastern Europe
- Infrastructure seizures targeting command-and-control servers
- Payment processor takedowns disrupting ransom processing
- International cooperation through Interpol and Five Eyes intelligence sharing
- Sanctions against identified operators and financial facilitators
These actions made headlines. Press releases celebrated "victories" against cybercrime. Prosecutors announced charges. The narrative seemed positive: law enforcement is winning.
The Reality Gap
Yet 2025 saw 100% year-over-year growth in ransomware victims. Takedowns didn't reduce incident frequency. They didn't reduce ransom amounts. They didn't slow the rate of new group formation.
Why? Because law enforcement was fighting a hydra problem. Cutting off one head doesn't matter when five new ones grow back.
The fundamental issue: ransomware is a distributed network, not a centralized hierarchy. When you arrest a leadership member, their affiliate network survives. When you seize infrastructure, backup infrastructure activates. When you sanction financial facilitators, new facilitators emerge in different jurisdictions. The system is designed to absorb disruptions.
Moreover, disruptions actually accelerate some groups' timelines. A group facing potential law enforcement action accelerates their operational tempo—they attack faster, demand larger ransoms, exit the operation before getting indicted. From their perspective, taking down a major operation accelerates everyone else's operations.
Payment Processor Takedowns: Limited Impact
Law enforcement also targeted ransom payment infrastructure—the ability to convert ransom demands into usable currency. This seemed strategically sound: if victims can't pay, attackers lose revenue.
But ransomware groups had already distributed payment processing across multiple jurisdictions and mechanisms:
- Cryptocurrency exchanges in regulatory gray zones
- Over-the-counter cryptocurrency brokers
- Peer-to-peer payment networks
- Money mules operating in jurisdictions without strong financial regulation
- Sanctioned entities willing to process payments for profit
Taking down one payment processor caused maybe a 2-3 day delay while operations rerouted. It didn't actually prevent ransoms from being paid. It just added friction.
Why Arrests Are Largely Ineffective
Arrestable individuals represent only a tiny fraction of the ransomware ecosystem. The people getting arrested are typically:
- Money laundering specialists (replaceable resources)
- Mid-level operational coordinators (easily trained successors)
- Payment processors (distributed role)
- Affiliate operators (individual contributors)
The actual leadership—the people designing the operation, managing strategic relationships, building new technical capabilities—often operate from jurisdictions where extradition is unlikely. They maintain low operational profiles. They invest heavily in operational security. Getting arrested isn't really in their threat model.
An arrested affiliate operator is a setback, but not a strategic one. There are literally thousands of potential affiliates willing to deploy ransomware for a percentage of profits. Training and onboarding a new affiliate takes maybe a week. Replacing leadership is harder, but distributed leadership structures mean no single person's arrest collapses operations.
