The VPN Crackdown Nobody Saw Coming (But Actually Everyone Did)
If you've been paying attention to digital rights over the past few months, you know the story. Iran tightened restrictions on VPN usage. Russia did the same. And suddenly, millions of internet users who relied on these tools to access information freely found themselves cut off, scrambling for alternatives.
But here's what makes this moment different from previous crackdowns: the technology companies themselves are getting involved. Windscribe, one of the more vocal VPN providers, made a public statement acknowledging the crisis and committing to develop solutions. Not vague promises. Specific ones. They're prioritizing support for Amnezia WG, an obscure protocol most people have never heard of.
Why should you care? Because what's happening in Iran and Russia isn't staying in Iran and Russia. Governments worldwide are watching these crackdowns, studying them, figuring out what works. If you live in a region with internet restrictions, or you're just interested in how authoritarian regimes are combating privacy technology, this story matters.
The situation reveals something uncomfortable: traditional VPN protocols are becoming easier to detect and block. ISPs and governments have gotten smarter. They're not just blocking IP addresses anymore. They're analyzing traffic patterns, identifying encryption signatures, and targeting specific protocols. It's a technological arms race, and VPN providers are playing catch-up.
Windscribe's decision to prioritize Amnezia WG isn't casual. It signals that the company understands the threat is real and immediate. Users in restricted regions need solutions now, not promises of solutions next quarter. This article breaks down everything you need to know about the crackdown, why it matters, and what Windscribe is actually doing about it.
Let's start with the basics, though. If you're not deeply familiar with how VPNs work or why governments block them, we need to establish that foundation first.
TL; DR
- Iran and Russia ramped up VPN blocking using advanced detection methods targeting standard protocols like Open VPN and Wire Guard
- Windscribe identified Amnezia WG as the solution because it obfuscates traffic to avoid detection by ISP-level filtering
- Amnezia WG combines Wire Guard's speed with obfuscation making it harder for governments to identify VPN usage
- Other VPN providers are watching closely and may adopt similar protocols to maintain functionality in restricted regions
- The crackdown accelerates protocol innovation pushing the industry toward stealth VPNs that disguise themselves as regular traffic

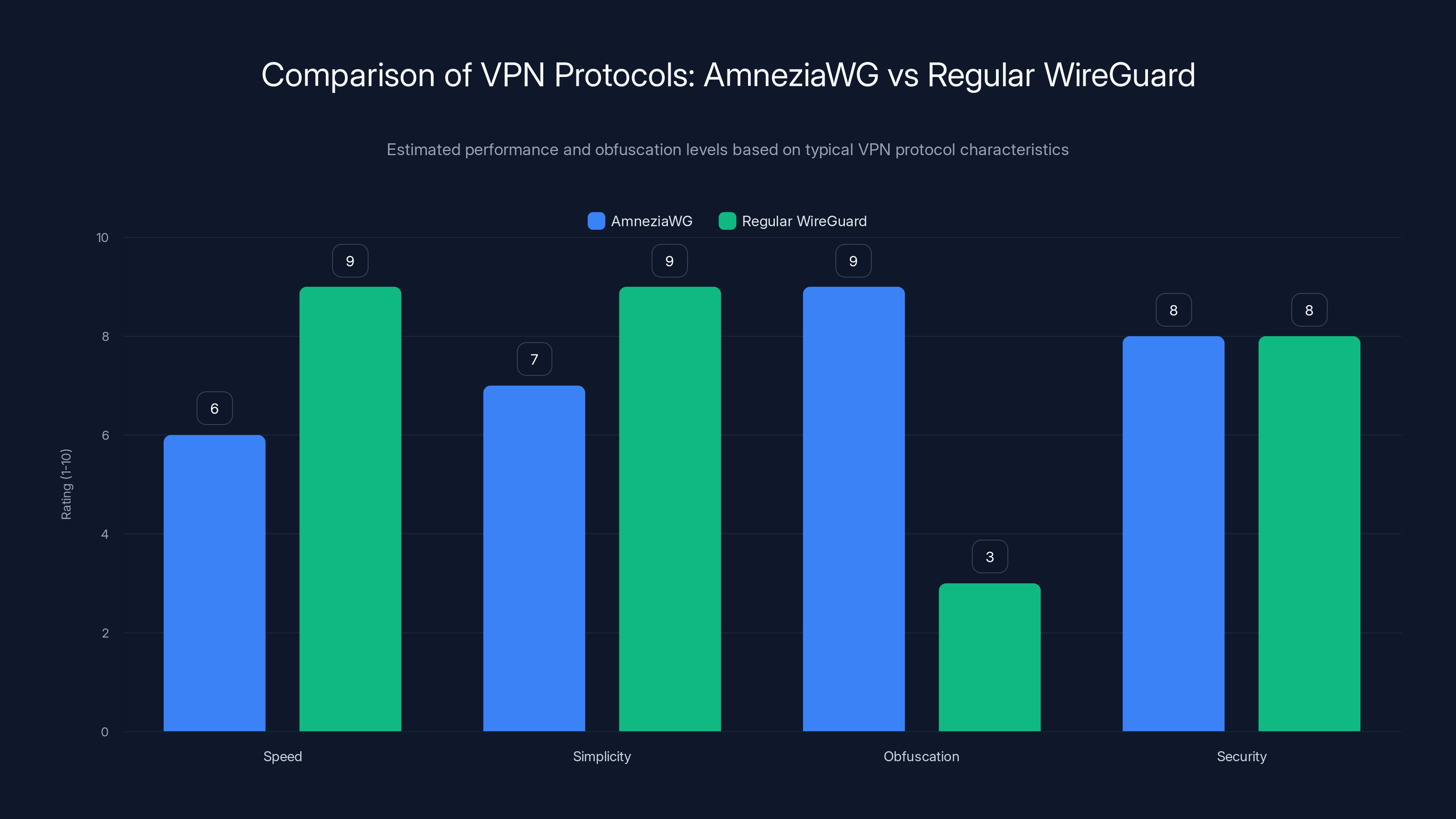
AmneziaWG offers higher obfuscation at the cost of speed compared to regular WireGuard, while maintaining similar security levels. (Estimated data)
Why VPNs Matter (And Why Governments Hate Them)
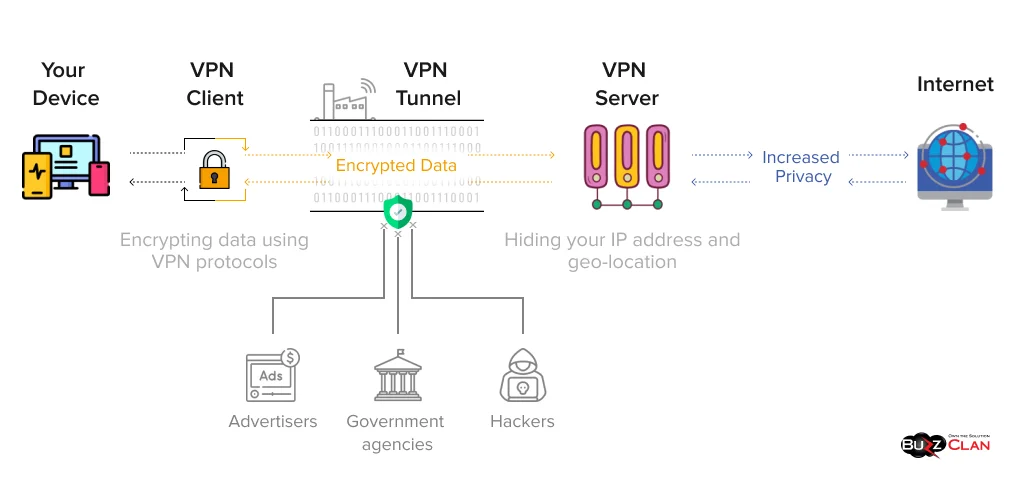
A VPN, or Virtual Private Network, does something deceptively simple: it encrypts your internet traffic and routes it through a server in another location. To anyone monitoring your connection (your ISP, your government, your employer), it looks like you're just connecting to a random server somewhere else. They can't see what websites you're visiting or what data you're transmitting.
