Void Link: The Chinese Linux Malware Raising Serious Red Flags [2025]
Something disturbing just landed on the cybersecurity radar, and honestly, it's got experts worried. Security researchers at Check Point have uncovered a previously unknown Linux malware framework called Void Link that's so advanced, so feature-rich, and so deliberately engineered that it's raising major questions about what's coming next.
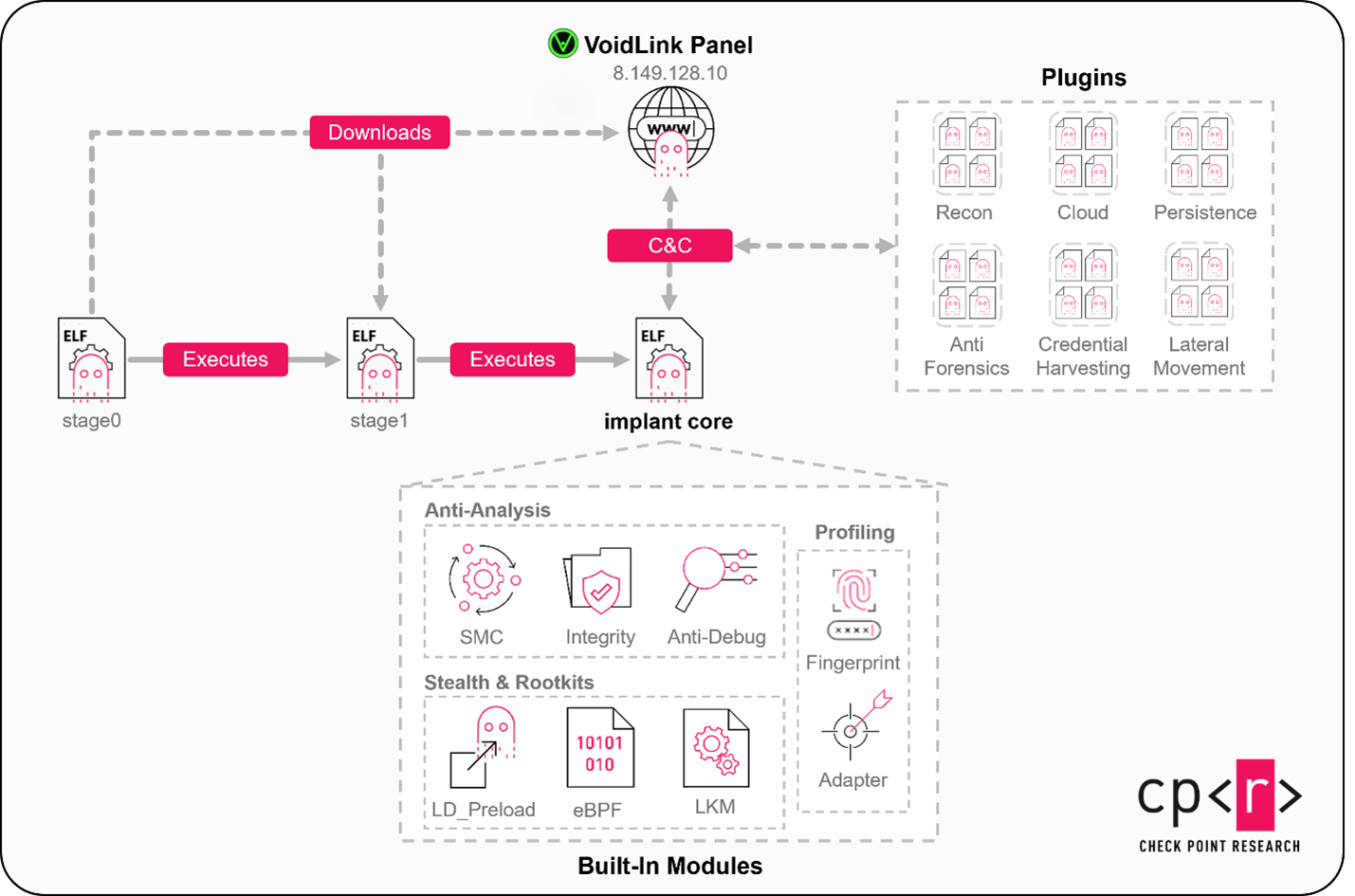
This isn't your garden-variety malware. Void Link is a full command-and-control platform with loaders, implants, rootkits, and over 30 modular plugins. It's being actively developed as of late 2025. The malware appears to be coming from Chinese state-sponsored developers. And here's the thing that's got security professionals nervous: there's currently no evidence of it being used in the wild yet.
That absence of real-world attacks? That's potentially more terrifying than if we were already seeing exploits. It suggests developers are either still building it out for future sale on underground markets, or they're perfecting it for a single high-value client with serious resources. Either way, the implications are significant.
TL; DR
- What It Is: Void Link is a sophisticated Linux malware framework with 30+ modular plugins designed for long-term, stealthy control over compromised systems
- Who Built It: Security evidence points to Chinese state-affiliated developers, likely created for cyber-espionage and persistent access
- Current Status: Still under active development as of late 2025, with no confirmed wild exploitation yet, suggesting preparation for future large-scale campaigns
- Primary Targets: Cloud environments and infrastructure, particularly Dev Ops engineers and cloud administrators managing AWS, Azure, GCP, Alibaba, and Tencent Cloud
- Key Danger: Its modular architecture, adaptive behavior, and sophisticated evasion capabilities make it exceptionally dangerous once deployed at scale
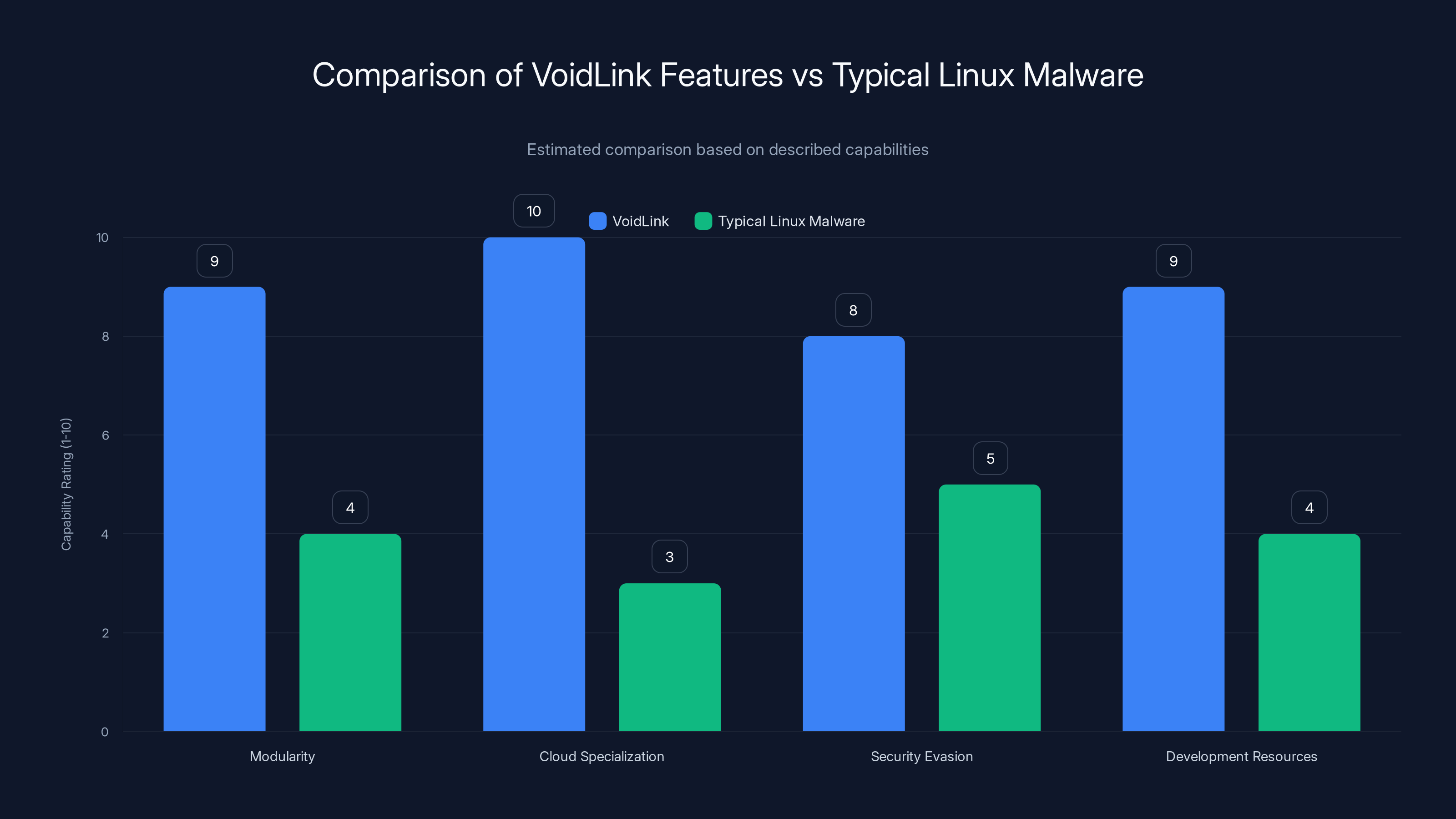
VoidLink significantly outperforms typical Linux malware in modularity, cloud specialization, security evasion, and development resources. Estimated data based on qualitative descriptions.