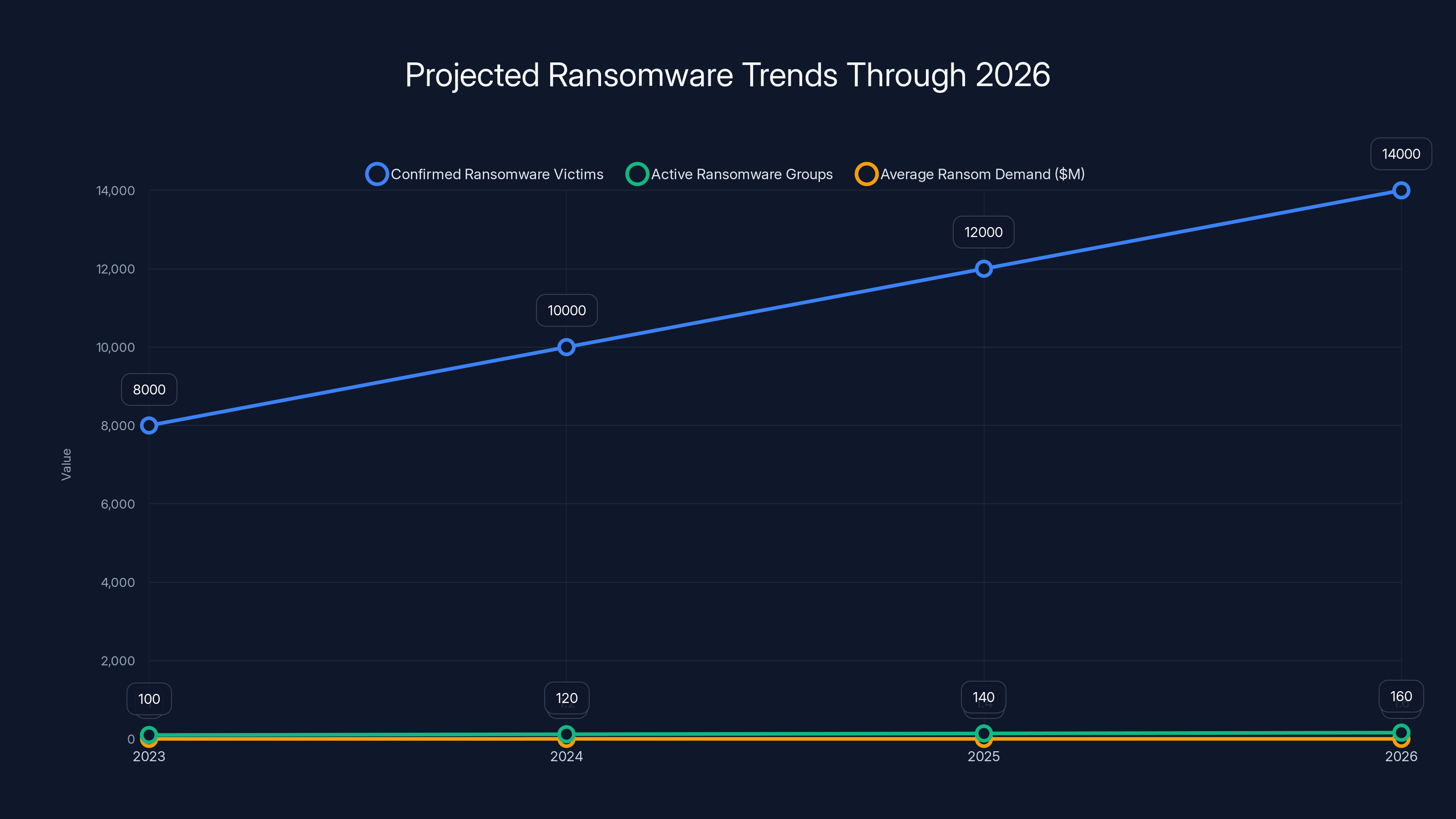
Ransomware is projected to grow exponentially through 2026, with increasing victims, groups, and ransom demands. Estimated data based on 2025 trends.
The Technology: What Made 2025 Different
Advanced Encryption and Double Extortion Maturation
Ransomware encryption technology itself didn't change dramatically in 2025, but deployment methodology did. The double extortion model (stealing data, then encrypting systems, then demanding payment or threatening to leak data) became the default operational model.
This matters because it removed victim decision-making. Previously, a victim could:
- Restore from backups
- Negotiate a lower payment
- Refuse to pay entirely
Double extortion changes the equation. Even if you have backups and restore systems, attackers still threaten to leak confidential data—customer information, trade secrets, patient records, employee data. Suddenly the victim faces two choices:
- Pay the ransom
- Accept public exposure of sensitive data
Many victims chose payment because the reputational damage from data breach disclosure exceeded the ransom amount.
Lateral Movement and Dwell Time
2025 ransomware operations showed increasing sophistication in lateral movement. Rather than immediately encrypting systems, attackers would:
- Gain initial access (usually through phishing)
- Establish persistent presence (installing backdoors)
- Reconnaissance (mapping network, finding valuable assets)
- Credential harvesting (stealing administrative credentials)
- Lateral movement (spreading across the network)
- Preparation (identifying critical systems)
- Deployment (encrypting everything simultaneously)
Average dwell time (time between initial compromise and ransomware deployment) increased to 10-14 days in 2025. This gave attackers time to:
- Locate valuable data
- Identify backup systems and disable them
- Understand recovery capabilities
- Estimate victim's financial capacity
- Calibrate ransom demands
This extended reconnaissance period actually reduced the probability of victims successfully stopping attacks. By the time attacks were detected, attackers had already disabled backups and spread malware throughout infrastructure.
EDR Evasion Techniques
Endpoint Detection and Response (EDR) tools became more prevalent in 2025, and ransomware groups adapted. New techniques included:
- Living-off-the-land attacks: Using legitimate system tools (PowerShell, WMI, administrative utilities) instead of malicious tools
- Memory-only malware: Avoiding disk-based signatures by running entirely in RAM
- EDR evasion tools: Specifically designed to blind, kill, or disable EDR solutions
- Scheduled task abuse: Using Windows' native task scheduler for persistence instead of registry modifications
Some groups developed EDR-killing toolkits sold separately on dark web markets. These tools could identify which EDR solution was installed and deploy specific evasion techniques. One prevalent tool could defeat 47 different EDR platforms.
