Introduction: Old School Meets Modern Threats
If you think botnets are all cutting-edge command-and-control frameworks with encrypted channels and sophisticated evasion techniques, think again. A nasty piece of malware called SSHStalker just proved that sometimes the oldest tricks work best.
We're talking about IRC. Internet Relay Chat. That protocol your uncle probably used to chat on BBS systems back in the 1980s. While everyone's been focused on fancy malware delivery systems and AI-powered threat detection, SSHStalker quietly went back to the future and weaponized technology from 1988.
Here's the kicker: it's working brilliantly.
Researchers recently discovered SSHStalker actively targeting Linux servers across cloud infrastructure, and the campaign is surprisingly sophisticated despite using a dead-simple command infrastructure. The botnet hunts for cloud servers, breaks in through SSH brute-force attacks, plants itself deep into the system using cron jobs that resurrect it every single minute, and then starts making money through cryptomining and AWS credential theft.
What makes this fascinating isn't just that it works. It's why it works. Modern defenders are so focused on detecting contemporary attack methods that they sometimes miss ancient ones staring them in the face. IRC traffic looks innocuous. Cron jobs running every minute? Probably just system maintenance. A compiler downloading and running locally? Common enough in development environments.
SSHStalker exploits these blind spots masterfully. By using old-school methods combined with cloud infrastructure targeting, attackers are hitting companies where they're least prepared to defend. And based on the numbers researchers found, they're hitting thousands of servers per month.
This article digs into exactly how SSHStalker works, why IRC is actually perfect for modern botnet operations, what it's doing on your servers once it gets in, and most importantly, how to keep it out.
TL; DR
- SSHStalker targets cloud servers with automated SSH brute-forcing, breaking into thousands of Linux systems monthly through weak credentials
- IRC protocol powers command-and-control, using 35-year-old technology for bot coordination because it's simple, reliable, and hard to detect at scale
- Persistence via cron jobs ensures infected servers restart the malware every minute, making manual removal nearly impossible without root access
- Monetization through cryptomining and AWS credential harvesting means attackers profit directly from stolen cloud infrastructure capacity
- Prevention requires SSH key authentication, compiler restrictions, and egress filtering to block outbound IRC connections

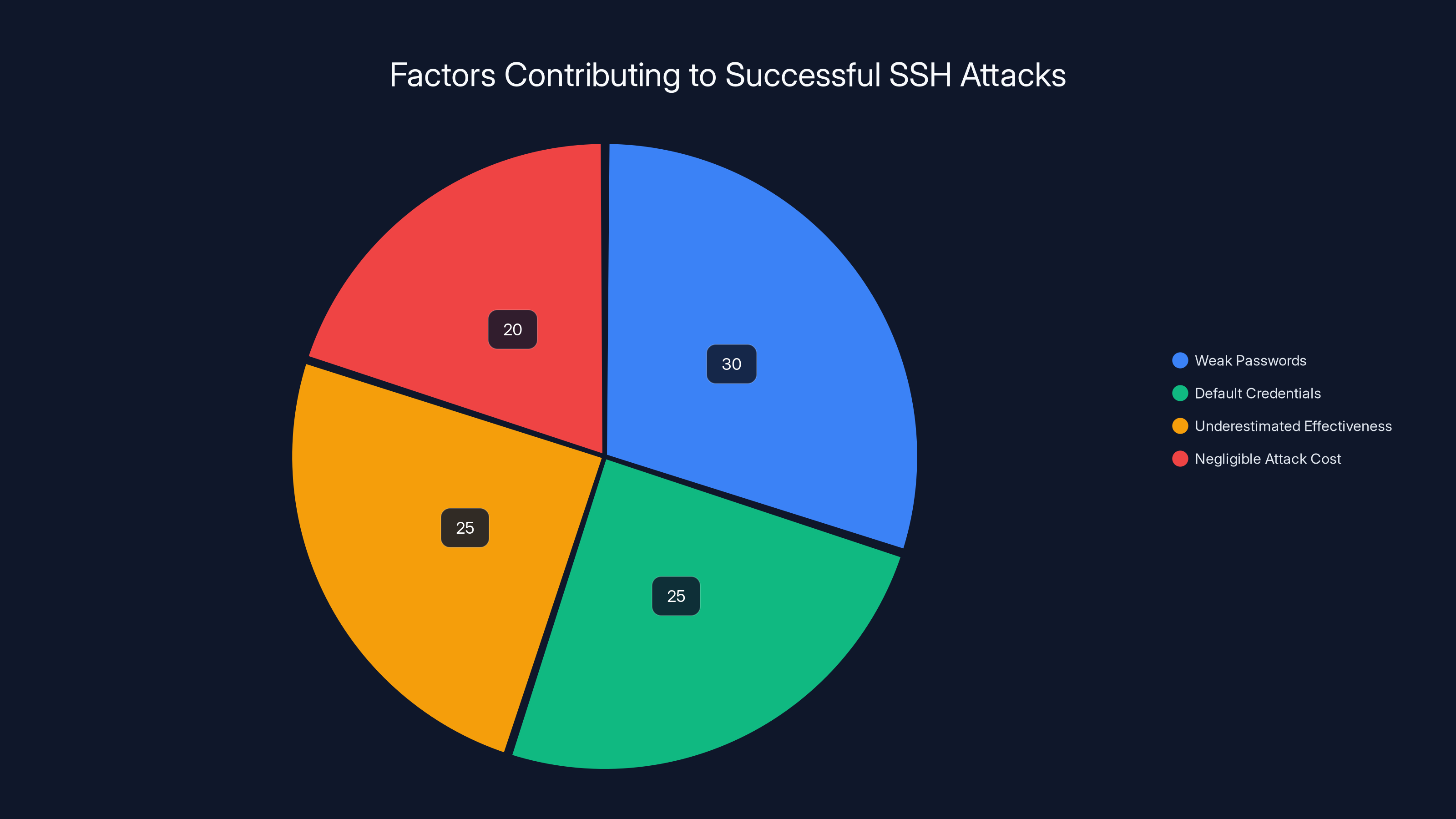
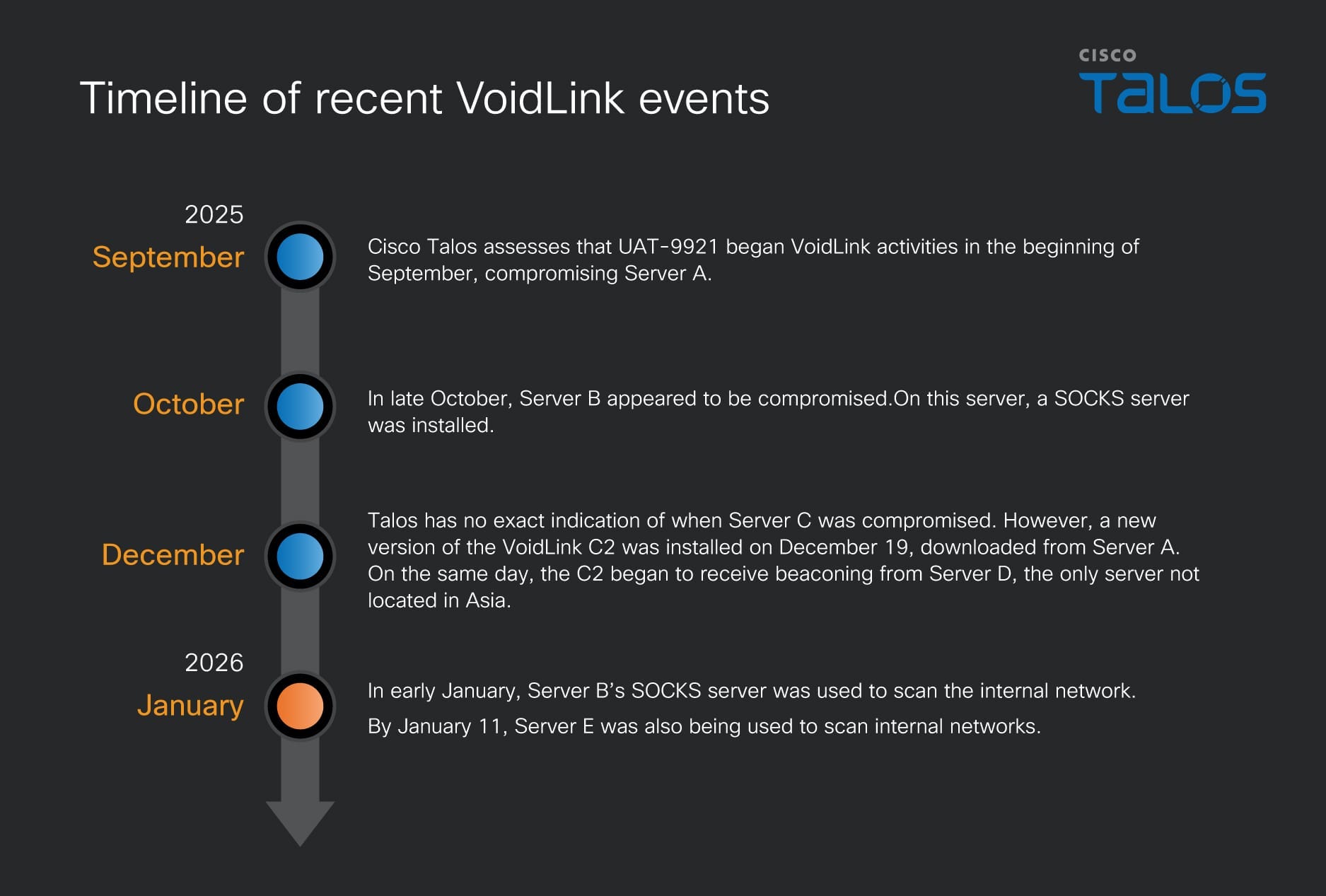
Weak passwords and default credentials are the primary factors contributing to successful SSH attacks, highlighting the importance of basic security hygiene. Estimated data.