What Exactly Is Void Link and Why Should You Care?
Void Link isn't just another piece of Linux malware that some script kiddie threw together. This is enterprise-grade, purpose-built malicious software that demonstrates sophisticated engineering principles and strategic thinking. Let's break down what makes it genuinely concerning.
Check Point Research describes Void Link as a complete command-and-control platform. That means it's not just code that infects a system. It's a full ecosystem designed to establish persistent access, maintain operational security, manage compromised assets, and coordinate complex attacks across multiple targets simultaneously.
The architecture is modular, which is important. Rather than cramming all functionality into a single codebase, Void Link uses a plugin-based approach. This means attackers can deploy different capabilities to different systems based on what they need to accomplish. One server might get a credential harvester. Another might get a network reconnaissance module. A third might get a rootkit for deep system access. This flexibility is a hallmark of sophisticated, professionally-developed malware.
The scope is staggering. Over 30 different plugins have been identified, each handling specific tasks. That's an enormous development effort. You don't create 30+ functional plugins unless you're serious about the capability you're building. This isn't a proof-of-concept or a rushed operation. This is planned, funded, and executed by people with serious resources.
The development timeline is also significant. The code shows active development as recently as late 2025. That means whoever built this is still improving it, adding features, and refining capabilities. They're not done. They're still working on it. That's different from discovering old malware from a campaign three years ago. This is current, ongoing development.
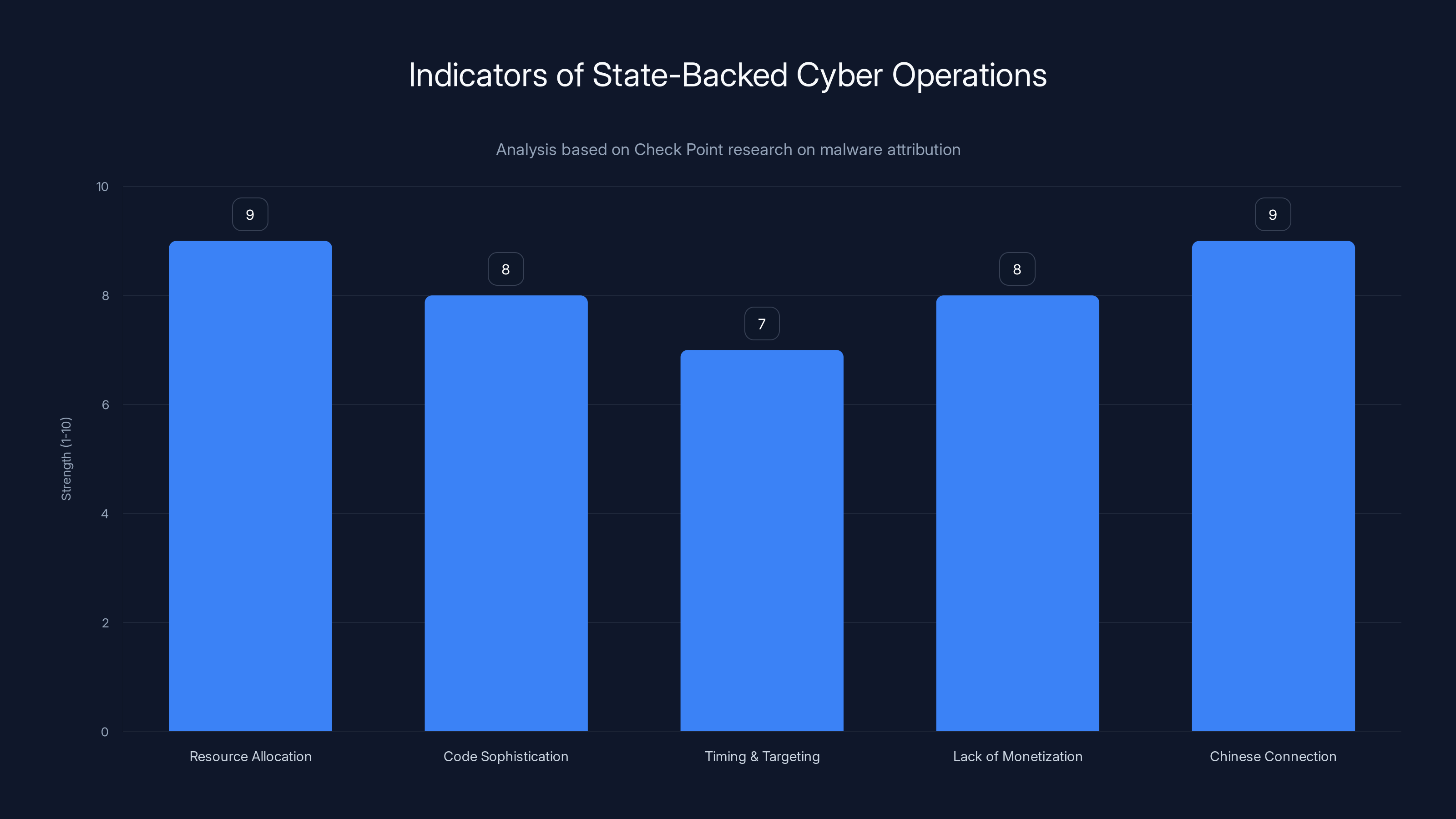
The analysis highlights strong indicators of state-backed operations, with resource allocation and Chinese connection being particularly compelling.
The Cloud-First Architecture: Why Cloud Admins Are Terrified
One of the most revealing aspects of Void Link is that it was designed from the ground up as a cloud-first malware. This isn't malware that was adapted for cloud environments. This is malware that was built specifically for cloud environments, which means the developers deeply understand cloud infrastructure and how to exploit it.
When Void Link infects a system, one of its first actions is to fingerprint the environment. It runs detection routines to determine the cloud provider hosting the compromised system. Is it running on AWS? Azure? Google Cloud Platform? Alibaba Cloud? Tencent Cloud? Each platform has different metadata services, different credential stores, and different attack surfaces.
But Void Link doesn't just identify the platform. It actively adapts its behavior based on what it finds. This is called adaptive malware, and it's much more dangerous than static malware that behaves the same way on every system.
The malware also detects container environments. If it finds itself running inside a Docker container, it adjusts its tactics. If it's in Kubernetes, different approach. This shows sophisticated understanding of modern cloud-native architectures.
Once it establishes what environment it's in, Void Link systematically harvests credentials and secrets. It looks for cloud metadata that contains API credentials, which is how cloud services authenticate requests to each other. It searches for Git credentials, which developers often store locally. It hunts for environment variables containing tokens and API keys. It searches for AWS access keys, Azure credentials, GCP service account keys. Anything that would let an attacker use the compromised system as a jumping-off point for lateral movement.