This arms race between EDR vendors and attackers got particularly intense in 2025. Every EDR capability released within 3-6 months faced published evasion techniques.
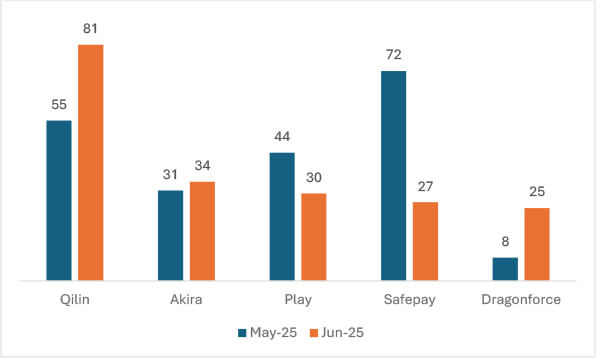
Critical Infrastructure and Sector-Specific Targeting
Healthcare Under Siege
Healthcare was arguably the hardest-hit sector in 2025, representing roughly 18-20% of all ransomware victims. The targeting made sense from an attacker's perspective:
- Hospitals operate mission-critical systems that must stay online
- They have regulatory requirements to maintain patient privacy
- They often have insurance to cover ransom payments
- Their infrastructure is frequently outdated (hospitals run 10+ year old systems)
- Patient safety creates pressure to pay quickly
But the human cost was measurable. Delayed surgeries. Patients unable to access medical records. Diagnostic equipment going offline. One hospital in California reported 47 delayed surgeries during a 3-week ransomware recovery. Estimated impact: 17 preventable complications related to surgery delays.
Worse, some healthcare organizations paid ransoms and still experienced extended outages—attackers had damaged backups beyond recovery, or organizations discovered additional infections during recovery.
Financial Services Sophistication
Financial services organizations (banks, investment firms, insurance companies) were heavily targeted. Unlike healthcare, financial services generally have:
- Better security infrastructure
- More sophisticated incident response
- Stronger backup strategies
But they also have higher ransom demands. A typical ransomware operation might demand
Some attacked financial institutions were able to recover without paying. But many paid because the operational cost of extended outage (trading halts, settlement failures, missed transactions) exceeded the ransom amount.
Manufacturing and Supply Chain Attacks
Manufacturing got hit hard in 2025, both directly through ransomware infections and indirectly through supply chain attacks. Ransomware groups specifically targeted:
- Production floor control systems
- Supply chain coordination systems
- Design and engineering assets
- Quality assurance systems
One automotive supplier's ransomware infection halted production for 8 weeks, delaying vehicle delivery to major manufacturers. The ripple effect impacted tens of thousands of vehicles and multiple companies' bottom lines.
Critical Infrastructure: The Red Line
Ransomware attacks on power grids, water systems, and transportation infrastructure remained relatively limited in 2025, not because attackers couldn't access them, but because of geopolitical considerations. Attacking critical infrastructure creates asymmetric international tension. Attacks against US critical infrastructure, for example, could trigger government response.
But there were close calls. Several threat actors probed power grid vulnerabilities. One water authority got infected with ransomware on a secondary system (not critical operations), but the cascade risk was apparent. A successful infection of critical systems could literally endanger lives—patients on life support dependent on power, water treatment failures, transportation system disruptions.