What Is SSHStalker and Where Did It Come From?
SSHStalker is a Linux botnet that emerged in 2024 as a significant threat to cloud infrastructure. Security researchers from Flare, a threat intelligence firm, documented the malware after observing nearly 7,000 bot scan results in a single month, with activity concentrated across cloud providers including Oracle Cloud, AWS, and other hosting environments.
The botnet gets its name from its hunting methodology: it literally stalks SSH services on Linux servers, using automated scanning to find targets and then launching brute-force attacks to break in. Once inside, it establishes persistence through mechanisms that are surprisingly low-tech but incredibly effective.
What's unusual about SSHStalker isn't that it exists—Linux botnets are common. It's the operational philosophy behind it. Most modern botnets use sophisticated command-and-control infrastructure with encrypted communications, peer-to-peer networks, or compromised legitimate servers. SSHStalker said no thanks to all that complexity. Instead, the operators chose to use IRC, a protocol so old that most modern security tools barely even look for it anymore.
This wasn't born yesterday either. The malware shows signs of being developed by actors with real experience in botnet operations. The code quality is decent, the targeting strategy is logical, and the monetization mechanisms are diverse. This is professionals at work, not script kiddies experimenting with proof-of-concept code.
The infrastructure Flare observed included multiple redundant IRC servers and channels, suggesting the operators have learned from past botnet takedowns. If one server goes down, the bots can reconnect to another. If one channel gets discovered and shut down, they have backups. This redundancy is expensive to maintain manually, but with thousands of infected servers generating revenue, the cost is trivial.
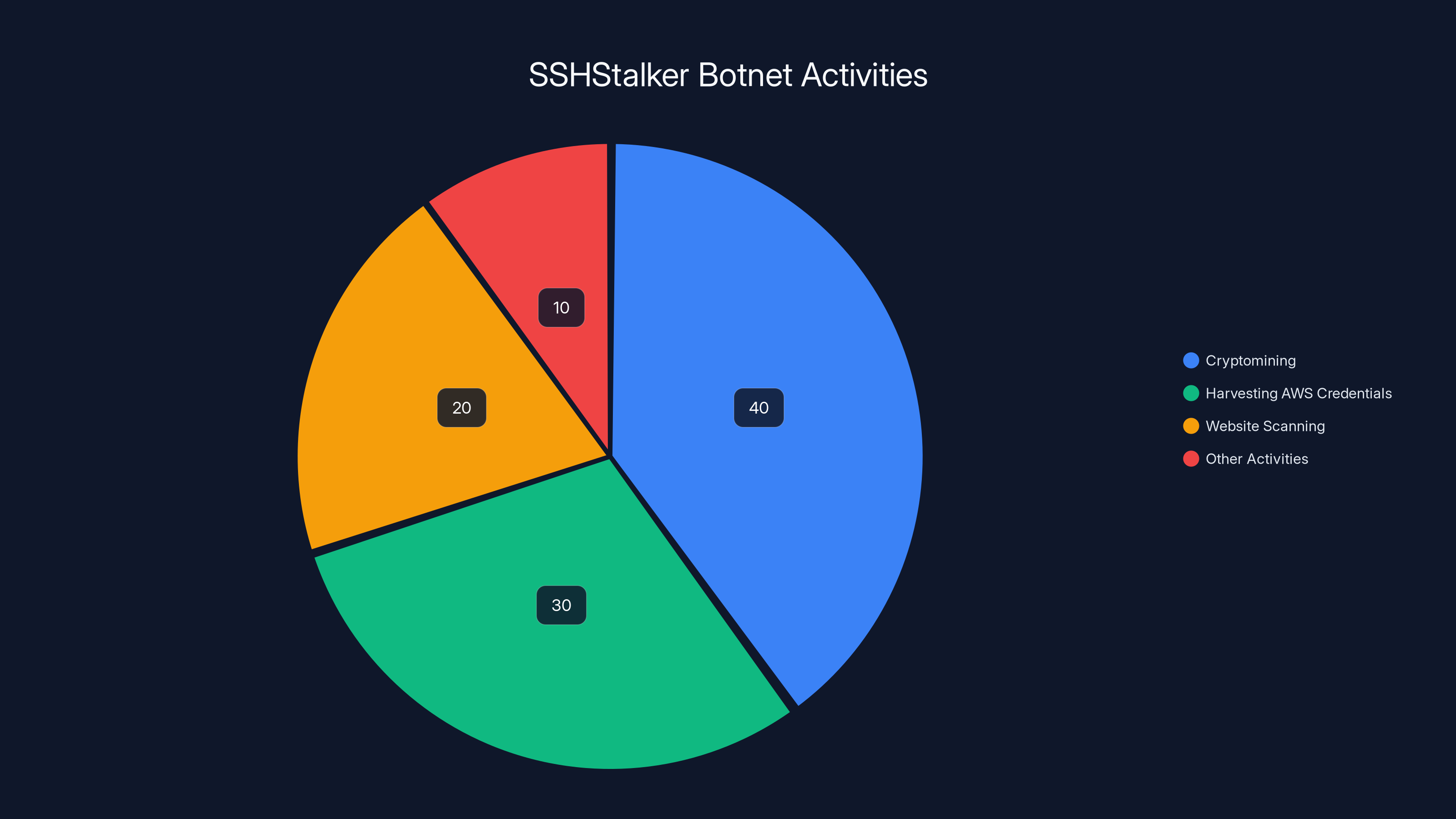
Estimated data suggests that cryptomining is the primary activity of SSHStalker, followed by harvesting AWS credentials and website scanning.
How SSHStalker Breaks Into Your Servers
SSHStalker doesn't use zero-days or sophisticated exploits to get its foot in the door. It uses one of the oldest, most reliable methods in the attacker's playbook: trying common passwords until something works.
The initial compromise happens through automated SSH scanning. The malware conducts widespread network reconnaissance, looking for systems with SSH exposed to the internet. Once it identifies a target, it launches dictionary attacks and brute-force attempts, trying default credentials and common password combinations. This sounds primitive, but it works with alarming frequency because:
- Many cloud instances still use default or weak SSH passwords
- Organizations often forget about test servers and leave them running with placeholder credentials
- Shared hosting environments sometimes inherit insecure configurations from previous tenants
- Developers occasionally leave SSH password authentication enabled for convenience
The malware is disguised as a legitimate tool—researchers identified it masquerading as nmap, a popular network scanning utility that's commonly found on Linux systems. This disguise helps it avoid immediate detection if someone glances at running processes.