This is devastating because cloud credentials are keys to the kingdom. A single cloud credential with the wrong permissions could give attackers access to databases containing millions of customer records, source code repositories, configuration files, backup systems. The scope of potential damage depends entirely on what permissions that credential has.
Stealth Mechanics: How Void Link Avoids Detection
What separates professional-grade malware from amateur hour is the stealth component. Void Link doesn't just sit there infecting systems and hoping nobody notices. It actively evades detection through several sophisticated techniques.
First, the malware profiles the host system. It examines what security tools are installed. Is there antivirus? Endpoint detection and response? Host-based intrusion detection? The malware runs through a checklist of common security products and looks for evidence of their presence.
Based on what it finds, it calculates a risk score. Think of it as a threat assessment the malware performs on the system it just compromised. How well defended is this target? What kind of aggressive behavior can we get away with without triggering alarms?
On a system with minimal security monitoring, Void Link might behave aggressively. It could scan ports, run network diagnostics, perform reconnaissance, enumerate systems, test credentials. It acts like an attacker would act if they had direct access to the machine.
But on a heavily defended system with sophisticated monitoring, Void Link behaves differently. It becomes extremely quiet. It reduces unnecessary system calls. It minimizes memory usage. It avoids suspicious patterns. It basically goes into hibernation mode, maintaining a light footprint while waiting for opportunities to act.
This adaptive behavior is the intelligence component that makes Void Link genuinely dangerous. Most malware follows a fixed playbook. Void Link adapts its playbook to the defense posture it encounters. That's the kind of sophistication you'd expect from a government-backed development effort.
The implications here are serious for incident responders. Traditional detection based on behavioral signatures becomes less effective. You can't just look for "malware doing malicious things" because this malware specifically avoids doing obviously malicious things when it detects it might get caught.
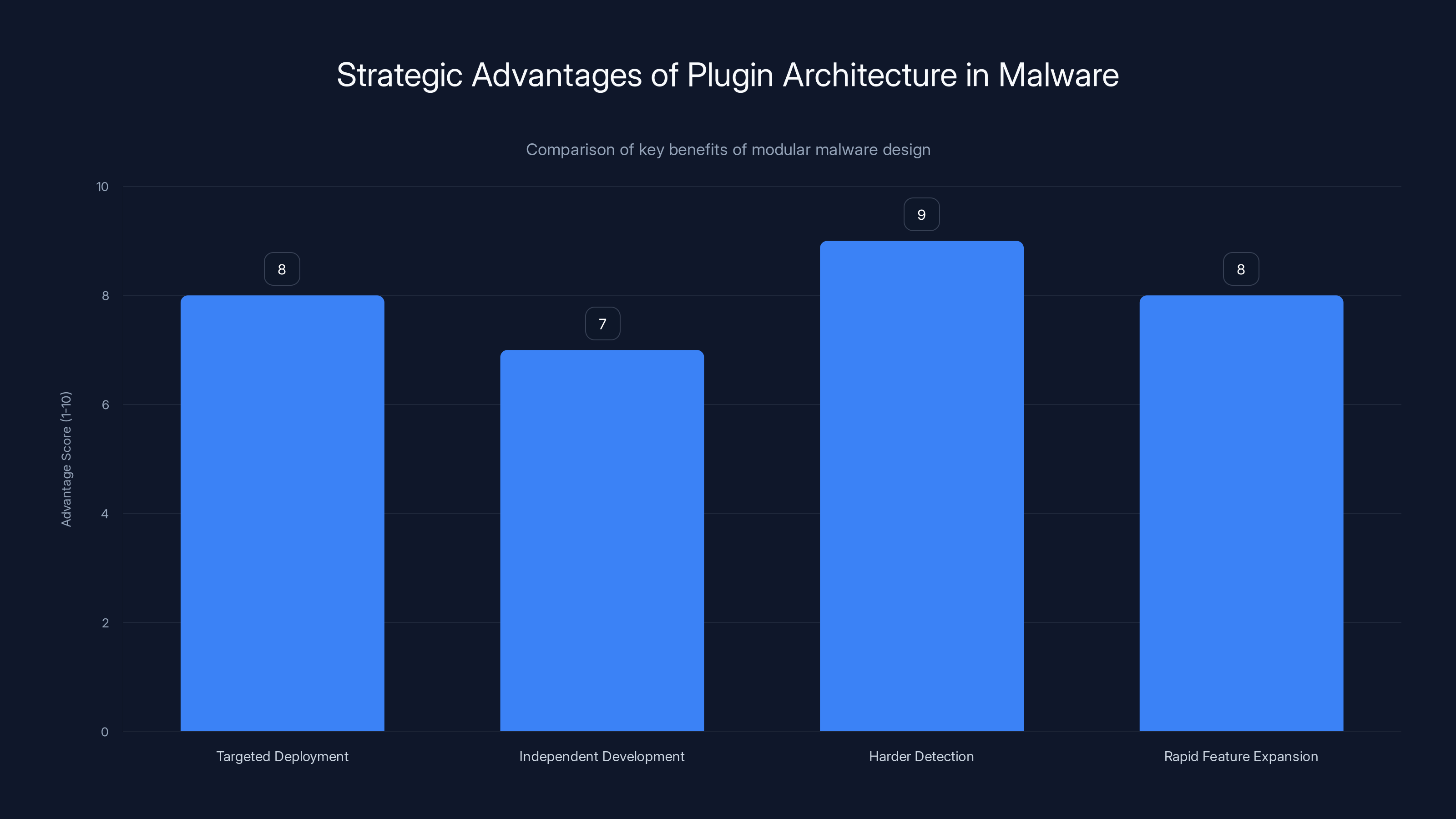
The plugin architecture in malware like VoidLink offers significant strategic advantages, including targeted deployment and harder detection, with estimated scores reflecting their impact. Estimated data.
The Attribution Question: Why Experts Believe This Is State-Backed
One of the most significant conclusions from the Check Point analysis is the attribution to Chinese state-affiliated actors. This isn't accusation. This is evidence-based analysis. So what actually points to state-backed development?
Resource allocation is the first clue. Creating 30+ functional plugins for a sophisticated malware framework requires significant development resources. You need programmers, testers, infrastructure, operational security, time. This isn't something a criminal gang throws together in a weekend. This requires funding and organizational structure.
Code sophistication is the second clue. The malware demonstrates deep knowledge of cloud platform internals, container technologies, credential management systems, and evasion techniques. Writing code that sophisticated requires experienced developers who have worked with these systems professionally. You don't learn Kubernetes exploitation by reading tutorials. You learn it by working with Kubernetes at scale.
Timing and targeting provide context clues. The malware specifically targets cloud infrastructure, which is where critical data lives for most governments and enterprises. A criminal group might target anything for profit. A state-backed operation targets strategic assets with strategic purpose.
The lack of monetization is revealing. Typically, if criminal groups create malware, they start exploiting it immediately. They sell access on underground forums. They demand ransoms. They exfiltrate data. Void Link shows no evidence of any of this. It's being developed but not deployed for profit. That's consistent with state actors who are building tools for future operations, not immediate financial gain.
The Chinese connection specifically comes from several indicators. Check Point researchers identified artifacts in the code that point to Chinese developers. This could be language-specific patterns, code structure similarities to known Chinese malware, infrastructure overlaps, or other technical indicators. Government attribution is never 100% certain, but the evidence appears credible.
Assuming the attribution is correct, what's the strategic goal? If China is developing this malware, why now and for what purpose?
The most likely explanation is cyber-espionage. Cloud environments contain sensitive data: source code, intellectual property, research data, communications, financial information. The ability to access these systems stealthily would be enormously valuable for intelligence purposes. A nation state could use Void Link to maintain persistent access to critical infrastructure and private company systems for years, harvesting intelligence continuously.
Persistent access is another probable goal. Rather than one-off attacks that get detected and cleaned up, state actors want long-term presence. Void Link's design suggests it's built for establishing presence that can persist for months or years, continuing to steal data and maintain influence over compromised infrastructure.