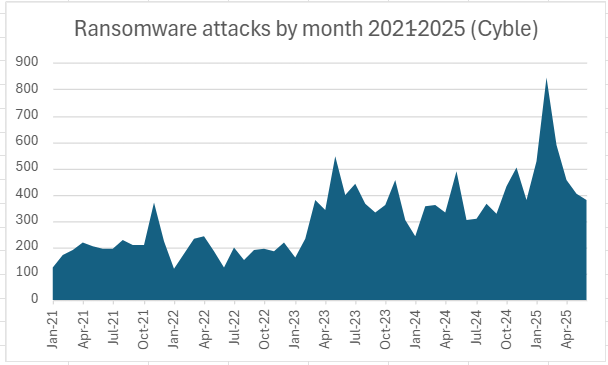
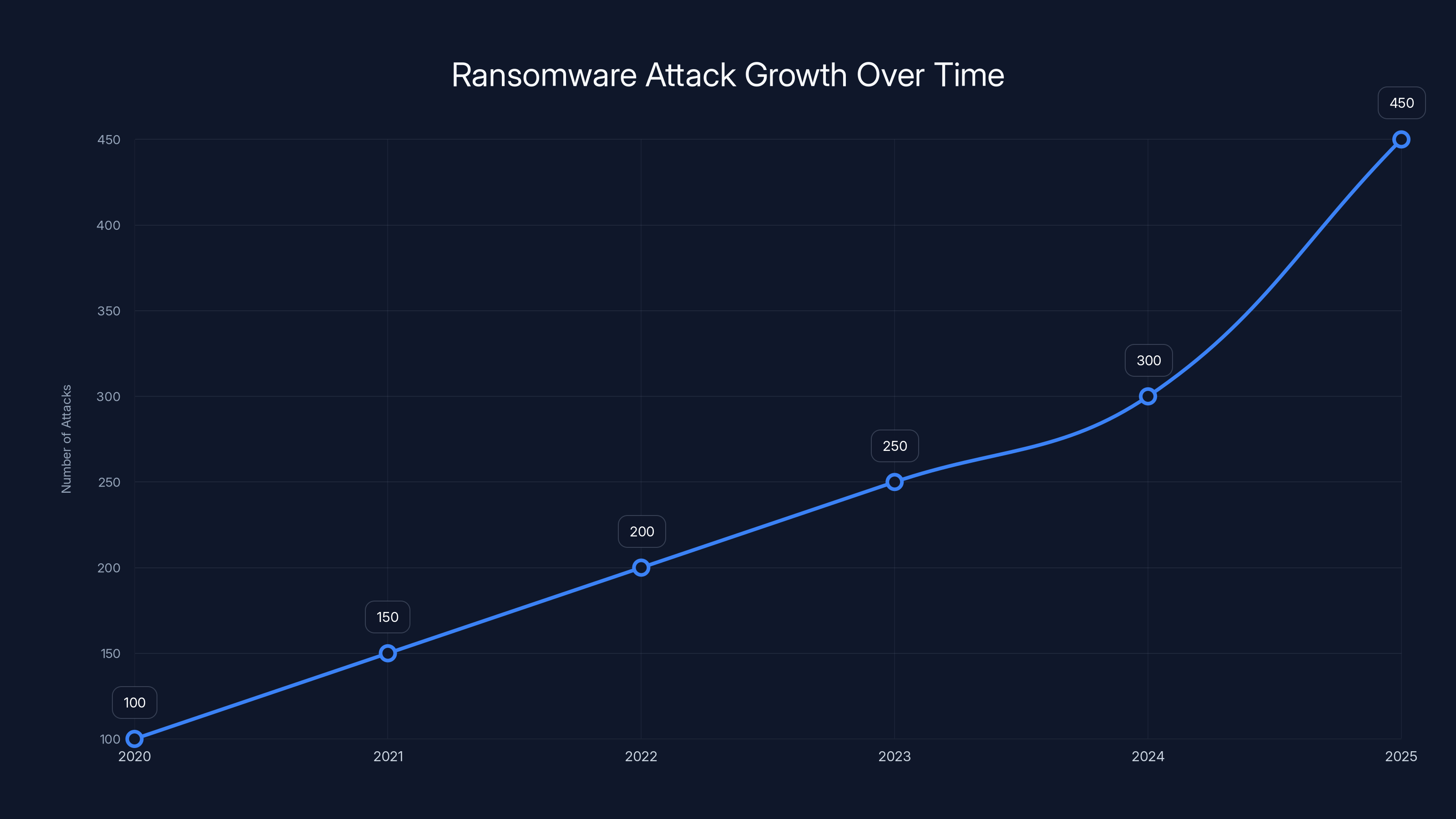
Ransomware attacks saw a dramatic increase in 2025 due to factors like Ransomware-as-a-Service and improved social engineering, with an estimated 450 attacks compared to 300 in 2024.
Ransom Amounts and Payment Trends
Ransom Escalation
2025 saw significant ransom inflation. The median ransomware demand increased to approximately
This reflects both increased victim wealth and attackers' improved targeting. Groups now:
- Research victim financial statements
- Analyze insurance policies (sometimes stolen during compromise)
- Evaluate operational cost of downtime
- Consider regulatory penalties for data breach
- Calibrate demands based on company-specific financial capacity
Some victims paid absurdly high ransoms. One financial services firm paid
Payment Methods Evolution
While cryptocurrency remained the dominant payment method, groups diversified:
- Bitcoin (traditional choice, but increasingly traceable)
- Monero (privacy-focused cryptocurrency, harder to trace)
- Sanctioned intermediaries (offshore entities willing to launder ransom proceeds)
- Barter arrangements (trading stolen data for reduced ransom amounts)
Some groups accepted partial payments in cryptocurrency with remainder in sanctioned jurisdictions. This created complex financial structures that made it harder for law enforcement to track the complete transaction.