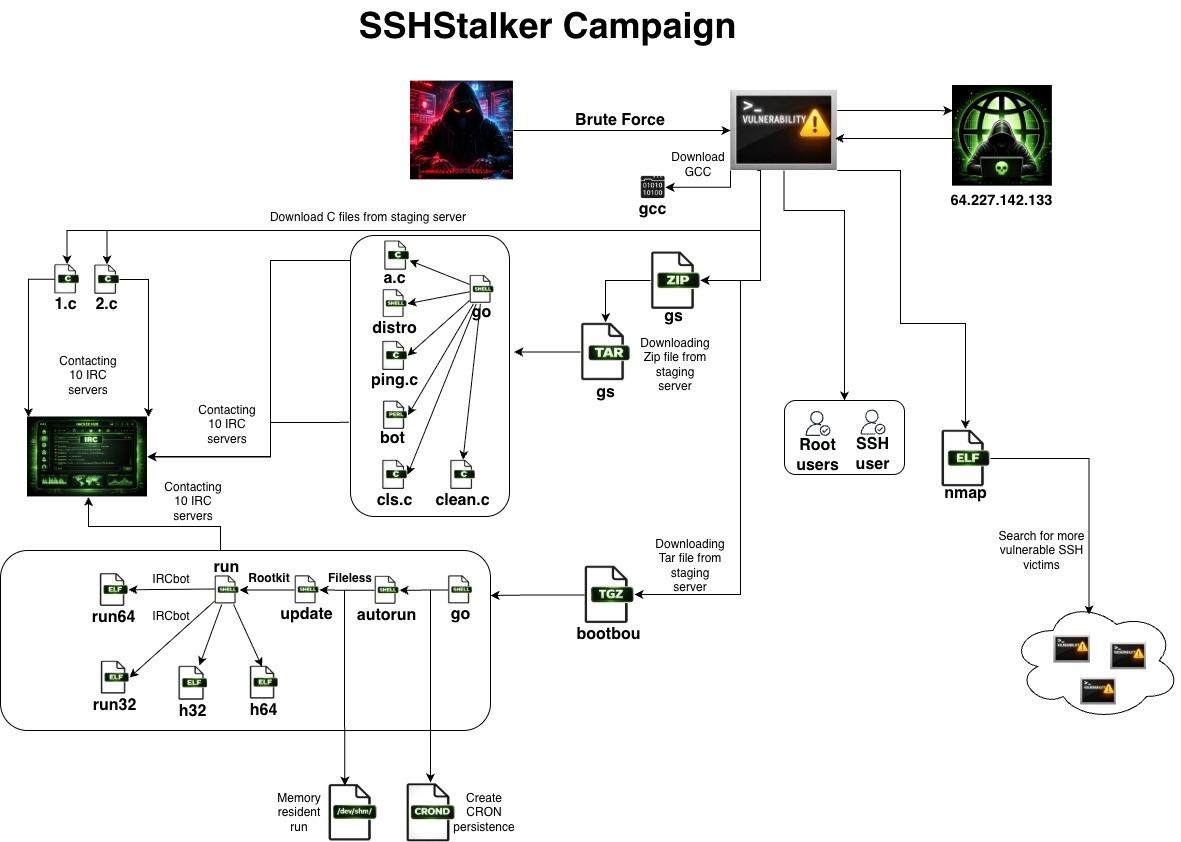
Once the brute-force attack succeeds and an attacker gains access with a low-privilege user account, SSHStalker immediately downloads and executes a payload written in Go. This is where things get interesting from a technical perspective. Instead of using pre-compiled binaries that might be outdated or incompatible across different Linux distributions, SSHStalker downloads the GCC compiler directly onto the target system.
The compiler is then used to build C-based IRC bot code directly on the compromised system. This approach is brilliant from an attacker's perspective because it guarantees compatibility. A pre-compiled binary might fail on a different Linux distribution due to library differences, but code compiled locally with the target system's native compiler will run reliably every single time.
By downloading the compiler and building locally, SSHStalker operators ensure their malware works across Ubuntu, Cent OS, Debian, Red Hat, and basically any Linux variant that has GCC available. This broad compatibility translates directly to a larger attack surface and more reliable infection rates.
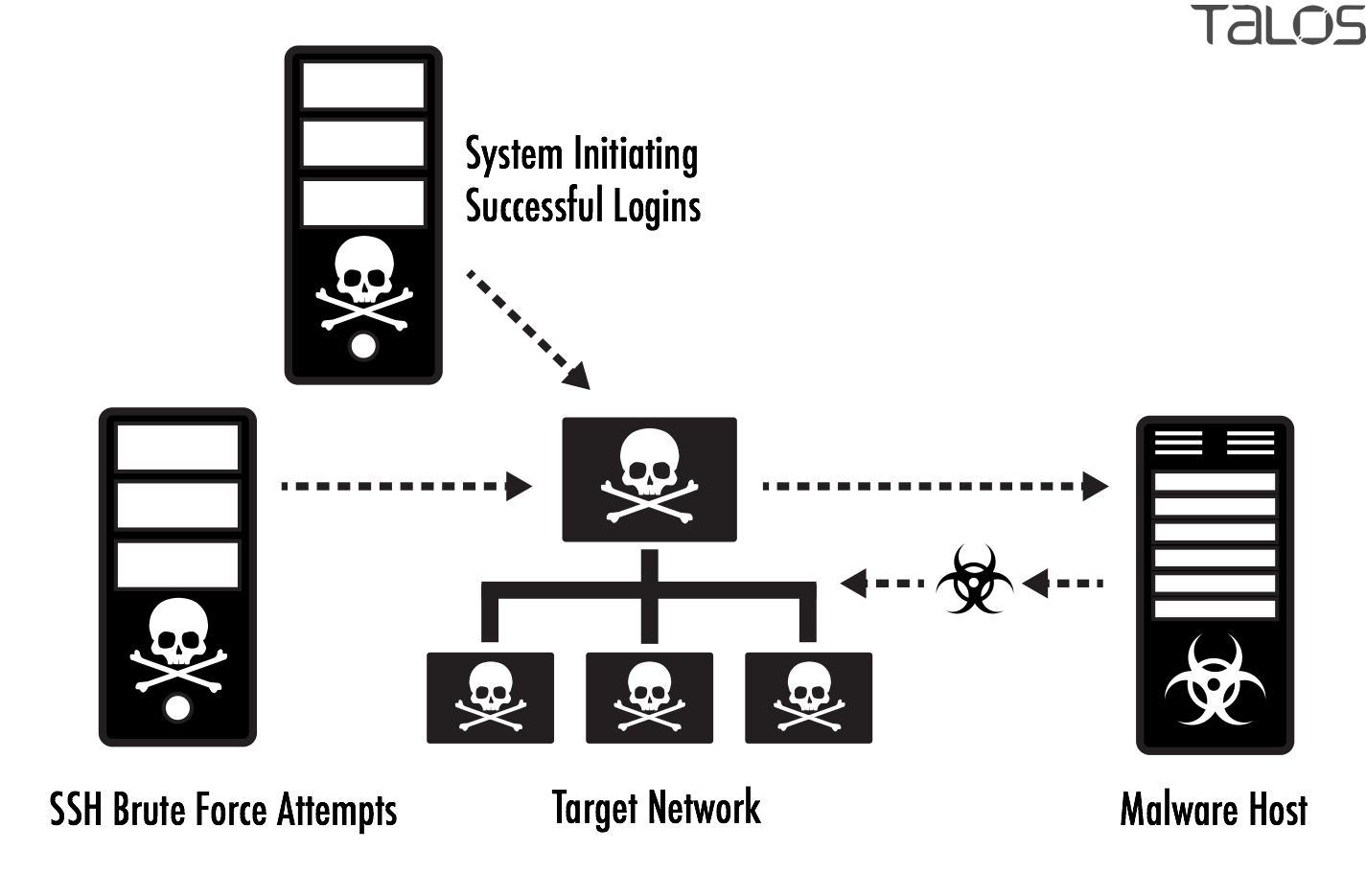
The IRC Command-and-Control Infrastructure
Now we get to the really interesting part: why on earth would modern botnet operators choose IRC as their command-and-control mechanism?
The answer reveals a lot about how security has evolved. Modern detection systems are optimized to catch contemporary attack patterns. They look for:
- HTTPS traffic to unusual domains
- DNS queries for suspicious subdomains
- Outbound connections to known malicious IP addresses
- Encrypted traffic with anomalous entropy patterns
- Large data transfers to cloud storage services
IRC traffic, by contrast, looks almost innocent. It uses plain TCP port 6667 or custom ports, transmits data in readable plaintext, and follows a protocol so simple that most security engineers stopped studying it years ago. When an analyst sees outbound IRC traffic in network logs, their first instinct is usually "oh, probably legacy systems" and they move on to investigating more suspicious patterns.
SSHStalker's IRC implementation includes:
Multiple Server Redundancy: The botnet connects to several hardcoded IRC servers, so if one goes offline, the bots automatically reconnect to another. This redundancy is essential for maintaining command infrastructure when operators know some servers will eventually be seized by law enforcement or ISPs.
Channel-Based Organization: Different groups of bots connect to different IRC channels, allowing the operators to segment their botnet. They might have one channel for bots involved in cryptomining, another for those harvesting credentials, and another for testing new payloads. This segmentation contains the blast radius if one channel gets disrupted.
Hard-Coded Credentials: The bot binary contains the server addresses, port numbers, and channel names baked directly into the compiled code. This means every infected bot knows exactly where to connect and what to do, with no need for domain generation algorithms or DNS lookups that might be logged and detected.
Persistent Connection Maintenance: If the IRC connection drops, the bot automatically reconnects. The cron job running every minute checks if the bot process is still running and the IRC connection is active. If either condition fails, it restarts everything.
The IRC traffic itself is straightforward. The botmaster sends commands through the IRC channel, and all connected bots receive them simultaneously. Need to activate cryptomining on all infected servers? Send one message to the IRC channel. Want to push a new payload? Post it. The simplicity is a feature, not a bug. Less complex code means fewer bugs, faster execution, and more reliable operation at scale.