The Plugin Architecture: Modular Danger
The fact that Void Link uses a plugin-based architecture deserves deeper analysis because it reveals strategic thinking about malware deployment and evolution.
Traditional malware is monolithic. Everything is in the main executable. You compromise a system, the entire payload installs, the entire feature set activates. This approach has problems. It's inefficient because you're installing capabilities you might not need. It's risky because every installed component is a potential detection vector. It's inflexible because adding new features requires recompiling and redeploying the entire malware.
Void Link bypasses all these limitations through modularity. The core is lightweight. It handles system communication and plugin management. Then, plugins handle specific functions. A plugin might handle credential harvesting. Another handles network reconnaissance. Another handles persistence mechanisms. Another handles data exfiltration.
This approach offers several strategic advantages:
Operators can deploy only the plugins needed for specific targets. A system where you're conducting reconnaissance gets different plugins than a system where you're maintaining persistent access.
New plugins can be developed and deployed without recompiling the entire malware. If developers discover a new vulnerability or create a new exploitation technique, they can develop a plugin for it and distribute it to deployed instances without disrupting operations.
Detection becomes harder because security researchers analyzing the malware might only see one or two plugins deployed on a particular system, not the full range of capabilities available.
Each plugin can be developed somewhat independently, allowing for parallel development efforts and faster feature expansion. Different teams can work on different plugins simultaneously.
Versioning and staging become possible. You can deploy version 1.0 of a plugin to test systems, then deploy version 2.0 with refinements to production systems once testing confirms stability.
The Check Point report identified over 30 different plugins. That's a massive plugin ecosystem. Each represents development effort, testing, operational integration, and maintenance. The scope of this project is enormous.
What kinds of plugins are we likely talking about? Based on typical malware architecture and the described use cases, you'd expect something like this:
- Credential harvesters that extract API keys, tokens, passwords from cloud metadata and configuration files
- Reconnaissance modules that map network topology, enumerate systems, identify valuable targets
- Persistence mechanisms that ensure the malware survives system reboots and security updates
- Lateral movement plugins that help spread the compromise from the initial target to other systems
- Data exfiltration modules that package and transmit stolen data back to command and control
- Container escape plugins that breakout of Docker or Kubernetes sandboxes to access the underlying host
- Privilege escalation exploits that gain root or elevated permissions
- Anti-analysis tools that detect and interfere with malware analysis attempts
- Backup and disaster recovery exploitation plugins that target backup systems where all data is centralized
- Log deletion modules that clear security logs to hide evidence of compromise
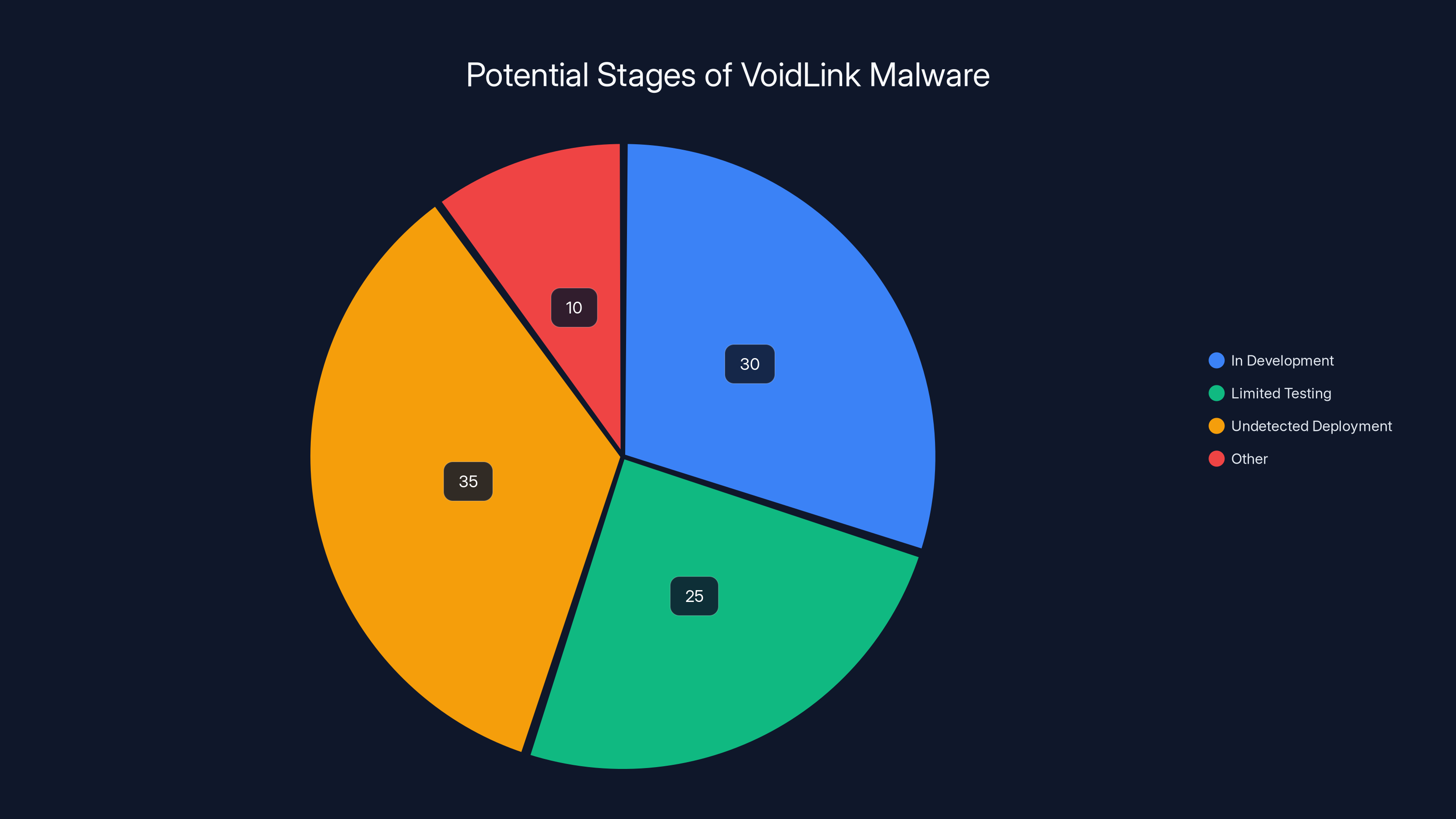
Estimated data suggests that VoidLink is most likely in undetected deployment (35%) or still in development (30%). Limited testing accounts for 25%, while other possibilities cover 10%.
The No Wild Exploitation Mystery: What Does It Mean?
Here's where the analysis gets really interesting and genuinely concerning. Void Link has been discovered before it's been deployed in any confirmed attacks in the wild. This is unusual and important.
Most malware gets discovered when it's actively being used. Researchers detect attacks, analyze the malware, publish findings. The discovery follows exploitation.
With Void Link, the order is reversed. Researchers discovered the malware through threat intelligence, likely through analysis of code samples or infrastructure before it saw large-scale use. The exploitation hasn't happened yet on any confirmed scale.
This creates an interesting situation. There are a few possible explanations:
First possibility: The malware is still in development. The developers might not be ready to deploy it yet. They're still adding features, testing in controlled environments, working out bugs, building out the command-and-control infrastructure. The timeline mentioned shows development activity through late 2025, which is recent. They might be planning deployment for 2026 or later.
Second possibility: The malware is being tested in limited environments. Developers might be running it against test systems or a small number of carefully selected targets to validate that everything works correctly before rolling out to full operational status. This kind of careful testing is consistent with state-backed development where you want to ensure reliability before committing resources.
Third possibility: The malware is already deployed but hasn't been discovered yet. This is perhaps the most unsettling possibility. Victims might be compromised and not know it. The malware might be sitting quietly on hundreds or thousands of systems, harvesting data, waiting for the day when its operators activate it for a specific operation. An organization could be infected and have no idea.