For most people in open democracies, VPNs are optional tools. Privacy enthusiasts use them. Remote workers use them. People who value their online privacy use them.
But in countries with strict censorship laws, VPNs are lifelines. They're how journalists access banned news outlets. How students research topics their government deems dangerous. How activists coordinate without surveillance. They're infrastructure for freedom in places where free speech doesn't exist.
Iran understands this. Russia understands this. That's why they block them.
The challenge for governments is that VPNs are encrypted. Banning an encrypted connection is like trying to ban envelopes. You can see the envelope, you can see it's mail, but you can't see what's inside without opening it (decrypting it). That's the entire point.
So governments have to get creative. They can't read the traffic, but they can analyze it. They can look for patterns. They can identify specific VPN protocols by their traffic signatures.
Think of it this way: if you watch thousands of people walk into a building, you start to recognize behavioral patterns. Tall people walk a certain way. Short people walk another way. People carrying briefcases walk differently from people without them. Even if you can't see inside their briefcases, you know what kind of briefcase they're carrying by how they carry it.
That's exactly how advanced VPN blocking works. Governments analyze the traffic pattern, identify the protocol signature, and block it at the ISP level.
AmneziaWG offers a balanced trade-off with slightly slower speed than WireGuard but enhanced security due to obfuscation. Estimated data.
Understanding the Iran VPN Crackdown
Iran's relationship with VPNs has always been complicated. The government officially bans them, but enforcement has been inconsistent. Sometimes people use them freely. Sometimes they get blocked.
But starting in late 2024, something changed. The crackdowns became more aggressive. More systematic. More effective.
Reports from Freedom House and other digital rights organizations documented a significant spike in VPN blocking. Standard protocols like Open VPN became nearly unusable. Wire Guard, the newer, faster protocol, lasted longer but eventually fell victim to blocking as well.
What made this crackdown different was the sophistication. Iranian ISPs weren't just blocking known VPN IP addresses. They were implementing deep packet inspection (DPI) technology. This analyzes the actual structure of data packets to identify VPN usage regardless of which IP address is being used.
DPI can identify Open VPN traffic by looking at how the protocol structures its packets. It can recognize Wire Guard by its distinctive connection patterns. It's like a fingerprint. Different protocols have different fingerprints. Once the ISP learns the fingerprint, they can block it.
Users in Iran responded by switching VPN providers, trying different protocols, and exploring more obscure solutions. Traditional VPN providers found themselves scrambling to maintain service. Some, like Express VPN and Nord VPN, invested heavily in obfuscation technology. Others eventually exited the market in heavily restricted countries.
Windscribe didn't exit. Instead, they committed to finding solutions.
Russia's Parallel Crackdown and Different Tactics
Russia's approach to blocking VPNs shares similarities with Iran's but differs in crucial ways. Both use sophisticated detection technology. Both are increasingly aggressive. But Russia's crackdown is tied to specific geopolitical events.
Following Russia's invasion of Ukraine in 2022, the government intensified control over the internet. They blocked independent news outlets. They restricted access to foreign social media platforms. And they accelerated efforts to block VPNs, particularly after Western sanctions made people more likely to seek alternatives.
Russia's blocking methods include:
- IP address blocking: Maintaining a list of known VPN server IPs and blocking them at the ISP level
- Deep packet inspection: Similar to Iran's approach, analyzing traffic patterns to identify VPN usage
- Protocol-specific blocking: Targeting Open VPN and other known protocols
- SNI filtering: Analyzing the Server Name Indication in encrypted connections to identify VPN traffic
The Russian government has been particularly effective at blocking because they control most major ISPs. When they issue a decree to block something, ISPs comply quickly. There's no fragmented system like in democracies where some providers comply and others resist.
Interestingly, Russia's approach is slightly different from Iran's in execution. Russian authorities seem focused on blocking at the application layer—making VPN apps and services unusable—rather than just blocking at the network layer.
This means that even if users find workarounds to bypass the deep packet inspection, they might still struggle if the app itself is targeted. Sideloading becomes necessary. Older versions of apps that still work get passed around. It becomes a cat-and-mouse game.
By late 2024, both countries had made VPN usage substantially more difficult. For users who absolutely need circumvention tools, the options became fewer and the learning curve became steeper.
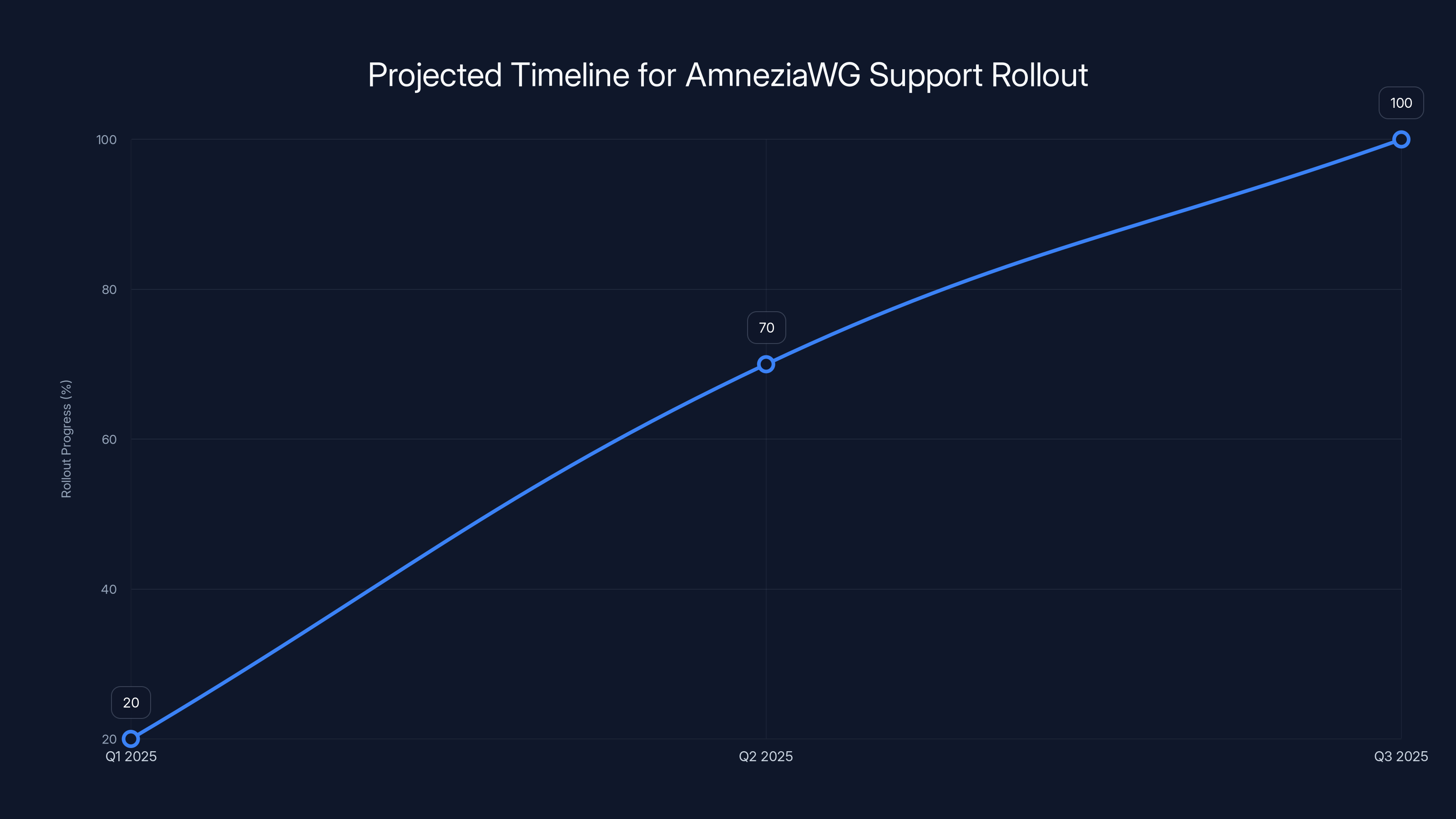
Estimated timeline for AmneziaWG support rollout: Beta testing in Q1 2025, wider availability in Q2 2025, and ongoing optimization from Q3 2025. Estimated data based on typical industry practices.