From an operational cost perspective, this is why SSHStalker chose IRC. Running a botnet across thousands of servers requires infrastructure. Cloud hosting costs money. Domain registration costs money. Bandwidth costs money. IRC lets attackers run their botnet on cheaply-hosted IRC servers that relay traffic between thousands of bots, distributing the cost across a tiny footprint.
Modern botnets using encrypted custom protocols require developers, maintenance, updates, and constant monitoring. IRC is fire-and-forget. Set it up, push commands through channels, collect profit. It's low-effort, low-cost, and weirdly effective.
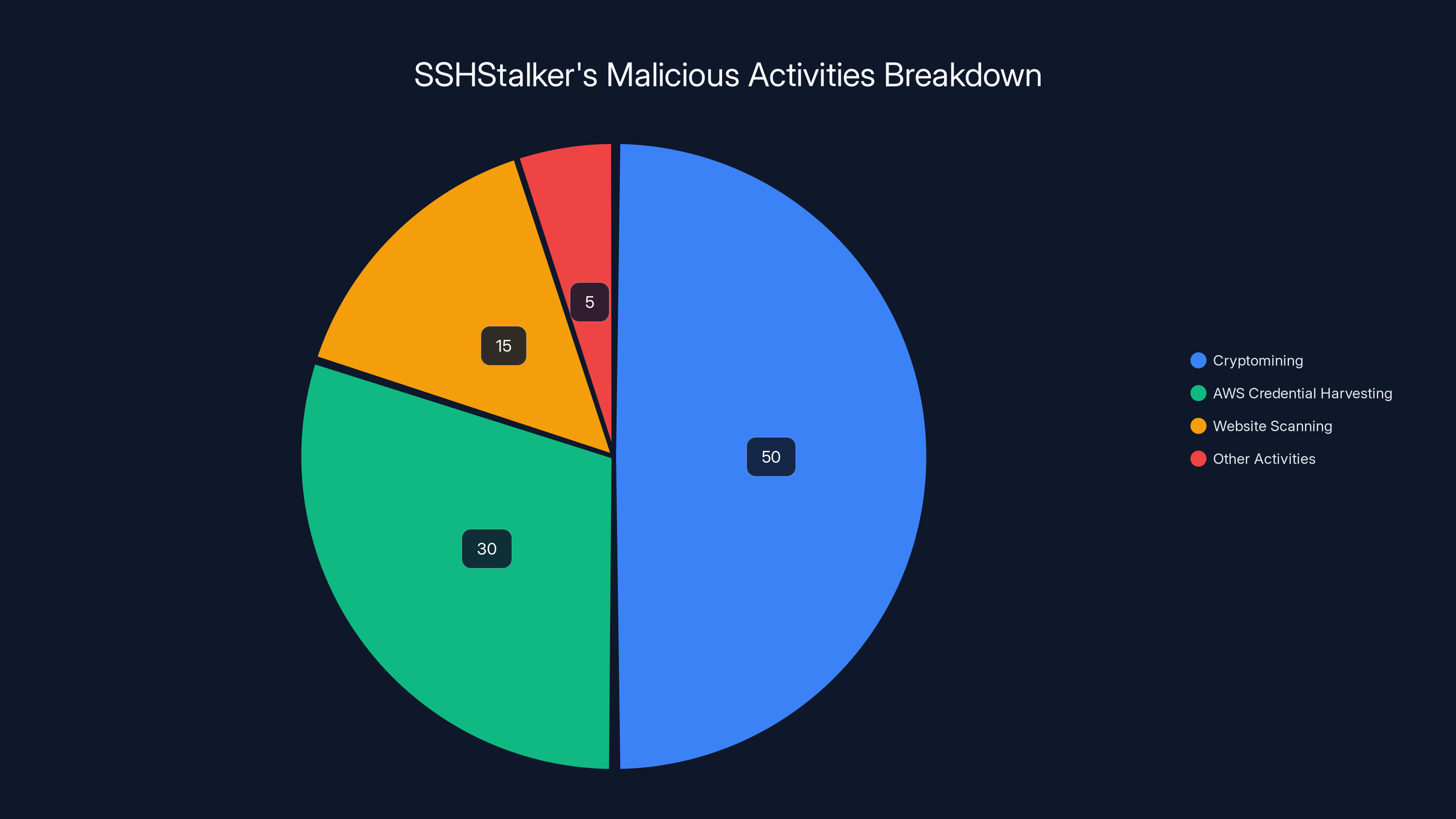
Cryptomining is the primary activity of SSHStalker, accounting for an estimated 50% of its operations, followed by AWS credential harvesting at 30%. Estimated data based on typical malware behavior.
Persistence Through Cron Jobs and Process Monitoring
Once SSHStalker infects a server and establishes IRC connectivity, ensuring it stays there is critical. Attackers use a deceptively simple but wickedly effective persistence mechanism: cron jobs.
A cron job is a scheduled task on Unix-like systems (including Linux) that runs a command at specified intervals. Administrators use cron for legitimate purposes—backups, log rotation, system updates. Attackers use cron for something else: ensuring malware keeps running.
SSHStalker sets up a cron job that executes every single minute. This job has one purpose: check if the main bot process is still running. If it's running, do nothing. If it crashed, was killed, or was manually stopped, restart it immediately.
Here's why this is so effective:
Minimal Overhead: Running a script once per minute uses negligible system resources. It won't trigger CPU alerts or cause performance degradation that might tip off administrators.
Rapid Recovery: Within 60 seconds of an administrator manually killing the bot process, it's running again. This makes manual removal nearly impossible without understanding the persistence mechanism.
Difficult to Detect: Cron jobs are legitimate system features. Administrators often don't closely review all cron entries, especially if the malicious job is buried among dozens of legitimate scheduled tasks or added during the initial compromise when they might not be monitoring carefully.
Survives Reboots: Cron jobs are configured in files that persist across system restarts. Even if someone reboots the server thinking it will help, the infected process comes right back.
The typical cron line might look something like this in the system crontab or a user crontab:
bash*/1 * * * * /tmp/.cache/bot >/dev/null 2>&1
Translated: every minute, every hour, every day, every month, every day of week, run the bot binary from the .cache directory and suppress any output (which keeps it quiet and invisible to logs).
To make detection harder, SSHStalker doesn't store its binary in an obvious location like /usr/bin or /opt. Instead, it hides in directories like /tmp/.cache or other locations that are less likely to be scrutinized. It might also use process name spoofing, giving the bot executable a name that sounds innocuous.
Some advanced variants also implement process monitoring that's more sophisticated. They might check if security tools have killed the process and use that as a signal to spread further or trigger additional payloads. The basic persistence mechanism, though, is this simple cron-based watchdog.
What makes this particularly insidious is that many companies don't monitor cron job execution. They look for network anomalies, unusual process behavior, or resource spikes, but they don't audit their scheduled tasks. SSHStalker exploits this monitoring gap ruthlessly.
Privilege Escalation: Breaking Out of Limited Access
When SSHStalker breaks into a server through SSH brute-force, it's usually getting in as a regular user, not root. This is actually typical for cloud servers—SSH password authentication usually connects to unprivileged service accounts.
From a limited user account, the bot can still cause trouble, but it's constrained. It can't modify system files, can't fully disable security features, and can't persist in ways that survive account deletion. So SSHStalker has a clever trick: exploit ancient Linux kernel vulnerabilities.
Researchers found that SSHStalker leverages CVEs (Common Vulnerabilities and Exposures) in the Linux kernel dating back to 2009 and 2010. These are 14-to-15-year-old vulnerabilities in older kernel versions. The exploits include:
CVE-2009-2692: A NULL pointer dereference in the sock_sendpage function CVE-2010-2959: A stack-based buffer overflow in the CAN bus implementation CVE-2010-3081: A NULL pointer dereference in the futex subsystem
These vulnerabilities probably don't sound familiar because they're ancient in tech years. Most organizations have patched them. But cloud environments often run older images or customers don't keep up with kernel security updates. For SSHStalker, these old vulnerabilities are a treasure trove.
Once a privilege escalation exploit succeeds, the bot gains root access. Now it can:
- Modify system-level cron jobs that can't be removed by non-root users
- Disable or bypass security tools
- Access all user files and credentials
- Modify the kernel or load kernel modules
- Completely hide its presence from detection tools
The fact that SSHStalker includes exploits for such old vulnerabilities reveals something important about the threat landscape: many servers in the cloud aren't running current kernel versions. Some organizations deprioritize kernel updates because they seem less critical than application updates. Others run older cloud images that haven't been updated in years.