Fourth possibility: The malware is designed for future use in a specific operation. The developers might be creating it for a particular objective that hasn't been executed yet. Intelligence gathering before a military operation, economic espionage targeting specific industries, preparation for disruptive cyberattacks on critical infrastructure. The malware is ready, waiting for the operation to commence.
The Check Point researchers concluded that the developers likely intended to either sell or rent the framework in underground markets, or develop it for a single well-paying client. The fact that it's not already circulating in criminal markets suggests the second scenario: this is custom development for a high-value client with specific operational needs.
What worries security professionals is the preparation phase we might be witnessing. Nation states don't develop sophisticated cyber weapons randomly. They develop them for operations. If Void Link is currently being finalized, that suggests operations that would employ it might be planned for the near future.
Targeting Profile: Who's Actually at Risk?
Void Link's design characteristics tell us a lot about who's most likely to be targeted.
Cloud infrastructure operators are the primary target. Companies running significant operations on AWS, Azure, Google Cloud, or other major cloud providers are at risk. This includes both private companies and government agencies. Basically, if you're using public cloud infrastructure, you're in the potential target zone.
Dev Ops engineers and cloud administrators are individually at risk. These are the people who have credentials and access to cloud infrastructure. If Void Link can compromise a Dev Ops engineer's system, it gains the credentials and access that engineer has. For someone managing critical cloud infrastructure, that could mean access to everything.
Development organizations are vulnerable. Void Link targets Git credentials, which means it's designed to steal access to source code repositories. Development organizations that have valuable intellectual property or security-sensitive code are targets.
Organizations handling sensitive data in the cloud are high-value targets. Financial institutions, healthcare organizations, government agencies, critical infrastructure operators. Anywhere sensitive data is stored in cloud systems.
Organizations with inadequate cloud security are especially vulnerable. Void Link's adaptive behavior means it's harder for well-defended targets, but easier for those with minimal cloud security. If you don't have strong cloud security practices, you're more at risk.
Small and medium businesses might actually be at higher risk than enterprises. Why? Because large enterprises typically have substantial security budgets and teams. Small and medium businesses might have cloud infrastructure but minimal security monitoring or incident response capabilities. Void Link could operate quietly on an SMB's systems for a long time before detection.
Geographically, organizations outside China might be more likely targets. A Chinese government actor developing this malware would presumably have different legal and operational constraints regarding targeting domestic Chinese infrastructure compared to foreign infrastructure.
Industries of particular concern include:
- Technology companies with valuable source code and intellectual property
- Financial services institutions with access to banking systems
- Telecommunications providers with access to communications infrastructure
- Defense contractors with military technology and weapons systems
- Critical infrastructure operators including power, water, transportation
- Pharmaceutical companies with research data and clinical trial information
- Research institutions with government or commercially valuable data
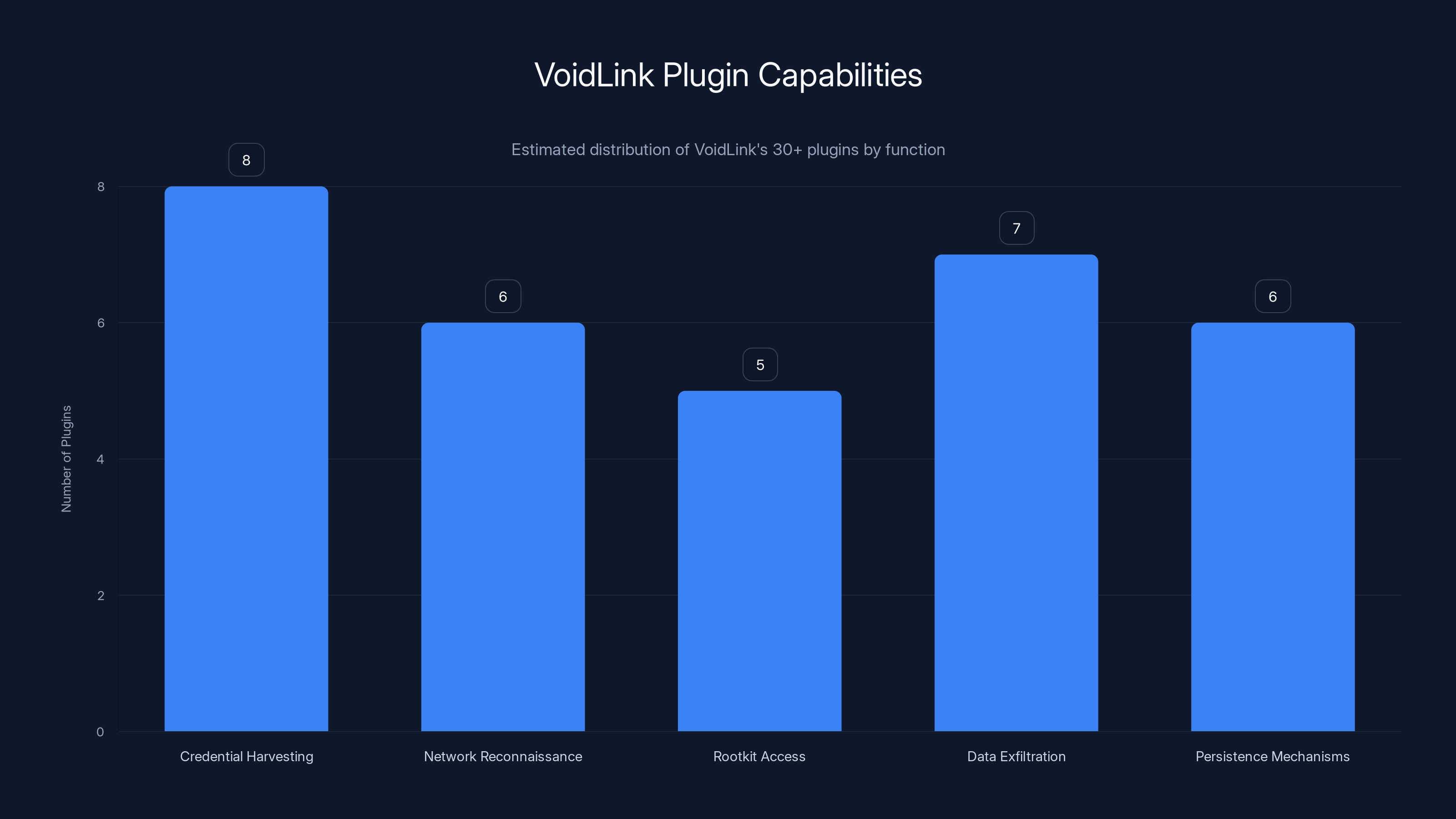
VoidLink's modular architecture includes over 30 plugins, with significant focus on credential harvesting and data exfiltration. Estimated data based on typical malware capabilities.
Credential Theft: The Real Power of Void Link
When we talk about Void Link's capabilities, credential harvesting is arguably the most powerful and dangerous aspect. Understanding why requires understanding how cloud security actually works.
Cloud providers like AWS don't authenticate humans. Well, they do, but that's not how the critical infrastructure works. Cloud infrastructure authenticates programmatically using API credentials. These are long strings of characters that act like passwords for code to authenticate to cloud services.
Every system running on AWS might have access to AWS credentials. These credentials grant permissions to perform actions in AWS, like reading from databases, writing to storage, launching virtual machines, modifying security groups, or deleting resources.
If Void Link steals those credentials, the attacker doesn't need the original system anymore. They can use the stolen credentials from anywhere in the world. They can make API calls directly to AWS with those credentials and perform whatever actions the credentials allow.
This is the nightmare scenario. Imagine a developer at a financial services company has AWS credentials that grant access to databases containing customer account information, social security numbers, financial data. That developer's laptop gets compromised by Void Link. The malware harvests the credentials. The attacker now has direct access to that sensitive data. It's not just about the developer's laptop. It's about every system and resource the developer has access to.
Multiplied across an organization, this becomes catastrophic. If Void Link compromises multiple systems within a company, it harvests the credentials from all of them. It maps out who has access to what. It identifies the highest-value credentials. It potentially creates a map of the entire organization's cloud infrastructure and who has access to each component.