Windscribe's Response: A Public Commitment
Most VPN providers respond to crackdowns quietly. They push updates. They add new servers. They hope users figure it out.
Windscribe did something different. They made a public statement. They acknowledged the problem. They committed to specific solutions. And they explained why.
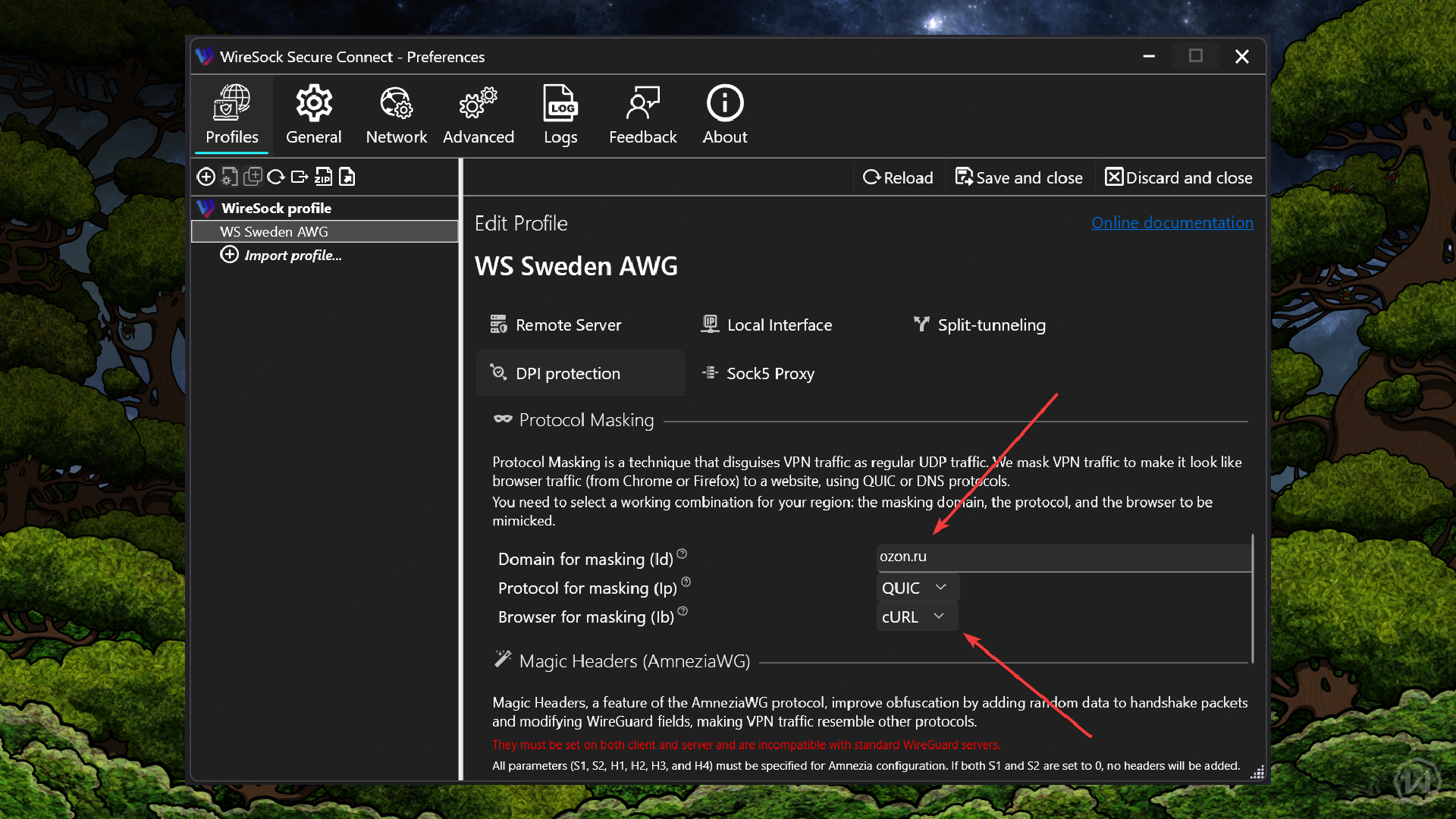
In public communications, Windscribe stated that they would prioritize supporting Amnezia WG protocol across their platform. This wasn't a vague promise to "improve service." It was a specific technical commitment with clear reasoning.
Why Amnezia WG specifically? Because it's designed to be invisible.
Most VPN protocols prioritize speed or simplicity or security. Amnezia WG prioritizes obfuscation. It wraps the Wire Guard protocol in additional encryption and traffic shaping that makes it look like regular internet traffic to anyone analyzing it.
Think of it like this: a traditional VPN is like sending a letter in a locked envelope. The letter (your data) is encrypted. The envelope makes it clear you've sent something. DPI is like someone saying: "I can't see inside the envelope, but I can tell it's an envelope, and you're not allowed to send envelopes."
Amnezia WG doesn't just lock the envelope. It disguises the envelope so it doesn't look like an envelope anymore. It looks like a regular package of newspapers. DPI can't even tell it's VPN traffic.
Windscribe's commitment to support Amnezia WG signals they understand this is the future of circumvention technology. Standard protocols aren't enough anymore. VPN providers need to actively obfuscate, disguise, and hide their traffic.
The company stated that Amnezia WG support would be their "highest priority." That's significant language. Not one of their priorities. The highest priority. For a company managing dozens of features and server locations, that's a major commitment.
But implementing Amnezia WG across a global VPN network isn't trivial. It requires:
- Protocol integration: Adding Amnezia WG support to their client applications across i OS, Android, Windows, mac OS, and Linux
- Server updates: Configuring all VPN servers to support the protocol
- Performance optimization: Ensuring the protocol performs adequately for users in restricted regions where connection speeds might already be compromised
- Testing: Rigorous testing in actual restricted environments to ensure it actually evades blocking
- User education: Helping users understand what Amnezia WG is and why they should use it
Each of these components is technically complex. Together, they represent a substantial engineering effort.
What Is Amnezia WG and Why It Actually Works
Let's talk specifics about why Amnezia WG is different from every other VPN protocol out there.
Wire Guard, released in 2019, was revolutionary. It was faster than Open VPN. It was simpler. It had fewer lines of code, which meant fewer potential security vulnerabilities. VPN providers immediately started adopting it.
But Wire Guard has a problem for users in restricted countries: it's detectable. Its traffic pattern is distinctive. ISPs and governments learned to recognize it quickly. By 2023-2024, Wire Guard blocking became common in Iran and Russia.
Amnezia WG takes Wire Guard and adds obfuscation. The underlying protocol is still Wire Guard—you get the speed and security benefits. But the traffic is disguised.
Here's how it works technically:
Wire Guard operates on UDP port 51820 by default. It sends packets with a distinctive structure. Anyone sniffing the network can recognize these packets as Wire Guard.
Amnezia WG wraps these packets. It adds junk data. It randomizes packet sizes. It changes the timing. To anyone analyzing the traffic, it looks completely different. It looks like regular internet traffic.