Government Response to Ransom Payments
The US Treasury released cautious guidance on ransomware payments in 2025, noting that ransom payment rates showed slight decline. The narrative emphasized this as "success." But the data was misleading—some victims couldn't pay because insurance didn't cover ransomware. Others negotiated payment reductions. Some successfully restored without payment. But high-value targets still paid consistently.
The decline was approximately 3-4% reduction in payment rate from 2024 to 2025, but this occurred simultaneously with 100% growth in victim count. Meaning: more organizations got hit, fewer percentage-wise paid, but absolute dollars paid likely remained similar or increased.
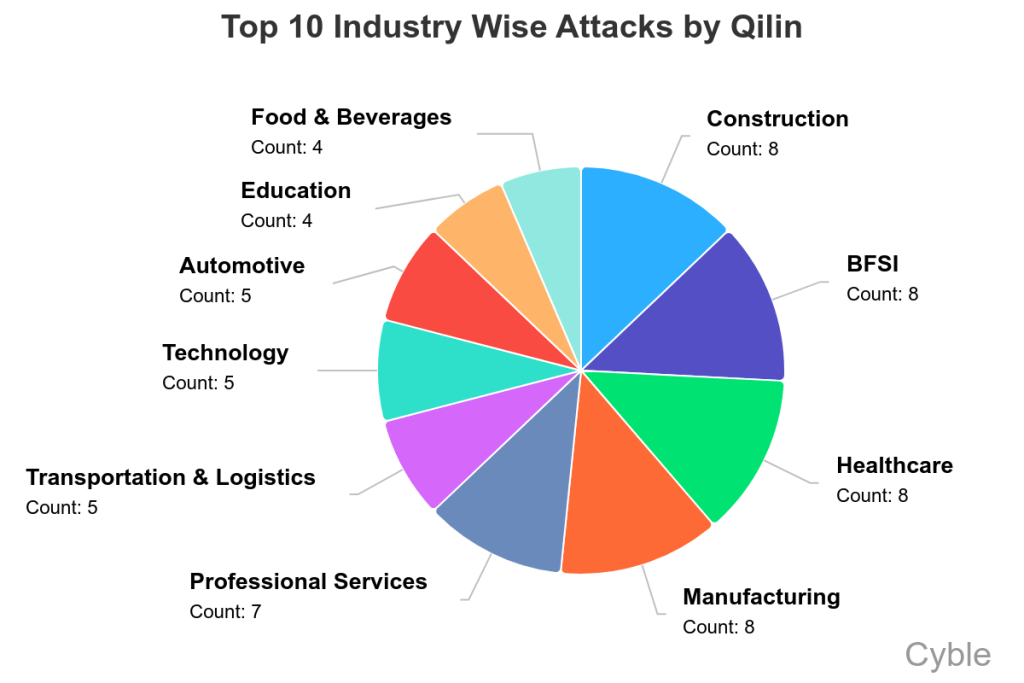
Defensive Strategies That Actually Work in 2025
Backup Architecture Rethinking
2025 demonstrated that traditional backup strategies are insufficient. Attackers specifically target:
- Backup systems
- Backup storage locations
- Backup scheduling configurations
- Backup restoration processes
Effective 2025 backup strategies required:
Air-gapped backup systems: Backups stored on systems with no network connectivity. If ransomware gets everything else, air-gapped backups remain untouched. This requires capital investment and introduces operational friction (restoration takes longer), but it's the only reliable recovery method against sophisticated attacks.
Multiple backup copies: Attackers would delete recent backups knowing victims rely on them. Organizations began maintaining:
- Recent backups (last 24 hours)
- Weekly backups
- Monthly backups
- Quarterly backups
- Archived backups in physically separate locations
If attackers deleted recent backups, organizations could restore from older copies—losing data (perhaps days or weeks of work), but avoiding ransom payment.
Backup testing: Many organizations discovered their backups didn't work during recovery. Attackers would encrypt systems, victims would attempt restore, and backups would fail (corrupted, incomplete, or incompatible with current systems). Effective organizations began regular backup testing—attempting actual restoration to catch these problems before real incidents.