Cloud security best practices recommend rotating credentials frequently, using strong authentication, limiting credential scope, and monitoring credential usage. But many organizations don't follow these practices well. Credentials might be reused across multiple systems. Credentials might be stored in configuration files in source code repositories. Credentials might be older and never rotated.
Void Link is specifically designed to exploit these weaknesses.
The Command and Control Infrastructure: How Void Link Communicates
For a malware to be useful to attackers, it needs to communicate with the people operating it. Void Link, being a command-and-control platform, has infrastructure for this communication.
The specifics of the command-and-control infrastructure aren't fully detailed in available reporting, but we can infer some things from the malware's architecture. The malware likely has hardcoded addresses for command-and-control servers where it sends harvested data and receives commands.
These communication channels need to be stealthy. If security researchers can identify the command-and-control servers, they can block them, interrupt the attacker's operations, and begin tracking the infrastructure. The malware would use encryption to obscure the data being transmitted. It might use steganography to hide malicious commands inside apparently innocent network traffic. It might use domain fronting to make malicious traffic look like legitimate traffic to popular websites.
The command-and-control infrastructure would likely be distributed across multiple servers in different jurisdictions, making it harder to disrupt. If one server is taken down, others continue operating.
Operators would need to manage infrastructure for receiving stolen data, which could be substantial. If this malware is deployed on hundreds or thousands of systems, each exfiltrating data continuously, the infrastructure needs to handle significant data volumes.
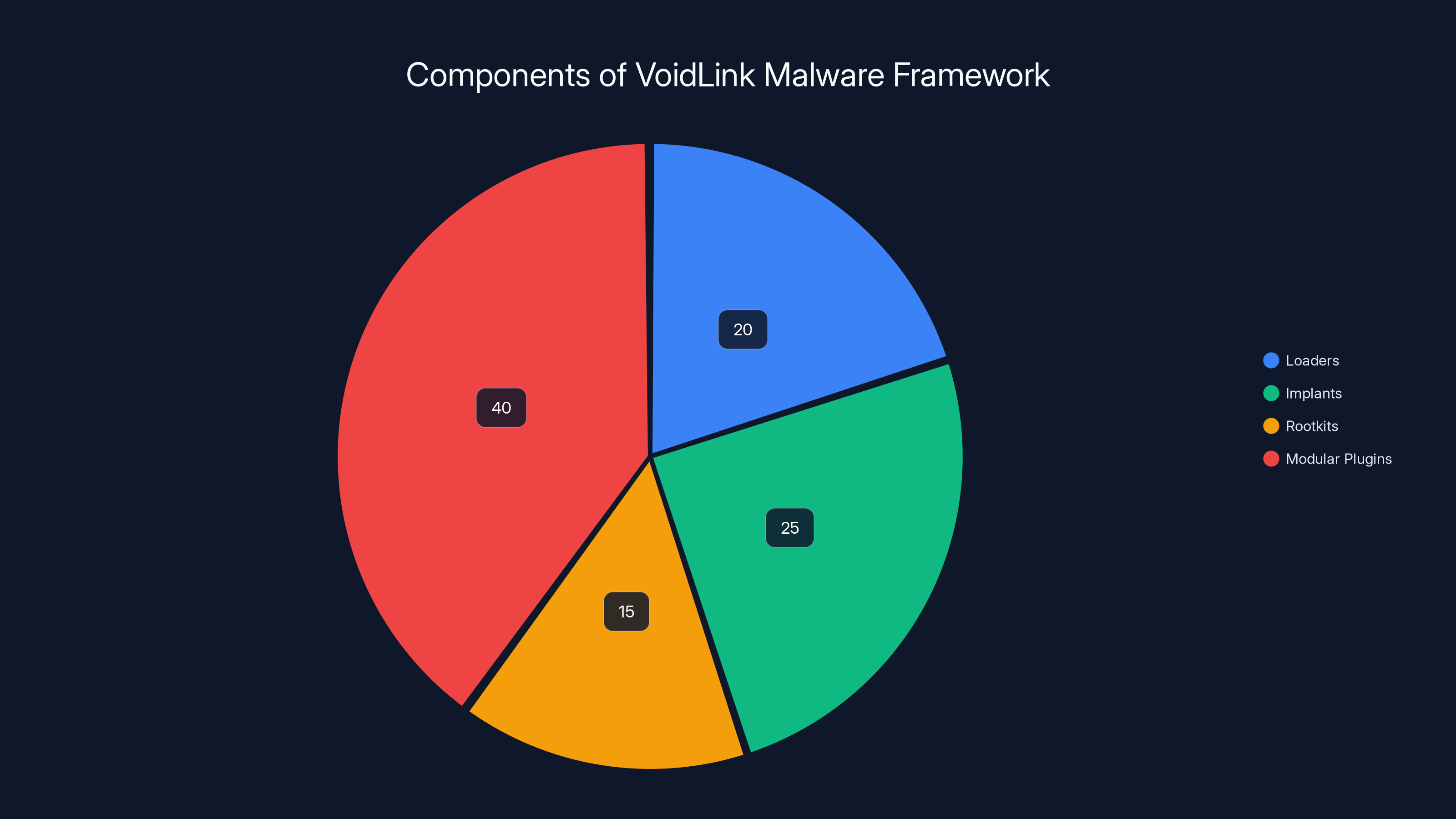
VoidLink's framework is estimated to have a significant portion dedicated to modular plugins, indicating a highly adaptable and customizable malware design. Estimated data.
Detection Challenges and Why This Malware Is Hard to Find
Given Void Link's design, security teams face significant detection challenges. Let's talk about why.
First, the adaptive behavior makes signature-based detection unreliable. Traditional antivirus and endpoint detection systems look for known malware signatures, known malicious behavior patterns. Void Link specifically modifies its behavior based on what security tools it detects. On a system running aggressive security monitoring, it behaves differently than on a system with minimal monitoring. Traditional signature-based detection assumes consistent malware behavior.
Second, the modular architecture means different systems might show different indicators. A system with the credential harvesting plugin looks different than a system with the reconnaissance plugin looks different than a system with the persistence mechanism. Security researchers analyzing a single infected system might see evidence of one plugin but not the full scope of what Void Link can do.
Third, the cloud-targeting nature means traditional endpoint security might not catch it. Endpoint detection and response tools focus on the endpoint. But Void Link's real danger is what it does in cloud systems. If the malware is quiet on the endpoint and active in cloud APIs, endpoint tools miss it. You need cloud-level monitoring to detect Void Link's actual malicious activity.
Fourth, legitimate tools complicate detection. Cloud administrators legitimately access cloud credentials. Developers legitimately access Git repositories. Legitimate systems legitimately make API calls. The malware is leveraging legitimate cloud functionality for malicious purposes. Distinguishing malicious use from legitimate use requires sophisticated behavioral analytics, which many organizations lack.
Fifth, the lack of file-system indicators is a detection problem. If the malware stays in memory and doesn't write to disk, traditional file-based antivirus scans miss it. Memory-resident malware is harder to detect than file-based malware because you need live memory analysis, not just file scanning.
Sixth, the stealth mechanisms specifically target detection tools. The malware actively looks for security tools and avoids triggering them. If your detection method is known to the malware developers, they've probably engineered the malware to avoid it.
These detection challenges are why security professionals are concerned about a malware that's under development but not yet deployed at scale. Once it's unleashed, early detection might be difficult, giving attackers time to operate undetected.

Incident Response Implications: What Organizations Need to Do
Assuming that Void Link or similar malware might already be in an organization's infrastructure, what should incident response teams actually do about it?
First, assume compromise. This is a security principle called "assume breach." Don't assume your organization is safe. Assume attackers have already compromised you and work from there. This changes your priorities. Instead of focusing purely on prevention, you focus on detection and response.
Second, implement detection mechanisms that would catch this specific malware. This means monitoring cloud API usage for unusual activity. You should see spikes in API calls that don't match normal usage patterns. You should detect credentials being used from unusual locations or unusual systems. You should monitor for connections to unknown command-and-control servers.