But that's not even the clever part. Amnezia WG also implements obfuscation tricks that make it look like encrypted traffic that isn't VPN. When DPI looks at the packets, it sees encryption (which it expects), but it doesn't see the VPN signature.
The result: ISPs and governments can't tell you're using a VPN. They can tell you're using some kind of encryption, but that's becoming increasingly common (HTTPS, TLS, etc.), so they can't just block all encryption.
Why didn't everyone just do this from the start? Because obfuscation adds overhead. It makes the connection slower. It makes the code more complex. For users in countries without blocking, these trade-offs aren't worth it.
But for users in Iran and Russia, the trade-off is obvious. Slower connection that works beats fast connection that doesn't work.
Amnezia WG is relatively new. It was developed specifically to address this problem. It's open-source, which means it's been reviewed by security researchers. It's been implemented by a handful of VPN providers, but widespread adoption is just beginning.
Windscribe's commitment to Amnezia WG support means they're positioning themselves as one of the few mainstream VPN providers taking this seriously.
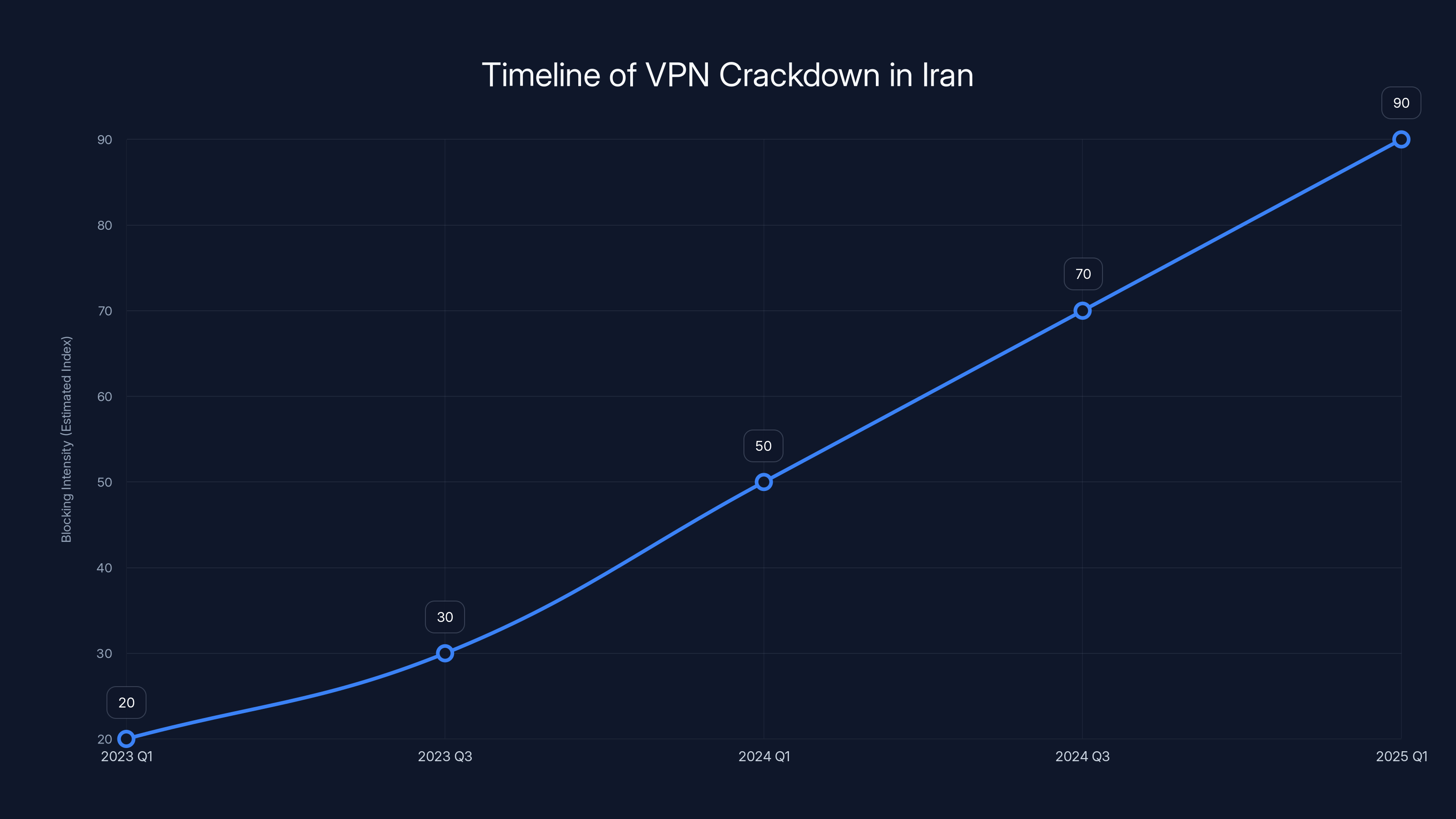
The intensity of VPN blocking in Iran increased significantly from late 2024, with deep packet inspection technology playing a key role. Estimated data based on reported trends.
Timeline: When Amnezia WG Support Will Roll Out
Windscribe hasn't released a specific date for Amnezia WG rollout, which is typical for security-focused features (announcing dates publicly makes it easier for governments to prepare countermeasures).
Based on similar deployments from other providers and Windscribe's public statements, here's a realistic timeline:
Q1 2025: Beta testing of Amnezia WG support with select users. Windscribe typically starts with a limited rollout to identify issues before broader deployment.
Q2 2025: Wider availability. Amnezia WG becomes available to most Windscribe users, though possibly as an optional protocol rather than default.
Q3 2025 onwards: Optimization and refinement. Based on real-world usage in restricted regions, Windscribe would refine performance and reliability.
These are estimates based on industry standards. The actual timeline could be faster or slower depending on technical challenges and priorities.
Why the timeline matters: if you're currently unable to use Windscribe in Iran or Russia, you need a solution now, not in Q2 2025. This is one of the difficult realities of the crackdown. Users need immediate solutions, but developers need time to build secure, effective solutions.
For users stuck in this gap, Windscribe has suggested other workarounds in the interim:
- Using older client versions that might have different signatures
- Trying different protocols and ports
- Combining Windscribe with other tools like proxy services
- Exploring other providers who already have obfuscation support
None of these are ideal. All require technical knowledge. But they exist as temporary solutions.
How Other VPN Providers Are Responding
Windscribe isn't alone in recognizing the Amnezia WG opportunity. Other providers are watching and some are already moving.