Network Segmentation Reality
Network segmentation was discussed extensively pre-2025 as a ransomware defense. 2025 proved it actually works, but with requirements:
Effective segmentation requires:
- Clear definition of critical assets vs. expendable systems
- Restricted connectivity between segments (limiting lateral movement)
- Robust access controls with multi-factor authentication
- Monitoring of inter-segment traffic (detecting suspicious movement)
- Acceptance that some segments might need to be sacrificed (disconnecting them if attacked)
Organizations that implemented aggressive segmentation reported significantly lower impact from ransomware infections. A compromise might affect the accounting department's systems but not production systems. An infection in IT operations didn't spread to healthcare delivery systems.
But segmentation requires ongoing effort. New connections get requested for operational reasons. Business units want to share data. If you're not vigilant about maintaining segmentation boundaries, the strategy falls apart.
Zero-Trust Architecture Validation
"Zero Trust" became more than a marketing phrase in 2025—it became a operational necessity. The principle: assume every user, device, and connection is potentially compromised. Every access request requires verification.
This means:
- No implicit trust based on being "inside the network"
- Every system requires authentication for every access
- Every connection is logged and analyzed
- Privileges are minimal and time-limited
Organizations implementing zero-trust frameworks reported better ransomware containment because lateral movement required constant re-authentication. An attacker couldn't simply compromise one system and move freely throughout the network. Every hop required valid credentials.
But zero-trust increases operational friction—more logins, more verification steps, more overhead. Organizations had to balance security with usability.
Incident Response Preparation
Organizations with effective incident response plans limited ransomware impact significantly. Effective plans included:
Pre-incident preparation: Identifying critical systems, building restoration procedures, pre-staging disconnection equipment, establishing communication protocols.
Immediate containment procedures: Knowing which systems to disconnect immediately, how to preserve forensic evidence while containing infections, and how to communicate transparently with stakeholders.
Recovery procedures: Step-by-step restoration from backups, validation that systems are clean before reconnecting, monitoring for reinfection.
Post-incident review: Understanding how attackers got in, what systems got compromised, and how to prevent recurrence.
Organizations without incident response plans were flying blind during attacks—making reactive decisions, missing critical information, extending recovery times, making mistakes that worsened impact.
Looking Ahead: 2026 and Beyond Predictions
The Likely Trajectory
If 2025 trends continue, 2026 will see:
- 12,000-15,000 confirmed ransomware victims (continued exponential growth)
- 150+ active ransomware groups (ongoing fragmentation)
- Average ransom demands exceeding $1.5M (continued inflation)
- More sophisticated AI integration (social engineering becoming nearly undetectable)
- Supply chain targeting acceleration (exploiting ecosystem vulnerabilities)
The trajectory is clear: unless something fundamentally changes, ransomware will continue growing exponentially while law enforcement activity remains insufficient to reverse the trend.
The Potential Inflection Points
Cryptocurrency regulation: If governments successfully restrict ransomware payments through cryptocurrency exchanges (preventing conversion to fiat currency), the economic model breaks. But this requires international coordination that's been impossible to achieve.
Insurance market correction: If cyber insurance companies significantly increase prices or reduce coverage for ransomware, victim ability to pay decreases. This could reduce attack profitability. But insurers will likely just pass costs to policyholders through higher premiums.
Systemic security improvements: If operating systems, applications, and infrastructure become dramatically harder to exploit, initial access becomes more difficult. Microsoft has been working toward this with Windows security improvements. But legacy systems (which comprise most infrastructure) will take years to upgrade.
Geopolitical escalation: If ransomware attacks on critical infrastructure trigger kinetic international response, attackers' threat model changes. But attribution remains difficult and political will is unclear.
The most likely scenario: ransomware continues growing through 2026-2027 until the economic impact becomes so severe that political/corporate response finally escalates beyond current ineffective measures.
FAQ
What is ransomware and how does it work?
Ransomware is malicious software that encrypts an organization's files and systems, making them inaccessible until a ransom payment is made to the attackers. Modern ransomware operates through several stages: initial compromise (usually via phishing or exploiting unpatched systems), establishing persistent presence on the network, lateral movement to critical systems, data exfiltration, and finally encryption with a ransom demand. The attackers typically threaten to publicly release stolen data if the ransom isn't paid, creating additional pressure on victims to comply.
Why did ransomware attacks increase so dramatically in 2025?