Third, implement cloud security monitoring. Most organizations have excellent endpoint security but terrible cloud security monitoring. You need to know who's accessing your cloud infrastructure, from where, using what credentials, and doing what. Cloud-level monitoring is essential for detecting a malware like Void Link.
Fourth, audit credentials and access controls. Review who has access to what in your cloud infrastructure. Implement the principle of least privilege: each person and system should have only the minimum access needed to do their job. If Void Link steals credentials, limiting the scope of stolen credentials limits the damage.
Fifth, implement detection at the container and Kubernetes level. Void Link specifically targets containerized environments. Your container orchestration platforms need security monitoring to detect suspicious behavior.
Sixth, hunt for indicators of compromise. This is the proactive approach to detection. Rather than waiting for alerts, security teams actively search systems for evidence of Void Link infection. This might involve searching for known malware signatures, looking for suspicious plugins, analyzing process execution history, reviewing network traffic logs.
Seventh, prepare an incident response plan specifically for this type of threat. When (not if) a compromised system is discovered, organizations need procedures for isolation, evidence collection, impact assessment, and remediation.
The Broader Threat Landscape: Where Void Link Fits
Void Link doesn't exist in isolation. It's part of a broader pattern of sophisticated cyber threats, particularly from Chinese state-backed actors.
Over the past several years, we've seen multiple sophisticated attack frameworks attributed to Chinese government entities. These include Volt Typhoon, which targeted critical infrastructure with a focus on persistence rather than immediate exploitation. We've seen Chinese state actors conducting sophisticated supply chain attacks, compromising software companies to distribute malware to downstream customers.
Void Link fits into this pattern. It's sophisticated. It's designed for long-term persistence and espionage. It targets critical infrastructure and valuable information. It shows evidence of significant resources and expertise.
The threat landscape is increasingly characterized by state-backed malware that's more sophisticated than criminal malware. Criminal malware wants to monetize quickly. State malware wants to establish long-term access for strategic purposes.
Void Link is state malware. It's designed for long-term espionage, intelligence gathering, and operational access. It's not trying to steal credit card data and sell it quickly. It's trying to establish persistent presence and harvest valuable intelligence continuously.
This raises the stakes for defenders. You're not defending against criminal gangs trying to make money quickly. You're defending against nation states with massive resources, expert developers, and strategic patience. The threat is more sophisticated and the stakes are higher.
What Cloud Providers Are Doing About It
Cloud providers are aware of threats like Void Link. AWS, Microsoft Azure, Google Cloud Platform, and others have security teams constantly monitoring for malicious activity.
Cloud providers implement controls that make it harder for malware to operate freely. They monitor for credential misuse. They implement anomaly detection that identifies unusual API usage patterns. They require multi-factor authentication for sensitive operations. They provide audit logging that tracks all activity within cloud environments.
But cloud providers also face limitations. They can't prevent customer credentials from being stolen. If a developer's laptop gets compromised and Void Link steals their AWS credentials, that's happening on the customer's side, not AWS's side. AWS's controls only protect against unauthorized use of credentials, not theft of credentials.
This is why the burden of defense falls on both cloud providers and their customers. Cloud providers provide the infrastructure for security. Customers need to implement practices that take advantage of that infrastructure.
Industry Response and Recommendations
The security industry has responded to the Void Link discovery with recommendations for organizations to harden their defenses against this threat.
The consensus recommendations include:
-
Implement strong cloud security practices: Use multi-factor authentication, enforce strong passwords, implement privileged access management, rotate credentials regularly, limit credential scope
-
Deploy cloud security monitoring: Implement detection mechanisms that would catch unusual cloud API usage, credential theft, or lateral movement within cloud environments
-
Segment cloud infrastructure: Isolate critical systems and data from general infrastructure so compromise of one system doesn't automatically grant access to everything
-
Monitor container and Kubernetes environments: If you're running containerized workloads, implement security monitoring at that level to detect escape attempts or malicious activity
-
Implement endpoint detection and response: Deploy EDR solutions that can detect malware infection at an earlier stage than traditional antivirus
-
Audit access controls regularly: Review who has access to what and implement least privilege principles
-
Prepare incident response procedures: Have procedures ready for detecting, containing, and remediating compromise
-
Stay informed about threats: Subscribe to threat intelligence feeds that would alert you if Void Link or similar malware appears in the wild
Timeline Concerns: The Timing Question
One detail that stands out is the development timeline. Void Link shows active development through late 2025. This is a recent discovery, meaning the malware was being actively improved and modified very recently.
For an organization to actively develop sophisticated malware for months or years and then not deploy it suggests strategic patience. They're waiting for something. They're waiting for the right moment, the right targets, or the right operational trigger.
This could mean several things:
First, major cyber operations might be planned for the near future. The malware is ready. It's being held as a tool for operations that haven't commenced yet. When those operations start, Void Link might be deployed at significant scale.
Second, specific high-value targets might be under development. Rather than deploying broadly, operators might be carefully identifying the highest-value targets and crafting specifically tailored deployments for each one.
Third, operational security might demand delayed deployment. Developing something and deploying it too quickly creates detection risk. Waiting between development and deployment makes the connection between developers and operators harder to trace.
Fourth, geopolitical factors might be relevant. Operations might be timed to specific geopolitical events or timelines. The malware is ready, waiting for geopolitical conditions that trigger operational deployment.
None of this is certain speculation. But the fact that a sophisticated malware framework shows recent development activity without corresponding deployment activity is concerning for security professionals tasked with defense.
Practical Defense: What Organizations Can Do Right Now
Assuming your organization operates cloud infrastructure and is concerned about Void Link-like threats, what should you do right now?
Immediate actions:
-
Audit your cloud IAM policies: Review who has what access and reduce access to the minimum necessary for their role
-
Enable MFA on all cloud accounts: Multi-factor authentication makes credential theft less useful because stolen passwords alone don't grant access
-
Implement cloud security monitoring: Deploy tools that monitor for unusual API usage patterns, suspicious credential usage, or anomalous behavior
-
Review your credential management practices: Stop storing credentials in code, configuration files, or documentation. Use centralized secret management
-
Scan for existing indicators of compromise: Look for signs of intrusion that might have occurred before Void Link's discovery
-
Review container security: If you're using Docker or Kubernetes, implement security monitoring at the container level
-
Prepare incident response procedures: Have a plan ready for the day a system is confirmed compromised
Medium-term actions:
-
Implement zero-trust security architecture: Assume no user or system is trustworthy and verify everything
-
Deploy endpoint detection and response: EDR tools help catch malware before it establishes persistence
-
Implement network segmentation: Isolate critical systems and data from general infrastructure
-
Develop threat hunting capabilities: Proactively search for signs of compromise rather than waiting for alerts
-
Establish threat intelligence programs: Subscribe to feeds that would alert you if Void Link appears in the wild
These aren't special actions just for Void Link. These are fundamental cloud security practices that would protect against Void Link and many other threats.

The Future of Linux Malware in Cloud Environments
Void Link likely represents the beginning of a trend rather than an isolated threat. Linux is dominant in cloud environments. Containers run Linux. Cloud servers run Linux. As more critical infrastructure moves to the cloud and depends on Linux, Linux becomes a more valuable target.
We should expect to see more sophisticated Linux malware designed specifically for cloud environments. Malware that understands Kubernetes, that targets container escape vulnerabilities, that exploits cloud-specific weaknesses.
The sophistication will likely increase. Just as Windows malware has become increasingly sophisticated over decades, Linux malware in cloud environments will likely become more advanced.
Defense needs to evolve accordingly. Traditional Linux security practices designed for on-premises systems won't adequately protect cloud-based Linux systems. New detection mechanisms, new monitoring approaches, new architectural patterns will be necessary.
Organizations that don't adapt their security posture to address cloud-specific threats will be increasingly vulnerable. This is less about being attacked by Void Link specifically and more about being vulnerable to a whole class of sophisticated cloud-targeting malware.