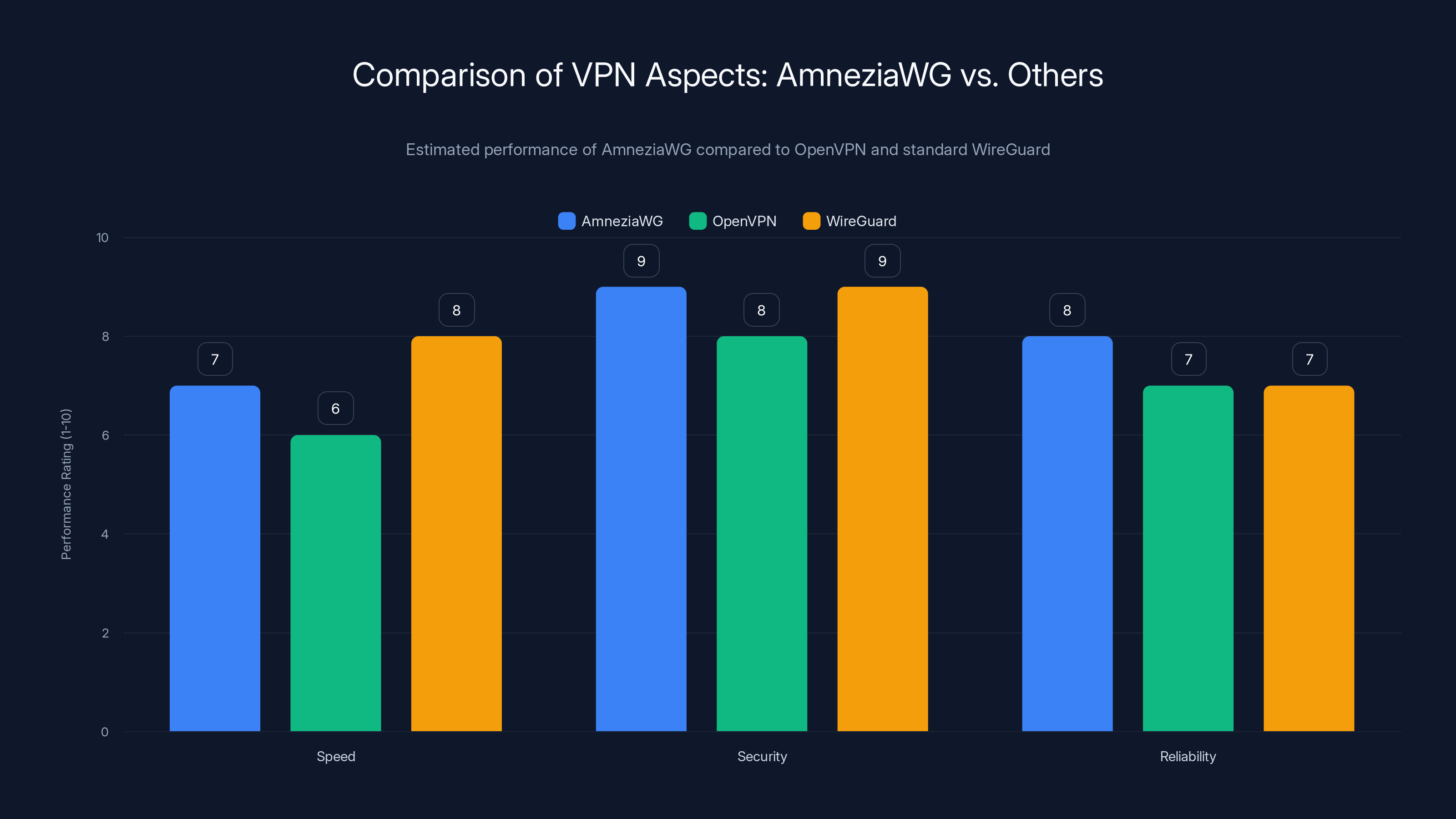
Mullvad VPN, another privacy-focused provider, has already implemented Amnezia WG support. They're one of the early adopters. Their deployment shows it's technically possible and genuinely effective.
Proton VPN hasn't officially announced Amnezia WG support, but they've invested heavily in their own obfuscation technology called Stealth Protocol. They're tackling the same problem with a different solution.
Express VPN, the market leader, uses their own obfuscation called Lightway. It's proprietary rather than open-source, which has advantages (they control the implementation) and disadvantages (less transparent to security researchers).
Surfshark offers obfuscation features but hasn't specifically committed to Amnezia WG.
The broader pattern: VPN providers are recognizing that standard protocols aren't sufficient anymore. They're investing in obfuscation. Some are open-source and transparent about their methods. Others are proprietary. But all are moving in the same direction.
For users, this fragmentation is frustrating. There's no universal solution. Different providers use different protocols. This means users in restricted regions have to experiment, to try different services, to find what works.
But it also means there's competitive pressure. If Windscribe successfully implements Amnezia WG and users in Iran and Russia report that it works, other providers will feel pressure to offer similar solutions. Competition drives innovation, even in the unusual market of circumvention technology.
Windscribe's public commitment is interesting partly because it creates accountability. By saying Amnezia WG is their highest priority, they're making a promise they'll be judged on. Users in restricted regions will test the implementation. They'll report if it works or doesn't. That public scrutiny is exactly what's needed to ensure companies actually follow through.
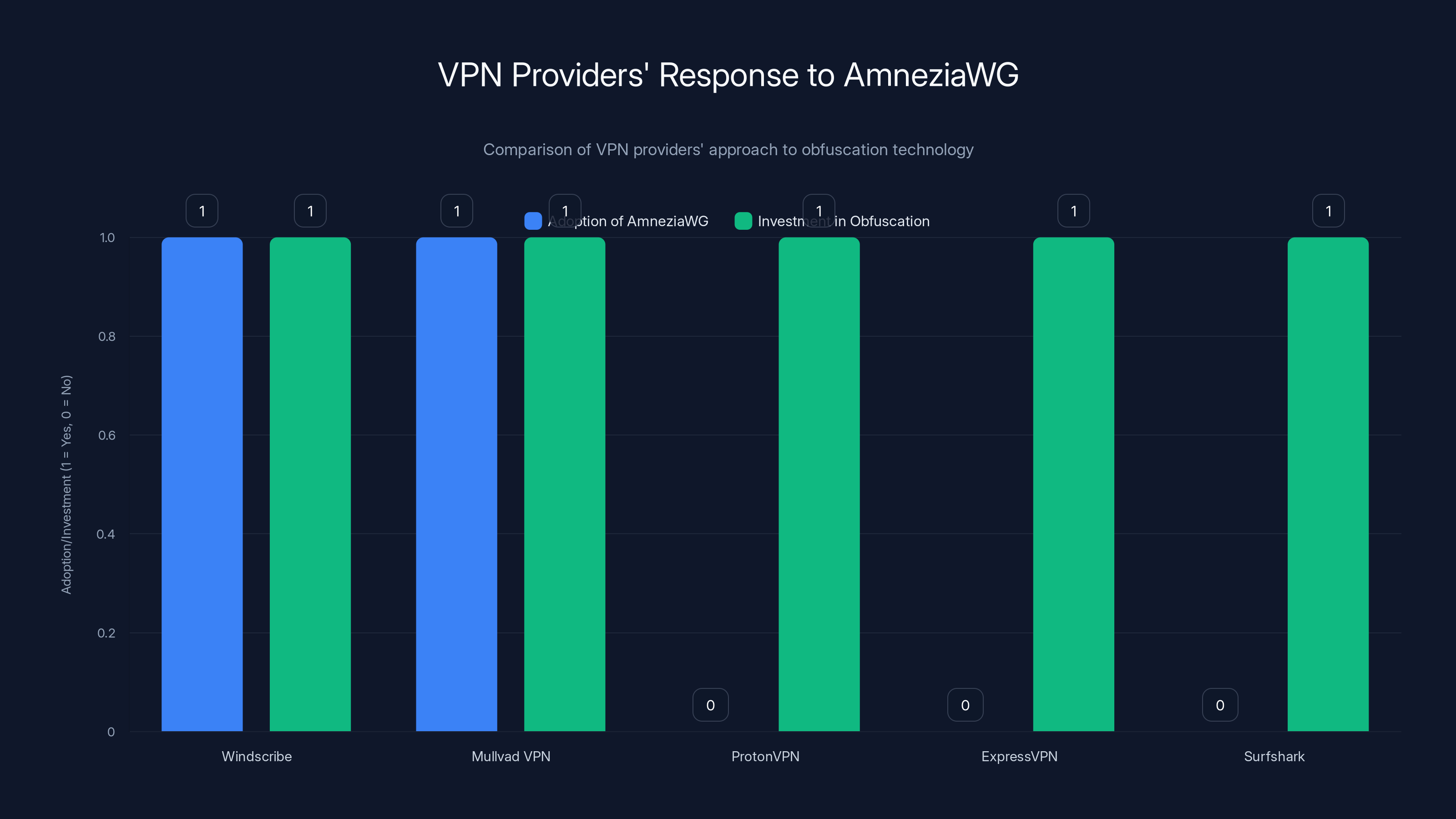
Most VPN providers are investing in obfuscation technologies, but only a few have adopted AmneziaWG. Estimated data based on current trends.