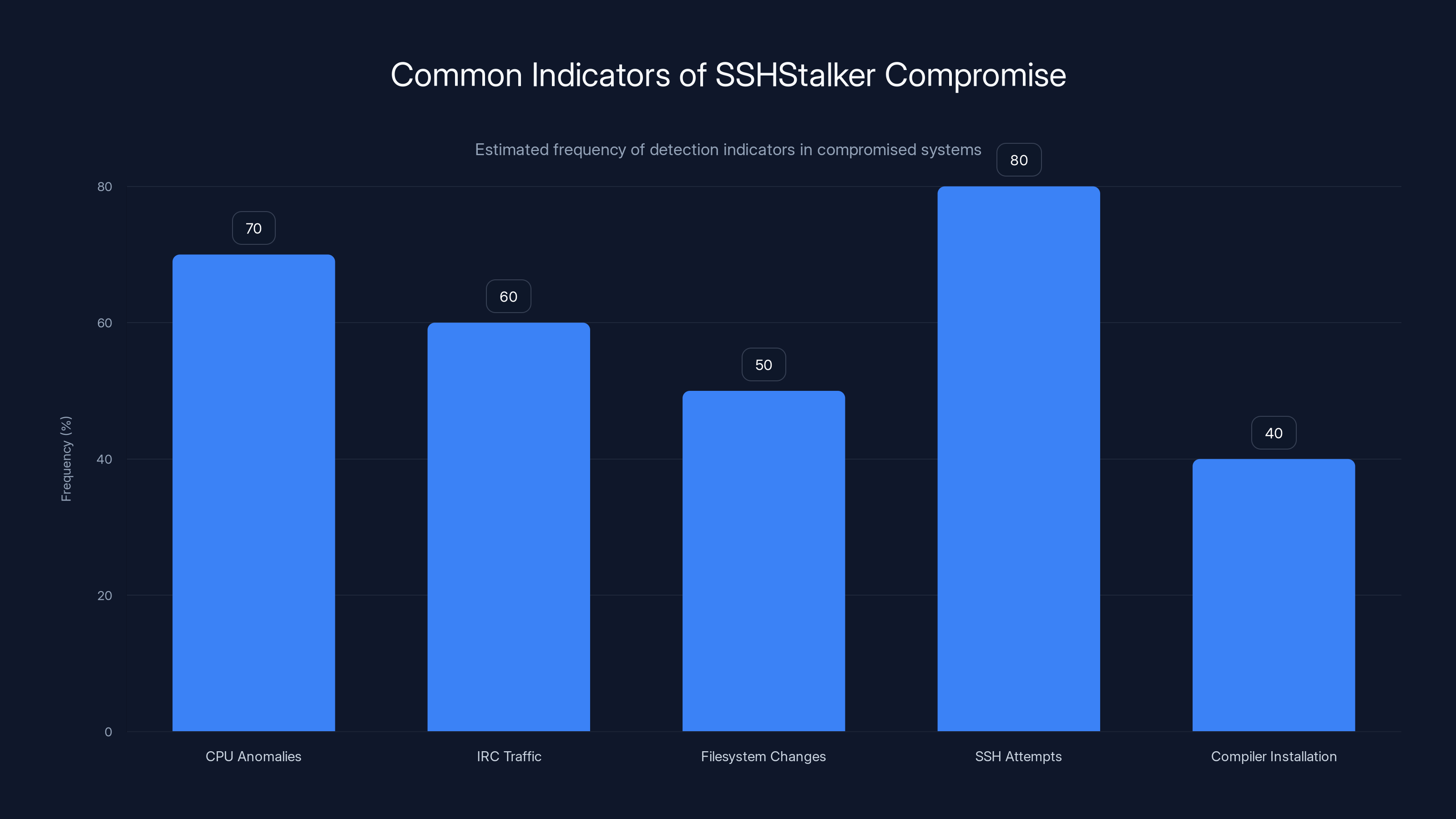
Estimated data suggests SSH brute-force attempts and CPU anomalies are the most frequent indicators of compromise, while unexpected compiler installations are less common.
What SSHStalker Actually Does Once It's Inside
SSHStalker isn't just lurking passively after infection. The malware has multiple payloads and mechanisms for generating revenue from compromised servers.
Cryptomining: The Primary Revenue Stream
The main moneymaker is cryptomining, specifically using a miner called Phoenix Miner to mine Ethereum. Once installed, the miner consumes CPU and GPU resources to solve cryptographic puzzles, and the solved blocks generate cryptocurrency that goes directly to the attacker's wallet.
For cloud server owners, this is a disaster. Their servers are suddenly running at high resource utilization, which:
- Causes application performance degradation
- Triggers expensive auto-scaling policies that spin up more expensive instances
- Heats up server hardware and shortens its lifespan
- Increases electricity costs substantially
For the attacker, it's profitable. If you've compromised a high-performance cloud instance with multiple CPU cores, you could mine hundreds of dollars worth of cryptocurrency per month. Scale that across thousands of servers and you're looking at significant income.
AWS Credential Harvesting
SSHStalker also harvests AWS access keys and credentials from compromised servers. Cloud instances often run with AWS IAM roles that grant them permission to access S3 buckets, databases, load balancers, and other AWS resources. If an attacker steals those credentials, they can:
- Copy sensitive data from S3 buckets
- Modify or delete databases
- Create new instances and use them for further attacks
- Access logs and configuration files
- Lateral move to other systems within the organization
Many organizations store AWS credentials directly in environment variables, configuration files, or even hardcoded in application code. SSHStalker searches for these credentials and exfiltrates them back to command servers.
Website Scanning and Reconnaissance
Beyond just mining and credential theft, SSHStalker performs website scanning on compromised servers. This reconnaissance helps attackers understand what services are running, what vulnerabilities might exist, and whether other interesting targets are accessible from the infected server.
The scanning capability also turns compromised servers into launch points for further attacks against other systems. Instead of attacking from their own IP addresses (which might be blocked or flagged), attackers use the compromised cloud servers to scan their next targets.
DDo S Capabilities: In Reserve
While researchers haven't observed SSHStalker actually launching DDo S attacks yet, the malware includes DDo S capabilities. This suggests the operators might be:
- Testing the functionality before deploying it
- Waiting for higher-value targets
- Hoarding access for sale to other criminal groups
- Using it selectively against systems that pose a threat to their operation
The fact that thousands of bots are already compromised with DDo S capability means if the operators decide to deploy it, they can suddenly launch devastating attacks from distributed sources worldwide.
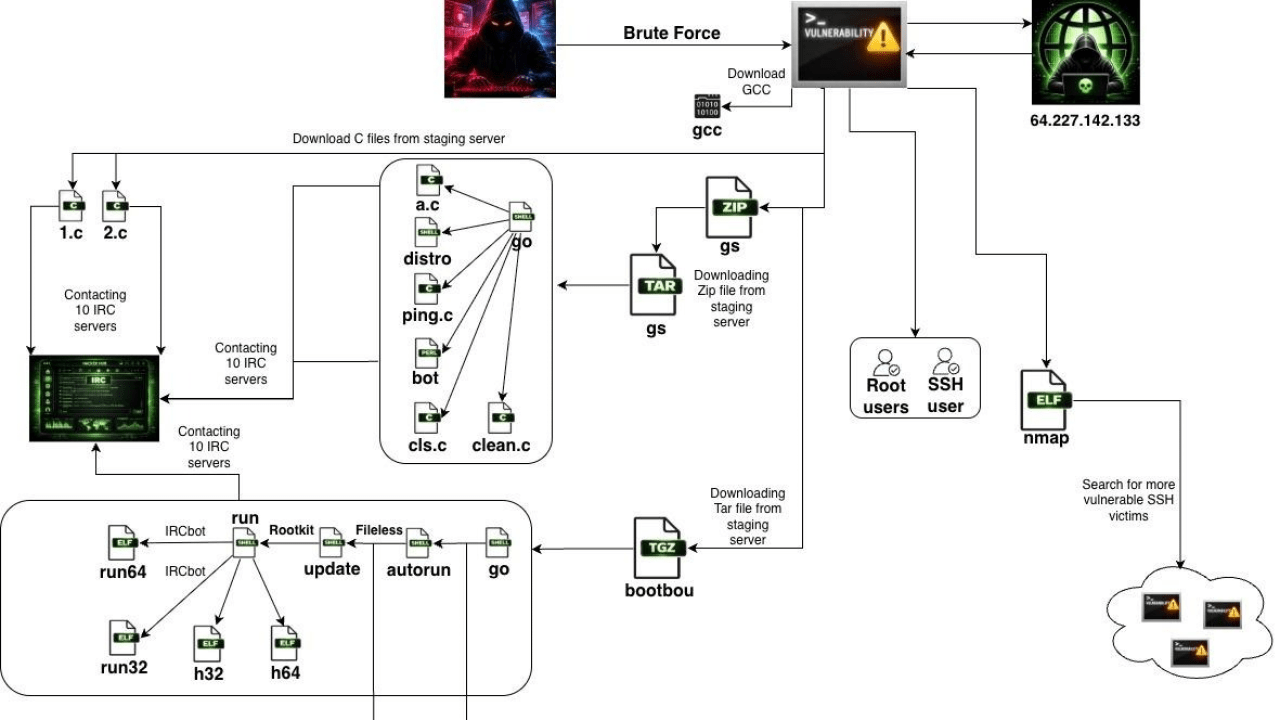
Why Cloud Infrastructure Is a Prime Target
SSHStalker focuses heavily on cloud environments, and there are good reasons why attackers find them so attractive.