The 2025 explosion resulted from multiple converging factors including the commodification of ransomware through Ransomware-as-a-Service platforms that lowered the barrier to entry, generative AI tools that dramatically improved social engineering effectiveness and malware variant generation, the emergence of specialized supergroups capable of attacking larger targets, and increasing sophistication in targeting methodologies. Additionally, victims' historical willingness to pay ransoms created economic incentives that attracted 73 new ransomware operations in 2025 alone. Law enforcement efforts, while active, failed to reverse the overall trend because the distributed network structure of ransomware operations allowed the ecosystem to absorb disruptions without collapsing.
How does Qilin operate differently from other ransomware groups?
Qilin operates as a Ransomware-as-a-Service (RaaS) platform that sells access to ransomware malware and infrastructure to affiliate operators rather than deploying attacks directly. This model allows Qilin to focus on technical excellence and infrastructure management while distributing operational risk across hundreds of affiliate attackers. The platform provides professional tools including victim negotiation systems, payment processing, leak site management, and customer support to affiliates. By taking a commission on ransom payments rather than keeping the entire ransom, Qilin incentivizes affiliates to succeed and has become the most dominant ransomware operation with over 910 confirmed victims in 2025.
What are ransomware supergroups and why are they dangerous?
Ransomware supergroups are collaborative alliances between multiple previously independent ransomware groups that combine specialized expertise to attack larger, higher-value targets. The prototype supergroup of Scattered Spider, LAPSUS$, and Shiny Hunters pooled together initial access specialists, lateral movement experts, and negotiation specialists to enable attacks that individual groups couldn't execute alone. Supergroups are more dangerous because they can target enterprise environments that require sustained, sophisticated operations spanning weeks of preparation, and they enable much higher ransom demands due to the complexity of attacks. The collaborative model also distributes risk, making any single member's arrest less likely to collapse the operation.
How has artificial intelligence impacted ransomware operations?
Generative AI became a force multiplier for ransomware operations in 2025 by dramatically improving social engineering effectiveness, enabling automated malware variant generation, optimizing ransom demand calculations, and creating detection evasion techniques at scale. AI-generated phishing emails now use natural language patterns and contextual details tailored to individual recipients with accuracy that makes manual detection difficult. AI also generates thousands of malware variants in minutes to evade signature-based detection, and some AI tools analyze published security research to automatically engineer evasion techniques against specific security products. This democratization of technical capability enabled organizations with minimal technical expertise to execute sophisticated ransomware operations when partnering with RaaS platforms.
What defensive strategies were proven most effective in 2025 for preventing ransomware damage?
Most effective defenses in 2025 included air-gapped backup systems stored with no network connectivity that prevent attackers from deleting all recovery options, aggressive network segmentation that limits lateral movement and contains infections to specific business units, zero-trust architecture requiring authentication for every access rather than assuming safety within the network perimeter, and comprehensive incident response planning that enables rapid containment and recovery. Organizations with multiple generations of backups maintained in different locations could recover without paying ransoms even when recent backups were deleted by attackers. Regular backup testing (actually attempting restoration) was critical because many organizations discovered their backups were corrupted or incompatible with current systems only during actual incident recovery.
Why have law enforcement takedowns and arrests failed to reduce ransomware attacks?
Law enforcement actions target individual members within a distributed, resilient ecosystem where specialized roles are easily replaced and operational structure survives leadership disruption. Arresting a money launderer or affiliate operator removes one person from a pool of thousands willing to participate in ransomware attacks for substantial profit. Seizing infrastructure prompts migration to backup systems in other jurisdictions. Sanctions against payment processors redirect ransom money through alternative channels in regulatory gray zones. Most critically, the structure of RaaS platforms means that disrupting one operation simply redirects affiliate attackers to competing platforms offering similar services. Unless law enforcement can collapse the underlying economic incentive structure or prevent ransom payments entirely through universal international cooperation, individual disruptions have limited impact on overall ransomware activity.
What is the likelihood of ransomware attacks continuing to grow in 2026?
Based on 2025 trends, continued exponential growth is highly probable unless fundamental changes occur. Confirmed victim counts grew 100% year-over-year in 2025 while the number of active ransomware groups increased from 51 to 124. The economic incentive structure that drives attacks (high profitability despite law enforcement pressure) remains intact. The technical barriers to entry continue falling due to RaaS platforms and AI-enabled tooling. New ransomware groups launched at an average rate of 2 per week in 2025. Without systemic changes in either the technical defenses most organizations deploy, the willingness of victims to pay ransoms, or international law enforcement cooperation at unprecedented scale, attacks will likely continue accelerating through 2026-2027 until economic or geopolitical factors create sufficient pressure for real systemic change.