The Technical Challenges of Implementation
Implementing Amnezia WG across a global VPN network isn't just downloading some code and flipping a switch. It requires solving multiple technical problems.
Client Application Support: Windscribe needs to update their client applications for every platform. Windows client. mac OS client. i OS app. Android app. Linux client. Browser extensions. Each needs to be updated independently, tested, and deployed. This is significant engineering effort.
Server-Side Infrastructure: Every Windscribe VPN server worldwide needs to be configured to support Amnezia WG. That's potentially thousands of servers across dozens of countries. Deploying changes at that scale requires careful orchestration.
Performance Optimization: Obfuscation adds processing overhead. On high-end computers, this is negligible. On mobile devices, it could noticeably drain battery and slow performance. Windscribe needs to optimize the implementation so it's effective without being unusable.
Testing in Restricted Regions: The only way to know if Amnezia WG actually works is to test it in Iran and Russia. This requires cooperation from testers on the ground. It requires careful security practices so testers aren't putting themselves at risk. It requires anonymized feedback channels so testers can report honestly.
Future-Proofing: Once Amnezia WG is deployed, governments will study it. They'll analyze the traffic patterns. They'll try to develop blocking methods. Windscribe needs to think ahead about how to evolve the implementation to stay ahead of blocking attempts.
Each of these components is technically non-trivial. Together, they explain why Windscribe is treating this as their highest priority but can't just flip a switch tomorrow.
The company has been transparent about this complexity. They're not overpromising. They're not giving specific dates. They're saying this is important and they're working on it. That's actually the right approach.

Real-World Impact: What Users Are Experiencing
To understand why Windscribe's commitment matters, you need to understand what users in Iran and Russia are actually experiencing.
In Iran, reports from digital rights organizations indicate that VPN usage has become dramatically harder. A user in Tehran who could reliably access international news sites three months ago might now find their VPN connections dropping multiple times per day. Standard VPN apps stop working. Switching providers helps temporarily, then those get blocked too.
The experience is frustrating and stressful. Users are essentially in a technological arms race with their government. Every week, a new blocking method emerges. Every week, users and providers scramble to find workarounds.
For journalists, this is a professional crisis. For activists, it's a security threat. For ordinary people who just want to access information, it's infuriating.
Russian users report similar experiences, though the timeline was slightly different. Blocking intensified following 2024 developments. Users who previously used standard VPNs without issue started experiencing blocks.
What's different between Iran and Russia is the intensity. Iran's blocking appears more aggressive and sophisticated. Russia's blocking is more selective, sometimes targeting specific apps rather than entire protocols.
But the trajectory is clear in both countries: VPN usage is becoming harder, and traditional solutions are becoming less reliable.
For Windscribe users specifically, the experience has been mixed. The service still works for many users, but with increasing instability. Connections drop. Speeds are slower. The service that was reliable months ago is becoming unreliable.
Windscribe's commitment to Amnezia WG is a response to this situation. The company is essentially saying: "We see what's happening. We understand the urgency. We're prioritizing a technical solution that might actually work."
That commitment is valuable precisely because it's specific. It's not vague. It's not "we're improving security." It's "we're implementing Amnezia WG as our highest priority."

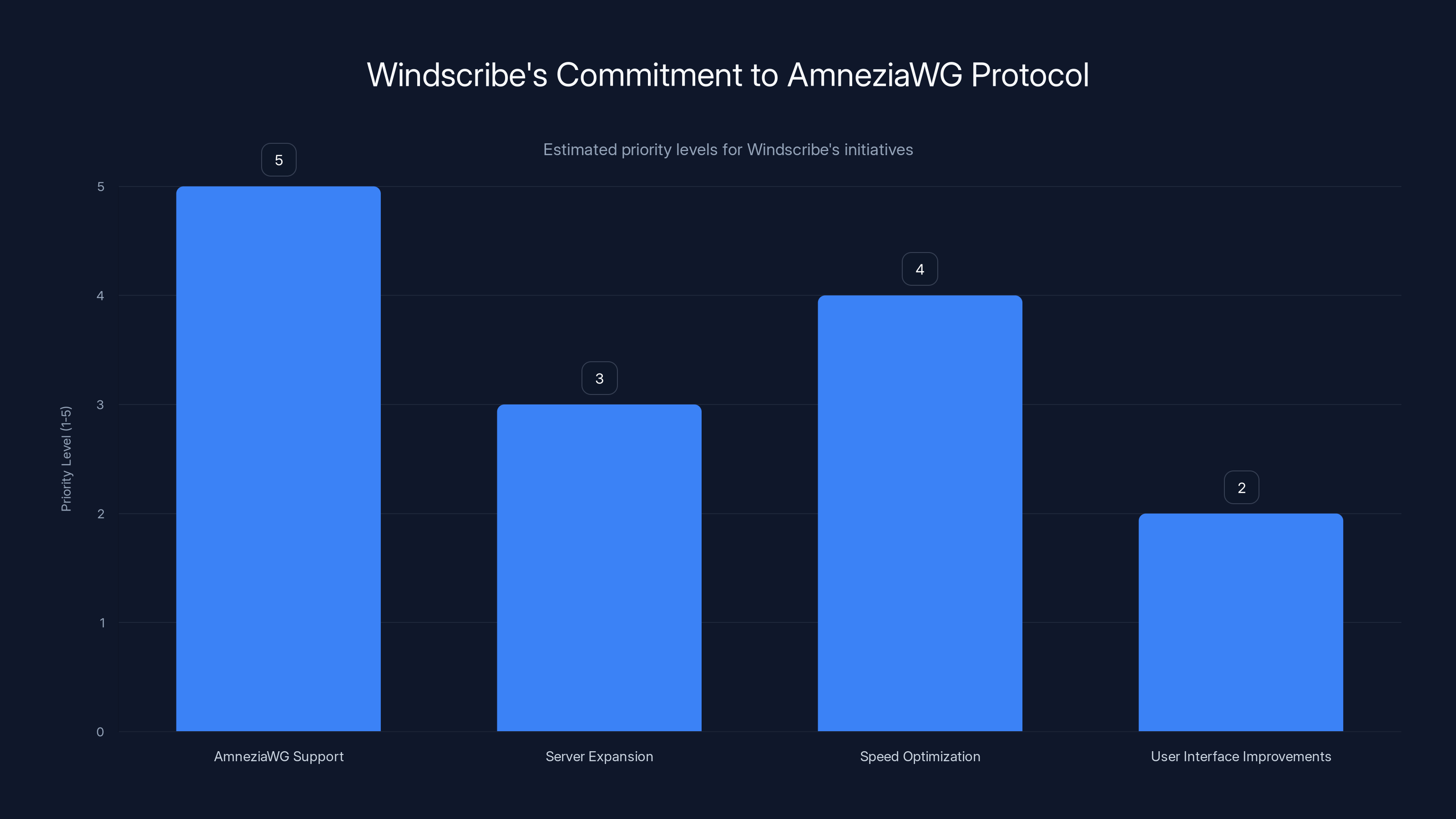
Windscribe has made AmneziaWG support their highest priority, reflecting the importance of obfuscation in VPN technology. Estimated data.
The Bigger Picture: Why This Matters Beyond Iran and Russia
You might be thinking: I don't live in Iran or Russia. Why should I care about Windscribe prioritizing Amnezia WG?
Because what's happening in Iran and Russia is a preview of what could happen elsewhere.
China already blocks VPNs extensively. The technology they use has been refined over years. But they're not the only government paying attention. Governments in Thailand, Vietnam, and other countries with internet restrictions are watching.