Weak Authentication at Scale
Cloud infrastructure is often created quickly for temporary projects, development environments, or testing. Security sometimes gets deprioritized in these scenarios. Test servers might use simple passwords for ease of management. Development environments might have broader access policies. SSH password authentication might be enabled because it's easier than managing keys.
When you multiply these oversights across thousands of organizations, you get millions of cloud instances with weak authentication that are vulnerable to brute-force attacks.
High Performance = High Profitability
Cloud instances are often quite powerful—multiple CPU cores, large amounts of RAM, sometimes GPUs. This makes them excellent for cryptomining. A single compromised high-end instance might generate more cryptocurrency per month than dozens of consumer laptops.
Automated Scaling Masks Resource Abuse
Many cloud environments use autoscaling, where additional instances spin up automatically when load increases. If cryptomining suddenly causes high resource usage, autoscaling might kick in and launch more expensive instances, compounding the problem.
Furthermore, the increased resource usage might get hidden among legitimate traffic patterns, making it harder to detect that something's wrong.
Valuable Credentials and Data
Cloud instances frequently have access to databases, APIs, and other sensitive resources. Compromising a cloud server sometimes gives attackers the keys to far more valuable assets. A single compromised web server might provide credentials for accessing a database containing millions of customer records.

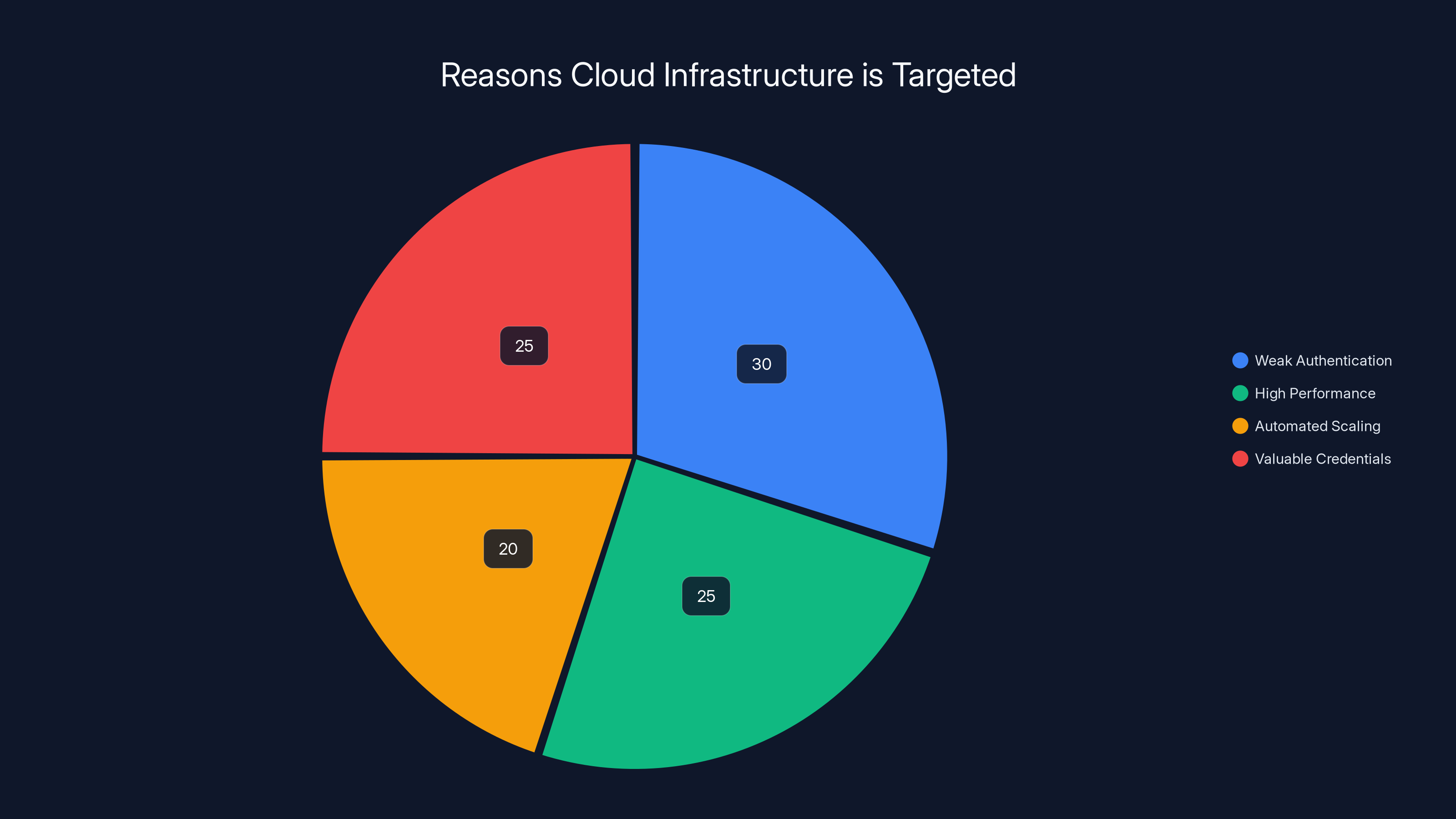
Estimated data shows that weak authentication and valuable credentials are major factors making cloud infrastructure a prime target for attackers.
Detection: What To Look For
Given how SSHStalker operates, defenders can look for specific indicators of compromise.
Process and Resource Anomalies
If you notice processes consuming unusual amounts of CPU without corresponding application activity, that's suspicious. Cryptomining processes are usually very CPU-intensive. Look for processes with names that seem to spoof legitimate tools—check process binaries to verify they are what they claim to be.
Network Indicators
SSHStalker establishes outbound connections to IRC servers. While plain IRC traffic is less conspicuous than encrypted command-and-control, it's still unusual in most corporate environments. Monitor egress firewall logs for outbound connections to unfamiliar IP addresses on ports commonly used by IRC (6667, 6668, 6697, etc.).
Look for IRC protocol traffic specifically—it uses specific commands (NICK, JOIN, PRIVMSG) that are identifiable even though the data isn't encrypted.
Filesystem and Cron Indicators
Regularly audit cron jobs on your systems. Check /etc/cron.d/, /etc/cron.daily/, /etc/cron.weekly/, and user crontabs for suspicious entries.
Searching for recently modified files in /tmp, /var/tmp, and .cache directories can reveal bot binaries. Look for executable files in locations where they shouldn't be.
SSH Brute-Force Attempts
Monitor SSH logs for failed login attempts. A sudden spike in authentication failures, especially from multiple IP addresses, indicates active scanning and brute-force attacks. While not all brute-force attempts succeed, they're a warning sign that attackers are probing your infrastructure.
Compiler Installation
If you see GCC, Clang, or other compilers installing unexpectedly on production servers, that's a major red flag. Legitimate production environments shouldn't be downloading compilers. This is a strong indicator of either active infection or ongoing compromise.
System Behavior Changes
Monitor CPU, memory, and network utilization baselines. Cryptomining causes sustained high CPU usage that should be obvious when compared against normal patterns. If a server that normally uses 10% CPU suddenly uses 80% consistently, something's wrong.
Defensive Strategies: How To Protect Your Infrastructure
Preventing SSHStalker infection requires a multi-layered approach.
Use SSH Key Authentication
The most critical defense is disabling SSH password authentication entirely and requiring key-based authentication. This makes brute-force attacks completely ineffective. The attacker could try a million passwords and none of them would work if password authentication is disabled.
Implementing this requires:
- Generating SSH key pairs for all users
- Distributing public keys to servers
- Disabling
Password Authenticationin/etc/ssh/sshd_config - Restarting the SSH service
- Testing that key-based authentication works before locking out password login
For cloud instances, use infrastructure-as-code tools that automatically deploy properly configured SSH keys during instance creation. Never rely on default credentials or manually-set passwords.
Restrict SSH Access with Firewalls
Not every server needs SSH exposed to the internet. Use network-level controls to restrict which IP addresses can connect to SSH ports. If possible, require SSH connections to go through a bastion host or VPN.
Cloud security groups and network ACLs should whitelist only necessary source IPs for SSH. If your developers work from home, they should connect through a VPN that presents a consistent outbound IP address.
Remove Compilers from Production
Production servers shouldn't have development tools installed. Removing GCC, Clang, and other compilers from production images eliminates SSHStalker's ability to compile bot code locally.
If you absolutely need compiling capability, isolate it to dedicated build servers that aren't internet-facing and have stronger security controls.