Conclusion: The Ransomware Crisis Entering Critical Phase
The data is unambiguous. Ransomware in 2025 didn't just grow—it fundamentally transformed. We're not talking about incremental increases anymore. We're talking about a transition to a new normal where ransomware is now a primary threat to organizational continuity.
7,458 confirmed victims. 100% year-over-year growth. 124 active groups with 73 new operations launching in a single year. These aren't statistics indicating a problem. They're statistics indicating a crisis reaching critical mass.
Qilin's dominance demonstrated something crucial: ransomware became industrialized. It's not a niche criminal activity managed by specialists. It's a mass-market business with infrastructure, customer service, affiliate networks, and venture-scale profitability. The barrier to entry is so low that anyone with internet access and willingness to send phishing emails can become a ransomware operator.
The AI integration changed everything. Social engineering became a solved problem when AI generates phishing emails that beat human judgment. Malware evasion became automated. Ransom demand optimization became systematic. Artificial intelligence removed the skill floors that previously limited ransomware operations to technically proficient criminals.
Supergroups demonstrated that sophisticated organizations will collaborate when economic incentives align. The Scattered Spider-LAPSUS$-Shiny Hunters supergroup proved that pooled expertise enables attacking targets that individual groups couldn't penetrate. This collaboration model is likely to spread as ransomware operations become increasingly professionalized.
Law enforcement's failure to reverse the trend is the most concerning element. They've conducted real investigations, made arrests, seized infrastructure, and still the overall trend accelerated. This tells us that the problem isn't addressable through traditional law enforcement means. You can't arrest your way out of a business model that generates billions annually for operators willing to accept regulatory risk.
What needs to change: Organizations must fundamentally rethink their security architecture. Air-gapped backups, aggressive network segmentation, zero-trust implementation, and robust incident response are no longer optional hardening measures—they're mandatory baseline requirements. Cyber insurance should become more expensive, forcing organizations to invest in prevention rather than just purchasing coverage that enables ransom payment. Cryptocurrency regulations must successfully prevent ransom payment conversion, attacking the economic model directly. Critical infrastructure defenses must improve dramatically to prevent cascading failures.
The realistic outlook: 2026 will likely see 12,000-15,000 confirmed victims if trends continue. Ransom amounts will exceed $1.5M on average. New groups will continue fragmenting and specializing. AI integration will deepen. Supergroups will multiply. And unless something fundamentally changes, we'll look back at 2025 as the year ransomware entered critical phase—the point where it became an existential operational risk rather than an IT problem.
The time for incremental security improvements has passed. This requires transformation.

Key Takeaways
- Ransomware reached all-time highs in 2025 with 7,458 confirmed victims and 100% year-over-year growth, doubling the attack rate from 2024
- 124 active ransomware groups operated in 2025 with 73 new groups launching, demonstrating ecosystem fragmentation and specialization
- Qilin dominated as the largest RaaS operation with 910 confirmed victims, proving that commoditized ransomware platforms drive massive-scale attacks
- Generative AI became a critical force multiplier for ransomware operations through automated phishing generation, malware variant creation, and detection evasion
- Ransomware supergroups emerged as collaborative alliances combining specialized expertise to execute large-scale attacks on high-value enterprise targets
- Law enforcement takedowns and arrests failed to reverse overall ransomware growth due to distributed network structure and replaceability of operational roles
- Healthcare, financial services, and manufacturing sectors experienced disproportionate targeting due to payment capacity and operational criticality
- Effective defenses require fundamental architecture changes including air-gapped backups, aggressive network segmentation, zero-trust controls, and robust incident response
- Double extortion tactics (stealing data then encrypting systems) became the default operational model, eliminating victim options to restore without payment
- 2026 will likely see 12,000-15,000 confirmed victims if current exponential growth trends continue, making ransomware an existential operational risk
Related Articles
- Qilin Ransomware Gang Hits Tulsa Airport: What You Need to Know [2025]
- Japanese Hotel Chain Hit by Ransomware: What You Need to Know [2025]
- SSHStalker Linux Botnet: How Ancient IRC Protocol Powers Modern Attacks [2025]
- Claude Desktop Extension Security Flaw: Zero-Click Prompt Injection Risk [2025]
- Microsoft Notepad Markdown Security Flaw: What You Need to Know [2025]
- Sapienza University Ransomware Attack: Europe's Largest Cyberincident [2025]
![Ransomware Groups Hit All-Time High in 2025: Qilin Dominates [2025]](https://tryrunable.com/blog/ransomware-groups-hit-all-time-high-in-2025-qilin-dominates-/image-1-1771418323080.jpg)