If Amnezia WG succeeds in Iran and Russia, other governments will study it and develop counter-measures. If it fails, governments will gain confidence that VPN blocking is achievable anywhere.
Beyond authoritarian governments, corporate networks and educational institutions sometimes block VPNs too. The same obfuscation techniques that circumvent government censorship can circumvent corporate firewalls.
There's also the fundamental technology question. If VPN protocols can be blocked by analyzing traffic patterns, what does that mean for network security and privacy long-term? Does encryption become less valuable if you can identify it by its signature?
Obfuscation answers that question partly. It suggests that effective privacy tools need to not only encrypt data but actively disguise their operation. This principle extends beyond VPNs to other privacy and security technologies.
Windscribe's commitment to Amnezia WG is part of a larger conversation about the future of internet privacy and what it will take to maintain privacy in increasingly hostile environments.

What About Speed, Security, and Reliability?
Amnezia WG improves obfuscation, but what about the other factors that matter for a VPN service?
Speed: This is where obfuscation creates trade-offs. Wrapping traffic adds processing overhead. Tests of Amnezia WG show it's faster than Open VPN (still pretty quick) but slightly slower than standard Wire Guard (the trade-off for obfuscation). For users in restricted regions, this is usually an acceptable trade-off. A slower connection that works beats a fast connection that's blocked.
Security: Amnezia WG is built on Wire Guard, which has a strong security reputation. The obfuscation layer adds additional security by preventing identification rather than adding encryption. Both aspects are important for users in restricted regions. You want strong encryption so your ISP can't see your traffic. You want obfuscation so they can't identify it as VPN traffic.
Reliability: This is critical. A VPN that works 50% of the time is worse than useless—it gives users false confidence. Amnezia WG's reliability depends on multiple factors: Windscribe's server infrastructure, the protocol's implementation quality, and how quickly it's updated as governments develop counter-measures. Early reports from Mullvad's deployment suggest reliability is solid, though like all circumvention tools, it's never perfect.
Logging Policies: Windscribe maintains a no-logs policy, meaning they don't record user activity. This is important for security and privacy. The Amnezia WG implementation doesn't change this—it's just a different way of transmitting data through Windscribe's network.
Jurisdiction: Windscribe is incorporated in Canada, which is generally favorable for privacy-conscious companies. They're not subject to Chinese, Russian, or Iranian law, which provides some protection against forced disclosure or backdoors.
For users in restricted regions, these factors matter. Security without reliability is worthless if the service doesn't work. Obfuscation without speed creates a bad user experience. Windscribe needs to balance all these factors.
Their choice to prioritize Amnezia WG suggests they've done the analysis and concluded that obfuscation is the most critical factor right now. That seems reasonable given the current landscape.

Alternative Solutions Currently Available
While Windscribe develops Amnezia WG support, users in restricted regions aren't without options. Several workarounds exist, though none are perfect.
Other Obfuscation Protocols: Mullvad VPN already supports Amnezia WG. Proton VPN offers Stealth Protocol. These provide alternatives if Windscribe's timeline is too slow.
Proxy Services: Instead of VPN, some users use proxy services like Shadowsocks or V2 Ray. These are lighter-weight than VPNs and some have built-in obfuscation. They're more technical to set up but can be effective.
Combining Tools: Some users combine VPN with proxy services, or use multiple VPNs in sequence. This adds complexity but provides additional obfuscation layers.
Wireguard Tunneling: Some implementations tunnel Wire Guard traffic through obfuscation proxies, achieving similar effects to Amnezia WG but through different technical means.
Tor: For users who can tolerate lower speeds, Tor Browser provides strong anonymity and circumvents many blocks. It's slower than VPN but much harder to block.
None of these are ideal for general internet browsing. Each has trade-offs. But together, they represent the current landscape of tools available to users in restricted regions.
Windscribe's commitment to Amnezia WG is valuable partly because it might consolidate these scattered solutions into something more user-friendly and accessible.

Government Response and Counter-Measures
Here's the uncomfortable truth: once Amnezia WG is deployed widely, governments will study it. They'll hire researchers. They'll analyze traffic. They'll develop blocking methods.
History suggests this pattern is inevitable. Every obfuscation technique that works for a while eventually gets blocked. The only question is how long the window of effectiveness is.
Iran's deep packet inspection systems are sophisticated enough that they can theoretically develop Amnezia WG detection if they commit resources to it. The obfuscation isn't magic—it's just clever traffic manipulation. Clever traffic manipulation can be analyzed and understood.
Russia's blocking approach gives them another angle of attack. Even if they can't block based on traffic patterns, they might block VPN apps directly by identifying their code signatures. Or they might mandate that ISPs require identification to access certain ports.
This doesn't mean Amnezia WG is worthless. It means that like all circumvention tools, it's part of an ongoing arms race. For a period of time—months, maybe a year—it could be genuinely effective. Then the situation evolves, and new solutions are needed.
VPN providers understand this. That's why they don't make permanent promises. They make good-faith efforts to stay ahead, but they know the situation is always changing.
Windscribe's commitment to Amnezia WG as their "highest priority" makes sense in this context. They're not saying "this is the final solution." They're saying "this is the most important thing we're working on right now."
After Amnezia WG is deployed and becomes less effective, they'll have to develop the next solution. Maybe it's something we haven't invented yet. The cycle continues.

Implications for Internet Freedom Advocates
For organizations working on internet freedom—Access Now, Opennet Initiative, Citizen Lab, and others—Windscribe's commitment matters.
When major companies publicly commit to developing solutions for censored regions, it sets expectations and creates accountability. It signals that internet freedom is worth investing in. It shows that some companies see this not just as a product feature but as a fundamental principle.
It also creates practical benefits. As Windscribe develops and deploys Amnezia WG, they'll generate data about what works. They'll publish technical details that other developers can learn from. They might contribute to open-source projects that benefit the broader ecosystem.
Internet freedom advocates often criticize VPN companies for not doing enough to help restricted users. Windscribe's specific commitment to Amnezia WG is the kind of concrete action that moves the needle.
That said, corporate solutions alone aren't enough. Open-source tools, community-driven projects, and grassroots innovation are also essential. No single company can solve censorship. But companies with resources and expertise can contribute meaningfully.

A Peek Into the Future of VPN Technology
If you zoom out, Windscribe's Amnezia WG commitment tells us something about the direction VPN technology is heading.
The next generation of VPNs will likely be defined not by speed or features but by obfuscation capability. The ability to disguise traffic will become the primary differentiator.
This means VPN client software will become more complex. Simple apps that just encrypt and route traffic will become insufficient. You'll need sophisticated obfuscation handling.
It also means that "VPN" as a category might evolve. The distinction between VPN, proxy, and other circumvention tools could blur. What matters is whether it works, not what you call it.
For users, this means more technical knowledge might be required to use these tools effectively. Default settings might not be optimal. Understanding which protocol to use in which situation might become necessary.
But it also means better tools will eventually emerge. Necessity drives innovation. As restrictions increase, the creative solutions increase too.
Windscribe isn't unique in moving in this direction. But their public commitment makes them a bellwether. If they successfully deploy Amnezia WG and it works, other providers will follow. If they struggle, other providers will learn from the mistakes.
Either way, the next few months are important. Windscribe's implementation will set expectations for how the industry responds to advanced VPN blocking.
Key Takeaways for Different Audiences
For users in Iran and Russia: Windscribe's Amnezia WG commitment means relief might be coming. In the interim, explore Mullvad VPN which already supports the protocol. Consider alternative tools if you need a solution immediately. Stay informed about deployment timelines.
For other VPN users: This development likely won't affect you immediately. But watch this space. If Windscribe successfully implements Amnezia WG, other providers will follow. It might become a standard feature across the industry.