What Happens When Void Link Is Actually Deployed?
This is the nightmare scenario security professionals worry about. Let's game it out.
Scenario: Void Link is discovered on a government agency's systems. Investigators determine the malware has been present for eight months. In that time, it's compromised dozens of systems including those of developers, administrators, and sensitive-area staff.
The malware harvested AWS credentials from multiple systems. Using those credentials, attackers accessed databases and repositories containing classified information. The scope of compromise is determined to be massive. Sensitive intelligence has been stolen. The damage assessment takes months.
The incident triggers law enforcement investigation, congressional hearings, potential criminal charges. Other government agencies audit their own systems, discovering similar compromise. Private companies with similar infrastructure discover their own infections. The incident becomes a significant national security issue.
When Void Link actually enters the wild and starts causing real damage, it will likely trigger significant geopolitical consequences. The discovery of a sophisticated state-backed malware causes diplomatic incidents, sanctions, and retaliatory action. The targeting of critical infrastructure causes operational disruption.
This is what makes Void Link's current development stage significant. We have opportunity to defend. Once it's deployed, the damage is largely done and remediation becomes crisis management.

FAQ
What is Void Link and how is it different from other Linux malware?
Void Link is a sophisticated command-and-control platform framework discovered by Check Point Research that's specifically designed for cloud environments. Unlike typical malware that behaves the same across all systems, Void Link adapts its behavior based on what security tools it detects, features over 30 modular plugins that can be deployed independently, and is designed to target cloud infrastructure and harvest cloud credentials. The combination of sophistication, modularity, and cloud specialization makes it significantly more dangerous than typical Linux malware.
Who is believed to have developed Void Link and what are the indicators?
Security analysis indicates Void Link was developed by Chinese state-affiliated actors based on several factors including the significant development resources required to create 30+ functional plugins, sophisticated understanding of cloud platforms and container technologies visible in the code, targeting of strategic assets rather than random profit-seeking, and lack of any monetization efforts suggesting development for state purposes rather than criminal profit. The extensive development effort and strategic focus are consistent with state-backed development rather than criminal malware.
How does Void Link's cloud-first architecture make it particularly dangerous?
Void Link is dangerous because it was built specifically for cloud environments rather than adapted to them, automatically detects which cloud provider it's running on and adjusts tactics accordingly, harvests cloud credentials and API keys that grant access to sensitive data and infrastructure, targets containerized environments like Docker and Kubernetes which are increasingly critical, and adapts its behavior based on detected security tools. This cloud specialization means it exploits weaknesses specific to cloud environments that traditional security tools weren't designed to defend against.
What makes Void Link so stealthy and hard to detect?
Void Link employs multiple evasion techniques including profiling host systems to detect security tools, calculating a risk score that determines how aggressively it behaves based on detected defenses, reducing suspicious behavior on heavily monitored systems and being extremely quiet on defended infrastructure, using modular architecture so different systems might show different indicators, and avoiding obvious file-system artifacts by operating primarily in memory. These techniques combined make it extremely difficult for traditional antivirus and endpoint security to detect.
Why is it concerning that Void Link hasn't been deployed in the wild yet?
The absence of confirmed wild deployment despite active recent development suggests the malware is either still being refined and tested, being prepared for a specific future operation, already deployed but not yet discovered on victims' systems, or ready for sale to other actors. Any of these scenarios is problematic because it suggests either imminent deployment, ongoing undetected compromise, or future large-scale attacks. The development without deployment indicates preparation for something significant.
What credentials and secrets does Void Link specifically target and harvest?
Void Link targets AWS access keys and credentials, Azure authentication credentials, Google Cloud Platform service account keys, API tokens for cloud platforms, Git repository credentials that developers store locally, cloud metadata containing API credentials, environment variables containing tokens and secrets, and application-level secrets that might grant access to databases or other systems. Harvesting these credentials effectively gives attackers access to all the systems and data those credentials can access, making the scope of potential damage enormous.
How should organizations prepare for or defend against Void Link?
Organizations should immediately enable multi-factor authentication on all cloud accounts, implement cloud security monitoring that tracks API usage for anomalies, audit and reduce cloud IAM permissions to least privilege, implement proper credential management using secret vaults rather than environment variables or configuration files, deploy endpoint detection and response tools, implement container and Kubernetes security monitoring, and prepare incident response procedures for the scenario where malware is discovered on systems. These practices provide general defense against Void Link and similar threats.
What is the expected timeline for Void Link deployment if it hasn't been deployed yet?
There is no confirmed timeline for deployment. The malware shows active development through late 2025, suggesting operational readiness is imminent, but deployment timing depends on factors including when operators believe targets are sufficiently vulnerable, geopolitical circumstances that might trigger operations, completion of testing and refinement, preparation of target-specific variants, and construction of command-and-control infrastructure. Security professionals assume defensive measures are needed now rather than waiting for deployment confirmation.
How does Void Link compare to other known state-backed Linux malware?
Void Link demonstrates characteristics similar to other state-backed malware like Volt Typhoon including emphasis on long-term persistence rather than quick exploitation, sophisticated understanding of target infrastructure, focus on stealth and avoiding detection, and apparent development for specific operational purposes. However, Void Link's cloud specialization and modular architecture represent evolution in state-backed malware design specifically adapted to modern cloud-native infrastructure and containerized workloads.
What role do cloud providers play in defending against Void Link?
Cloud providers implement security controls including credential anomaly detection, multi-factor authentication requirements, audit logging of all API activity, network monitoring for command-and-control communications, and security teams monitoring for malicious activity. However, cloud providers cannot prevent credentials from being stolen on customer systems, so customer responsibility is equally important. Defense requires both cloud provider security infrastructure and customer practices that take advantage of that infrastructure.
Void Link represents a critical inflection point in the malware threat landscape. It's a sophisticated tool developed by well-resourced actors specifically for attacking cloud infrastructure that forms the backbone of modern technology. The fact that it exists, is under active development, and shows no signs of wild exploitation yet suggests preparation for something significant.
The appropriate response isn't panic. It's action. Organizations should treat the discovery of Void Link as an urgent signal to audit and improve their cloud security posture. This means implementing the fundamental cloud security practices that would defend against Void Link and similar threats. It means deploying monitoring that would catch this malware operating. It means assuming compromise and preparing response procedures.
The advantages go to the prepared. Organizations that have strong cloud security practices in place, robust monitoring, and incident response procedures will be significantly better positioned if Void Link or similar malware targets them. Organizations that lack these fundamentals are at serious risk not just from Void Link but from the entire class of sophisticated cloud-targeting malware.
The window for preparation is now. As Void Link transitions from development to potential deployment, that window closes. The time to strengthen cloud security is before the attacks begin, not after.
Key Takeaways
- VoidLink is a sophisticated state-backed Linux malware framework with 30+ modular plugins specifically designed for cloud infrastructure attacks and credential theft
- The malware shows adaptive behavior that evades detection based on security tools present, making traditional signature-based detection unreliable
- Active development through late 2025 with no confirmed wild deployment suggests preparation for significant cyber operations in the near future
- Cloud credentials harvested by VoidLink could grant attackers access to entire organizations' sensitive data, making credential theft the primary attack vector
- Organizations can defend by implementing multi-factor authentication, cloud security monitoring, proper credential management, and incident response procedures immediately
Related Articles
- VoidLink: The Advanced Linux Malware Reshaping Cloud Security [2025]
- N8n Ni8mare Vulnerability: What 60,000 Exposed Instances Need to Know [2025]
- Target Data Breach 2025: 860GB Source Code Leak Explained [2025]
- Hackers Targeting LLM Services Through Misconfigured Proxies [2025]
- Kimsuky QR Code Phishing: How North Korean Hackers Bypass MFA [2025]
- Why Cybercriminals Are Getting Younger: The Crisis of 2025 [2025]
![VoidLink: The Chinese Linux Malware That Has Experts Deeply Concerned [2025]](https://tryrunable.com/blog/voidlink-the-chinese-linux-malware-that-has-experts-deeply-c/image-1-1768399918400.jpg)