Implement Egress Filtering
Most organizations focus on preventing inbound attacks but neglect egress filtering. Outbound connections to suspicious destinations should be blocked at the firewall level. Specifically:
- Block or heavily monitor outbound IRC connections (ports 6667, 6668, 6697, etc.)
- Block connections to known malicious IP addresses (using threat intelligence feeds)
- Require explicit allow rules for outbound traffic rather than defaulting to allow
- Monitor DNS queries for unusual domains
Many cloud providers make this difficult because applications legitimately need internet access. However, you can at least block known malicious networks and monitor IRC traffic as suspicious.
Keep Systems Patched
SSHStalker exploits kernel vulnerabilities from 2009-2010. These are trivial to fix—just update to a current kernel version. This means:
- Establishing a regular patch schedule
- Testing patches in staging environments before production
- Using tools that automate patch detection and application
- Monitoring which versions of the kernel are running across your infrastructure
For cloud environments, periodically re-image instances with the latest OS versions rather than running old images indefinitely.
Monitor Process Execution and Cron Jobs
Implement endpoint detection and response (EDR) tools that alert on suspicious process behavior. Specifically:
- Alert when compilers execute unexpectedly
- Monitor cron job execution
- Track unexpected processes consuming high CPU
- Detect processes with spoofed or suspicious names
Automated monitoring makes it much harder for attackers to operate silently.
Use Antivirus and Malware Detection
While signature-based antivirus is less effective against novel malware, it's still useful for detecting known threats. Deploy antivirus tools that:
- Detect malicious binaries by signature
- Monitor suspicious file modifications
- Alert on known malware indicators
- Automatically quarantine suspicious files
Combine signature-based detection with behavioral analysis that flags unusual activity patterns.
Implement File Integrity Monitoring
File integrity monitoring tracks changes to critical system files and alerts when they're modified. This catches persistence mechanisms and modifications to configuration files:
- Changes to
/etc/cron.d/ - New files in
/tmpor.cache - Modifications to SSH configuration
- Unexpected binary replacements

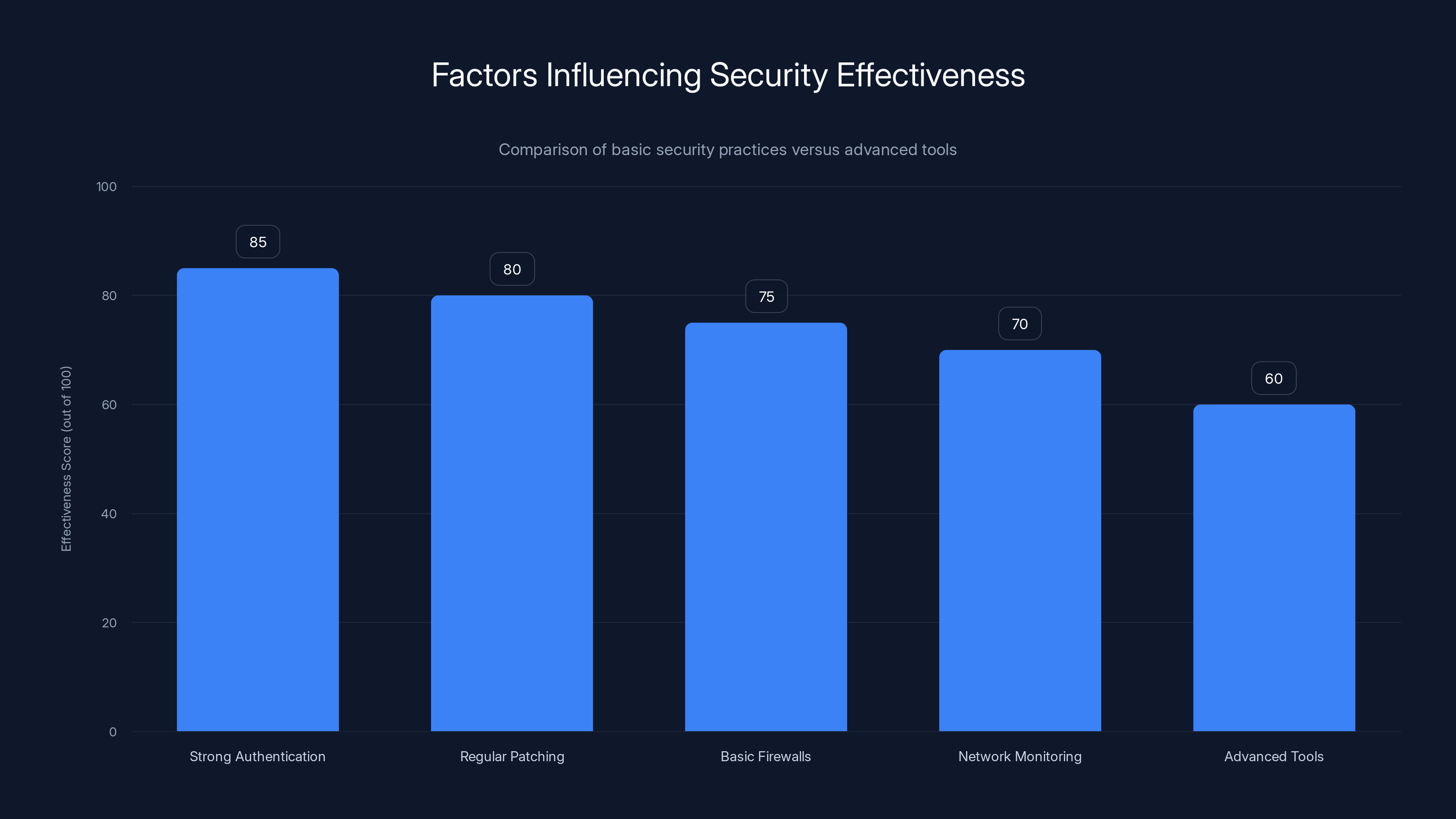
Basic security practices like strong authentication and regular patching are more effective than relying solely on advanced tools. Estimated data.
The Broader Threat Landscape
SSHStalker isn't an isolated incident. It's part of a broader pattern of attackers exploiting legacy infrastructure and weak security practices.
Why Old Methods Still Work
Security teams often focus on preventing cutting-edge attacks while overlooking established threat vectors. SSH brute-force attacks are decades old, but they still work because:
- Organizations underestimate their effectiveness at scale
- Many systems still use weak passwords
- Default credentials often aren't changed
- The attack cost (just sending connection attempts) is negligible
- Success rates are often higher than expected
Modern attackers understand this. They might lack the sophistication of state-sponsored groups, but they make up for it with scale and persistence. They automate everything and hit thousands of targets, knowing that even a small success rate generates substantial profit.
The Economics of Botnet Operations
SSHStalker's use of old-school methods reveals something important about botnet economics. It's not about technical sophistication—it's about cost efficiency and reliability.
If an attacker compromises 1,000 cloud instances and mines cryptocurrency on them, even if each instance generates only
Compare that to running a sophisticated botnet with custom protocols, dedicated developers, and encrypted communications. That infrastructure costs significantly more and requires constant maintenance. From a pure financial perspective, SSHStalker's approach makes sense.
The Evolution of Attack Sophistication
There's an interesting paradox here. SSHStalker is simultaneously simple and sophisticated. The methods are simple and old, but the targeting, scale, and coordination are sophisticated. The operators understand:
- Which cloud providers and regions host the most exploitable targets
- How to efficiently scan massive IP ranges for vulnerable servers
- How to compile code for multiple Linux distributions
- How to maintain infrastructure across thousands of nodes
- How to avoid detection while generating profit
This suggests competent operators with real botnet experience, not just script kiddies running off-the-shelf tools.
Future Implications
What does SSHStalker tell us about the future of cyber threats?
The Persistence of Legacy Vulnerabilities
As long as organizations run outdated systems, attackers will exploit outdated vulnerabilities. Even patches from 15 years ago matter if servers still haven't been updated.
This suggests the security industry needs to focus more on helping organizations patch legacy systems efficiently. The problem isn't that patches don't exist—they do. The problem is that organizations struggle to deploy patches at scale and maintain software currency.
The Underestimation of Simple Attacks
When security professionals think about threats, they often focus on sophisticated techniques: zero-day exploits, advanced evasion, custom malware. Meanwhile, simple brute-force attacks achieve massive success because few organizations defend against them properly.
This might push more defenders toward basic security hygiene as a competitive advantage. Organizations that nail the fundamentals—strong authentication, basic firewalls, regular patching—might find themselves far ahead of competitors focusing on exotic threats.
The Value of Monitoring and Visibility
SSHStalker is detectable if you're looking for it. The problem is that many organizations don't have the visibility to detect the indicators. They don't monitor SSH logs carefully, they don't audit cron jobs, they don't track compiler executions.
As attackers continue exploiting visibility gaps, defenders will need to invest more heavily in monitoring infrastructure and threat detection. The organizations with the best visibility will catch compromises earliest and limit damage.