For privacy advocates: Windscribe's commitment shows that some companies take internet freedom seriously. Support providers who publicly commit to helping restricted users. Use your platform to hold them accountable for following through.
For technologists and security researchers: Amnezia WG is interesting technology worth understanding. Following this implementation will provide insights into how obfuscation technology works and how it might evolve.
For governments and policymakers: The VPN blocking arms race continues. If you're considering implementing VPN restrictions, understand that technology will develop to circumvent them. The only way to maintain information control long-term is through legal and social controls, not technological ones.

FAQ
What exactly is Amnezia WG and how does it differ from regular Wire Guard?
Amnezia WG is a variant of the Wire Guard protocol that adds obfuscation layers to disguise VPN traffic. While regular Wire Guard is optimized for speed and simplicity, Amnezia WG sacrifices some speed to add traffic obfuscation that makes it harder for deep packet inspection systems to identify it as VPN traffic. The underlying encryption and security model remains Wire Guard's strong foundation, but the traffic signature is altered to appear as regular encrypted internet traffic rather than a distinctive VPN protocol.
Why haven't other VPN companies committed to Amnezia WG like Windscribe has?
Multiple factors influence this decision. Some providers have already implemented Amnezia WG (like Mullvad) or developed their own obfuscation protocols (like Proton VPN's Stealth Protocol). Others may be evaluating the technology or waiting to see if it's truly effective before committing resources. VPN companies balance speed-to-market with security considerations, and rushing to deploy untested circumvention solutions in restricted regions could harm users. Windscribe's public commitment was notable partly because it's unusual for companies to be this specific about priorities.
When will Amnezia WG be available for all Windscribe users?
Windscribe hasn't provided a specific date, which is typical for security-sensitive features. Based on industry timelines and the company's public statements, realistic expectations are mid-2025 for wider availability, though this could shift. The company is likely conducting testing in restricted regions to ensure the implementation actually works before broader rollout. Users needing immediate solutions shouldn't wait for this deployment; alternatives exist now.
If I'm in Iran or Russia, should I switch to Mullvad VPN now instead of waiting for Windscribe?
If your current VPN isn't working, switching to Mullvad VPN (which already supports Amnezia WG) makes sense. If Windscribe is still functional but becoming unreliable, you might try experimenting with Amnezia WG on Mullvad while keeping Windscribe as a backup. Different protocols work differently in different regions and ISPs, so personal testing is valuable. Also consider your existing Windscribe subscription investment; switching providers has its own costs and learning curve.
Is Amnezia WG actually effective against government blocking, or will it just be blocked soon after deployment?
Based on initial reports from Mullvad VPN's implementation, Amnezia WG appears genuinely effective at avoiding detection in restricted regions. However, all circumvention technologies face this timeline: they work until governments study them and develop counter-measures. Amnezia WG probably provides several months to a year of reliable effectiveness before advanced blocking methods are developed. This doesn't make it worthless—a solution that works for months is vastly better than one that never works—but it's important to understand this is a temporary advantage, not a permanent solution.
Do I need to manually switch to Amnezia WG when it's available, or will it be automatic?
Windscribe will likely provide the protocol as an option that users can select in their settings, similar to how they currently offer other protocols. Early in the rollout, users will probably need to manually switch to it. Over time, it might become the default for users in restricted regions. It will depend on Windscribe's implementation strategy, which they haven't detailed yet. When the feature becomes available, their documentation will explain how to enable it.
What if Amnezia WG doesn't work for my specific ISP in Iran or Russia?
Different ISPs use different detection methods and blocking strategies. What works on one ISP might not work on another. If Amnezia WG doesn't work on your connection, you'd likely need to try other protocols or providers. This is where the multi-tool approach becomes valuable: having access to VPN, proxy, and other circumvention tools increases your chances of finding something that works on your specific ISP. Windscribe's support channels might also provide ISP-specific guidance once Amnezia WG is deployed.
Is Windscribe's no-logs policy still valid if they're implementing Amnezia WG?
Yes. Amnezia WG is just a different protocol for transmitting data through Windscribe's servers. The company's logging practices—or lack thereof—aren't affected by which protocol users employ. Windscribe's no-logs policy is a business decision and legal commitment, separate from the technical protocol used. Amnezia WG obfuscates traffic from ISP-level monitoring but doesn't prevent Windscribe servers from logging if they chose to. The company's stated no-logs policy continues to apply.
How does obfuscation actually work technically? Isn't encryption enough?
Encryption solves the problem of others reading your data. Obfuscation solves the problem of others knowing you're using a VPN at all. Deep packet inspection can identify VPN traffic even without reading the encrypted content by analyzing packet size patterns, timing, connection initiation sequences, and other characteristics. Obfuscation adds layers that change these recognizable patterns, making encrypted VPN traffic look like regular HTTPS or other encrypted traffic. Together, encryption and obfuscation provide both privacy (encryption) and anonymity from ISP-level identification (obfuscation).
Conclusion: The Windscribe Moment
Windscribe's commitment to prioritizing Amnezia WG support matters not because it's a complete solution to government censorship—it's not—but because it represents a tech company taking a concrete stand on an important issue.
In the world of VPN providers, it's easy to be cynical. Most companies make vague commitments. They promise "improved service" and "enhanced security." They rarely follow through in meaningful ways. Windscribe's specific commitment to a specific protocol is refreshing partly because it's specific.
For users in Iran and Russia, this commitment means hope. It means a major VPN provider is actively working on solutions tailored to their situation. It means someone is paying attention to their needs and investing resources to address them.
For the broader internet freedom community, it sets a precedent. If Windscribe succeeds, other providers will face pressure to make similar commitments. Success doesn't require perfect solutions—just good-faith efforts to stay ahead of blocking technologies.
The timeline is uncertain. The implementation challenges are real. The likelihood that Amnezia WG eventually becomes less effective is high. But that's how circumvention technology works. It's always temporary. It's always in motion.
Windscribe understands this. They're not promising a permanent solution. They're promising a current priority and specific direction. That's the most any company can reasonably commit to in this landscape.
The next few months will be crucial. As Windscribe develops and tests Amnezia WG, we'll learn whether obfuscation can truly evade detection or whether governments have countermeasures ready. We'll learn whether the company can scale the protocol across thousands of servers without reliability issues. We'll learn whether users will adopt it and whether it actually improves the experience for people in restricted regions.
Until then, users in Iran and Russia continue navigating an increasingly hostile digital environment. For them, Windscribe's commitment is more than a press release. It's a signal that their situation matters to some companies, and that solutions—imperfect, temporary, but real—are being developed.
That's not nothing. In the realm of internet freedom, it's actually significant.
For everyone else, pay attention to this story. How Windscribe executes on their commitment will tell us something important about the future of internet privacy. Whether obfuscation actually works against advanced detection systems will influence how VPN technology develops globally. Whether major companies follow Windscribe's lead will determine whether internet freedom becomes a priority across the industry.
The crackdown in Iran and Russia is a preview of what could happen elsewhere. The solutions being developed now might be needed globally later. Understanding this moment—what's being attempted, why it matters, and what challenges remain—provides insight into the future of digital privacy and freedom.
Related Articles
- Uganda Internet Restored But Social Media Blocked: What's Really Happening [2025]
- Iran's Digital Isolation: Why VPNs May Not Survive This Crackdown [2025]
- Russia's VPN Crackdown 2026: New Laws & Blocking Tactics [2025]
- Are VPNs Really Safe? Security Factors to Consider [2025]
- Why Brits Fear Online Privacy But Trust the Wrong Apps [2025]
- I Tested a VPN for 24 Hours. Here's What Actually Happened [2025]
![Windscribe VPN Iran Russia Crackdown: AmneziaWG Solutions [2025]](https://tryrunable.com/blog/windscribe-vpn-iran-russia-crackdown-amneziawg-solutions-202/image-1-1769791130426.jpg)