FAQ
What is SSHStalker and how does it spread?
SSHStalker is a Linux botnet that spreads through automated SSH brute-force attacks against cloud servers and data centers. Once it breaks into a server using weak credentials, it downloads a Go-based bot disguised as nmap, then uses the system's GCC compiler to build C-based IRC bot code locally. This local compilation ensures the malware runs reliably across different Linux distributions, maximizing the botnet's reach and reliability.
Why does SSHStalker use IRC instead of modern command-and-control methods?
IRC is ideal for botnet operators because it's simple, reliable, and appears innocuous in network logs. Modern detection systems focus on contemporary attack patterns and encrypted communications, often overlooking plaintext IRC traffic that looks like legacy system communication. IRC also requires minimal infrastructure—running just a few IRC servers to coordinate thousands of bots costs far less than maintaining sophisticated encrypted command-and-control networks. The simplicity means fewer bugs and more reliable operation at scale.
How does SSHStalker maintain persistence on infected servers?
SSHStalker uses cron jobs set to run every minute, continuously checking if the bot process is still running. If the process has crashed, been killed, or was manually stopped, the cron job immediately restarts it. This watchdog mechanism makes manual removal nearly impossible without understanding the persistence mechanism or having root access to delete the cron entry. Even if administrators kill the process, it resurrects within 60 seconds automatically.
What does SSHStalker do once it infects a server?
Once installed, SSHStalker performs cryptomining using Phoenix Miner to mine Ethereum for the attackers' profit. It harvests AWS credentials and API keys from the infected system, which attackers use to access S3 buckets, databases, and other AWS resources. The malware also performs website scanning and reconnaissance to map network topology and identify additional attack targets. Advanced variants include DDo S capabilities, though these haven't been actively deployed yet.
What are the key indicators that a server has been compromised by SSHStalker?
Suspicious signs include sustained high CPU usage from cryptomining processes, recent GCC or compiler installation on production servers, new cron job entries (especially in /etc/cron.d/), unexpected outbound connections to IRC ports (6667, 6668, 6697), failed SSH login attempts in system logs, and unfamiliar executable files in /tmp, /var/tmp, or .cache directories. Additionally, watch for processes with names spoofing legitimate tools and unexpected AWS credential access or S3 operations in Cloud Trail logs.
How can I prevent SSHStalker from infecting my servers?
The most critical defense is disabling SSH password authentication entirely and requiring SSH key-based authentication, which makes brute-force attacks completely ineffective. Combine this with firewall rules restricting SSH access to only necessary IP addresses. Remove compilers (GCC, Clang) from production servers since SSHStalker relies on them to build code locally. Implement egress filtering to block outbound IRC connections, establish a regular patching schedule to fix old kernel vulnerabilities, monitor cron jobs and process execution continuously, and deploy endpoint detection and response tools that alert on suspicious behavior.
Why are cloud environments particularly vulnerable to SSHStalker?
Cloud infrastructure often prioritizes speed of deployment over security, leaving instances with weak authentication, default credentials, or password-based SSH enabled. Cloud servers are typically high-performance with multiple CPU cores, making them extremely profitable for cryptomining operations. Autoscaling features can mask resource abuse since high CPU usage might trigger legitimate scaling policies. Additionally, cloud instances often have credentials granting access to valuable databases, storage buckets, and other resources, making compromises particularly valuable to attackers.
How old are the kernel vulnerabilities that SSHStalker exploits?
SSHStalker exploits Linux kernel CVEs dating back to 2009 and 2010, making them 14-15 years old. Despite their age, these vulnerabilities remain relevant because many organizations don't keep their kernel versions current, especially in cloud environments where old images are sometimes run for years without updating. The fact that attackers successfully use 15-year-old exploits reveals that patching practices are far from universal even in modern infrastructure.
What should I do if I discover SSHStalker on one of my servers?
First, immediately isolate the affected server from the network if possible to prevent further spreading. Kill the bot process, but understand that cron jobs might restart it—locate and delete the cron entry. Search the filesystem for suspicious binaries, particularly in /tmp, /var/tmp, .cache directories, and any custom installation paths. Review SSH logs to understand how the attacker gained initial access. Audit and rotate any AWS credentials that might have been harvested. Finally, rebuild the server from scratch using a clean image with current security patches, SSH key authentication enabled, and compilers removed.
Can SSHStalker be detected by standard antivirus software?
Standard antivirus can detect SSHStalker if the malware signature is in their database, particularly after the initial discovery. However, attackers continuously update the code to evade signatures, so detection isn't guaranteed. Behavioral-based detection systems that monitor for cryptomining activity, unexpected compiler execution, and suspicious cron jobs are often more effective than signature-based scanning alone. The most reliable detection comes from comprehensive network and system monitoring combined with regular security audits.
What makes SSHStalker different from other Linux botnets?
While other Linux botnets exist, SSHStalker stands out for its deliberate choice of old-school operational methods—IRC for command-and-control, cron jobs for persistence, local compilation for payload reliability. Rather than using sophisticated encryption and complex infrastructure, it emphasizes simplicity and cost efficiency. The targeted focus on cloud infrastructure, the inclusion of multiple monetization mechanisms (cryptomining and credential harvesting), and the demonstrated operational sophistication suggest this is developed by competent criminal operators rather than amateur threat actors.

Conclusion: The Uncomfortable Truth About Modern Security
SSHStalker represents something uncomfortable for the security industry: despite decades of progress in threat detection and defense, incredibly old and simple attack methods still work at scale. We invest billions in sophisticated security tools, yet attackers succeed using a protocol from 1988 and brute-force attacks that were old when most of us weren't in IT yet.
The lesson isn't that modern security is broken—it's that security effectiveness is uneven. Organizations with strong fundamentals (proper authentication, regular patching, basic firewalls, network monitoring) can defend against SSHStalker trivially. Organizations that neglect the basics get compromised despite fancy detection tools.
What's particularly striking about SSHStalker is the operational sophistication masking beneath the simple methodology. The operators clearly understand:
- How to scale an attack across thousands of targets
- How to compile code for multiple Linux distributions reliably
- How to maintain command infrastructure despite node takedowns
- How to generate revenue through multiple mechanisms
- How to evade or hide from defenders
This isn't a tool that works by accident. It's a purpose-built piece of malware developed by actors with real expertise.
For defenders, SSHStalker is both a threat and an opportunity. It's a threat because it's actively targeting cloud infrastructure and succeeding. It's an opportunity because the attack vector is straightforward to defend against if organizations prioritize the fundamentals.
The bigger implication is that security effectiveness might be less about having the most sophisticated tools and more about consistency in the boring stuff—keeping systems patched, enforcing strong authentication, monitoring what actually matters, and cleaning up dangerous practices like leaving development tools in production.
If you manage Linux servers in cloud environments, SSHStalker should be on your radar. But more importantly, it should motivate you to audit your current practices against the defenses we've covered. The attackers are doing their homework. The question is whether your organization is doing its homework too.
The good news? Most of these defenses are free or nearly free to implement. Key-based authentication costs nothing. Egress filtering is a configuration change. Removing compilers is a build process modification. Monitoring cron jobs requires only an audit script. These aren't expensive, sophisticated solutions—they're basic security hygiene.
SSHStalker's success might just be the wake-up call your organization needs to get the fundamentals right.
Use Case: Use an automation platform to generate automated security monitoring reports and alerts when suspicious processes or cron jobs are detected on your infrastructure.
Try Runable For Free
Key Takeaways
- SSHStalker demonstrates that ancient attack methods remain highly effective at scale, using 1988 IRC protocol for command-and-control instead of modern sophisticated infrastructure
- SSH brute-force attacks succeed regularly because many cloud servers use weak passwords or password authentication instead of key-based security
- Cron job persistence makes manual malware removal nearly impossible—the bot automatically restarts every 60 seconds regardless of manual termination attempts
- Cryptomining generates primary revenue while harvested AWS credentials and stolen data provide supplementary income, making cloud infrastructure highly profitable targets
- Fundamental security practices (SSH keys only, egress filtering, regular patching, compiler removal) provide simple but highly effective defenses against SSHStalker
Related Articles
- Claude Desktop Extension Security Flaw: Zero-Click Prompt Injection Risk [2025]
- Microsoft Notepad Markdown Security Flaw: What You Need to Know [2025]
- Microsoft's Strange Email Routing Mishap: What Happened to example.com [2025]
- AI-Powered Phishing: How LLMs Enable Next-Gen Attacks [2025]
- AI Cybercrime: Deepfakes, Phishing & Dark LLMs [2025]
- Cloud Security in Multi-Cloud Environments: Closing the Visibility Gap [2025]
![SSHStalker Linux Botnet: How Ancient IRC Protocol Powers Modern Attacks [2025]](https://tryrunable.com/blog/sshstalker-linux-botnet-how-ancient-irc-protocol-powers-mode/image-1-1771108615242.jpg)



